LogoKit update – The phishing kit leveraging Open Redirect Vulnerabilities
Cybercrime Intelligence


Resecurity, Inc. (USA), a Los Angeles-based cybersecurity company providing managed threat detection and response for Fortune 500's, identified threat actors leveraging Open Redirect Vulnerabilities popular in online services and apps to bypass spam filters to ultimately deliver phishing content.
Using highly trusted service domains like Snapchat and other online-services, they create special URLs which lead to malicious resources with phishing kits. The kit identified is named LogoKit, which was previously used in attacks against the customers of Office 365, Bank of America, GoDaddy, Virgin Fly, and many other major financial institutions and online-services internationally.
The spike of LogoKit was been identified around the beginning of August, when multiple new domain names impersonating popular services had been registered and leveraged together with Open Redirects. While LogoKit is known for a while in the underground, at least since 2015, the cybercrime group behind it is constantly leveraging new tactics.
LogoKit is known for its dynamic content generation using JavaScript – it is able to change logos (of the impersonated service) and text on the landing pages in real-time to adapt on the fly, by doing so the targeted victims are more likely to interact with the malicious resource. Around November 2021, there were over 700 identified domains names used in campaigns leveraging LogoKit – their number is constantly growing.
Notably, the actors prefer to use domain names in exotic jurisdictions or zones with relatively poor abuse management process - .gq, .ml, .tk, ga, .cf or to gain unauthorized access to legitimate WEB-resources, and then use them as hosting for further phishing distribution.
