
During the month of Ramadan, Resecurity observed a significant increase in fraudulent activities and scams, coinciding with a surge in retail and online transactions. Middle Eastern enterprises, facing this heightened risk, are urged to bolster consumer protection and reinforce their brand security. Notably, in the Kingdom of Saudi Arabia (KSA), consumer spending topped regional charts, exceeding $16 billion. This spike in e-commerce activity has, unfortunately, drawn the attention of cybercriminals who exploit these platforms to execute scams, leading to substantial financial repercussions for both consumers and businesses. The estimated total financial impact of these activities ranges between $70 and $100 million, accounting for frauds perpetrated against expatriates, residents, and foreign visitors.
Cybercriminals are increasingly employing cunning methods to defraud individuals, using complex schemes that outsmart standard security protocols. This poses a significant challenge for financial institutions, which often struggle to identify and react to such scams promptly. The effectiveness of these scams is partly due to the victims inadvertently authorizing these fraudulent transactions, misled by the scammers' tactics. Resecurity emphasizes the importance of enhancing customer awareness about these deceptive practices. By improving customer knowledge and strengthening security verification methods, it's possible to counteract these fraudulent activities more effectively and swiftly.
The fraudulent tactics observed during this period align with the "Smishing Triad", a group previously identified by Resecurity. This approach has been used to target consumers in the U.S., U.K., various European Union countries, and the UAE. It now appears to be emerging as a new wave of cybercriminal activity focused on the Middle East. This pattern suggests a deliberate shift in the cybercriminals' focus to this region.
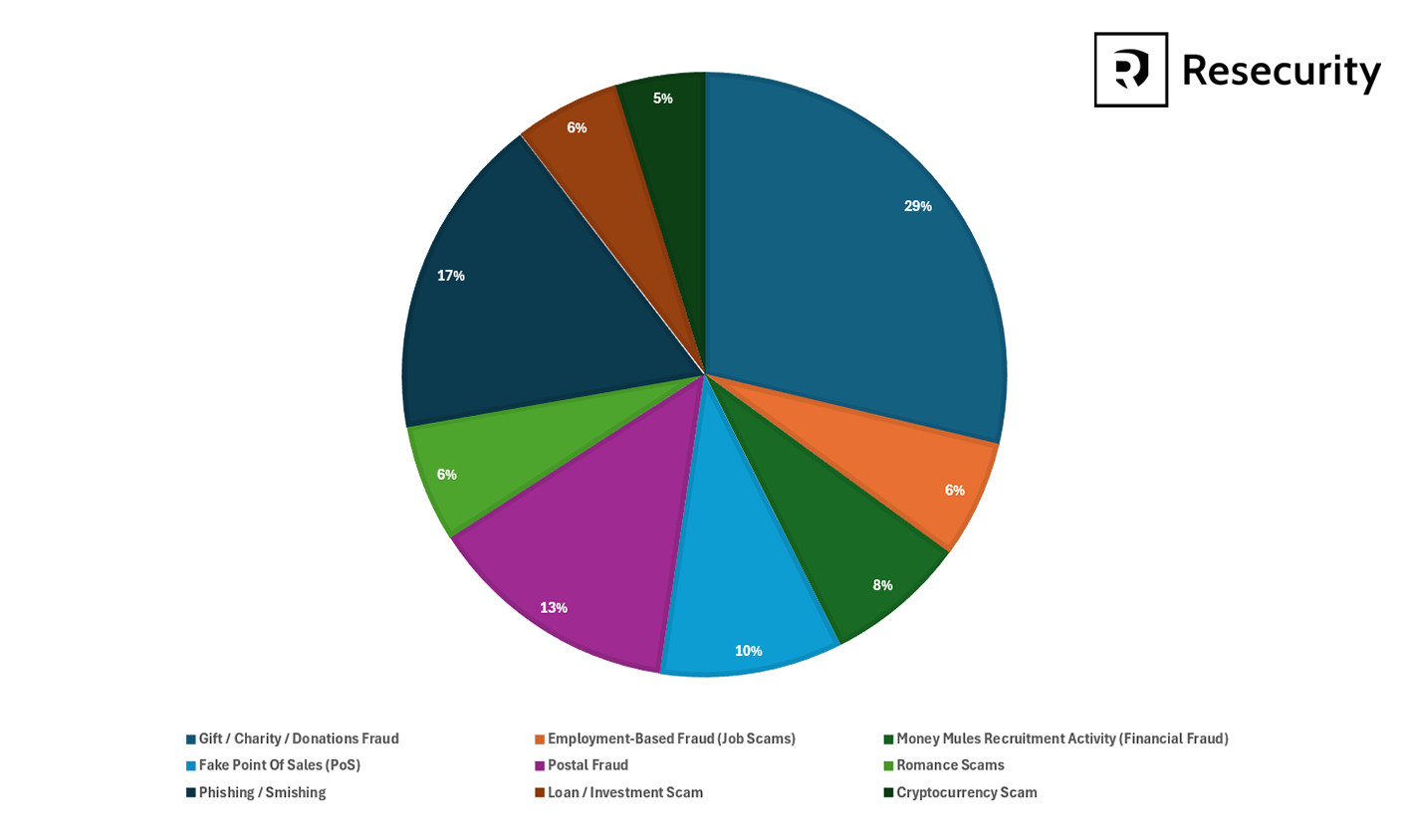
As the most emerging types of fraudulent activity observed in the region during this important time of the year, Resecurity may outline:
- gift/charity/donations fraud;
- employment-based fraud (job scams);
- money mules recruitment activity (financial fraud);
- fake point of sales (PoS) (for e.g., registered on platforms like Haraj);
- impersonation of logistics and postal providers (Aramex, SMS, Zajil, SPL);
- romance scams / blackmail;
- phishing/smishing activity;
- loan/investment fraud;
- cryptocurrency scams.
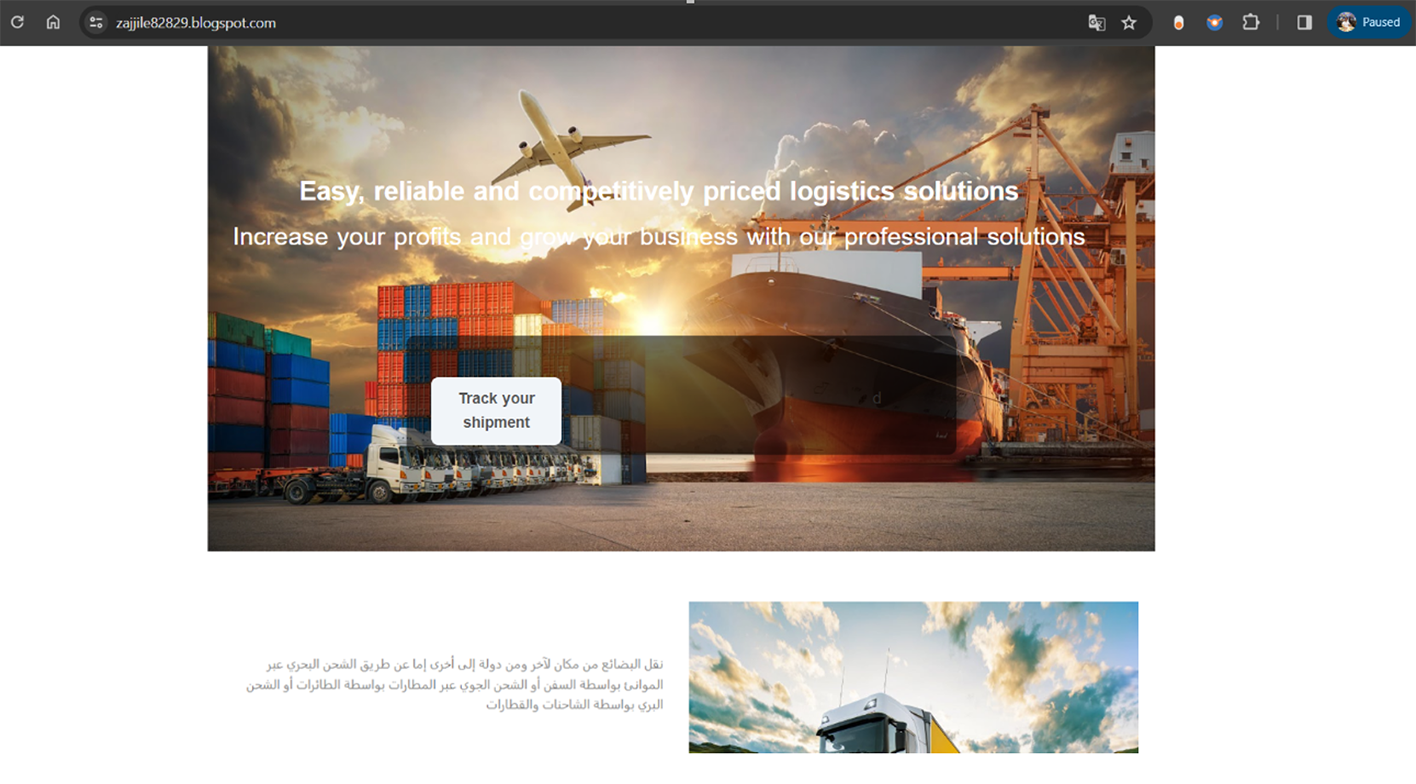
Logistics Providers - Impersonation of Aramex, SMSA and Zajil Express
Resecurity has noted a rising trend in scams involving bogus notifications from well-known shipping companies like Aramex, SMSA Express, and Zajil Express. These scams target many people through SMS or iMessage. The messages falsely claim that a parcel delivery is pending due to unpaid fees, urging the recipient to make an immediate payment. This method is designed to trick individuals into believing they owe money for a delivery, prompting a quick response.
In certain instances, these cybercriminals enhance their smishing (SMS phishing) scams by persuading victims to disclose their credit card or online banking details. Many have received these deceptive messages, which alarmingly include their actual addresses and references to known senders. This indicates that the bad actors have likely accessed this personal information through third-party data breaches. Furthermore, it's evident that such data is being traded extensively on the Dark Web and within illegal online communities, where cybercriminals profit from selling stolen information.
