How NFC-Enabled POS Terminals Facilitate Cybercriminal Money Laundering Chains
Fraud Intelligence

Introduction
Chinese cybercriminals are especially active in NFC-enabled fraud and are known for their well-established money laundering chains across multiple continents. In previous threat intelligence reports dedicated to the Z-NFC tool and its alternatives, Resecurity has reported on the increase of NFC-enabled fraud originating from China. In addition to specialized tools, cybercriminals need to arrange for an NFC-enabled POS terminal and a merchant account linked to it to process payments.
Their terminal will allow them to perform illegal operations and launder stolen money via a controlled merchant registered with money mules. Getting started with NFC payments is a straightforward process, but it does involve specific requirements. To begin accepting NFC payments, cybercriminals need to prepare the following:
- NFC-Enabled Payment Terminal: The business will require a payment terminal that supports NFC technology. Customers make their payments at this terminal.
- NFC-Compatible Device: This can include smartphones, tablets, or other NFC-enabled devices. This is crucial if they use their devices to accept payments.
- Merchant Account: This should be arranged with a financial institution or payment processor. This account is essential for processing NFC transactions and receiving funds. Merchant accounts are typically registered for individuals or businesses.
This research is related to money laundering chains based on NFC-enabled POS terminals and the associated merchants, which play a vital role in this type of fraud. Without having them, cybercriminals must rely on other actors providing such services, often at a cost. Some of these actors require the cybercriminals to provide compromised payment data in advance to process it on their own, which always creates distrust between cybercriminals. That's why the most professional groups prefer to organize their merchants, whom they can control, to ensure that stolen funds will be collected in full.
Black Market of Merchant Accounts
Point-of-sale (POS) merchant account fraud involving money mules is a sophisticated financial crime in which cybercriminals use unwitting or complicit individuals to open legitimate-looking merchant accounts that are then used for fraud.
Cybercriminals typically recruit money mules through:
- Job scams advertising work-from-home opportunities
- Social media platforms
- Email solicitations
- Dating site scams
- False business partnerships
- Money mules are directed to apply for merchant accounts using their legitimate personal information.
