

Overview:
DragonForce ransomware is a type of malicious software designed to encrypt files on infected systems and demand ransom payments in cryptocurrency (Bitcoin) in exchange for the decryption key. Like many ransomware strains, DragonForce is distributed via phishing emails, malicious websites, or exploiting vulnerabilities in systems. This ransomware follows the general structure of most modern ransomware but comes with unique characteristics and behaviors. Below is a step-by-step breakdown of how DragonForce operates:
1. Initial Infection and Delivery
DragonForce ransomware is commonly spread through phishing campaigns. The email might appear legitimate, pretending to be a legitimate business or service, and includes an attachment (typically a Microsoft Office document, such as a Word or Excel file) or a malicious link.
Once the victim opens the attachment or clicks the malicious link, the malware exploits vulnerabilities in outdated software and uses social engineering techniques to convince the user to enable macros, which then triggers the malware’s execution.
2. Execution and Payload Deployment
Once executed, DragonForce ransomware does the following:
DragonForce will replicate itself using MITRE ATT&CK T1105 in various directories, often copying itself to other systems on the network after gaining initial access.
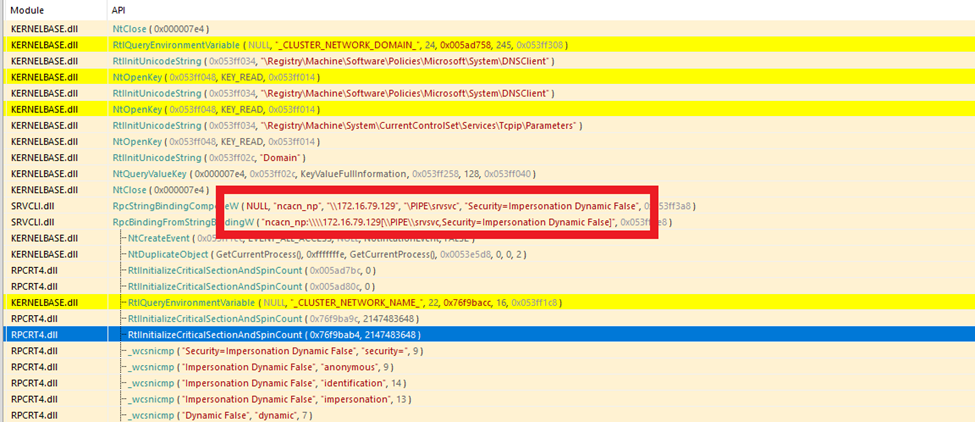
The ransomware modifies Windows registry keys or creates new scheduled tasks to maintain persistence across system reboots, ensuring it is executed each time the system starts up.
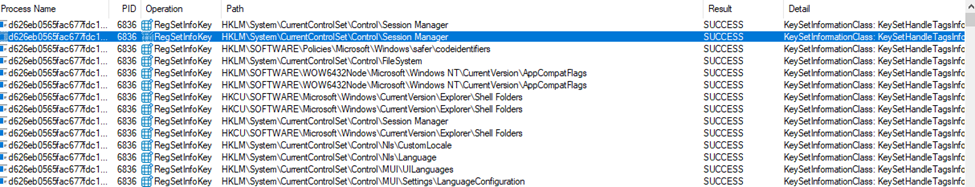
DragonForce uses MITRE ATT&CK techniques T1070,T1089 and T1562 to remove or disable antivirus software, delete system logs, and erase any indicators that could help security tools detect its presence. This involves cleaning up event logs and utilizing fileless execution techniques.
