Welcome “Frappo” – The new Phishing-as-a-Service used by Cybercriminals to attack customers of major financial institutions and online-retailers
Cybercrime Intelligence

The Resecurity HUNTER unit identified a new underground service called “Frappo”, which is available in the Dark Web. “Frappo” enables cybercriminals the ability to host and generate high-quality phishing pages which impersonate major online-banking, e-commerce, popular retailers, and online-services to steal customer data.
“Frappo” acts as a Phishing-as-a-Service – providing anonymous billing, technical support, updates, and the tracking of collected credentials via a dashboard. Initially, the service popped up in the Dark Web around 22ndMarch, 2021, and has been significantly upgraded since then.
Most recently, it provided phishing pages for over 20 financial institutions (FIs), online-retailers and popular services such as Uber.
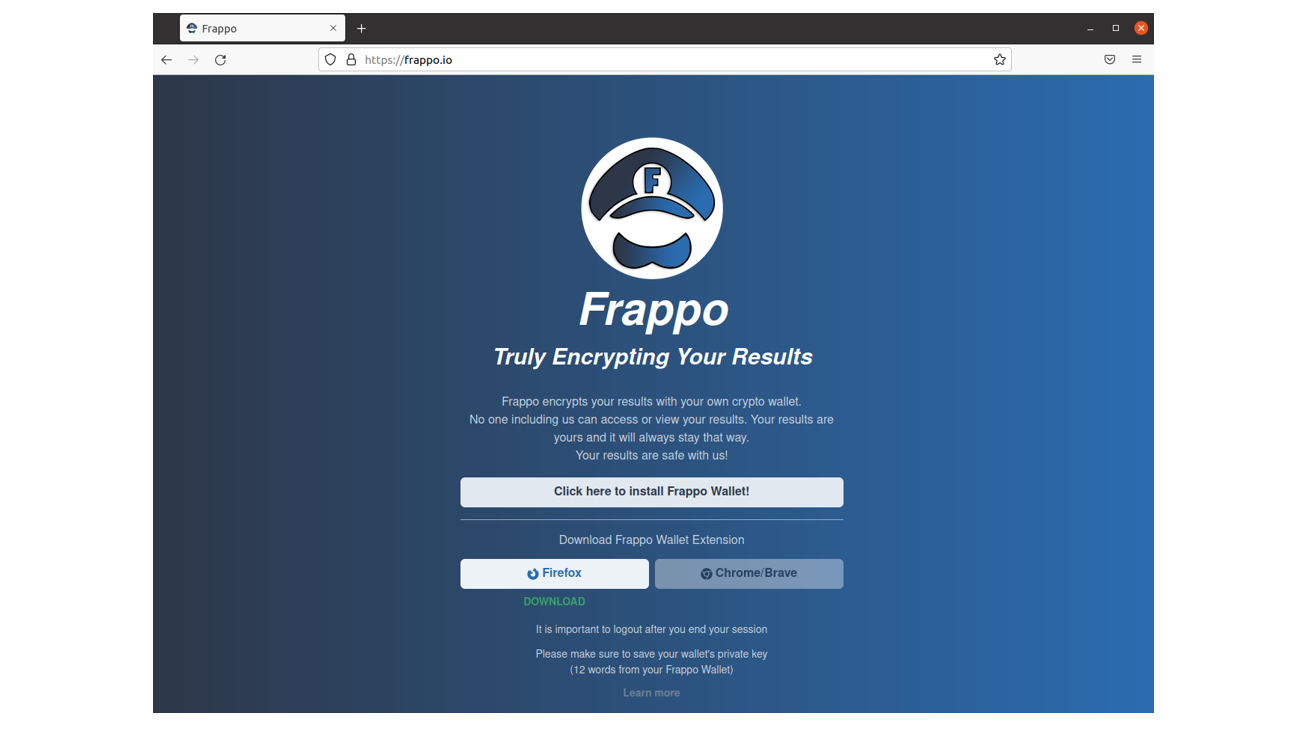
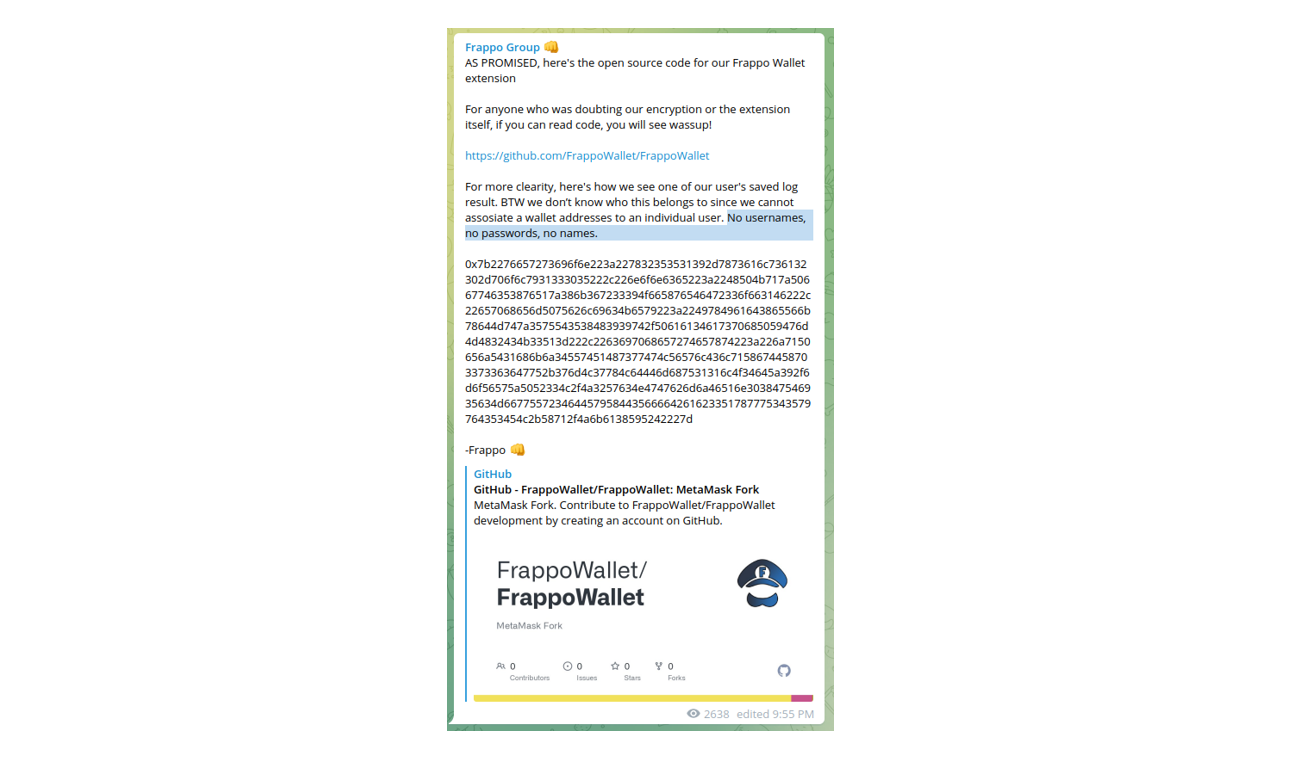
It’s worth noting, upon first inspection “Frappo” was designed to be an anonymous cryptocurrency wallet. However, the project with a similar name is currently available on GitHub (https://github.com/FrappoWallet/FrappoWallet) which allows software developers to integrate payment methods which support Ethereum and Bitcoin. Technically, it is a “MetaMask-like” browser extension providing the ability to browse blockchain enabled websites.
