

Context of the blog
In this blog, we will explore how defenders can combat cybercrime and fraud with the help of Infinite Game theory. It’s important to allocate resources toward researching the dark web to achieve this.
- There is no end state in which the cybercrime issue is solved, where there are no longer victims of cybercrime.
Dealing with cybercrime is a continuous challenge that demands persistent efforts. While it may not be possible to eliminate it entirely, precautionary measures can be taken to reduce the number of victims and minimize its effect on those affected. Limiting the resources available to attackers, making it tough for new cybercriminals to enter the field, and reducing the motivation of those who might contemplate indulging in cybercrime are ways to enhance defenses against it. - The defender’s success is when cyber threats are reduced to a manageable level with no/limited impact potential.
Defenders often focus on measuring the effectiveness of their defense mechanisms. However, evaluating how well they are impeding the attacker is equally important. Defenders should compare their metrics to the attacker's success metrics to obtain an accurate efficacy assessment. To prevent future cybercrime attacks, it is important to understand the attacker's motivations and supply chain capabilities.
As more information is gathered about cyber-attacks, a clearer picture of the human attackers behind them will emerge. This includes their changing motivations, objectives, skills, rewards, limitations, and patterns. The incidence and severity of cybercrime have hit an all-time peak. Cybercriminals have greater resources than ever, while those working to stop them are disadvantaged. Furthermore, the cost of cyber defense for defenders is higher than the profits made by professional cybercriminals.Dark web research can aid defenders.
Researching on the dark web can be a helpful tool for teams to understand the motives of attackers, anticipate their next moves, and plan effective defenses. It's important to remember that defenders must protect against not only the attacker's abilities but also their supply chain. dark web research can assist teams in gaining a better understanding of the threat landscape, identifying previously undetectable threats, and disrupting the cybercriminal's supply chain. Additionally, insights from the dark web can help teams develop metrics to measure the impact of disrupting the attacker's cost of goods sold (COGS) and return on investment (ROI). By implementing this strategy, defenders can improve their ROI and allocate their resources towards addressing other cyber threats.
- One of the inspirations for this paper is the book “The Infinite Game” by Simon Sinek in 2019.
- While combating cybercrime can be considered an Infinite Game, this paper finds other important perspectives to fight against it effectively.
The problem statement
Dealing with cybercrime is an ongoing challenge that requires continuous effort, much like traditional crime. The goal of defenders is to minimize the harm caused to individuals, companies, and other targeted entities by cyber criminals. While eradicating cybercrime is the aim, it's an impossible task. It's like putting out a forest fire; even if the flames are successfully extinguished, any remaining ember can reignite the entire forest. Even if a defender thwarts an attack and the perpetrator is caught, the strategies, shared knowledge, supply chains, and monetization methods used by cybercriminals will still be present for the next attacker. This is like an Infinite Game, where the players may change, but the game remains the same.
To successfully address the continuous problem, it is important to acknowledge certain crucial factors that play a role in the Infinite Game dilemma. We can strive towards implementing practical and efficient solutions by comprehending these dynamics.
- Embrace adaptability: It is crucial to comprehend that individuals engaged in cybercrime are constantly innovating and discovering new methods of operation. The apprehension of current offenders will not completely resolve the problem, as new ones will likely emerge. Therefore, the primary focus should be constructing robust defenses that adjust to evolving threats.
- Recognize the asymmetry: Defenders face challenges when confronting cybercriminals who work outside of societal norms. However, cybercriminals still follow certain standards and have reputations within their supply chain. Utilizing these dynamics can disrupt their reputation and business models, leading to distrust within the cybercrime industry.
- Understand the profitability factor: It's important to recognize that completely eradicating cybercrime is not feasible. Rather, the focus should be on minimizing its impact and reducing its profitability for those who commit these crimes.
- Embrace the complexities: Movies may portray a world where justice prevails, but the reality of dealing with cybercrime is far more intricate and chaotic. Successfully tackling cybercrime requires a comprehensive strategy considering technical, legal, societal, and educational aspects. Collaboration and cooperation between various groups, including government bodies, industries, and individuals, is crucial to combat cybercrime effectively.
- Continual improvement and vigilance: To effectively protect against cyber threats, it's important to view cybersecurity as an ongoing process rather than a one-time solution. It's crucial to remain vigilant in identifying new threats, enhancing security measures, and promoting cybersecurity awareness among individuals and organizations.
- An imbalance between defenders and attackers: Notably, there are more defenders than professional attackers, and the former has spent more money on defense than the profits the latter has gained. However, it is concerning that malicious actors are still earning more money. Further exploration of this issue will be discussed in a forthcoming paper.
To reduce the impact of cybercrime and establish a safe digital environment, it is important to comprehend these dynamics and adopt a comprehensive strategy.
Dark web research indeed plays a crucial role in threat intelligence and cybersecurity
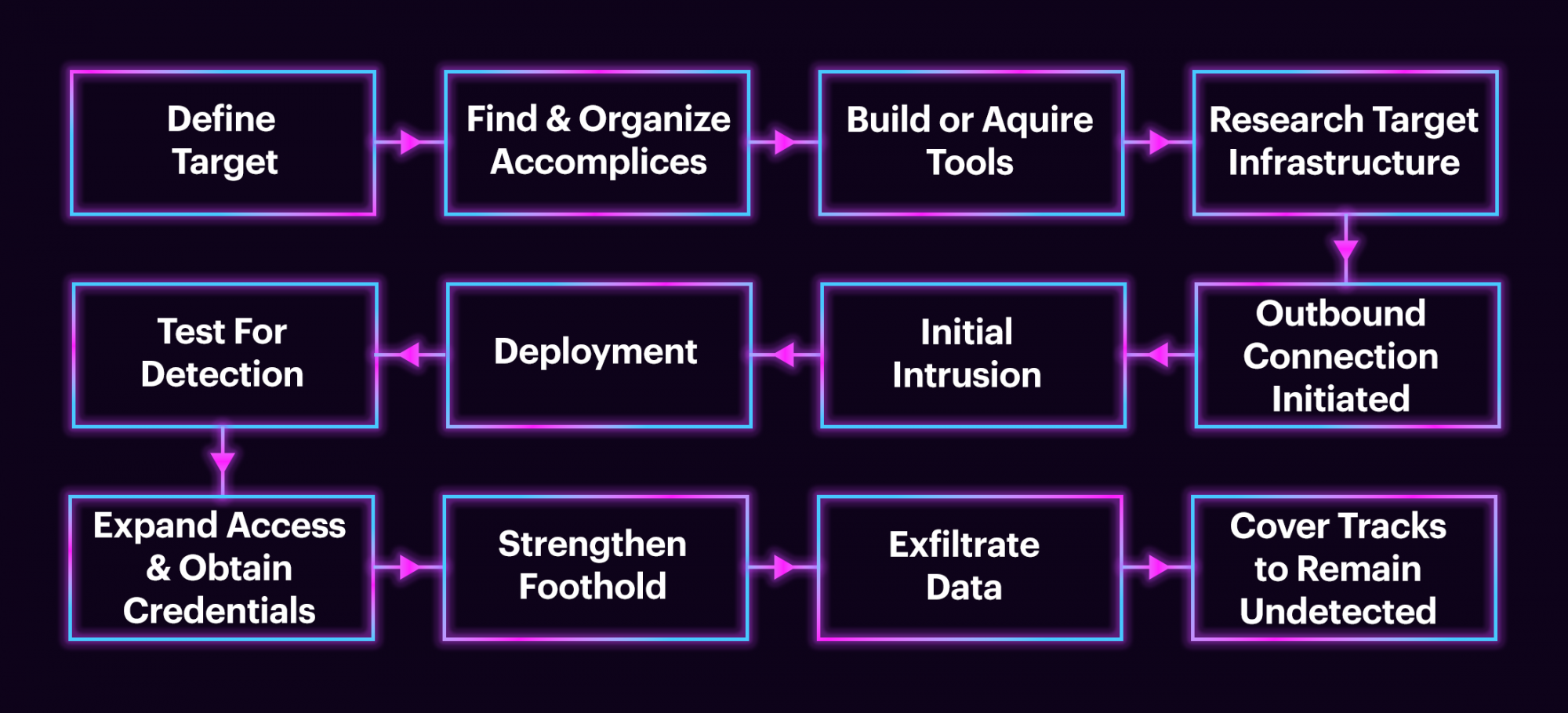
To effectively counter potential cyberattacks, cybersecurity teams must understand the activities and motivations of malicious actors operating in the internet's hidden corners. Here are some key points to keep in mind:
- Enhanced threat understanding: By researching the dark web, cybersecurity teams can gain valuable insights into the strategies, tactics, and tools used by threat actors. This knowledge allows them to identify potential threats and vulnerabilities early on, enabling them to implement timely defense measures.
- Human motivations and capabilities: Research on the dark web can provide valuable insights into the human motivations behind cyber-attacks. By understanding these underlying reasons, teams can better assess the potential impact of attacks, identify targets, and develop appropriate defense and mitigation strategies. Furthermore, studying the capabilities of threat actors can help determine their level of sophistication and the potential harm they can cause.
- Countermeasures and defense planning: Organizations can gather valuable information to develop strong defense mechanisms and countermeasures by researching the dark web. This includes implementing proactive security and fraud controls, creating incident response plans, and reinforcing vulnerabilities to minimize the risks of potential threats.
- Threat intelligence effectiveness: Intelligence agencies heavily depend on human intelligence (HUMINT) to understand their adversaries. Organizations with strong threat intelligence capabilities can gain an advantage by exploring human attackers on the dark web. This method complements technical intelligence gathering and aids in bridging the gap between technology-based defenses and the human elements responsible for cyber threats.
Organizations need to research the dark web for threat intelligence and cybersecurity purposes. This research helps gain valuable insights into malicious actors' motives, abilities, and tactics. With this information, organizations can develop effective defense strategies and reduce cyber risks in a complex threat environment.
Finite Games vs. Infinite Games
The battle against cybercrime can be seen as an Infinite Game, meaning that the goal is not to achieve a final victory but rather to continually defend against and reduce the impact of cyber threats over an extended period. Here are some essential factors to consider.
- Finite Games vs. Infinite Games: In finite games, set rules and goals signal the game's conclusion. In contrast, Infinite Games, like fighting cybercrime, have no fixed end, allowing players to adjust their tactics as necessary. The emphasis is on constant progress and durability rather than attaining a definitive win.
- Ever-changing Players: The world of cyber defense is constantly changing as players adapt their tactics to gain an advantage. New actors enter the scene, and existing ones may change their methods or motivations. Defenders need to stay agile and adaptable to address evolving threats effectively.
- Defenders and Adversaries: Those who defend against threats must follow the rules, policies, and budgets to maintain legal and societal standards. Those who pose dangers, such as cybercriminals, may exploit weaknesses and operate outside these limitations. Nonetheless, the cybercriminal supply chain has specific models and reputations influencing its behavior. Knowing these dynamics can aid defenders in preparing for and tackling new risks.
- Persistent Business Objectives: While the players and tactics may change, the underlying business objectives of cybercriminals tend to remain consistent. They seek notoriety, promotion, financial gain, data breaches, disruption, or other malicious goals. Defenders must recognize this motivation and build resilient defenses to deter and disrupt their activities.
Cyber defense is an ongoing, ever-evolving effort that aligns with an Infinite Game's characteristics. By understanding the nature of the game, defenders can adopt strategies that emphasize adaptability, continuous improvement, and a deep understanding of the evolving threat landscape.
Combating Cybercrime as a Finite Game
When defenders play with a Finite mindset in an Infinite Game, the odds increase that they will find themselves in a quagmire. Were the defenders burning through the will and resources they needed to keep trying to play a Finite Game against an adversary playing an Infinite Game.
Mismatched strategies: When defenders approach cyber defense with a finite mindset, focusing on short-term metrics and attempting to "win" specific battles, they may find themselves in a quagmire. This approach leads to a reactive "whack-a-mole" game where defenders struggle to add significant friction against the adversaries playing the Infinite Game. This results in minimal impact on deterring future attacks.
This also results in the defenders measuring themselves by Finite Game metrics, which motivates them into taking action that is measured by some metric that demonstrates how “successful” they are, without counting the impact they have at protecting victims from the current attacks, as well as discouraging bad actors from conducting future attacks.
Shifting measurement of success: Defenders often measure their success based on arbitrary metrics that do not align with the objectives and metrics of the attackers. While defenders focus on metrics such as detection rates and time to mitigation, attackers evaluate success based on achieving their goals and return on investment (ROI). As a result, defenders may claim victory based on their metrics, but their actions do not significantly deter attackers or impact their ROI.
Aligning metrics with attackers: To have a tangible impact on dissuading attackers and reducing their ROI, defenders should align their metrics to be opposed to the success metrics of the attackers. This can include reducing the time from initial attack to mitigation, hindering the attacker's ability to scale their attacks, applying learnings from known attacker techniques to discover new threats, and deploying mitigations before attacks become profitable.
The impact can also be measured by things other than numeric metrics. For example, durability can measure when others contribute to the ongoing effort, not just during the time they are there but well beyond their tenure.
Impact on the attack cycle: Defenders should aim to impact it earlier, ideally before attackers achieve their expected ROI or profit. By deploying effective mitigations, increasing the cost and risk for attackers, reducing their capacity to launch various attacks, and focusing on transactional fees rather than fixed costs, defenders can disrupt the attacker's cycle and hinder their ability to leverage the efficiencies of the dark web supply chain.
By shifting from a finite mindset to an infinite perspective, defenders can focus on strategies that impart enough friction to disrupt current attacks and discourage future ones. Aligning metrics with the attackers' objectives and targeting the attack cycle at critical stages can lead to a more impactful defense against cybercrime.

Aligning metrics: Defenders commonly measure their success based on metrics such as the number of detections and the timeframe from detection to mitigation. However, these metrics may not directly impact the attacker's objectives and ROI. To align with attackers, defenders can focus on metrics that directly disrupt their activities, such as reducing the time from the initial attack to mitigation.
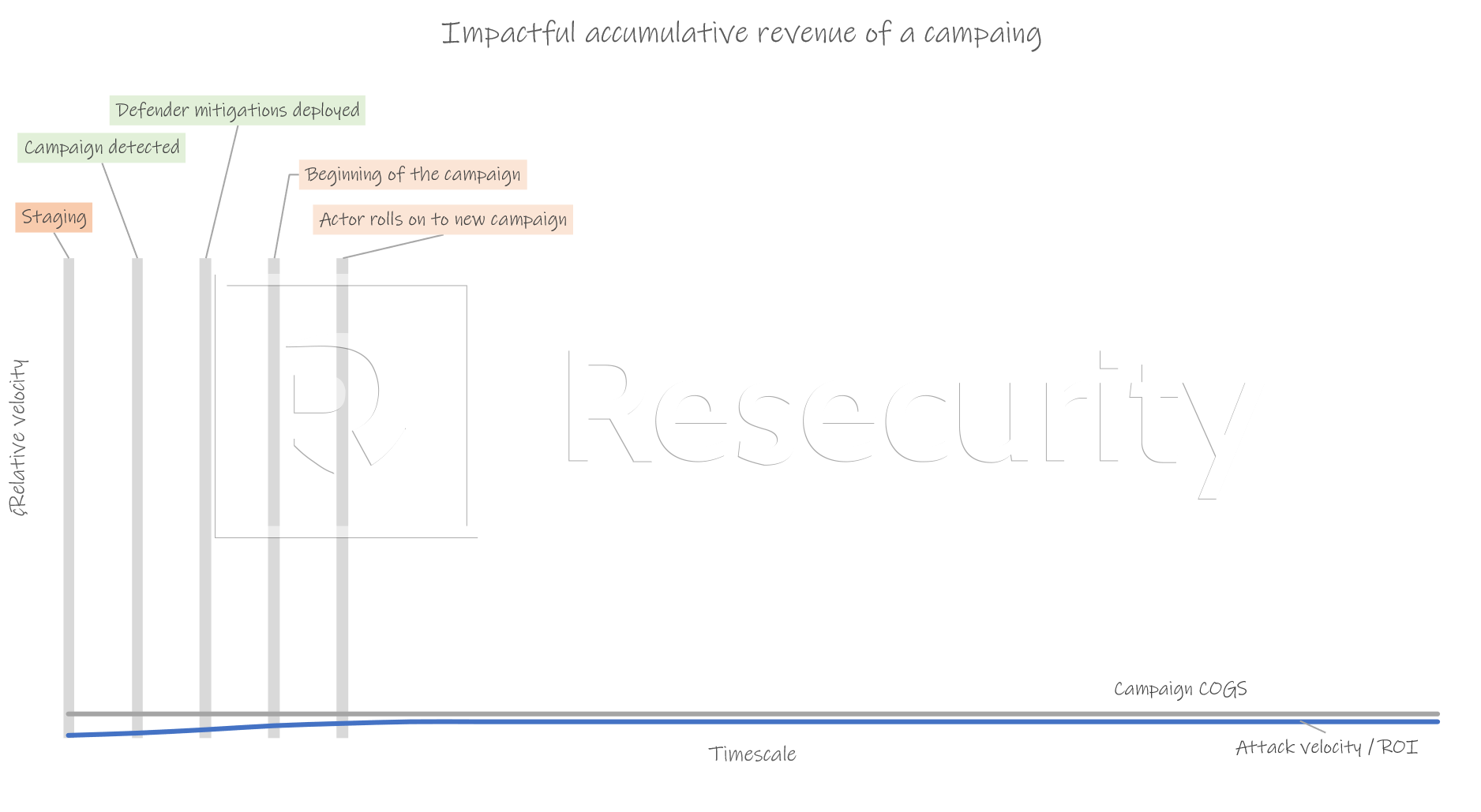
- Reducing attack-to-mitigation time: Defenders can limit the attacker's ROI by decreasing the window between the initial attack and mitigation. This approach makes the attack less profitable for the adversary, potentially falling below the cost of goods sold (COGS) or the opportunity cost of pursuing a different attack. Timely detection and swift response are crucial in achieving this objective. (i)
- Limiting attack scalability: Defenders can also measure their effectiveness by decreasing the attacker's ability to scale their attacks. This can be achieved by promptly sharing forensics and threat intelligence with others in the cybersecurity community, enabling a faster and more comprehensive defense against similar attacks. By impeding the attacker's ability to expand their operations, defenders can increase the costs and risks associated with their activities.
- Mitigate the attacker’s objectives: The defenders have four recommended options.
- Deploy mitigations before the attack becomes profitable.
- Reduce the predictability of the ROI, which can also include increasing cost and risk, and decrease the likelihood of achieving the intended goal, "profit," and being able to leverage the efficiencies of the dark web supply chain.
- Reduce the capacity of the attacker to increase the volume of different attacks.
- Focus on the transactional costs of the attack and not fixed costs.
- Impacting the attacker's campaigns earlier in the attack cycle, before they achieve their expected return on investment (ROI) and any profit, is an ideal approach for defenders. By doing so, defenders can disrupt the attacker's operations and make their attacks financially unviable or need to meet their non-financial goals.
- When the defender's metrics oppose the attackers, their actions and mitigations have effectively slowed the attack's velocity, preventing them from reaching their desired ROI. This could be achieved by deploying proactive defenses, detecting and responding to threats early, and implementing effective security measures.
- If the defender can reduce the ROI of the attacker's campaign below the cost of the campaign (COGS), it becomes economically unfavorable for the attacker to continue their activities. This can be accomplished by implementing security measures that increase the cost and risk for the attacker, making it more difficult for them to achieve their goals.
- Defenders can effectively disrupt their operations and dissuade them from conducting future attacks by focusing on metrics directly impacting the attacker's campaign and profitability. It highlights the importance of proactive defense strategies and the need to measure success not only in detections and mitigations but also in terms of the financial viability and impact on the attackers' objectives.