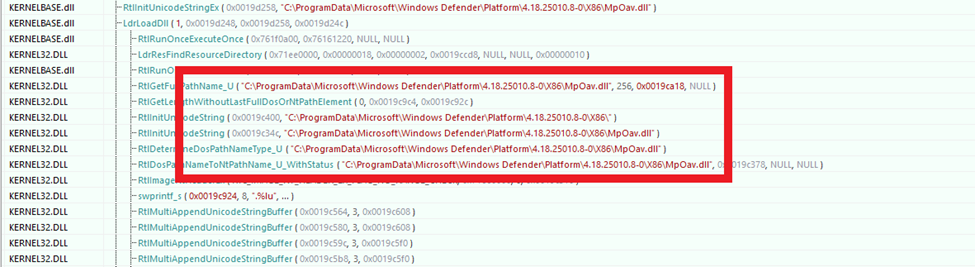
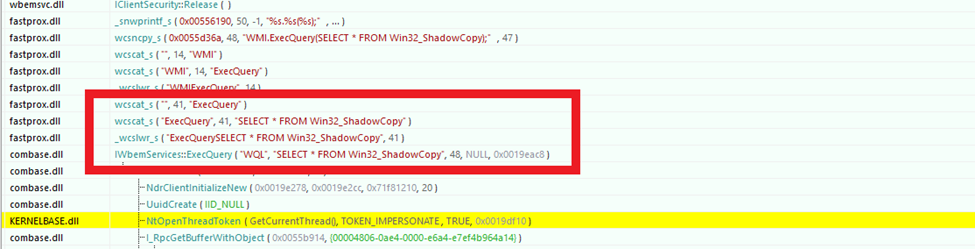
To terminate processes, the ransomware requires administrator privileges. Once it has confirmed it has elevated privileges, it attempts to escalate its access to SYSTEM-level by exploiting Access Token Manipulation. The ransomware enumerates the running processes to identify one with SYSTEM-level privileges. It then duplicates the access token using DuplicateTokenEx() and utilizes CreateProcessWithTokenW() to launch a new process under the security context of NT AUTHORITY\SYSTEM
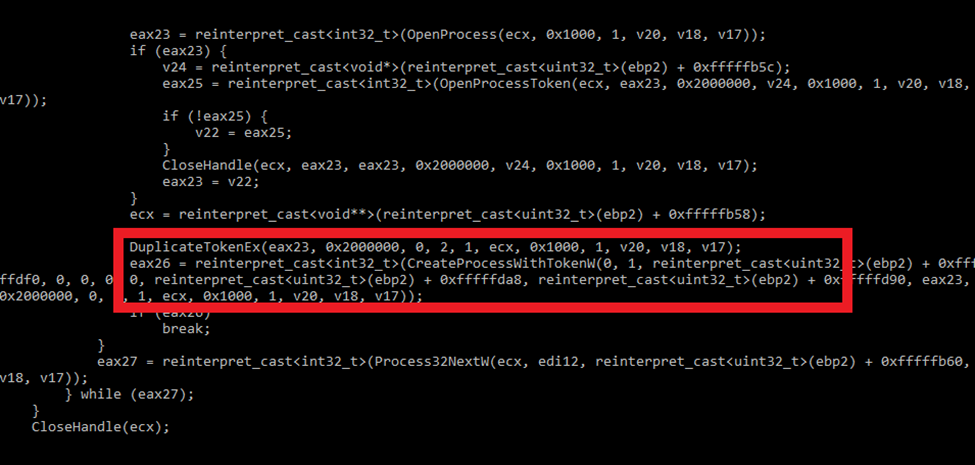
DragonForce employs obfuscation techniques (MITRE ATT&CK T1027) to conceal its presence, such as packing the payload or encrypting parts of the code designed to dynamically load a DLL and invoke a function within it. Both the DLL and function names are obfuscated to evade detection and hinder static analysis.
