CyFI: An Essential Paradigm for Financial Crimes Compliance and Risk Management in the 21st Century
Fraud Prevention

A recent global bank risk management survey published by consultants Ernst & Young found that cybersecurity was the top concern cited by finance industry chief risk officers for the upcoming year. Fifty-eight percent of respondents also said their inability to manage cyber-risk was their top strategic concern for the next three years.
While respondents likely factored their outlook within the broader geopolitical storm precipitated by the war in Ukraine, which has amplified the risk of cyber-military attacks against Western firms, the legacy of the COVID-19 pandemic also looms large in the backdrop. Beyond banking, the lasting impact of the pandemic also continues to ripple across the fintech and e-commerce sectors.
Collectively, these three verticals are projected to be significant vessels for some $635 billion in losses attributable to identity fraud in the U.S. this year. While this figure remains meaningfully below ID-fraud-related losses recorded in 2020 and 2021, 2023 estimates signal an uptick over the previous year. This trendline is the byproduct of cybercriminal evolution during the pandemic.
As COVID-era lockdown policies forced consumers online, global public health mandates inevitably led to an explosion of traffic on e-commerce websites and online banking portals. Adoption of peer-to-peer (P2P) payments apps, fintech lending platforms, wealthtech apps, and cryptoassets also surged.
Unprecedented growth in fintech usage was inevitable, as harsh restrictions imposed by public health authorities forced consumers and businesses to adopt digital and user-friendly solutions to adjust their needs to quarantined commerce. At the same time, the so-called ‘creator economy’ took flight, empowering over 200 million economically displaced young people to become influencers and monetize various forms of user-generated content on a variety of social media and streaming platforms.
Creators proliferated in this environment, producing content geared toward online marketing, entertainment, gaming, investment, crypto, and adult audiences. While social media platforms like Instagram, SnapChat, TikTok, and Twitch became conduits for mainstream business-to-creator and P2P value transfer, the popularity of user-generated porn sites like OnlyFans erupted. Recent annualized data released by OnlyFans revealed that the number of creators on the platform increased 34% in 2021, reaching 2.16 million. The number of OnlyFans users also jumped 128% to 188 million in 2021.
Not to be overlooked, is hyper-growth in the less glamorous ‘gig economy,’ which expanded by 33% in 2020. During the pandemic, working class American flocked to platforms like Uber, Lyft, Upwork, Fiver, and other digital channels to supplement their diminished incomes. Further expanding the digital fraud attack surface were generous pandemic relief and unemployment benefits packages issued by governments to people all over the world.
These stimulus payments and programs gave fraud actors a trove of new public-sector intrusion vectors to target. Most recently, the Pandemic Response Accountability Committee, an oversight body established to track the integrity of CARES Act spending, found that over 69,000 suspicious social security numbers (SSNs) were used to obtain $5.4 billion in COVID-related business loans.
Beyond CARES Act scams, identity theft, carding, authorized push payment (APP) frauds, crypto investment schemes, phishing attacks, and business email compromise (BEC) incidents also metastasized. Despite being three years past the start of the outbreak and authorities lifting restrictions on in-person banking and shopping, lasting shifts in consumer behavior continue to drive cyber-enabled fraud losses even higher.
Over seventy percent of respondents in a survey of fraud in financial services (finserv) conducted last year reported losing at least $500K to fraud last year. Another alarming trend converging with omnipresent digital commerce today is the mainstream accessibility of online fraud tooling to unsophisticated actors on cybercriminal forums today.
While cyber-enabled scams like credit card theft, phishing attacks, and account takeover (ATO) fraud used to be the exclusive domain of tech-savvy hackers, the meteoric rise of the crime-as-a-service (CaaS) economy has significantly lowered barriers to entry for novice thieves. With the perpetually growing inventory of stolen personally identifying information (PII), credit card data, hacking toolkits, webinjects, and hacker-for-hire services being solicited on the dark web and Telegram, online fraud has never been easier to perpetrate.
Beyond the more straight-forward fraud typologies cited above is the explosion of ransomware. A report by the Financial Crimes Enforcement Network (FinCEN) last year identified some $1.2 billion in ransomware payments processed by U.S. financial institutions (FIs) alone in 2021.
The proliferation of online theft and ransomware is not exclusively limited to consumer protection and fraud prevention compliance mandates either. As the pandemic illustrated, cyber-fraud-derived proceeds are inevitably laundered via increasingly complex, multi-platform, and multi-nodal channels.
This dynamic plunges FIs, fintechs, and e-commerce firms further in the crosshairs of anti-money-laundering (AML) regulators and, in the case of ransomware, sanctions enforcement. Amidst growing oversight pressure and enforcement activity targeting fintech, online banking, crypto, and ecommerce providers, a new approach to combatting cyber-enabled financial crime is needed.
The old compliance silos that segregated fraud, traditionally a reactive compliance process, from AML, which is based on preemptive screening and transaction monitoring, has become obsolete. Today, a hybrid approach that combines artificial intelligence (AI) and predictive analytics with fluid, real-time data sharing between cyber-risk, fraud, and AML compliance units has become essential.
Enter the new generation of cyber-financial intelligence (CyFI). This approach fuses cybersecurity, preemptive fraud intelligence, and AML systems into singular compliance and risk-management portal. This integrated cyber-risk and compliance unit seamlessly sources, scans, and correlates data streams from a wide variety of alternative device identifiers, customer account activities, web domain intelligence resources, social media accounts, and other platforms.
In addition to legacy feeds, a well-tuned CyFI program should centralize collection and monitoring of fraud, know your customer (KYC), know your business (KYB), AML, and sanctions risk data from novel vectors like network traffic, social media, and e-commerce listings, for example. CyFI adoption further empowers financial firms, fintechs, and e-commerce companies to transform their historically reactive approach to fraud intervention into an active fraud prevention model.
The following white paper will educate finance industry, fintech, ecommerce, and compliance stakeholders on the rapidly emerging CyFI fraud prevention and AML paradigm, while highlighting modern fraud attack typologies and heightened regulatory concerns.
Introduction
The biggest consequence of the pandemic was its Hubble-scaled magnification of a preexisting and systemic problem in modern finserv – firms don’t know who their customers are. With the rate of bank branch closures doubling during COVID, punctuating a decade-long trend of physical downsizing, and the growing surge in fintech adoption, modern finserv providers no longer physically interact with their customers.
The overwhelming majority of the customer experience today occurs online. Risk management and financial crimes compliance has been slow to adapt, but CyFI consciousness is steadily evolving. The CyFI unit is a transformative approach to finserv compliance pioneered by bank executive Patricia Sullivan, back when she was Standard Chartered’s head of financial crime compliance for Europe and the Americas.
Enter the new generation of cyber-financial intelligence (CyFI) with Resecurity. This approach fuses cybersecurity, preemptive fraud intelligence, and AML systems into a singular compliance and risk-management portal. This integrated cyber-risk and compliance unit seamlessly sources, scans, and correlates data streams from a wide variety of alternative device identifiers, customer account activities, web domain intelligence resources, social media accounts, and other platforms. In addition to legacy feeds, a well-tuned CyFI program should centralize the collection and monitoring of fraud, know your customer (KYC), know your business (KYB), AML, and sanctions risk data from novel vectors like network traffic, social media, and e-commerce listings, for example. CyFI adoption further empowers financial firms, fintechs, and e-commerce companies to transform their historically reactive approach towards fraud intervention into an active fraud prevention model.