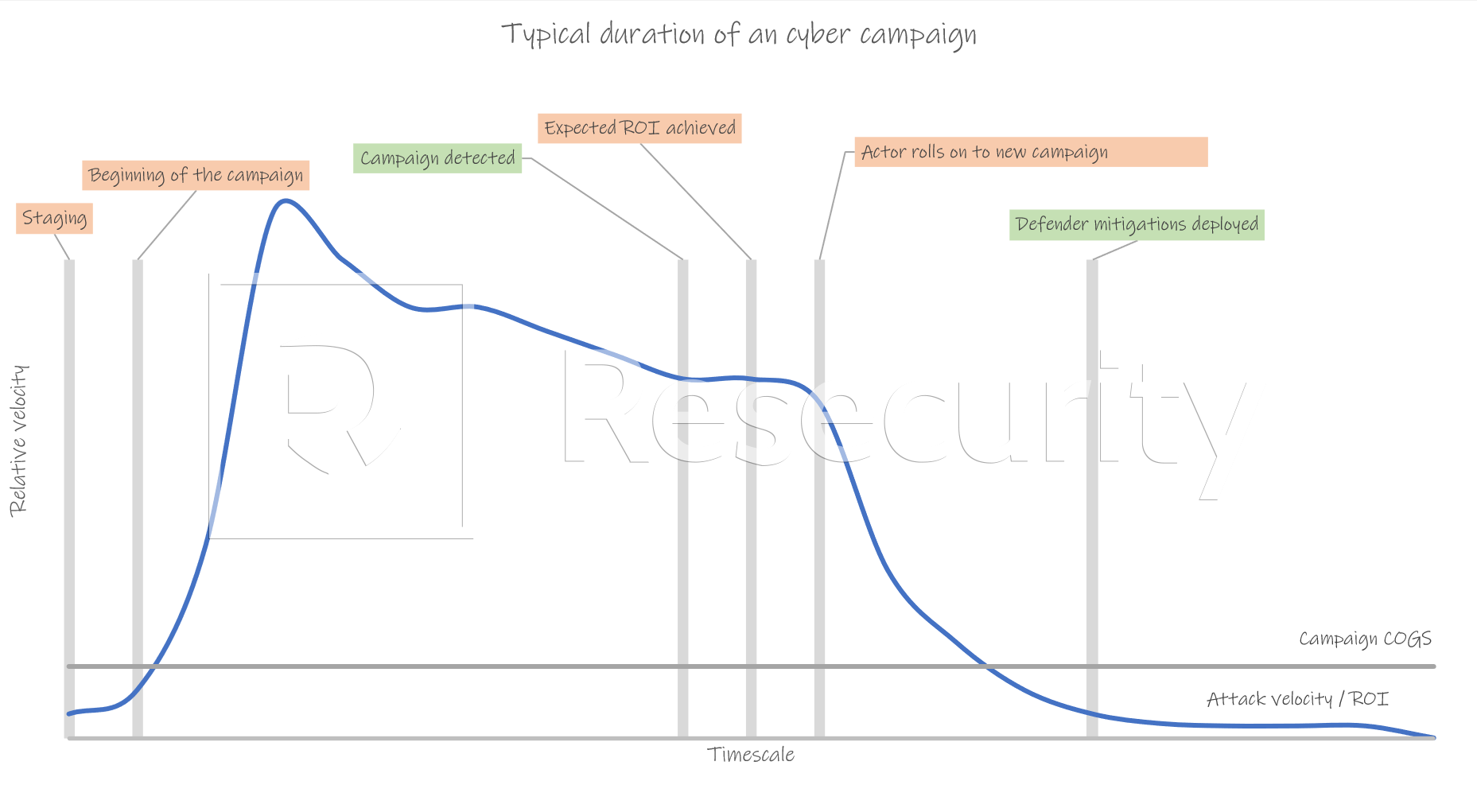
The typical velocity / ROI graph, which does not deter current and future attacks
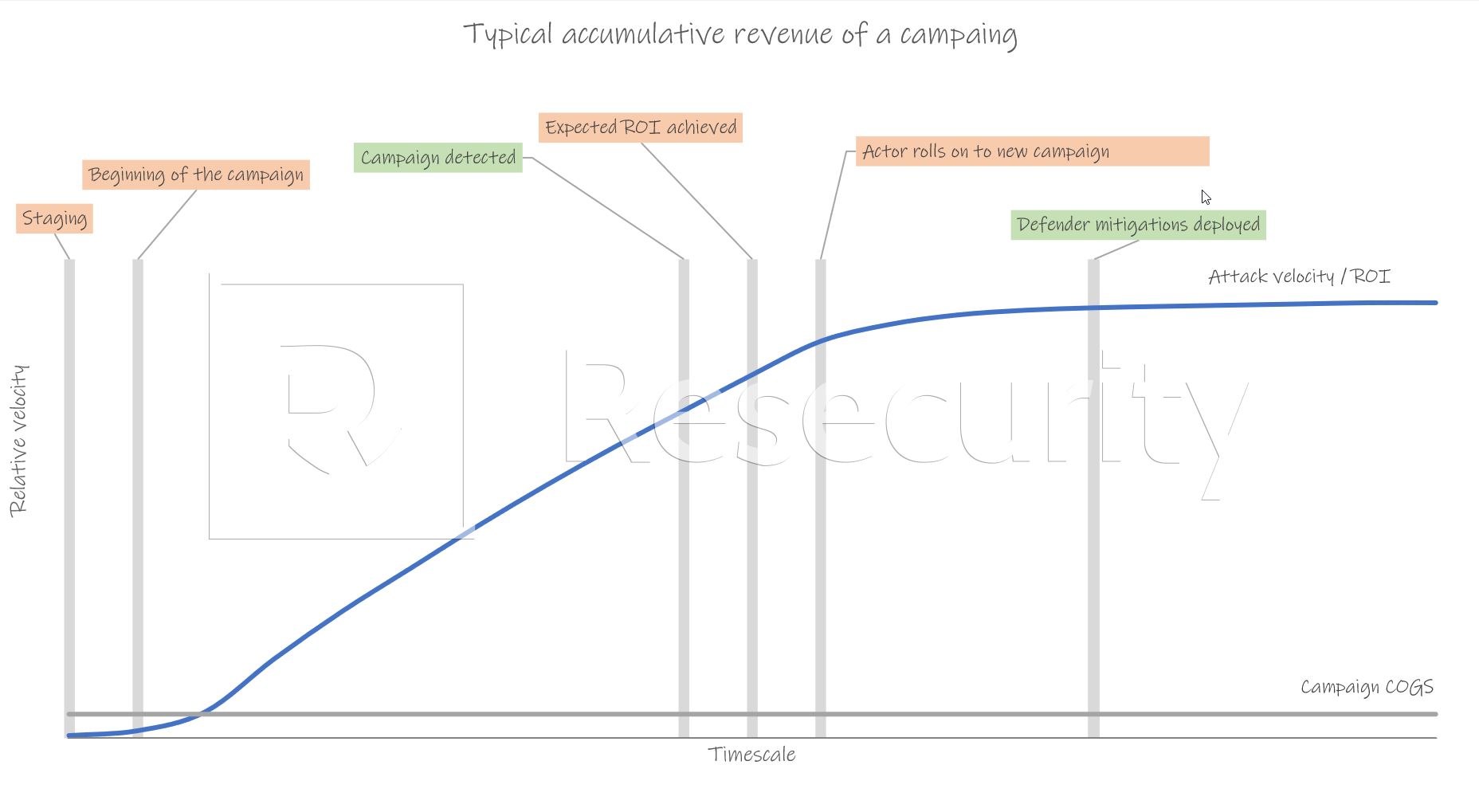
The desired velocity / ROI graph, which does deter current and future attacks
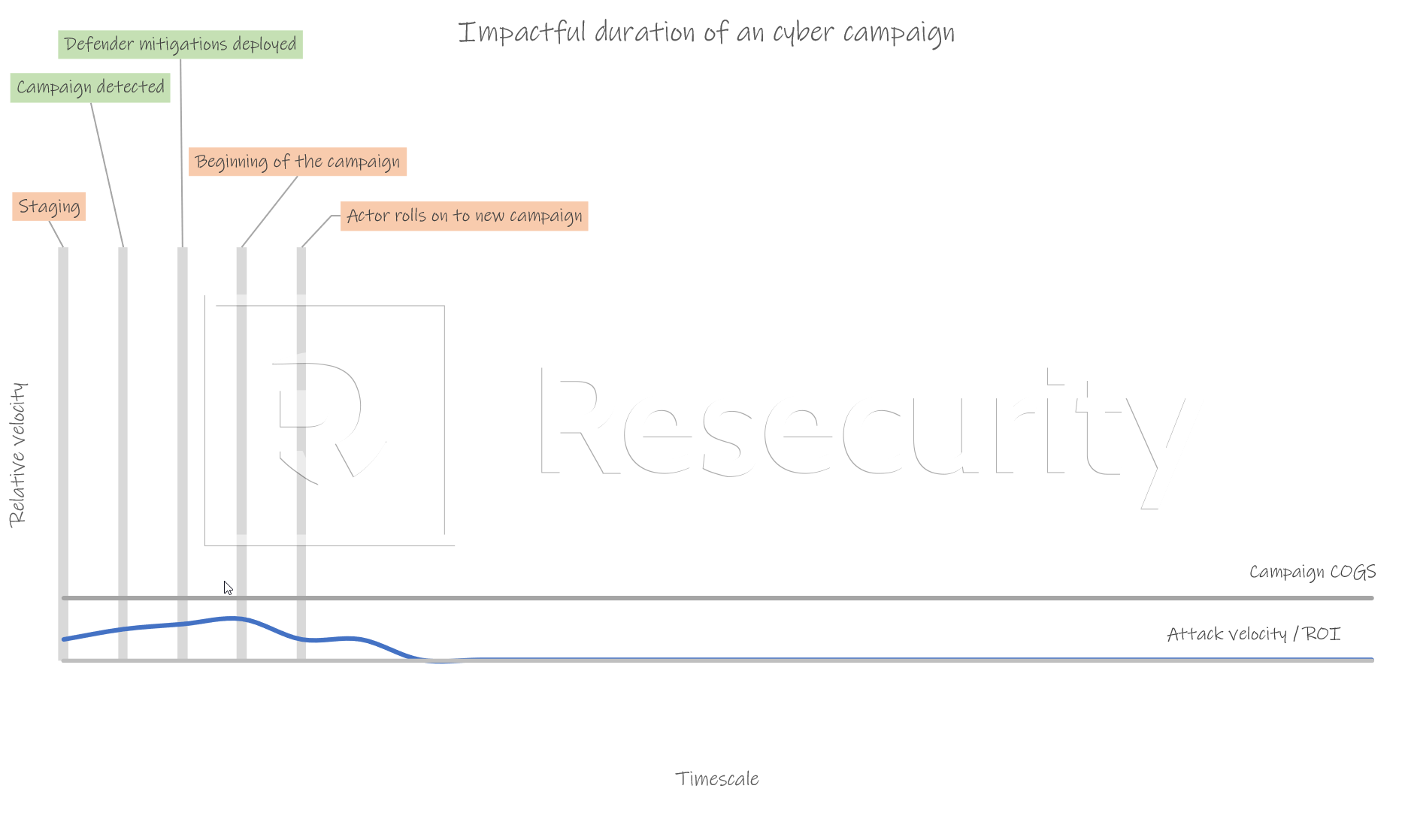
Combating Cybercrime in an Infinite Game
In the fight against cybercrime, defenders must understand the mindset they should adopt. We can think of it as police work, and it's essential to recognize that cybercriminals are only individuals with a plan or resources. This analogy is particularly relevant.
Indeed, the objective of defenders is not to "win" in an absolute sense or eliminate cybercrime but rather to make it more difficult for cybercriminals to operate and to deter potential criminals from engaging in illicit activities. The goal is to frustrate the will and exhaust the attackers' resources while continuously improving defense strategies.
Recognizing cybercriminals as worthy adversaries, despite their immoral objectives, allows defenders to learn from their techniques and constantly improve their capabilities. This requires treating cybercriminals as rivals who challenge defenders to become better rather than underestimating their abilities. (ii)
Defenders must understand that victories in specific battles against cybercriminals do not equate to winning the war. The landscape of cybercrime is constantly evolving, and new players will emerge to fill any vacuums left by removing significant rivals. This necessitates a perpetual state of conflict and a continual commitment to remain vigilant and adaptive.
By maintaining humility, acknowledging the ever-present threat, and recognizing that the game is ongoing, defenders can better prepare themselves to face the challenges posed by cybercriminals. It emphasizes the importance of resilience, constant improvement, and a long-term perspective in the fight against cybercrime.
