
Intro
According to Time Magazine, “2024 is not just an election year. It’s perhaps the election year.” With “more voters than ever in history” heading to the polls in 2024, Resecurity has identified a growing trend of malicious cyber-activity targeting sovereign elections globally. In an era of unprecedented geopolitical volatility, this trend is particularly concerning, as Time Magazine notes that 64 countries (plus the European Union) are set to hold national elections this year.
Collectively, some two billion eligible voters represented in these races constitute roughly 49% of the global population. For many of these voters, the results of these elections “will prove consequential for years to come,” according to Time Magazine. By far, the most significant contest this year is the U.S. presidential election, the outcome of which could radically alter the destinies of geopolitical relations and military conflicts globally.
FBI Director Christopher Wray acknowledged in January that the threat of election interference in the U.S. race is unprecedented as “more nation-states want to get in the business of trying to interfere or at least influence elections.” In this volatile backdrop, Resecurity noted that the proportion of global elections targeted by cyberattacks increased from 10 percent in 2015 to 26 percent in 2022.
The Canadian Centre for Cyber Security (CCCS) published a report right before the start of 2024 that said cyberattacks targeting elections are increasing, echoing our findings. The proportion of global elections targeted by cyberattacks has increased from 10 percent in 2015, to 26 percent in 2022. Over the course of this reporting period, approximately 25 percent and 35 percent of the countries targeted in these attacks were NATO and OECD countries, respectively.
Besides the continued targeting of the U.S. and its allies, activity observed by Resecurity between 2023 and early 2024 indicates a 100 percent increase from the previous analysis period. This assessment is based on multiple incidents that Resecurity observed and reported to relevant authorities globally in the following jurisdictions: Africa, the European Union, the United Kingdom, Ecuador, Bangladesh, Indonesia, Israel, Iraq, Lebanon, Turkey, and Mexico.
According to a report released by the National Counterintelligence and Security Center (NCSC) on foreign threats to elections, the primary types of malicious typologies targeting election integrity fall into five distinct categories:
- Cyber operations targeting election infrastructure,
- Cyber operations targeting political parties, campaigns, and public officials,
- Covert influence operations to assist or harm political organizations, campaigns, or public officials,
- Covert influence operations to influence public opinion and sow division,
- Covert efforts to influence policymakers and the public
These types of incidents generally act as precursors for more significant malicious activity that can be further amplified by foreign interference campaigns. Besides cyberespionage, threat actors aim to sow uncertainty about the integrity of elections via operations that aim to disrupt and manipulate public opinion globally. Unfortunately, these incidents remain complicated from an investigation perspective and are often imperceptible to the public.
Amidst historic geopolitical volatility and uncertainty, marked by escalating conflicts throughout the Middle East and Eastern Europe, securing elections from hostile cyber-threats has become vital to the preservation of the global democratic order. In the following report, Resecurity will discuss malign cyber-activity targeting elections in more than 17 countries all over the world.
Leak of D.C. voters' information – cyber-attack on DCBOE
On October 5, 2023, the infamous Ransomed.vc syndicate created a data-leak entry for the District of Columbia Board of Elections (DCBOE). The threat actors allegedly stole the personally identifying information (PII) of 600,000 D.C. voters. The gang published the data of one registered voter as proof (including the individual's name, registration ID, voter ID, partial social security number, driver's license number, date of birth, phone number, email address, and more).
While Ransomed.vc claimed responsibility for the attack, security researchers found that the same dataset was listed for sale two days earlier on the underground hacking communities Breach Forums and Sinister.ly by a user named "pwncoder." Those posts have since been deleted.
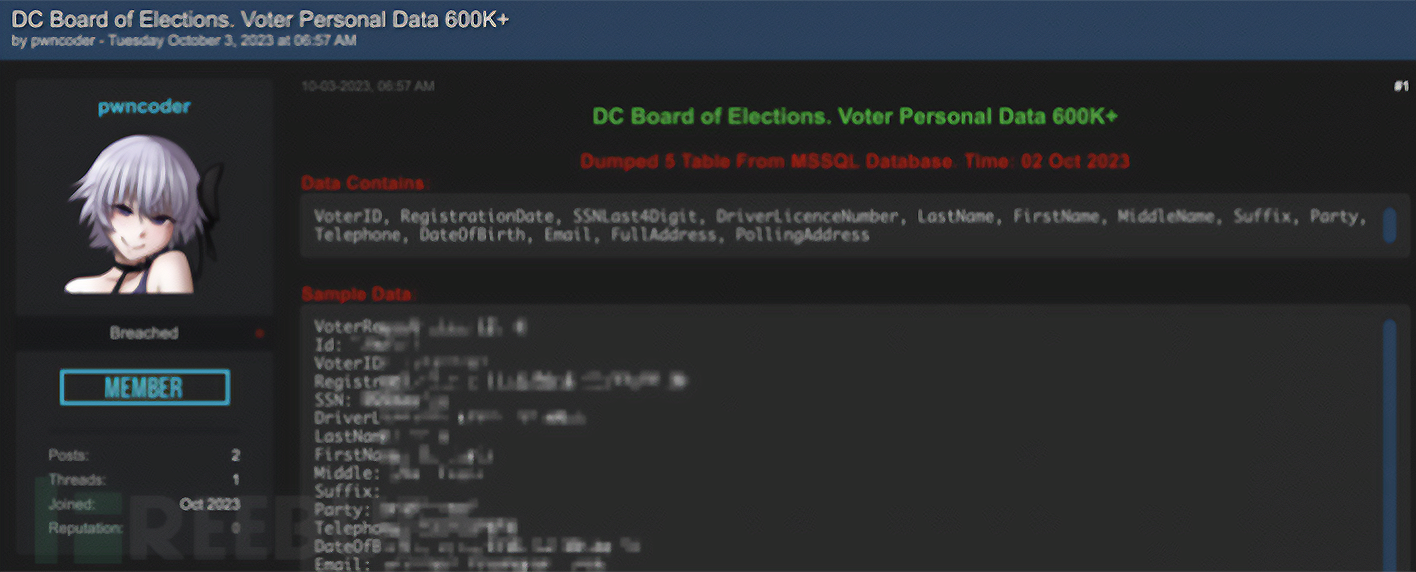
Resecurity shared extensive details about Ransomed.vc in a previous report documenting attacks against large Japanese companies. DCBOE acknowledged that a cyber-incident had taken place and launched an internal investigation. The organization issued a statement that said its internal databases and servers were not compromised. Assuming data was successfully exfiltrated, threat actors likely obtained it through a compromised third party.
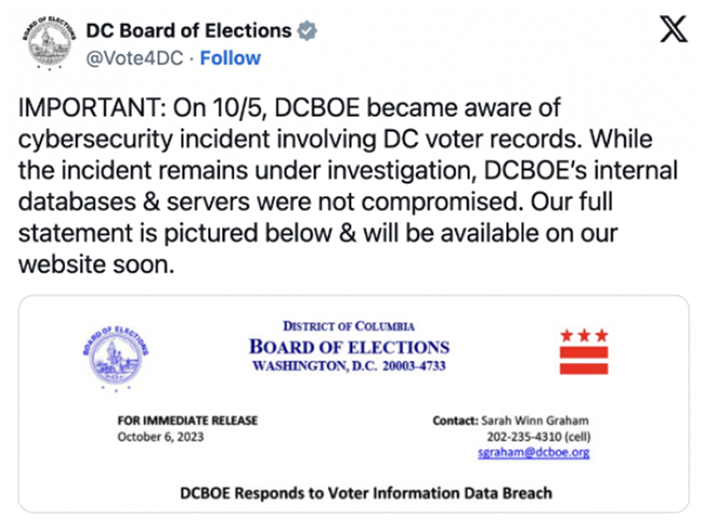
According to the DCBOE's investigation, the attackers accessed the information through the web server of DataNet Systems, the hosting provider for Washington D.C.'s election authority.
Just over two weeks after the DCBOE’s initial statement, they issued a follow-up announcement stating that the “full voter roll MAY have been accessed in the breach of DataNet Systems’ database server.”

Prior to this cyber-incident, the May 2023 hack of the Hillsborough County Supervisor of Elections Office in Florida exposed 58,000 voters’ private information. An unauthorized user appears to have illegally accessed and copied files containing PII - including SSN and DL numbers - primarily from files to conduct voter registration list maintenance, according to Hillsborough Supervisor of Elections Craig Latimer. It is unlikely that this incident is linked to the DCBOE breach. However, the HCSEO attack further illustrates the threat posed by voter data theft to the integrity of American elections.
Highlighting this risk scenario is the indictment of two Iranian nationals who were charged for conducting a cyber-enabled campaign to disrupt the 2020 U.S. Presidential election. This operation involved intimidating American voters, undermining voter confidence, and spreading discord.
The suspects obtained confidential U.S. voter information, sent threatening emails, and created a video that transmitted disinformation about election infrastructure vulnerabilities. These threat actors’ activities were part of a broader effort to manipulate U.S. public opinion, highlighting the evolving nature of international cyber threats to the democratic process.