Example of fraudulent WEB-site impersonating Zajil Express:
Cybercriminals frequently use WhatsApp, a popular messaging IM app, as their main way to communicate with potential victims. This platform is chosen due to its widespread use and familiarity, making it an effective tool for their deceptive practices.
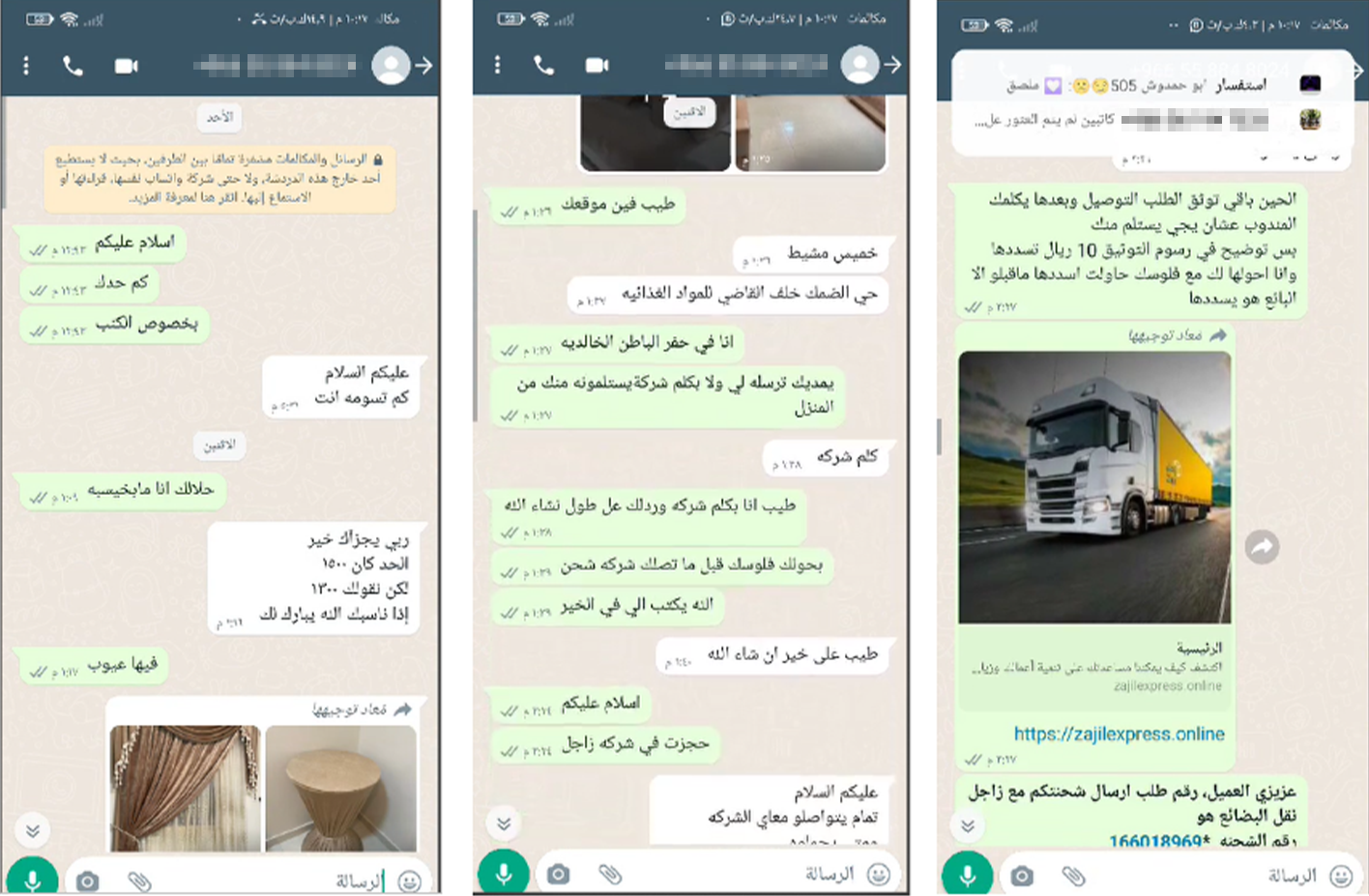
The victim gets a false notification claiming a parcel has been successfully delivered. This message asks for confirmation and requests personal information. It often includes details like full name, mobile number, address, and sometimes even more sensitive information, potentially exposing the victim to further risk.
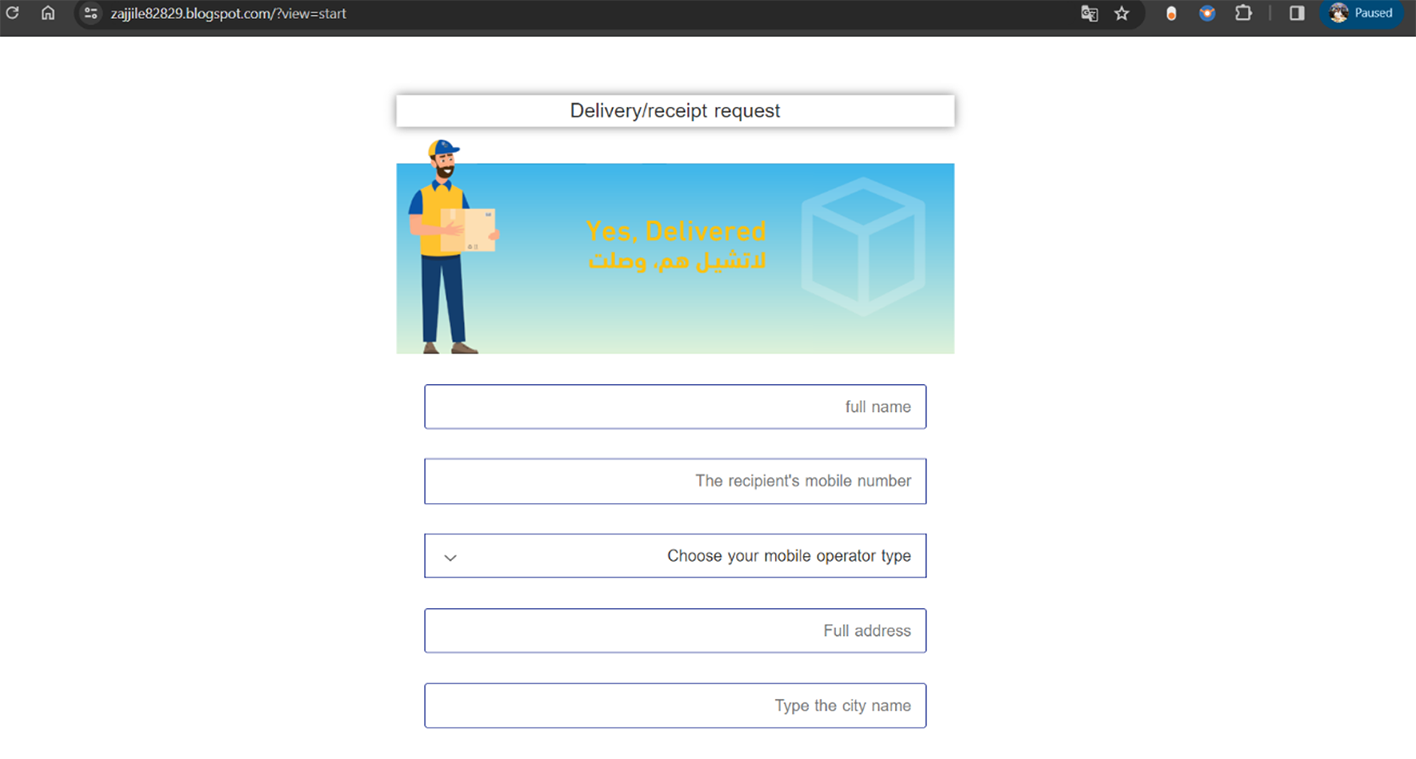
Example of fraudulent WEB-site impersonating SMSA Express:
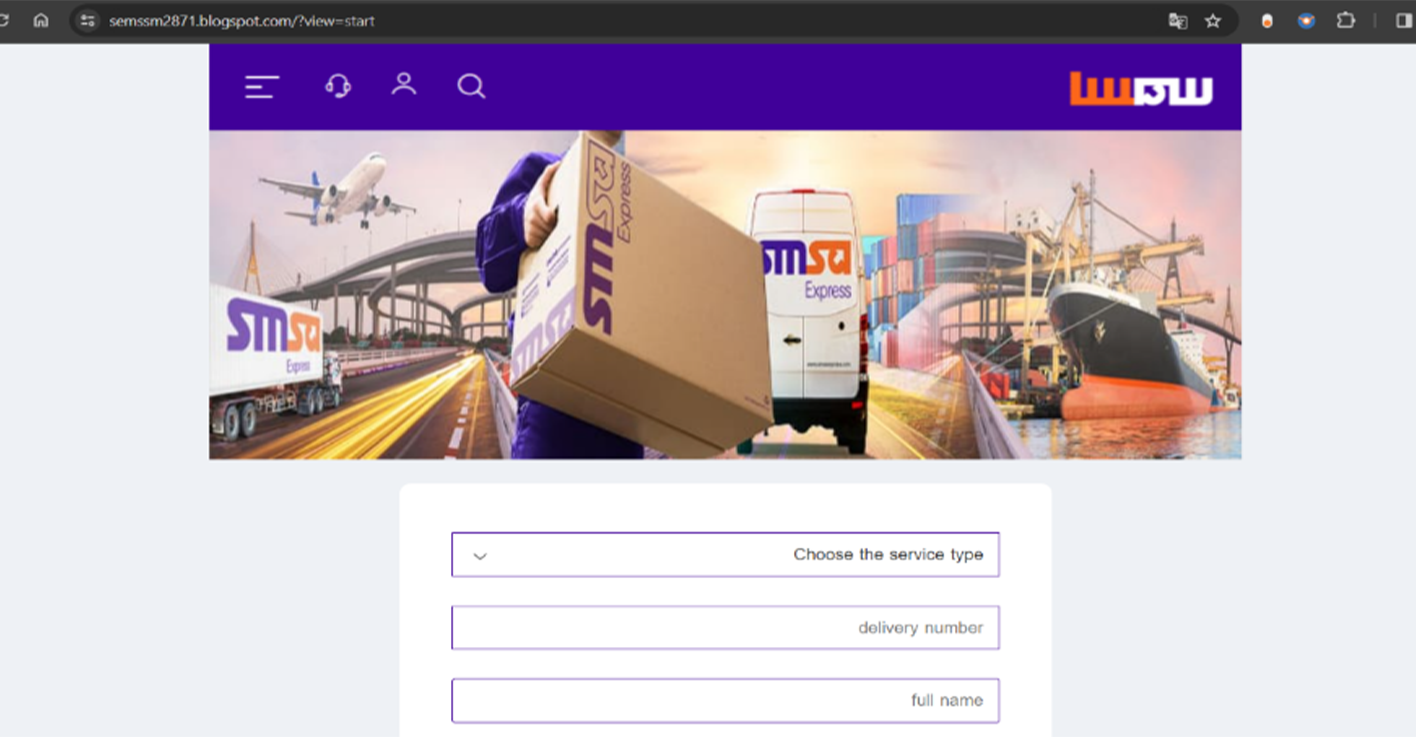
Example of fraudulent WEB-site impersonating Aramex:
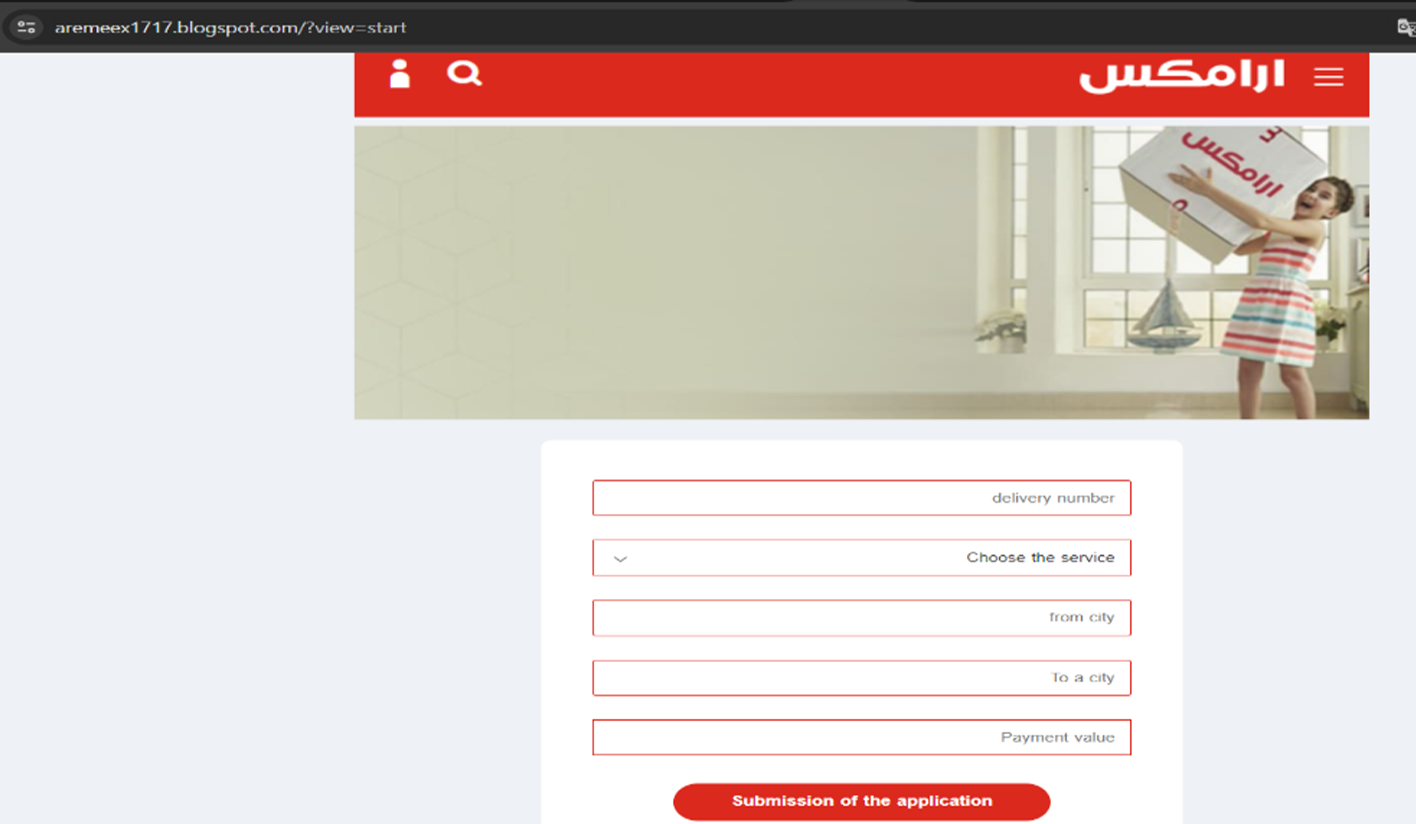
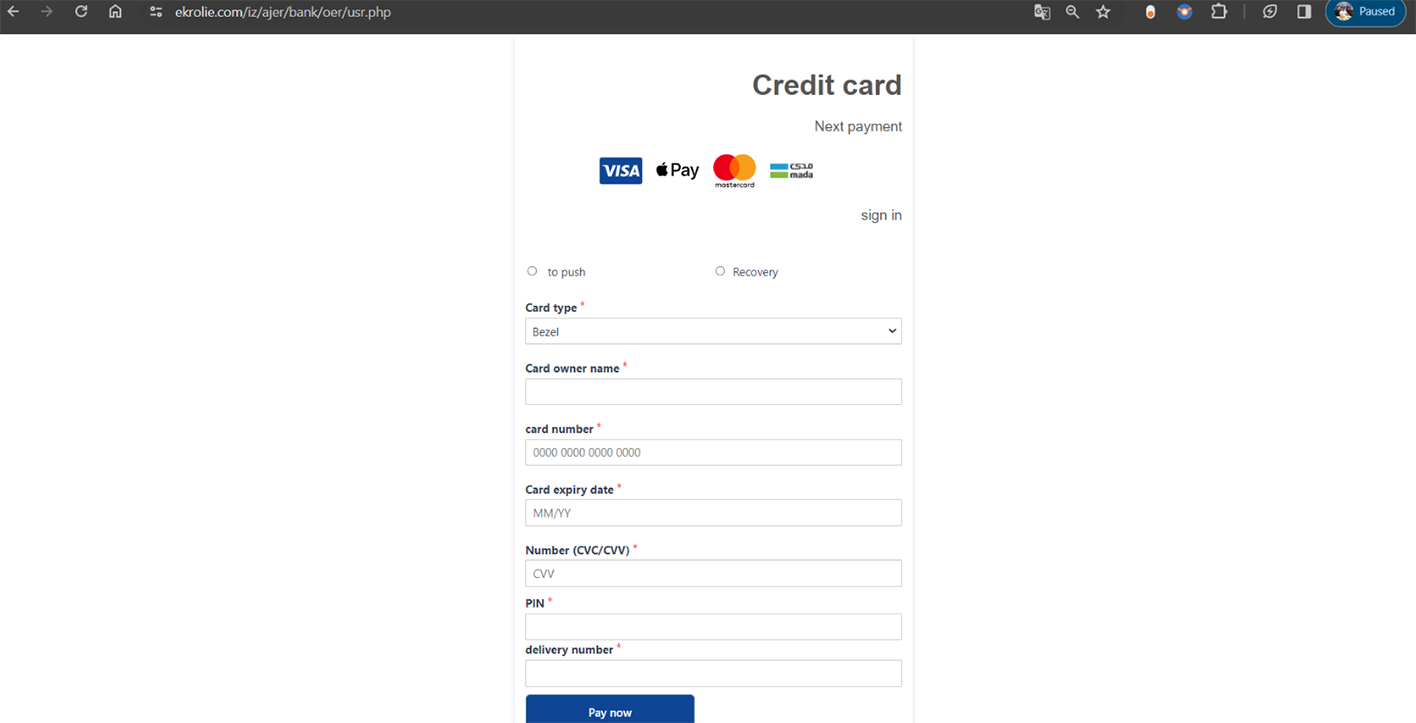
After the victim provides their personal details, the phishing scheme progresses to the next stage, where the victim is directed to make a payment. The scammers use the guise of unpaid fees that need to be cleared before the parcel can be delivered. The victim is then presented with a fraudulent payment form, which appears legitimate and offers various payment options, mimicking those used by well-known financial institutions in the KSA like SNB, Riyad Bank, Bank Aljazeera, SABB, and others. This step is designed to further deceive the victim into completing a transaction.

