

Intro
DragonForce ransomware has recently been reported to target organizations in Kingdom of Saudi Arabia (KSA). A significant incident involved a data leak from a prominent Riyadh real estate and construction company. This ransomware attack is part of a broader trend of cyber threats facing the region, particularly against critical infrastructure and major corporations. The new incident is an important signal to local law enforcement and the cybersecurity community, as new victims will soon appear in the MENA region. The attack will likely expand beyond the MENA region as their techniques prove effective.

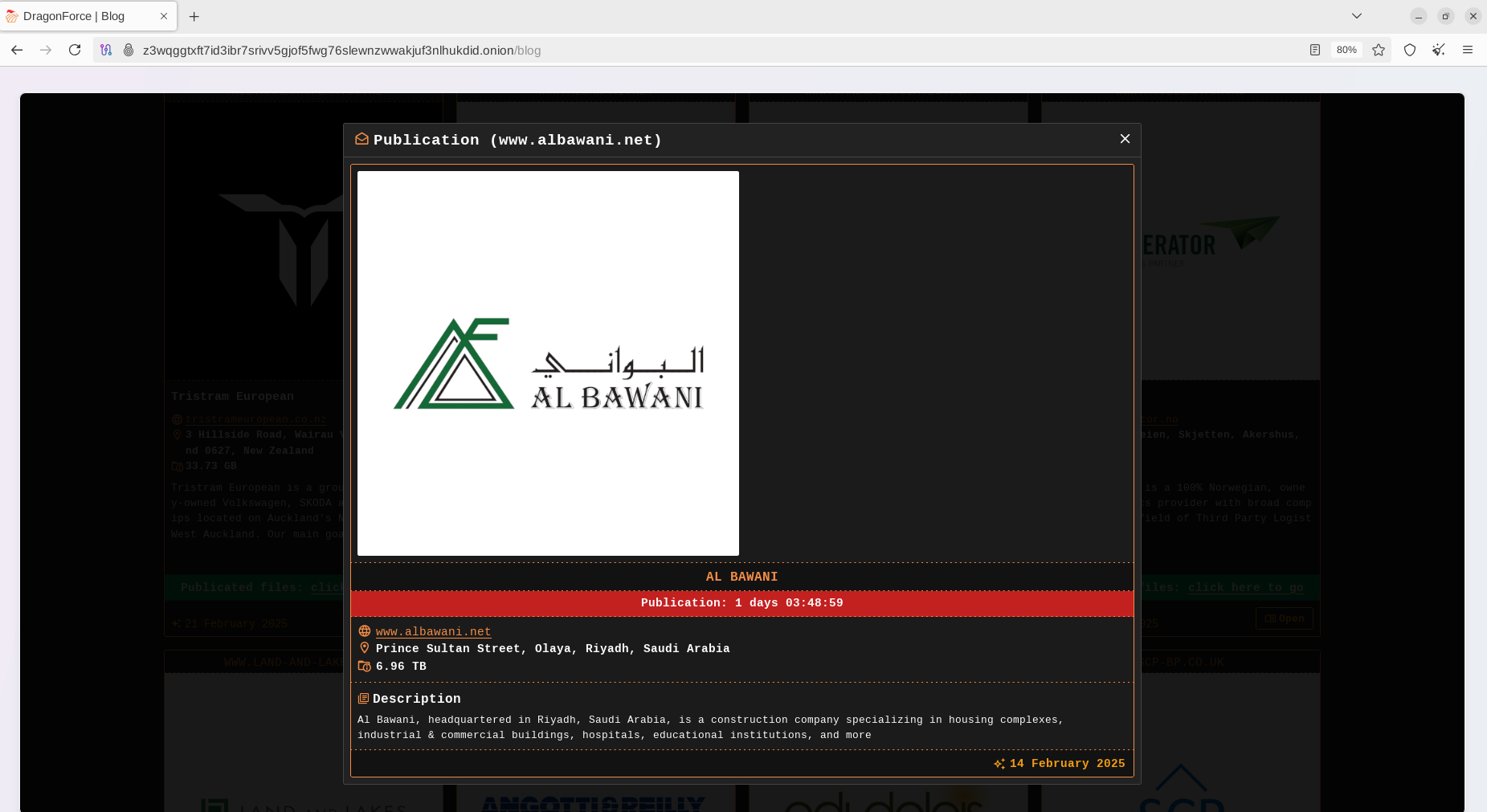
It is the first time the ransomware gang has targeted a large KSA enterprise entity. According to claims made by the actors, the total volume of exfiltrated data exceeds 6 TB. Notably, the target and timing were not chosen randomly. Initially announced on February 14, 2025, DragonForce started to extort the victim to pay to prevent the publication of stolen data. The deadline was set for one day before Ramadan begins on February 28, 2025.
Why did ransomware gangs shift toward the real estate and construction segments in the KSA?
- Construction is one of the main non-oil economic drivers in the KSA, given the emergence of large infrastructure projects with multi-billion-dollar investments.
- Real estate and construction firms often have a large and complex IT infrastructure, with many interconnected systems and a wide range of third-party vendors. This creates a large attack surface for cybercriminals.
- Such organizations also have access to large volumes of sensitive data, including clients' personal information, financial records, and confidential property details.
- This data is highly valuable to cybercriminals. A successful ransomware attack can freeze a construction or real-estate company’s assets and disrupt critical business operations, such as construction projects, property transactions, and rental collections. This can cause significant financial losses and reputational damage.
As soon as the deadline had been reached, DragonForce released the leaked data consisting of over 6 TB of files, which included internal and confidential documents related to the operations and clients of the company. Typically, the group created a dedicated URL for this that was different from the official DLS site.