- Criminals provide fake or deepfake business documentation to support the applications.
- The mule's clean credit history and legitimate identity help pass initial security checks.
- Once approved, the cybercriminals take control of the merchant accounts.
The fraudulent merchant accounts are then used for:
- Processing stolen credit card numbers
- Running unauthorized transactions
- Laundering money from other criminal activities
- Creating shell companies for further fraud
Multiple actors have been identified opening merchant accounts and using NFC-enabled terminals to perform fraudulent transactions. There is high demand for them on the Dark Web. Cybercriminals sometimes ask each other to ship them activated terminals for further use (with activated eSIM cards for data).
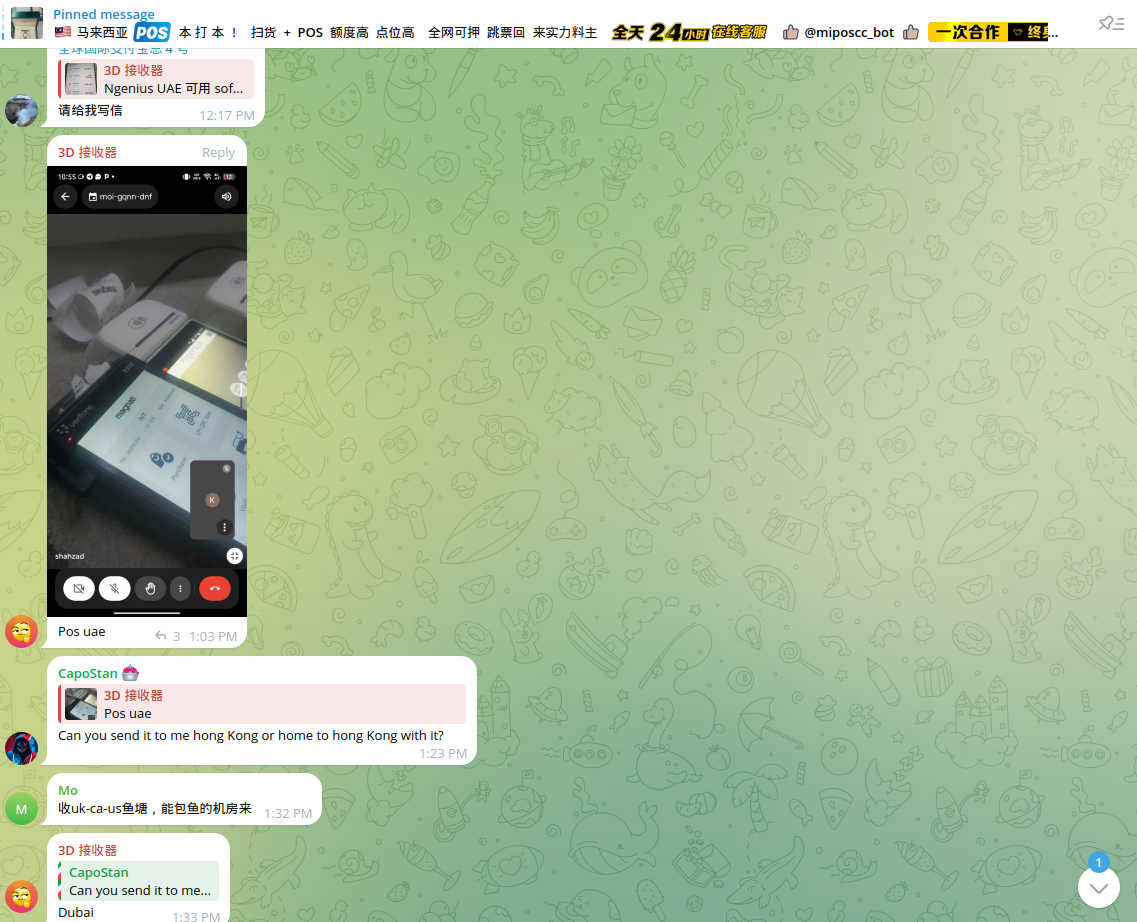
Typically, cybercriminals negotiate the conditions under which they will split the profits from successful fraudulent transactions. The most common model involves equal commission sharing. However, the actor responsible for the POS (Point of Sale) merchant may receive a larger share, as they will have to handle additional payout fees for their associate(s).

The terminals could be deployed in any geography, depending on the countries where potential victims reside, as their cards may have different limits based on the origin of the transaction and the destination merchant account. For example, if the transaction is performed domestically, the limit is likely much higher than a transaction conducted abroad. That's why cybercriminals prefer to set up merchant accounts and NFC-enabled POS terminals in the same country as their victims, targeting large-scale businesses that can process a high volume of transactions. This allows fraudulent operations to blend with legitimate ones; otherwise, payment processors may quickly block such merchants. For example, in one of the identified instances, cybercriminals targeted POS systems at a large hotel chain that services many customers worldwide. In such a scenario, they will need an insider to facilitate further laundering to cash out stolen funds. That's why they are looking for business owners who are not against earning some "dirty money" on the side.

Multiple fraudulent merchants tied to various businesses, such as restaurants, stores, entertainment venues, car rental services, and fuel stations, have been identified. In several postings, Chinese cybercriminals searched for the owners of these businesses in different countries to negotiate the terms of cooperation.
