Following the AnyDesk Incident: Customer Credentials Leaked and Published for Sale on the Dark Web
Cyber Crime Intelligence

On February 2, 2024, it was disclosed that AnyDesk recently suffered a cyberattack, granting hackers access to the company's production systems.
Following a public statement published by the company regarding indications of an incident on some of AnyDesk's systems, the company conducted a security audit and found evidence of compromised production systems.
As a precautionary measure, the company recommended that all customers change their passwords if the same credentials were used elsewhere.
On February 3, 2024, Resecurity identified multiple threat actors selling access to compromised AnyDesk credentials on cybercriminal forums. One of these threat actors, going by the alias "Jobaaaaa," and who had initially registered their forum account in 2021, listed over 18,000 AnyDesk customer credentials for sale on Exploit[.]in, a prominent Dark Web forum. Cyber threat intelligence analysts from our HUNTER team were able to establish contact with the actor to acquire context about this activity. The actor said - "this data is ideal for technical support scams and mailing (phishing)". These compromised account credentials are believed to have been obtained via infostealer infections. Resecurity has collected available information to share with the broader security community, with the aim of increasing cybercrime awareness and galvanizing risk-mitigation efforts.
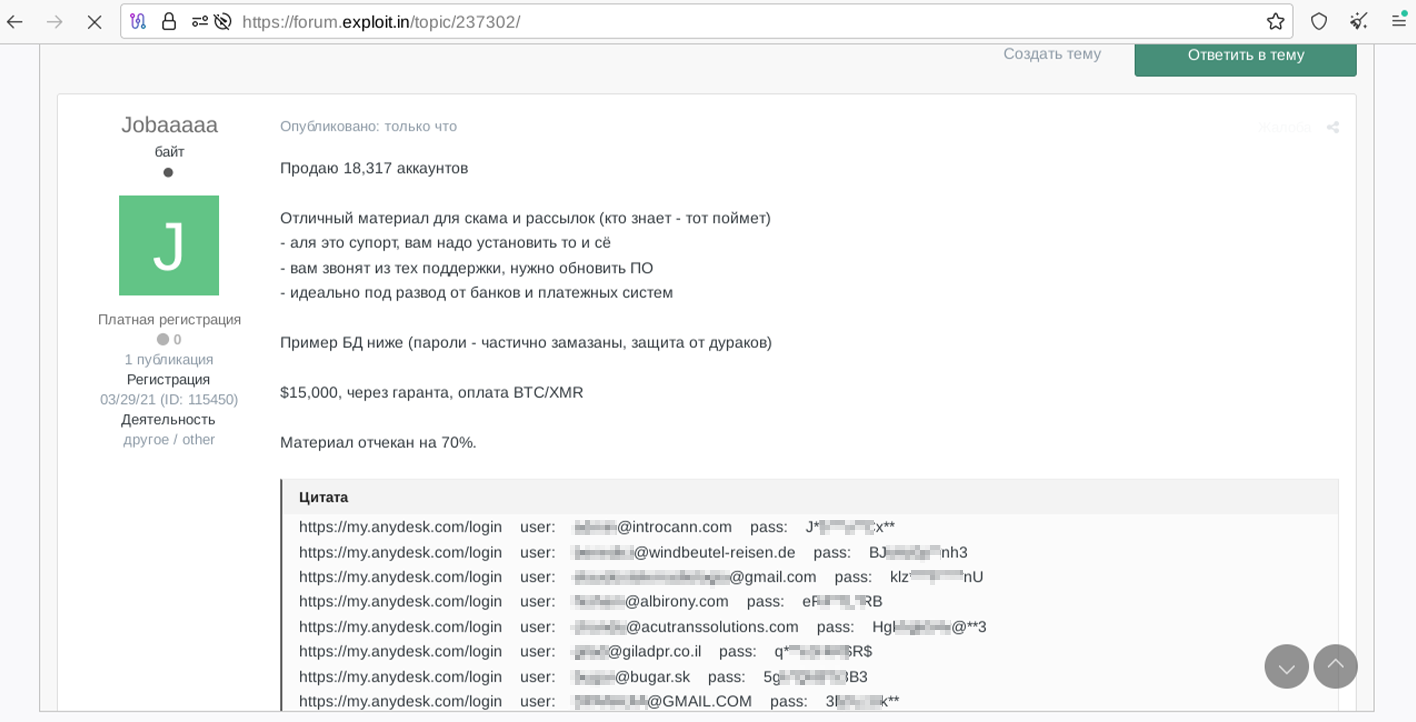
The samples provided by the threat actors were related to compromised access credentials that belong to various consumers and enterprises, and which grant access to the AnyDesk customer portal. As a security measure, the threat actor sanitized some of the passwords. The threat actor offered 18,317 accounts for $15,000 to be paid in cryptocurrency. He also agreed to make a deal via escrow on Exploit. Resecurity reached out to the majority of the contacts identified as potential victims and confirmed they had used AnyDesk products recently or long ago. The threat actor didn't share any additional information.