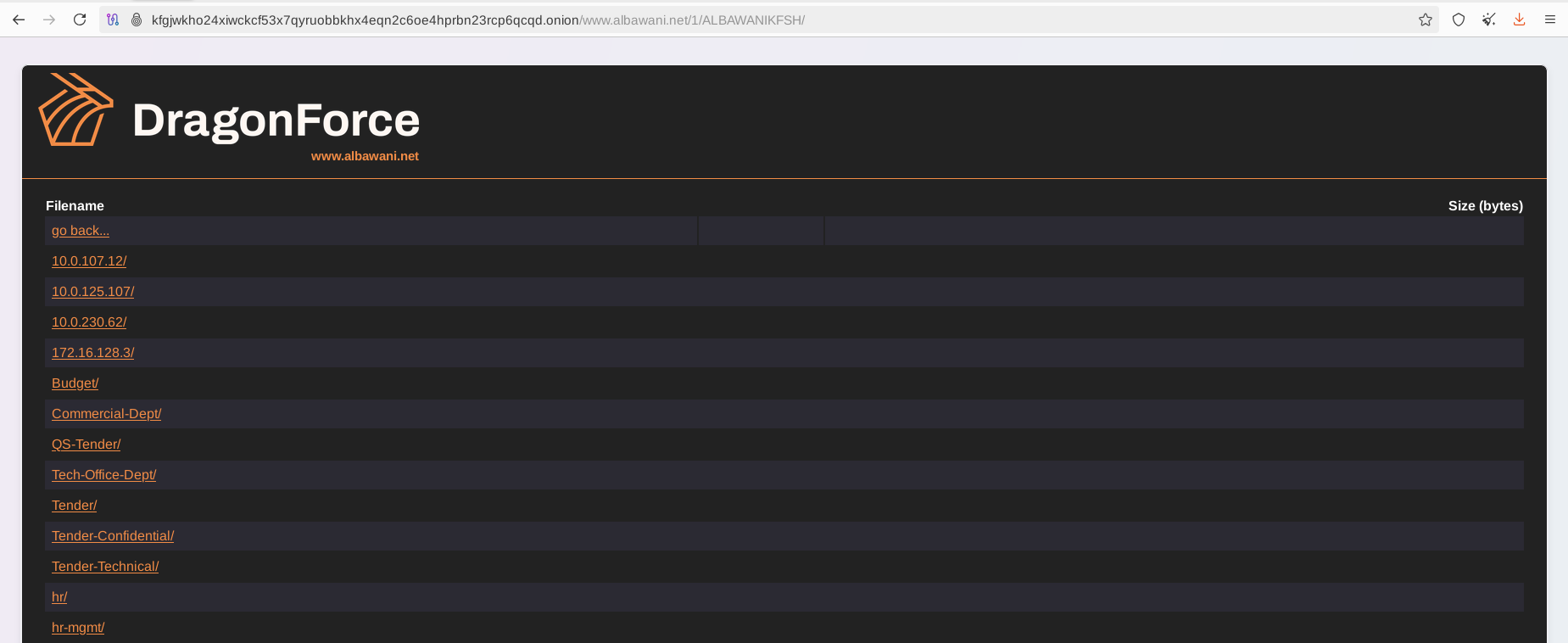
Advanced-Data Leak Site (DLS)
One of the first victims (Heart of Texas Region MHMR Center) was added to their data leak site (DLS) around December 6, 2023. Since then, the group has been operating and extensively developing its affiliate network based on a RaaS (Ransomware-as-a-Service) model. Currently, the group has two resources on the TOR network:
http://z3wqggtxft7id3ibr7srivv5gjof5fwg76slewnzwwakjuf3nlhukdid[.]onion
http://dragonforxxbp3awc7mzs5dkswrua3znqyx5roefmi4smjrsdi22xwqd[.]onion
DragonForce ransomware's notable feature is its customized CAPTCHA filter and mechanism, which prevents content from being automatically indexed by Cyber Threat Intelligence and Dark Web Monitoring platforms.
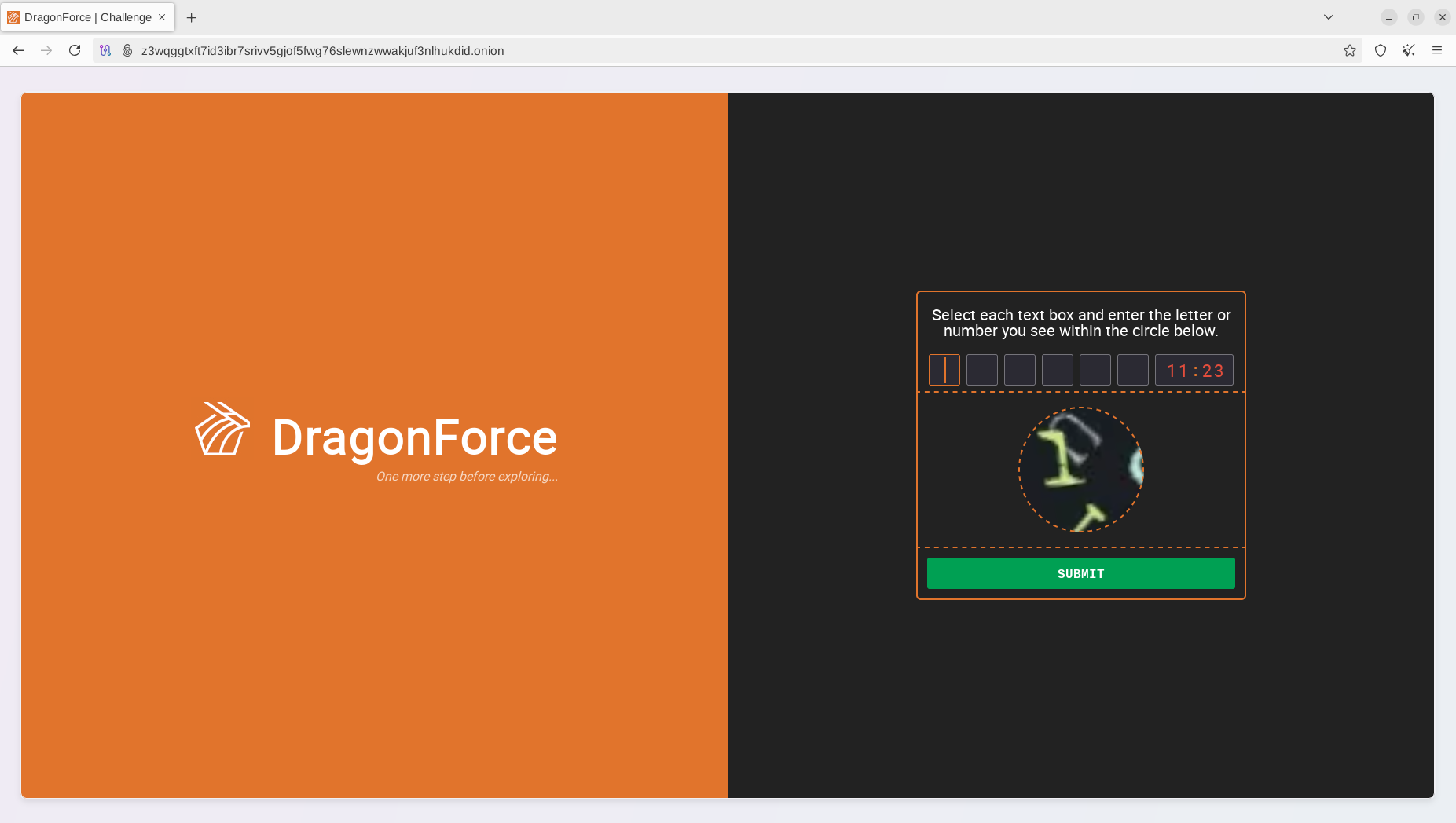
Legitimate bot detection and fraud prevention systems in the industry use a similar approach, and threat actors have implemented similar mechanisms to protect their resources. This makes it challenging for cybersecurity researchers and threat intelligence analysts to track these activities using automated means and receive timely updates.
Underground Affiliate Network
DragonForce ransomware offers one of the highest commission rates for affiliates in the Dark Web market: up to 80% of successful ransom payments are received from victims.
They use TOR-based IM (TOX) as their main communication channel with victims. To encrypt communications with possible victims and affiliates, the group also shared its PGP public key, which was published on RAMP, a prominent underground forum for ransomware operators and access brokers.
