Crypto-Influencer DeepFakes Are the Cybercriminal Economy’s Latest Business Line
Cybercrime Intelligence


Recent reports that Patrick Hillman, the chief communications officer at crypto exchange Binance, was impersonated in an attempted ‘deepfake’ attack is another reminder that this fraud is typology industry-agnostic.
Deep fakes are a type of digital forgery produced by generative adversarial networks (GANs), which are sophisticated implementations of machine learning technology. Introduced by Canadian researchers to the public in 2014, GANs typically imitate people’s faces, speech, and unique facial gestures.
However, deviant applications of deepfake technology began to surface in 2019. As the ensuing COVID-19 pandemic of 2020 caused a mass-remote labor diaspora especially, news reports about scammers using audio and video-based GANs to perpetrate successful business email compromise (BEC) attacks against organizations began to rise.
Specifically, scammers use GANs to credibly impersonate C-Suite executives in video chats or phone calls to issue fraudulent wire transfer instructions to their colleagues and personnel. This brings us to the recent deepfake attack that impersonated Binance’s comms executive.
The Binance Attack
In August, Hillman wrote a post on the Binance blog recounting his puzzlement after receiving various messages from blockchain entrepreneurs thanking him for taking the time to “meet with project teams regarding potential opportunities to list their assets” on the exchange.
While Binance, the largest crypto exchange in the world by assets and volume, would make a tantalizing target for threat actors, please note that vulnerable Web3 entrepreneurs duped by the Hillman GAN were the real marks in this attempted fraud.
The thank-you notes took Hillman by surprise because he never spoke to any of these teams, nor does he possess any decision-making authority in token listings, wrote the executive. Instead, Hillman discovered that a slick threat actor had compiled video clips of his previous news interviews and TV appearances to create a deepfake in his image.