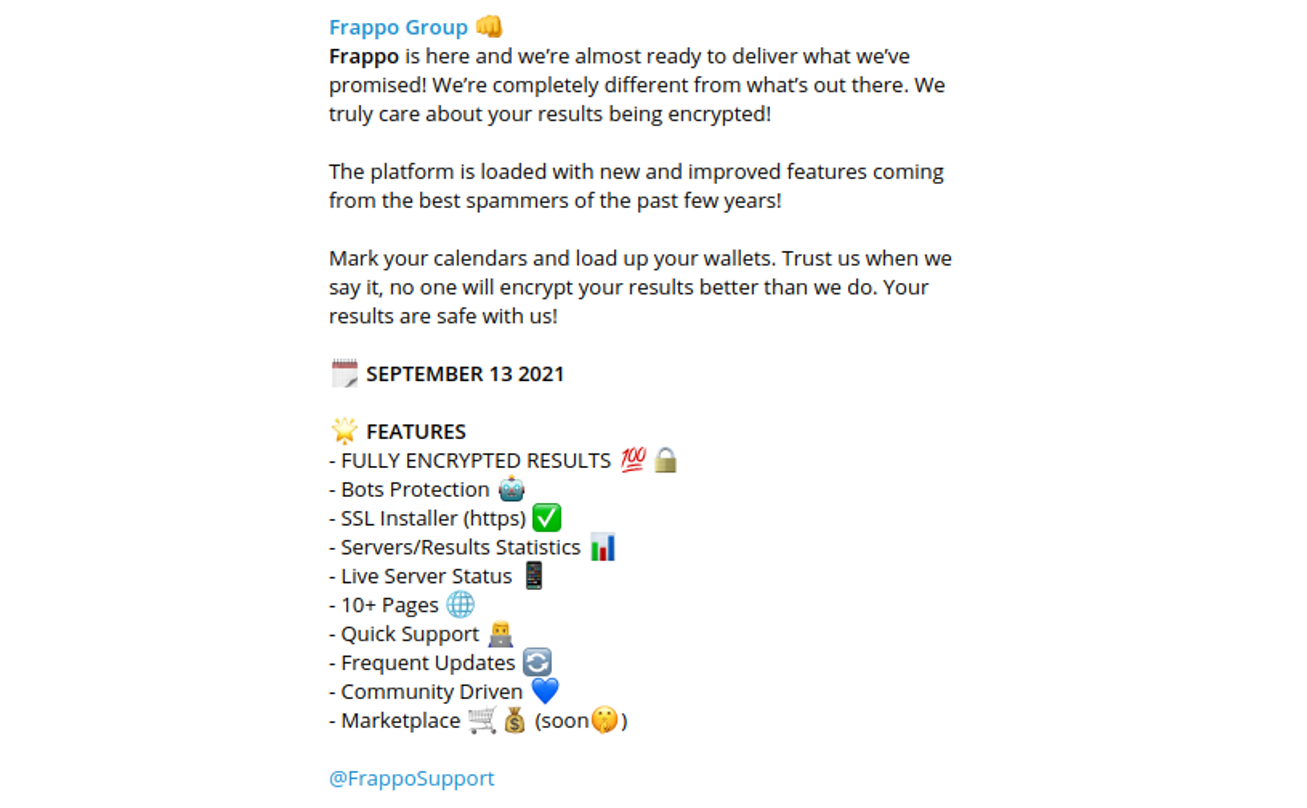
“Frappo” is completely anonymous and doesn’t require a threat actor to register an account.
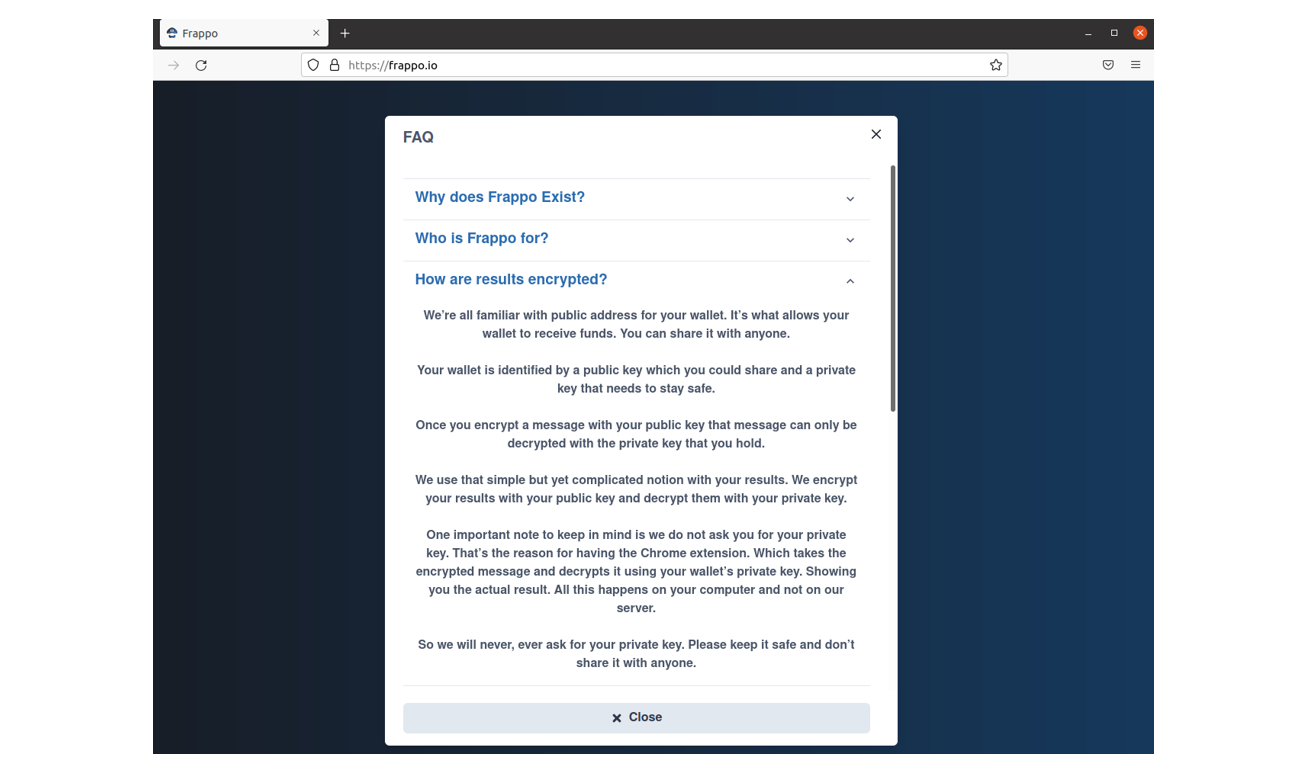
“Frappo” claims to guarantee end users high anonymity and encryption which is a very attractive component for cybercriminals:
Cybercriminals are granted the ability to work with stolen data anonymously and in an encrypted format:
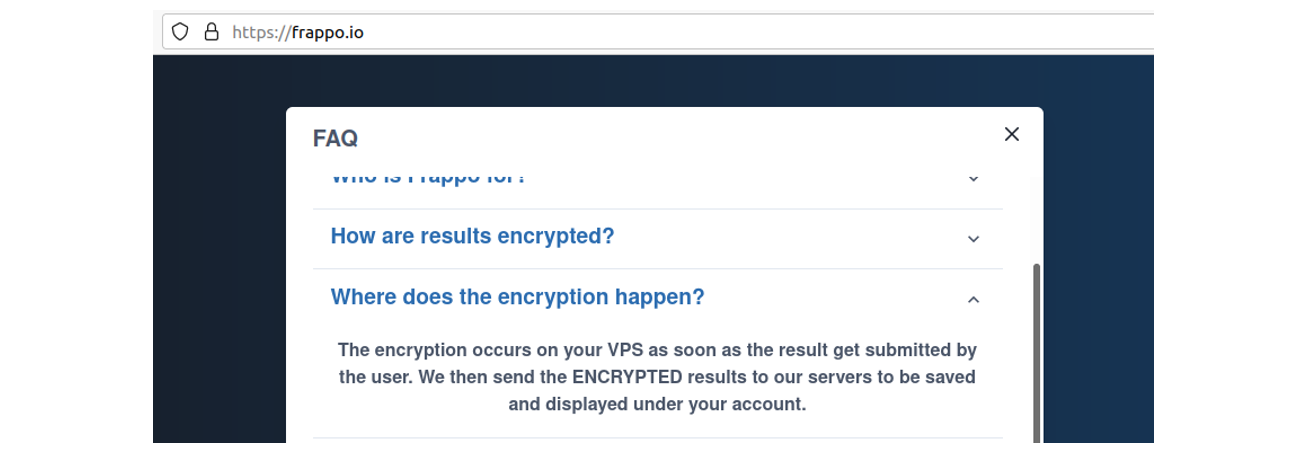
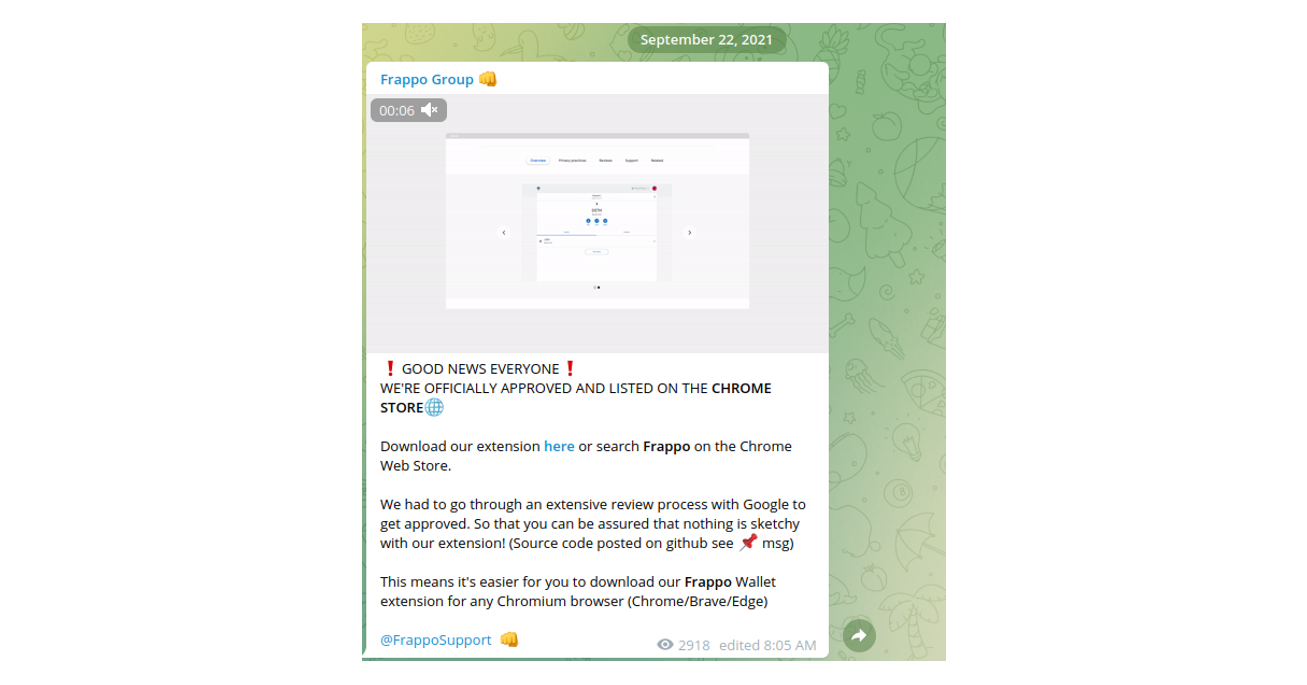