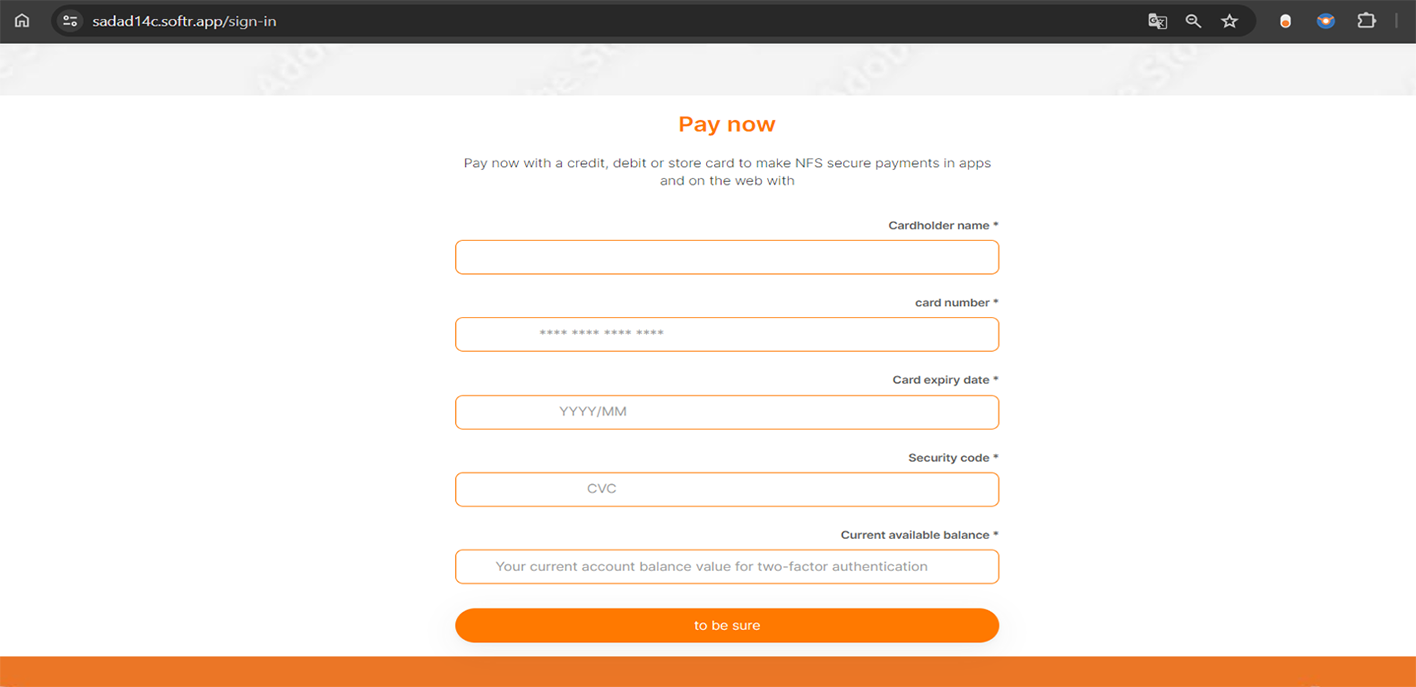
Cybercriminals skillfully replicate the payment forms of financial institutions, closely imitating their design and branding. This makes the forms look authentic to the victim, adding to the credibility.
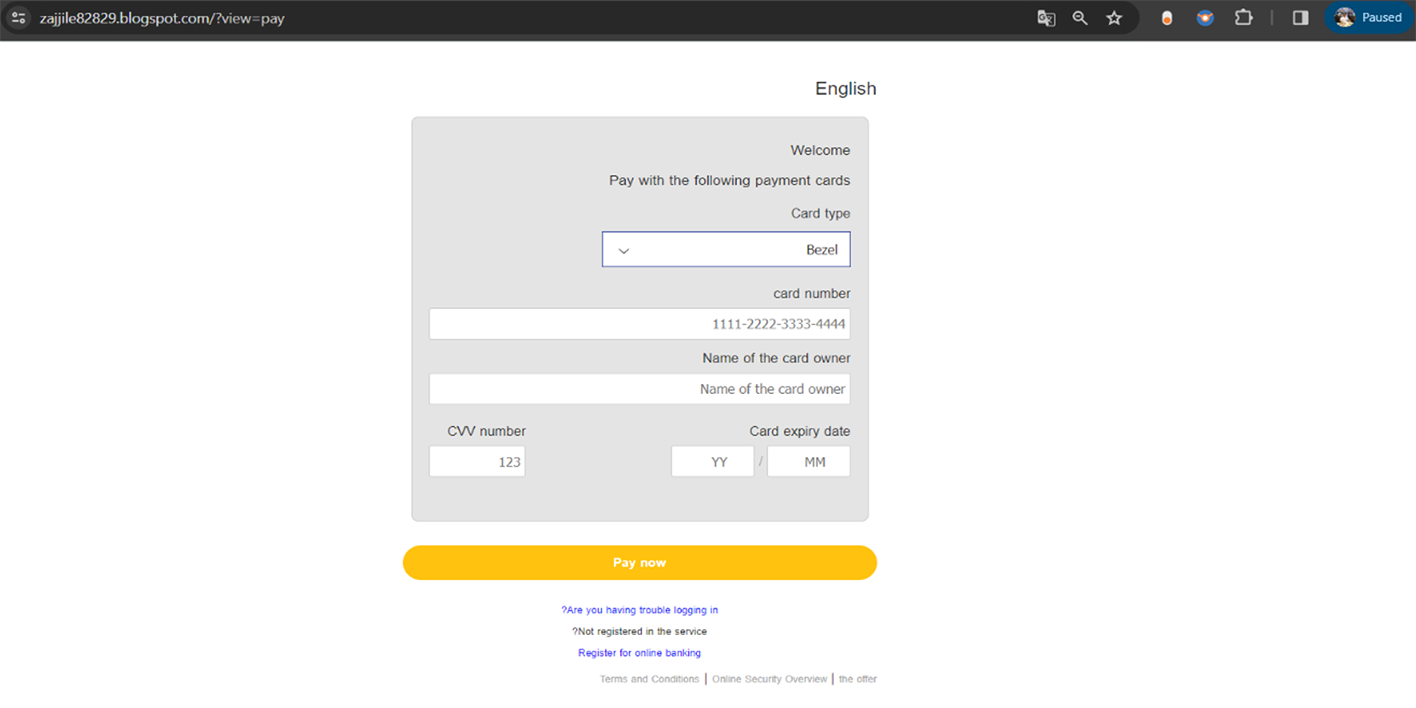
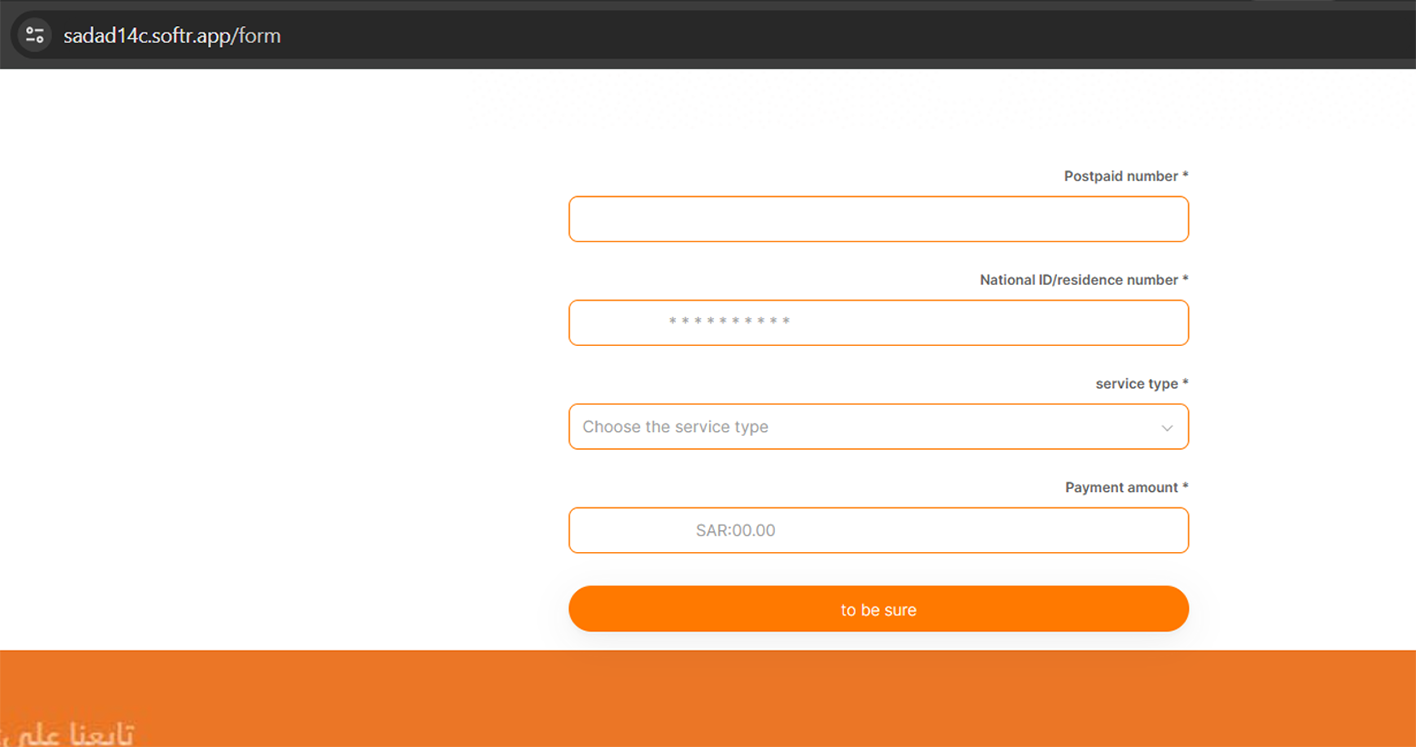
In addition to seeking cardholder information like the credit card number, CVV, and expiration date, cybercriminals also target victims' online banking account passwords. Gaining access to this range of information opens up multiple avenues for fraud, ranging from unauthorized credit card charges to more severe cases of online banking fraud and identity theft.