Vast Voter Data Leaks Cast Shadow Over Indonesia’s 2024 Presidential Election
Resecurity found that Indonesia is increasingly being targeted by cyber-threat actors who have staged attacks that pose significant long-term risks to the integrity of the country’s elections. These findings coincide with the critical and fast-approaching Indonesian presidential election set to take place in February this year. This contest may have significant implications for the political destiny of the majority Muslim Southeast Asian (SEA) nation, which is also the third-largest democracy in the world.
One particularly alarming breach tracked by HUNTER analysts led to the leak of 6.8 million voter records related to the 2017 Jakarta gubernatorial election on the ‘eleakstore’ and Hydra Market cybercriminal forums. The sensitive data exposed in this breach has set the stage for a more destabilizing attack scenario targeting the Indonesian general election this year.
The Jakarta gubernatorial election is particularly significant to Indonesia because the city is both the capital of the country and its largest metropolis. Threat actors obtained Jakarta voters’ records after breaching and exfiltrating data from web resources presumably related to the DKI Jakarta Provincial government. The structure of the data leaked is arranged by family card number (no_kk), single identity number (NIK), name (nama), place of birth (tmpt_lahir), birth date (tgl_lahir), gender, address (alamat), city (kota), and district (kecamatan).
Just before the start of 2024, an individual known as Jimbo disclosed details regarding a suspected breach of the General Elections Commission of Indonesia's (KPU) information system. This breach reportedly involves a substantial database containing records of numerous citizens, totaling 252,327,304 entries. Jimbo has put this database up for sale at a price of $74,000, equivalent to two Bitcoins. The data set in question is said to include PII, including passport details.
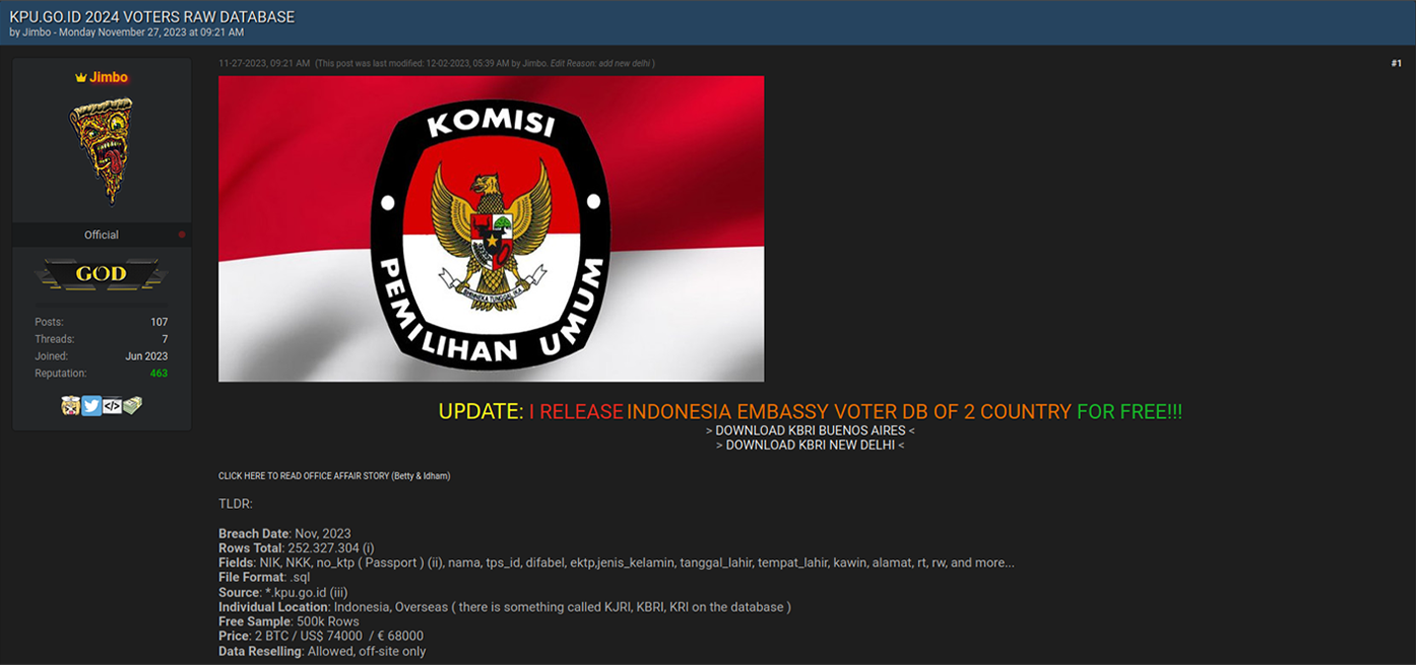
The motive behind this attack may be something other than foreign interference and cyberespionage. Notably, the Civic Media Observatory, a research project sponsored by the Global Voices nonprofit foundation, highlighted the important issue of gender-based cyberbullying in Indonesia. Specifically, conservative Muslim narratives try to “silence women online” in Indonesia, according to CMO research . These initiatives include the use of “cyber-troops,” or hacktivists focused on harassing and repressing women. While these claims should be investigated in deeper detail, homegrown opposition to gender equality could be a possible factor behind these data breaches.
Notably, the Indonesian government already investigated a similar breach in 2021. Three years ago, a threat actor claimed to have leaked and sold the personal data of at least 279 million Indonesians on the Dark Web. The Ministry of Communication and Information said at the time that it investigated the suspected data leak and its sale on Raid Forums, which was seized by law enforcement in 2022. Information related to the alleged leak of Indonesians' data first surfaced on social media, with reports claiming that these records were stolen from the Health Care and Social Security Agency (BPJS Kesehatan). The ministry's spokesperson, Dedy Permadi, said investigating a data leak of that magnitude would take time.
In this context, it’s possible that the data leaked by Jimbo in November 2023 may actually be a case of threat actors repurposing previously compromised data, as Indonesian voter PII remains sufficiently fresh for adversarial exploitation.
Leak Of 6.5 Million Israeli Voter Records Highlights Growing Cyber-Threats To Democracy
Analysts from Resecurity’s HUNTER (HUMINT) unit identified a data leak of 6,453,254 Israeli voter records on the eleaks cybercriminal forum. Records exposed in this leak include Israeli ID number, gender, family name, first name, city, street and house number, telephone number, name of the father, the names of the officials in charge of the voting area, ballot number, ballot address, voter transportation means, language spoken by the voter, and more.
The data leak, which was first flagged around 2021, has been reused multiple times, including at the start of the latest Israel-Gaza conflict, with bad actors weaponizing it to target specific individuals. Specifically, threat actors cherry-picked data from the dump to threaten Israeli military personnel and dox their family members in 2023.
Resecurity traced this leak back to a breach of Elector, an Israeli software application used to manage political campaigns across races varying from national to municipal elections and at the primary level. This software can also assist in managing election campaigns within private organizations, according to the Elector website. The Elector leak is just the latest example of the growing value of voter data for adversaries who are seeking to interfere in, manipulate, or otherwise disrupt democracies globally.
The application developer of this campaign management tool is Elector Software Ltd. The company is based in Ashkelon, Israel. The Elector app is compatible with both the iOS and Android operating systems. Elector is also available in desktop versions. Furthermore, this software has been used in various American elections, helping unspecified candidates prevail in various races, according to the company website.
The Elector app is available for download via the App Store and authenticates users by phone number.