Interestingly, the actors were able to publish “Frappo” in the Chrome Store, this was done in the form of an extension which grants instant activation:
https://chrome.google.com/webstore/detail/frappo/mhoekmcdfpahflkdfgejnnjjigbagbpl
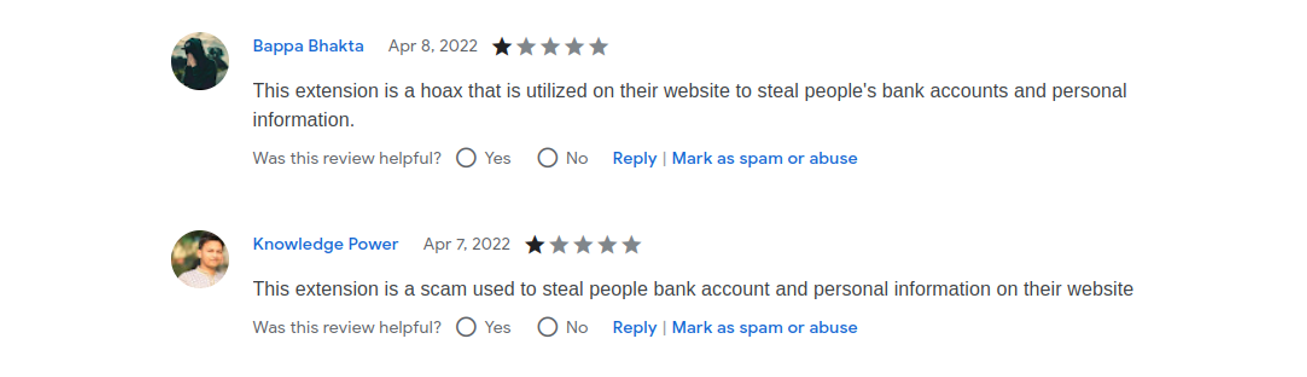
According to users’ feedback, it’s unlikely this extension is for good purposes, and could be used to steal personal data:
To activate the extension, all that’s needed is to install the browser plugin on FireFox or Google Chrome, and then proceed further with a payment.
