The Next-Generation Platform
for Enterprise Endpoint Protection
A revolution in cybersecurity for Enterprises of all sizes.
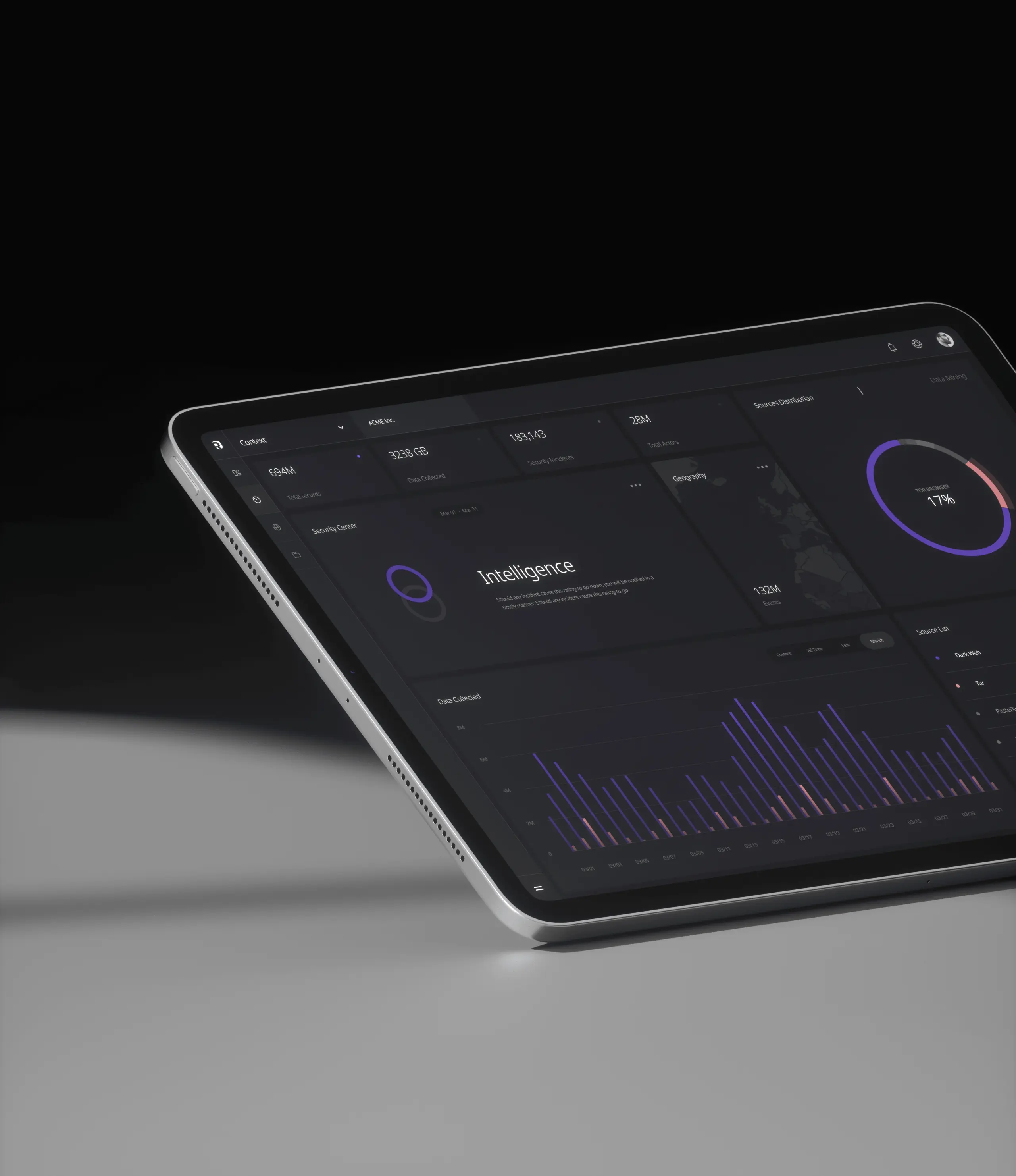
Consumers Protected by Resecurity
Digital Risk Indicators Analyzed
Enterprise Assets Under Protection 24/7
Geographical Locations
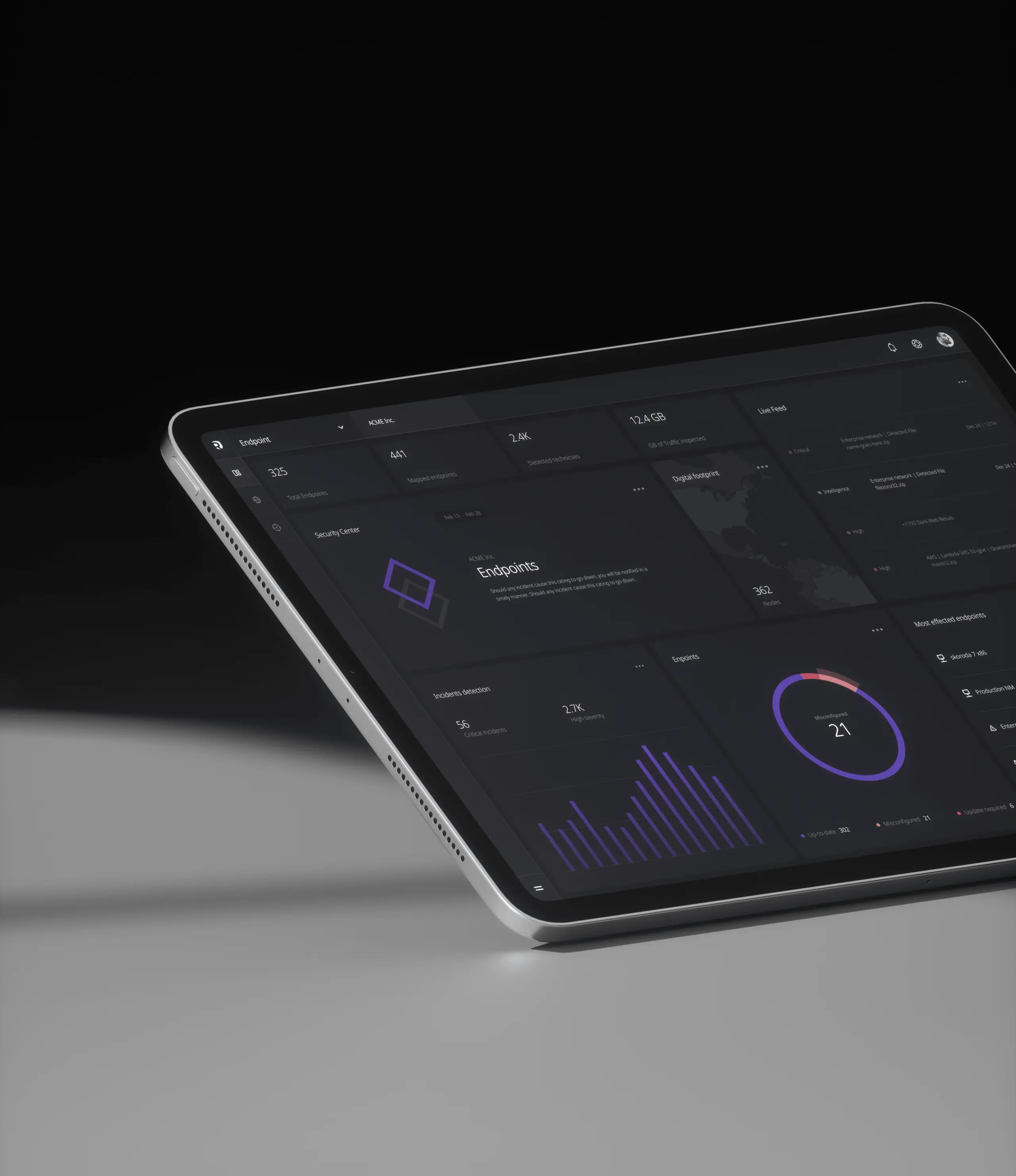
Lightweight and intelligent, instantly blocks attacks and records endpoint activity by leveraging rich APIs.
Accelerate response to threats by using smart-mesh technologies to identify, block and mitigate threats.
Zero impact on endpoint, end-user performance and productivity.
Seamless integration with existing workflows including DevOps and architects.
Streamline cybersecurity monitoring and response with comprehensive visibility, detection and analysis housed on one platform.


Without compromising speed, Resecurity defends your enterprise by utilizing our AI cloud-scaled architecture.
- Immediate time-to-value with no additional hardware or software.
- Simplified deployment reduces operational costs.
- Focused accuracy & uninterrupted speeds on cloud-scaled AI.
- Unparalleled resiliency & flexibility to meet your expectations.