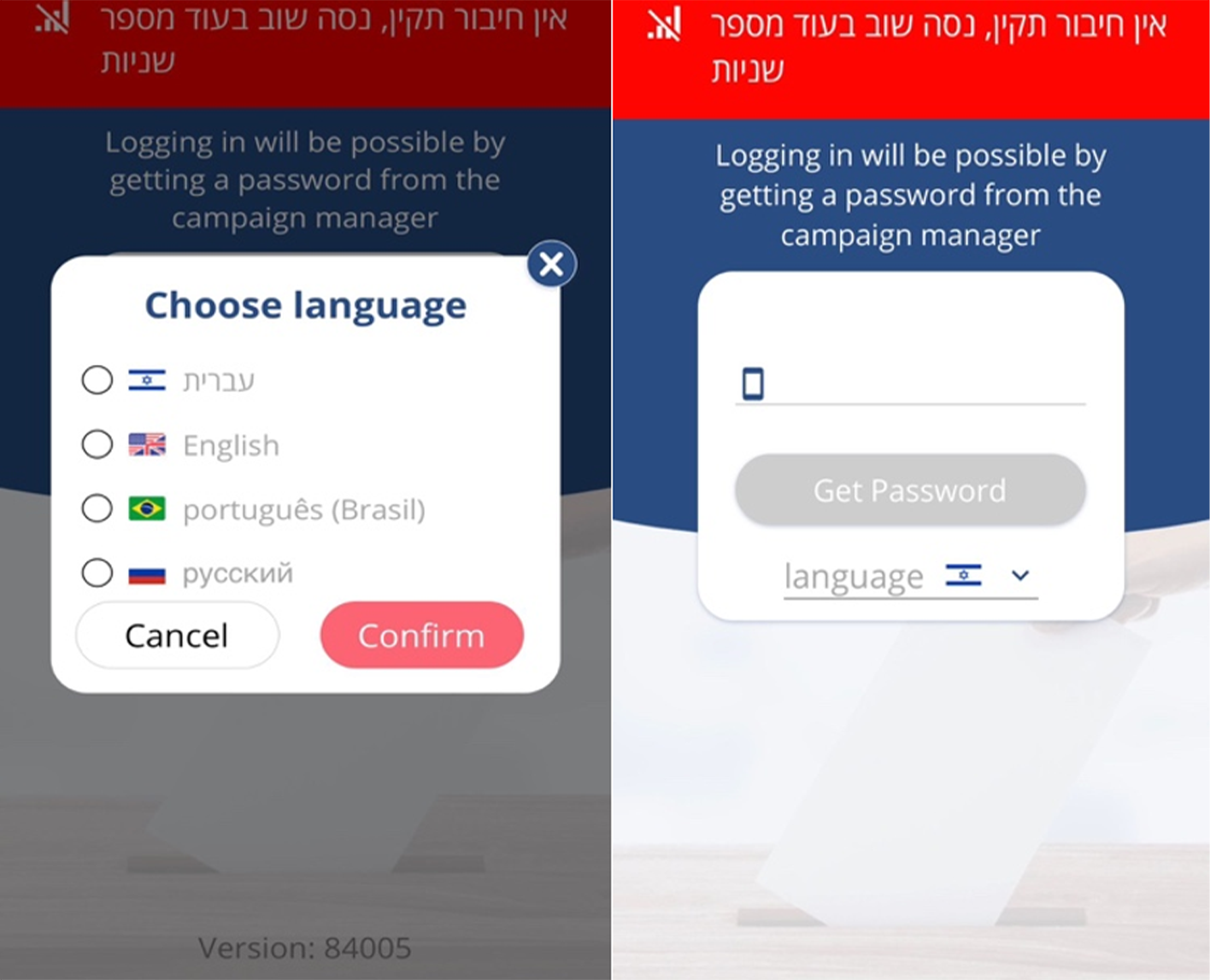
When interacting with the Elector app, HUNTER investigators quickly learned it was trivial to access voters' personal information. Whoever exploited Elector's website did so by using their web browser to perform a standard source-code request on the Elector Website. Even the most basic user can easily perform this routine action on virtually any web browser. The exposed source code included an internal link to the Elector website, which read, among other things, “get-admins-users.”
By entering the above link in their browser, the threat actor was able to see the login information of all users with the highest levels of information-access permissions. Basically, manipulating this link exposed all of Elector’s system admins’ username and password pairs in plain text in the browser’s page-source window. Logging into Elector and downloading the entire registry was thus a trivial task.
Resecurity hazards to speculate who was behind this leak. The threat actor or actors behind this breach could have been anyone from a financially motivated cybercriminal, a nation-state adversary, or a malicious insider. Absent more contextual information that likely only Elector would be privy to, each of the three previously described scenarios has the same degree of probability.
Approximately 6,453,254 Israeli voter records collected through 2021 were exposed in this leak. Prior to the release of these records in July 2022, Israeli political parties had undertaken a comprehensive operation to collect vast amounts of information about the political views of Israeli voters and other personal elector data. Beyond traditional data inputs, some collection initiatives managed to acquire Israeli voters’ medical and psychographic data, for example.
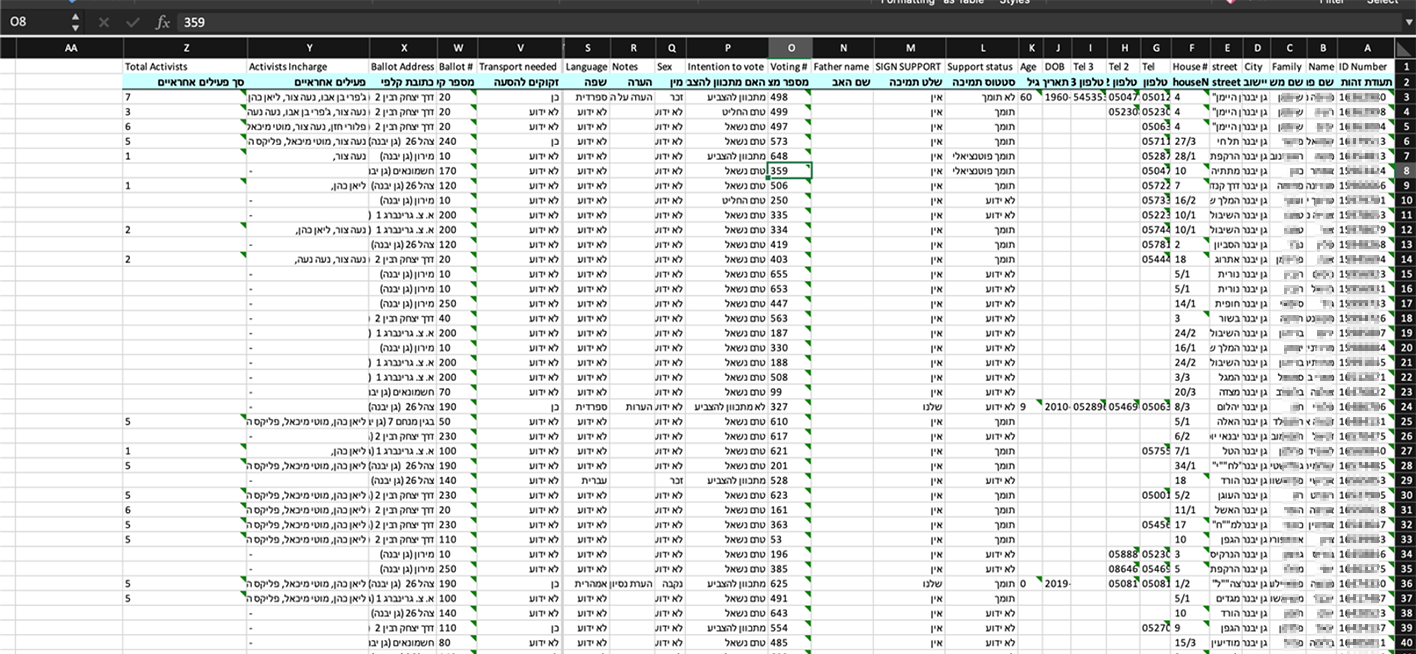
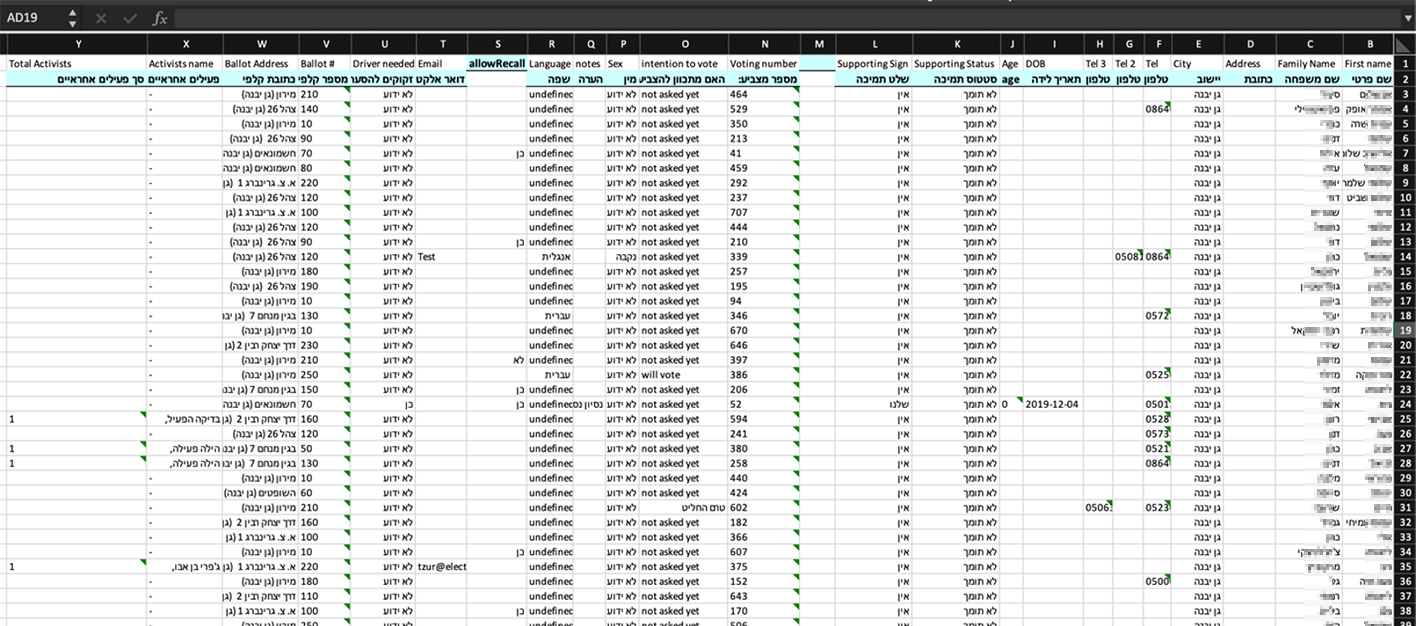
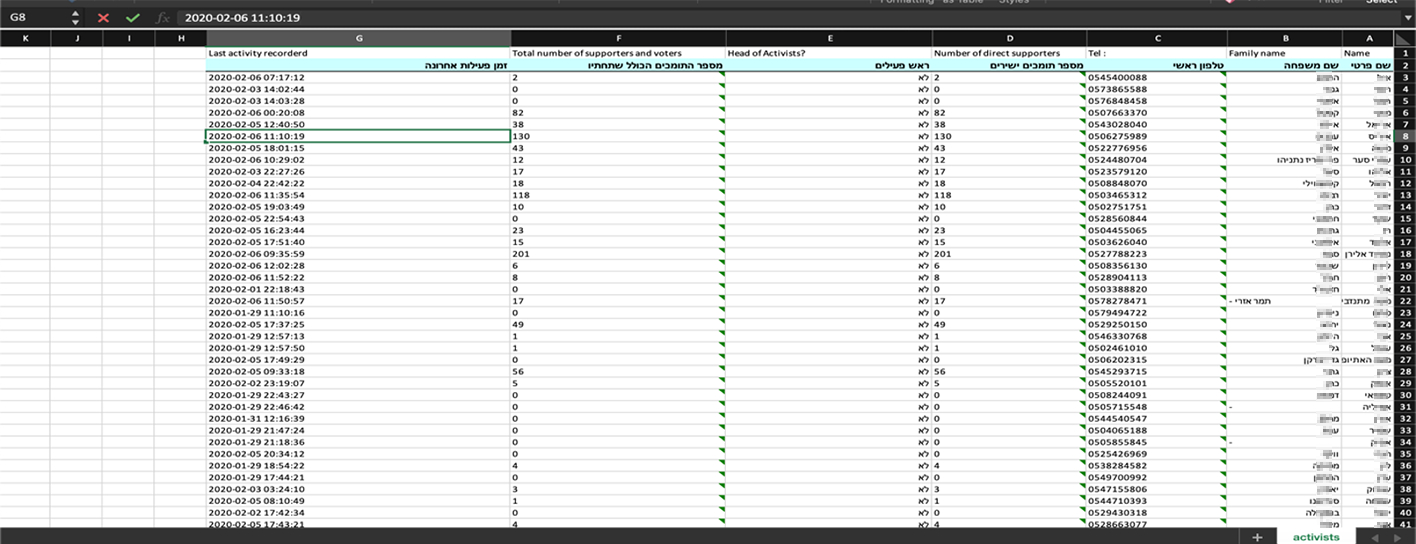