Notably, there were identified multiple text signatures written in Chinese in the code, such as:
癆瘞瘠
瘚瘳癬瘃
朓朚杆朳朊朚杮朅杛末朮
塆堈堻塜堻堻堈堚塃
3. Encryption Process
The core functionality of DragonForce revolves around encrypting user data and making it inaccessible without the decryption key:
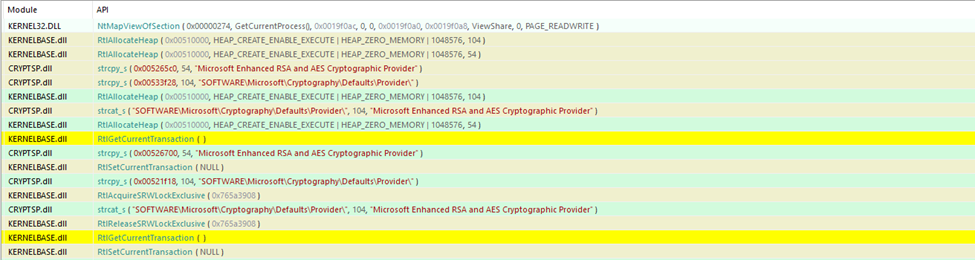
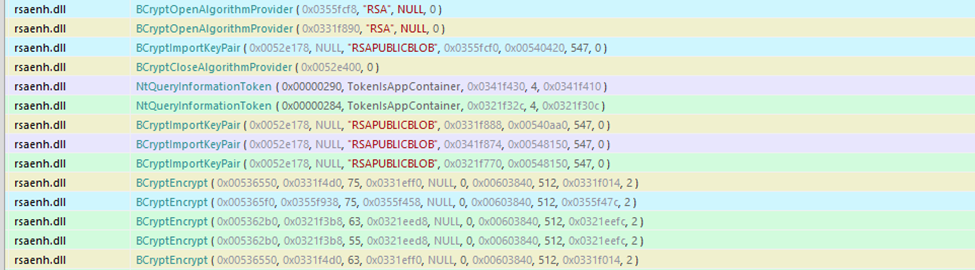
DragonForce ransomware uses strong encryption algorithms, such as AES-256 (Advanced Encryption Standard) or RSA for encrypting files and target common file types such as following:
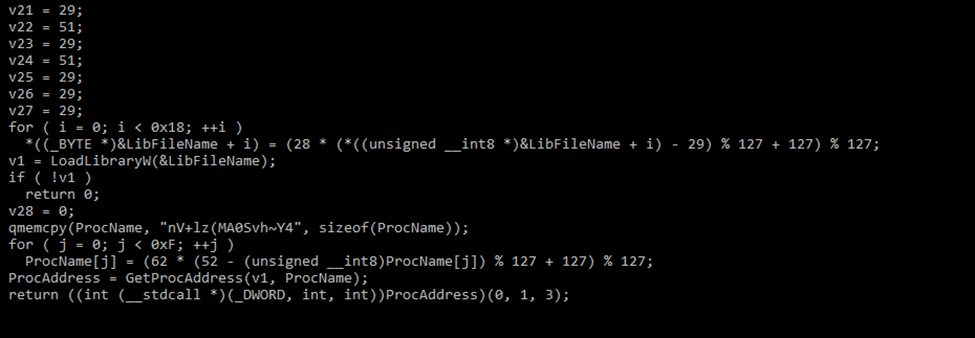
The ransomware uses Base32 encoding for filenames and appends a specific extension to the encrypted files, such as .dragonforce_encrypted.
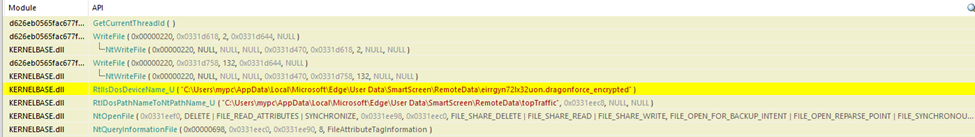
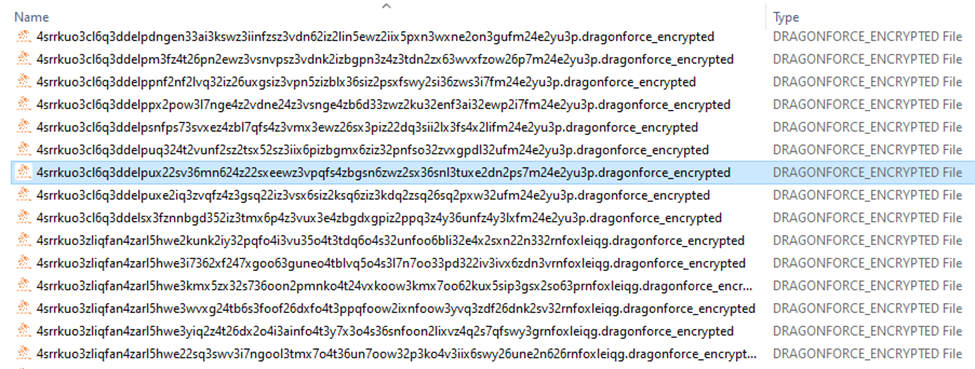
DragonForce generates a unique encryption key for each infected machine, where the public key encrypts the files and the private key is kept by the attackers. It employs encryption algorithms such as AES-256 (MITRE ATT&CK T1486) to lock files and demands a ransom for their decryption.