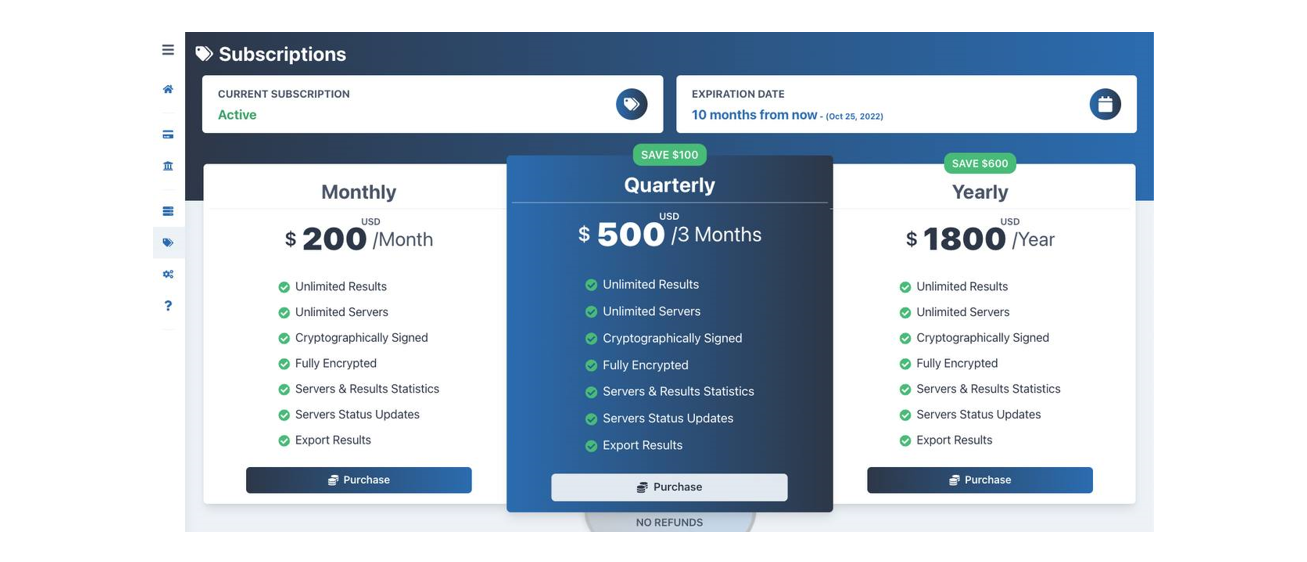
The authors of “Frappo” provide several payments plans for cybercriminals depending on their chosen duration of the subscription. Like a SaaS-based services and platform for legitimate businesses, “Frappo” allows cybercriminals to minimize costs for the development of phishing-kits, and to use the same on the bigger scale.
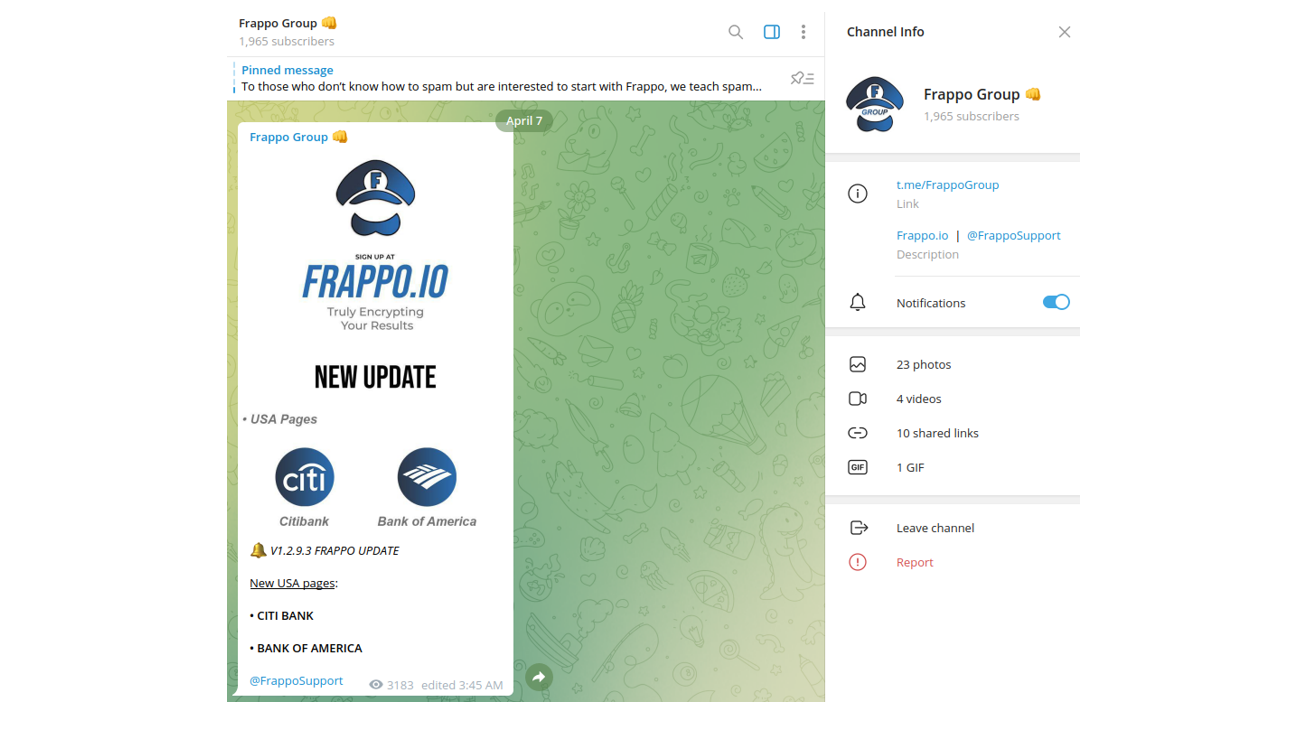
Customer support is available via a secure Telegram IM, and in the group are over 1,965 members – this is highly likely where other cybercriminals discuss how successful they’ve been attacking the customers of various online-services, or to request additional assistance.
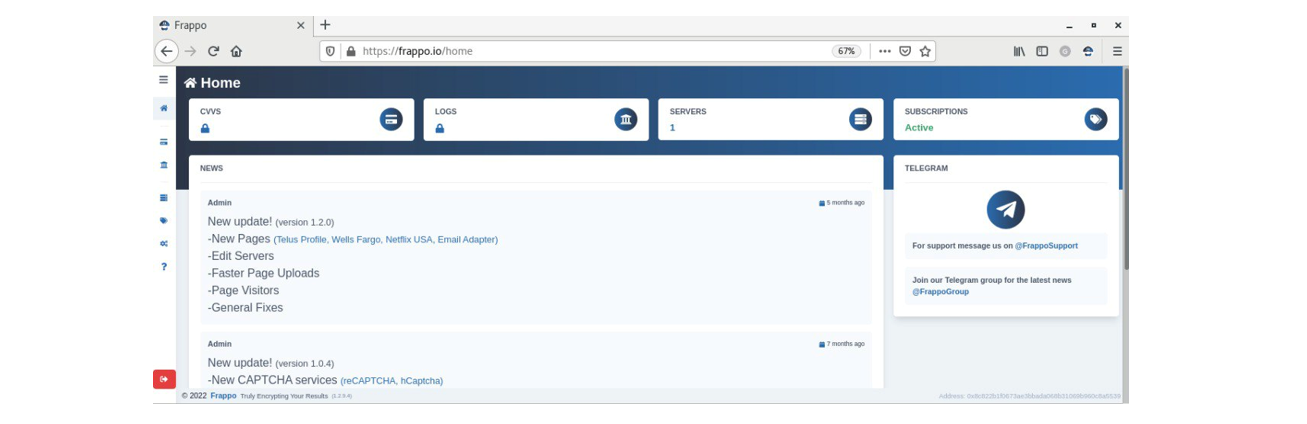
Once “Frappo” is activated, the operator will see the following navigation menu allowing them to generate a new phishing page (or “phishlet”) followed by the ability to host it:
1 - New update
2 - New Pages
3 - Edit servers
4 - Faster Page Upload
5 - Page Visitors
6 - General Fixes
“Frappo” then provides an interactive wizard allowing the operator to configure settings, define server credentials, and choose the brand to impersonate. The available phishing pages are categorized by brand and profile:
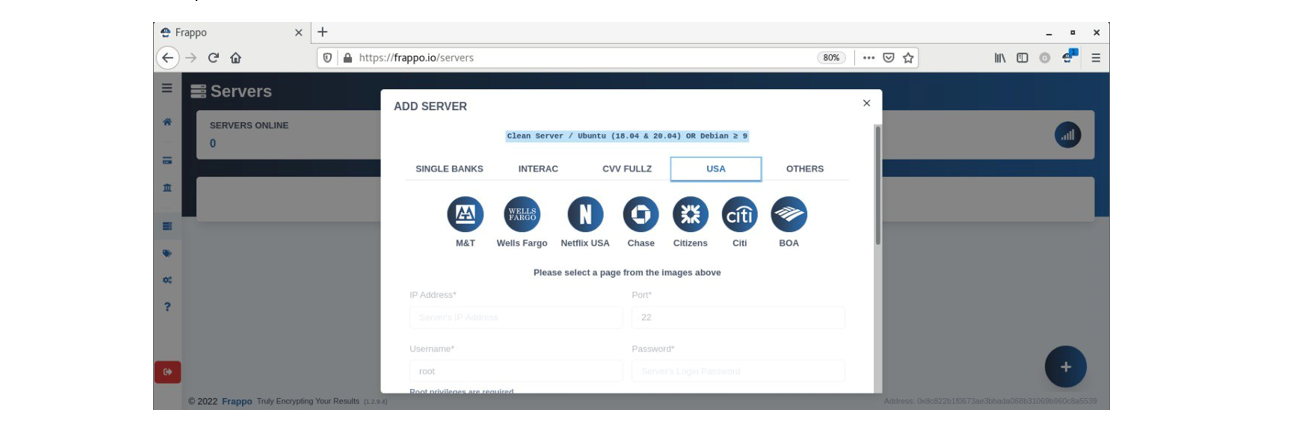
Category “SINGLE BANKS” includes major financial institutions from Canada:
- Scotia
- BMO
- CIBC
- ATB
- RBC
- Tangerine
- TD
- Desjardins
Category “INTERAC” includes various customized phishing templates to steal payment data and credit card details:
- Fullz
- Custom
- Costco
Category “USA” includes phishing pages with designs surrounding major financial institutions in the U.S.:
- M&T
- Wells Fargo
- Netflix USA
- Chase
- Citizens
- Citi
- BOA
Category “OTHERS” includes phishing pages for well-known e-mail and customer authorization front-ends:
- Roundcuble