The aim is not to win the fight against cybercrime, as this battle has no definitive end. Instead, the goal is to maintain the defender's strength and resources while thwarting the attackers' efforts and wearing them down over time.
Putting it another way and using a police metaphor: Police can never stop/prevent all crime. Instead, the police can only make it more difficult for criminals to be criminals, thereby deterring some potential criminals from taking up a life of crime.
Crime has existed in every society for millennia and will continue until the end of time. The best police and cybercrime defenders can do to mitigate the impact of crime, dissuade a portion of potential criminals from becoming criminals, and reduce the resources and opportunities criminals have at their disposal. (iii)
The "Broken Windows" theory can also be applied to cybercrime. Cybercriminals often take advantage of opportunities for easy attacks that offer high returns on investment. They have access to many "broken windows" in the cyber world. Including:
- Botnet data with usernames, passwords, device fingerprints, cookies, and security tokens are taken from PCs infected by malware used by their employees, supply chain, vendors, and customers.
- Breach data, which includes usernames and passwords, of their employees, supply chains, vendors, and customers.
- Perimeter scans of their network can disclose devices that have vulnerabilities or have been misconfigured.
- Buying access from initial access brokers gives attackers beachhead access into the company’s network for as little as $35.00.
- Dark web chatter that indicates the company was breached before, therefore, likely can be breached again.