The global head of financial crime and compliance business control & oversight for the corporate and investment banks at Deutsche Bank, Patricia Sullivan told Resecurity, “When I was the Americas Head of FCC at SCB I launched a Cyber Financial (CyFI) unit. Not sure if it was the first of its kind, but it might have been, and within Wolfsberg, no one had seen it done before.” In a 2018 Standard Chartered powerpoint presentation, Sullivan defined CyFI as a compliance program that “produces intelligence through the fusion of financial data, cyber threat intelligence, web research, mining of restricted access sites, and much more.” CyFI, as envisioned by Sullivan, focuses on blockchain analytics, dark web threat intelligence, and the investigation into more traditional obfuscation techniques like money mule networks.
In a 2018 Standard Chartered power point presentation, Sullivan defined CyFI as a compliance program that “produces intelligence through the fusion of financial data, cyber threat intelligence, web research, mining of restricted access sites, and much more6.” CyFI, as envisioned by Sullivan, focuses on blockchain analytics, dark web threat intelligence, and investigating more traditional obfuscation techniques like money mule networks.
Mule networks are associated with 90% of cyber-enabled or cyber-dependent crime, according to Interpol 6. Detecting modern money-mule rings are central to the CyFI evolution because, higher-threat “professional money laundering (PML) networks specialise in the transfer of illicit proceeds from criminal acts. Money mules are recruited and managed by mule herders, who provide specialized services to other Organized Crime Groups (OCGs),” according to Standard Chartered.
The proliferation of online mules also highlights the systemic KYC dysfunction noted above. When an AML investigation officer probes a suspicious activity alert (SAR) generated by bank or fintech transaction monitoring systems (TMS) and submits a request for information (RFI) to the branch or onboarding department for more details about the customer’s odd account activity, they ask a standard series of questions.
What is the client’s source of funds? What is the purpose of the activity? How is the customer related to the beneficiary?
In the age of digital-first finserv, firms must email or call accountholders to obtain the requested information. Absent customer outreach, only 12% of firms today can fulfill requests submitted by AML teams, according to recent research from regtech specialists Refine Intelligence.
This means 88% of firms will have no idea who their customers really are unless their personnel manually conduct more persistent and time-consuming due diligence. Obtaining accurate information in this context also depends on the legitimate nature of the customer’s account activity. Even more absurd, are Refine’s findings that 73% of RFIs target ordinary consumers, while the other 27% seek more information on businesses.
Obviously, business accounts are more likely to have more complex profiles, given their larger transaction volumes, counterparty relationships, and multi-jurisdictional supply chains and customer bases. In short, business accounts are much more suitable for financial criminals, cyber-enabled and otherwise. These are just a couple of key reasons why CyFI compliance transformation has become so imperative.
While Resecurity has expanded the CyFI coverage area to monitor attacks stemming from malicious bot activity, bank malware, and rapidly emerging threats like authorized push payment (APP) fraud, the cyber-enabled PML synergies cited by Sullivan are more crucial than ever in the post-pandemic era.
Compounding oversight risks for financial institutions (FIs) and fintechs, is an unprecedented, war-time sanctions landscape that has aggressively targeted malign foreign GOV-connected funding streams, cybercriminal gangs, and illegal crypto exchanges.
Takeaways From Recent CyFI-Related Sanctions
The most recent actions highlighting the nexus between cybercrime and wartime sanctions are the joint-U.S. and UK designations against seven members of the Trickbot syndicate, which gained notoriety for its online banking malware. Trickbot’s trojan viruses have “infected millions of victim computers worldwide, including those of U.S. businesses, and individual victims,” according to the U.S. Treasury. The Treasury’s press announcement also noted that “current members of the Trickbot Group are associated with Intelligence Services8.”
Also noteworthy is the January arrest of Anatoly Legkodymov, the founder and majority owner of Bizlato, an allegedly criminal crypto-exchange. Registered in Hong Kong, Bizlato stands accused of facilitating over $700 million worth of crypto transactions for various darknet markets and ransomware groups, according to the Department of Justice press release heralding Legkodymov’s arrest.
The DOJ also said, “Bitzlato’s largest counterparty in cryptocurrency transactions was Hydra Market (Hydra), an anonymous, illicit online marketplace for narcotics, stolen financial information, fraudulent identification documents, and money laundering services that was the largest and longest running darknet market in the world.”
At the same time, FinCEN designated Bizlato as a “primary money laundering concern in connection with illicit finance.” FinCEN also accused Bizlato of “facilitating illicit transactions for ransomware actors, including Conti, a Ransomware-as-a-Service group.”
These two recent examples further illustrate why the integration of cyber, fraud, and last-hop AML risk management has become crucial for finserv compliance organizations. Overall, some 6.7% of global GDP, or $5.8 trillion, was laundered annually in 2018, according to John Cusack, the former chair of the Wolfsberg Group, a supernational association of the world’s 13 largest banks, which helps shape and inform global AML standards.
Most of these illicit funds are derived from kleptocracy and ‘washed’ with the help of PML organizations and networks via a complex constellation of white-collar specialists, offshore shell companies, trusts, nominees, and anonymous real estate transactions. Granted, PML-cycled funds largely move electronically via cross-border wire transfers, but that does not make these financial crimes cyber-enabled in the technical sense.
More relevant to cyber-derived illicit finance is the modernization of transnational organized crime, which collectively generated $2.4 trillion worth of illicit proceeds in 2018, according to Cusack’s estimates. Today, organized crime has increasingly migrated online to perpetrate fraud, sell drugs, recruit money mules, operate online gambling businesses, and traffic sex slaves.
Hyperconvergence of Malign Cyber-Financial Ecosystems
OCGs’ digital migration has created a new era of fluid and cooperative cyber-enabled PML networks, spanning crypto to mobile payment apps, ecommerce transactions, online gambling, creator payment terminals, centralized virtual currencies, alternative lenders, sham companies, and cross-border bank wires. This phenomenon can best be described as a hyperconvergence of malign cyber-financial ecosystems.
Given the general traceability of blockchain transactions, the lower hanging fruit in this illicit financial swamp is crypto. This asset class registered a record-high $20.6 billion worth of criminal transaction flows last year, according to recent research from blockchain forensics firm Chainalysis. As Cusack’s projections illustrate, these malign funding streams are a veritable rounding error in the global laundromat but have received significantly more scrutiny from international financial crime regulators nevertheless.
Chainalysis did note in their report, however, that this figure is a “lower bound estimate” and that they are still uncovering more of last year’s illicit crypto addresses. The company also said their data doesn’t capture “proceeds from non-crypto native crime (e.g. conventional drug trafficking involving cryptocurrency as a mode of payment).” Chainalysis also found that the largest sources of suspected illicit crypto transactions originated from sanctions evasion and various scams, respectively.
In fact, 43% of 2022’s illicit crypto transaction volume came from activity associated with entities that has been sanctioned by the Office of Foreign Asset Control, according to Chainalysis. The crypto exchange Garantex accounted for the bulk of sanctions-related transactions last year. Other notable crypto entities sanctioned last year were Hydra and the mixer service, Tornado Cash.
