Cybercriminals Impersonate Dubai Police to Defraud Consumers in the UAE - Smishing Triad in Action
Fraud Intelligence

Intro
Resecurity has identified a wide-scale fraudulent campaign targeting consumers in the UAE by impersonating law enforcement. Victims are asked to pay non-existent fines online (traffic tickets, parking violations, driving license renewals) following multiple phone calls made on behalf of Dubai Police officers. This social engineering scheme has been amplified by targeted phishing, smishing, and vishing activities, with a noticeable increase around the winter holidays. Dubai Police have warned against calls from scammers asking for financial details, reminding residents that official institutions will never request this information over the phone.
Notably, a spike in fraudulent activities has been detected around a significant date for the UAE - National Day, now known as Eid Al Etihad, celebrated annually on December 2. The Ministry of Human Resources and Emiratisation (MoHRE) has announced that December 2 and 3, 2024, will be official paid holidays for all private sector employees in the UAE. Cybercriminals quickly took advantage of this festive period when citizens were relaxed, and less vigilant at home, resulting in financial losses.
According to a recent Strategic Analysis Report released by the UAE Financial Intelligence Unit (UAEFIU), fraud, particularly in the UAE, remains a major risk, contributing to money laundering activities, with an estimated financial loss of AED 1.2 billion (equal to USD 326 million) between 2021 and 2023. The expert report by the authority outlined that vishing, phishing, and smishing are the top fraud types in the UAE, based on the analyzed STRs (Suspicious Transaction Reports) and SARs (Suspicious Activity Reports).
Rogue Law Enforcement - Scam Exploiting Trust
The actors launched a sophisticated campaign, targeting multiple victims with phone calls from individuals impersonating law enforcement officials requesting payment arrangements. A month earlier, Dubai and Abu Dhabi Police warned citizens not to share their confidential information, including their account, card details or online banking credentials.
The actors became more creative. Before contacting victims, they sent fake payment requests via SMS/iMessage and email notifications mimicking Dubai Police branding, which included a payment page. This caused confusion among victims, who assumed they were receiving legitimate instructions to act.
In one documented call reported by Resecurity, the victim was contacted by an individual with an Indian accent and background noise typical of call centers. The individual introduced himself as an inspector and warned the victim that if he did not pay, his driving license would be revoked and his vehicle would be seized. Typically, such fraudsters are part of organized crime groups that stress the victims and extort payments.
With the victim's permission, our team is sharing the conversation transcript between the fraudster (who was impersonating Dubai Police) and the victim. Our goal is to increase consumer awareness and protect them against such scams.
Fraudster: We are calling you to check your records. Victim: OK, checking my records? Fraudster: In this regard, we are calling you. Victim: Yeah, OK, go ahead. Fraudster: Yeah. You can check your mobile inbox, and our department at Dubai police will send you the investigation file number. Hope you have already received it from Dubai police. Victim: No, I didn't receive anything. Once I receive it, I will check, OK. Fraudster: Did you receive it? Victim: I didn't. I didn't receive anything. Fraudster: Right now, you can check it. Victim: OK, one minute. Yeah, I have received it. OK. Fraudster: Now we can continue. This is a recorded line. Officers are listening to you on the call. We will ask you some investigation questions, give the correct answer on the recorded line. First of all, you can tell me, what is your legal occupation in our country? Victim: Hello. Fraudster: First, can you tell me your legal occupation in our country? Victim: What exactly? Fraudster: What is your legal work in our country? Victim: I don't understand you. Why? Why are you asking me this question? Fraudster: This is the investigation call, and this is the recorded line. Officers are listening to you on the call. I will ask you some investigation questions and you will answer correctly on the recorded line. Victim: OK. OK. Officer. OK, officer. OK. Fraudster: So, you can tell me about your legal work in our country. Victim: And who are you again? Fraudster: Who I am again, Captain Sheikh Abdul Aziz Ibrahimi.
Network Infrastructure
The actors abused multiple domain names belonging to major enterprises in Albania (.al). In the most recent episode, a malicious email campaign leveraged multiple compromised business emails belonging to one of the Albania's leading companies in the copper mining industry.

After the successful de-obfuscation of malicious content, references were also found to domain names controlled by the bad actors, which are registered in the .om domain zone (Oman) - traffic[.]itv[.]om.
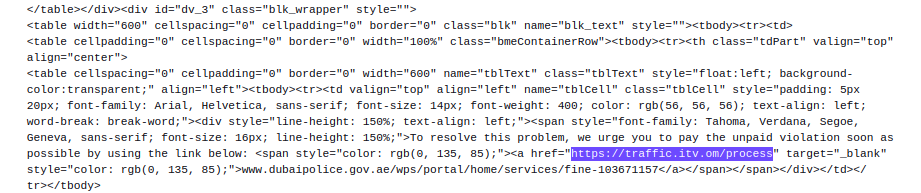
Smishing content delivered via iMessage has been sent from compromised and registered Gmail accounts (e.g., "dawnpricemdhxcidhv9359@gmail.com") with fake notifications sent on behalf of Dubai Police.
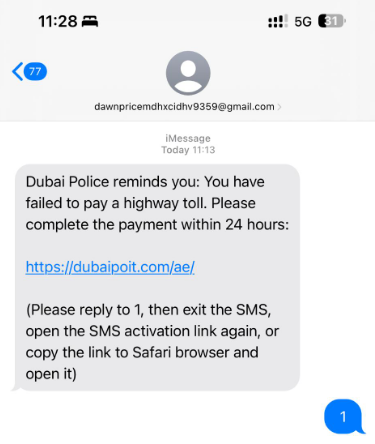
Further smishing scenarios included a reference to a minimal fine, which encouraged the victim to provide credit card details. The low amount and the notification from Dubai Police tricked many victims. Once the credit card details were entered, cybercriminals used them for much higher charges at the controlled merchants registered on money mules.
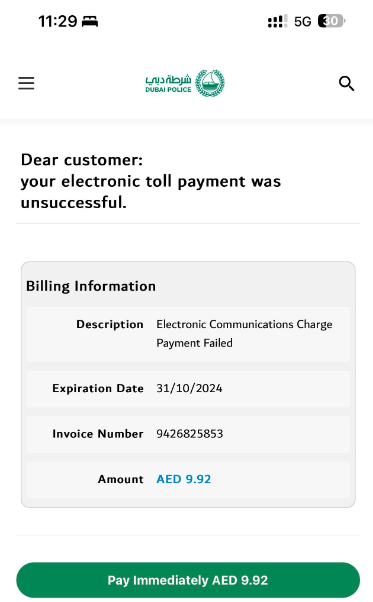
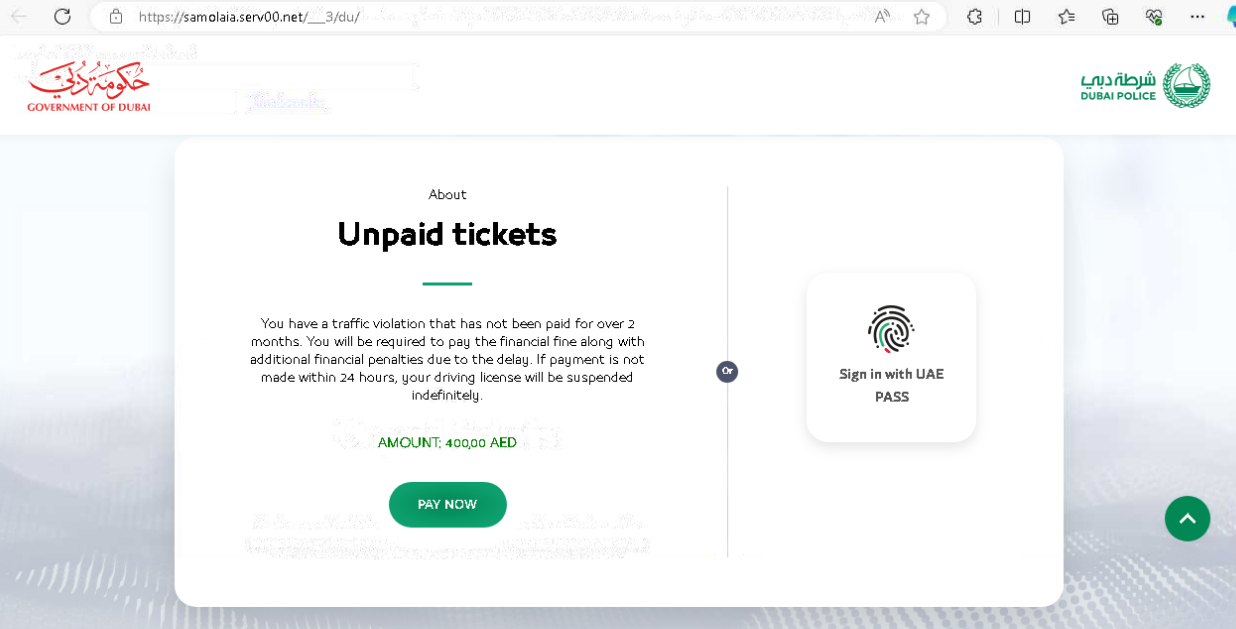
A smishing scenario involved imitating an online payment form copied from legitimate e-government resources to pay penalties for traffic violations.
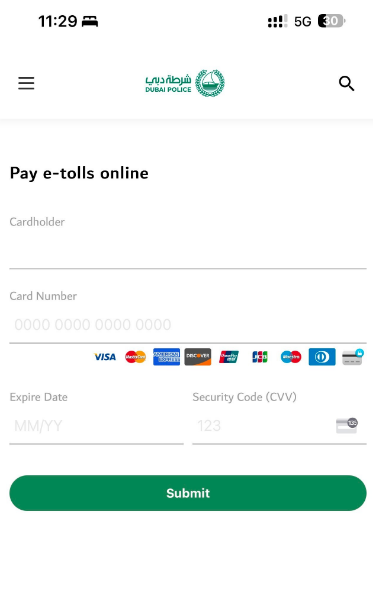
Multiple variations designed for PC and mobile devices were detected, including scenarios involving the theft of personally identifiable information through a fake UAE PASS form.
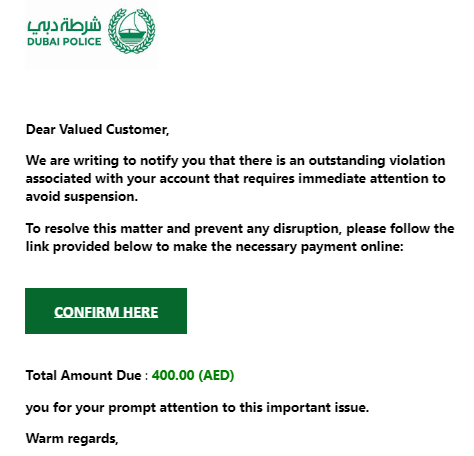
Like the previous scenario, the victims received fake notifications via e-mail asking them to pay outstanding violation fees:
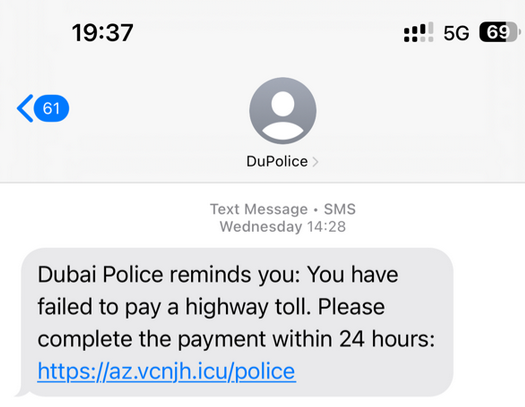
Resecurity identified over ten different templates that bad actors used to bypass spam filters.
Smishing Triad - Sentiments with Chinese Tint
Notably, some of the domain names identified in the observed campaign have been registered via Chinese domain registrar "59.cn":
Based on historical WHOIS records, Resecurity recovered information about the registrar organization and identified a cluster of domains in the ".icu" zone the attacker controls:
Domain Name: VCNJH.ICU Registry Domain ID: D488102544-CNIC Registrar WHOIS Server: whois.59.cn Registrar URL: http://www.59.cn Updated Date: 2024-11-18T10:56:26.0Z Creation Date: 2024-09-23T10:22:50.0Z Registry Expiry Date: 2025-09-23T23:59:59.0Z Registrar: ZHENGZHOU CENTURY CONNECT ELECTRONIC TECHNOLOGY DEVELOPMENT CO., LTD Registrar IANA ID: 2805 Registrant Organization: zhou zhen hua Registrant State/Province: Qing Dao Shi Registrant Country: CN Name Server: DM1.DNS.COM Name Server: DM2.DNS.COM DNSSEC: unsigned Registrar Abuse Contact Email: abuse@59.cn Registrar Abuse Contact Phone: +86.15515571878
Another group of domains has been registered via Gname.com Pte. Ltd., a Singapore-based company that the Smishing Triad used in previous campaigns.
Domain Name: DUBAIPOIT.COM Registry Domain ID: 2931929839_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.gname.com Registrar URL: www.gname.com Updated Date: 2024-11-29T03:16:23Z Creation Date: 2024-11-06T07:10:19Z Registrar Registration Expiration Date: 2025-11-06T07:10:19Z Registrar: Gname.com Pte. Ltd. Registrar IANA ID: 1923 Registrar Abuse Contact Email: complaint@gname.com Registrar Abuse Contact Phone: +65.31581931 Registrant State/Province: DSFDS Registrant Country: AX Name Server: A.SHARE-DNS.COM Name Server: B.SHARE-DNS.NET
The malicious scenarios used were consistent in code with those observed in a similar campaign impersonating the UAE Federal Authority for Identity and Citizenship, as reported by Resecurity last year. The tooling used by the Smishing Triad has been initially identified by Resecurity and is offered by a Chinese-speaking actor on Telegram. Notably, the group includes members from Indonesia, Vietnam, and other countries involved in fraudulent activities.
Indicators of Compromise (IOCs)
Based on available Passive DNS records, Resecurity identified over 144 domain names registered by the actors in the .com, .om, .site, .top and .icu domain zones. Notably, some of them were registered between September and November 2024. The total number of domain names registered that contain variations of the "Dubai Police" signature exceeds 730, as identified within the same timeframe. A substantial number of domain names has also been registered in alternative TLDs such as .buzz, .click, .one, and .xyz. However, not all of these have been attributed to the same group. Multiple threat actors and cybercriminal groups are leveraging similar patterns by impersonating Dubai Police.
According to independent research, a 40 percent increase was identified in phishing attacks involving the new generic top-level domains (gTLDs), which attract fraudsters due to low prices and a lack of registration detail validation requirements, thereby opening doors for abuse.
Some examples of the identified domain names are provided below. Resecurity has successfully disrupted the hosts controlled by threat actors and has arranged successful takedowns to stop this malicious activity, and shared collected intelligence with relevant law enforcement organizations.
September, 2024 |
October, 2024 |
November, 2024 |
www.ityht.icu ju.fhjre.icu ex.xnkkg.icu ws.tyrrt.icu zc.bnfhf.icu ww.xbhff.icu fs.fdghe.icu www.zvdeasa.icu sx.ssgxvx.icu fc.xcbbx.icu bc.cnbjgds.icu gf.uoyty.icu qq.bcvgdf.icu fc.hjffd.icu tg.sdhju.icu xx.cxbdf.icu ws.bnfhfd.icu az.vcnjh.icu gv.ityht.icu yg.utyus.icu ws.vdsfsh.icu pl.fhm.icu fs.vjddg.icu ut.ddgjcv.icu ws.dsgsv.icu va.sdwdf.icu dsw.jffdd.icu jffdd.icu erfdg.icu fswwr.icu rfsfh.icu yrn.rfsfh.icu poc.kjf.icu dsfjd.icu gev.dsfjd.icu vhu.kgfhre.icu kgfhre.icu vgu.kgfhre.icu zvm.icu wds.zvm.icu zvdeasa.icu fs.zvdeasa.icu cxzve.icu ccss.cxzve.icu fgrecb.icu rc.fgrecb.icu vnvcn.icu fcs.vnvcn.icu kjf.icu uhbds.icu dsgey.icu fdg.icu xcber.icu dub.xcber.icu dcxbj.icu dub.dcxbj.icu adfte.icu rfcxb.icu auedu.rfcxb.icu edfsg.icu qad.edfsg.icu qad.uhbds.icu qad.dsgey.icu qad.fdg.icu oijsd.icu rdf.oijsd.icu xstyj.icu rdf.xstyj.icu fhiugcx.icu yhbfl.fhiugcx.icu asfjte.icu tfs.asfjte.icu dfuewe.icu yhbfl.dfuewe.icu etyur.icu tfs.etyur.icu bxahj.icu aued.bxahj.icu czsfhjh.icu aued.czsfhjh.icu cxbha.icu tfs.cxbha.icu dcnar.icu hgf.dcnar.icu gjhdf.icu zvvbgf.icu ijnvb.icu tfs.gjhdf.icu okj.ijnvb.icu aued.zvvbgf.icu asytfsv.icu aued.asytfsv.icu sagy.site urwyu.icu sxf.sagy.site dah.icu uhk.urwyu.icu yg.dah.icu yoidg.icu rfv.yoidg.icu bvwds.icu hgf.bvwds.icu joujg.icu ygv.joujg.icu |
dubaipoliauey.top fhjrw.icu ityht.icu uoyty.icu ssgxvx.icu bnfhf.icu cnbjgds.icu sdhju.icu cxbdf.icu yrtrer.icu ddvvs.icu dfhkk.icu gfjut.icu tgv.gfjut.icu fhjyd.icu ygv.etw.icu yt.dfhkk.icu hg.ddvvs.icu jjfdfe.icu cxdfh.icu bcvgdf.icu ddgjcv.icu dsgsv.icu vdsfsh.icu hjffd.icu xnkkg.icu vc.jjfdfe.icu fdghe.icu dq.fhjyd.icu xcbbx.icu fhjre.icu sdwdf.icu vcnjh.icu utyus.icu ghl.icu vjddg.icu bnfhfd.icu fgf.yrtrer.icu |
etw.icu dsgwe.icu tyrrt.icu dubaipoit.com |
Significance
Previously, Resecurity described multiple episodes of Smishing Triad activity targeting online banking, e-commerce and payment systems customers in other geographies including USA, EU, UK, Pakistan, India, UAE and KSA:
- Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season
https://www.resecurity.com/blog/article/cybercriminals-impersonate-uae-federal-authority-for-identit...
- Smishing Triad Impersonates Emirates Post to Target UAE Citizens
https://www.resecurity.com/blog/article/Smishing-Triad-Impersonates-Emirates-Post-Target-UAE-Citizen...
- Smishing Triad Targeted USPS and US Citizens for Data Theft
https://www.resecurity.com/blog/article/smishing-triad-targeted-usps-and-us-citizens-for-data-theft
Our analysts estimate the scale of threat actors' activities: they send between 50,000 and 100,000 messages daily. To achieve this, they leverage stolen databases acquired from the Dark Web, which contain citizens' sensitive personal data, including phone numbers.
Mitigation
Dubai, Sharjah, and Ajman residents can report scam numbers by calling the toll-free call center number at 901. In Abu Dhabi, scam numbers can be reported by calling 800-2626, sending an SMS to 2828, or emailing aman@adpolice.gov.ae.
References
- Dubai Police warn residents of scam calls
https://www.arnnewscentre.ae/en/news/uae/dubai-police-warn-residents-of-scam-calls/
- Report cyber-crimes online
https://u.ae/en/information-and-services/justice-safety-and-the-law/cyber-safety-and-digital-securit...
- Organized Financial Fraud - Trends and Enablers - A Strategic Analysis Report (by UAE Financial Intelligence Unit)
https://www.uaefiu.gov.ae/en/more/knowledge-centre/publications/trends-typology-reports/organized-fi...