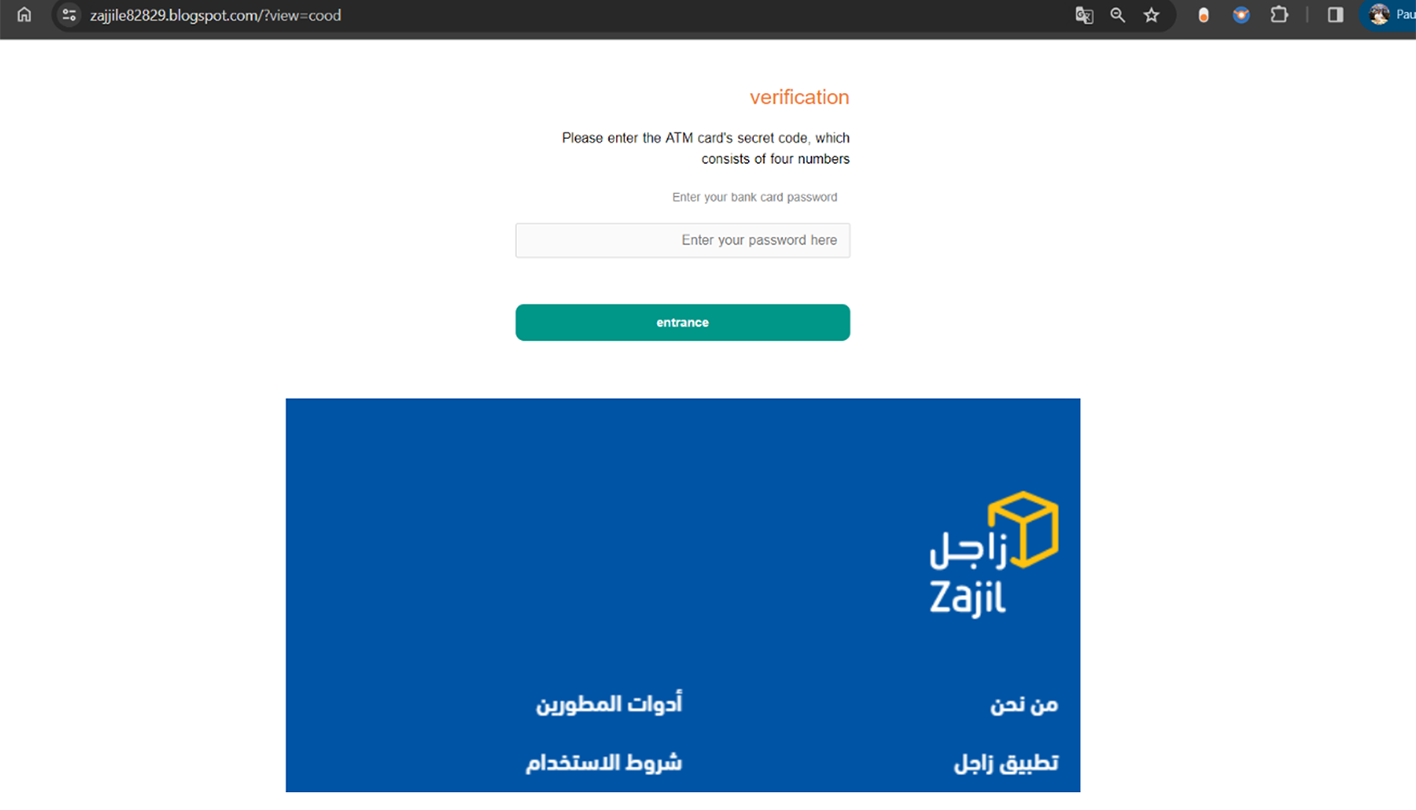
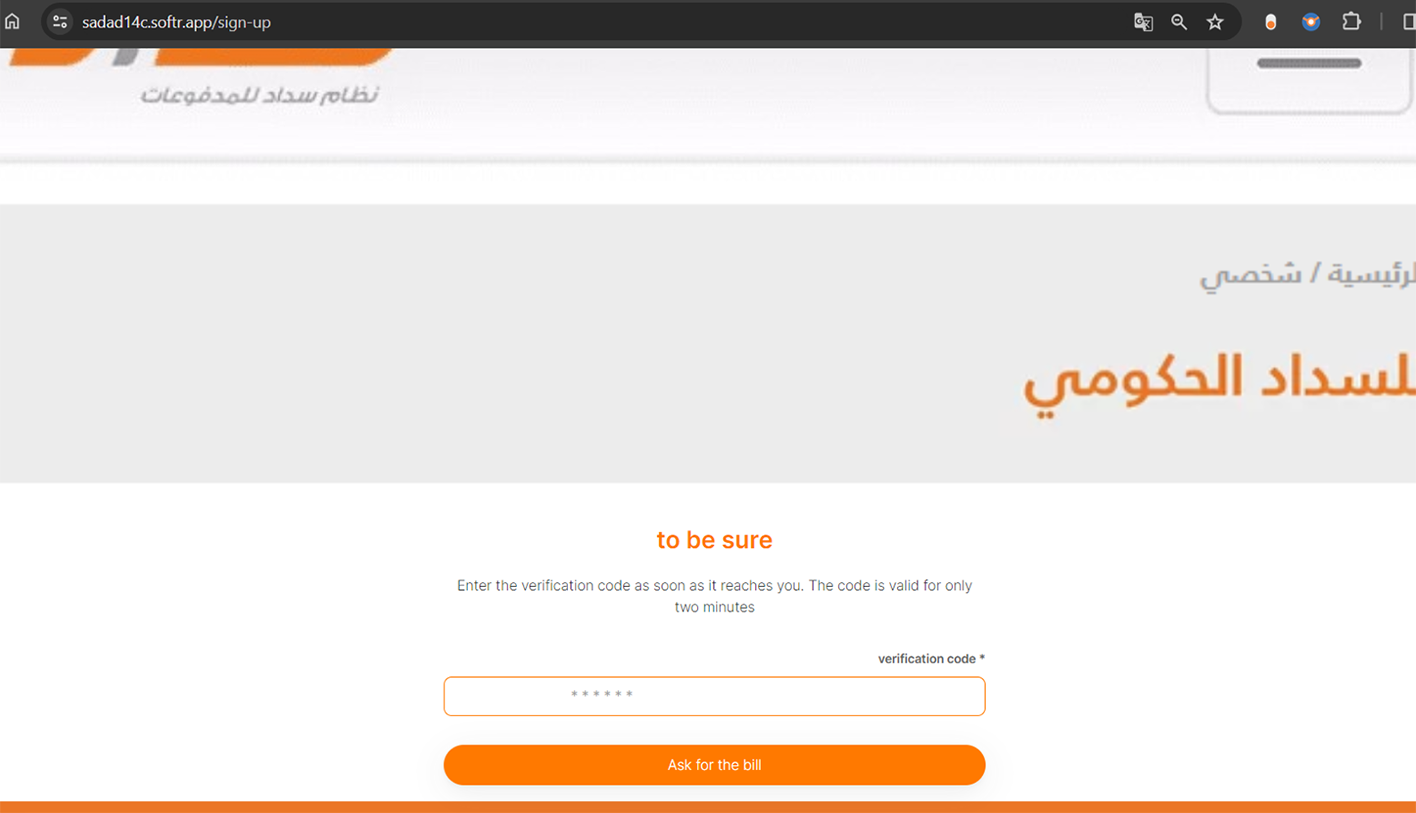
Interestingly, the phishing scheme goes a step further by prompting users to enter their login credentials for the SADAD platform. SADAD is a digital service primarily used for the payment of bills, zakat, taxes, and other financial transactions across various banking channels. This additional credential request indicates a deeper level of deception, targeting more than just credit card or banking details.
Abuse of SADAD and MUSANED Platforms
Resecurity has detected several fraudulent campaigns involving the SADAD and MUSANED platforms. Cybercriminals created fake WEB-resources hosted on the Softr platform.
- SADAD serves as a central system for online bill payments in the Kingdom of Saudi Arabia. SADAD facilitates bill payments for individuals, banks, companies, and the government sector.
Original website: https://www.sadad.com/
Phishing website: https://sadad14c.softr.app/
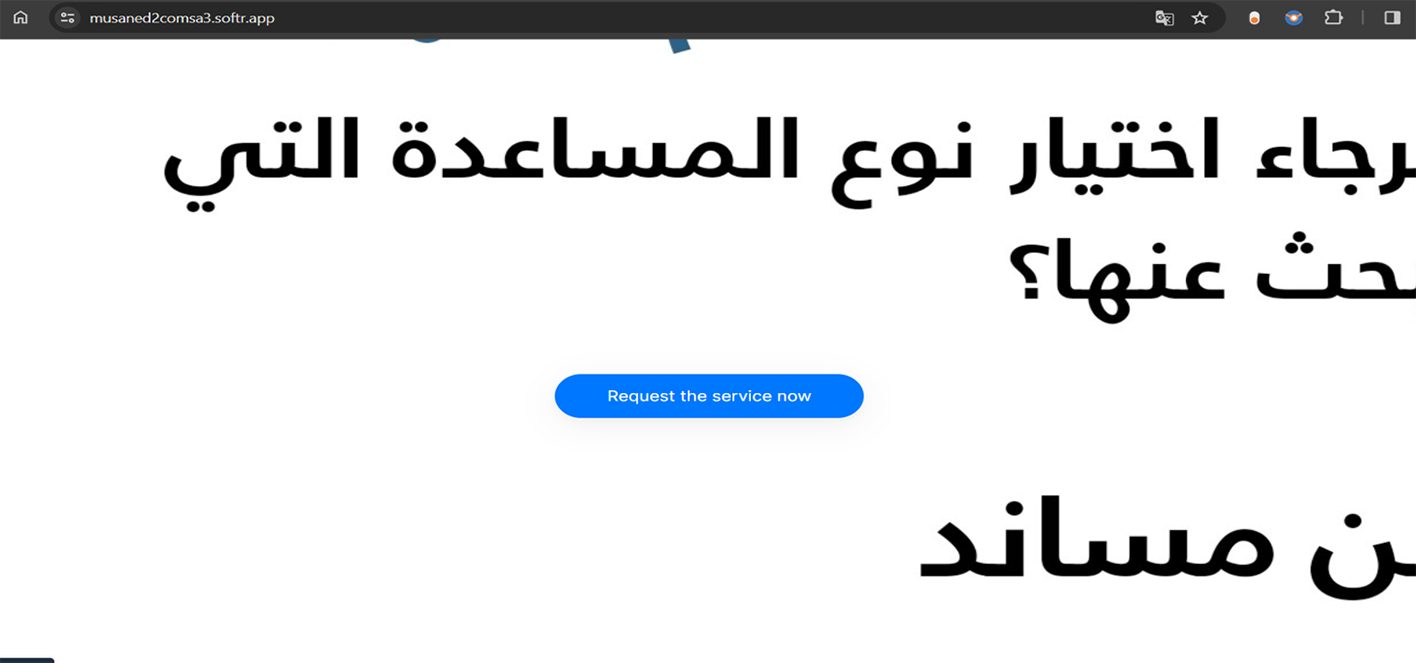
- Musaned is an electronic platform and a new integrated system that facilitates recruitment procedures in an unprecedented manner.