With the rise of decentralized finance (DeFI) platforms, 2022 was also the most significant year for crypto hacking, as threat actors primarily linked to North Korea, collectively stole some $3.8 billion from various platforms. The majority of hacked DeFI proceeds were laundered through mixers like Tornado Cash, decentralized exchanges, and esoteric crypto-lending contracts like ‘flash loans.’
While cyber-enabled actors generally lack the white-collar-savvy and institutional relationships unique to klepto-scale PML operators, the global Cambrian explosion of money laundering service providers on cybercriminal forums has amplified payment-flow complexities for investigators.
Granted, previous cyber-enabled laundering operations like BTC-e and QQAAZZ were particularly noteworthy in scale and sophistication, washing billions of dollars of criminal and klepto-derived crypto via dozens of offshore companies and bank accounts in the case of the former.
QQAAZZ, a syndicate that offered laundering services to cybercriminals, used false identities to register fake businesses offshore and leveraged Asian bank accounts as ‘drops’ to move tens of millions worth of illicit-origin crypto and fiat. The QQAAZZ gang advertised it services on notorious cybercrime forums like Mazafaka and Verified. But the rackets above have typically been the exception, not the rule.
To be fair, however, the war-time sanctions environment has directly amplified the CyFI klepto-risk landscape, as many notable actors initiated a wave of crypto liquidations in the United Arab Emirates (UAE), following the outbreak of fighting in Ukraine. Regardless, there are political and jurisdictional nuances that have largely immunized the UAE from Western diplomatic reprisals and sanctions enforcement, given how essential the country has become to global finance.
More pertinent to FI’s risk exposures is heightened cooperation between transnational illicit cyber-financial networks that occurred during the pandemic. This deviant symbiosis has made laundering and cash-out services more accessible than ever to modern-day threat actors. The net result has been the establishment of a full-fledged money-laundering-as-a-service (MLaaS) industry that leverages both virtual asset and fiat transaction rails.
Growing Money Laundering and Muling Vectors
In today’s hyper-connected black market, consider that carders and ransomware actors can use human trafficking networks, which diversified more aggressively into cyber-pimping their victims on OnlyFans and cam model sites during the pandemic, as laundering and cash-out terminals, as one example.
Only Fans
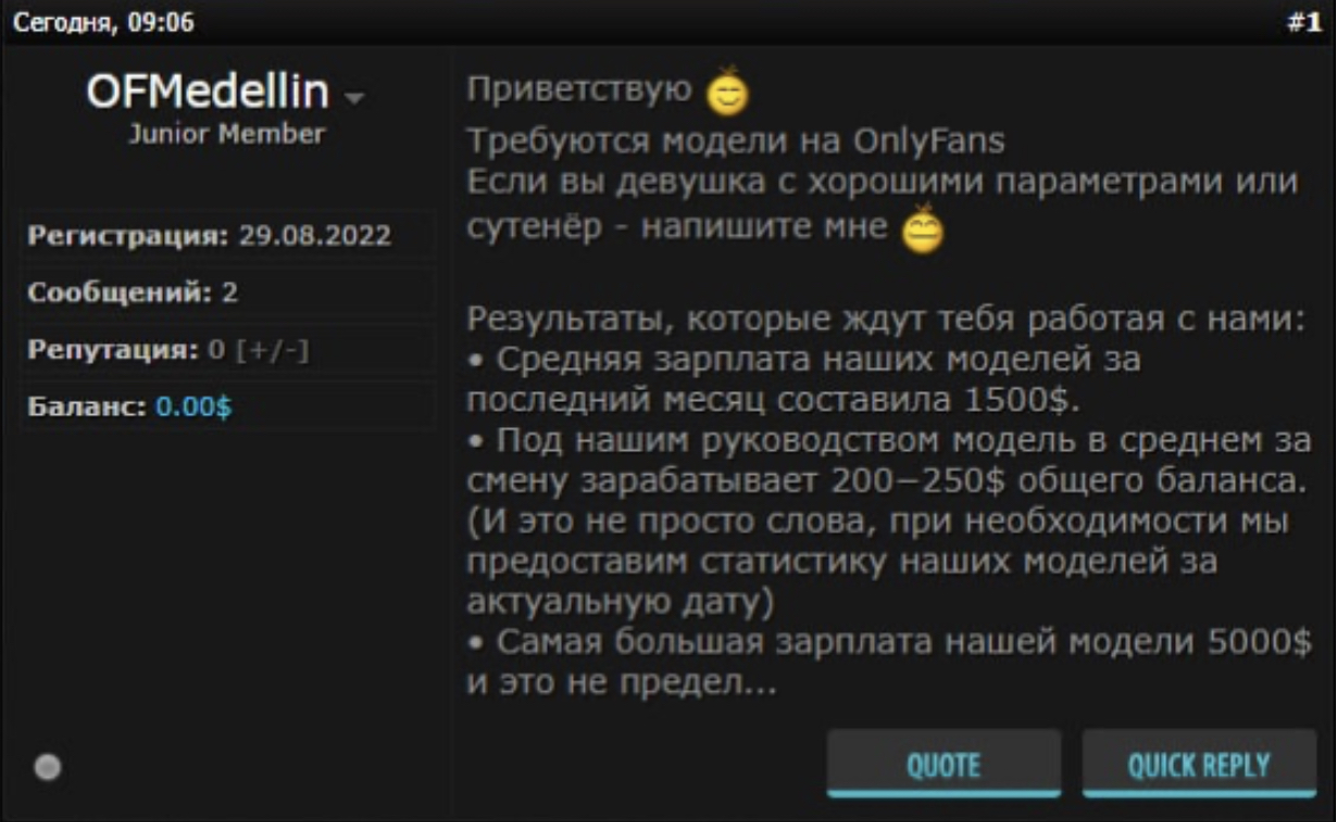
In the above post from carding forum Crdclub.su, the actor ‘OFMedellin’ writes: “Models Wanted on OnlyFans. If you are a girl with a high follower count or a pimp- write to me. Results that await you if you work with us: The average salary of our models for the last month was $1,500.”
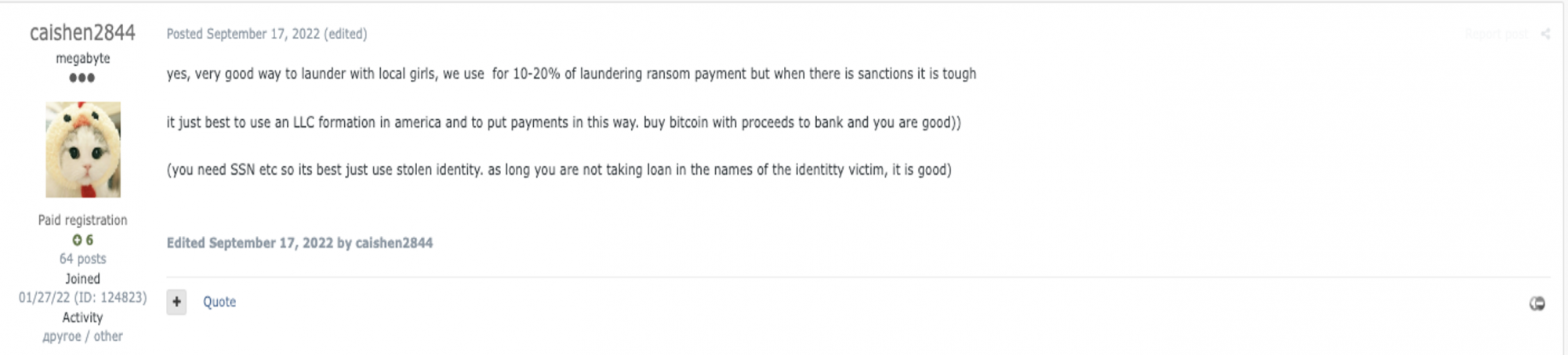
In the above post from cybercriminal forum Exploit.in, threat actor ‘Caishen2844’ solicits an OnlyFans laundering service that enlists local girls that pays out 10-20% of ransom payments to co-opted models. This threat actor also advises moving the money through American LLCs registered with stolen SSNs and other PII. OnlyFans is particularly interesting due to the amount of value transfer being processed on the platform, which acquiring banks would classify as ‘high-risk,’ given its adult-oriented business model.