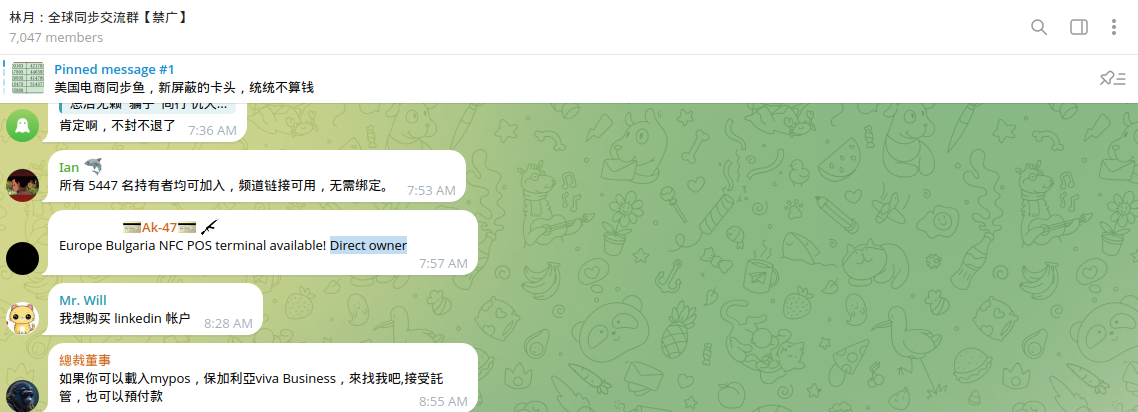
The volume of fraudulent transactions may vary. For example, one of the groups identified by Resecurity could process between $25,000 and $80,000 per day, so it was looking for a reliable partner to handle the money laundering.

Typically, owners of fraudulent merchants supporting NFC offer services and specify the exact volume they can process. Their merchant accounts will be terminated, and they will have a limited time to move or withdraw stolen funds. The payout to associates is typically arranged via cryptocurrency.
As NFC technology became more widespread, reports of fraud and carding incidents started to emerge, mainly as mobile payment systems like Google Wallet and Apple Pay were introduced. The actors use Android-based phones and tools like Z-NFC, covered in our previous report, with numerous cards loaded into mobile wallets for further fraud. This is why cybercriminals prefer to use NFC-enabled terminals to process such transactions.

NFC-enabled POS Terminals - for Sale on the Dark Web
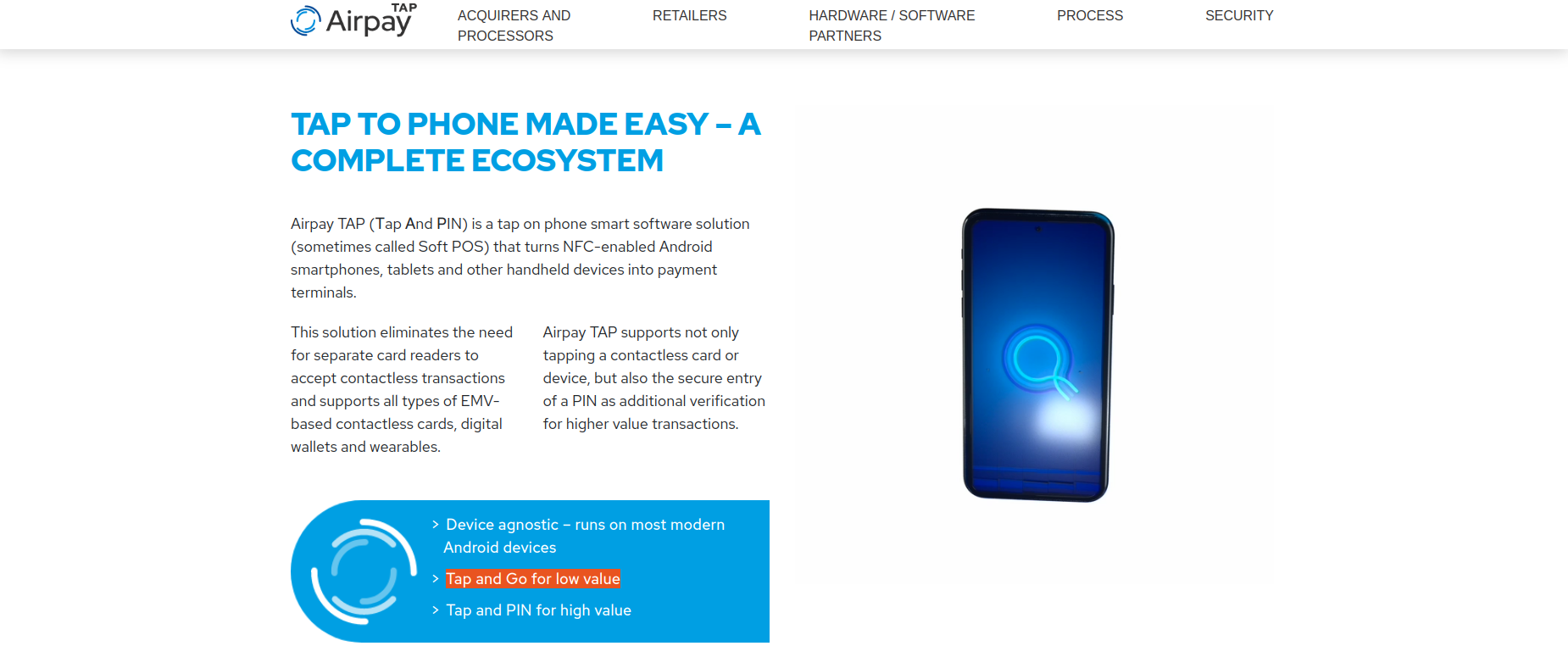
Why is NFC-enabled fraud still possible? Traditional payments typically require some Cardholder Verification Method (CVM) such as PIN or signature. For low-value contactless payments below the “Contactless CVM limit,” no CVM is needed—the consumer can Tap & Go. Note that the Contactless CVM limit varies from country to country. Besides traditional POS terminals, cybercriminals abuse tap-on-phone smart software solutions (sometimes called Soft POS) that turn NFC-enabled Android smartphones, tablets, and other handheld devices into payment terminals.
Cardholder verification is required for contactless card transactions above the CVM limit (e.g., by online PIN using the merchant PIN pad or signature). The merchant is liable for contactless transactions above the CVM limit without cardholder verification. Unfortunately, cybercriminals exploit this issue by executing multiple transactions below the limit while leveraging a high volume of compromised cards.
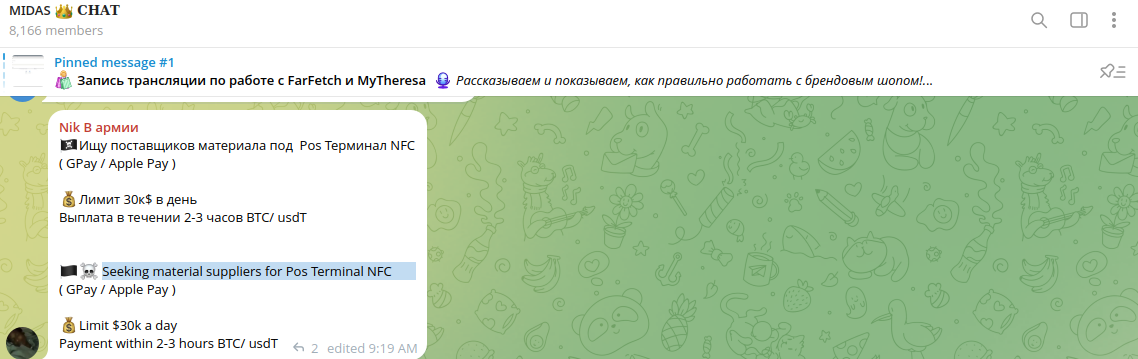
Resecurity identified multiple Chinese cybercriminal groups offering NFC-enabled POS terminals to facilitate fraudulent transactions and money laundering operations. The bad actors register these terminals with money mules, creating merchant accounts in various processing systems and financial institutions globally. Such fraudulent merchants have been identified in China, Malaysia, Nigeria, and South Africa.

Typically, these merchants have a daily limit, so cybercriminals are always looking for new ways to scale their operations by adding new money mules who can open accounts for a commission.
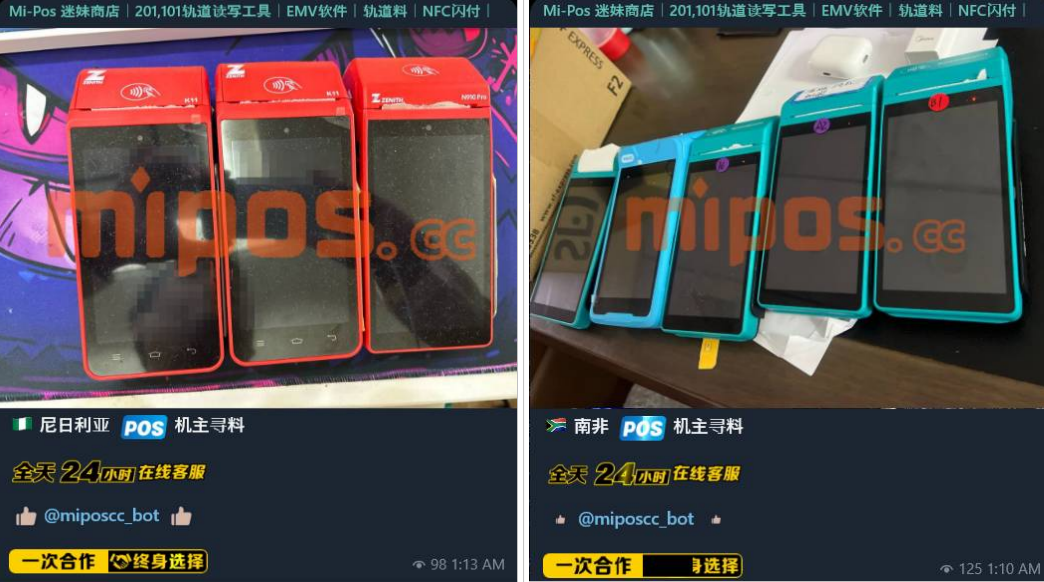
Chinese cybercriminals use stolen, compromised payment data to automate transactions using tools like Z-NFC and NFC-enabled POS terminals.
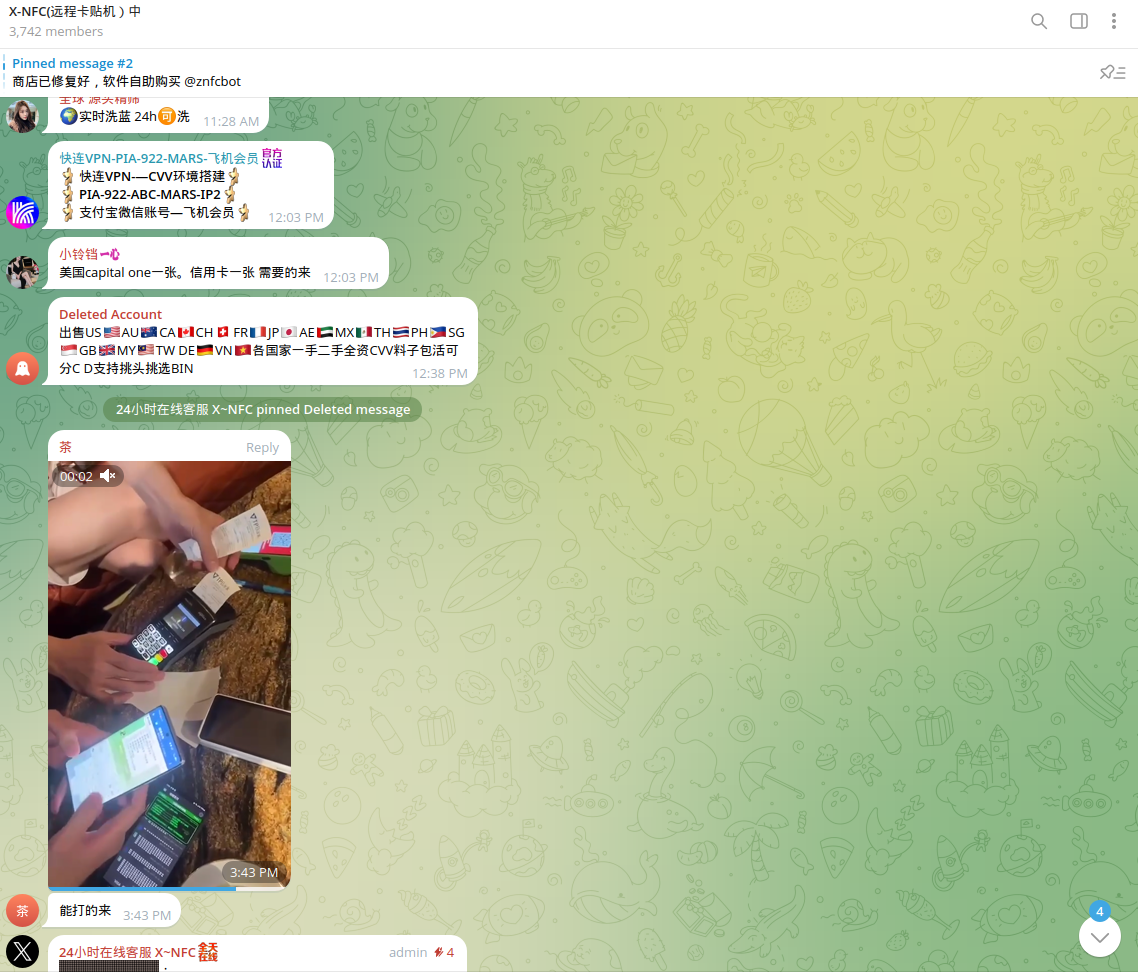
Cybercriminals sometimes abuse existing NFC-enabled POS terminals installed by legitimate businesses. This is typically done by dishonest insiders who use their businesses for money laundering—'double dipping' from both sides: their own business and cybercrime. Notably, such merchants are valuable to cybercriminals because they already have an established track record and history of legitimate