LogoKit relies on sending users phishing links that contain their email addresses. Once the victim navigates to the URL, LogoKit fetches the company logo from a third-party service, such as Clearbit or Google's favicon database. The victim’s email is then auto filled in the email or username field which consequently tricks them into feeling they’ve previously logged in before. Should the victim then enter their password, LogoKit performs an AJAX request, sending the target's email and password to an external source, then finally redirecting the victim to their “legitimate” corporate website.
These tactics allow cybercriminals to masquerade their activity behind the notifications of legitimate services to evade detection, thus tricking the victim into accessing the malicious resource. Unfortunately, the use of Open Redirect vulnerabilities significantly facilitates LogoKit distribution, as many (even popular) online-services don’t treat such bugs as critical, and in some cases – don’t even patch, leaving the open door for such abuse.
Let’s take a closer look at how it works on the example of the campaign identified in July 13th, it was targeting Office 365 users from the U.S. and Latin America:
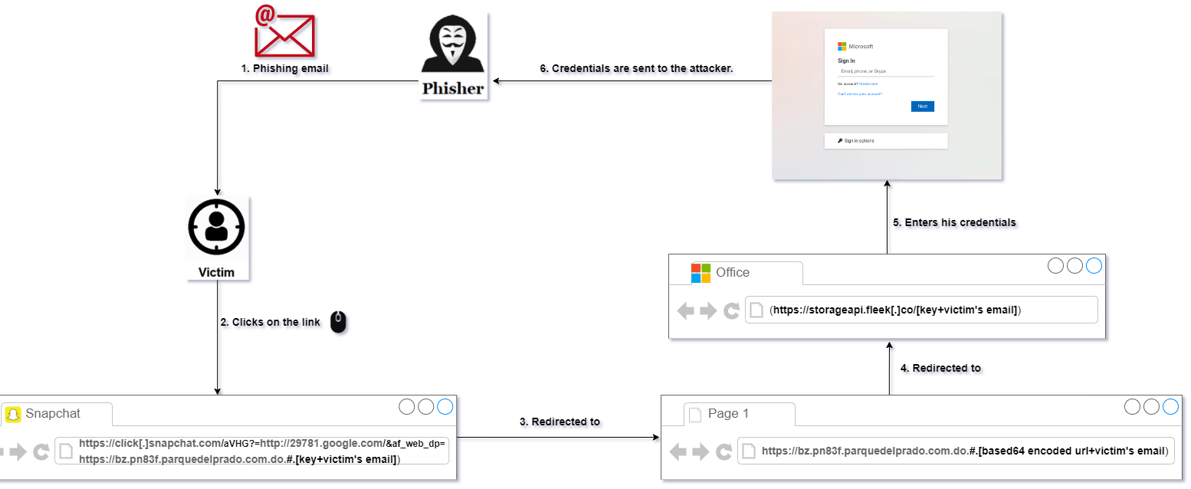
This is an example of an email containing text and a link with an embedded link inside it
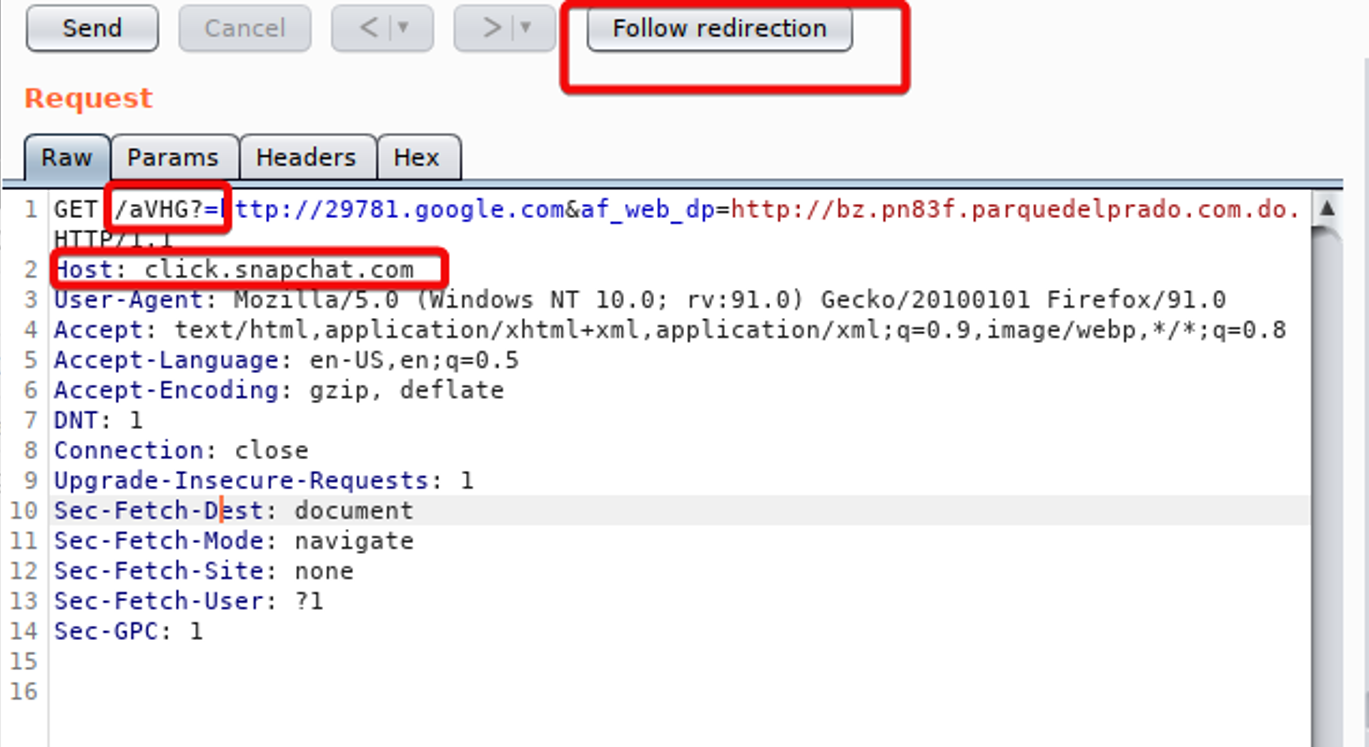
The embedded link is leveraging Open Redirect Vulnerability in Snapchat, and another URL from Google leading to a phishing resource:
Notably, some of the observed anti-spam mechanisms don’t flag such links as malicious scoring them as trusted.