Recent financial data released by the company revealed that OnlyFans creators $3.86 billion in 2021, a 115% jump over the previous year4. It remains to be seen how much the Ukraine war impacted value transfer on the platform, given the rise of laundering service providers targeting models and pimps there. The broader trend illustrated by the OnlyFans malign value transfer vectors highlighted above is that money mule recruitment has never been easier.
Today, mule herders can easily target a broad audience of unwitting or indifferent young people, disenfranchised by war-time economic conditions, on video-game streaming sites like Twitch or popular social and messaging apps like SnapChat, and Telegram Telegram. Last year, Turkish police arrested 40 people in a scheme where credit card fraudsters used Twitch streamers with low follower counts to launder roughly $10 million.
In a notorious Twitch scam, fraudsters used to stolen cards to purchase in-platform currency, called Bits, to streamers who then refunded scammers real money at a rate of 70-80% of the virtual currency transferred to them. As for Telegram, this app has become a key cog in online mule recruitment for the specific purpose of check fraud. One of the oldest financial crime typologies in history, Telegram has propelled the rise of check fraud, with this crime increasing 84% in 2022 over the previous year, according to FinCEN.
Telegram ‘Walkers’
The fifth most cited suspicious activity report (SAR) category by banks and credit unions in 2021, check fraud assumed the top spot for SAR production last year. Check fraud brokers have been using Telegram to recruit mules, which they call ‘walkers,’ to physically deposit stolen and altered checks at bank branches.
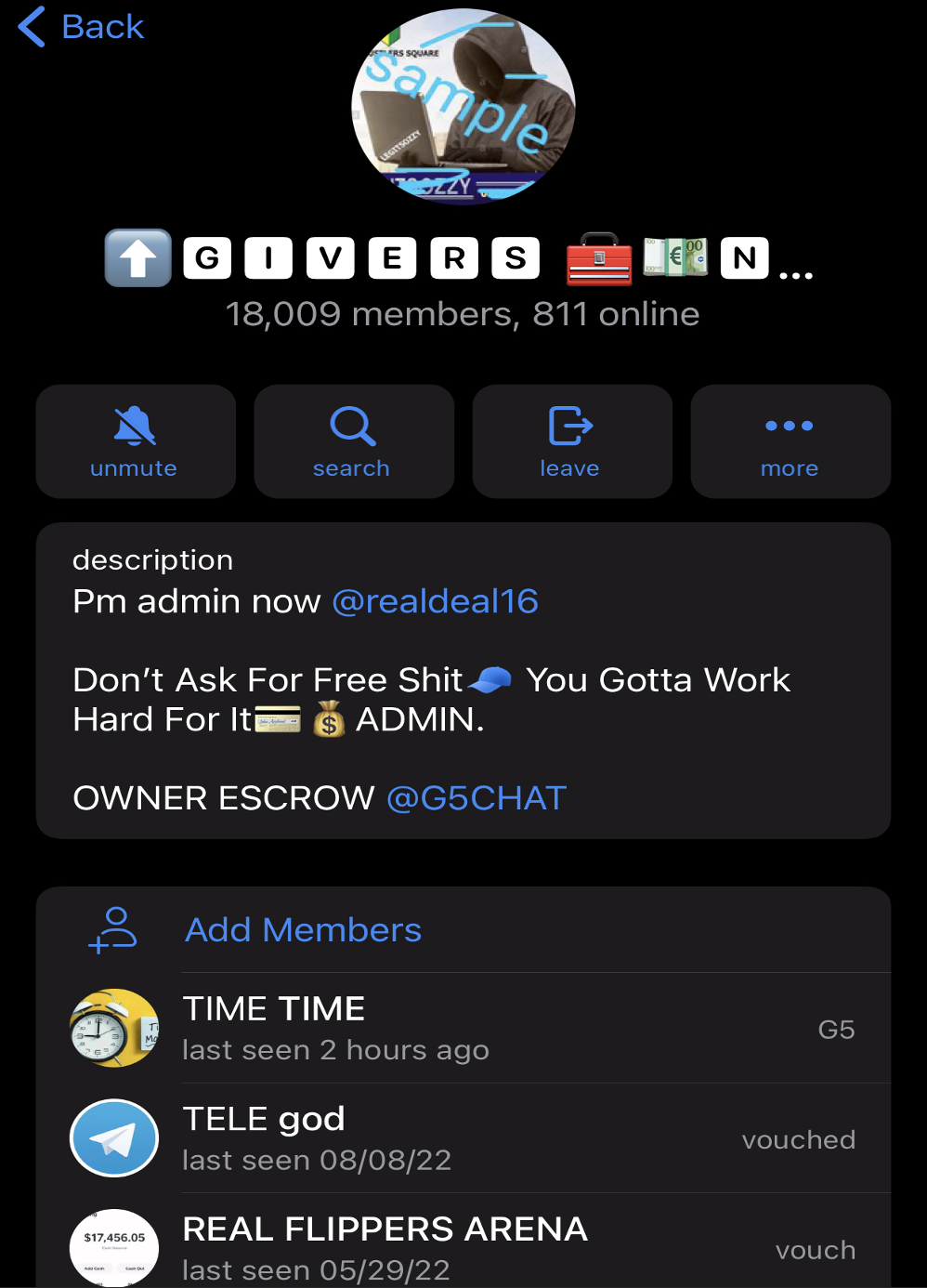
The above screenshot, shows one prominent fraud-focused Telegram channel called “Wall Givers Never Lack”, has over 18,000 members. This channel frequently posts advertisements for “check deposit sauce,” with accompanying photos of bank deposit receipts. The channel admin, ‘@realdeal16’, has disabled members’ ability to screencap photos and posts within the chat.
Resecurity identified multiple underground vendors providing cash-out services (via network of money mules) from stolen VCC, banking, e-commerce and cryptocurrency exchange accounts.
“Verta” is one such vendor who specializes in processing funds stolen via Business Email Compromise (BEC) scams and other fraudulent transfers. This threat actor also charges a relatively high 50% commission for their cash-out services. The Verta service is accessible via Telegram and Jabber, following the initial vetting of cybercriminal customers. This vetting includes information about threat actors’ sources of stolen funds.

The minimum amount of funds Verta will process starts at $15,000 (for personal accounts) and $75,000 (for business). Typically, cybercriminal cash-out providers eschew processing lower transaction amounts because they do not justify their risk.