4. Data Gathering and Logging
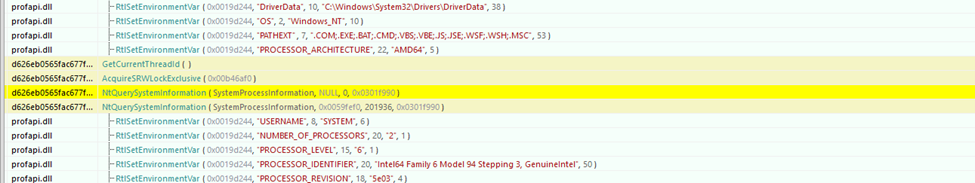
DragonForce ransomware not only encrypts files on infected systems but also implements a sophisticated data-gathering mechanism. Upon infection, it gathers crucial system information, including user credentials, system configurations, and other sensitive data that may assist the attackers in further compromising the system or in launching additional attacks. This data collection is often done silently, without user knowledge, to avoid detection by security software.
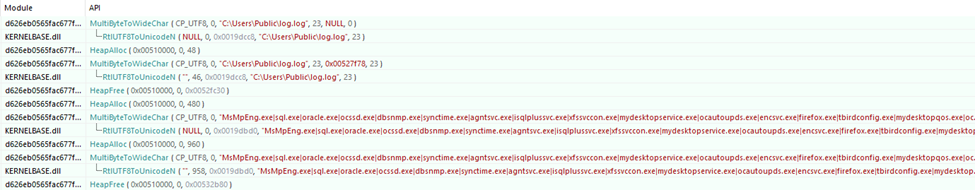
The ransomware creates a log file at the following location on the compromised machine:
C:\Users\Public\log.log

This file stores detailed records of the activities and information gathered by the malware. It can include data such as:
- Information about the operating system version and architecture
- A list of installed applications and running processes
- User account names and potentially even login credentials
- Network information, including active connections and external IP addresses
The log file is a crucial part of DragonForce’s functionality, enabling the attackers to analyze the infected system's vulnerabilities and prioritize which files or data are most valuable. This data can then be used to enhance the ransomware's capabilities, track infected machines, or guide the attackers in their ransom demands.
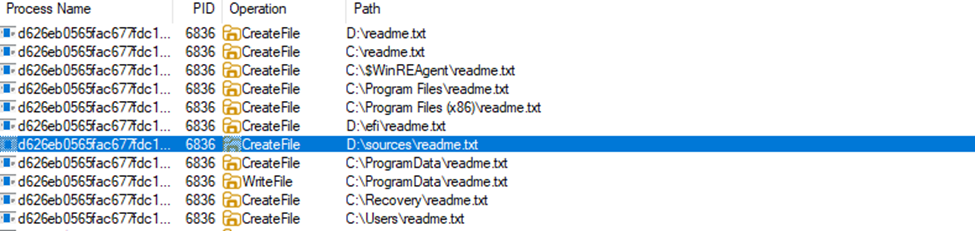
5. Ransom Note Creation
Once the encryption is complete, DragonForce drops a ransom note, usually named README.txt, on the victim’s desktop and in the directories where files were encrypted.
The message instructs the victim to pay a ransom via a .onion website. The note contains:
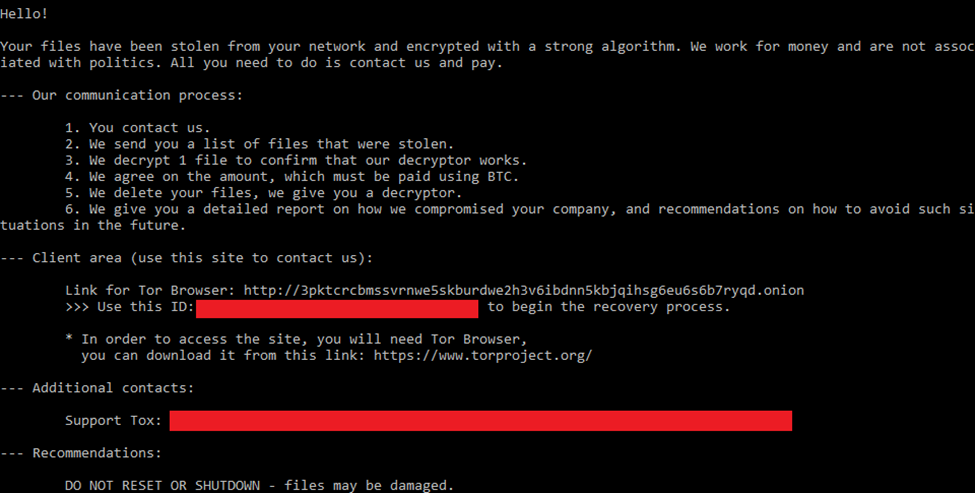
6. Communication with C2 Server
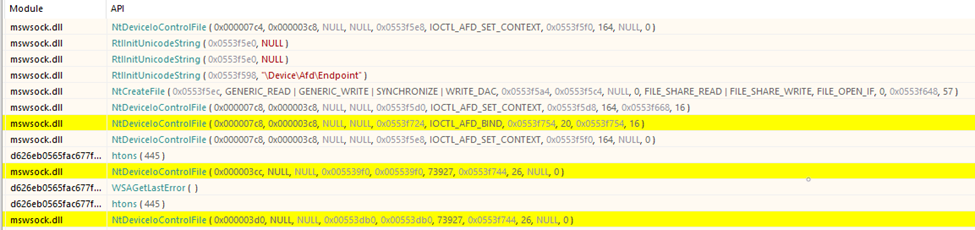
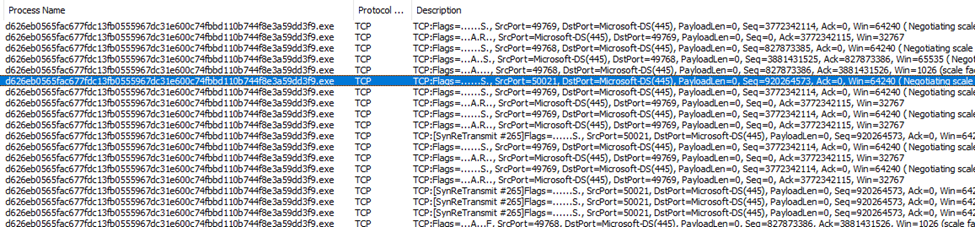