Once we decoded it, we found another link which contains the email address of the victim in question:
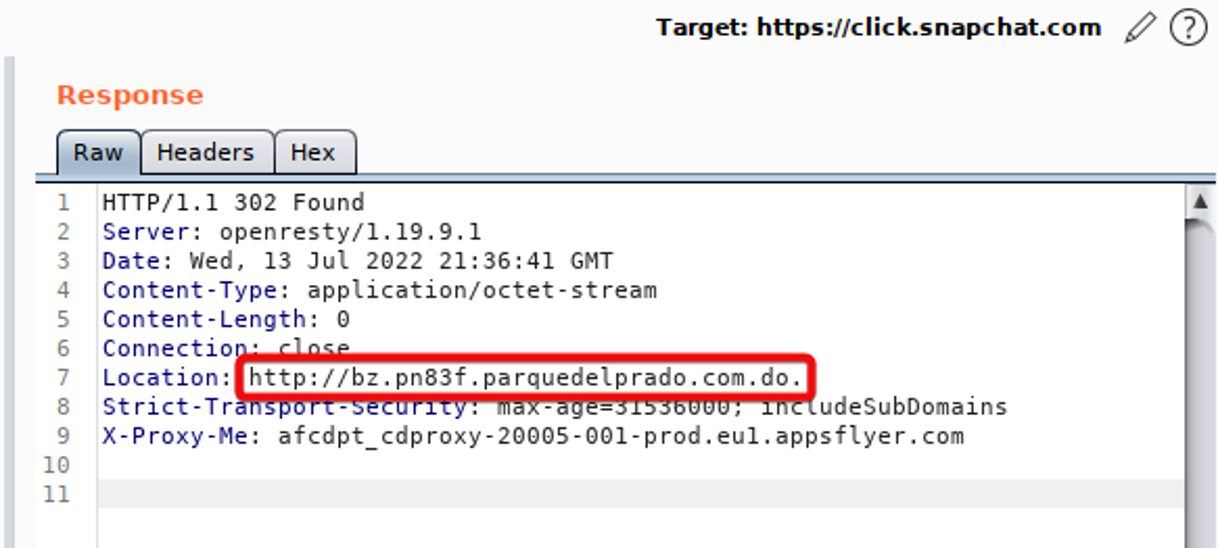
The attacker used the Open Redirect in Snapchat to redirect the victim to new URL http://bz.pn83f.parquedelprado.com[.]do
The content of the pages generated by LogoKit is typically obfuscated.
https://storageapi.fleek[.]co/0ad91b1c-9994-4a1d-bf88-18cf07dbaf52-bucket/continue.html?#contact@victim.com
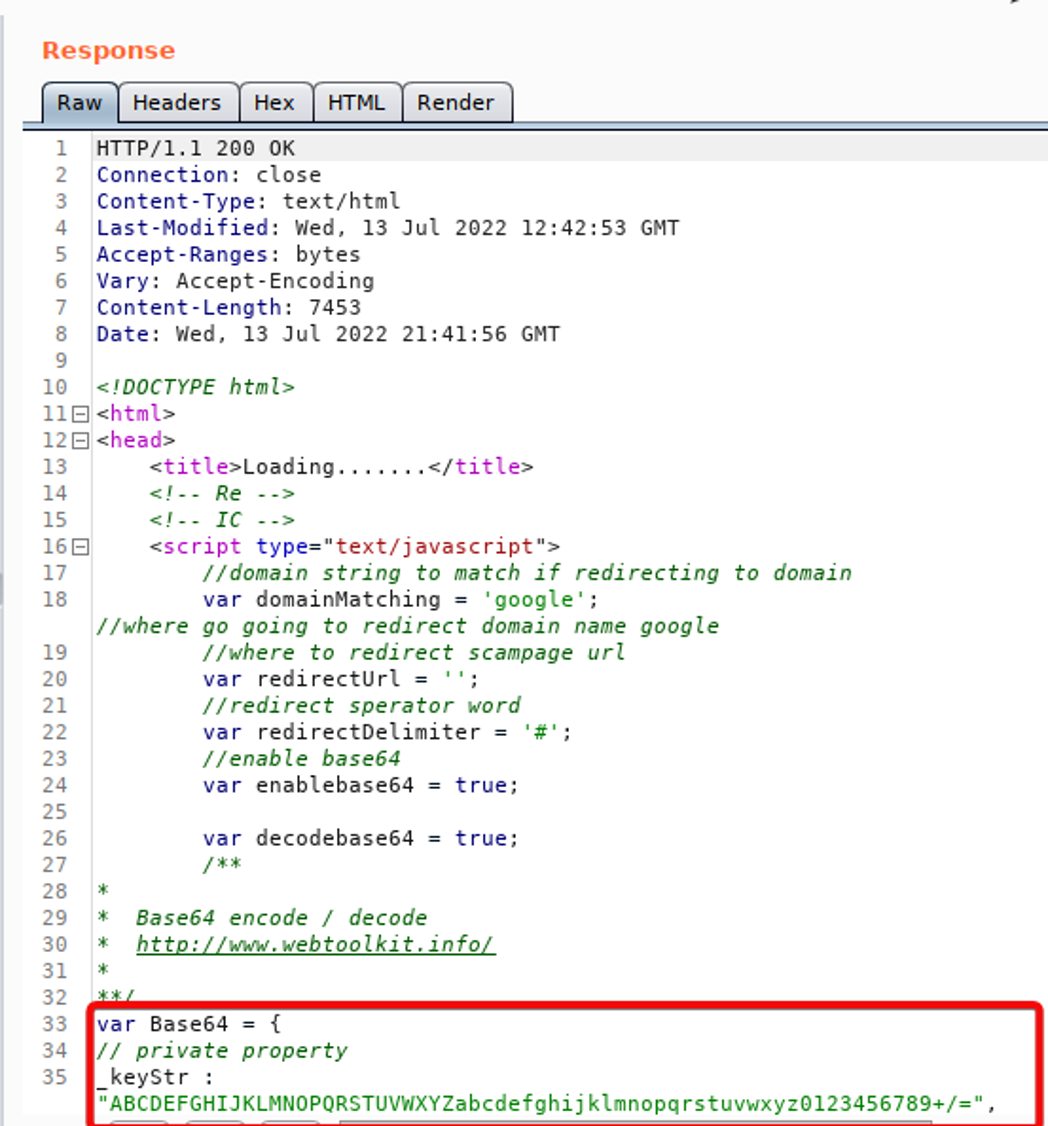
Here you can see the code that deals with the Base64 portion of the attack.