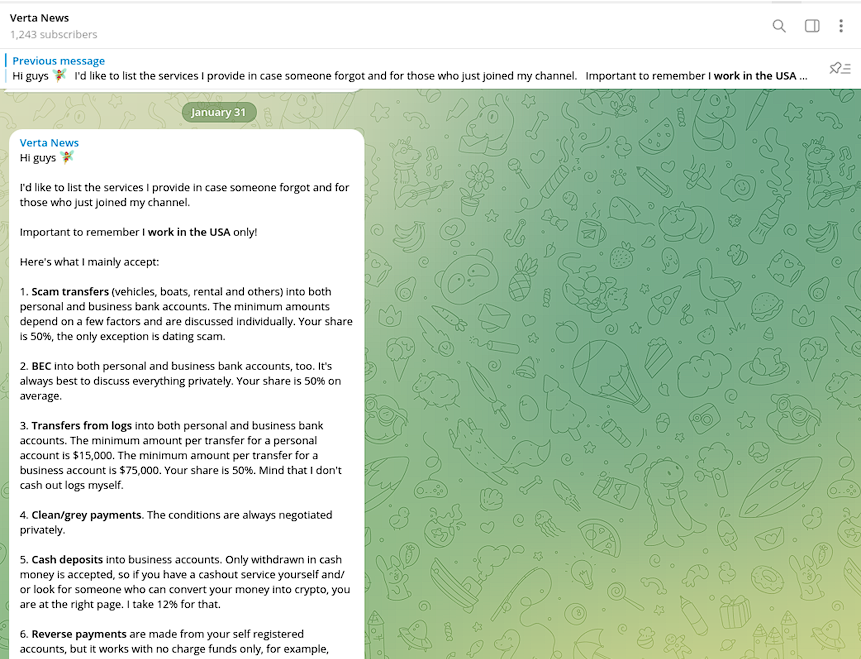
Notably, the commission on processing stolen funds from VCC is significantly higher compared to ACH/WIRE transfers.
Resecurity also identified a group of trending cash-out vendors that charge commissions based on the exact BIN of the card and brand of gift card. The commission spread depends on the popularity of the service/bank, the complexity of cash-out process, including the tactics the launderers will have to deploy to successfully circumvent a payment platform’s anti-fraud filters.
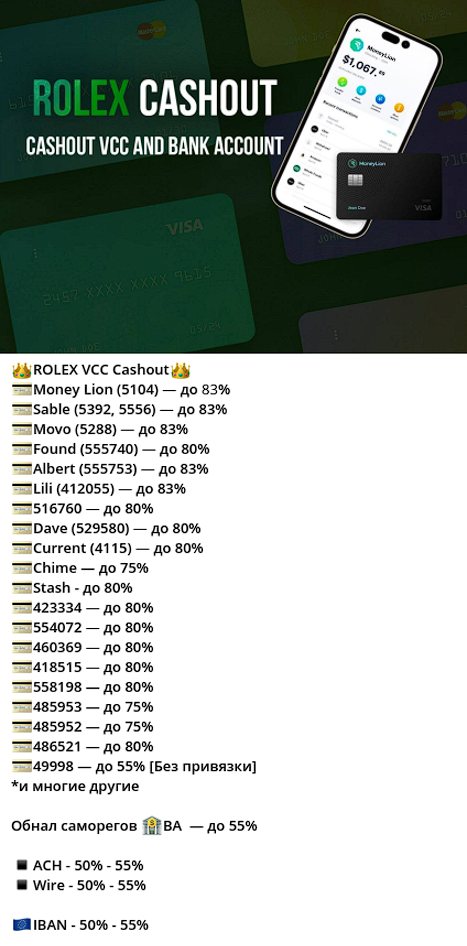
Digital Ads
Another emerging attack vector for illicit cash-outs is digital advertising, a sector that could be exploited to launder $100 billion this year, based on global ad fraud estimates. Ad fraud researchers like Augustine Fou have even referred to digital advertising as “the mother of all money laundries.”
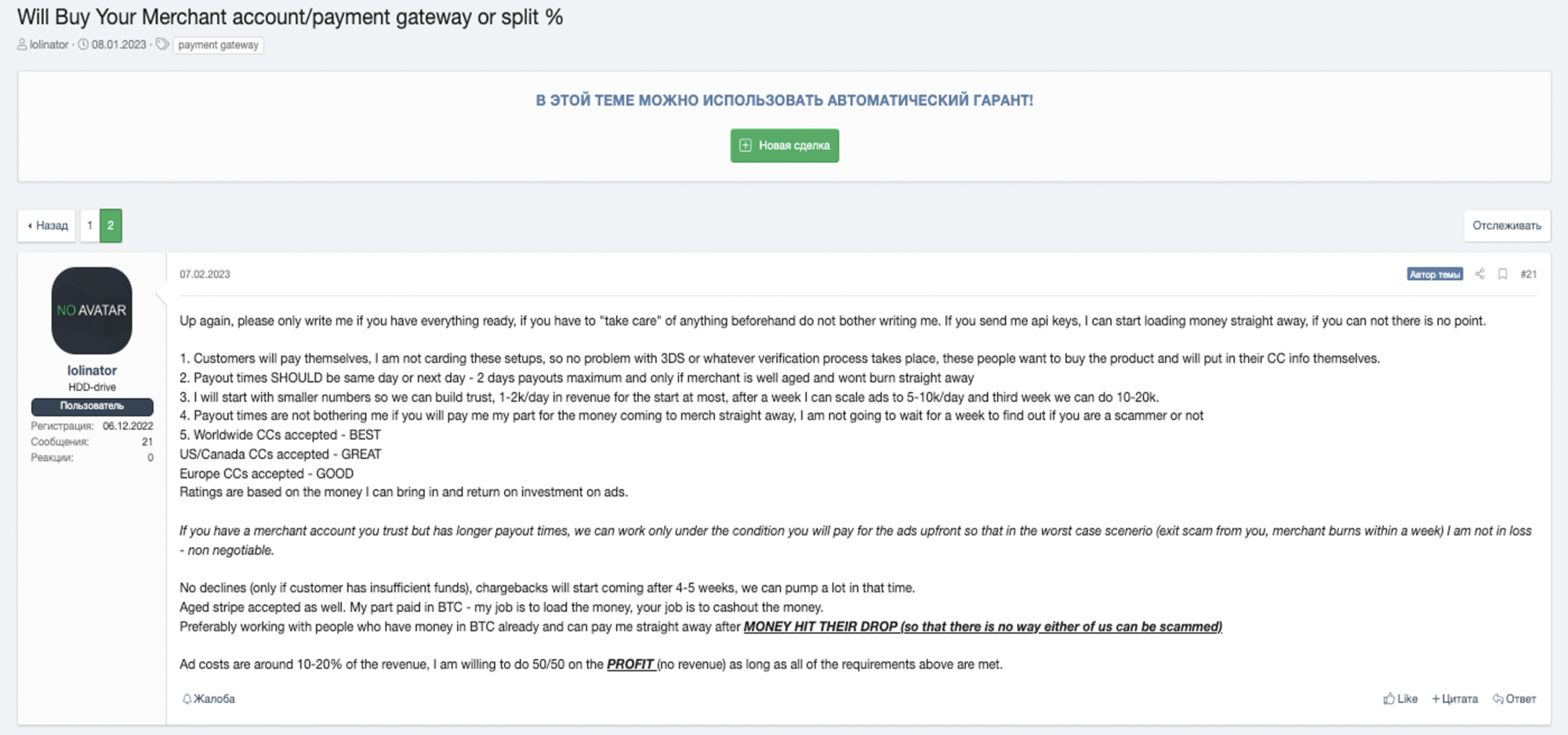
Highlighting laundering risk exposures in the digital advertising sector is the above XSS cybercriminal forum thread from January of this year. In this thread, threat actor ‘lolinator’ posts a solicitation that offers to “Buy Your Merchant account/payment gateway or split %.”