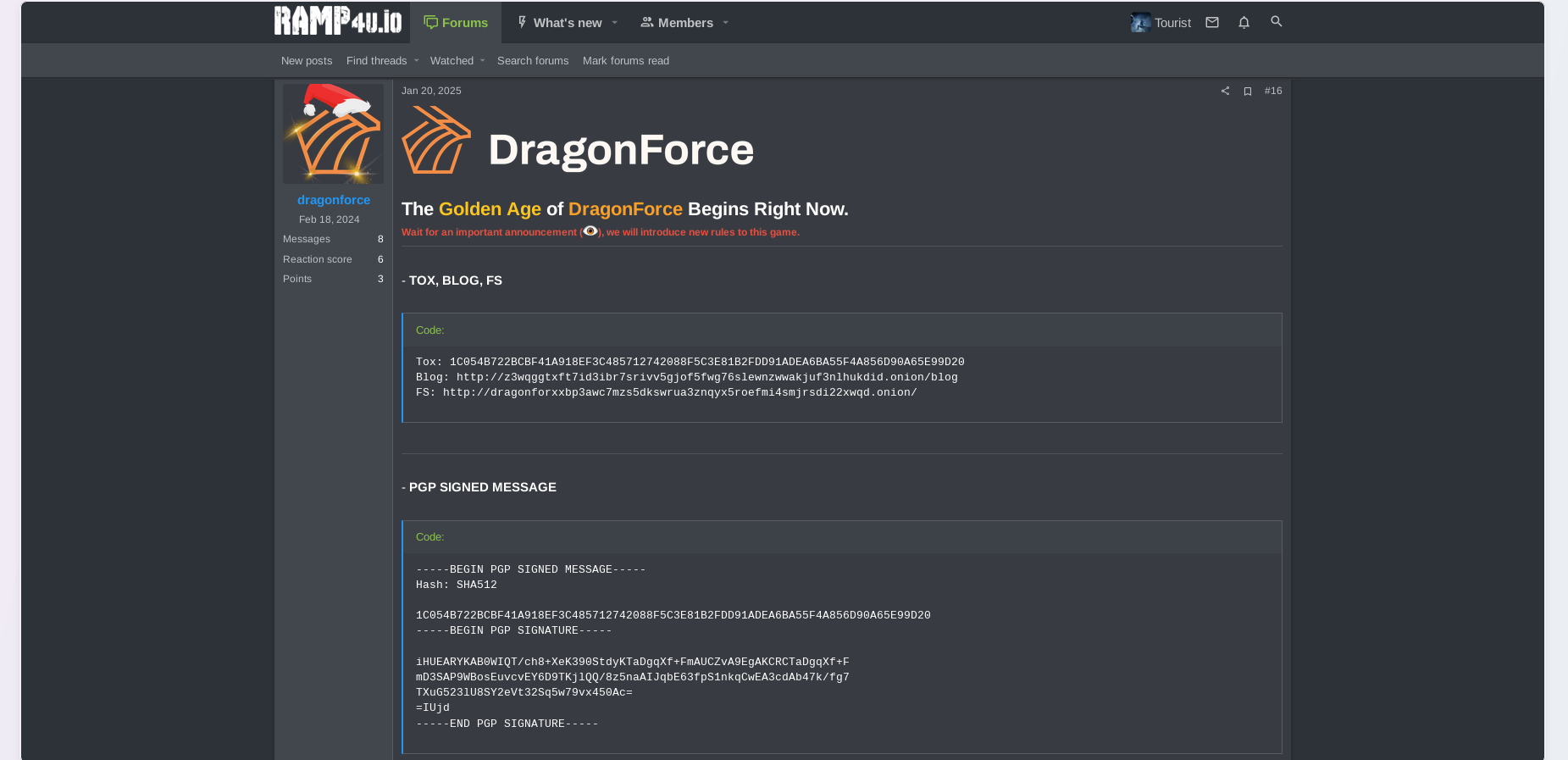
The DragonForce ransomware group runs ads on the RAMP underground forum to recruit new affiliates. Today, its affiliate network is described as "one of the best on the Dark Web market. " It supports various platforms, including Windows, Linux, and ESXi, and offers stable payouts.


One of the most recent postings by DragonForce ransomware was observed on January 20, 2025.
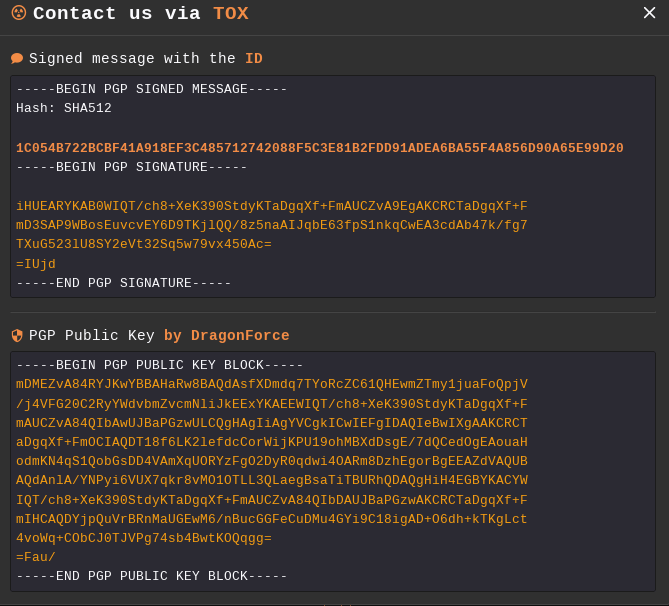
Note that the PGP key was generated on September 2024.
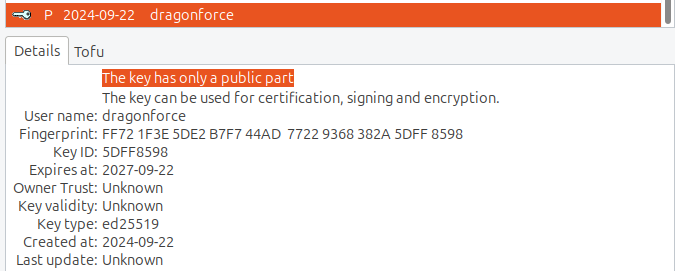
The actors' last visit to the RAMP forum was identified around February 24, 2025. This may confirm their activity on the Dark Web and relatively frequent communications monitoring on prominent underground communities.
Some time ago, the gang suffered a leak involving details about the URLs provided to affiliates for extorting victims. After that, DragonForce significantly improved the vetting process for new affiliates and implemented stricter protocols. Newcomers were asked to demonstrate proof of access (to the victim), the volume of data collected or file tree, and other details to validate their motivation for the project.
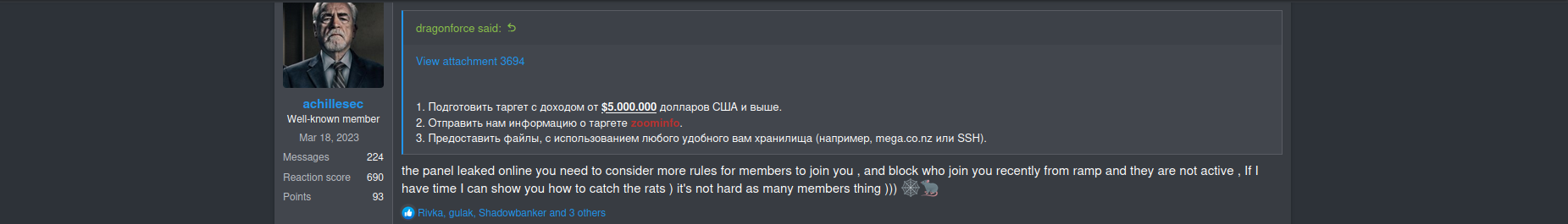
The gang provides strong technical support to affiliates by offering additional services such as 'call services' (to contact and exert further pressure on victims) and NTLM/Kerberos hash decryption, which is extremely valuable for access brokers dealing with the post-compromise of Active Directory environments.