Original website: https://musaned.com.sa/home
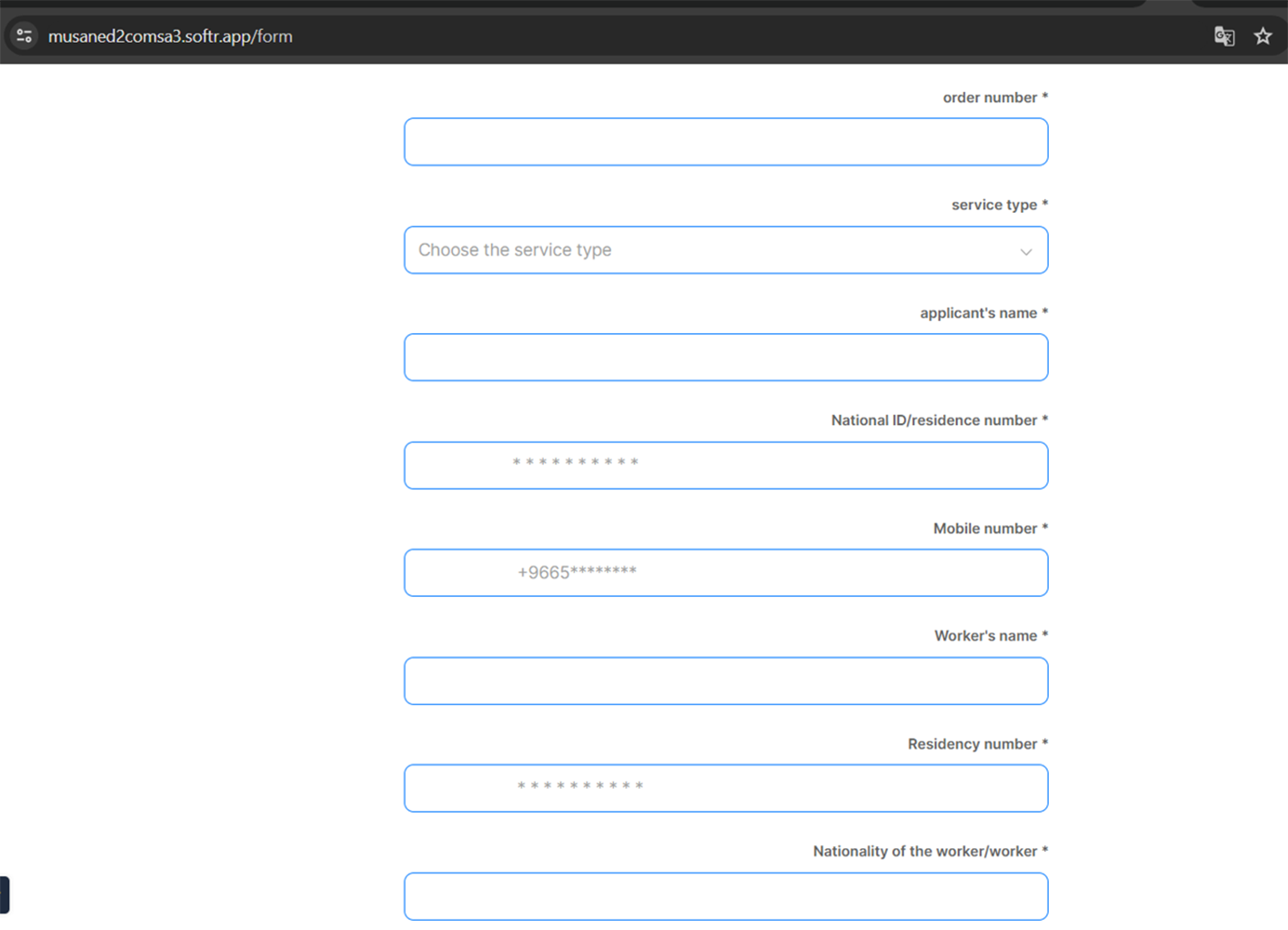
Phishing website: https://musaned2comsa3.softr.app/
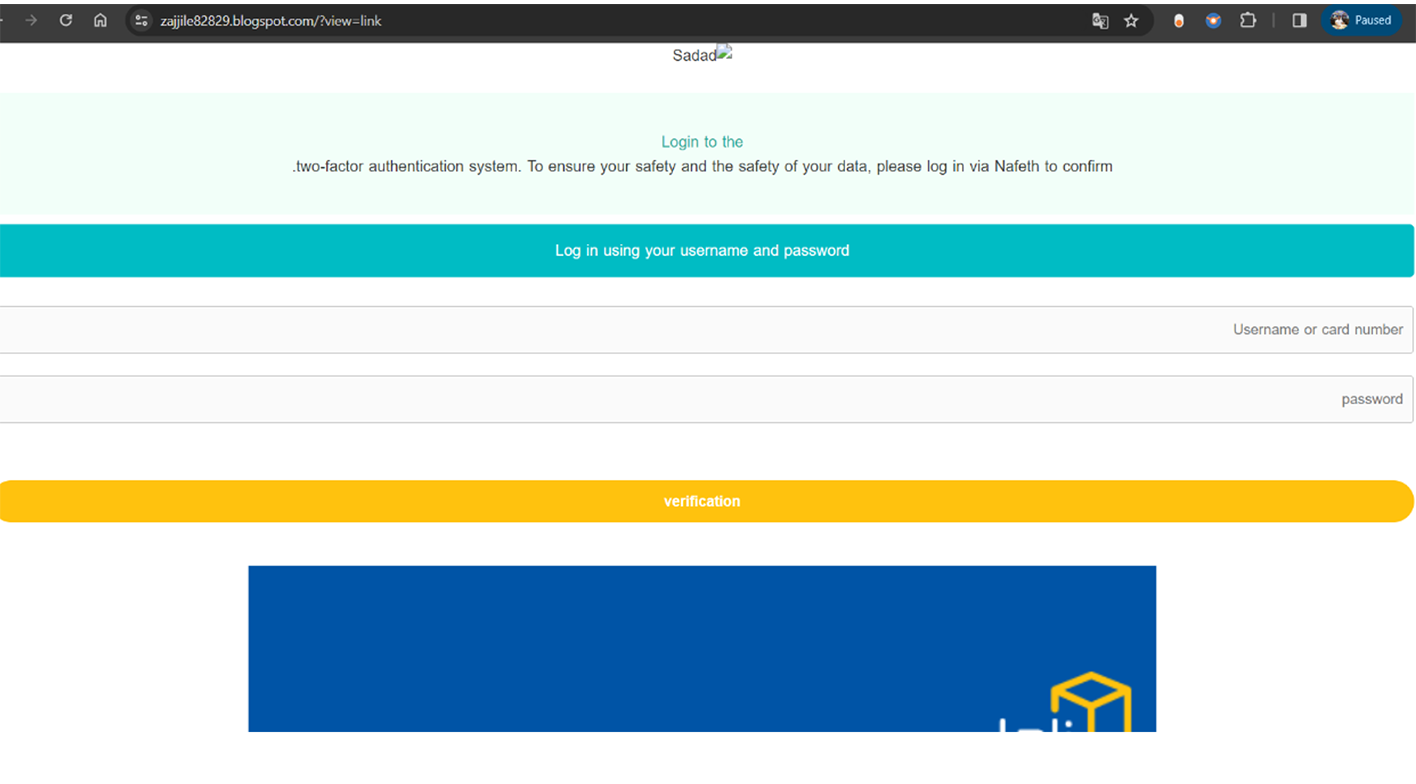
Cybercriminals utilize a multi-stage phishing kit designed to intercept two-factor authentication (2FA) or one-time passcode (OTP) codes. These codes are typically sent to the victim's phone or email when an attempt is made to access their account, adding an extra layer of security. However, with this sophisticated phishing approach, the criminals aim to capture these codes, thereby bypassing this security measure and gaining unauthorized access to the victim's accounts.
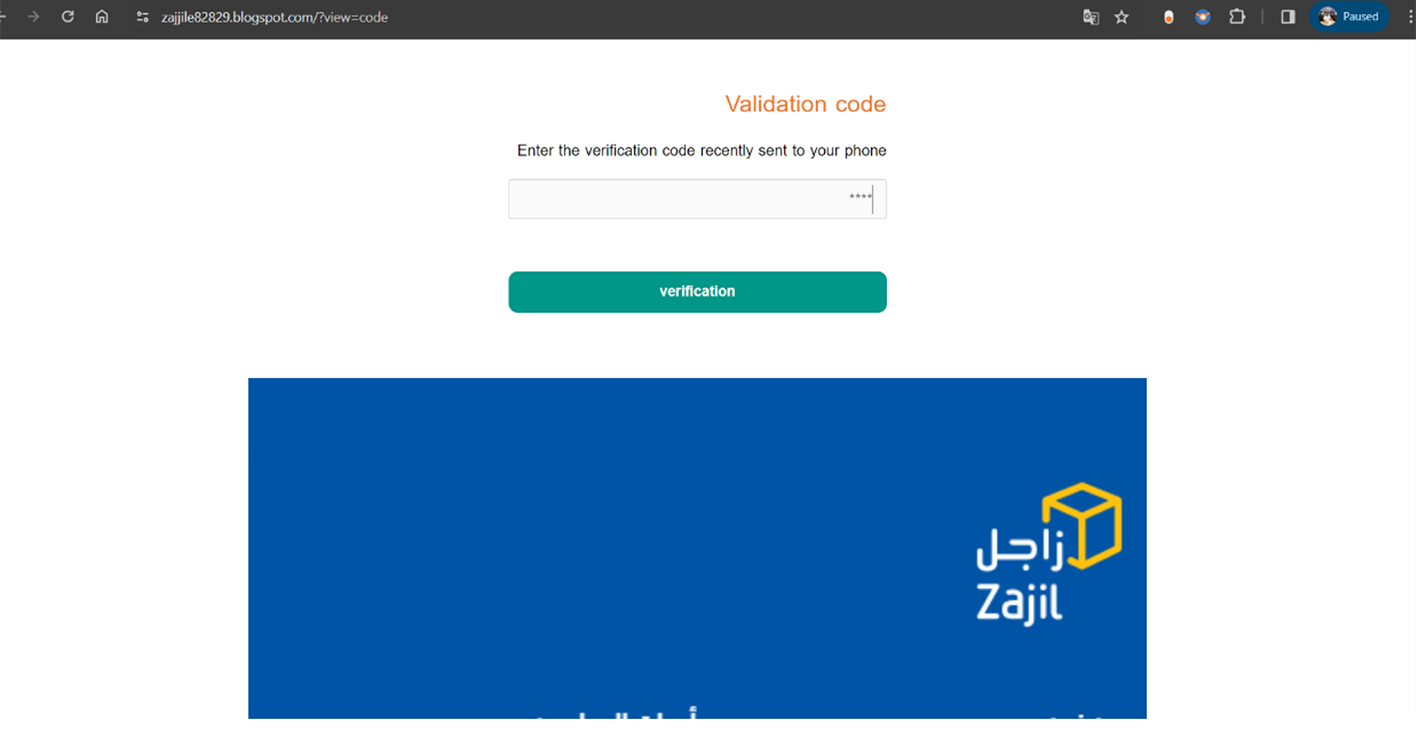
A scammer distributed a link to a phishing website along with an invitation to join a related WhatsApp group. Below is a snapshot of a text message that this scammer shared, providing insight into their tactics.