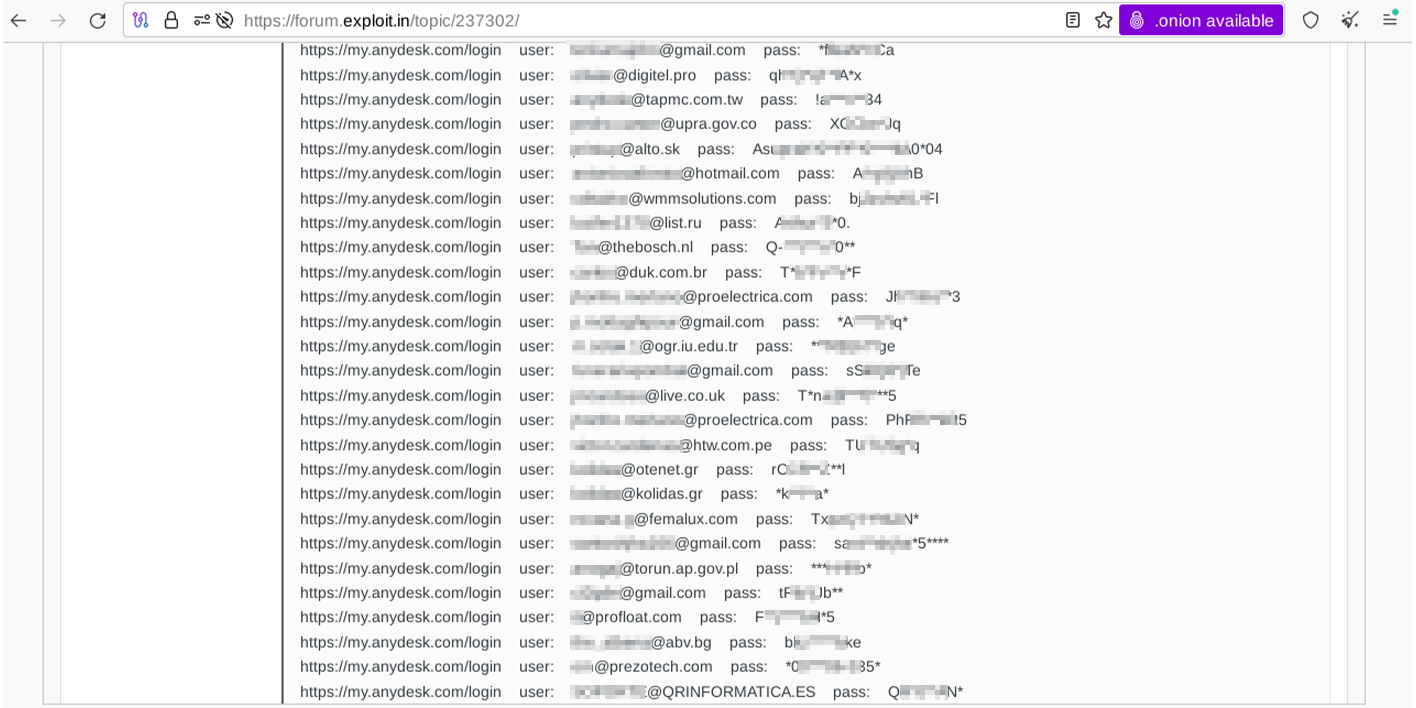
The sources and methods for acquiring data of this nature may vary depending on threat actors’ unique Tactics, Techniques, and Procedures (TTPs). While this credential leak is widely believed to be the result of infostealer infections, this uncertainty nevertheless creates a new area of concern. Assuming the prevailing infostealer hypothesis is correct and considering the latest incident disclosure, timely password resets would be a mandatory mitigation measure for all AnyDesk customers. The end-users of AnyDesk include IT administrators, who are often targeted by threat actors. Thus, it is critical that AnyDesk ensures this cyberattack hasn’t impacted access to any other critical systems to which their IT admins may have privileged access.
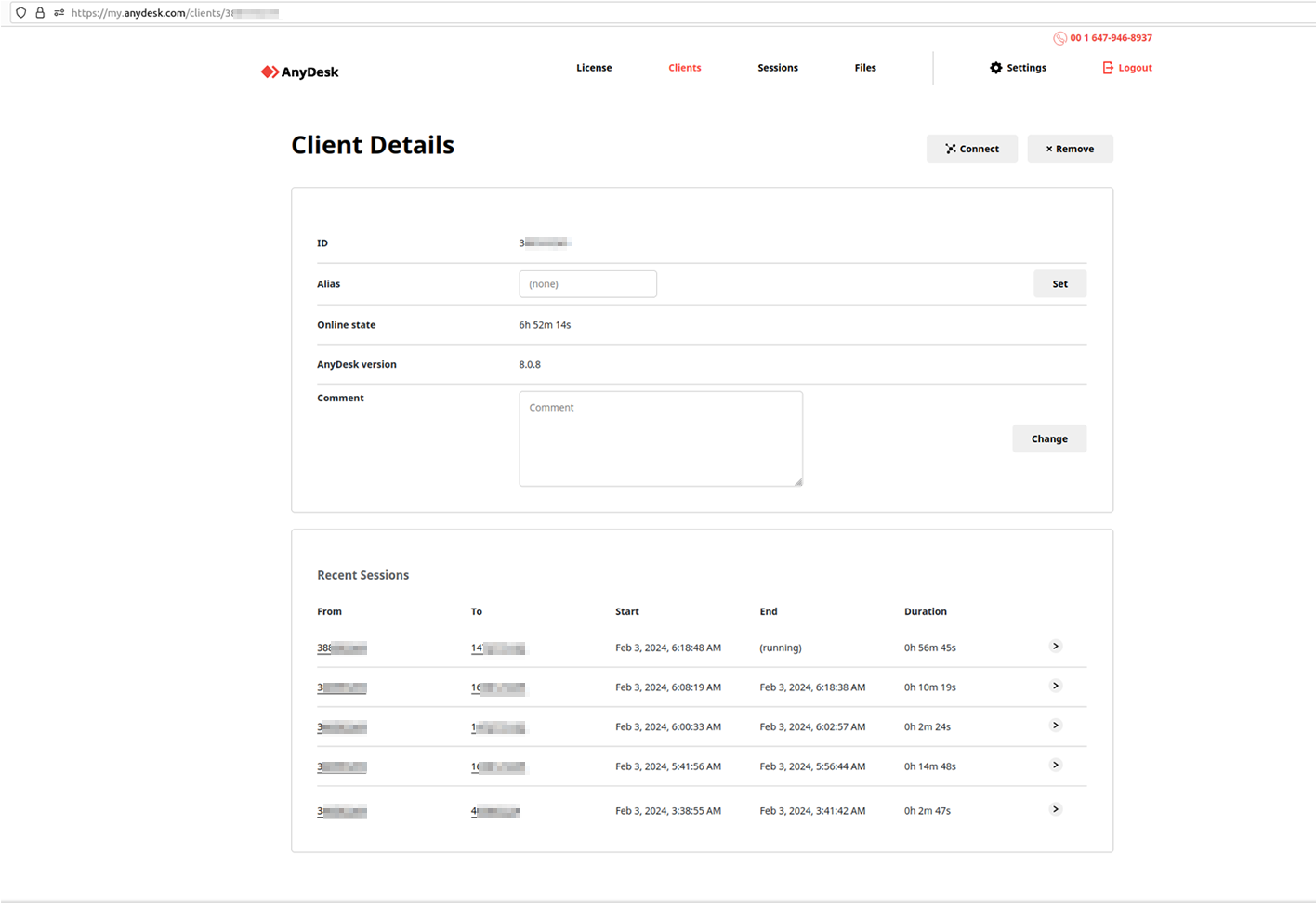
By gaining access to the AnyDesk portal, bad threat actors could learn meaningful details about the customers – including but not limited to the used license key, number of active connections, duration of sessions, customer ID and contact information, email associated with the account, and the total number of hosts with remote access management software activated, along with their online or offline status and IDs. This threat is particularly amplified by the risk of threat actors leveraging advanced TTPs to gain and maintain stealth access to one or more privileged IT admin accounts. This scenario has the potential to evolve into a more devastating supply-chain attack, impacting AnyDesk’s enterprise customers.