- TELUS Profile
- Email Adapter
Category “CVV FULLZ” includes various templates designed as popular consumer apps including online-retailer, TV streaming, and major ISP:
- Amazon
- Uber
- Netflix
- Rogers
Notably, the templates used for credit card data interception supports multiple payment systems which include AMEX, Discover, Diners, Mastercard, UnionPay and even Russian MYR.
// starts with 34/37; 15 digits amex: /^3[47]\d{0,13}/, // starts with 6011/65/644-649; 16 digits discover: /^(?:6011|65\d{0,2}|64[4-9]\d?)\d{0,12}/, // starts with 300-305/309 or 36/38/39; 14 digits diners: /^3(?:0([0-5]|9)|[689]\d?)\d{0,11}/, // starts with 51-55/2221–2720; 16 digits mastercard: /^(5[1-5]\d{0,2}|22[2-9]\d{0,1}|2[3-7]\d{0,2})\d{0,12}/, // starts with 5019/4175/4571; 16 digits dankort: /^(5019|4175|4571)\d{0,12}/, // starts with 637-639; 16 digits instapayment: /^63[7-9]\d{0,13}/, // starts with 2131/1800; 15 digits jcb15: /^(?:2131|1800)\d{0,11}/, // starts with 2131/1800/35; 16 digits jcb: /^(?:35\d{0,2})\d{0,12}/, // starts with 50/56-58/6304/67; 16 digits maestro: /^(?:5[0678]\d{0,2}|6304|67\d{0,2})\d{0,12}/, // starts with 22; 16 digits mir: /^220[0-4]\d{0,12}/, // starts with 4; 16 digits visa: /^4\d{0,15}/, // starts with 62/81; 16 digits unionPay: /^(62|81)\d{0,14}/ }, |
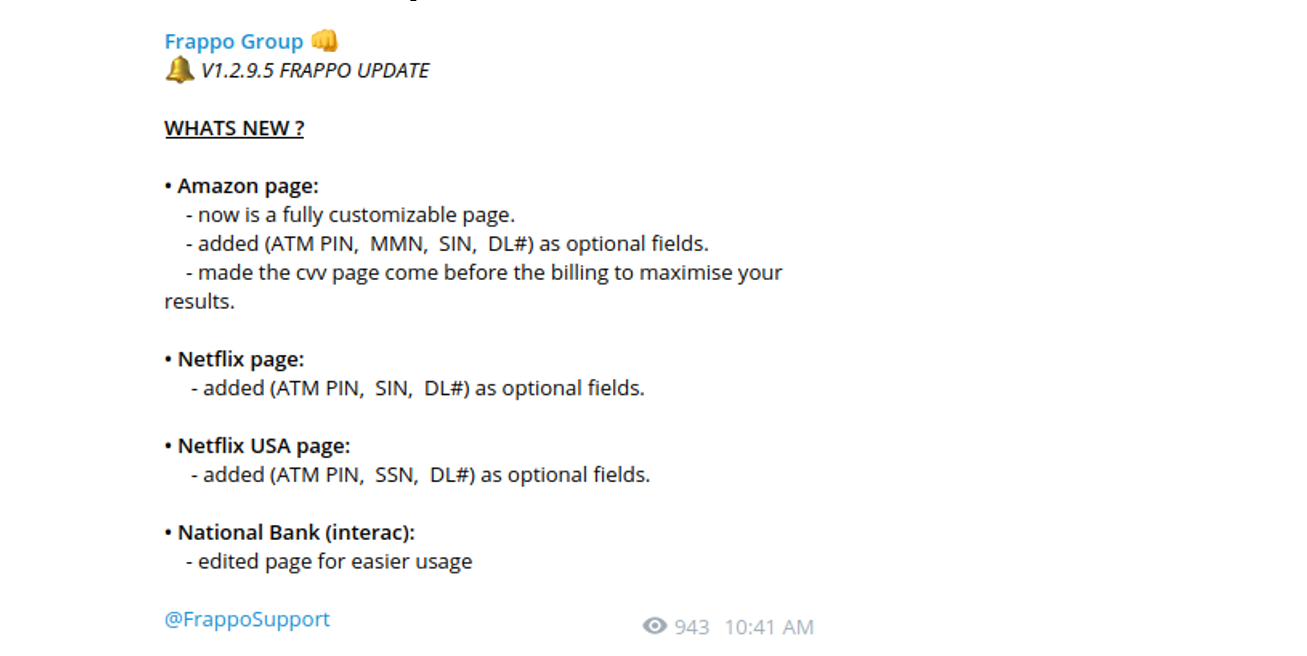
Interestingly, one of the recent updates issued on April 22nd, “Frappo” began supporting PINs interception to trick victims into entering it:
Cybercriminals may use their own VDS/VPS or bulletproof servers to integrate “Frappo”. After the server credentials have been defined, the operator is then asked to configure the phishing campaign tracking settings. The service also provides a Free SSL Certificate generation service enabling the delivery of phishing content via a secure HTTPS connection.