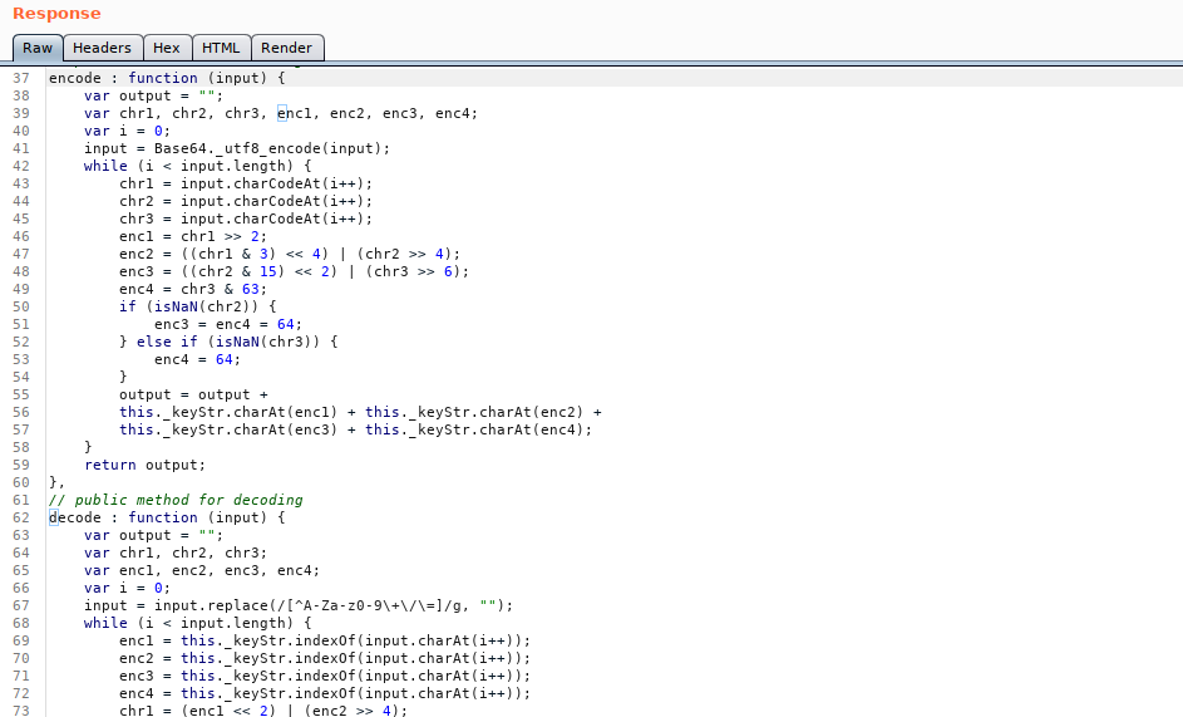
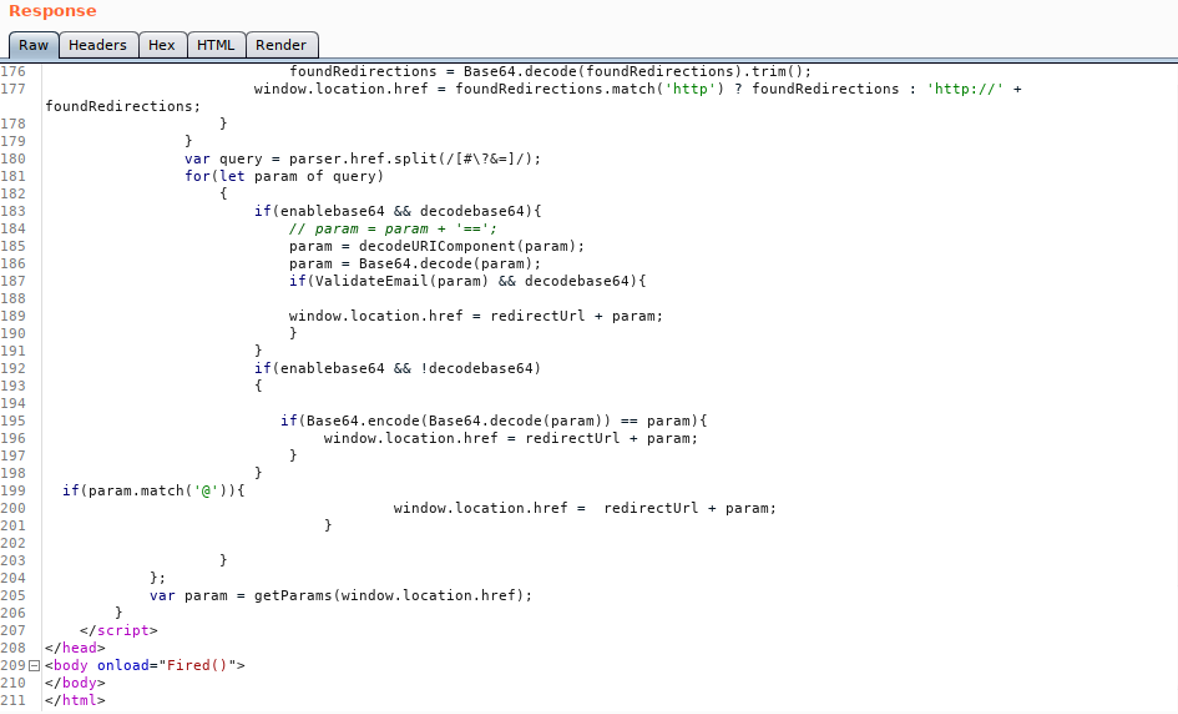
And here is the redirection part.
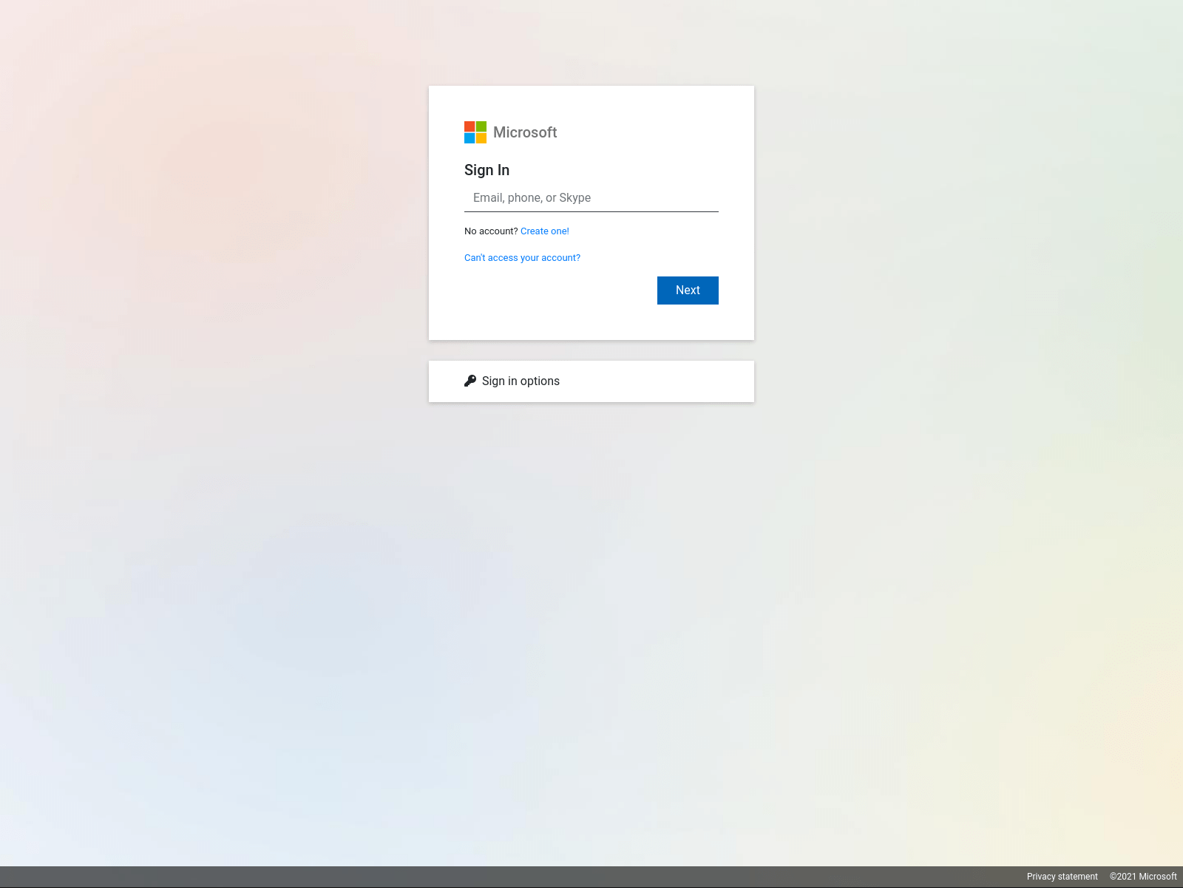
The final page is leading to phishing impersonating Microsoft Office 365:
Numerous others were identified with A records leveraging exactly the same domains:
https://urlscan.io/result/94a6995d-fa52-4007-acca-06a7effd168c/related/
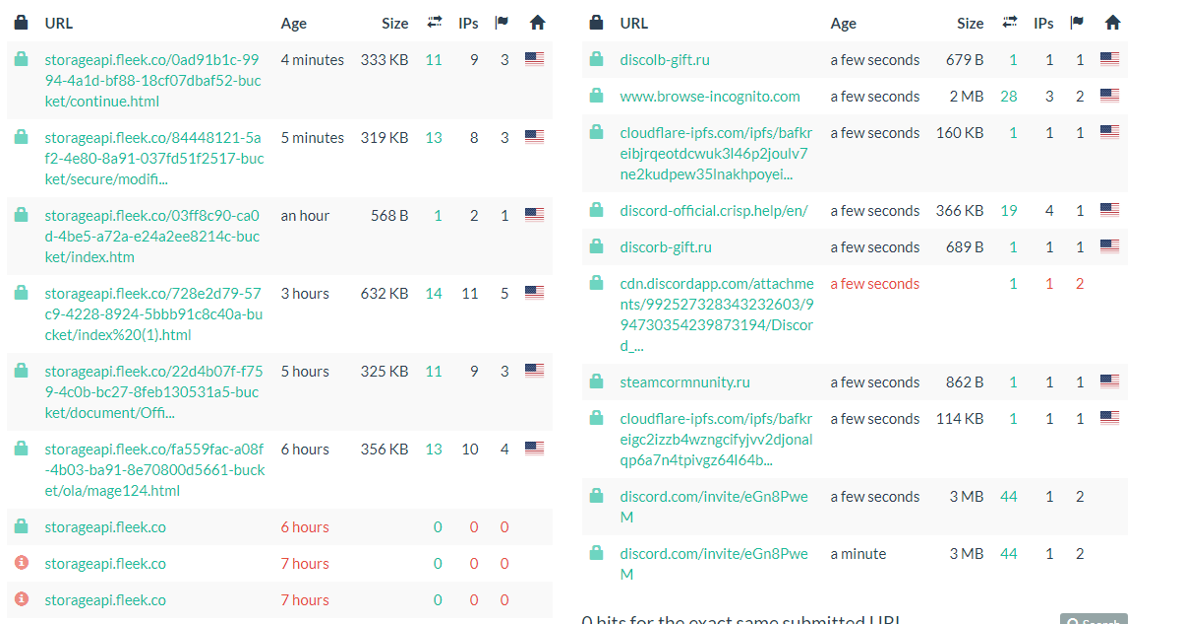
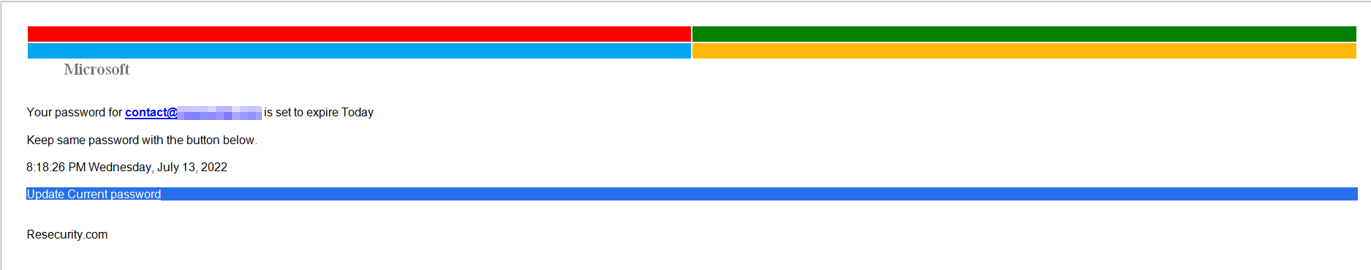
Initially, multiple victims received phishing links from compromised emails registered at GMX:
Password Notification Wednesday, July 13, 2022 8:18:26 PM |
|