“Other than the 15 pounds that I gained during COVID being noticeably absent, this deep fake was refined enough to fool several highly intelligent crypto community members,” wrote Hillman.
The Binance deep-fake attack is the second high-profile attack that has attracted mainstream media coverage, following the attempted BitVex trading platform scam that featured deep fakes of Elon Musk and other prominent cryptocurrency influencers.
Cybercrime Forum Chatter
In the wake of these attempted frauds, it seems the dark web community is catching on to the trend, as evidenced by recent chatter on the Exploit.in cybercriminal forum.
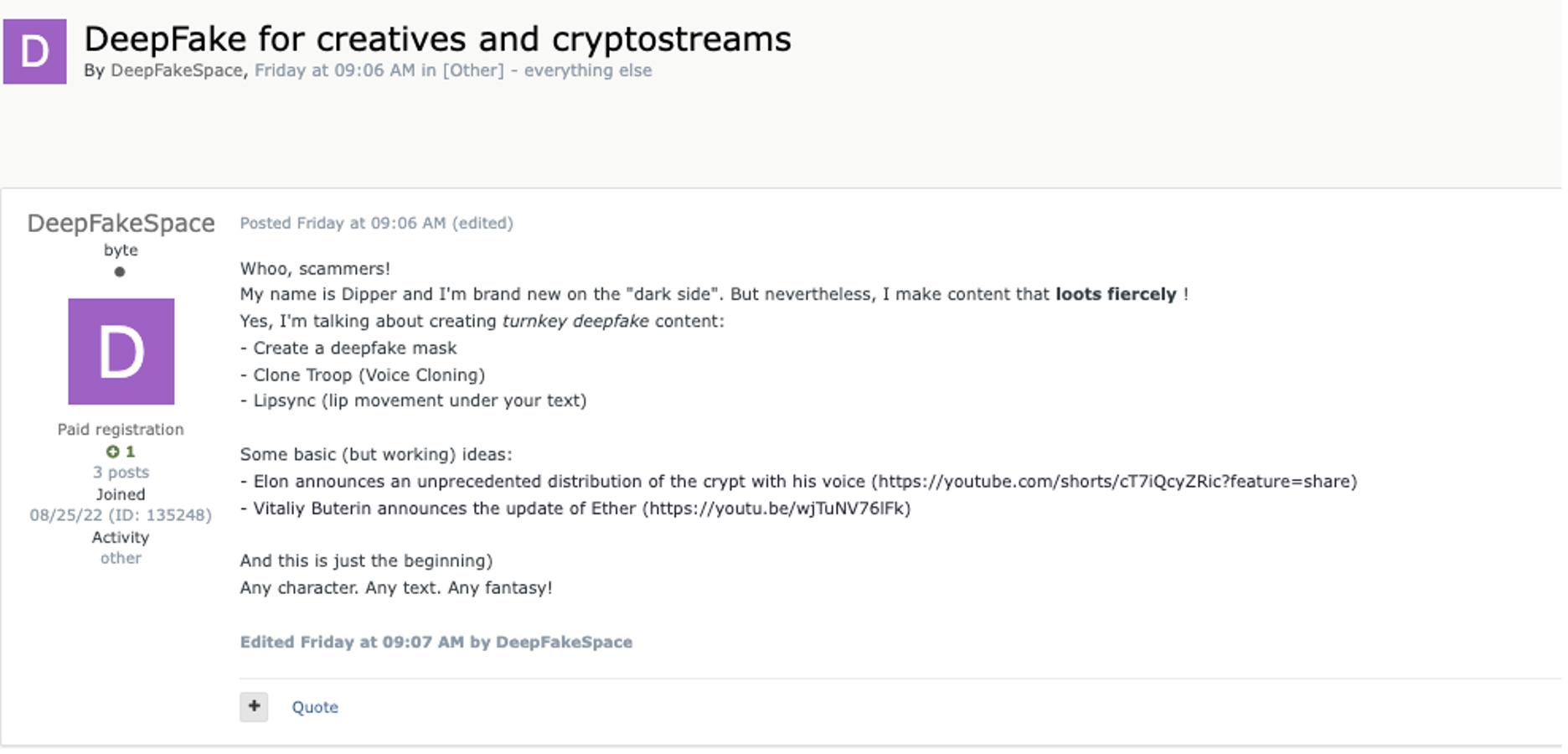
In August, Exploit user ‘DeepFakeSpace’, who claimed to be “brand new to the ‘dark side’,” solicited an eponymous turnkey service, including deep-fake masks, voice cloning, and lip syncing threat actor text. Samples of the user’s video forgeries provided in the Exploit posting include this skillfully rendered imitation of Elon Musk:

The poster also included a link to this passable deepfake of Ethereum founder Vitalik Buterin (note the ETH logo on his shirt), where he addresses the audience in Russian:

The Buterin video was posted on August 26, the same day the poster decided to turn to the “dark side” and solicit his services on Exploit. This page also provided a Telegram link to a channel operated by a deepfake artist, who uses the handle, ‘DeepSpace’. The logo below is the same as the watermarks on the above YouTube clips and the emoticons used by the YouTube poster.

The DeepSpace Telegram channel currently has 1,792 followers. The Telegram channel administrator also referenced their August 26 Exploit posting on the same day.
Some deep fake video creation services are appearing in the dark web, here is an example of a post found on a popular dark web forum advertising the new service from "RealDeepFake".
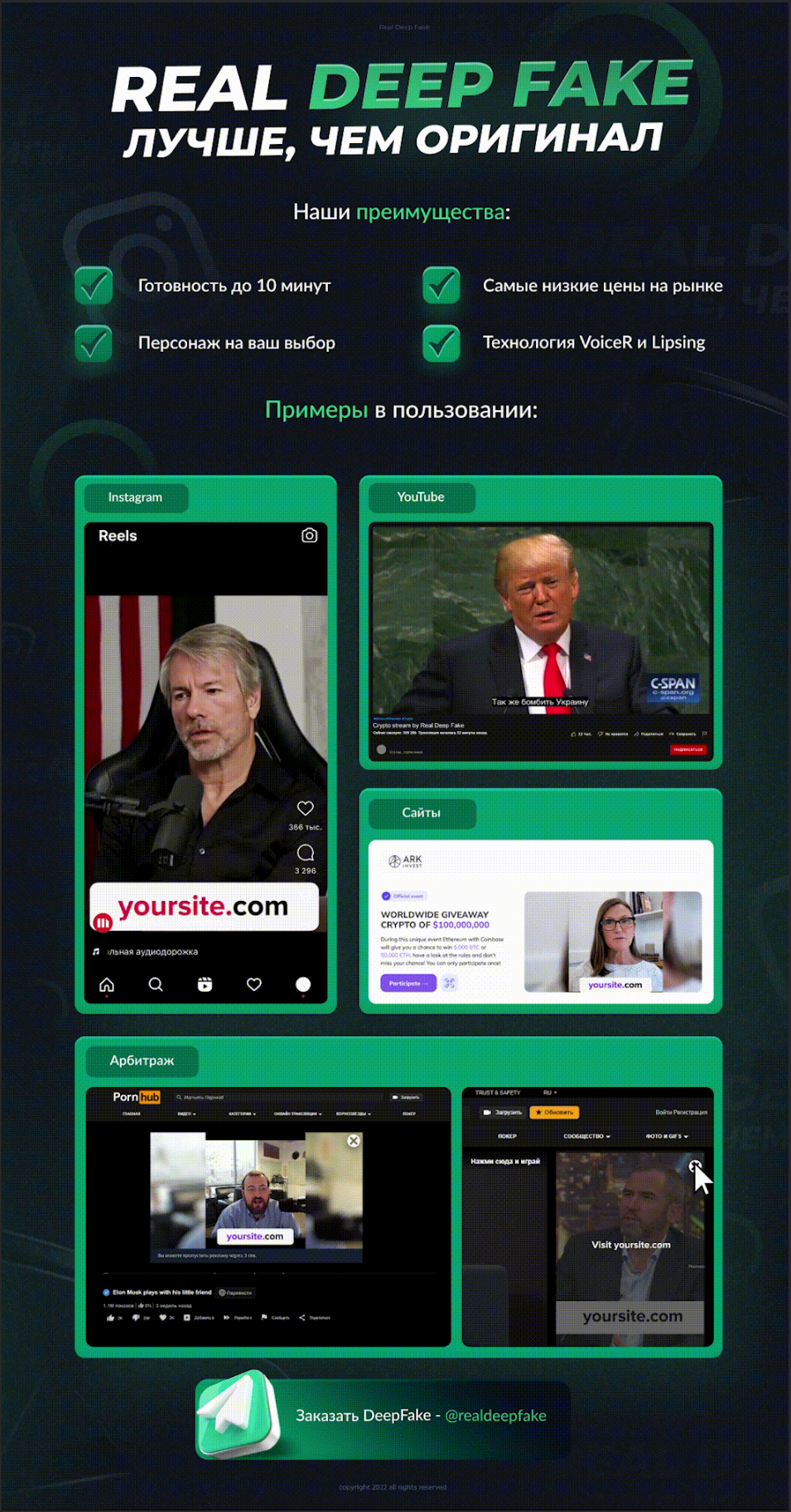
Below is an example video from RealDeepFake with Elon Musk as the character, this example was found in the Telegram group where you can purchase the RealDeepFake service.
Below is another example video, however this time staring Cristiano Ronaldo as the character, this example was also found in the same Telegram group.
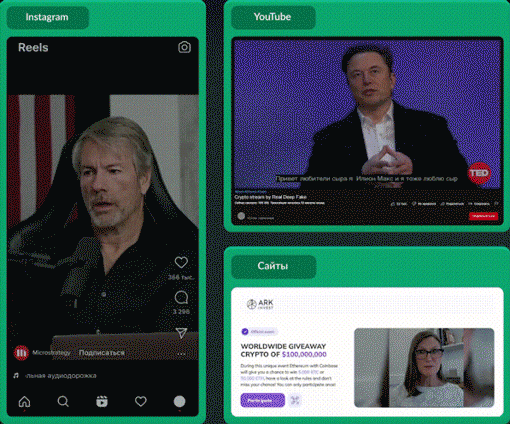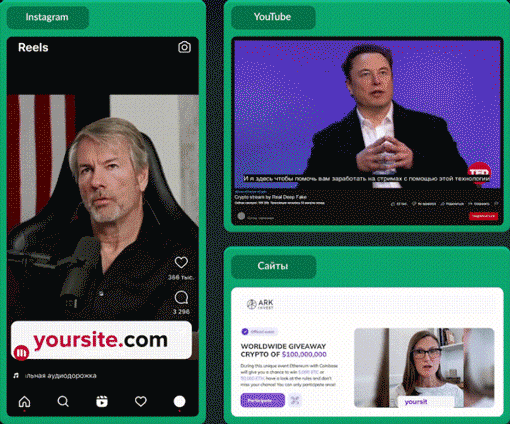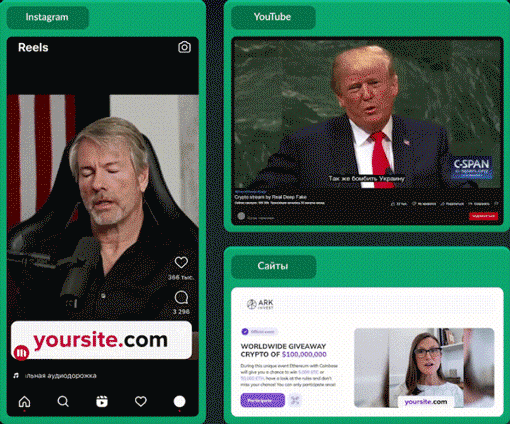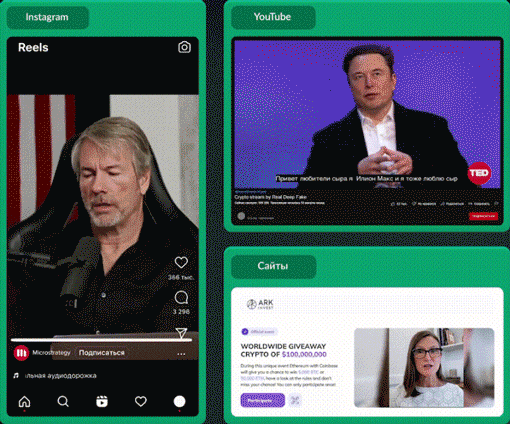
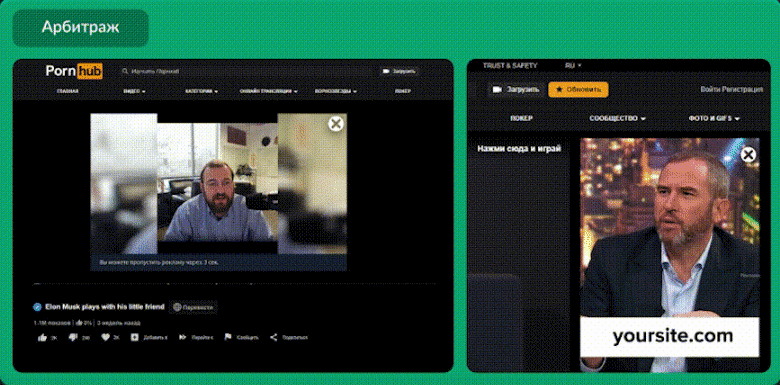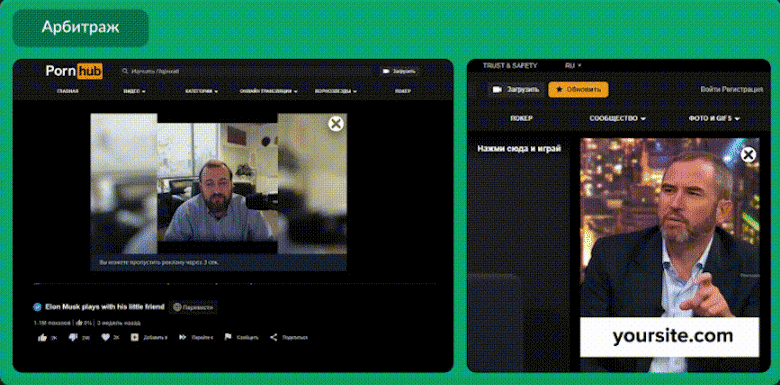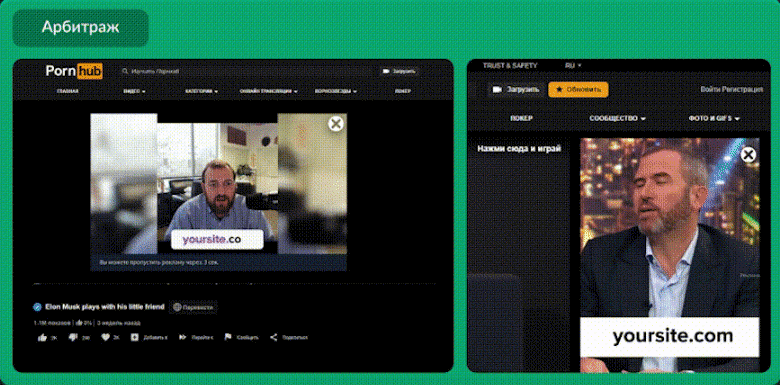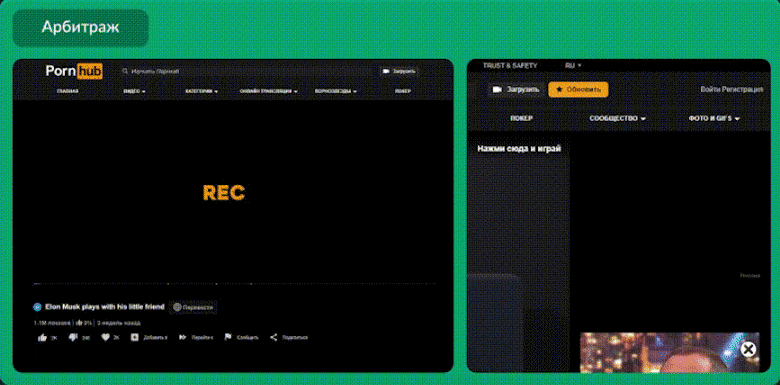
This is an example video that has been released in the Dark Web by actors providing the RealDeepFake service.
Significance
The accelerating rise of deepfake BEC and phishing frauds targeting the Web3 community comes amidst the backdrop of Federal Trade Commission reports that American consumers have lost over $1 billion in crypto as a result of scams since the start of 2021.
The June FTC report tracked losses through the end of this past March and found that roughly half of crypto-scam victims were targeted by fraudulent ads, postings, or messages on various social media platforms. The top platforms identified by the FTC were Instagram (32%), Facebook (26%), WhatsApp (9%), and Telegram (7%), according to the report.
Instagram is particularly relevant to the emerging threat of deepfake Web3 celebrity forgeries because it is a social media portal where crypto influencers have previously thrived. However, the steep crash in cryptocurrency markets has caused this group to lose significant ‘clout’ among would-be speculators.
Regardless, in the second quarter of this year, blockchain security firm CertiK observed 290 crypto-phishing attacks across different social media platforms, marking a 170% jump over the previous quarter. One noteworthy attack impacted the trendy Bored Apes Yacht Club (BAYC) NFT brand this past April.