To process normal online card-not-present (CNP) transactions, scammers must have an established merchant payment gateway account. This appears to be a fraud where a digital ad scammer co-opts a carder’s merchant terminal to process scam advertising affiliate payments, before legitimate card holders report fraud.
When victims report theft, this forces a chargeback where affiliate partners or other types of digital ad space sellers must refund the money. The specific type of affiliate scam that is likely being perpetrated here is “transaction fraud.”
In this scheme, “scammers use the stolen credit card information or payment account to create a fraudulent transaction on an affiliate partner’s account,” according to web hosting firm Hostinger. “While this type of fraud harms affiliate marketers and customers whose data was stolen, it also impacts companies. The company must pay the commission for sales generated from affiliate links and fees when affiliates file a chargeback for the fraud.”
The affiliate nature of Lolinator’s fraud is more than likely the typology being solicited, given this requirement he specifies near the end of his post:
1.“No declines (only if customer has insufficient funds), chargebacks will start coming after 4-5 weeks, we can pump a lot in that time.”
Below are some other interesting conditions specified by this threat actor. For institutional CyFI sleuths these merchant specifications are helpful because they can use them as a guide for suspicious transaction markers to investigate further when dealing with unestablished digital advertising clientele.
“2. Payout times SHOULD be same day or next day - 2 days payouts maximum and only if merchant is well aged and wont burn straight away
3. I will start with smaller numbers so we can build trust, 1-2k/day in revenue for the start at most, after a week I can scale ads to 5-10k/day and third week we can do 10-20k.
5. Worldwide CCs accepted - BEST
US/Canada CCs accepted - GREAT
Europe CCs accepted – GOOD
Ratings are based on the money I can bring in and return on investment on ads.”
The threat actor also expresses a payment in bitcoin, highlighting an illicit crypto financing vector not captured by Chainalysis estimates:
“Aged stripe accepted as well. My part paid in BTC - my job is to load the money, your job is to cashout the money.
Preferably working with people who have money in BTC already and can pay me straight away after MONEY HIT THEIR DROP (so that there is no way either of us can be scammed)”
Another interesting dimension to this fraud is the ‘laundering fee’ involved in digital ad buys: “Ad costs are around 10-20% of the revenue.” This is the same laundering fee advertised in one of the OnlyFans cash-out scams above. Lolinator also says he is “willing to do 50/50 on the PROFIT (no revenue) as long as all of the requirements above are met.”
On the AML side, the financial crime being perpetrated post-fraud is transaction laundering, where a “fraudulent company processes payment card transactions through the merchant account of a real business.” TL is generally favored by illegal online gambling operators and rogue Internet pharmacies, according to the Electronic Transactions Association.
The ETA also estimates that “50%-70% of online sales for illicit drugs, counterfeit goods, and unlawful adult content involve some form of transaction laundering25.” But digital advertising may overtake these other sectors, given the opacity of the ecosystem.
AML Implications and SAR Stats
Focusing more on the macro side of cybercrime, the total cost of the black hat hacking industry to the global economy is projected to grow from $8 trillion this year to $10.5 trillion by 2025. But it’s unclear how much of the losses will amount to take-home pay for threat actors, as these projections must factor incident response, remediation, operational disruption, and potential legal costs into their models.
With roughly half of all cyberattacks targeting the U.S., however, it's inevitable that a significant portion of cybercriminal proceeds will transit through the SWIFT interbank payment system at some point. As the premiere financial terminal for clearing dollar transactions, SWIFT accounts for 90% of all cross-border flows. This places the lion’s share of cybercriminal-derived proceeds within the purview of American financial crime regulators and enforcement agencies.
Financial, payments, and e-commerce entities subject to AML and sanctions regulations must take note, particularly following the enforcement actions against Trickbot and Bizlato. FinCEN, for its part, has been mandating the following data inputs on suspicious activity reports (SARs) involving cyber-events since 2016: description and magnitude of the event; known or suspected time, location, and signatures of the event; indicators of compromise; relevant IP addresses and their timestamps, device identifiers, attack methods used; and other identifiers.
But today the Treasury’s financial intelligence unit is more overwhelmed than ever before with cyber-enabled reports of suspicious and fraud-derived activity. Consider that since FinCEN started mandating cyber-event-related SARs in 2016, the volume of these reports metastasized from just over 2,063 in 2018 to 53,774 in 2022, according to data provided to Resecurity by Jim Richards, the operator of compliance advisory RegTech Consulting and a former Wells Fargo executive. Year-over-year, 2022 cyber-event-related SARs increased by nearly 12%, according to the data.
The majority of these cyber-events are those that target finserv customers, as opposed to the institution itself. Fueling the explosive rise in cyber-event-related SARs is the self-perpetuating and regenerating data-theft economy. Additionally, as noted above, the resurgence of check fraud and the laundering schemes involving adult and game-streaming platforms further illustrate how CyFI risks have been further compounded by the accessibility of money mules across the digital spectrum.
Key Fraud Trends to Watch in 2023
The era of always-on connectivity has created a parallel cybercriminal CaaS ecosystem of stolen data vendors, initial access brokers, rogue mobile app developers, and a growing customer base. With data breaches and the records exposed therein increasing every year, fraudsters have an ever-expanding inventory of PII to operationalize attacks on consumers and businesses.
For example, the 22 billion records exposed in over 4,145 data breaches in 2021, is projected to grow by as much as 5% for 2022 after all the data is analyzed.
This growing, continuously replenishing, and affordable inventory of stolen data empowers cybercriminals to relentlessly launch attacks, ranging from phishing, ATO, synthetic identity (SID), brand impersonation, authorized push payment (APP), bot-scripted, ransomware, and various e-commerce frauds. The problem deteriorated to the point that the UK is set to reclassify fraud as a threat to national security this year.
In the U.S., the Federal Trade Commission found that young people between the ages of 20 and 29 accounted for 41% of all fraud victims, more than any other age demographic. Some of the top cybercrime trends observed by Resecurity for the upcoming year include the continued proliferation of APP fraud and increasing sophistication of SID frauds as threat actors escalate the targeting of direct deposit and merchant accounts.
App Fraud
APP fraud is of particular concern and the fastest growing financial crime trend. This typology now represents 75% of all online banking payments fraud, according to research published last year. Unlike ATO fraud, where cybercriminals use stolen credentials to access accounts from new or previously unrecognized devices, APP fraud is an attack method where fraudsters use social engineering and domain spoofing to convince victims to willfully send them money electronically.