<20221307201826FA327A984E$921DB1434A@gmx.net> |
|
Wed, 13 Jul 2022 20:18:26 +0000 (Delivered after 6 seconds) |
|
"Service Request" <tafuskazutcom4q@gmx.net> |
|
<contact@victim.com> |
Notably, the actors are using hacked WEB-resources leveraging the access to them for placing phishing without owners knowledge:
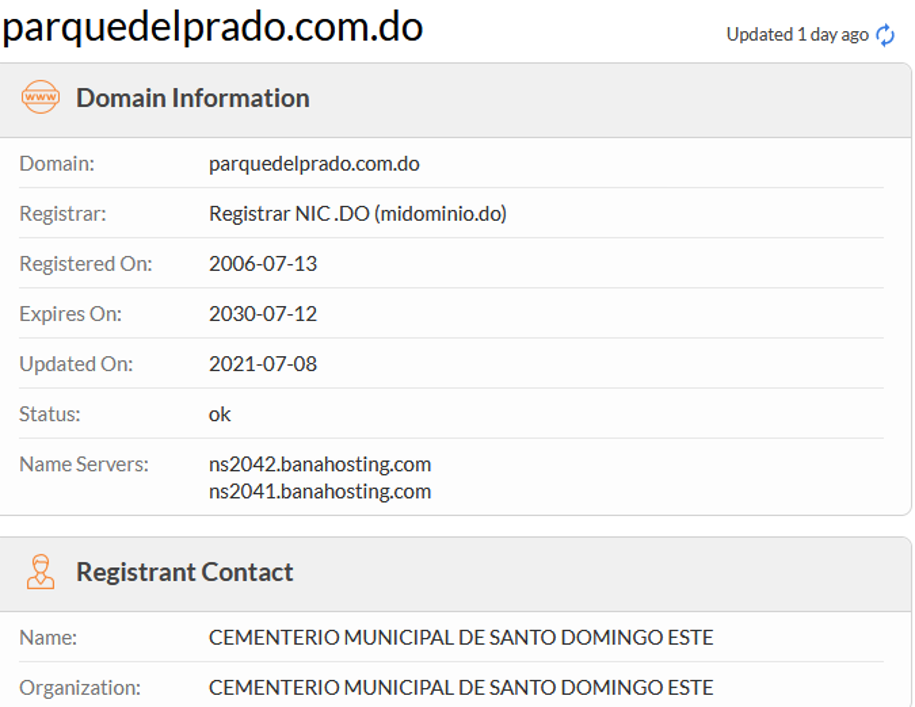
And here we can see how the attacker was using the fleek service to host their malicious code.
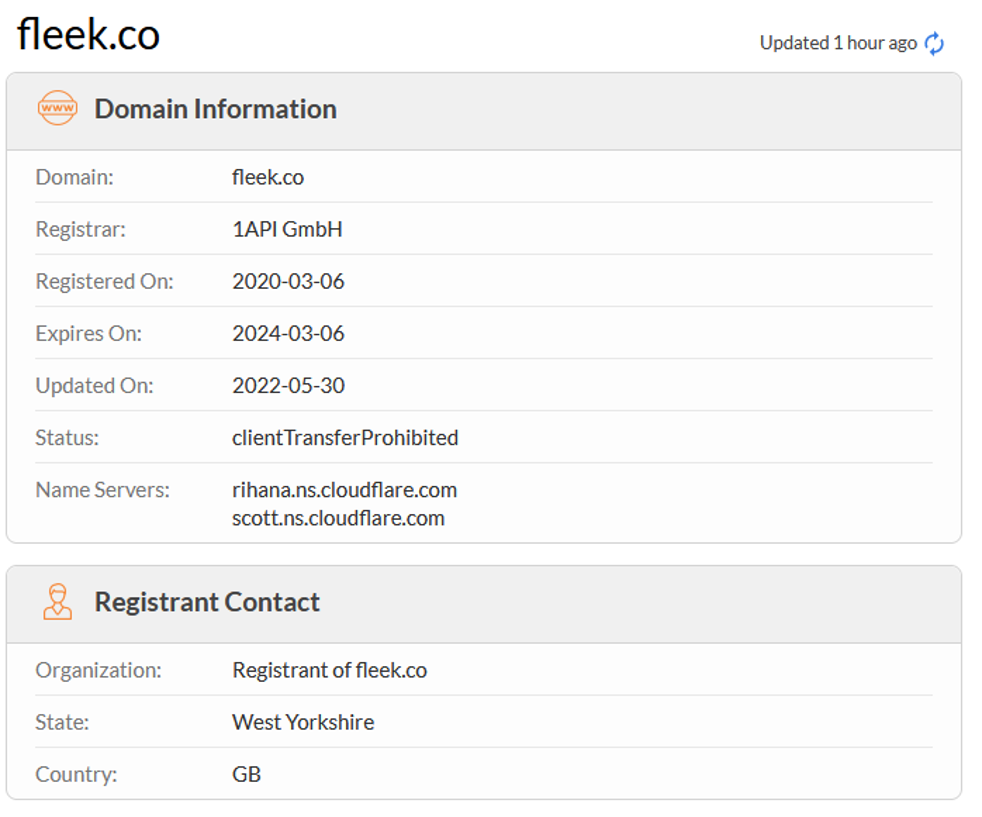
LogoKit have already been identified on more than 300 domains which took place over the past week, and more than 700 sites over the past month.