The Elector app is a significant force multiplier for its customers. This tool helps political campaigns collect sensitive personal information about voters throughout the year. Elector can also be used to promote voter participation. The leak of Elector-sourced Israeli voter data may not only violate the privacy of the country's citizens but also open the door for propaganda tailored to manipulate Israelis’ personal views and demographic inclinations. In this regard, the threat is similar to the dubious business model exposed in the Cambridge-Analytica scandal. The leakage of the Elector database also creates the risk of discrimination based on political bias, particularly in the context of hiring.
Ecuador
Beyond hack-and-leak operations, threat actors may also seek to disrupt the availability of the online systems countries use to collect votes. In August, Ecuador, a country that has been increasingly destabilized by drug cartel-related violence, experienced a cyberattack that impacted the absentee voting component of its national election systems. This attack prevented many of the country's 120,000 overseas voters from accessing the country's voting system before the polls closed.
This disruption was caused by malicious intrusions targeting the country's telematic voting platform, according to Ecuador’s National Electoral Council President Diana Atamaint. In a press conference, the election official also emphasized that votes which had been previously cast were not compromised in the attacks. Moreover, overseas voters based in Europe were particularly affected by the incident, noted Atamaint in a separate interview.
"Electoral authorities will analyze within the framework of the law what is appropriate to do," Atamaint said at the time. Ecuadorians based in Madrid protested their inability to cast their votes following the incident.
Lebanon
January 19, 2024 - the group known as R00Tk1T CYBER TEAM recently targeted Qatar and Malaysia then released a JSON dump with 90,000 voters from the past Parliamentary Elections in Lebanon. The records only contain details about citizens residing in Beirut. The total number of the affected victims remains unclear. Notably, this data was never previously published on the Dark Web and was likely released with the intention of triggering social uncertainty in the upcoming elections scheduled for 2026.