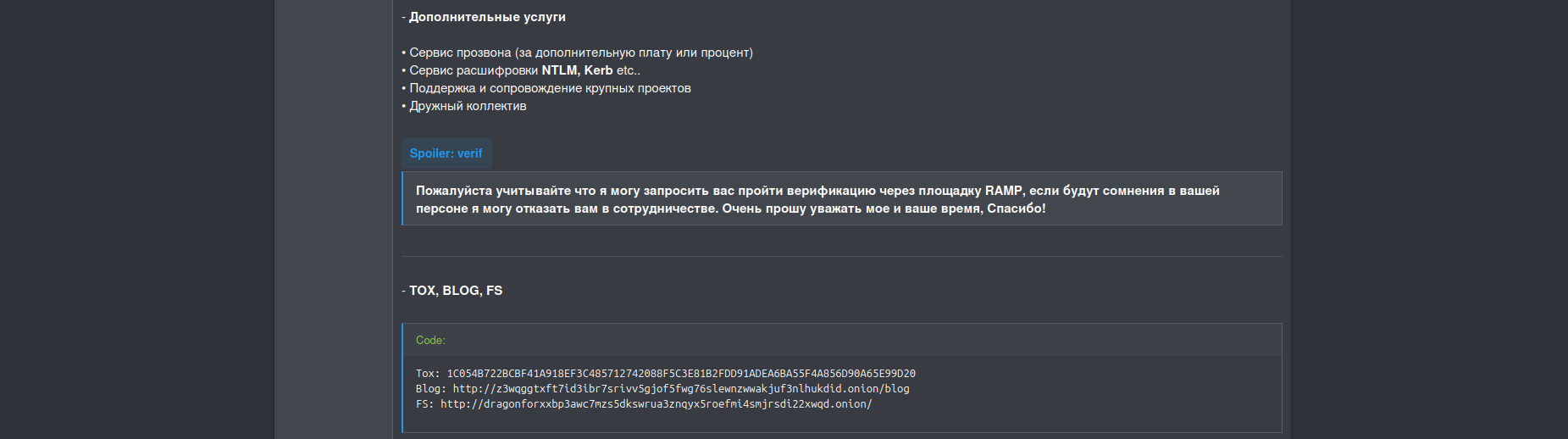
Only vetted affiliates will receive such services for additional fees, and the RAMP underground forum will be one of the key platforms for their selection.
Some sources mistakenly associate the group with another hacktivist group with the same name from Malaysia, which practices DDoS attacks and defacements. However, DragonForce is an independent ransomware project without connections to this group.
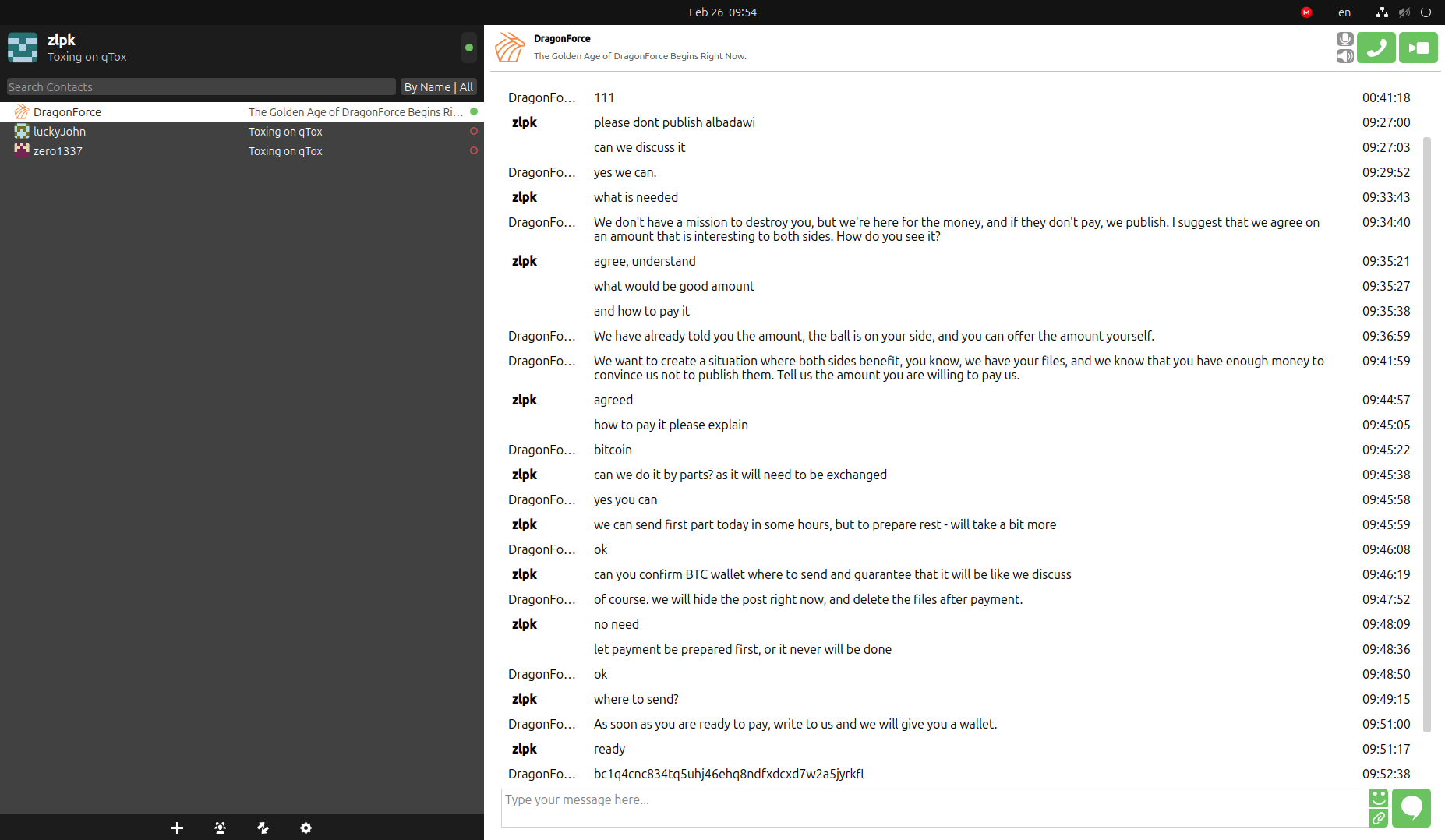
Collecting Ransom Payments
Resecurity acquired one of the chats via TOX IM between DragonForce ransomware and a likely victim. The actors shared a BTC wallet to receive ransom payments:
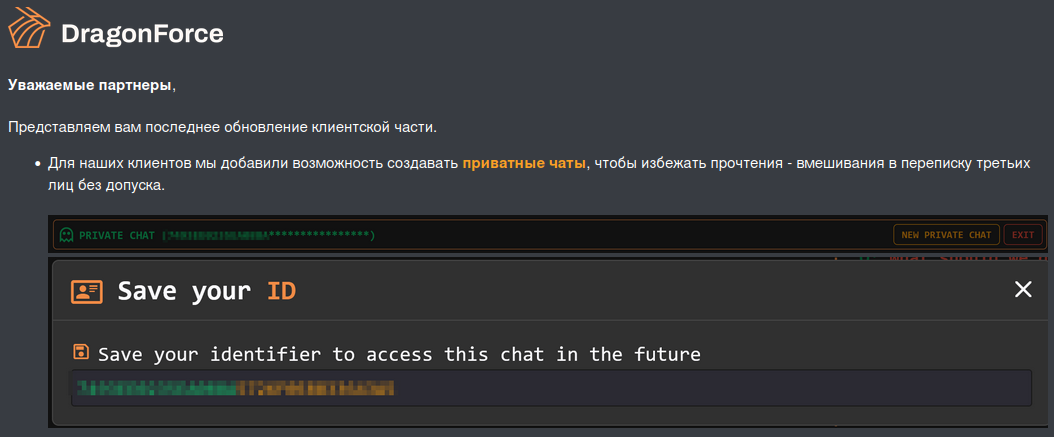
Some time ago, DragonForce ransomware also introduced a private chat mechanism. This feature is available for victims who cannot use TOX IM and adds more flexibility in communications with non-tech-savvy users.