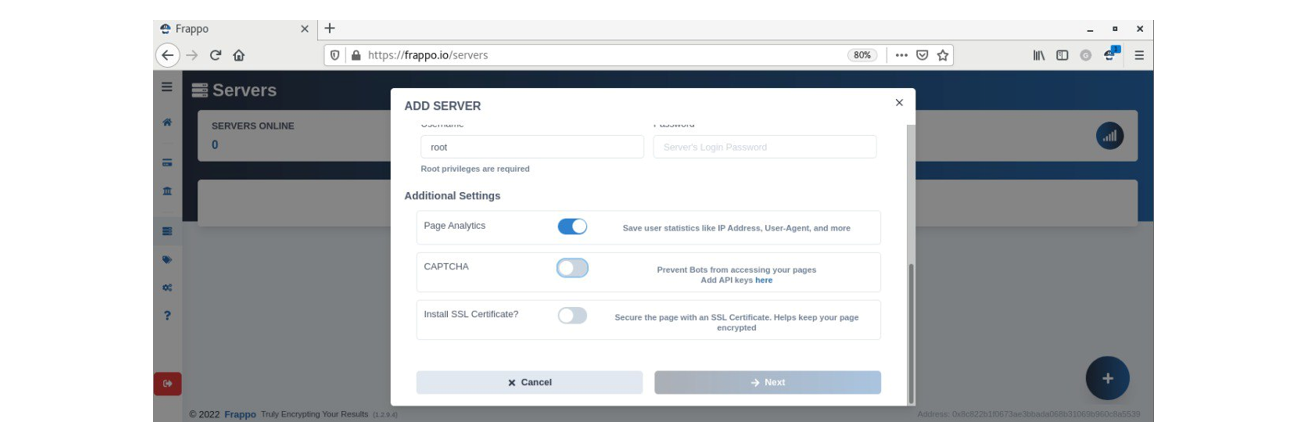
Additional configuration options enable mobile versions of phishing pages which target victims using mobile devices or tables like Apple iPhone, iPad, or Google Android. “Frappo” also provides “Geo Lock” options which allow filtering hosts accessing the phishing kit, making it strictly available to victims from particular regions, e.g. the U.S.:
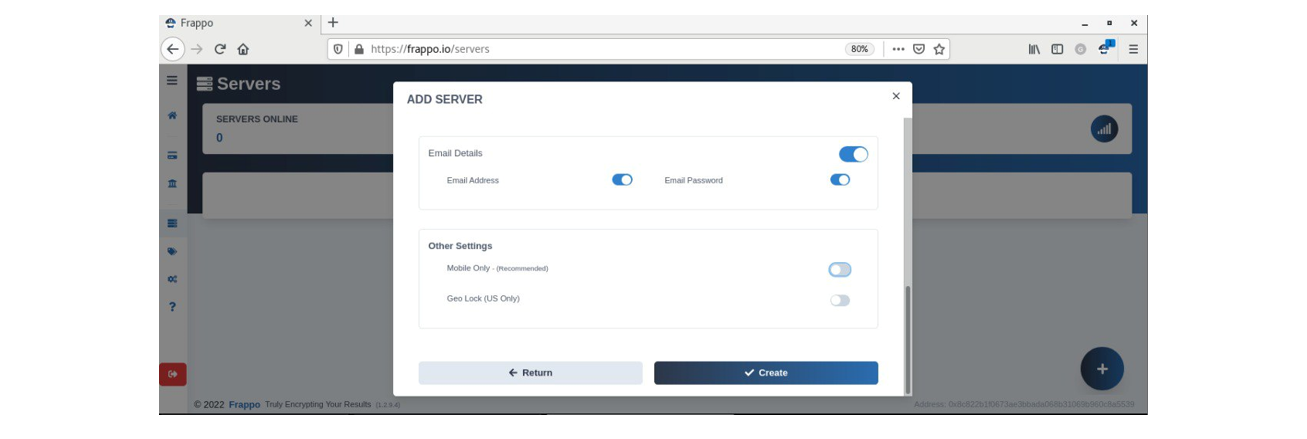
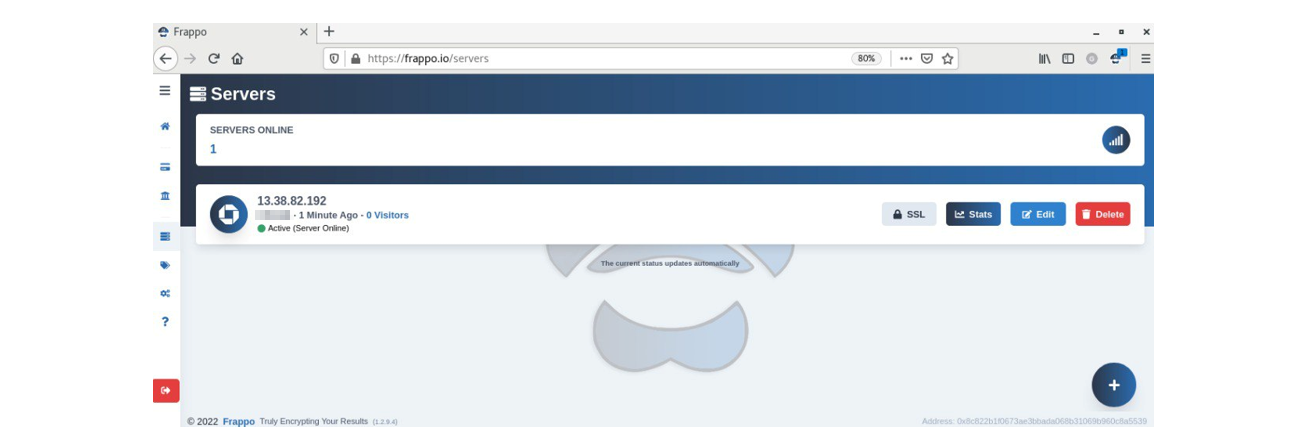
Once the instance is properly configured, the server will be visible in the listing with further statistical data being collection – such as how many victims opened the phishing page, accessed authorization and entered credentials, uptime, and the server status (in the event it gets banned by an ISP or hosting provider). If the server goes offline, “Frappo” will send an alert via a Telegram notification.
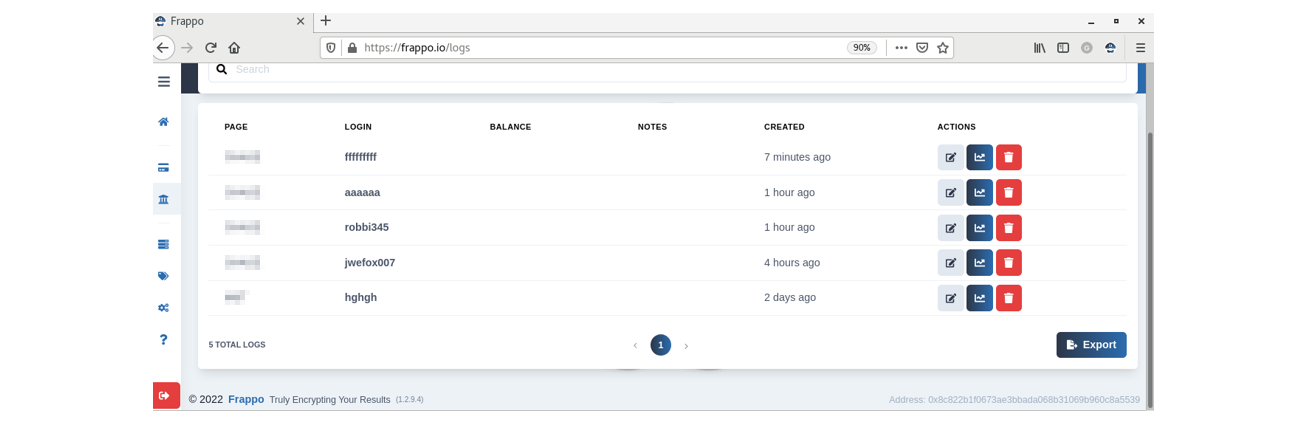
Compromised credentials will be visible in the “Logs” section with additional details about each victim (IP address, User-Agent, Username, Password, Referrer, and etc.):
Resecurity HUNTER team was able to analyze the installation process and packages delivered by the “Frappo” server-side via SSH. The service drops interactive installation packages allowing deployment of the phishing-kit, and enables an API to “Frappo” for further statistics collection, management, and updates. Notably, the actors request SSH credentials with significant privileges, this is done because they’re also installing additional services in the system which include the addition of a user. Such tactics could then be used for potential credential theft of other cybercriminals who use “Frappo” – what has been detected on practice by various password stealers and online-banking trojans having hidden backdoors or vulnerabilities allowing the authors to profit.