An unidentified threat actor compromised BAYC’s official Instagram and Discord accounts to disseminate a malicious smart contract to their online followers. The link impersonated a ‘mint’ for an upcoming Yuga Labs (BAYC’s development studio) NFT land sale. Unfortunately, the scam contract was designed to withdraw NFTs for victim’s wallets and ultimately netted the theft of roughly $3 million in BAYC tokens from unwitting users.
Another notable phishing attack resulted in the theft of $1.7 million from 17 users of the leading NFT market place, OpenSea, last February. Attackers managed to obtain contact information for OpenSea registrants to distribute a malicious phishing link and steal NFTs from an undisclosed number of victims.
When the marketplace updated its smart contract, the threat actor copied the email blast and resent the announcement to its list of OpenSea users, while directing them to a link for their counterfeit NFT website. Additional victims were defrauded in this follow-on attack.
The reason these phishing attacks are relevant to emerging deepfake influencer and BEC threats is that cybercriminals targeting the Web3 community will likely crosspollinate fraud typologies in the future. As cybersecurity standards evolve throughout the cryptocurrency industry, so too will threat actors upgrade their tradecraft to deceive their victims.
Now summer has ended, and crypto markets move into the third quarter Resecurity expects to see more hybrid attacks that combine convincing email and social media blasts, fraudulent mints, and expertly rendered deepfakes of high-profile Web3 influencers to deceive both everyday consumers and crypto professionals alike.