Builder
DragonForce ransomware has introduced what is likely one of the most advanced payload builders currently available on the Dark Web. The builder offers affiliates extreme flexibility in binary configuration, including encryption scope, timing, file extensions, network settings support, and options for collaboration both within the team and with victims.
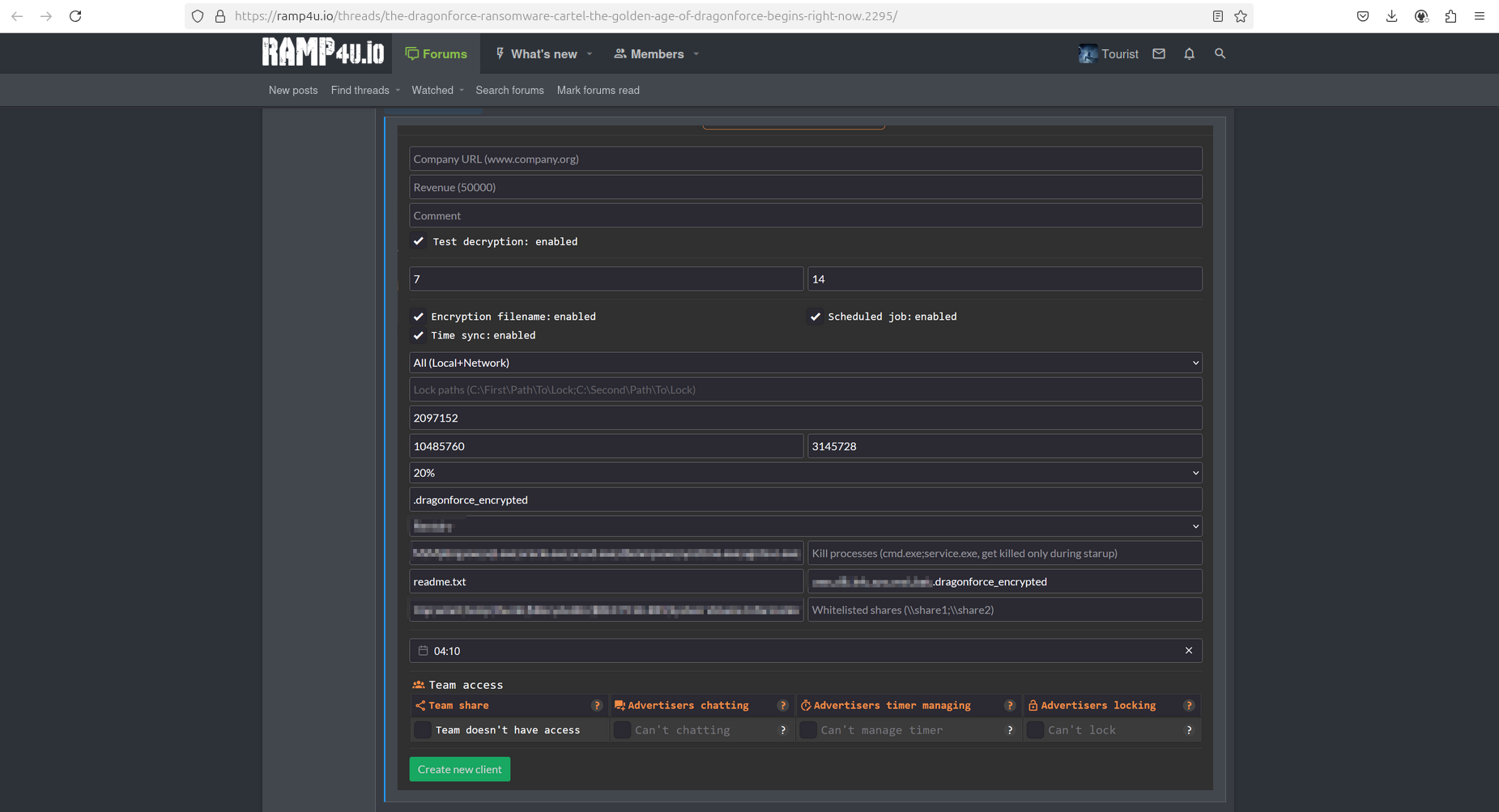
Like other groups, such as BlackLock, Blacksuit, Conti, and Lockbit, DragonForce is actively leveraging legitimate tools for file transfers, such as SFTP and MEGA clients, during data exfiltration and its further upload to DLS. This makes detection extremely complicated because such tools are widely used in almost every enterprise environment and operate via the HTTPS/SSL protocol, which makes timely data leak prevention nearly impossible in practice unless those tools are banned (blacklisted) by hash and network connection settings.
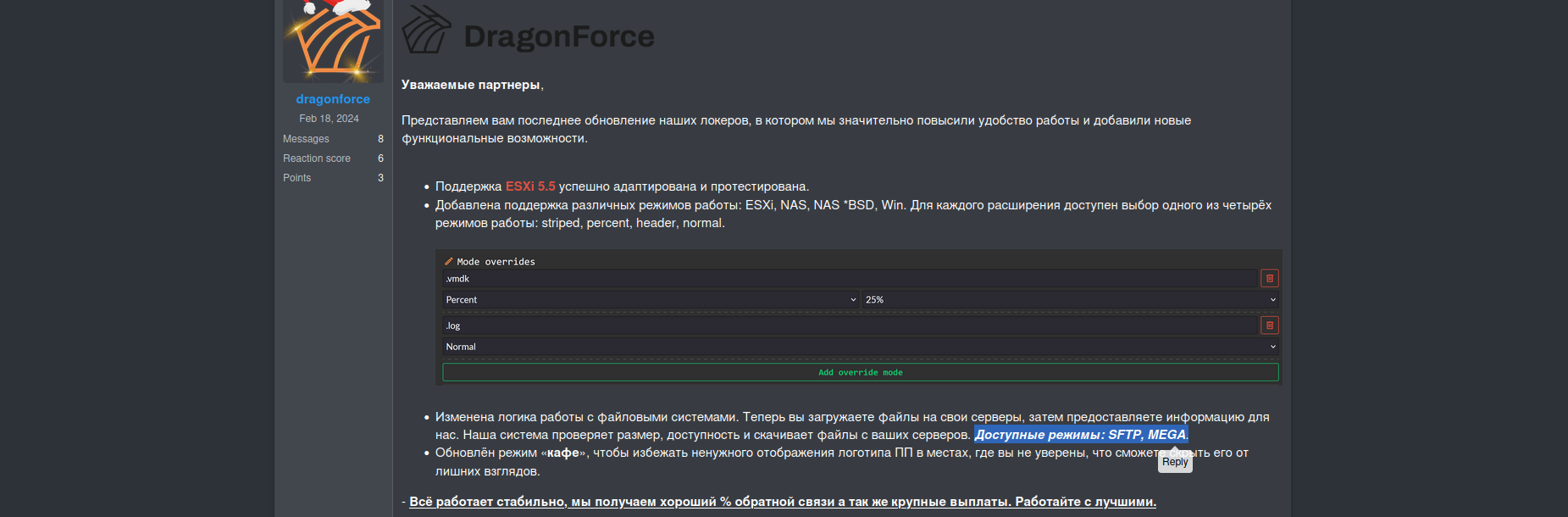
Affiliates receive builders via a special panel for collaboration within the RaaS program.