Resecurity
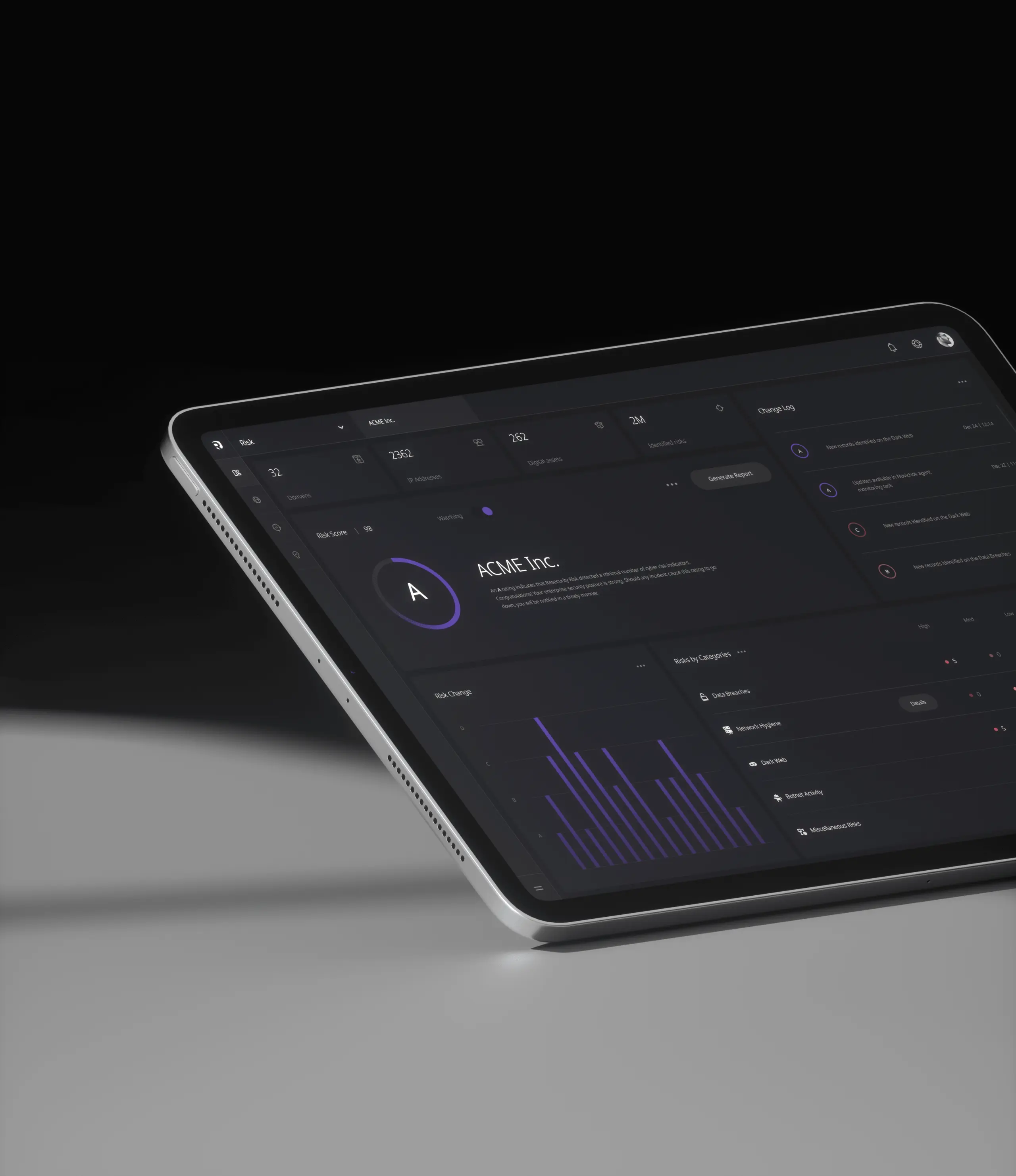
Our Threat Graph is the neural network behind our AI, it is the mesh that detects and mitigates threats.
- Continuous ingestion and real-time contextualization of analytics by cross-referencing trillions of events.
- Comprehensive endpoints and workload telemetry automatically updated instantaneously.
- Prediction, investigation and threat hunting within the Enterprise environment yields accelerated response and mitigation.
Enterprise Protection
Resecurity extends and reinforces the security perimeter covering all critical dimensions of modern enterprise.
- Assets
- Users
- Apps
- Network
- Services
- Devices
- IoTs
- Clouds
- Supply Chains
- 3rd Party Riskrd Party Risk
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps