Cybercriminals are Targeting Elections in India with Influence Campaigns
Cyber Threat Intelligence

Intro
Resecurity has identified a spike of malicious cyber activity targeting the election in India, which is supported by multiple independent hacktivist groups who arrange cyber-attacks and publication of stolen personal identifiable information (PII) belonging to Indian citizens on the Dark Web. The general election in India will take place from 19 April to 1 June 2024, spanning seven phases. The election will elect all 543 members of the Lok Sabha. The votes will be counted, and the results will be declared on 4 June 2024, marking the culmination of the election process.
The early stages of cyber attacks have been observed since the launch of #OpIndia campaign last year. The number of attacks increased by nearly 300% following the launch of #OpIsrael, which coincided with heightened online protests in the context of the ongoing Israel-Gaza crisis. With a massive population exceeding 1.4 billion people and a GDP of over 3.417 trillion USD, India has become a prime target for foreign threat actors and nation-state groups.
According to a report released by the National Counterintelligence and Security Center (NCSC) on foreign threats to elections, the primary types of malicious typologies targeting election integrity fall into five distinct categories:
- Cyber operations targeting election infrastructure,
- Cyber operations targeting political parties, campaigns, and public officials,
- Covert influence operations to assist or harm political organizations, campaigns, or public officials,
- Covert influence operations to influence public opinion and sow division,
- Covert efforts to influence policymakers and the public
These types of incidents generally act as precursors for more significant malicious activity that can be further amplified by foreign interference campaigns. Besides cyber espionage, threat actors aim to sow uncertainty about the integrity of elections via operations that aim to disrupt and manipulate public opinion globally. Unfortunately, these incidents remain complicated from an investigation perspective and are often imperceptible to the public.
Amidst historic geopolitical volatility and uncertainty, marked by
escalating conflicts throughout the Middle East and Eastern Europe,
securing elections from hostile cyber-threats has become vital to the
preservation of the global democratic order. In one of the recent reports, Resecurity outlined facts of malign cyber-activity targeting elections in more than 17 countries all over the world. The identified malicious activity against India in period of general elections follows the same pattern - involving data leakage, misinformation, public opinion and foreign interference campaigns.
Resecurity has summarized the key risk indicators of malicious activity to increase cybersecurity awareness among Indian citizens, encouraging them not to react to any claims or narratives originating from unreliable sources planted by cybercriminals, which could affect their votes.
Elections in India - Threat Landscape
Resecurity has identified the most active threat groups targeting India, which are:
1. Anon Black Flag | Indonesia
2. Anonymous Bangladesh
3. Morocco Black Cyber Army
4. Toxcar Cyber Team
5. Islamic Cyber Team
6. Lulzsec Indonesia
7. TEAM CYBER MAFIA
8. ANON TEN BD
9. Ketapang Grey Hat Team
10. ANON SEC BD
11. Team Ahadun Ahad (2.0)
12. Bangladesh Dark Net
13. Nixon Cyber Team
14. Cyber Sheild Force BD
15. UnitedSec-313
16. Sylhet Gang
These 16 groups have targeted multiple law enforcement, government, healthcare, financial, educational, and private sector organizations in India, taking advantage of geopolitical narratives before recent elections.
Leaked Voter ID Cards
Based on ongoing social media network monitoring and Dark Web monitoring, multiple episodes were identified where threat actors leaked Voter ID Cards, an identity document issued by the Election Commission of India to adults who have reached the age of 18 and are domiciled in India. The source of this data remains unclear, but it may be linked to compromised third-party entities collecting information for Know-Your-Customer (KYC) purposes and ID verification. Resecurity has alerted relevant law enforcement organizations and federal authorities to the leaked data, providing them with collected samples.
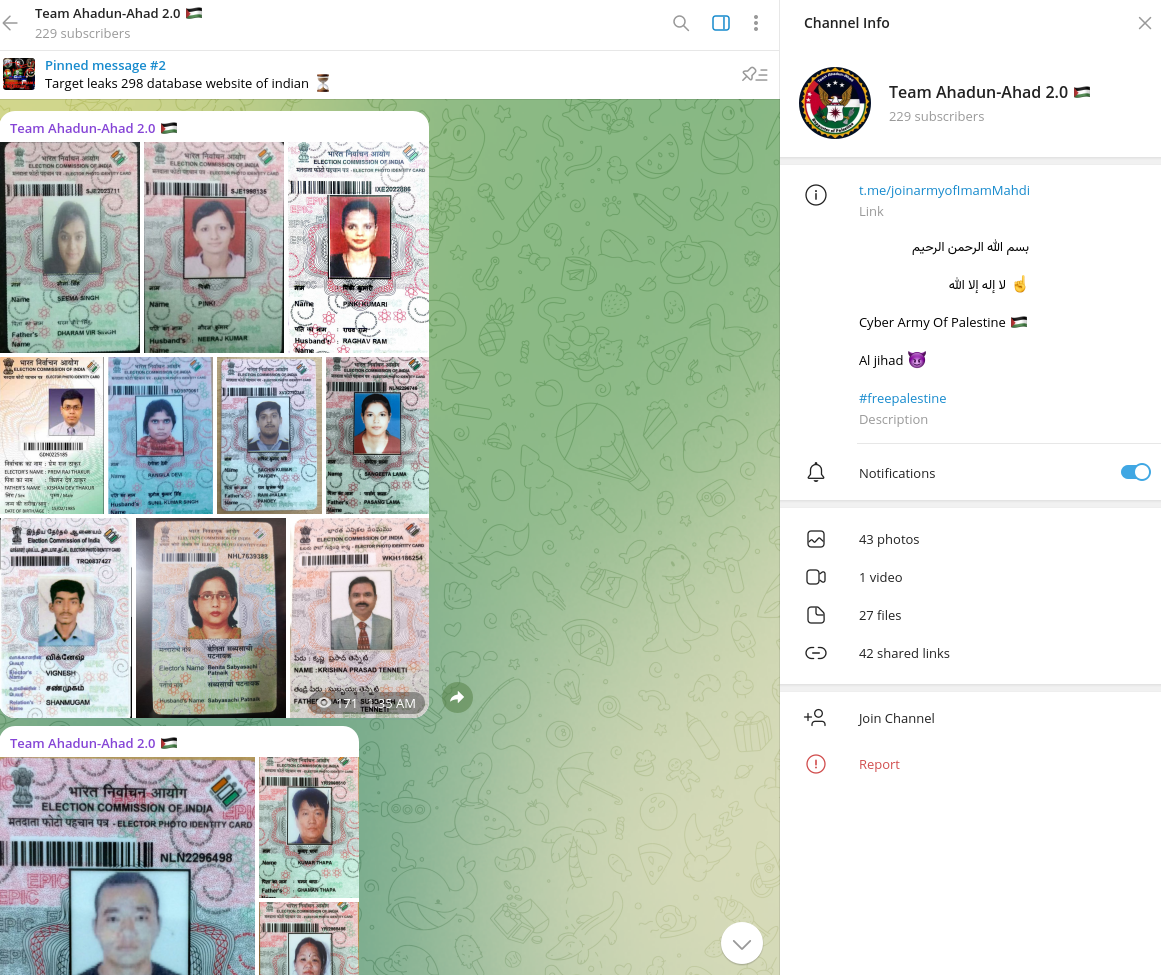
The primary goal of such leaks by foreign actors is to generate a narrative that Indian election systems are insecure and vulnerable to cyberattacks, which may affect public opinion and create distrust in electoral processes. In fact, such data has nothing to do with the insecurity of election systems, but rather relates to identity theft incidents where hackers steal documents of citizens from compromised lending, insurance, and other systems.
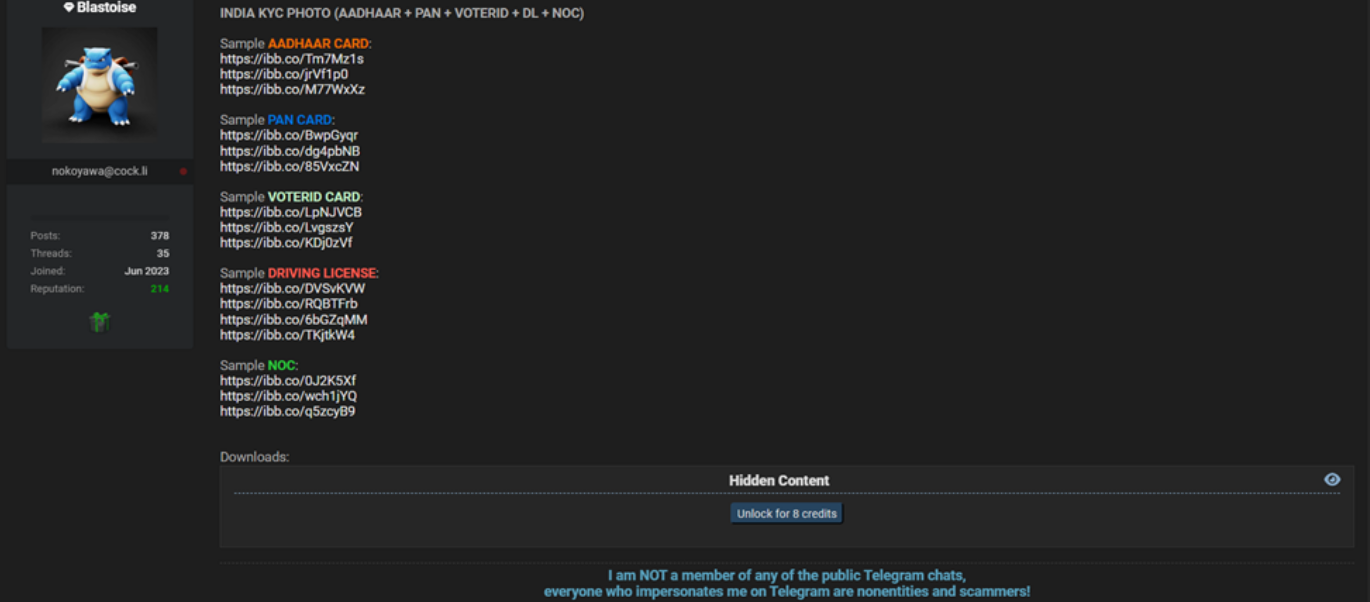
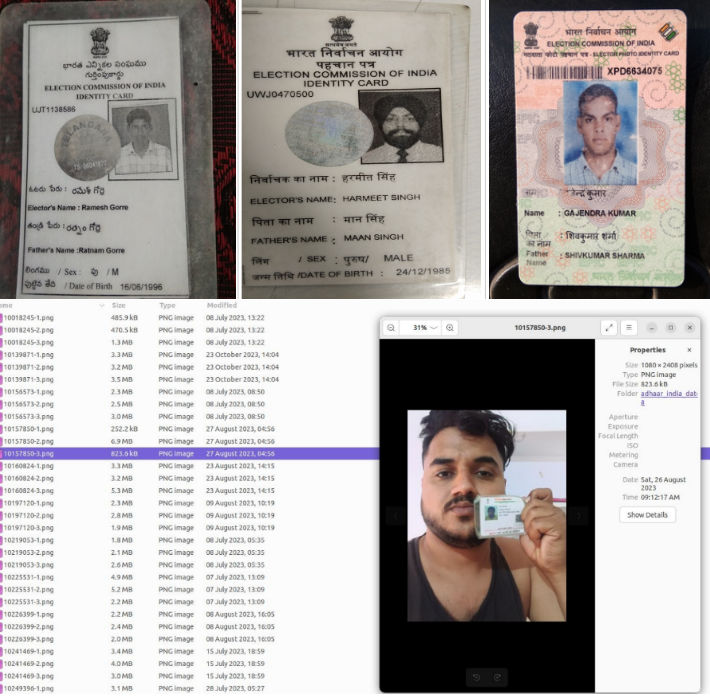
Prior to the publication of voter ID cards by the Ahadun-Ahad 2.0 Team on Telegram, similar data was offered on the Dark Web by cybercriminal actors along with stolen AADHAAR, PAN, driving licenses, and NOC documents. Notably, the majority of documents were provided in graphic form, where the victim was holding the document in hand as typically provided for KYC purposes with a selfie, which confirms that the data is originating from a third-party KYC system.
Adversaries could reuse this information by generating a public opinion manipulation campaign leveraging the narrative of election system insecurity during general elections. Resecurity acquired 36 GB of stolen personal identifiable information (PII) belonging to Indian citizens and applied computer vision to recover details about victims from a graphical form.
The data observed in recovered datasets from the dark web matches the records leaked during the general elections, suggesting a potential link between the two.
Besides graphical data files, including voter registration records, the actors also leaked large data sets containing voters' credentials. Based on our analysis of the leaked data, we believe that these credentials could be obtained through malicious software programs known as infostealers (password grabbers), which are designed to steal sensitive information. Such malware programs, including Nexus, Medusa, Redline, Lumma, and Racoon, are designed to steal sensitive information such as login credentials and financial data.
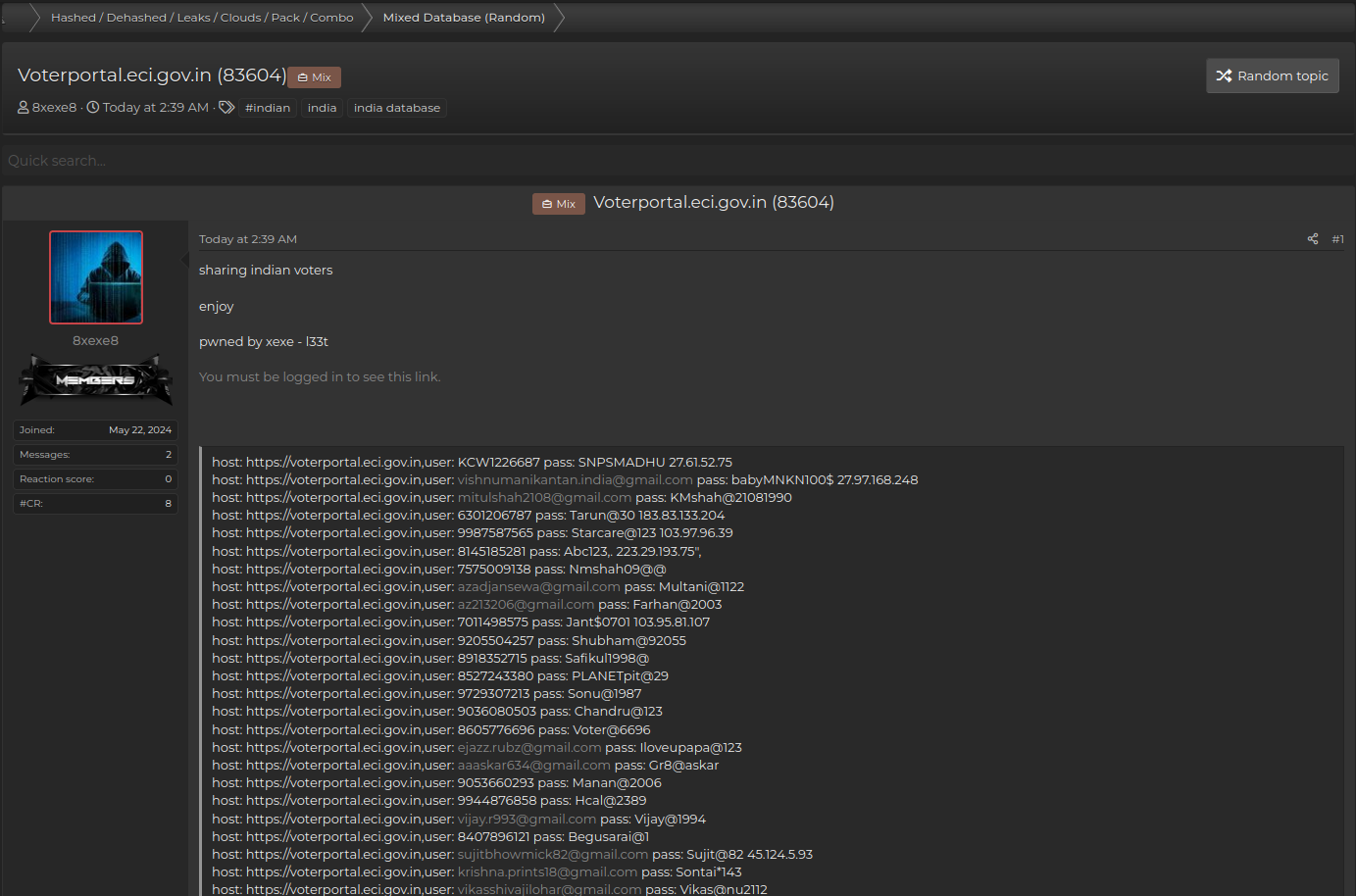
Specific signatures identified in leaked data sets may confirm that they originate not from any vulnerable election systems, but likely from compromised consumers with malicious code. The compromised credentials could have been obtained by intercepting login forms on popular Internet browsers or by accessing password storage on compromised devices.
Resecurity reached out to multiple victims whose credentials were compromised. The victims' feedback revealed that they recognized their passwords, with some noting that their passwords were old, but also acknowledging that they had been infected with malware and had to reinstall their operating system. At some point, threat actors were aiming to leak a big number of voters' records to create a perception that elections systems are vulnerable. In fact, the origin of these credentials is on the consumer side, as many Internet users are getting infected with malware due to poor network hygiene and lack of cybersecurity awareness.
Public Opinion Manipulation and Influence Campaigns
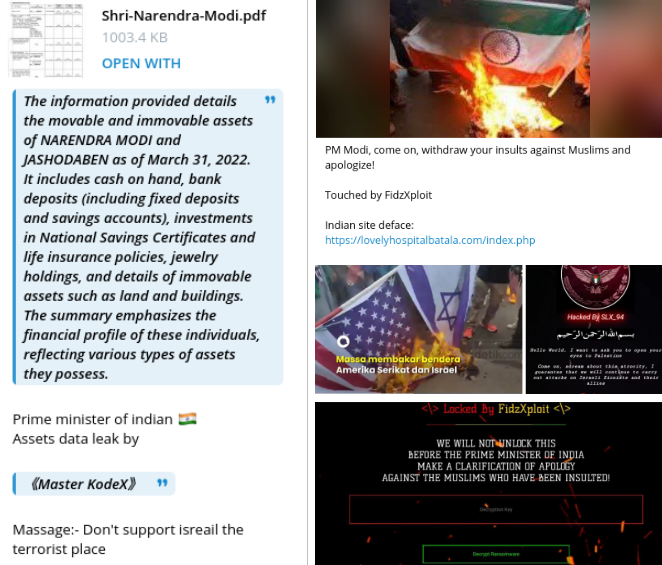
Resecurity has observed several public opinion manipulation campaigns targeting Indian government leaders, including the Prime Minister. Adversaries combine data leaks, website defacements, and political narratives to abuse the public profile of the government. These 'cyber-guerilla' tactics enable them to blur attribution and operate under the 'false flag' of independent hacktivists. The activity of these adversaries is coordinated by efforts and timing, which suggests that they may be influenced by external parties.
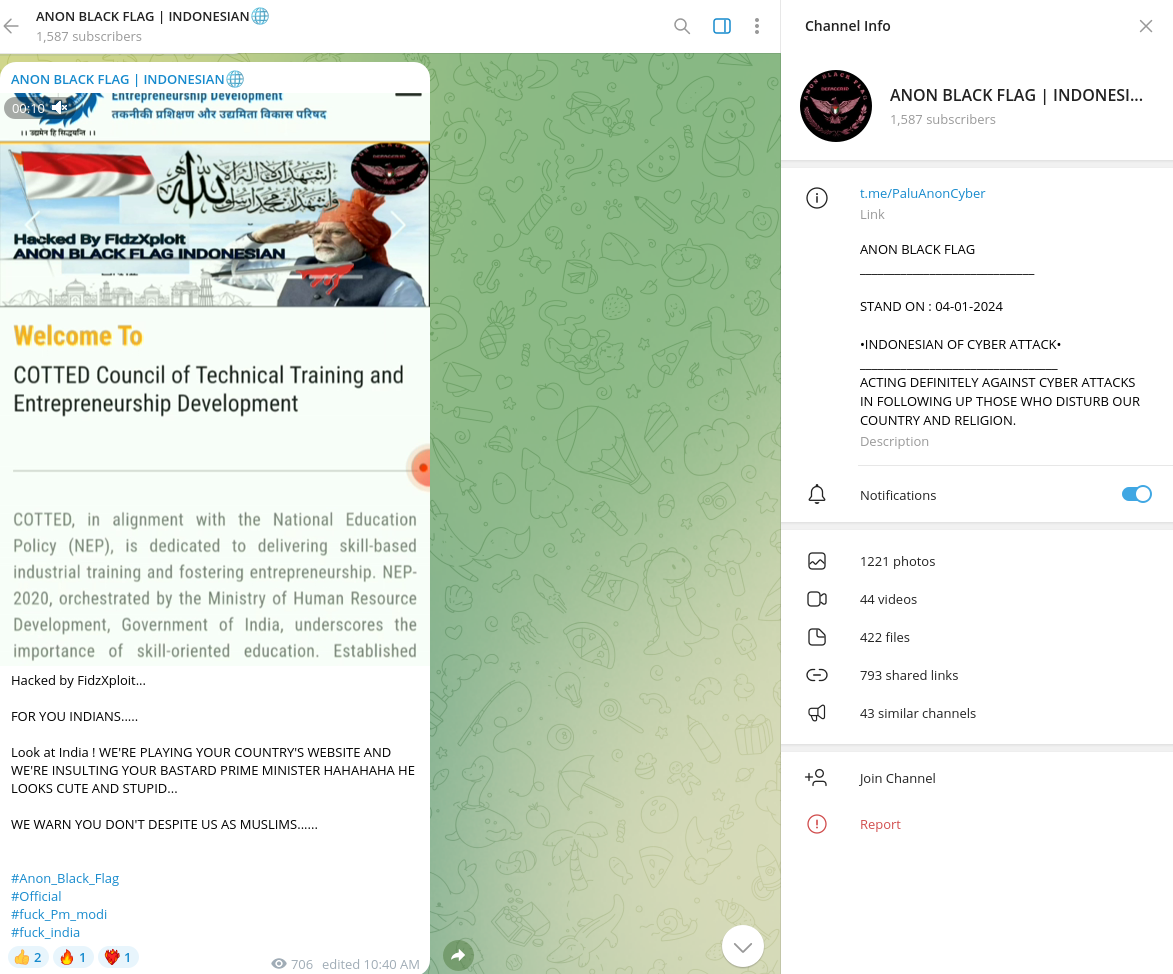
The majority of these groups also aim to create a social conflict between Indian and Muslim populations, which is critical to prevent in light of a complicated geopolitical situation in the world. In one such campaign, adversaries attempted to combine fake narratives about the country's leadership with abusive nationalist rhetoric.
Ongoing Cyber Conflicts and "False Flags"
After coming to power in November last year, President of Maldives, Mr. Mohamed Muizzu, who is considered pro-China, asked India to withdraw its troops from Maldives. The new deal with China marks a significant shift in Maldives’ foreign policy from Muizzu’s pro-India predecessor, Ibrahim Mohamed Solih. Given their geographic proximity and strong historic and economic ties, India was for decades Maldives’ closest partner and New Delhi viewed the region as part of its traditional sphere of influence.
Such geopolitical trends are rapidly exploited by cyber threat actors. Before general elections, multiple groups were identified as conducting cyberattacks. These groups were exploiting the narrative, exaggerating the problem. "Pro-India"-looking cyber groups have launched targeted attacks on key Maldivian institutions, including the Maldives National Defence Force, Maldives Bureau of Statistics, Maldives Business Times, Juvenile Court of Maldives, Maldives Immigration Department, and the Finance Department of Maldives. Key groups involved in these cyber operations include:
1. Team UCC
2. Network Nine
3. Black Dragon Sec
4. Team Blackdragonsec
5. Team NWH Security
6. Kerala Cyber Black Squad
7. Kerala Cyber Extractors
8. Team Anon One
9. Team ICP
10. Anonymous India
11. Unknown Cyber Cult
12. India Cyber Punk
13. Team NWH
14. All India Hackers
15. Network Nine
16. Black Dragon Sec
17. Dark Cyber Warrior
18. Glory Sec
19. Team Garuna.
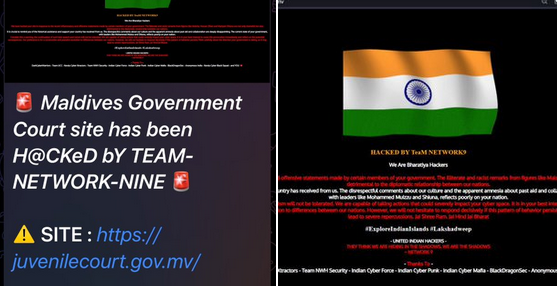
Such activity could be conducted under a 'false flag' to generate more tensions. Another nation-state actor might be interested in amplifying these narratives to achieve their goals. This episode may be a good example of a cyber-influence operation conducted prior to elections in India with the aim of affecting foreign policy matters via cyberspace. To mitigate the risk of growing tensions, it is critical to promote principles of cyber peace. Establishing proper channels for diplomacy is crucial. Additionally, further investigation of such activity should be conducted via relevant law enforcement organizations.
Risk Mitigation
It is important to ensure that the collection, storage, and use of digital identity data comply with data protection regulations and do not violate citizens' privacy rights. Implementing robust security measures and adhering to privacy regulations can help build trust among voters and protect their privacy.
Threat actors can use stolen identities to create and disseminate false information, including disinformation about election infrastructure vulnerabilities. This can lead to confusion among voters and undermine trust in the electoral process. By spreading disinformation, threat actors can also profit from selling stolen information on the dark web or using it for targeted campaigns.
It's critical to implement robust digital identity protection measures to minimize the risk of identity theft. To achieve this, Resecurity launched a digital identity protection solution in India that safeguards citizens' national ID documents. As a pioneer in this field, Resecurity successfully launched its solution in 2023, providing a critical layer of protection against identity theft and fraud.
In order to build a cybersecure society and safeguard the citizens identity information, it is critical to implement proper identity protection mechanisms with proactive notifications for citizens when such leaks are detected in dark web. Resecurity notified the affected victims and enabled monitoring of leaked AADHAAR and Voter ID Cards records via the Identity Protection solution and mobile app which is available for Android and Apple iOS.
References
- Cyber threat activity against election infrastructure
https://www.cyber.gc.ca/sites/default/files/cyber-threats-canada-democratic-process-2023-update-v1-e... - Understanding
cybersecurity throughout the electoral process: a reference document.
An overview of Cyber Threats and Vulnerabilities in Elections. https://www.usaid.gov/sites/default/files/2023-01/Understanding-Cybersecurity-Throughout-the-Elector...
- Securing the 2024 Elections
https://www.brennancenter.org/our-work/policy-solutions/securing-2024-election - Security experts warn of foreign cyber threat to 2024 voting
https://apnews.com/article/iran-united-states-government-russia-arizona-3cbfa1c46051416fac1f4183774a...
- The Pivotal Elections of 2024: Key Races That Will Shape the Global Landscape
https://www.usip.org/publications/2024/01/pivotal-elections-2024-key-races-will-shape-global-landsca...