customer transactions. As a result, it may take time to detect fraud involving them, and the seller may act as if they do not know anything about it.
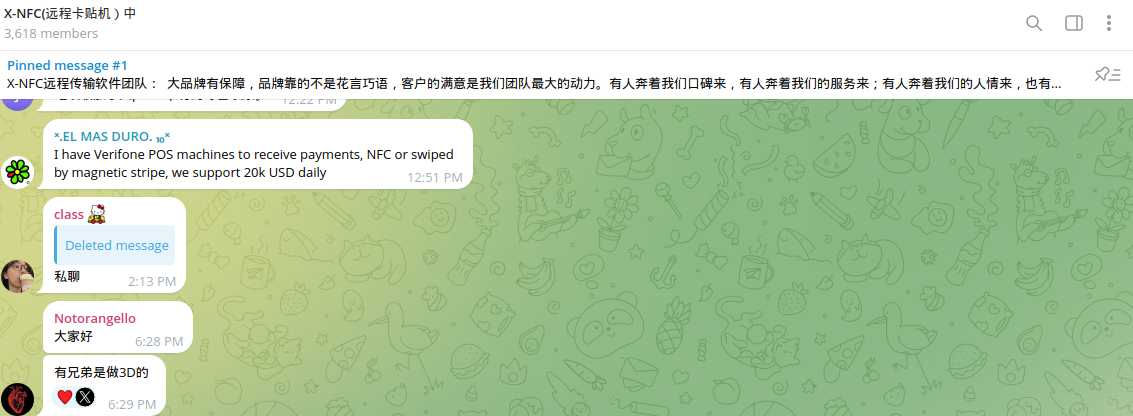
So-called "grey" merchants with NFC-enabled POS terminals are in high demand on the Dark Web. Chinese cybercriminals are looking for associates in different countries who can provide these terminals for criminal purposes.
In addition, various cybercriminal channels have been identified that offer equipment to orchestrate fraud via NFC, including NFC readers, compatible cards (white plastic), encoders, and other devices.