Defenders must not over-indexing the tactics, techniques, and procedures (TTPs) used by attackers. While understanding and mitigating TTPs are crucial for detecting and responding to current attacks, focusing on the motivations (Ms) driving attackers and the predictability of their return on investment (ROI) is equally essential. (iv)
Defenders must increase their efforts to prevent entry-level cybercrime from deterring new attackers from entering the cybercrime ecosystem. It is too easy for beginners to engage in simple forms of cybercrime, such as click fraud, basic phishing attacks, and small-scale fraud. This allows them to acquire the required skills, confidence, social network, and resources for more advanced cybercrime. We can discourage potential cybercriminals from pursuing this path by preventing low-level cybercrime.
Defenders can focus on their motivations and return on investment (ROI) to deter future attacks and hinder an attacker’s activities. This strategy acknowledges that attackers can quickly modify their tactics, techniques, and procedures (TTPs), but their motivations and financial incentives are typically limited and harder to replace.
Another thing to consider is that most of the costs defenders impose on attackers equate to a fixed cost to the attacker. Defenders need to determine what transactional fee they can inflict on an attacker. That way, as the attacker scales their attack, their cost increases.
To impact the cost of goods and services (COGS) associated with an attack, defenders can shorten the attack’s duration, decrease the attacker’s capabilities, and create obstacles that hinder their ability to scale or repeat the attack. Additionally, implementing deceptive defenses can make the ROI unpredictable for attackers, increasing their costs and effort. (v)
By understanding the why behind the attacker’s actions and addressing the motivations driving them, defenders can make the TTPs less critical because the underlying reasons for the attack are addressed. This approach shifts the focus from solely reacting to individual attacks to proactively discouraging future attacks by targeting the root causes.
Creating an unpredictable ROI for attackers also plays a role in deterring them. Attackers calculate the ROI compared to the opportunity cost (OC) of conducting the attack. Suppose the ROI becomes unpredictable and falls below the OC most often. In that case, attackers are more likely to redirect their efforts toward targets where the ROI is predictably greater than their OC.
By aligning efforts toward understanding and disrupting the motivations and ROI of attackers, defenders can introduce scalable and durable disruptions that make it more challenging for attackers to achieve their objectives. This approach complements the focus on TTPs and adds a strategic layer to cybersecurity defenses, aiming for long-term impact and discouragement of attackers.
The tragedy of the commons also comes into play
The actions taken by individual defenders to protect their interests will inadvertently contribute to the overall strength and resources of attackers, which can then be used to target other victims.
The example of ransomware attacks is particularly relevant. When companies pay ransoms to attackers, they have significant financial resources to reinvest in improving their attack capabilities. This cycle perpetuates the ransomware ecosystem and enables attackers to develop more sophisticated tools and techniques to target a broader range of victims. The collective impact of these payments strengthens the attackers' position and encourages further attacks.
Similarly, when defenders primarily focus on mitigating compromised accounts without addressing fraud accounts and allow the attacker to substitute fraud accounts with compromised accounts (and vice versa) that enable such compromises, it becomes a game of whack-a-mole. Attackers can quickly adapt using different versions, rendering the defender's efforts less effective. It highlights the importance of a comprehensive approach that addresses attacks' root causes and motivations rather than just their immediate manifestations.
Collaboration and information sharing among defenders are crucial to combat the tragedy of the commons in cybersecurity. By working together, sharing insights, and coordinating actions, defenders can pool their resources and knowledge to disrupt attackers more effectively. Additionally, engaging with law enforcement agencies and policymakers can help create an environment that discourages cybercriminal activities and imposes consequences on attackers.
Ultimately, the solution lies in a collective effort to create a more secure digital ecosystem. It requires a shift from a narrow focus on individual interests to a broader perspective considering cybersecurity defenses' everyday excellent and long-term sustainability.
How dark web Research can aid in Combating Cybercrime via an Infinite Game
The impact of insights obtained from the dark web
Inside looking out: When combating cybercrime, many companies leverage internal telemetry. This TTP telemetry has success in detecting and mitigating current attacks if monitored. However, through the dark web research project spanning over a decade, we have yet to see a discernible impact on the cybercrime industry. Defenders have had little to no impact on the attacker's M (monetization strategy) or long-lasting negative effects on the attacker's ROI.
The attacker's supply chain has matured to offer them significant services and the ability to switch from one TTP to another quickly. This also significantly reduced the barriers to entry of new bad actors while making the cybercrime industry more resilient, efficient, and effective.

Outside looking in: Leveraging dark web research can give companies a unique perspective on the attacker's motivations, supply chain, and monetization strategies. It offers valuable insights that can inform defenders of actions to disrupt the attacker's ROI and minimize their impact. Here are some key ways dark web research can contribute to combating cybercrime:
- Improve Security Posture: dark web research can provide companies with tips and insights to enhance their security posture, including identifying vulnerabilities, improving supply chain security, and implementing effective security measures from the attacker’s perspective.
- Understand the Attacker's Supply Chain: By delving into the dark web, it becomes possible to gain insights into the capabilities and workings of the cybercrime supply chain. This understanding can help identify chokepoints and vulnerabilities that can be targeted for disruption by the defender, industry groups working together, law enforcement, and other government and non-government agencies.
- Develop Relevant KPIs: dark web research can aid in developing Key Performance Indicators (KPIs) from the attacker's perspective. These KPIs help monitor the impact of disruptions on cybercriminal activities over time and assess the efficacy of specific actions taken.
- Create Distrust and Friction: Coordinated disruptions can be conducted to introduce distrust and friction within the cybercriminal supply chain. Targeting specific points of the supply chain can decrease the attacker's scale, erode their reputation on the dark web, reduce the predictability of their ROI, and increase the overall cost of their operations.
- Threat Assessments and Planning: During the planning phase, dark web research can be utilized to conduct threat assessments for new products and services. This allows product and service teams to proactively address potential attack vectors and strengthen security measures before launching a new product or service.
- Recover Pilfered Content: When content is stolen, dark web research can help recover and analyze the stolen data, providing valuable insights into the methods and techniques used by attackers.