DragonForce ransomware regularly communicates with a Command and Control (C2) server to transmit stolen information and receive updates. This communication occurs over HTTP/HTTPS. The malware sends critical system data—such as the machine ID, username, IP address, and public encryption key—back to the C2 server, enabling attackers to track and manage infected machines.
Although DragonForce’s primary function is encryption, some variants of this ransomware are known to exfiltrate sensitive data before initiating encryption. This may include:
- Stealing documents, credentials, or other sensitive information
- Uploading this data to a remote server controlled by the attackers
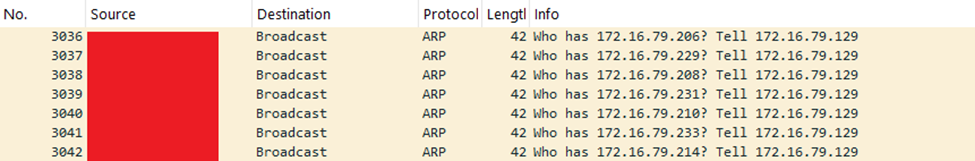
In some variants, DragonForce also attempts to spread across networks, infecting multiple machines. This propagation can occur through:
- Exploiting network vulnerabilities
- Stealing credentials to move laterally within a corporate network
- Leveraging Remote Desktop Protocol (RDP) and SMB vulnerabilities to spread within the network
7. Indicators of Compromise (IOC)
IP Addresses:
These IP addresses are associated with DragonForce ransomware's Command and Control (C2) servers. Monitoring or blocking network traffic to/from these IPs may help in detecting or mitigating ransomware infections.
2[.]147[.]68[.]96
185[.]59[.]221[.]75
69[.]4[.]234[.]20
Notably, one of the identified C2 servers used at the early stage of the group's activity was located in Iran
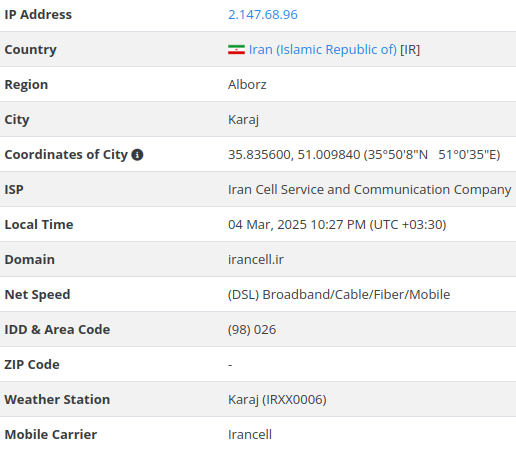
Considering the identified signatures (in Chinese) found in the code, and the C2 located in Iran, it is possible Dragonforce Ransomware includes actors from multiple countries and/or collaborates with other cybercriminal syndicates to outsource specific functions such as malicious payload development and network infrastructure management.