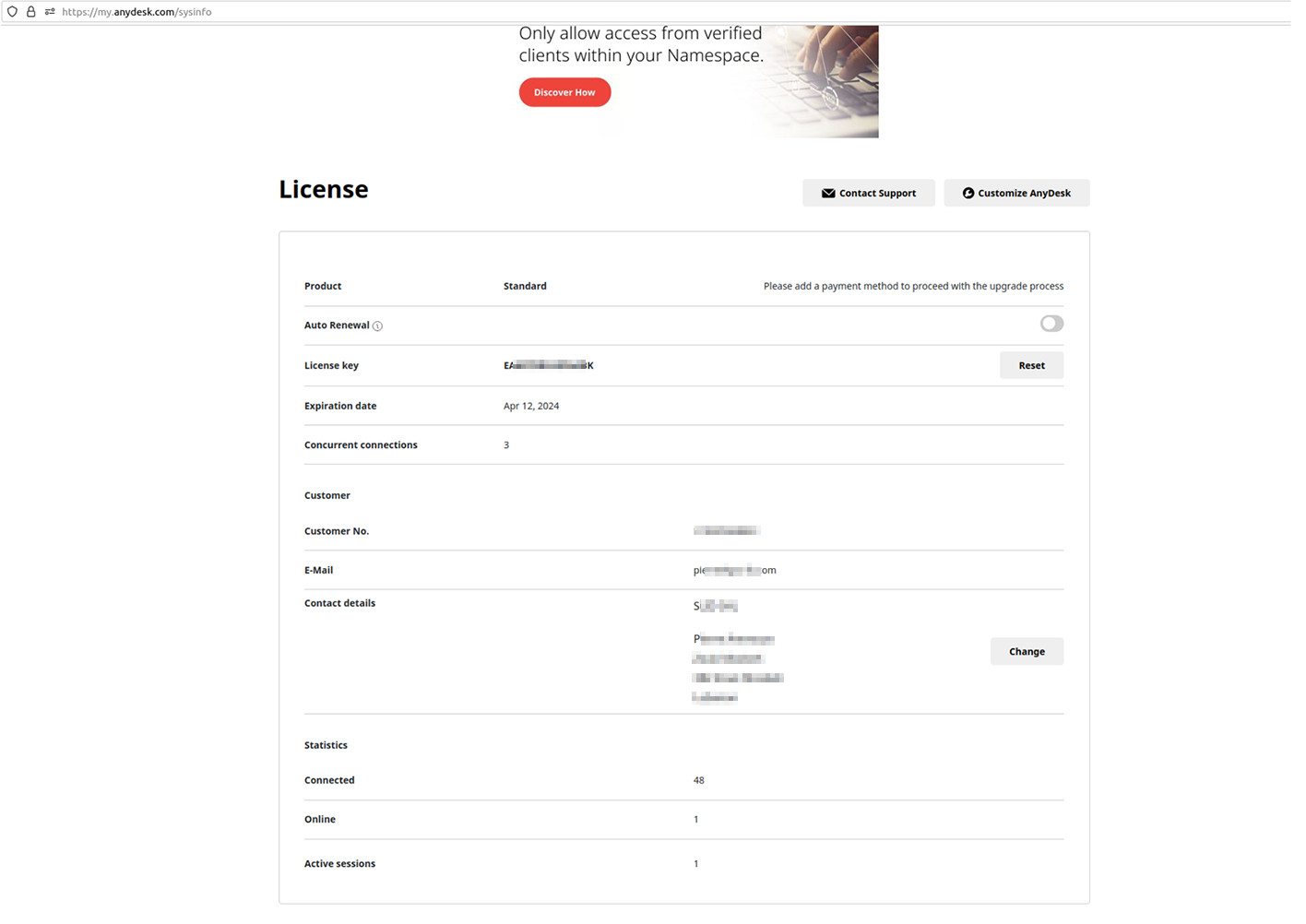
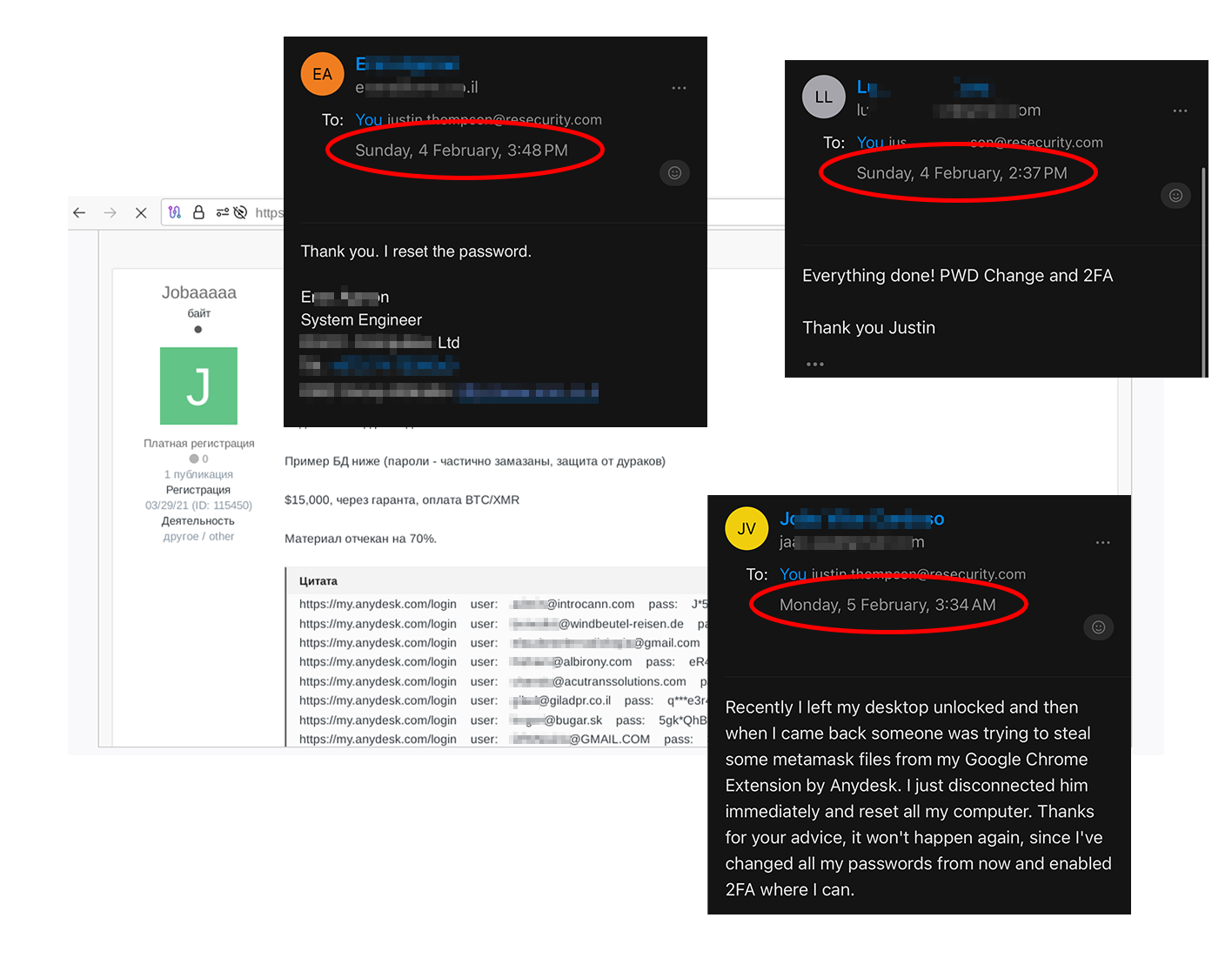
Notably, the timestamps visible on the shared screenshots by the actor illustrate successful unauthorized access dated February 3, 2024 (post-incident disclosure). This suggests not all customers have still not changed their access credentials, or this mechanism was still ongoing by the affected parties. Undoubtedly, the complexity of deploying proper remediation measures is more significant when servicing a large customer base, and such procedures may not be instantly executed, requiring proper planning. For example, this exact scenario could be leveraged by the threat actors concerned about losing previously acquired access. Therefore, proper planning and threat modeling are necessary evils for effective remediation programs. Notably, Resecurity discovered, via additional interactions with the threat actors, that the majority of exposed AnyDesk accounts listed on the Dark Web didn’t have 2FA enabled.
The availability of this data for cybercriminals could serve as a catalyst for new attacks, including targeted phishing campaigns. With additional data about a particular customer, cybercriminals significantly increase their odds of a successful account compromise. For example, one possible scenario could involve these details being used in malicious emails sent on behalf of the software vendor, managed services providers (MSPs), or IT outsourcing companies with the goal of obtaining sensitive information. In the hands of a sophisticated adversary, this entry point could also serve as a gateway to a devastating SolarWinds-style attack.
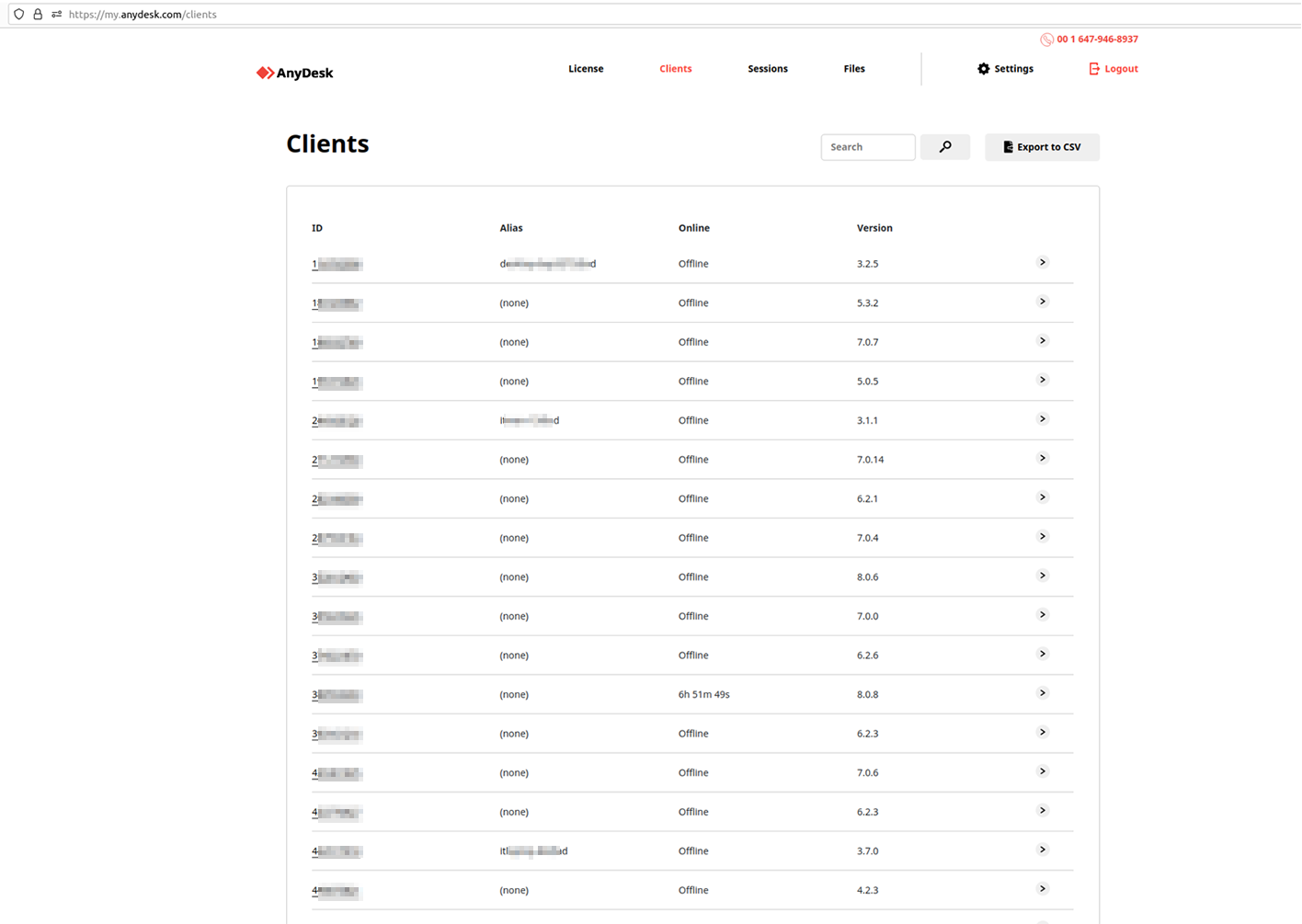
Some of the screenshots acquired from the actor contained customer notifications about AnyDesk’s planned migration to a new customer portal.
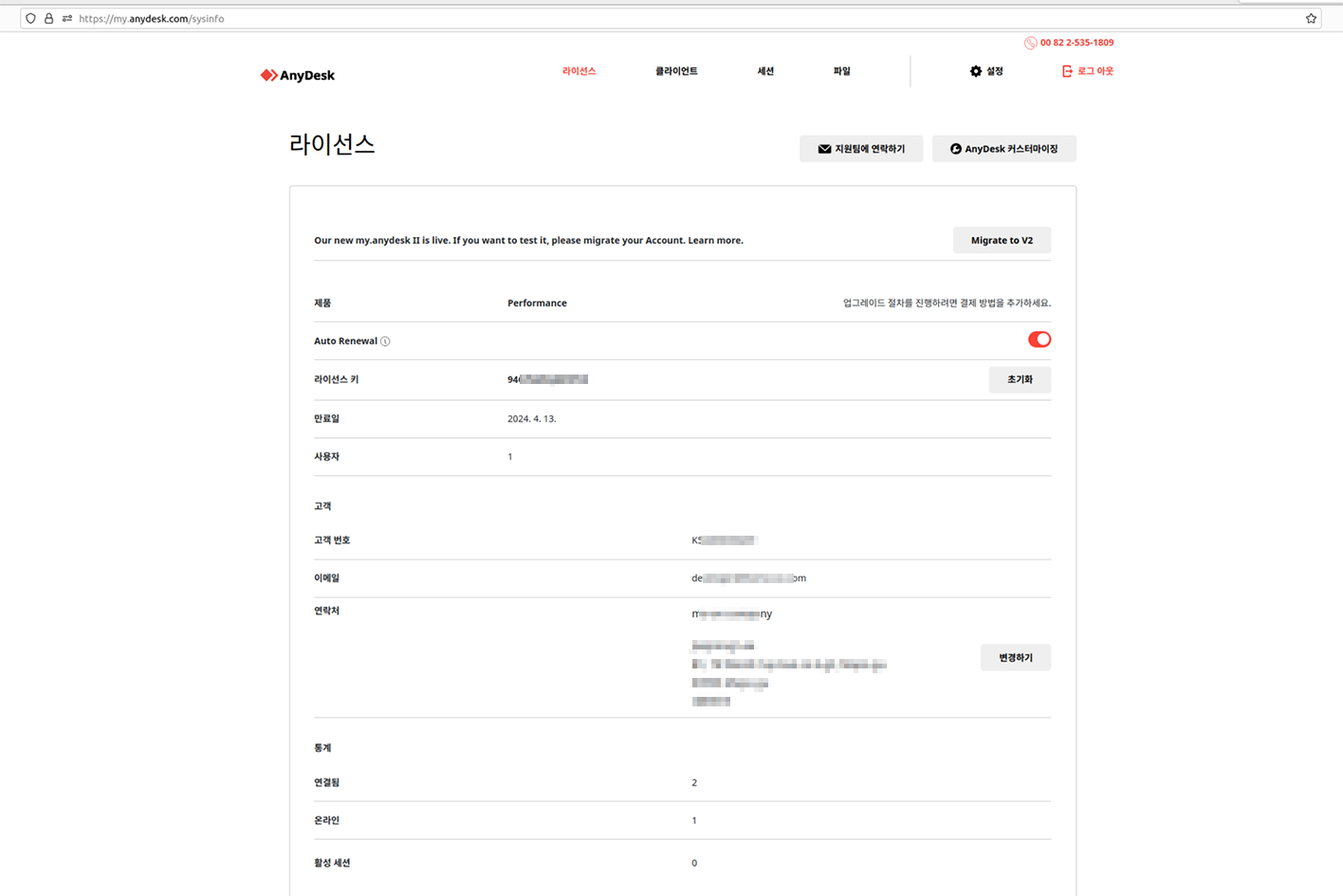
Notably, some of the screenshots acquired from the threat actor contained localization in other foreign languages, indicating an extremely geographically diverse range of potential victims.
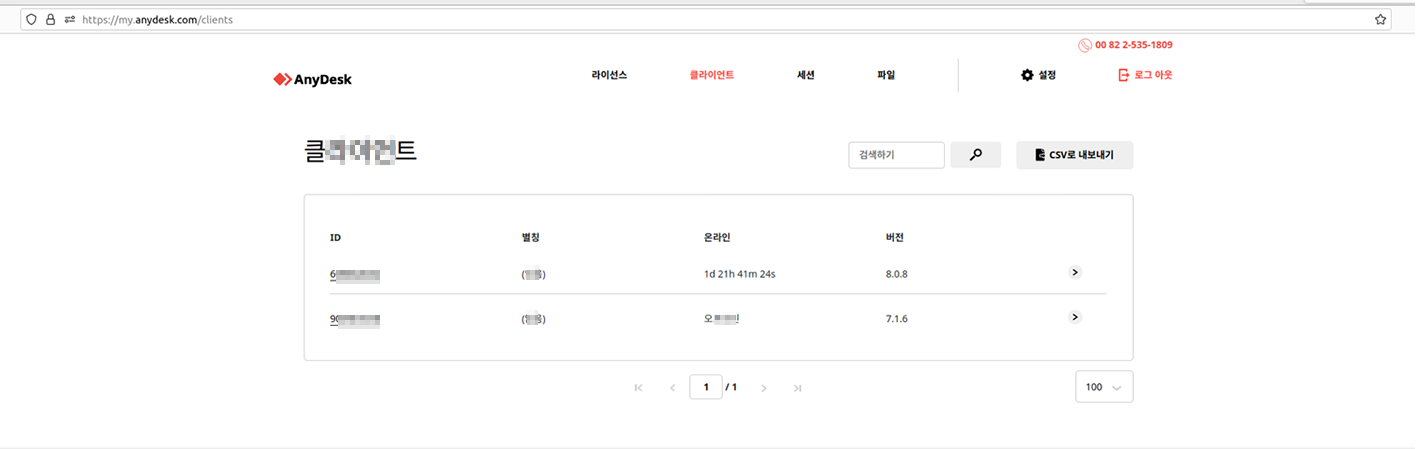
According to the services availability information page, AnyDesk informed their customers about planned maintenance starting on January 29th. During this period, the company disabled the ability to log in to the AnyDesk client. This measure was likely taken by the company as a security precaution during the incident containment.
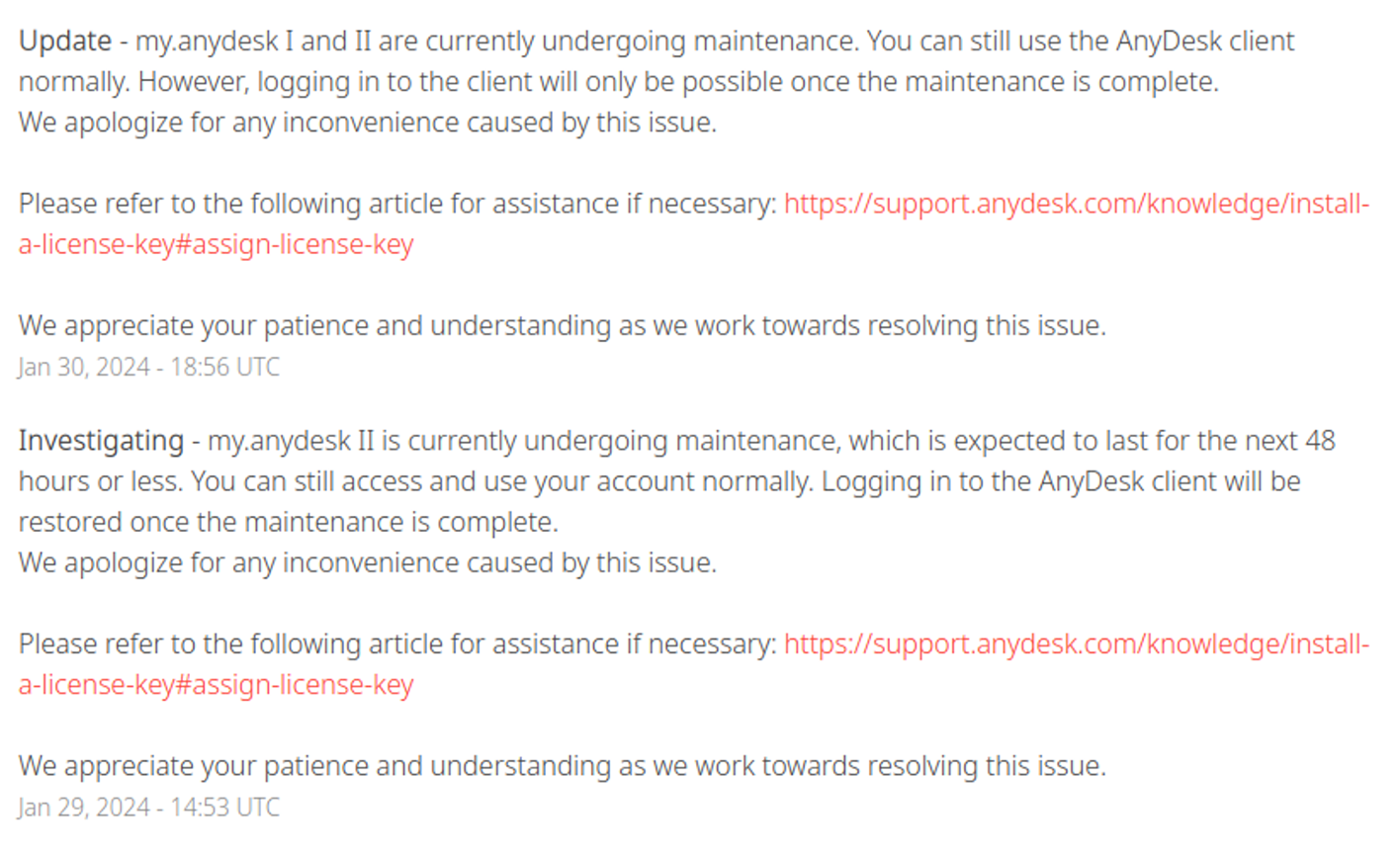
The login functionality was restored by February 1, 2024, with reference to available SSO and IDP.
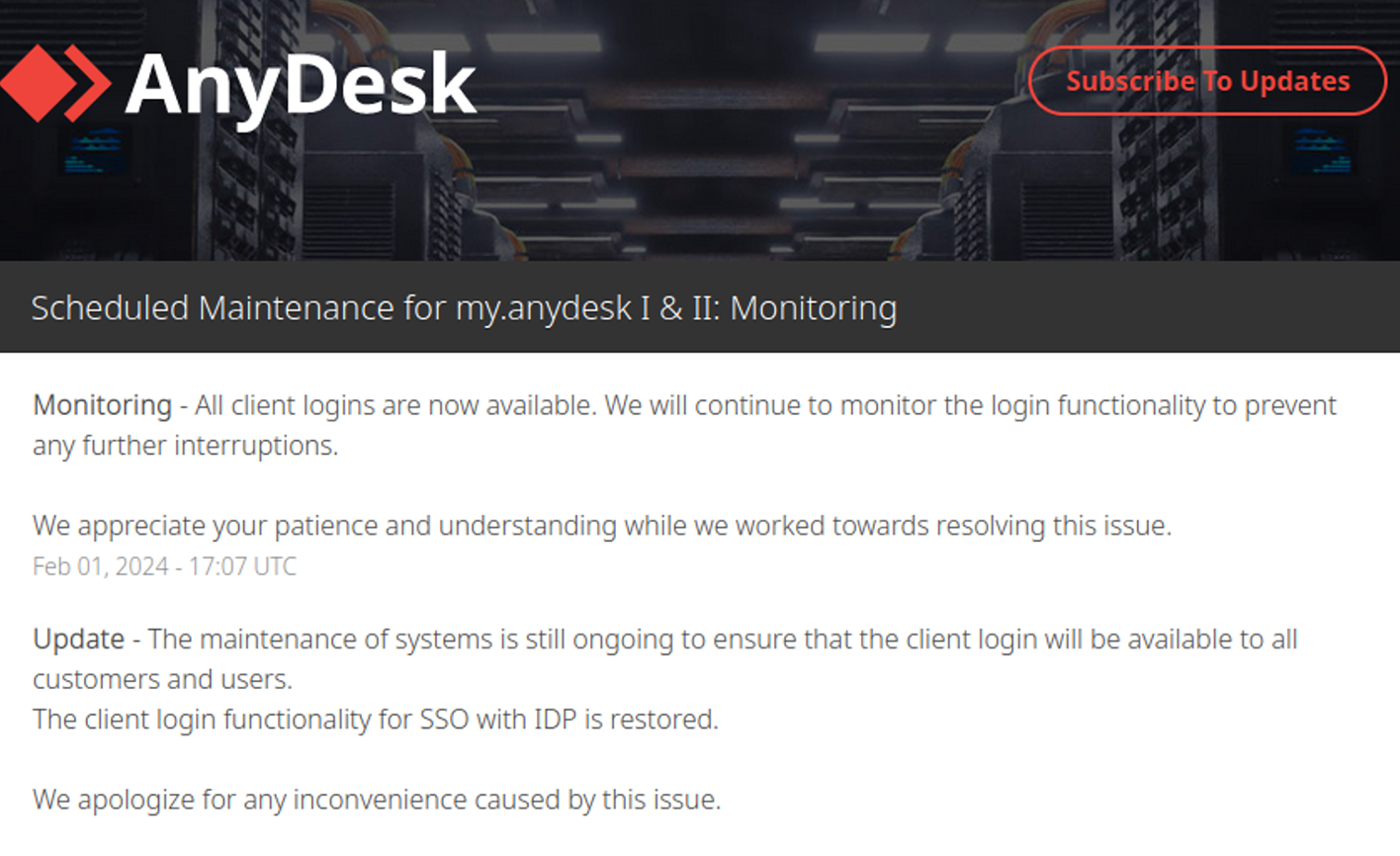
It is possible that cybercriminals familiar with the incident are hurrying to monetize available customer credentials via the Dark Web, with the awareness that AnyDesk may take proactive measures to reset their credentials. Such data could be extremely valuable for scammers, initial access brokers (IABs) and ransomware groups who are familiar with AnyDesk, and who have exploited the application for previous network intrusions.