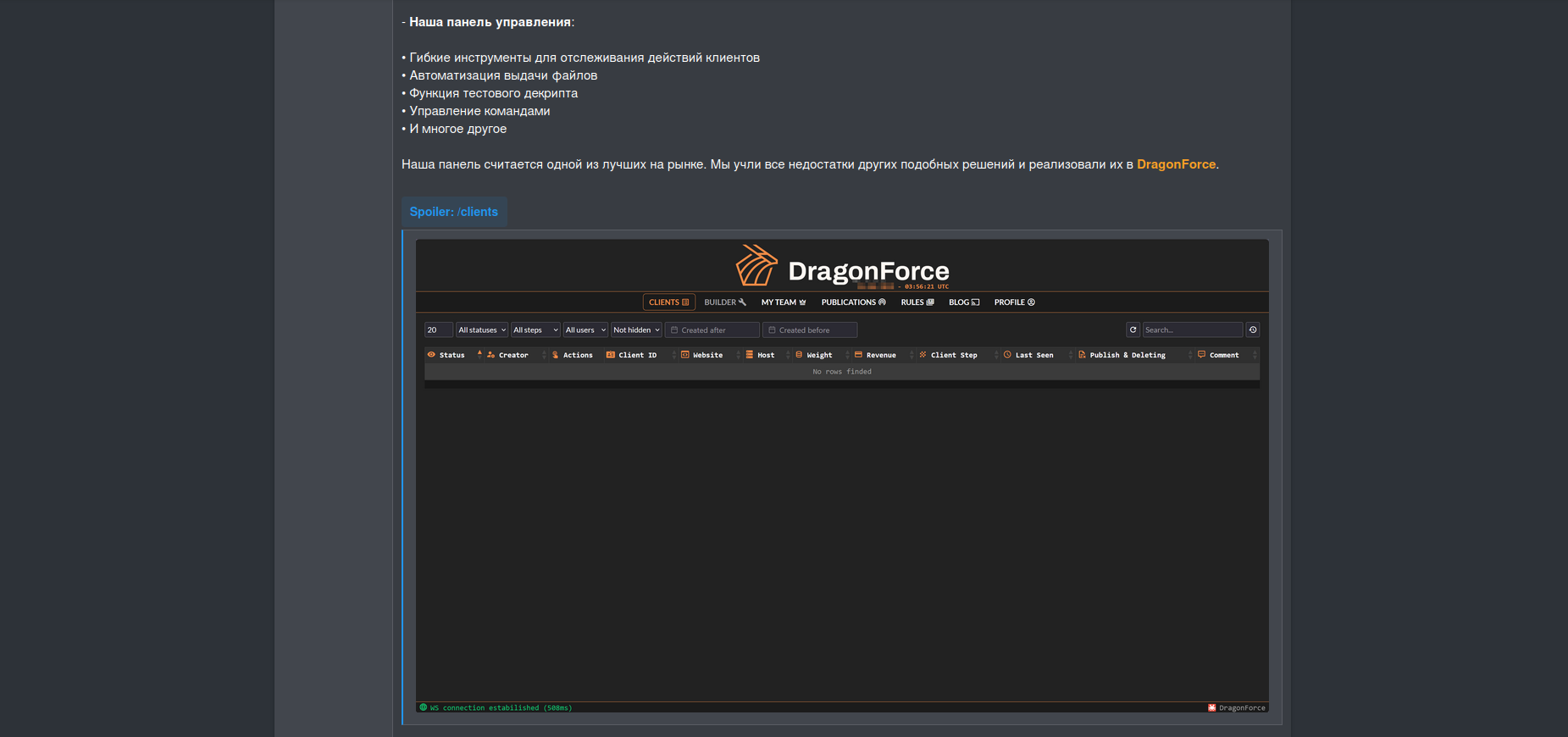
DragonForce ransomware is designed for 'lone wolves' and experienced cybercriminal teams collaborating to gain access and extort victims. The project's administration panel allows affiliates to add multiple team members with different permissions and settings to manage various victims.
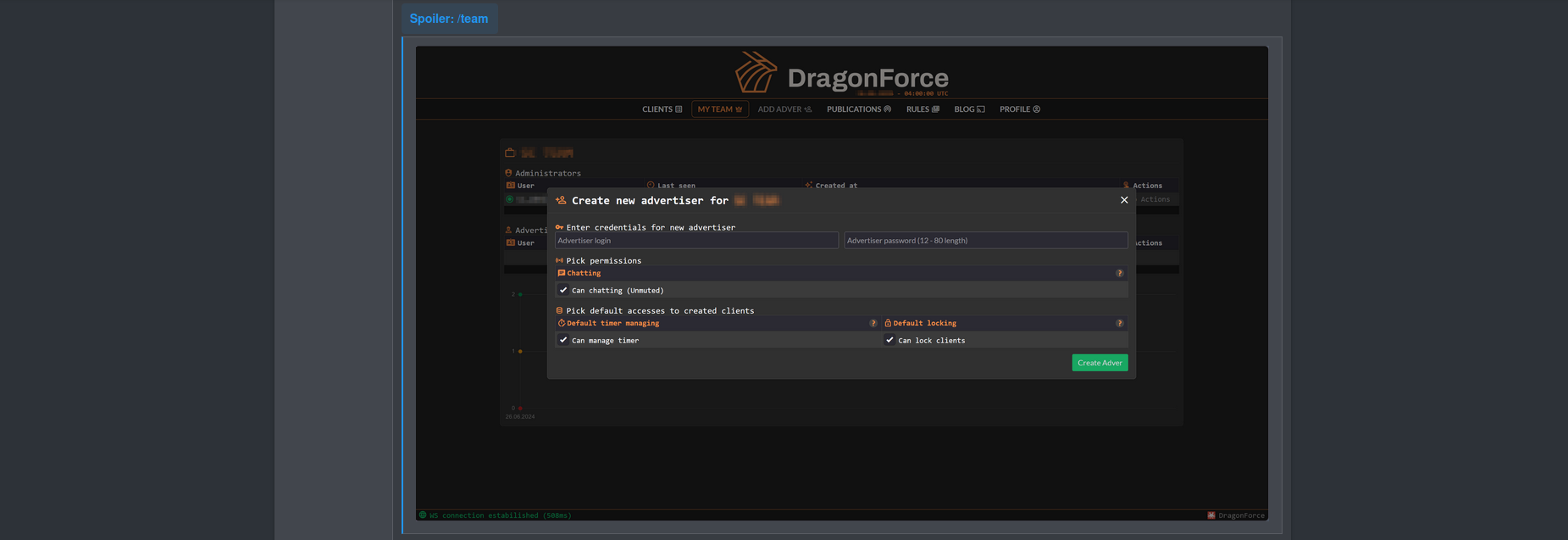
The latest build update allows up to six builds (one for each victim) to be generated and managed from a single dashboard.