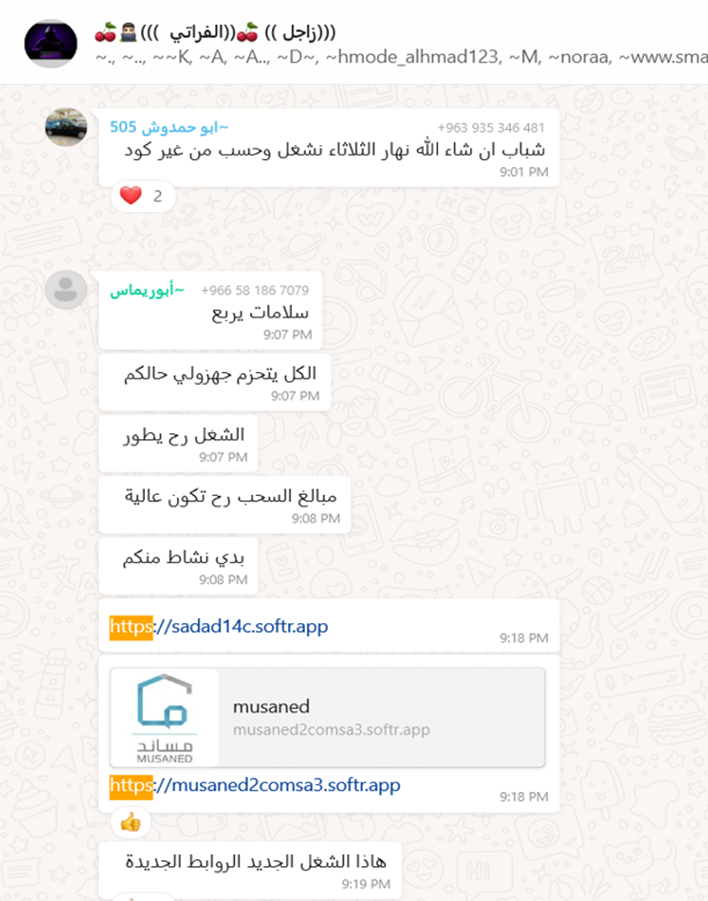
Translation:
I need activity from you
This is the new job, new links
I will give you the details if you know how to work.
Guys, I will show you how to work in this group.
Social Engineering Narratives:
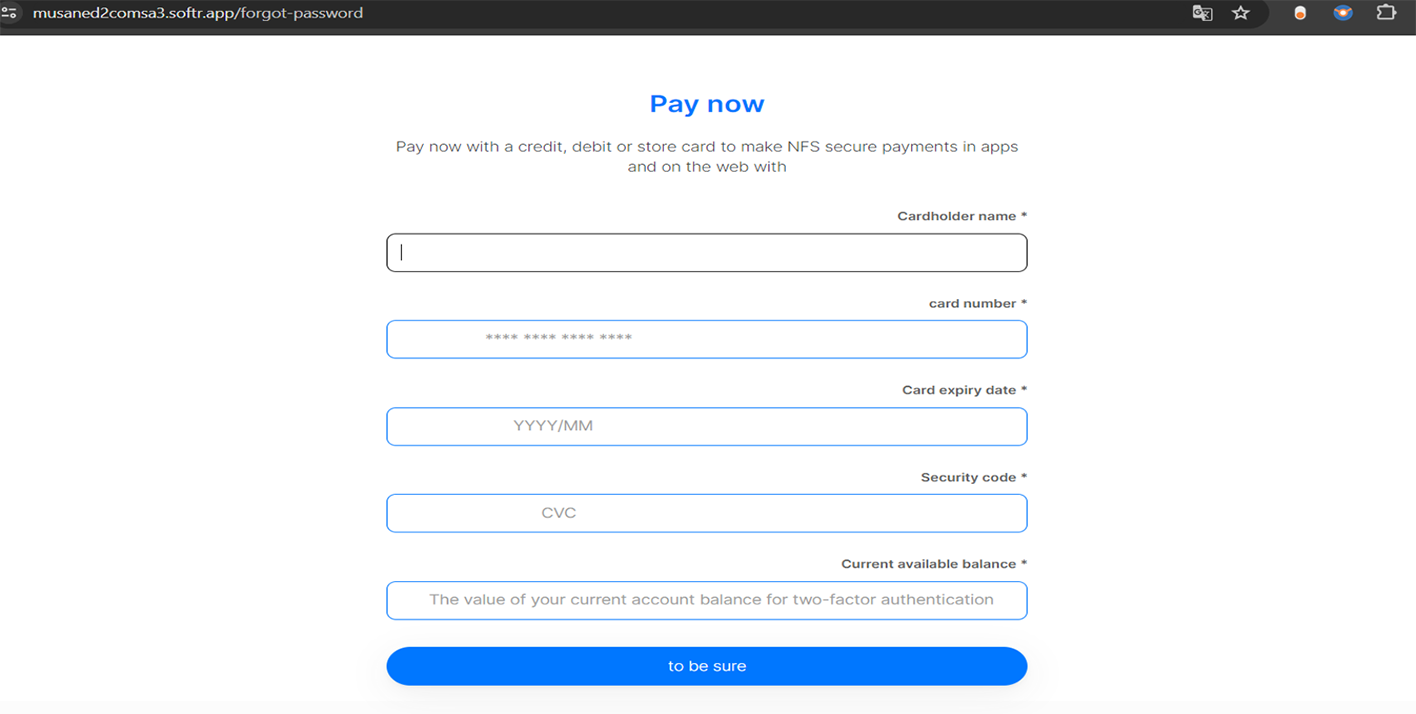
This scammer group employs a similar approach to the one described in the first case. However, a notable addition is the inclusion of an 'available balance' category in their payment interception form. This tactic allows the fraudsters to identify which credit cards have larger balances, making them more lucrative targets for card cloning and other financially motivated scams.
Example of fraudulent WEB-site impersonating Sadad:
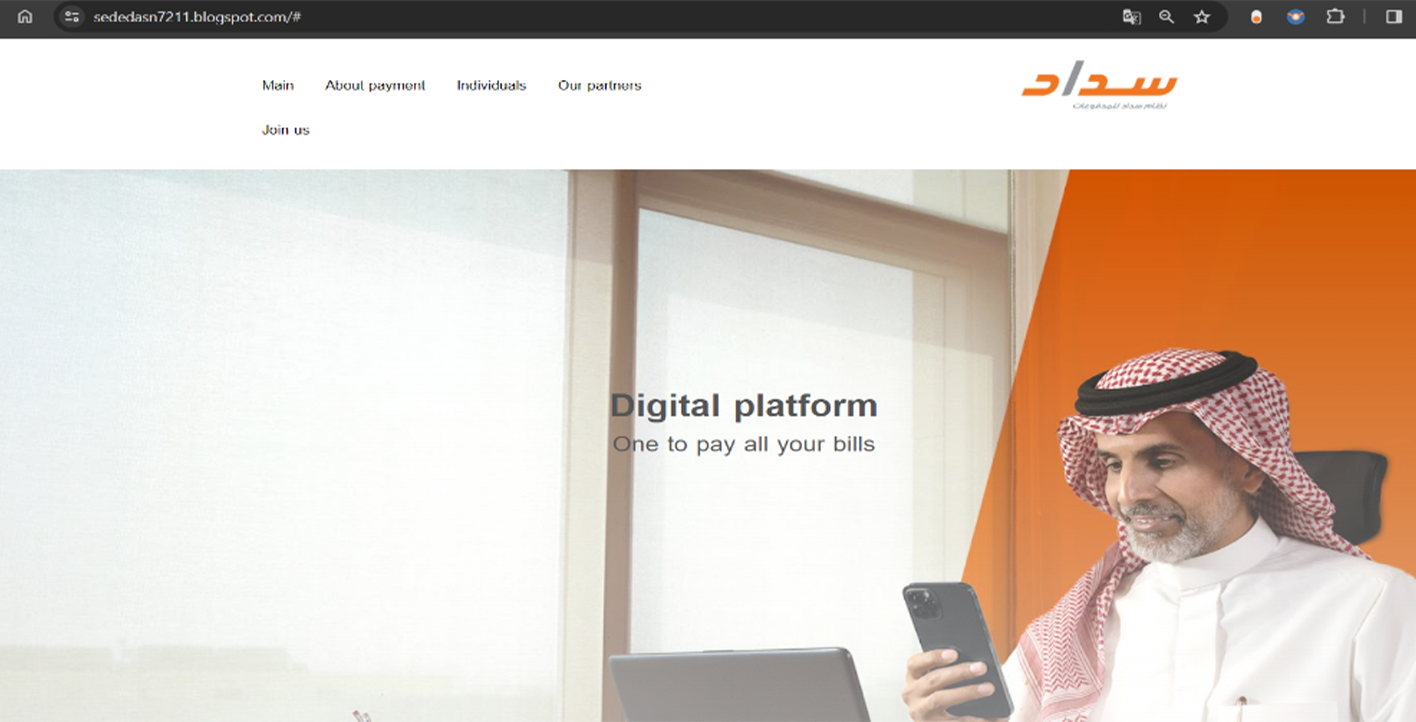

Example of fraudulent WEB-site impersonating Musaned:
https://musaned2comsa3.softr.app/
Besides payment data, the phishing kit observed in this particular campaign is also collecting job-related information. Such data may be extremely useful for scammers and fraudsters trying to recruit consumers for illicit activity or further scam.