Window of Exposure
A changelog for AnyDesk Windows version 8.0.8 showed it invalidated a previous code signing certificate on January 29. That suggests its previous code signing certificate was likely compromised.
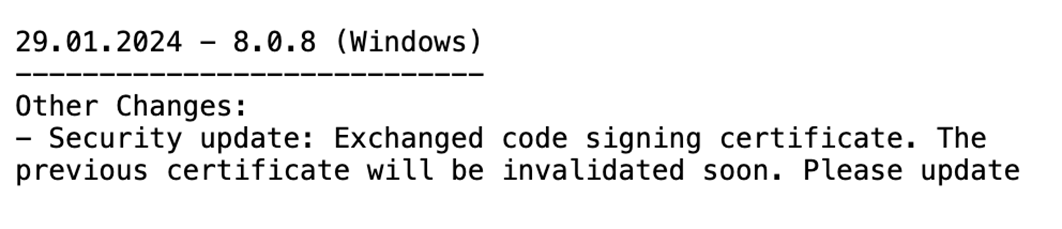
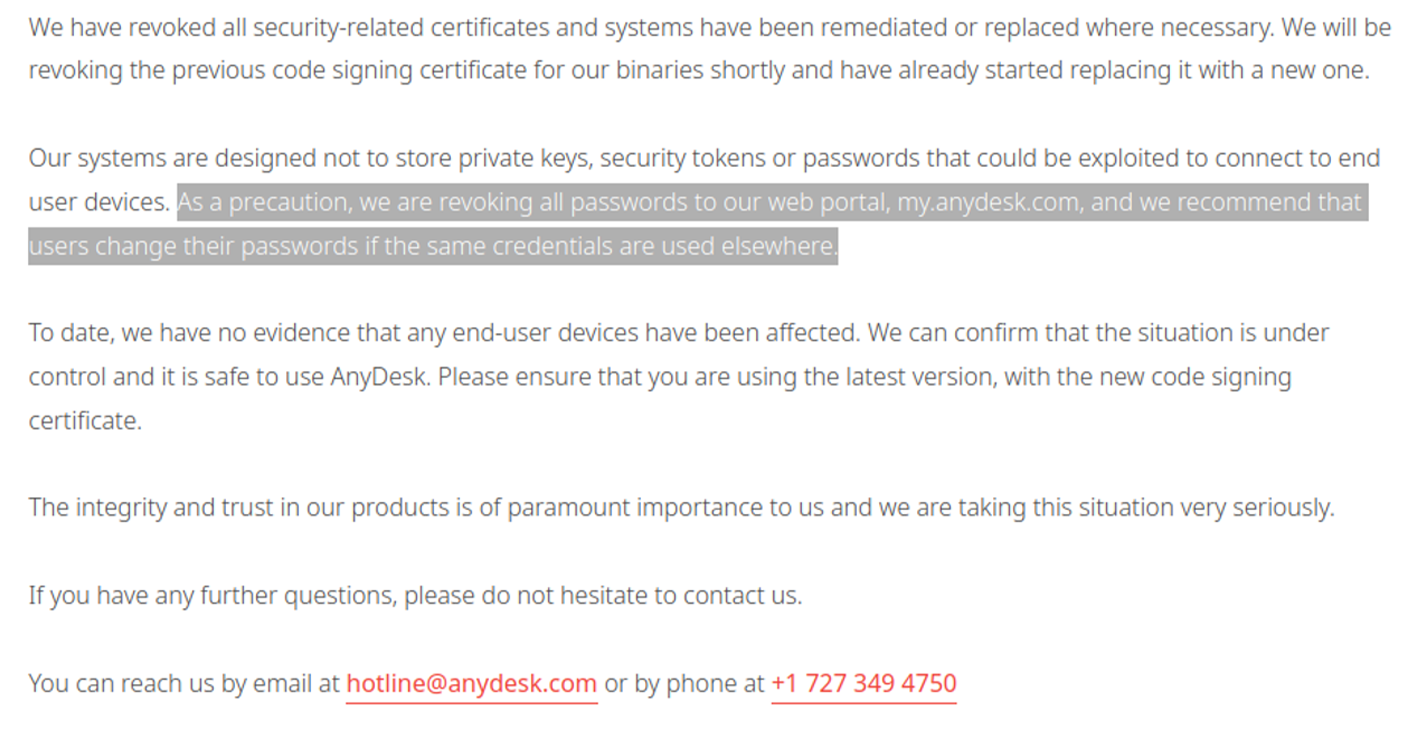
In the security advisory (Feb 2), AnyDesk stated they "have revoked all security-related certificates and systems have been remediated or replaced where necessary," and "as a precaution, we are revoking all passwords to our web portal, my.anydesk.com, and we recommend that users change their passwords if the same credentials are used elsewhere."
Based on feedback received from multiple victims from February 3-5, some impacted users were still unaware of AnyDesk's mitigation recommendations. These AnyDesk customers were still using their old passwords and had not yet enabled 2FA on their accounts.
Stay Aware and Proactive
Besides underground ransomware operators, online scammers have previously abused AnyDesk and operationalized it in various fraudulent schemes. AnyDesk describes three of the most common attack typologies on its website:
- Technicians from Microsoft claim they need to clean your device from malicious software and ask you to install AnyDesk for remote access.
- Scammers try to gain trust by pretending to represent a legitimate company. Microsoft will never cold-call you.
- Fictious AnyDesk support staff claims they need to patch a bug in Windows, even in cases when the victim is using a macOS device.