Besides detailed PII, the data also includes the following fields related to voting preferences:
- voterId
- universalVoterKeyId
- ballotBox
- votingCenter
- voterKeyTitle
- voterKeyNumber
- voterKeyPhoneNum
- hasVoted
- politicalAffiliationObj
- politicalAffiliationName
- politicalAffiliationId
- preferredPoliticalAffiliationObj
- preferredPoliticalAffiliationName
- preferredPoliticalAffiliationId
- preferedVotingListObj
- preferedVotingListName
- preferedVotingListId
- preferedCandidateName
Screenshot from JSON dump:

Turkey
In addition to direct attacks on election systems and their databases, threat actors may also target specific political parties and their members. For example, threat actors leaked some 9,352,148 records related to Turkey’s Justice and Development Party. This data leak encompasses JDP records from 2016, but threat actors were still recycling these records on the Dark Web as recently as last year (2023).
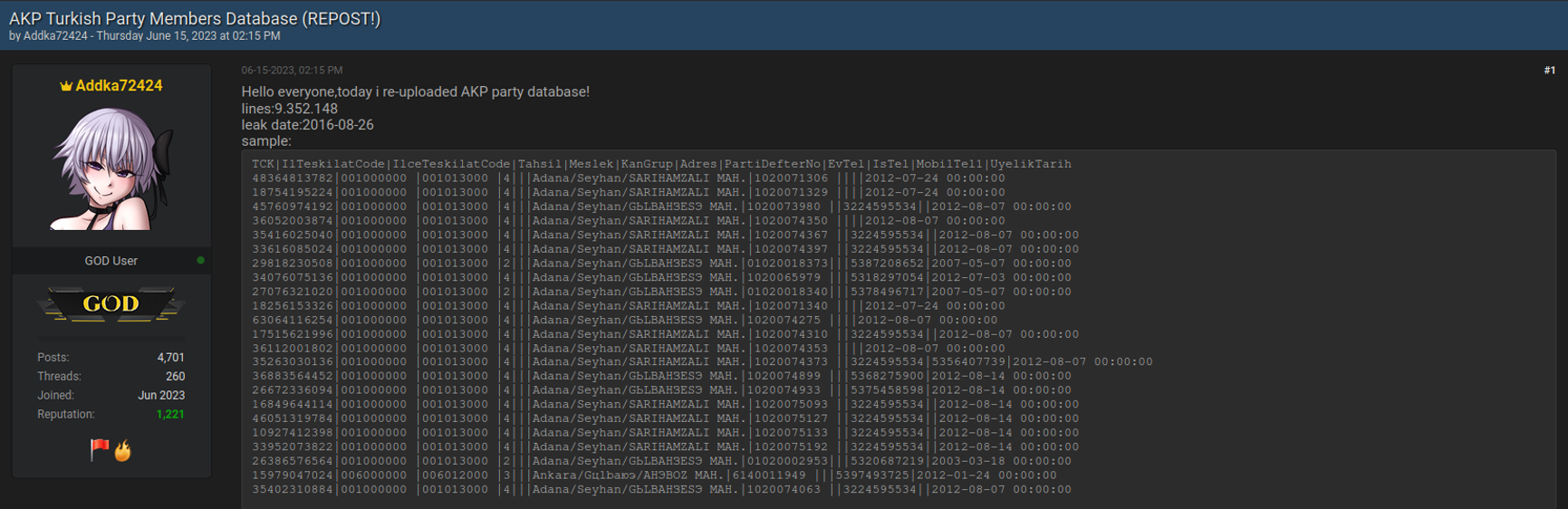
Another group known as KromSec leaked information about members of Turkey’s Hüdapar Party, also known as The Free Cause Party. This political group is a Kurdish Sunni Islamist political party. The leaked database included extensive information about their followers, including but not limited to:
- Name and Surname
- National ID
- Phone Number
- Mail Address
- Address
- Job
- Educational status
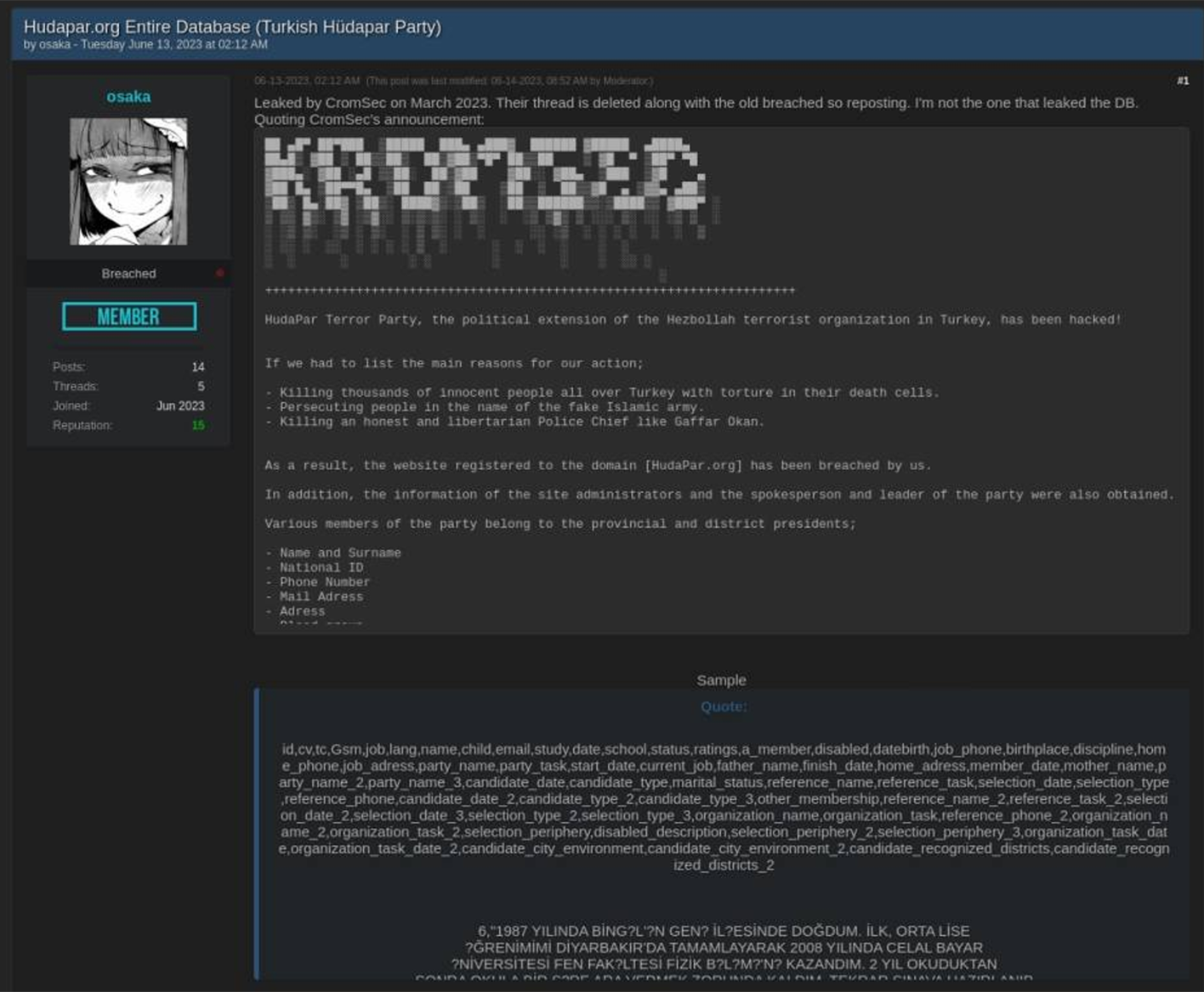
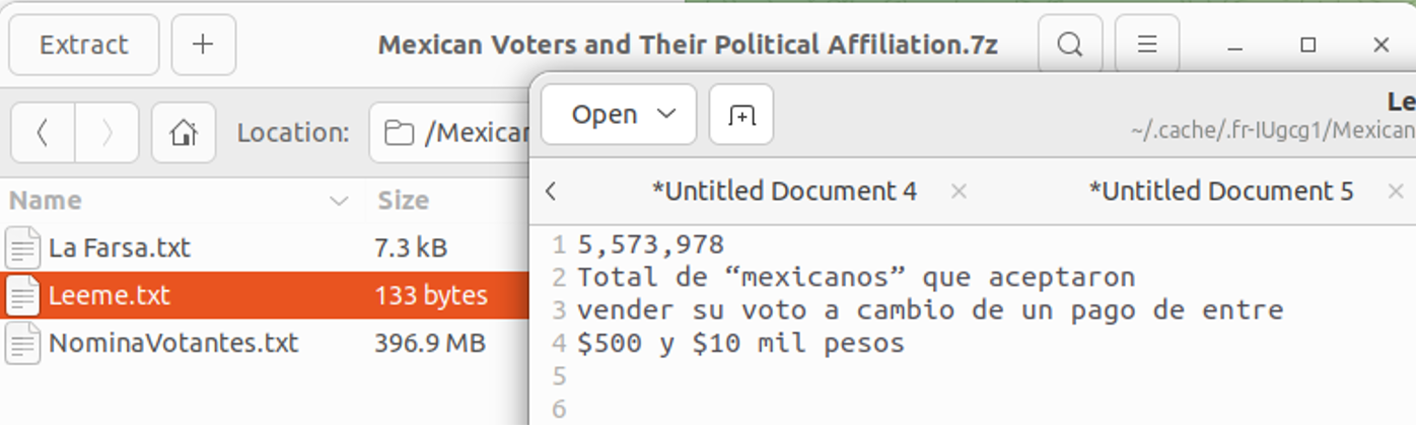
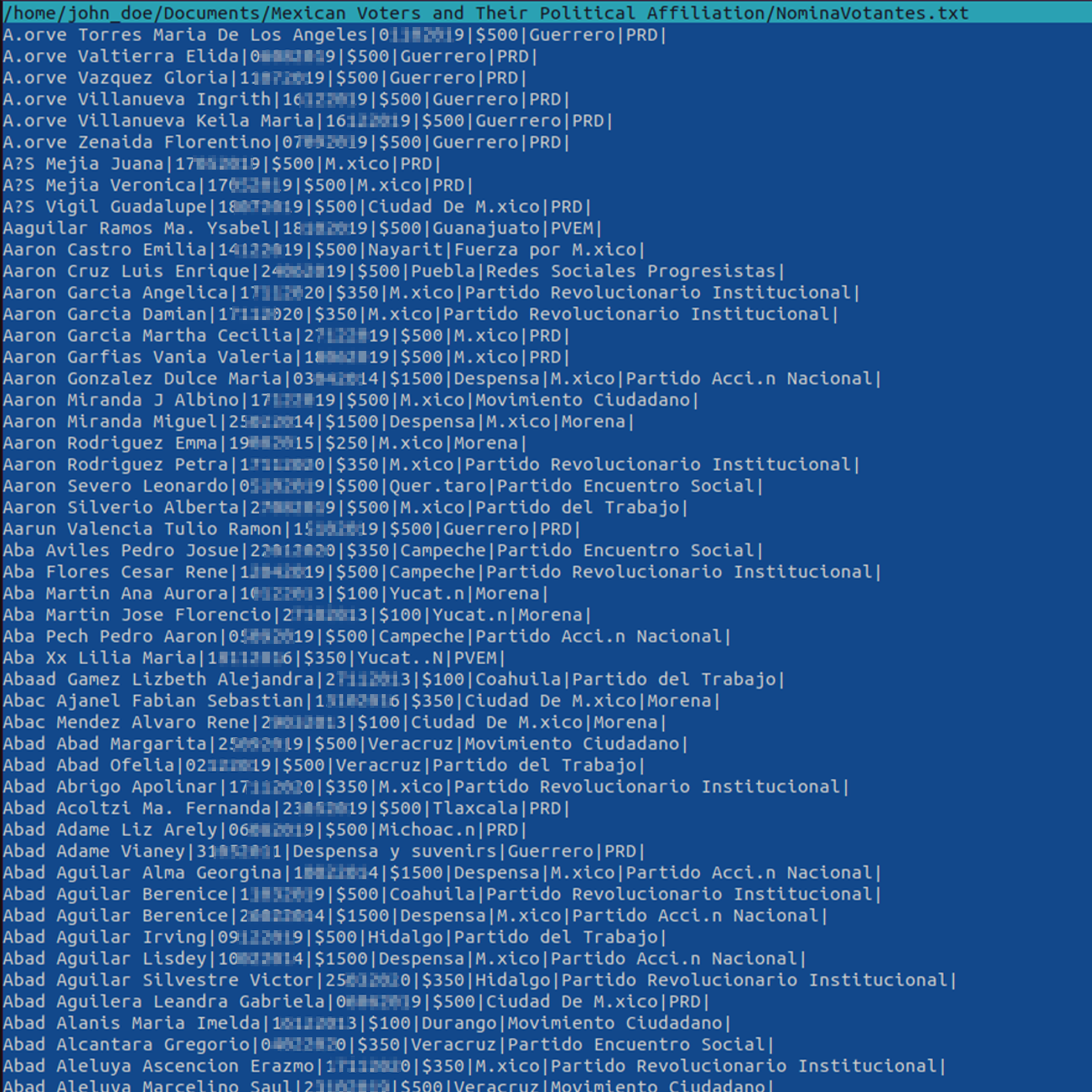
Mexico – Disclosure of Voters’ Political Affiliations
In July 2023, threat actors published a dump of Mexican voter data that included victims’ political affiliations
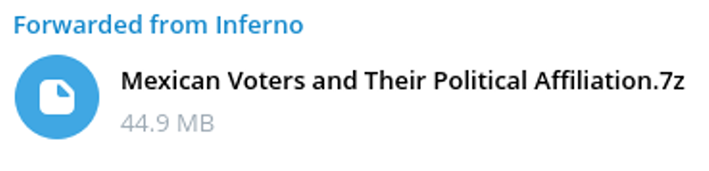
Notably, the motive behind the leak was not financial. The threat actor was trying to sow social discord by perpetuating a narrative of electoral fraud.