- Consulting Services: dark web research teams can offer consulting services to aid various groups within the organization in understanding their threat profile and implementing appropriate security measures.
- Insider Threats: dark web research can provide intelligence on insider threats that may impact the company and its customers, enabling proactive mitigation and response.
- Attribution Research: When necessary, dark web research can contribute to attribution efforts, supporting civil actions and providing valuable information for law enforcement referrals.
By leveraging the insights gained from dark web research and targeting specific areas within the cybercrime ecosystem, companies can disrupt cybercriminal activities, decrease their scale and velocity, and increase costs, ultimately impacting their ROI and overall effectiveness.
Footnotes
(i) While defenders need to align their metrics with the objectives of bad actors to have a meaningful impact on cybersecurity, it doesn't mean that all internal health and success metrics should only focus on opposing the attackers. Defenders should still track and measure their operational effectiveness using traditional metrics that reflect their day-to-day activities and operational goals.
Defenders can achieve a comprehensive view of their performance by balancing operational metrics and success metrics that are diametrically opposed to those of bad actors. Operational metrics provide insights into the efficiency and effectiveness of their security operations. In contrast, success metrics aligned against bad actors' metrics indicate their impact on deterring attacks and reducing the attacker's ROI. In other words, the defenders have metrics that gauge when the defender wins and the attacker.
By combining these different sets of metrics, defenders can evaluate their performance from multiple angles and make informed decisions on how to improve their security posture. This holistic approach enables defenders to assess their operational health and effectiveness in countering cyber threats.
(ii) Disrupting the cybercrime ecosystem requires more than targeting individual attackers. It involves understanding the mechanisms and dynamics that allow cybercriminals to operate effectively. This includes exploring the anonymous and remote interactions in the cybercrime-as-a-service market, where trust is built within the cybercrime ecosystem.
To effectively combat cybercrime, defenders must work towards disrupting the trust, infrastructure, and support networks that sustain the ecosystem. This can involve law enforcement collaboration, intelligence sharing, targeted takedowns of infrastructure, and raising awareness about the risks and consequences of cybercriminal activities.
By addressing the cybercrime ecosystem, defenders can impose significant friction on cyber criminals, making it more challenging for them to operate efficiently and profitably. This approach recognizes the interconnected nature of cybercrime and the importance of disrupting the entire ecosystem to achieve meaningful impact.
(iii) Traditional defensive actions can lead to unintended consequences and long-term problems. Similarly, in cybercrime, solely focusing on eradication will prompt criminals to adapt and find new ways to continue their activities.
Applying excessive pressure or pursuing an approach of complete eradication in the cyber realm will have unintended consequences, such as driving criminals to develop new techniques, tools, or technologies to bypass defenses. It can also result in a constant game of cat and mouse, where defenders constantly play catch-up.
Instead, adopting a more holistic and sustainable approach, like integrated pest management in agriculture, can be beneficial. This approach aims to balance controlling pests and preserving the ecosystem. In the context of cybercrime, it involves creating enough pressure to deter and disrupt criminal activities without eliminating them.
By implementing effective cybersecurity measures, promoting awareness, collaborating with law enforcement, and continuously adapting defensive strategies, defenders can maintain a dynamic and proactive stance against cybercrime. This approach acknowledges that complete eradication may not be feasible. Still, by applying sufficient pressure and keeping cybercriminals in check, the overall impact of their activities can be minimized over the long term.
Just as allowing birds to control pests in agriculture can contribute to a healthier ecosystem, embracing a balanced and sustainable approach to combating cybercrime can help maintain a more secure and resilient digital environment.
(iv) Changing tactics, techniques, and procedures (TTPs) will vary in cost for attackers. Depending on the complexity and scale of the attack, the cost of changing TTPs can range from being relatively free to incurring some variable or fixed costs.
Changing TTPs may be as simple as modifying a few lines of code or using different tools, resulting in minimal or negligible costs. This is especially true for attackers with high expertise and flexibility in adapting their methods.
On the other hand, more sophisticated attacks or attacks conducted by organized cybercriminal groups may involve significant investments in developing new TTPs, acquiring specialized tools or services, or even recruiting skilled personnel. In such cases, there might be a variable cost associated with changing TTPs.
However, it's important to note that once attackers have developed or acquired new TTPs, they can often reuse them across multiple attacks, effectively amortizing the cost and making subsequent attacks relatively cheaper.
Therefore, while changing TTPs may involve costs, attackers can often absorb them quickly, especially considering the potential financial gains they seek through successful attacks. This highlights the importance of not solely relying on TTP-focused defenses but also addressing attackers' underlying motivations and ROI to create significant disruptions and deterrents.
(v) Attackers prioritize their return on investment (ROI) over minimizing costs. The primary goal for attackers is to maximize the gains they can achieve through their attacks, such as financial rewards or attaining specific objectives. As a result, they may need to allocate more resources or effort to minimize the cost of the attack itself.
It is typical for the research on the dark web, and attackers' cost of goods and services (COGS) aligns with the general understanding that attackers aim to optimize their ROI rather than minimize their costs. An attacker's COGS is commonly 10% but can be as low as 0.01% for their ROI. This further supports the notion that attackers prioritize ROI over reducing COGS.
Addressing TTPs, improving defender hygiene, and raising the bar against known and common attacks are essential defensive strategies. By understanding and mitigating known TTPs, defenders can enhance their security posture and protect against prevalent attack techniques. This approach helps to prevent successful attacks and reduce the risk of compromise.
While focusing on TTPs is crucial for immediate threat mitigation, it's also essential to consider a holistic defense approach that includes understanding attackers' motivations, objectives, and ROI. By gaining insights into the underlying factors driving attacks, defenders can develop proactive strategies that disrupt and deter attackers over the long term, even as they adapt and evolve their tactics.