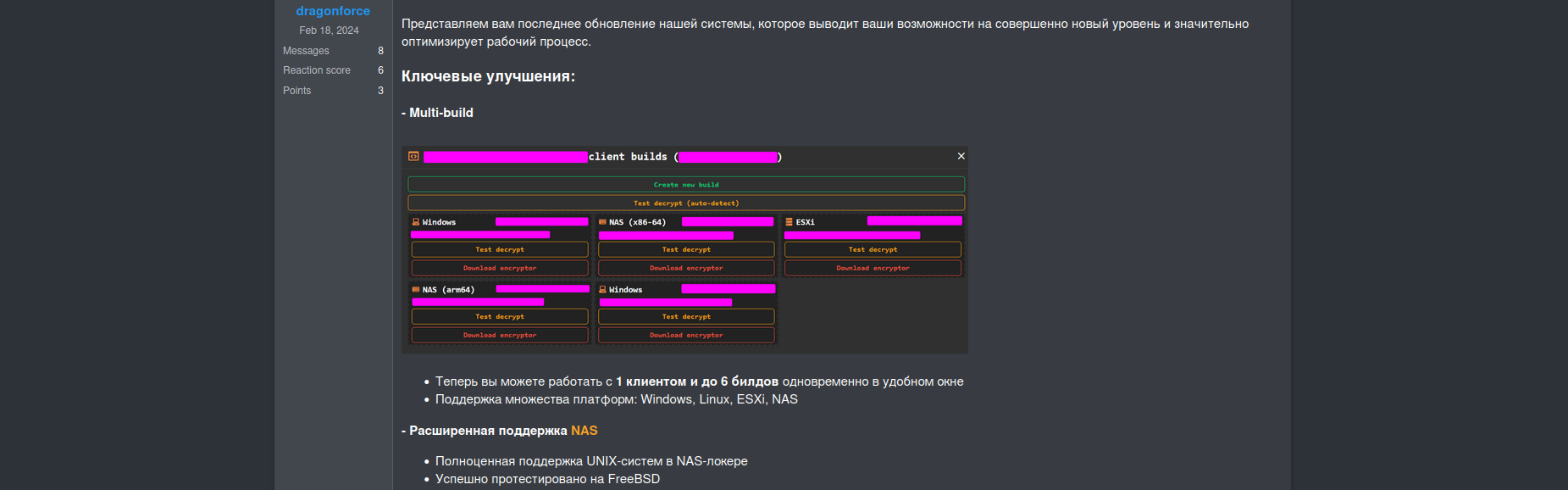
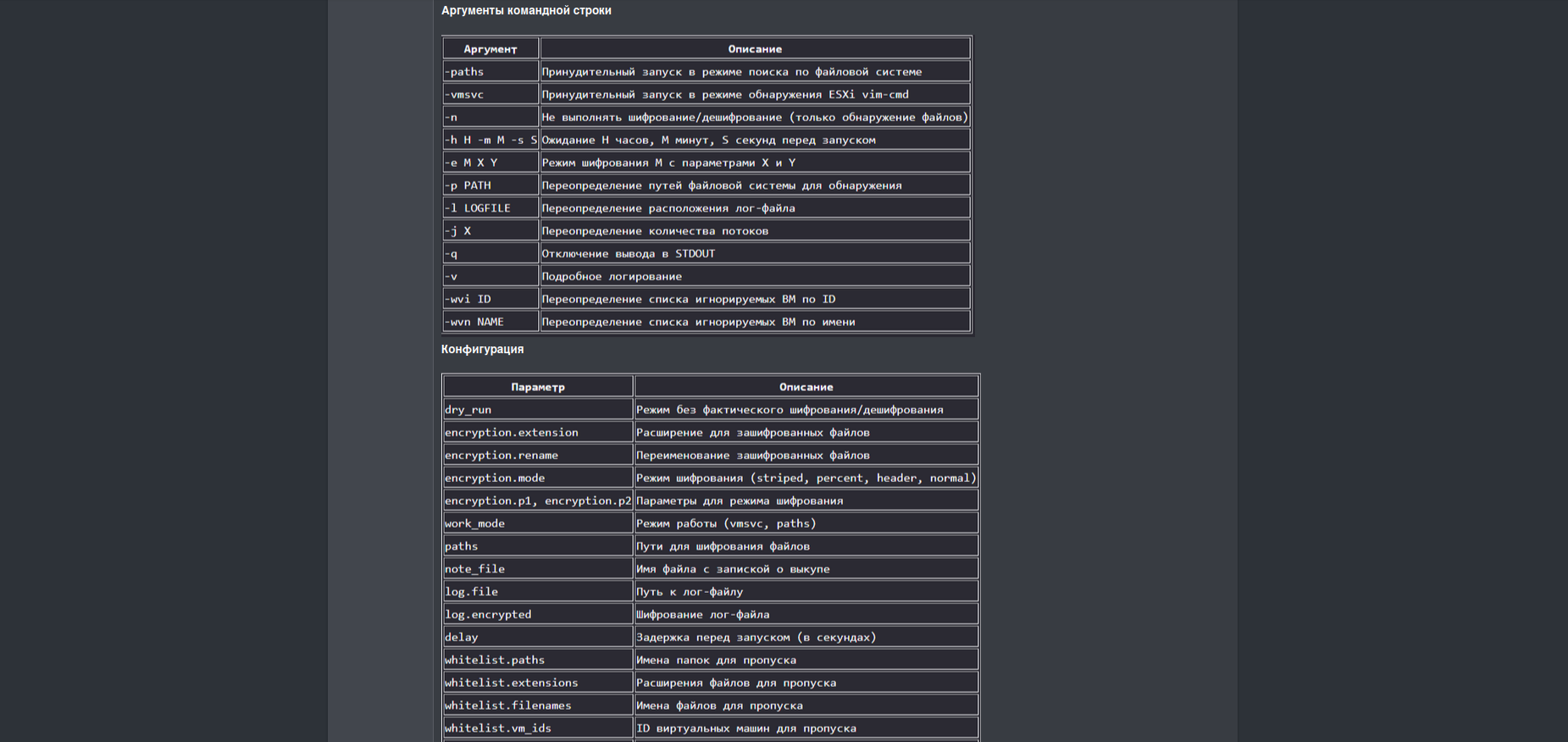
The binary can be executed from a console supporting multiple commands:
• Support for various encryption modes: striped, percent, header, normal
• Change file names
• Compact size (about 120 KB)
• Command line support
• Automated work with ESXi (VM shutdown -> encryption)
• Ability to exclude VM by ID or Name
• Delayed start with options [-h H][-m M][-s S]
• Logging to file with log encryption
• Statistics output with the ability to disable
• Ability to kill a list of processes by name
• Setting up encryption paths
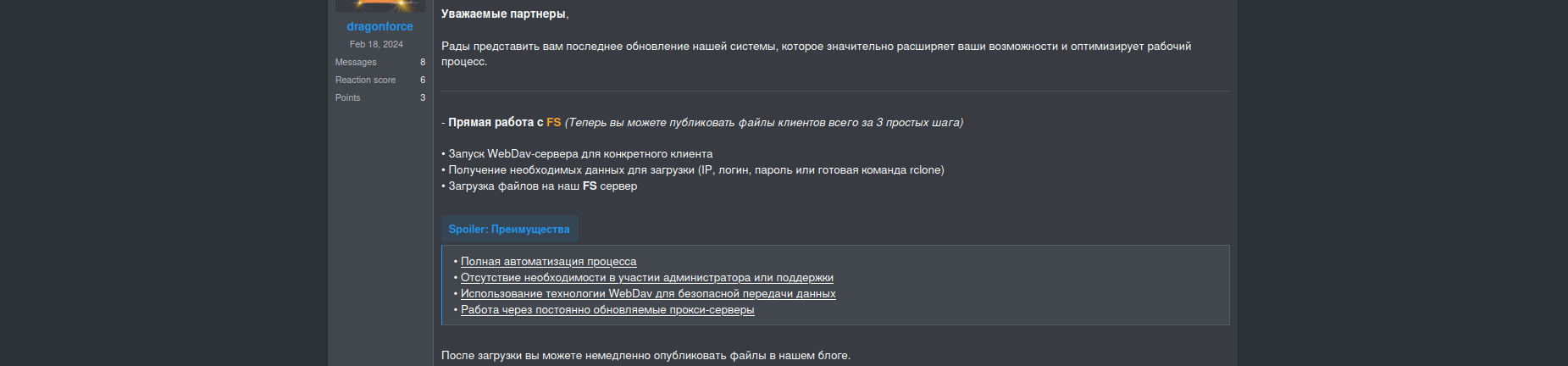
Data exfiltration and subsequent publication are fully automated. A WebDAV server will also be initiated, and the payload will transmit all collected files to the DragonForce server using a configuration file containing clone credentials. Alternatively, the files can be uploaded to an affiliate's server.
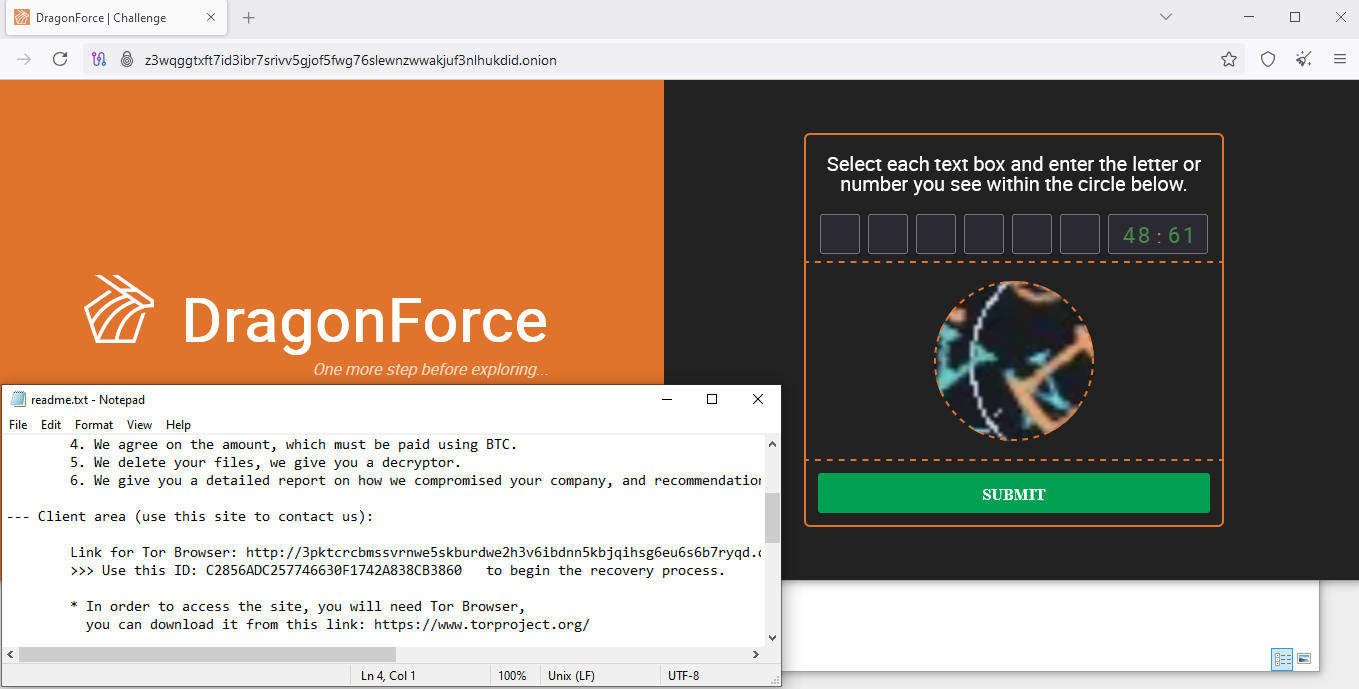
The files can be immediately published in the blog (DLS) if the affiliate decides to do so. After a successful infection, the victim will be assigned an identifier (ID) and a dedicated URL to communicate with DragonForce regarding the payment needed to decrypt the compromised data.
Tools, Tactics and Procedures (TTPs)
DragonForce has also distinguished itself through its operational ruthlessness and unconventional methods, such as publishing audio recordings of negotiations with victims on its Dark Website. This approach intensifies pressure on organizations to comply with the ransom demands.
DragonForce typically begins its attacks by phishing emails or exploiting vulnerabilities in Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) solutions. Once it infiltrates the network, DragonForce can quickly propagate, using encryption algorithms to secure critical systems and data.
DragonForce is widely using the following CVEs to compromise victims’ environments:
CVE-2021-44228
CVE-2023-46805
CVE-2024-21412
CVE-2024-21887
CVE-2024-21893
Like many ransomware groups, DragonForce uses a dual extortion strategy, locking out victims from their systems through encryption and threatening to expose stolen data on the Dark Web unless ransom demands are met.
Initial Access
T1190
Execution
T1204
Defense Evasion
T1070
T1140
T1562
Discovery
T1082
T1083
Collection
T1560
Impact
T1486
Command and Control
T1090
Indicators of Compromise (IOCs)
DLS
http://z3wqggtxft7id3ibr7srivv5gjof5fwg76slewnzwwakjuf3nlhukdid[.]onion
http://dragonforxxbp3awc7mzs5dkswrua3znqyx5roefmi4smjrsdi22xwqd[.]onion
http://kfgjwkho24xiwckcf53x7qyruobbkhx4eqn2c6oe4hprbn23rcp6qcqd[.]onion
MD5
2915b3f8b703eb744fc54c81f4a9c67f
7bdbd180c081fa63ca94f9c22c457376
d54bae930b038950c2947f5397c13f84
SHA256
1250ba6f25fd60077f698a2617c15f89d58c1867339bfd9ee8ab19ce9943304b
9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
07ab218d5c865cb4fe78353340ab923e24a1f2881ec7206520651c5246b1a492
330730d65548d621d46ed9db939c434bc54cada516472ebef0a00422a5ed5819
62cd46988f179edf8013515c44cbb7563fc216d4e703a2a2a249fe8634617700
9479a5dc61284ccc3f063ebb38da9f63400d8b25d8bca8d04b1832f02fac24de
a4dfa099e1f52256ad4a3b2db961e158832b739126b80677f82b0722b0ea5e59
ab7d8832e35bba30df50a7cca7cefd9351be4c5e8961be2d0b27db6cd22fc036
feab413f86532812efc606c3b3224b7c7080ae4aa167836d7233c262985f888c
Implications and Concerns
The targeting of KSA by ransomware groups like DragonForce raises concerns about the security of critical infrastructure in the region. Resecurity and other cybersecurity experts warn that such attacks will have severe implications for the affected companies, national security, and economic stability. The potential involvement of state-sponsored actors in these cyber incidents further complicates the landscape, as geopolitical tensions can exacerbate the frequency and severity of attacks.
The Middle East is home to some of the world's wealthiest economies, such as the Gulf Cooperation Council (GCC) countries, that's why targeting on countries like the Kingdom of Saudi Arabia is highly expected due to massive economy and attractive targets for cyber-attacks. Ransomware groups view the region as a lucrative target, as potential victims are more likely to pay ransom demands to recover their data and resume operations. While countries like Saudi Arabia and the UAE rank highly in global cybersecurity indices, many organizations in the region still lack robust cybersecurity measures. This makes them more vulnerable to ransomware attacks. Some ransomware groups, such as those based in Iran, may specifically target organizations in the Middle East due to geopolitical tensions in the region.
The combination of wealthy targets, cybersecurity gaps, and geopolitical factors make the Middle East an attractive region for ransomware groups to exploit, making these attacks more profitable for them. In summary, the DragonForce ransomware targeting KSA and the associated data leak from the recent victim in KSA underscore the urgent need for enhanced cybersecurity measures to protect vital national assets and sensitive information.