File Hashes:
b9bba02d18bacc4bc8d9e4f70657d381568075590cc9d0e7590327d854224b32
ba1be94550898eedb10eb73cb5383a2d1050e96ec4df8e0bf680d3e76a9e2429
d626eb0565fac677fdc13fb0555967dc31e600c74fbbd110b744f8e3a59dd3f9
1250ba6f25fd60077f698a2617c15f89d58c1867339bfd9ee8ab19ce9943304b
9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
07ab218d5c865cb4fe78353340ab923e24a1f2881ec7206520651c5246b1a492
330730d65548d621d46ed9db939c434bc54cada516472ebef0a00422a5ed5819
62cd46988f179edf8013515c44cbb7563fc216d4e703a2a2a249fe8634617700
9479a5dc61284ccc3f063ebb38da9f63400d8b25d8bca8d04b1832f02fac24de
a4dfa099e1f52256ad4a3b2db961e158832b739126b80677f82b0722b0ea5e59
ab7d8832e35bba30df50a7cca7cefd9351be4c5e8961be2d0b27db6cd22fc036
feab413f86532812efc606c3b3224b7c7080ae4aa167836d7233c262985f888c
MITRE ATT&CK Details:
Tactic |
ID |
Description |
Initial Access |
Exploit Public-Facing Application (T1190) |
DragonForce may exploit vulnerabilities in public-facing applications to gain initial access to the target system. Although not explicitly mentioned, this is common in ransomware. |
Execution |
User Execution (T1204) |
DragonForce is delivered via phishing campaigns, where the victim is tricked into opening a malicious attachment (e.g., Word or Excel file) or clicking a malicious link, triggering the execution of the ransomware. |
Defense Evasion |
Indicator Removal on Host (T1070) |
DragonForce disables or removes antivirus software, deletes system logs, and erases indicators to avoid detection by security tools. |
Defense Evasion |
Obfuscated Files or Information (T1027) |
DragonForce obfuscates its payload by packing or encrypting parts of the code to evade detection and hinder static analysis. |
Defense Evasion |
Impair Defenses (T1562) |
DragonForce clears event logs and uses other techniques to disable or remove defenses, such as antivirus software, in order to evade detection. |
Defense Evasion |
Disabling Security Tools (T1089) |
DragonForce disables security tools, particularly antivirus software, to facilitate its persistence and to remain undetected. |
Discovery |
System Information Discovery (T1082) |
DragonForce gathers system information such as the operating system version, architecture, and installed applications to identify vulnerable targets. |
Discovery |
File and Directory Discovery (T1083) |
DragonForce explores file and directory structures to identify valuable files for encryption, which is typical behavior for ransomware. |
Collection |
Archive Collected Data (T1560) |
DragonForce collects sensitive data such as user credentials, system configurations, and network information, storing it in a log file for future exploitation. |
Impact |
Data Encrypted for Impact (T1486) |
DragonForce uses encryption algorithms, such as AES-256 or RSA, to lock files and demands a ransom for their decryption. |
Command and Control |
Application Layer Protocol (T1090) |
DragonForce may use proxy or tunneling techniques to hide its communication with attackers, maintaining control over the infected machine while evading detection. |
Execution |
Remote File Copy (T1105) |
DragonForce replicates itself in various directories and may copy itself to other systems on the network after gaining initial access. |
Conclusion
DragonForce ransomware is a sophisticated and highly dangerous threat. It demonstrates typical ransomware behavior, such as file encryption, ransom demands, and communication with a C2 server. However, it also exhibits advanced evasion techniques like obfuscation, anti-analysis, and potential data exfiltration, which makes it a significant threat to both individual users and enterprises.
Organizations are strongly advised to implement a multi-layered defense strategy involving:
- Regular updates and patch management.
- Network monitoring for unusual activity.
- Comprehensive backup and recovery plans.
Given the evolving nature of ransomware, continuous monitoring and adaptation of defense strategies are critical in combating malware like DragonForce.