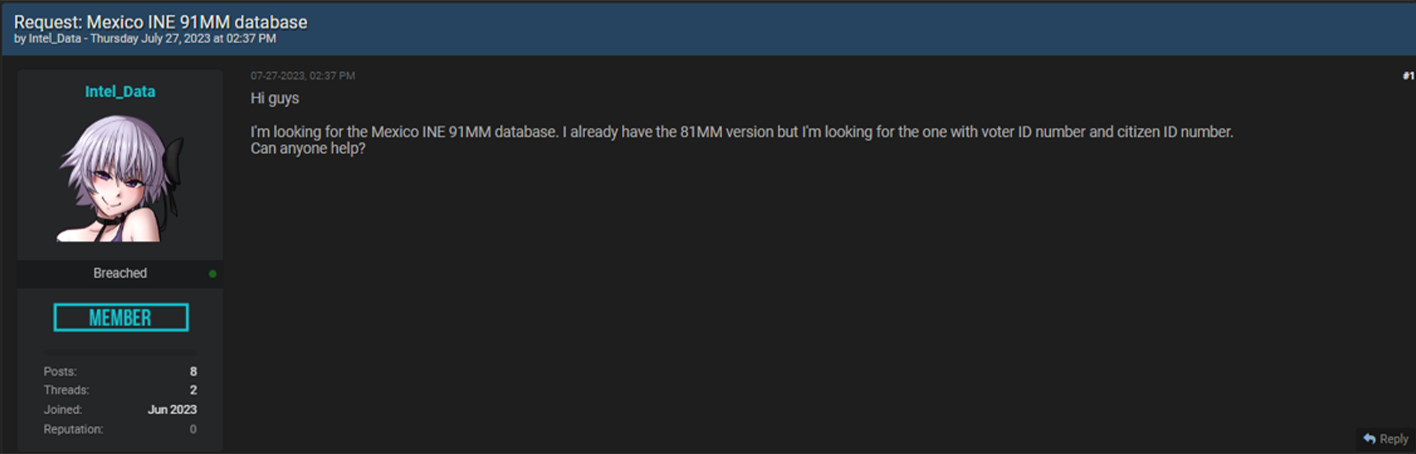
It is essential to note that threat actors are actively seeking access to Mexico's INE (National Electoral Institute) database, which contains the PII of 91 million citizens. The Breach Forums Dark Web posting below illustrates the importance of enhancing cybersecurity controls to safeguard voters' sensitive data.
Africa in the Crosshairs
Kenya
Multiple reports have outlined the use of “cyber mercenaries” to conduct influence campaigns targeting politicians in Kenya. An undercover investigation led by the investigative journalism nonprofit Forbidden Stories revealed that Team Jorge, an Israeli firm led by ex-special forces operative Tal Hanan, has influenced over 30 global elections through hacking and disinformation. Specializing in "black ops," the firm controls thousands of social media profiles, significantly impacting elections, with a focus on Africa. This case underscores the rising power of private firms in manipulating elections, posing a serious threat to democratic integrity worldwide.
Nigeria
In February 2023, candidates and voters in Nigeria expressed frustration some 30 hours after the general election after the country’s election results portal failed to display results from several states. In April, Nigeria’s information minister Lai Mohammed said the country’s Independent National Electoral Commission (INEC) “deliberately withheld the real-time upload of presidential election results from polling units” due to a “suspected cyberattack.”
As noted by Nigerian news outlet Premium Times, “Mr. Mohammed’s claim is, however, different from what INEC told Nigerians a day after the 25 February election,” as the “commission had told Nigerians that its failure to upload the results was due to technical glitches and not any form of sabotage or cyberattack.” During that election cycle, Nigeria’s Ministry of Communications and Digital Economy also revealed that the country experienced a total of 12,988,978 cyberattacks “from within and outside Nigeria” targeting the presidential and National Assembly elections.
The Minister of Communications and Digital Economy's spokesperson, Uwa Sulaiman, said that a “series of hacking attempts were recorded during this period, including Distributed Denial of Service (DDoS), email and IPS attacks, SSH Login Attempts, Brute force Injection attempts, Path Traversal, Detection Evasion, and Forceful Browsing,” according to news outlet Sahara Reporters.
Zimbabwe
Zimbabwe’s presidential election took place last August. The country’s then-incumbent President won
a second term with “roughly 53% of the vote, but the opposition and analysts immediately questioned the result.” In a statement published the day after the Zimbabwe election the U.S. State Department noted that “multiple observation missions have expressed deep concerns and stated that the country’s electoral process did not meet regional and international standards for credibility.”
The State Department also noted the “systemic bias against political opposition during the pre-election period and reports from respected civil society groups that ZEC officials pressured election observers to sign altered polling station result forms.” One key pre-election incident highlighting this systemic bias against the opposition transpired in April when local civic activists, Team Pachedu, accused the “Zimbabwe Electoral Commission (ZEC) of having passed voters’ data to ZANU-PF in breach of privacy and electoral rules.”
The leak resulted in pro-ruling party messages being sent to "constituency voters including those in the opposition who never supplied their personal details to ZANU-PF,” according to local news reports. Text messages, personalized by district and signed "President ED Mnangagwa," raised activists’ concerns about privacy and electoral integrity. The ZEC denied Team Pachedu ‘s claims.
Rest of the World: Elections on the Radar of Malicious Actors
Philippines
The Philippines' Commission on Elections (COMELEC) is currently under investigation for an alleged hacking incident. The National Privacy Commission (NPC) is examining claims of a data breach where over 60 GB of sensitive electoral information was allegedly stolen. COMELEC disputes these claims, asserting that this data was not stored in their systems. The incident raises concerns as the Philippine general election is approaching in May. It's noteworthy that COMELEC faced a significant data breach in 2016, emphasizing the importance of cybersecurity in electoral processes.
The European Union
A December 2023 report in Politico noted that the EU Parliament faces significant cybersecurity challenges ahead of its upcoming election in June 2024. The report cited an internal report authored by the EU Parliament warning that its cybersecurity controls have “not yet met industry standards” and are “not fully in-line with the threat level" posed by state-sponsored hackers and other threat groups.
Increased remote work has further amplified these risks. Recent attacks, notably by Russian group Fancy Bear, underscore the urgency for stronger security measures. The Parliament is actively working to enhance its defenses, including hiring more cybersecurity experts and increasing its budget, to protect the integrity of the June election that will decide the rebalancing of political power between the union’s 27 member countries.
Estonia
In March 2023, Estonia's parliamentary elections faced an onslaught
of cyberattacks that ultimately proved unsuccessful. The National Cyber Security Centre-Estonia (NCSC-EE) was on high alert during the election period, facing a variety of threats including DDoS attacks and phishing campaigns. Despite these heightened cyber threats, which were largely attributed to Russian actors, Estonia's Internet voting system remained secure. This situation reflects Estonia's ongoing cybersecurity challenges, particularly in light of its historic geopolitical tensions with Russia.
The United Kingdom
In September 2023, the UK Electoral Commission grappled with a significant cybersecurity breach that exposed the data of up to 40 million citizens. This complex cyberattack was discovered 14 months after the fact. The breach led to unauthorized access to sensitive information and raised concerns about Commission’s security measures. Compromised data includes electoral registers, voter information, and potentially sensitive records. This incident underscores the vulnerability of election oversight bodies and the critical need for heightened cybersecurity to safeguard electoral processes.