To wit, tutorials for creating fake crypto mints are also being mass-marketed on the Exploit forum by user ‘WebCrypt’. All users need to properly execute a scam like this are a “minimal understanding of programming, a drop of cunning and imagination, some resources, and $20 per host and domain.”
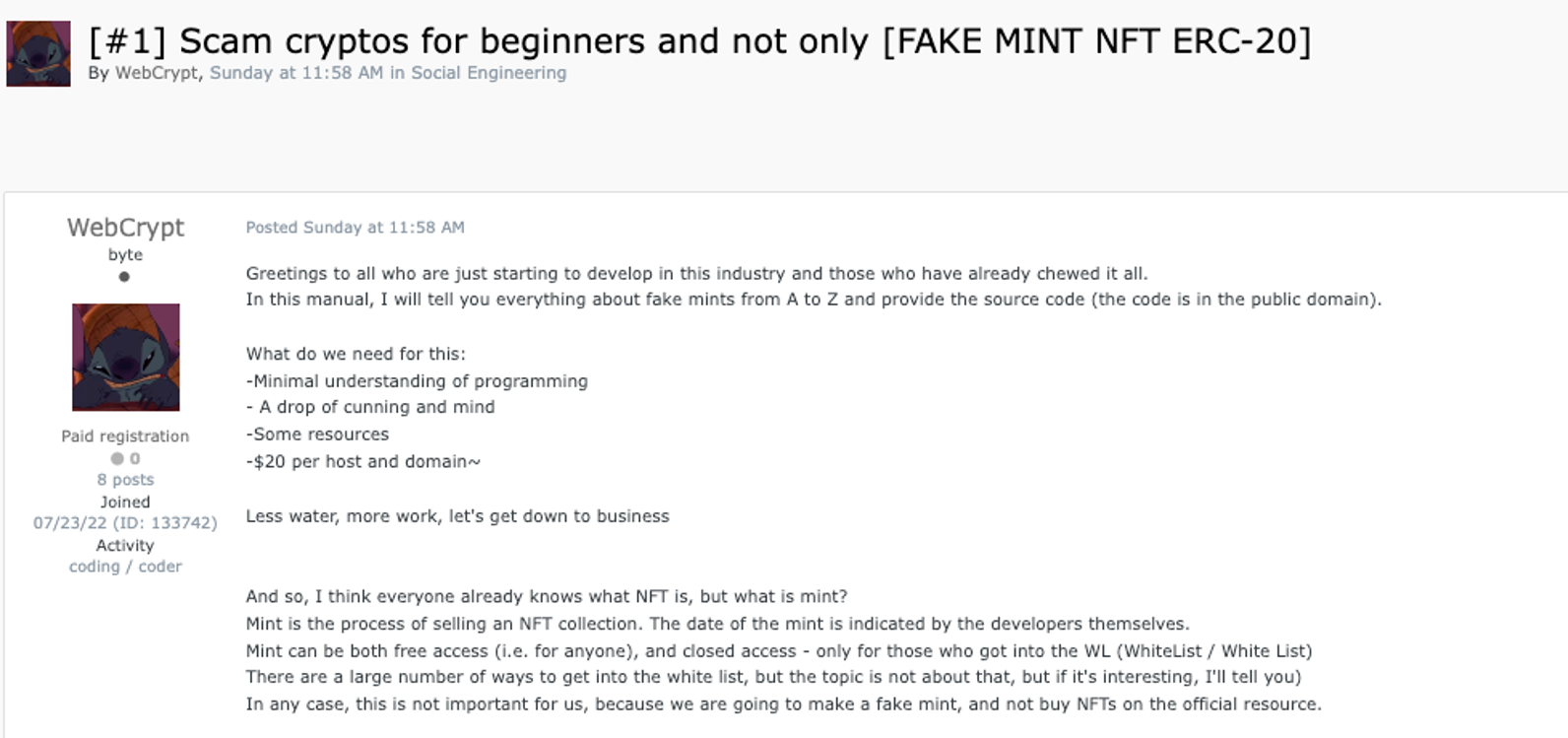
But just imagine how much more effective an attack like this could be conducted if performed in combination with a high-quality deepfake of a credible influencer.