Unfortunately, scammers have been successful in using advanced social engineering techniques, leading victims to fall for scams, despite numerous warnings and advisories published by IT vendors and the cybersecurity community. An example of these security failures is described by one victim on Reddit:
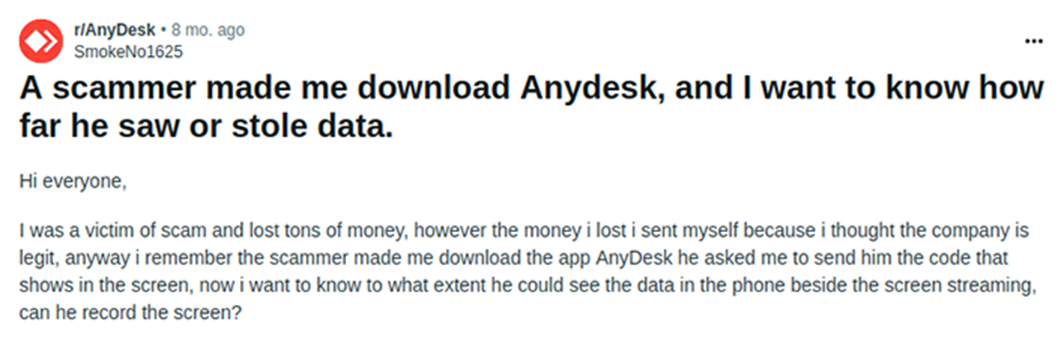
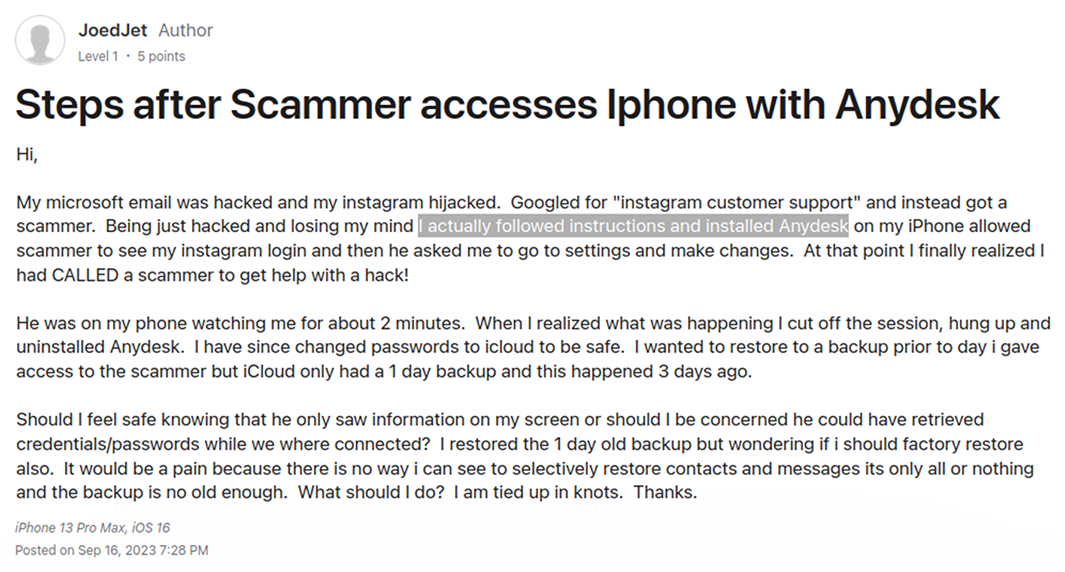
Some time ago, the Criminal Investigation Department (CID) and Reserve Bank of India (RBI) cautioned users about a type of online fraud, where scammers make fraudulent transactions by misusing the AnyDesk app installed on victims’ computers. Notably, this issue is also relevant for users on mobile devices. There are multiple instances where social engineering attacks have led to consumers being defrauded via the malicious installation of AnyDesk on their phone. This scenario attack typology is widely used for online banking theft. One victim shared their unfortunate experience on the Apple Community forum:
Notably, this issue is also relevant for users on mobile devices. There are multiple instances when consumers have been defrauded as a result of social engineering leading to AnyDesk installation on their phone. This scenario is widely used for online banking theft. One victim shared their experience on the Apple Community forum:
Based on Resecurity’s assessment, Dark Web actors have expressed a strong and growing interest in AnyDesk customer credentials. The opportunity to acquire AnyDesk credentials in bulk will be extremely attractive for actors involved in spam, online banking theft, business email compromise (BEC), and account takeover (ATO) activities.
Significance
The compromised AnyDesk credentials listed for sale on the Dark Web create a significant threat for the company’s individual and enterprise customers. The spectrum of risks associated with this leaks has proliferated exponentially, with attack scenarios ranging from the use of this data in downstream bank fraud and scam campaigns to targeted phishing and other types of malicious cyber activity. Resecurity informed AnyDesk and notified multiple consumers and enterprises whose credentials were exposed on the Dark Web. Notably, the activity with AnyDesk comes right after Cloudflare announced it was targeted, along with Microsoft and Hewlett Packard Enterprise disclosing cybersecurity incidents conducted by a suspected nation-state attacker known as Midnight Blizzard / Nobelium. Activity observed by Resecurity may also highlight the thin line between cybercrime and nation-state activity, where the latter could operate under the guise of a cybercriminal actor selling access on the Dark Web, after executing a specific campaign.
Mitigation Recommendations
Resecurity advises all AnyDesk customers to contact the company for further information regarding the potential impact on their organization. Passwords alone do not offer the necessary level of protection against sensitive credential leaks.
AnyDesk
also provides a whitelist
feature that
allows customers to whitelist people (AnyDesk IDs) they trust. This
ensures that only the persons whitelisted can connect to the
authorized user’s device. For businesses, whitelisting
a namespace adds
additional security, as only IDs that are part of that particular
namespace can connect.
Resecurity also strongly recommends the use of additional security measures, including available forms of MFA (Multi-Factor Authentication). As a proactive measure, it would be prudent to monitor unexpected password and MFA changes for customers accounts, suspicious sessions, and possible emails sent on behalf of other entities referencing AnyDesk account information.
References
- Two-Factor Authentication
https://support.anydesk.com/knowledge/two-factor-authentication - AnyDesk Abuse Management
https://support.anydesk.com/knowledge/abuse-management - How to Avoid Remote Access Scams
https://anydesk.com/en/abuse-prevention - AnyDesk says hackers breached its production servers, reset passwords
https://www.bleepingcomputer.com/news/security/anydesk-says-hackers-breached-its-production-servers-reset-passwords/? - How to Escape the “Phishing Net” Successfully
https://blog.anydesk.com/phishing-hacks/