Bangladesh
In July 2023, a security researcher stumbled upon an insecure government web portal that exposed the personal data of 50 million Bangladeshi citizens, including their names, phone numbers, birth certificates, and national ID numbers. After reporting the breach, authorities took nearly two weeks to remove the data. Bangladeshi officials insisted that this exposure was the result of website security “weaknesses” rather than a cyberattack. The incident highlights the importance of securing sensitive data and the potential risks associated with vulnerable IT infrastructures.
In January 2024, Ukraine and Germany were accused of crashing an app used in Bangladesh’s national election in an incident described as a “cyberattack.” Mohammed Jahangir Alam, official secretary of the Bangladesh Election Commission, did not offer details on the type of attack or any possible motive behind it.
Alam blamed Ukraine and Germany for the disruption. However, it is unlikely that either country willfully sought to sabotage the Bangladeshi election. OODA Loop reported that “targeted DDoS attacks were not ruled out as a cause of the app’s malfunction, but researchers from Cloudflare say that botnets operating within Ukraine and Germany could have been the cause of the issue.”
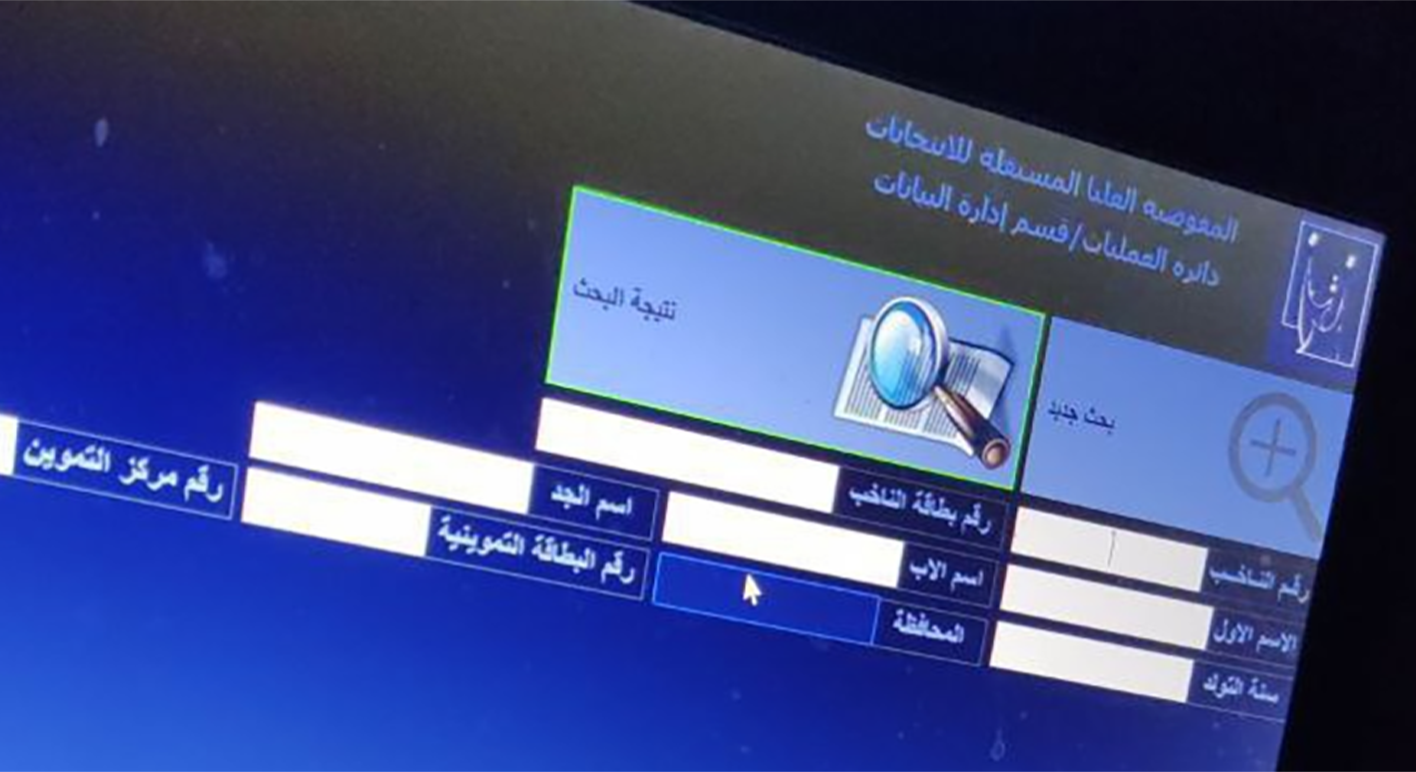
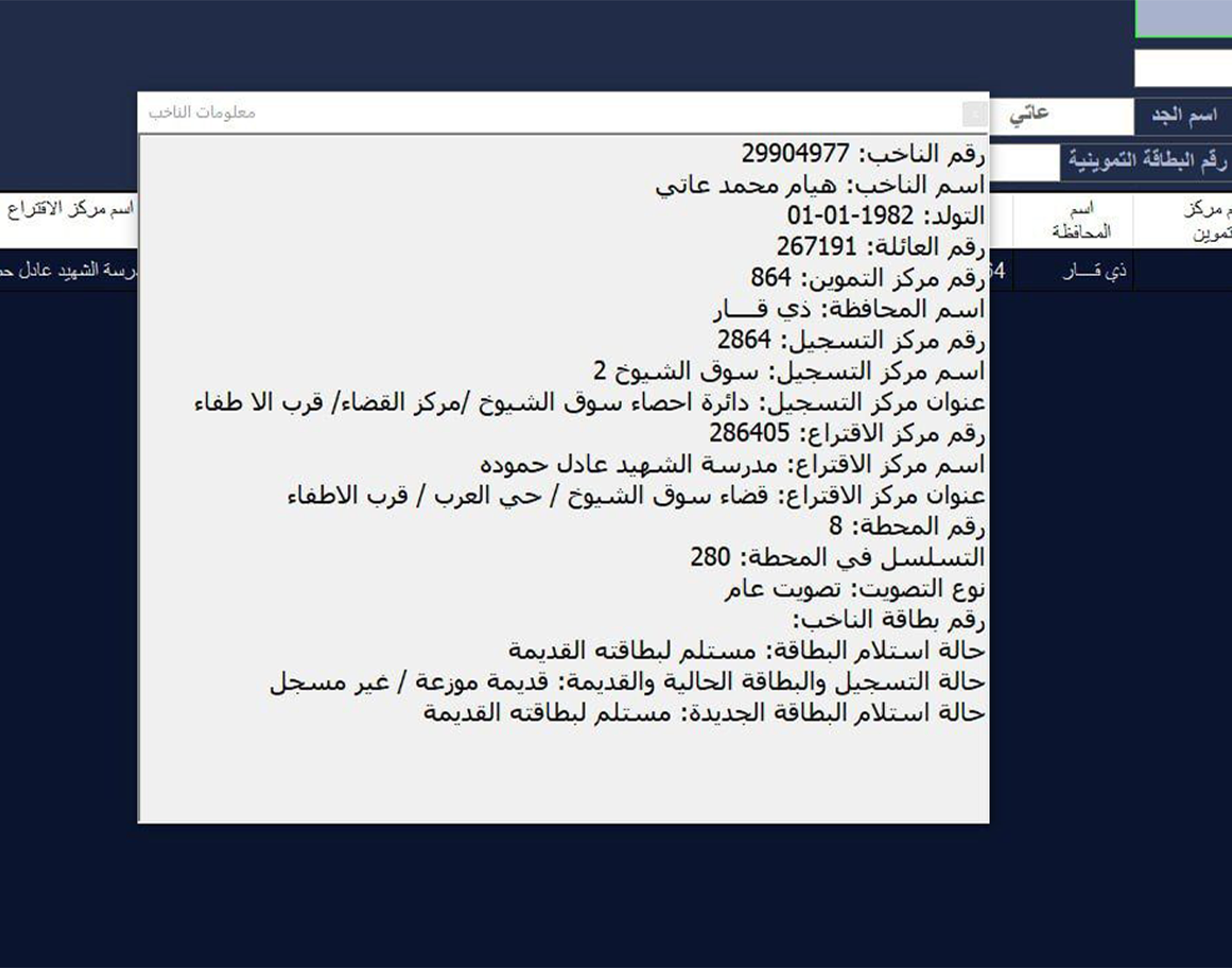
Iraq
Resecurity identified an individual who claimed to be selling a database containing information about Iraqi citizens that are eligible to vote in elections. However, the threat actor expressed a desire to keep this transaction confidential. To prove the legitimacy of their offer, they shared an image containing a sample output from the database.