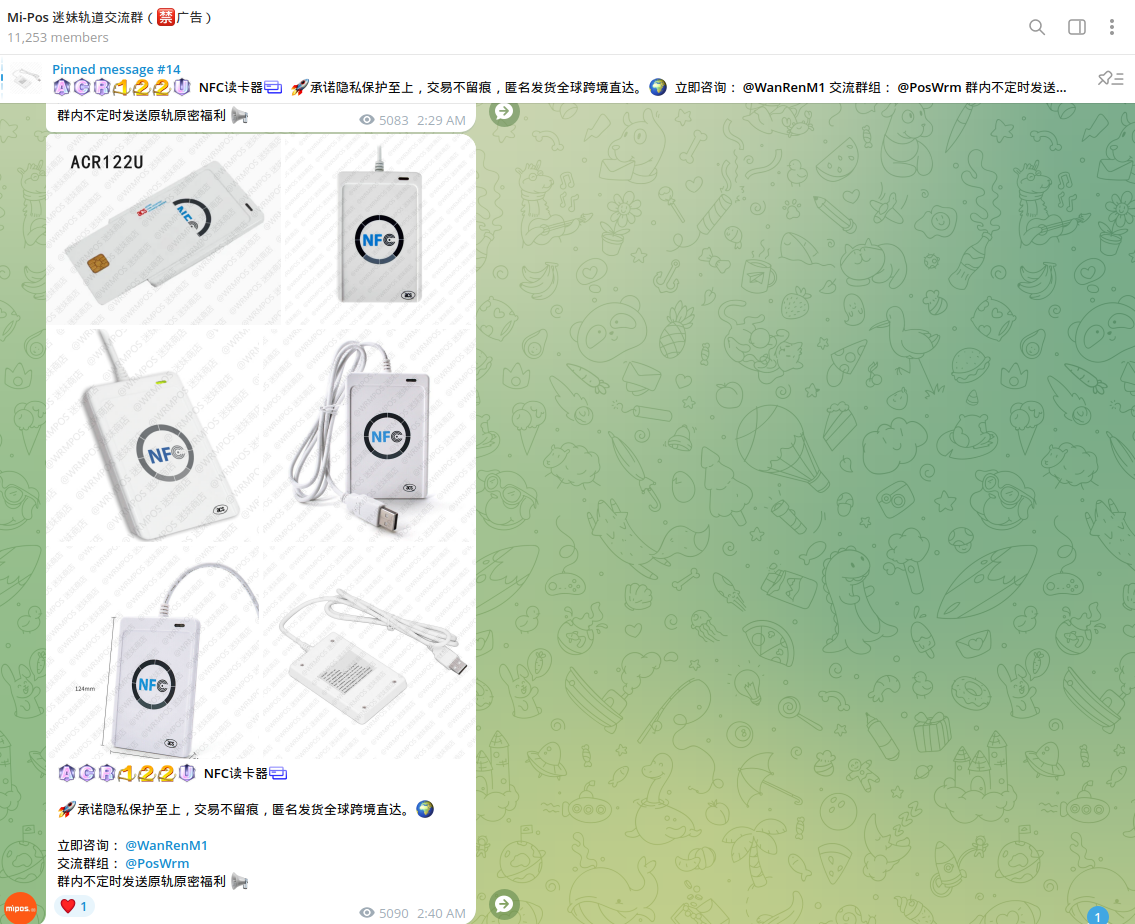
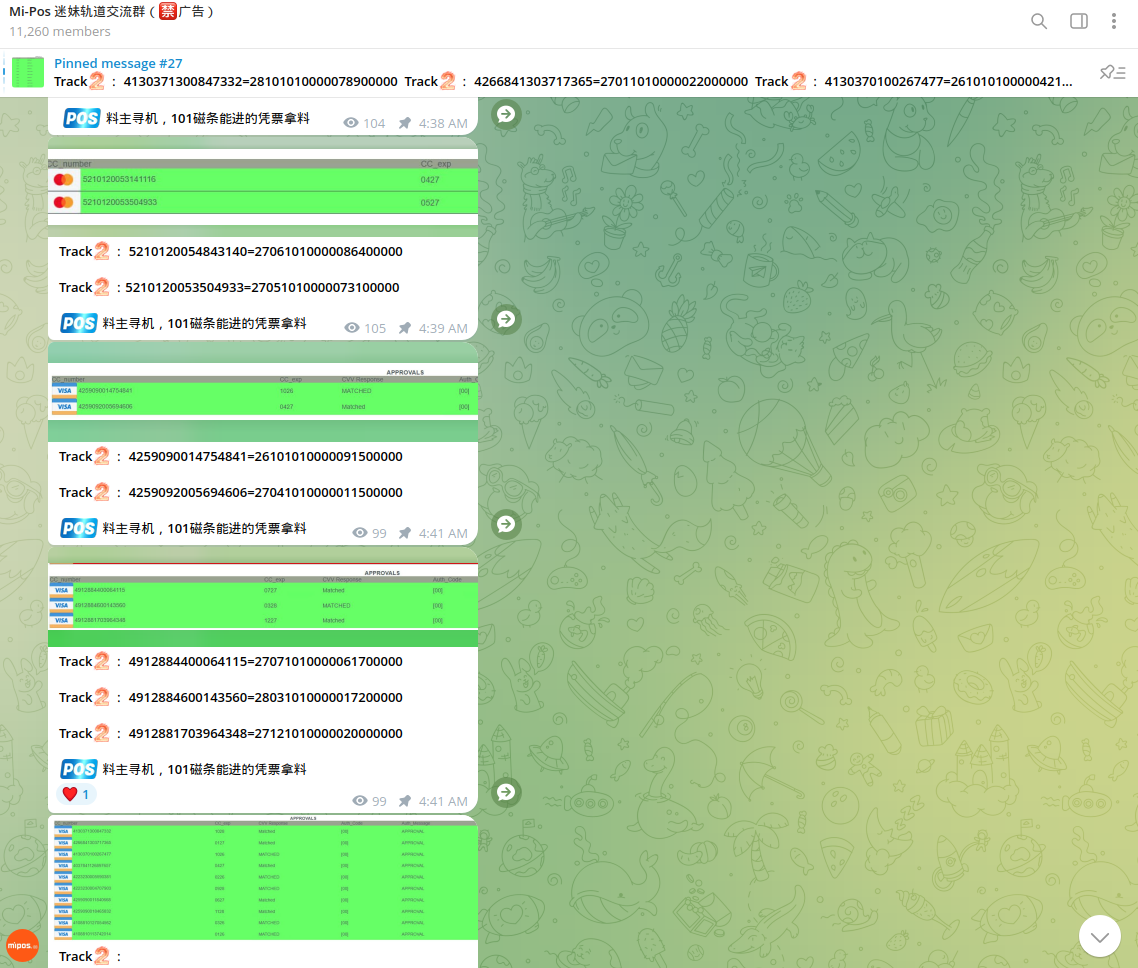
Cybercriminals use stolen Track 2 data, which is intercepted by ATM skimmers or acquired on the Dark Web, to record it on 'white plastic' and then use it on POS terminals.
On the same Telegram channel, they share samples of Track 2 data, exchanging experience and successful fraudulent operations.
Cybercriminals also sell e-SIM contracts to activate the Internet on POS terminals and communicate with payment gateways. These contracts can be activated by money mules or registered under fake details. Some of the e-SIM offerings have been observed to originate from Hong Kong, Japan, and the United States.
An e-SIM allows users to quickly switch between operators without needing a physical SIM card or a traditional internet connection, making cybercriminal operations extremely mobile.
Impact and Consequences
Merchant fraud can generate significant compliance and financial and reputational challenges for legitimate businesses and financial institutions. A lack of KYC and AML measures may result in regulatory penalties and other negative consequences for the company. Therefore, compliance officers must work closely with cyber threat intelligence teams, investigators, and fraud prevention teams to promptly detect possible suspicious activity and abnormal operations with POS terminals.
One of the main issues is that some fraudulent transactions are similar and are mixed with legitimate transactions. Therefore, it is critical to perform Dark Web monitoring and acquire actionable intelligence to avoid potential misuse and abuse by cybercriminals. NFC plays a vital role in the modern POS market and enables contactless payments globally. Cybercriminals will target such technologies at scale; therefore, financial institutions must develop preemptive tactics to defend themselves and their customers.
Non-compliance may result in significant issues for your brand, as well as create challenges in future audits by regulators:
For Financial Institutions
- Monetary losses from chargebacks
- Increased security costs
- Damage to reputation
- Regulatory compliance issues
For Money Mules
- Criminal or civil liability
- Damaged credit history
- Potential legal consequences
- Banking relationship difficulties
For Legitimate Businesses
- Higher processing fees
- Stricter merchant account limitations