The transfer of files via SSH has been registered from IP 192[.]227[.]131[.]120, this is one of the nodes the actors use to distribute Docker images and files with “Frappo”.
“Frappo” transfers a Docker container which contains a set of scripts written in Bash for further deployment. It’s worth noting, after the installation process is complete, all logs and executed commands are erased. We were able to log some of the commands used during and after the installation to obtain additional insight:
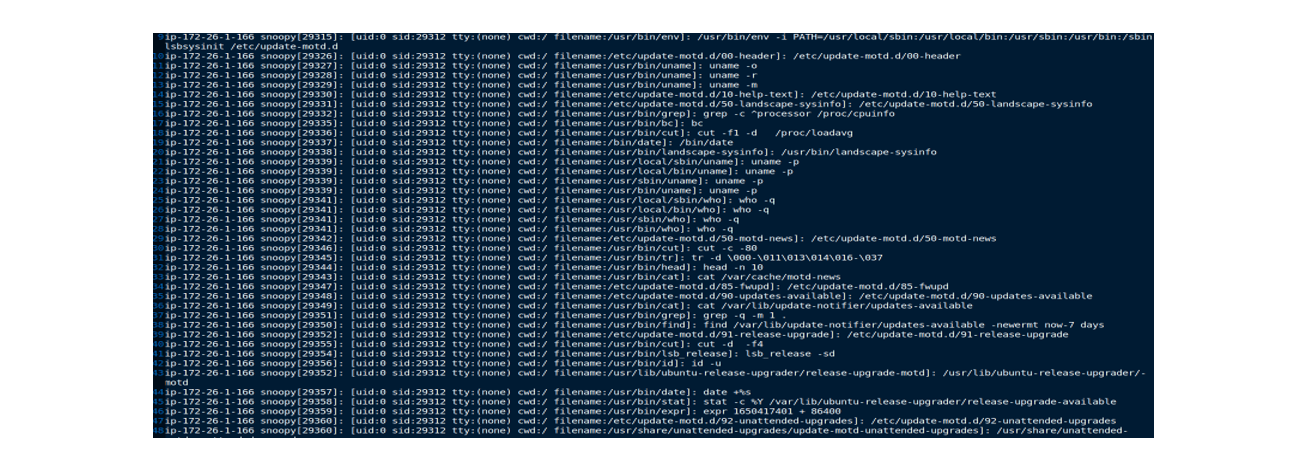
Some of the most noteworthy commands contained references to several archives “Frappo” downloads from the remote hosting which include – “webpage.zip” and “encryption.tar”.
rm -f -- .//alternatives.tar.6 .//alternatives.tar.6.gz rm -f -- .//dpkg.statoverride.6 .//dpkg.statoverride.6.gz rm -f -- .//dpkg.diversions.6 .//dpkg.diversions.6.gz rm -f -- .//dpkg.status.6 .//dpkg.status.6.gz find /var/crash/. ! -name . -prune -type d -regextype posix-extended -regex .*/[0-9]{12}$ ( -mtime +7 ) -exec rm -Rf -- {} ; find /var/crash/. ! -name . -prune -type f ( ( -size 0 -a ! -name *.upload* -a ! -name *.drkonqi* ) -o -mtime +7 ) -exec rm -f -- {} ; xargs -r -0 rm -f rm -f -- .//apt.extended_states.6 .//apt.extended_states.6.gz rm -rf /etc/caddy/Caddyfile.dpkg-dist rm -rf /root/webpage.zip rm -rf /root/encryption.tar rm -rf /usr/share/caddy rm -f /tmp/ipp rm -rf /tmp/os-prober.gu4DFd rm -rf /tmp/os-prober.r0gY15 rm -f /var/lib/os-prober/labels rm -f /boot/grub/grub.cfg.new rm -f /tmp/apt-fast.lock rm -f -- /tmp/apt-fast.list rm -f /var/lib/update-notifier/tmp.CrECFEsHye rm -rf /tmp/apt-key-gpghome.SvmsPAgdtl |
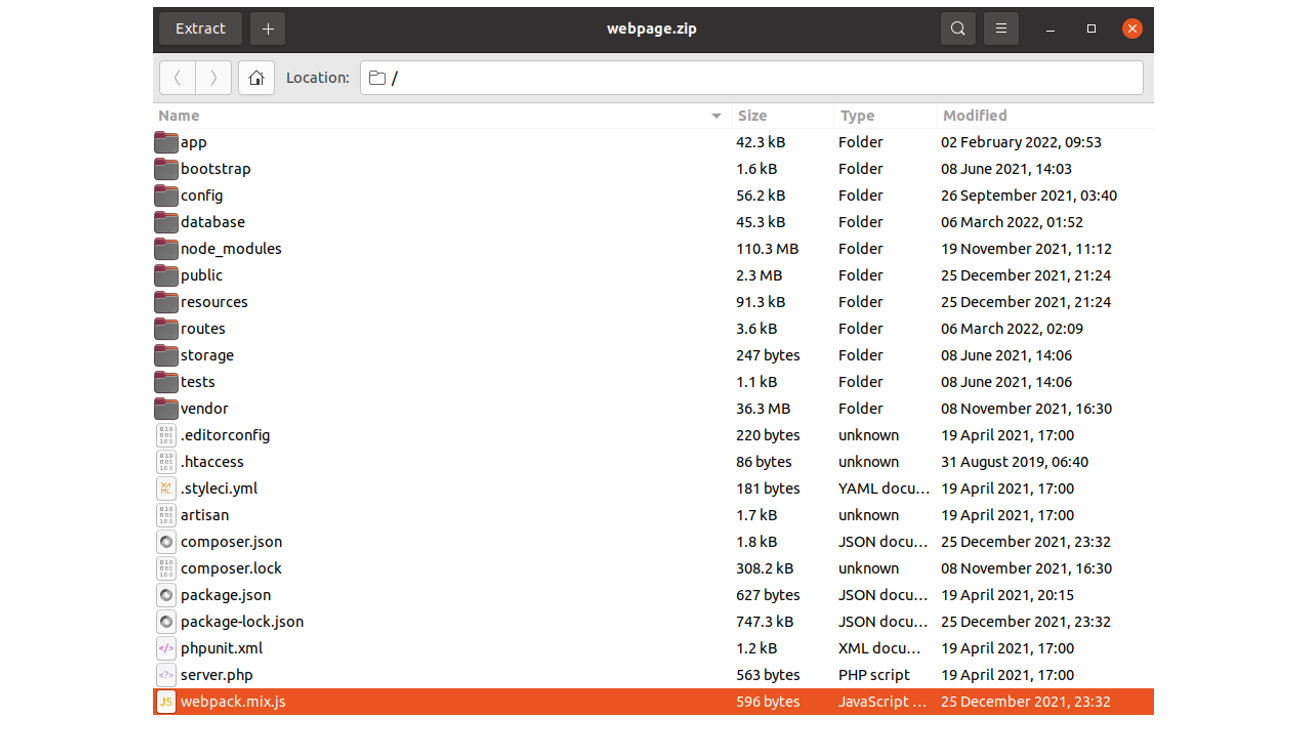
Here we can see the archive “webpage.zip” which contains a set of scripts:
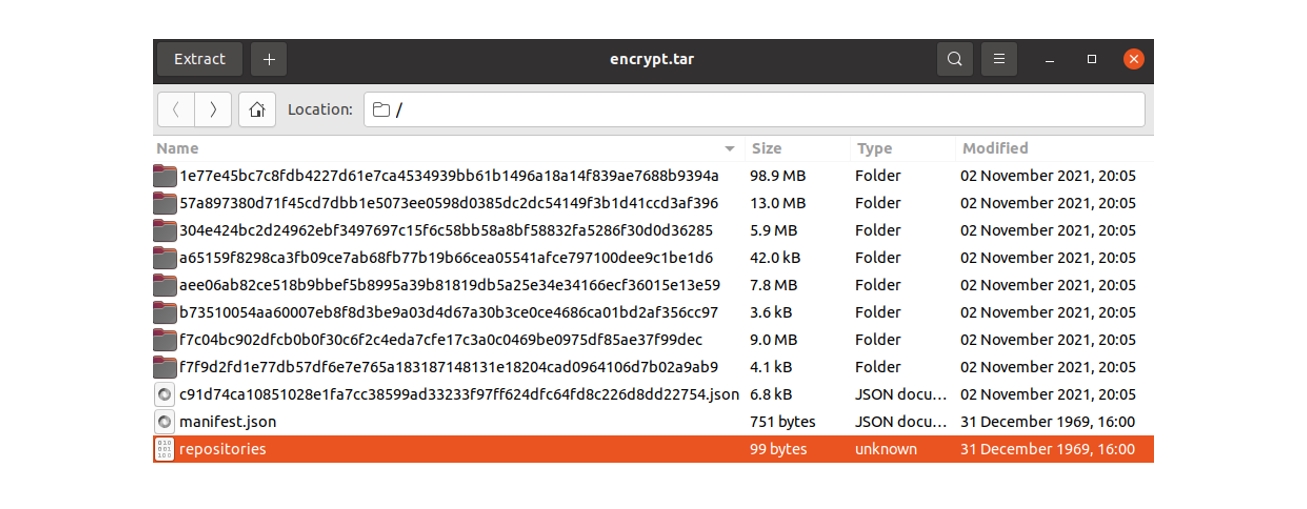
And here we can see the archive “encrypted.tar” which contains Docker and other configuration files:
[{"Config":"c91d74ca10851028e1fa7cc38599ad33233f97ff624dfc64fd8c226d8dd22754.json","RepoTags":["frappo/encryption:1.0.1"],"Layers":["304e424bc2d24962ebf3497697c15f6c58bb58a8bf58832fa5286f30d0d36285/layer.tar","1e77e45bc7c8fdb4227d61e7ca4534939bb61b1496a18a14f839ae7688b9394a/layer.tar","aee06ab82ce518b9bbef5b8995a39b81819db5a25e34e34166ecf36015e13e59/layer.tar","f7f9d2fd1e77db57df6e7e765a183187148131e18204cad0964106d7b02a9ab9/layer.tar","b73510054aa60007eb8f8d3be9a03d4d67a30b3ce0ce4686ca01bd2af356cc97/layer.tar","a65159f8298ca3fb09ce7ab68fb77b19b66cea05541afce797100dee9c1be1d6/layer.tar","57a897380d71f45cd7dbb1e5073ee0598d0385dc2dc54149f3b1d41ccd3af396/layer.tar","f7c04bc902dfcb0b0f30c6f2c4eda7cfe17c3a0c0469be0975df85ae37f99dec/layer.tar"]}] |
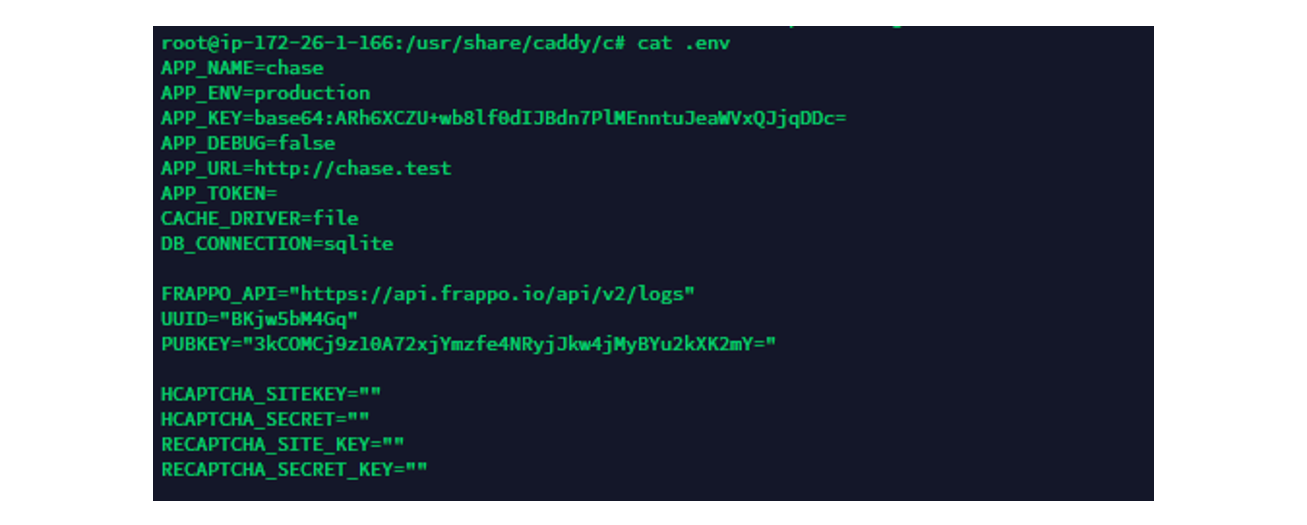
We also identified a “.env” file which contained key settings and public keys to encrypt logs which will then later be delivered to “Frappo” via API:
The observed phishing pages (or “phishlets”) are high-quality and contain interactive scenarios which trick the victims into entering authorization credentials.
Phishing-as-a-Service like “Frappo” are successfully used by threat actors for things like Account Takeover (ATO), Business Email Compromise (BEC), Payment and Identity Data Theft.
Cybercriminals are forever leveraging advanced tools and tactics to attack consumers globally. The protection of digital identity becomes one of the top key priorities for online-safety, and a subsequently becomes a new digital battlefield – wherein threat actors are hunting on stolen data.
Resecurity® is committed to protecting consumers and enterprises all over the globe, and is actively involved in public-private partnerships to share actionable cyber threat intelligence (CTI) with financial institutions, technology companies and law enforcement to ultimately minimize the risk of credentials being compromised and data breaches being executed. Resecurity® is an Affiliate Member of FS-ISAC and an Official Member of Infragard who aim to combat cybercriminal activity targeting financial services and Internet users.