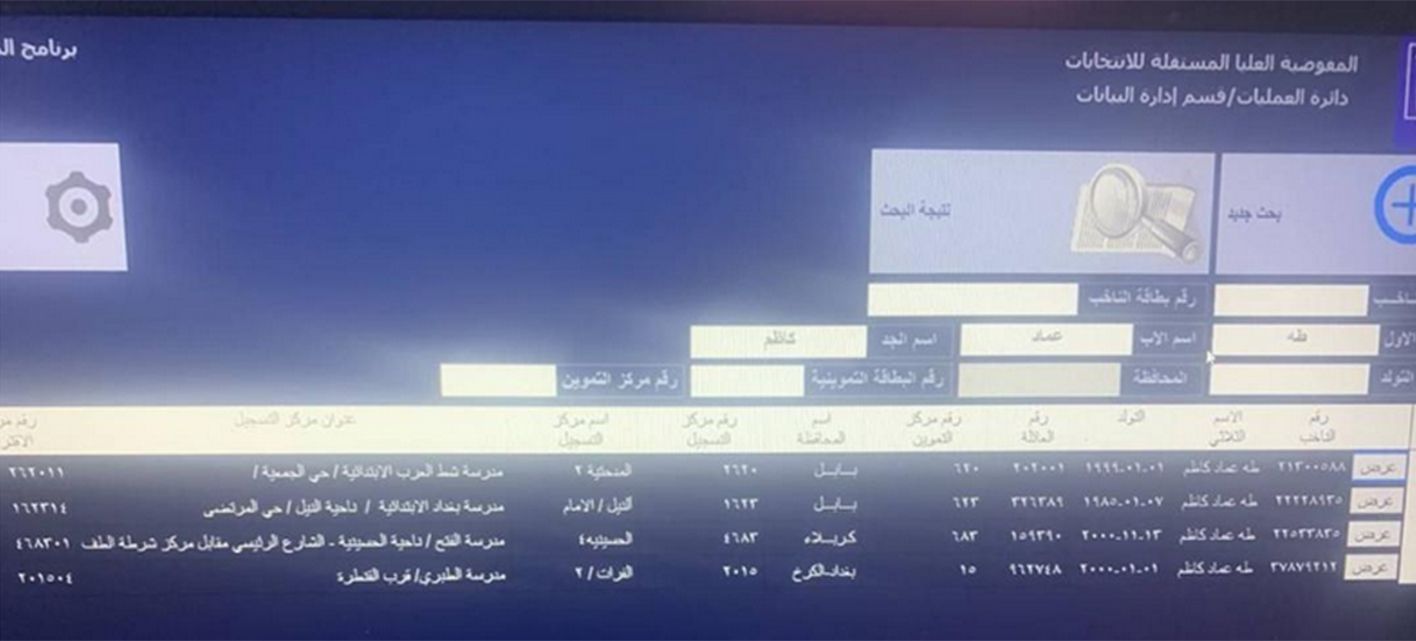
According to Resecurity’s analysis of the acquired 21.58 GB database and supported by the official verification of this data by sources familiar with these digital record repositories, the leak likely occurred around 2019.
The leaked database from the Independent High Electoral Commission (IHEC) breach matches the details of a voter data leak affecting 24.3 million voters in Iraq, as found in a widely-circulated Dark Web post. Resecurity also uncovered a similar Dark Web posting from 2022, though this data was found to be corrupt. Investigations revealed that various actors who had access to this information were reselling it on the Dark Web.
The text below the logo refers to "Operations \ Data Management Department."
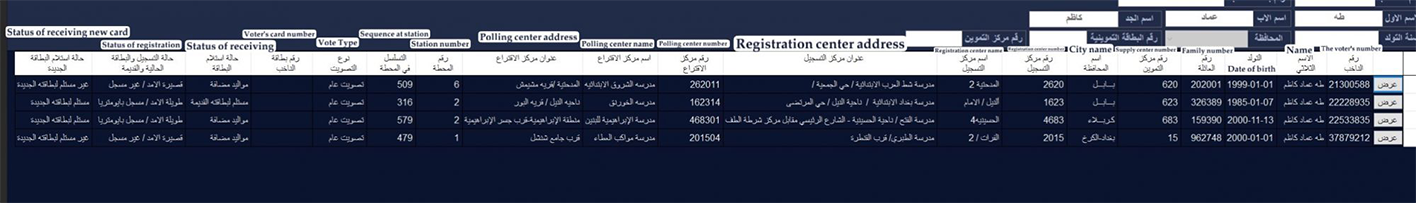
Translation of the key fields confirmed that the database contains voting information with details about voters, polling stations, and registration centers to collect votes:
- Status of the new (voter's card)
- Status of registration
- Status of receiving
- Voter's card number
- Vote Type
- Sequence at station
- Station number
- Polling center address
- Polling center name
- Polling center number
- Registration center address
- Registration center name
- Registration center number
- City
- Supply center number
- Family number
- DOB
- Name
- Voter's number

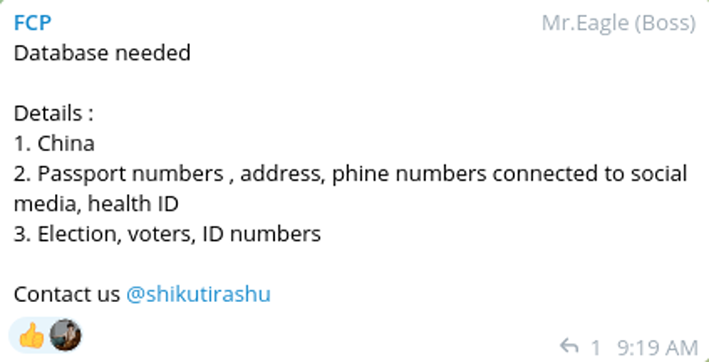
Taiwan
According to reporting by Politico, Taiwan faced a deluge of cyberattacks days before the country’s presidential election in January. Experts blamed China for an unprecedented and increasingly sophisticated level of interference in Taiwan’s election. Meanwhile, last March, Resecurity observed multiple threat actors looking to purchase Chinese voter data. It is not clear if these efforts were connected. Nevertheless, this activity confirms threat-actor interest in the Asia-Pacific region.
Pakistan
The Pakistani government restricted access to the country’s most widely used social media platforms as of January 7, 2024. This restriction coincided with appeals made by the country’s jailed former prime minister Imran Khan to the online world.
"Live metrics show a nation-scale disruption to social media platforms across Pakistan, including X/Twitter, Facebook, Instagram and YouTube; the incident comes as persecuted former PM Imran Khan's party, PTI, launches its election fundraising telethon", tweeted UK-based internet watchdog NetBlocks on January 7.
Ultimately, politically targeted network censorship is a significant element of malign cyber- activity during the electoral process. This type of activity is almost universally considered illegal. The Human Rights Council of Pakistan strongly criticized the move, deeming it "a violation of international law." The organization wrote in a tweet: "HRC Pakistan believes that all political parties have the right to carry out their activities. In the context of elections, all political parties should get the basic right of freedom of expression. It is the responsibility of the government of Pakistan to uphold fundamental rights."
Conclusion
With the 2024 General Election rapidly approaching in the U.S., the intelligence collected about the incidents discussed in this report serves as a stark reminder that threat actors are actively trying to acquire and exploit voter data. While some of the threat actors behind these leak operations are purely motivated by profit and opportunistic hacktivism (driven by ideology), other cogs in this cybercriminal supply chain may be looking to weaponize voter data to craft targeted propaganda campaigns and subvert democracies worldwide.
Similar to the phenomenon of account compromise due to password reuse across multiple platforms, leaked voter data remains exploitable years after the initial leak. This is one of the most crucial issues that governments should address. In the backdrop of rapidly increasing cyber-threats, ensuring comprehensive identity protection for voters has become foundational to preserving the integrity of the democratic process. Cyberespionage groups, operating under the direction of nation-state actors, are targeting voter PII, plotting to use it as a long-term weapon for electoral interference. This data reveals crucial demographic insights and context about target populations during both pre-election and post-election stages.
For these reasons, it is vital for organizations and individuals to monitor their Dark Web data footprint. Resecurity’s Identity Protection solution is a leap-ahead cyber-threat intelligence (CTI) collection application that can help individuals and enterprises monitor their exposure to malicious data leaks on the Dark Web.
References
- Cyber threat activity against election infrastructure
https://www.cyber.gc.ca/sites/default/files/cyber-threats-canada-democratic-process-2023-update-v1-e... - Foreign Threats to U.S. Elections Election Security Information Needs
https://www.dni.gov/files/ODNI/documents/DNI_NCSC_Elections_Brochure_Final.pdf - Understanding cybersecurity throughout the electoral process: a reference document. An overview of Cyber Threats and Vulnerabilities in Elections. https://www.usaid.gov/sites/default/files/2023-01/Understanding-Cybersecurity-Throughout-the-Elector...
- Securing the 2024 Elections
https://www.brennancenter.org/our-work/policy-solutions/securing-2024-election - Security experts warn of foreign cyber threat to 2024 voting
https://apnews.com/article/iran-united-states-government-russia-arizona-3cbfa1c46051416fac1f4183774a...
- The Pivotal Elections of 2024: Key Races That Will Shape the Global Landscape
https://www.usip.org/publications/2024/01/pivotal-elections-2024-key-races-will-shape-global-landsca...