In more sophisticated higher-dollar APP cons, like BEC fraud, scammers may infect victim devices and surveil communications between executives or counterparties involved in transactions. This way, when scammer operationalize their schemes, they can sound more credible when requesting fund transfers from victims. APP fraud has manifested prominently in BEC swindles, romance scams, and various ‘pig butchering’ attacks. From 2016-2021, BEC fraudsters stole some $43 billion from businesses, according to the Federal Bureau of Investigation.
Romance scams, where scammers target desperate people on online dating sites and convince them to wire money or send cryptocurrency netted $547 million from victims in 2021.
Meanwhile, pig butchering scams, where scammers lure victims into wiring large sums of money into fraudulent crypto or foreign exchange investment vehicles, and which sometimes overlap with romance frauds, duped victims into wiring $429 million in 2021.
Many of these pig-butchering frauds are hatched from “industrial-scale scam centers” in Southeast Asia, where organized crime rings force labor trafficking victims to work grueling hours scamming foreigners over the phone. Highlighting the professional nature of these frauds, a recent probe by the Observer and The Bureau of Investigative Journalism, a non-profit, identified “168 UK companies accused of running fraudulent cryptocurrency or foreign exchange trading schemes, around half of which are likely to be linked to pig-butchering scams”.
The investigation also found that “many of these firms are linked through domain registrations and while the vast majority of company directors are resident in China, details about the real owners are scant due to loopholes in the Companies House registration system.” These findings illustrate why the automated integration, analysis, and risk decisioning for business accountholder web domain registration data are foundational to an effective CyFI program.
Merchant and Government Impersonators
Another rising APP fraud typology involve merchant scams and government impersonators. According to the FTC, “government and business impersonation scams rose sharply at the beginning of the COVID-19 pandemic.” From the beginning of 2017 through mid-last year, the FTC received 2.5 million reports of these kinds of frauds, which duped consumers out of over $2 billion.
To perpetrate these frauds, threat actors create impersonator websites to sell counterfeit products, fulfill orders with stolen merchandise, or process payments without delivering any products. From the vantage point of FIs’ fraud detection systems, APP fraud attack vectors have been particularly difficult to detect and prevent because money transfers originate from and are authorized by ‘trusted’ devices that have already been fingerprinted.
The trusted and authorized nature of these fraudulent transfers makes them virtually impossible to reverse, as the window to actively respond to these scams closes rapidly.
In the banking and ecommerce sectors, the most sophisticated threat that Resecurity has encountered is the specialist ‘InTheBox’ mobile malware forum. However, the attack vector facilitated by webinjects sold on this forum is ATO fraud.
Beyond outright fraud, another significant brand impersonation typology is the counterfeit industry. Predominantly based out of mainland China, professional counterfeiters cost the global economy $500 billion a year, according to the U.S. Chamber of Commerce. U.S. consumers represent over one fifth of the market for the consumption of fake products.
According to a 2020 bulletin from the Department of Homeland Security, counterfeit “goods trafficked to American consumers by ecommerce platforms and online third-party marketplaces threaten public health and safety, as well as national security.”
Compounding the counterfeiting attack surface, are reports that multiple actors are evolving past being a transshipment hub for fake Chinese imitation products and itself becoming major producer of knockoff luxury goods. This trend could obviously place negligent ecommerce sellers at greater risk of sanctions enforcement.
Beyond, ecommerce payment gateways, APP fraudsters have also been using P2P money transfer apps as channels to siphon money from victims. But as recent controversies involving fraudulent Zelle transfers and tenacious lobbying efforts from the American Bankers’ Association forbode, consumers will continue to bear the ultimate burden of frauds perpetrated via P2P apps at a minimum.
SID Fraud
Also concerning is the advanced persistence and deep fake evolution of SID fraudsters. SID scams entail threat actors creating entirely fictitious identities assembled from a variety of real PII and false credentials to open bank accounts. In fact, SID fraud is becoming an increasingly integral staging technique in the furtherance of various APP frauds described above. When SID frauds linked to credit card scams are added to losses with those affecting regular direct deposit accounts (DDAs) at banks, total SID losses approached $4.88 billion last year, according to identity verification specialists Socure.
Once predominantly focused on defrauding FIs via credit account ‘bust outs,’ that net fraudsters $13K on average, changes in consumer behavior effected by the pandemic have led to more merchants and consumers being targeted by SID scammers. Ecommerce merchants, for example, are projected to lose $48 billion to fraud this year, up from 16% from 2022. While a meaningful portion of these scams will feature traditional CNP and ATO-based attacks, scammers are increasingly weaponizing breached data on the dark web to create synthetic identities for the purpose of defrauding merchants.
Merchants also have more difficulty detecting synthetic frauds since no legitimate consumer is victimized, which eliminates the filing of fraud reports by defrauded cardholders. On the flip side, some threat actors may engage in ‘double dipping,’ where they use synthetic accounts to buy online products, then claim their orders were never received or defective. Fraudsters then file chargebacks with their issuing banks, which merchants are ultimately obligated to return to FIs.
As the brand impersonation scams discussed in the previous section noted, consumers are also being targeted by SID scammers. A significant portion of these consumer-focused frauds are being perpetrated by Zelle and other P2P apps, created with funding from SID-opened DDA bank accounts. In fact, 18 million, or 7% of Americans were defrauded via P2P apps in 2020, the last year for which numbers are available.
While data on the segment of these P2P frauds that involved synthetic identities is scant, it’s logical to assume that scammers were likely impersonating online sellers or just running scam shops. To wit, there is a growing risk that merchant accounts are being created with synthetic IDs. Complicating matters further is the secondary market for online merchant payment gateways.
Mike Cook, an executive at Socure who coined the term ‘synthetic identity fraud,’ told Resecurity, “I've been concerned that merchant accounts are being set up under synthetic identities for years, but have never been able to gain the attention of acquirers to test the theory. We’ve seen increased attacks on deposit accounts by synthetic identities, especially following COVID.”
Another emerging weapon in SID fraudsters arsenals are deep fake technologies. Neobanks and fintechs, which do not require in-branch customer verification, are particularly at risk. Beyond fake photos, AI-generated video is rapidly evolving to the point that fictious digital avatars can be deployed by scammers to successfully pass financial firms’ digital onboarding controls.
While data from last year estimates that banks and fintechs are able to detect 1,500 deep-fake spoofing attacks a month, these frauds are typically recognized by humans after firms have been defrauded. Additionally, the deep fake attacks noted above largely entailed generative AI impersonating real people. As China’s recent deployment of entirely deep-fake-generated news broadcasters to disseminate disinformation on social media forbodes, SID fraudsters will soon have commercial access to attack kits with this level of sophistication36.
Regulatory Risk Landscape for Financial Firms
When it comes to regulatory intervention for cyber-related fraud, money laundering, terrorism financing (TF), and sanctions, the overwhelming majority of firms targeted by U.S. authorities have been crypto firms. Yet some banks and fintechs have recently been fined for CyFI-relevant violations.
The most egregious CyFI-related enforcement action in history was the $578 million fine issued by Australian regulator AUSTRAC against Westpac in 2020 for, among other things, facilitating over 23-million transactions between a network of pedophiles.
Specifically, Westpac-banked sex offenders were buying and selling access to live-stream child sexual abuse content being disseminated from the Philippines. Presumably, the live stream services being accessed were being hosted on the dark web.