Money Mules Recruitment via Ajeer
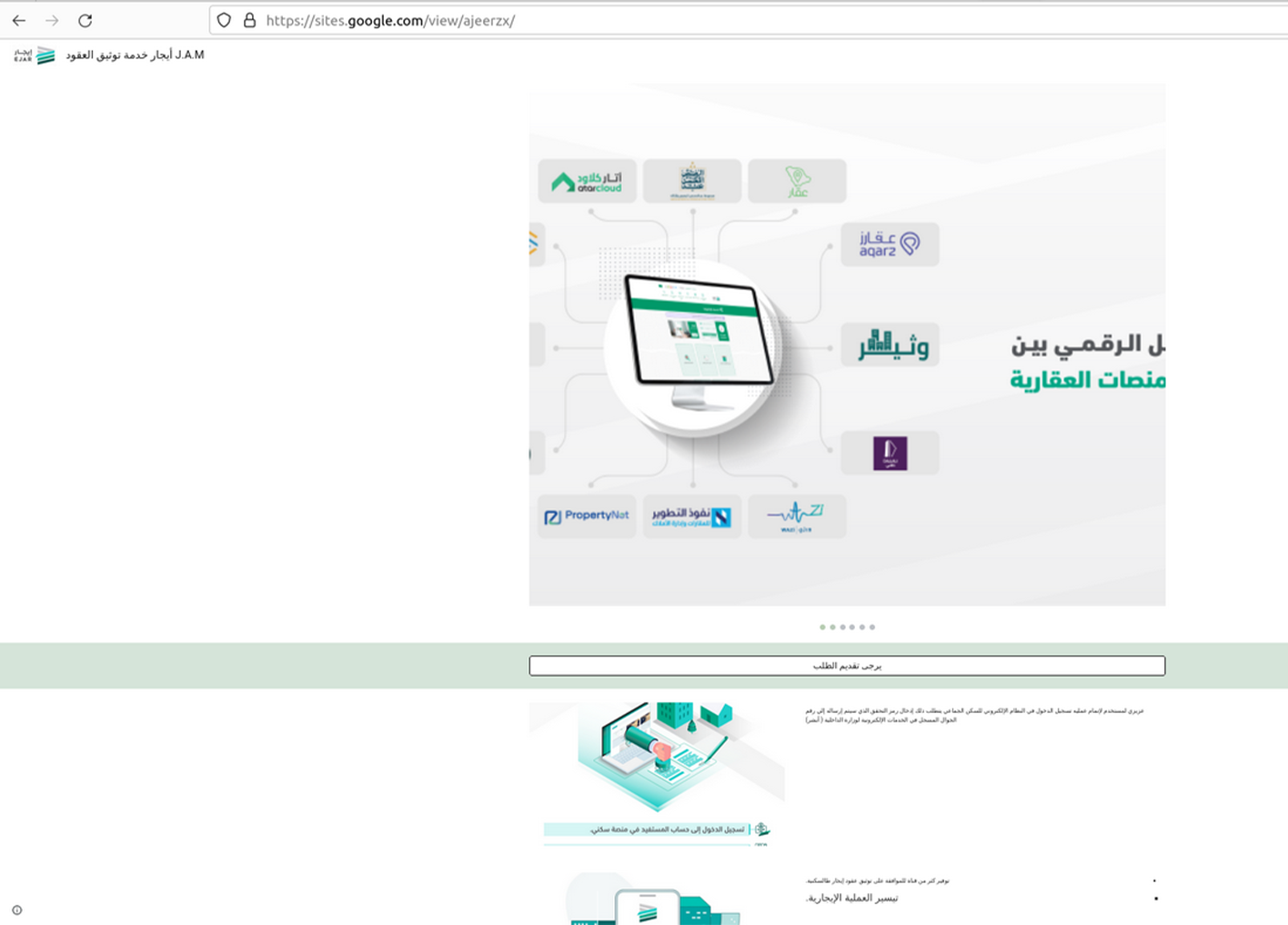
Ajeer is the official program sponsored by the Ministry of Human Resources and Social Development, which contributes to organizing temporary work and facilitating access to a workforce (labor force rental services). It aims to facilitate the procedures for accessing workers in the labor market, as well as completing the process of linking service providers and beneficiaries to ensure the provision of services in the labor market electronically. The Ajir portal enables establishments wishing to loan or transfer the services of their workers to upload the workers’ CVs and present them to establishments wishing to benefit from them. Fraudsters create fake resources to offer non-existing jobs to profit from illicit activity, as well as to exploit workers illegally. In many cases, they try to recruit innocent people and leverage them in various fraudulent activities, for example, as "money mules" (to receive stolen funds).
Original website: https://ajeer.qiwa.sa/
Phishing website: https://sites.google.com/view/iger-1
Rental Scams via Ejar Platform
Ejar is simplifying the process of leasing properties by providing a secure and convenient electronic solution for finalizing leases, utilizing a standardized contract approved by the Ministry of Justice.
Original website: https://www.ejar.sa/
Phishing website: https://ejar-sa-ar.netlify.app

The platform’s integration with the Kingdom’s government agencies simplifies the process of renting, eliminating the need to write checks or visit government offices in-person. Fraudsters create fake WEB-sites and social media groups misrepresenting Ejar.
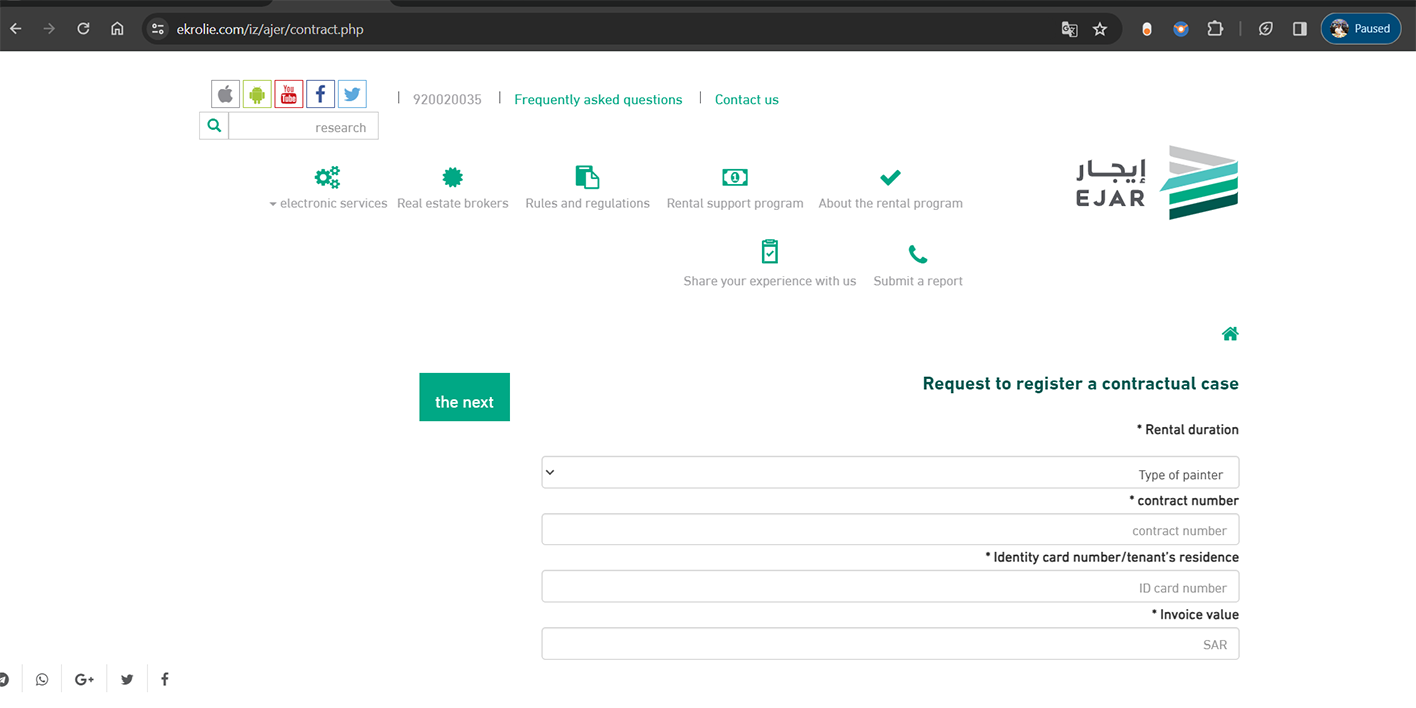
Additionally, they have integrated a payment system to intercept their victims' payment data, including card identity information, which likely leads to identity theft.
Conclusion
Due to continued efforts in brand protection for many clients in the Middle East, Resecurity has effectively blocked over 320 fraudulent sites and platforms that were impersonating key logistics providers and e-government services.
Cybercriminals are aggressively exploiting platforms such as Sadad, Musaned, Ajeer, Ejar, and well-known logistics services to deceive internet users and draw them into different scams. It is strongly advised to refrain from sharing personal and payment information on questionable sites or with individuals posing as bank or government employees.
Please reach out to your local law enforcement and the designated contacts in these organizations to report any suspicious resources, helping to prevent potential fraud risks. Resecurity is expecting fraudsters to intensify their use of these tactics in various social engineering schemes, exploiting the growing trust in e-government platforms.
The malicious actors utilize cloud-based hosting services like Softr, Netlify, and Vercel, which offer pre-defined templates, to create websites using AI. This method allows them to scale their operations efficiently, saving time and effort while rapidly generating new fraudulent sites at an unprecedented rate.
Indicators of Compromise (IOCs)
semssda6266[.]blogspot[.]com
aremexss549[.]blogspot[.]com
smsa[.]expries[.]com
zajil-express1[.]softr[.]app
musaned2comsa4[.]softr[.]app
ajer3[.]softr[.]app
zajil[.]expries[.]com/mh
smsa[.]expries[.]com/sa
sites[.]google[.]com/view/ajeerzx/
sites[.]google[.]com/view/iger-1
sites[.]google[.]com/view/sdad-8
anszajjlaty[.]vercel.app
3[.]zajil[.]shop
semsja66[.]blogspot[.]com
smsaas[.]site[.]pro
zajills[.]site[.]pro
ekrolie[.]com/iz/ajer
ejar-sa-ar[.]netlify[.]app