Other CyFI-relevant enforcement actions taken by global regulators against FIs and non-crypto fintechs have been largely tame Last year, the UAE fined fintech company Wise $360K for breaching the country’s AML controls last year. In 2021, German authorities fined neobank N26 €4.25 million for weak AML safeguards.
But the tide for mainstream FIs may be changing given the recent $2.3 million fine issued by the Federal Reserve Board on Popular Bank for processing six applications linked to PPP fraud during the pandemic. The Fed’s response marks the first fine assessed by a regulator against an FI for enabling any manner of financial crime that could be interpreted as cyber-enabled, as virtually all PPP frauds were.
While these enforcement actions have been relatively minor, the crypto sector has been much more aggressively targeted by authorities. Most notably, the New York Department of Financial Services, fined crypto exchange Coinbase $100 million after the regulator found “significant failures” in the firm’s compliance with the state’s “virtual currency, money transmitter, transaction monitoring, and cybersecurity regulations.”
According to the NYDFS, “these failures made the Coinbase platform vulnerable to serious criminal conduct, including, among other things, examples of fraud, possible money laundering, suspected child sexual abuse material-related activity, and potential narcotics trafficking.” It should be noted that the NYDFS is an exceptionally powerful state regulator, as the mass-concentration of international FIs and finserv firms operating on Wall Street grants the agency sweeping extraterritorial enforcement powers.
Additionally, recent reports in the Wall Street Journal assert that Binance, the largest crypto exchange in the world is ready to settle claims with U.S. regulators regarding various probes, including an AML-related investigation from 2018. Even more foreboding for crypto firms, are reports in Reuters that the recent FTX collapse is bound to give regulators the greenlight to aggressively target them for enforcement.
While the report is largely focused on the Securities & Exchange Commission’s purview, there is no reason to believe that entities like the Consumer Financial Protection Board, FinCEN the DOJ won’t also sharpen their focus on crypto firms when it comes to violations involving fraud and AML. In fact, crypto is being targeted by regulators to the point that certain banks, including blue chip lender Citigroup, are increasingly de-risking their exposure to crypto clients.
Additionally, the report does note that this emerging “enforcement focus will hit a wide range of complex, illiquid products and financial services where less transparent practices pose hidden risk to investors42.” Regardless, the elephant in the room when it comes to CyFI vigilance for the upcoming year is sanctions compliance, particularly as it pertains to designated cyber-enabled entities in China, Russia, Iran, and North Korea.
Cyber-Sanctions, PEPs, and ITAR
Beyond previously sanctioned crypto exchanges and cybercriminal gangs are the most recent OFAC actions targeting seven threat actors linked to Trickbot and ransomware gangs Conti and Ryuk. This means that any FI or fintech who unknowingly banks these individuals or who is coerced into making a ransomware payment to a crypto wallet address linked to these actors could potentially be targeted by OFAC.
The same principle applies for recent sanctions enforcement actions taken against members of Iran’s Revolutionary Guard Corps for their role in malicious ransomware campaigns. Iran and several other countries further compound the cryptocurrency threat landscape as both countries have legalized the use crypto for international trade to bypass Western sanctions.
Also relevant is the expansion of OFAC sanctions against the North Korea-based crypto-hacking gang, Lazarus Group. This threat actor group is believed by U.S. authorities to use proceeds from DeFI hacking and other crypto exploits to help finance North Korea’s nuclear weapons program.
On the more traditional side of financial crime, CyFI-enabled screening for ultimate beneficial ownership (UBO) can be assistive in identifying assets linked to sanctioned kleptocrats and oligarchs from the jurisdictions cited above.
When it comes to sanctions and politically exposed persons (PEPs), however, even the best CyFI tools will encounter difficulties overcoming the European Court of Justice’s recent ruling to close EU member states’ central UBO registries.
A key provision of the EU’s Fourth Anti-Money Laundering Directive (4AMLD), which went into effect in 2017, member states were supposed to created publicly accessible national registries of UBO data for legal entities. But a judge in Luxembourg declared these registries invalid and ordered their closure after citing “privacy concerns” this past December62.
Even before the ECJ’s ruling these UBO registries imposed non-intuitive and “complex registration systems” that limited their accessibility to the public, “in clear breach of EU rules,” according to a 2021 report from financial integrity watchdog Transparency International.
Regardless, next-generation CyFI screening tools may enhance firms’ ability to find the needle in the haystack buried in a vast digital constellation of web intelligence (WEBINT) markers like email addresses, IP markers, device identifiers, social media accounts, and other unique fingerprinting tools to identify threat actors and their proxies.
Not to be overlooked in the regulatory risk outlook is compliance with International Traffic in Arms Regulations (ITAR) in the U.S. According to the U.S. Department of State, the “Directorate of Defense Trade Controls strongly encourages registered exporters, manufacturers, brokers, and others engaged in defense trade, to maintain compliance programs that assist in the monitoring and control of exports and other regulated activities.”
In the backdrop of the war in Ukraine, U.S. arms sales to third countries surged by nearly 50% last year to over $51.9 billion. With no peaceful resolution to the war in sight, firms operating in the defense trade must take special care that the weapons they produce, and export are not diverted to bad actors. Thus, CyFI tools can better equip firms covered by ITAR to accurately verify the integrity of international counterparties with whom they may do business.
Embracing CyFI Transformation
For FIs, fintechs, and e-commerce firms, the modern and unyielding cyber-enabled financial crimewave mandates a risk-appropriate response. Embracing CyFI transformation will entail a dynamic reimagining of organizational financial crime compliance and risk management functions, processes, technologies, and data sources. High-performance AI will be central to this undertaking, leveraging machine learning technologies to authenticate digital identity and business integrity, while also scanning transaction flows to accurately identify anomalous funding streams.
Some AI-based technologies that firms must incorporate into their compliance programs today include: blockchain analytics, device fingerprinting, computer vision, natural language processing, malware detection, link analysis, dark web surveillance, and other cutting-edge tools to parse through terabyte streams of big data and identify bad actors.
At the same time, the antiquated silos segregating AML, fraud, and cybersecurity departments must be dissolved to facilitate the establishment of an integrated authentication, risk management, and customer-monitoring portal.
The key theme here is dynamically and continuously connecting all the dots in the vast and perpetually growing constellation of network traffic, new device registrations, web domain data, malware analyses, customer fund flows, corporate formations, adverse media coverage, and other relevant records.
While CyFI will be more effective in combatting cyber-derived fraud and the spin cycle it spawns, this paradigm still has significant utility for mitigating the risk of more professionally networked white-collar laundering threats. With the number of external banking APIs used by firms projected to double by 2025, CyFI compliance restructuring shouldn’t be prohibitively difficult for most incumbent FIs, given their existing adoption of SaaS technologies.
For digitally native firms achieving CyFI singularity should be even less painless. Beyond the private sector, central banks and other oversight agencies are also reimagining their supervisory technology (SupTech) compliance stacks within CyFI frameworks to better monitor covered firms. With fraud and illicit finance becoming more cyber-enabled, both private and public sector entities must evolve to protect commercial interests and national security.
In order to protect Financial Institutions (FIs) and their customers, Resecurity provides Fraud Prevention and Cyber Threat Intelligence (CTI) solutions. Our team of analysts, financial crimes investigators and ex-law enforcement specialists assist to protect their assets, as well as to stay cyber resilient in today's dynamically changing threat landscape.