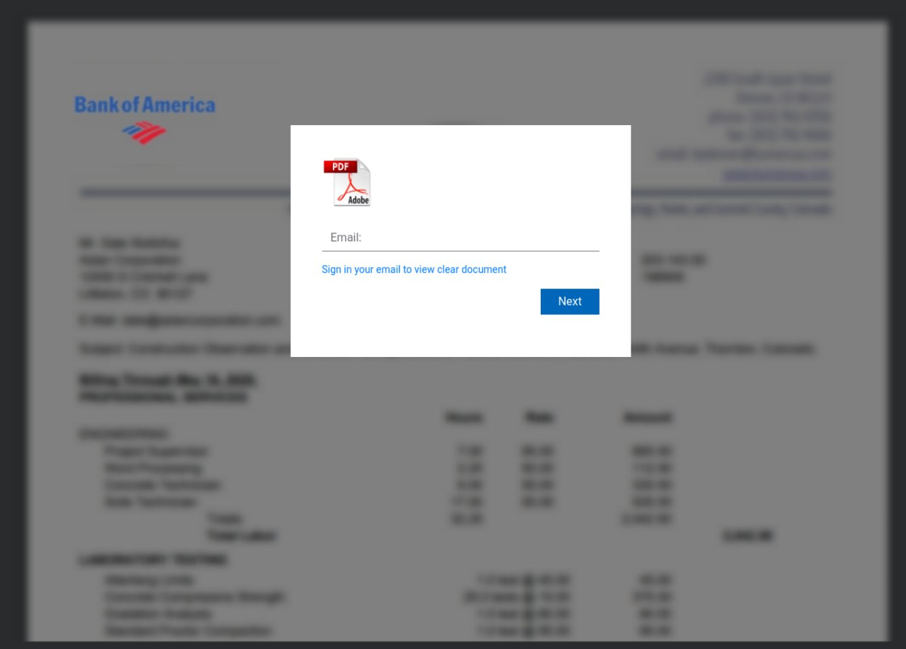
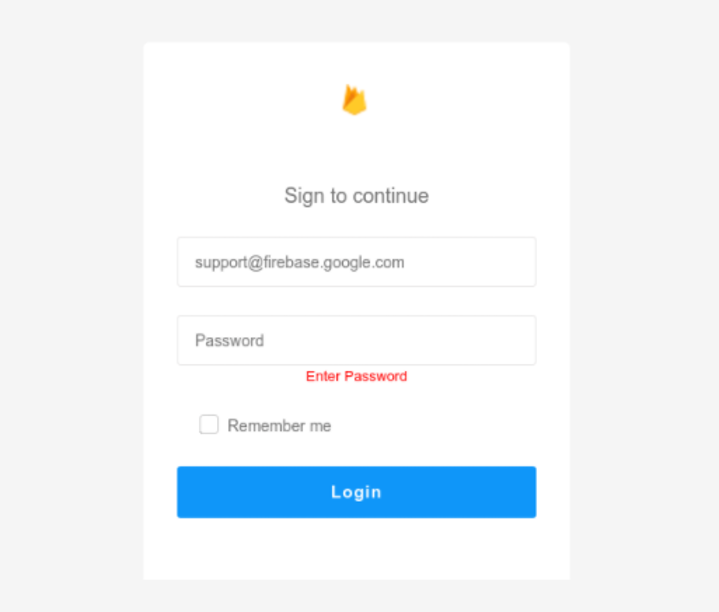
Some examples of various templates leveraged by LogoKit:
- Bank of America
- Virgin Fly
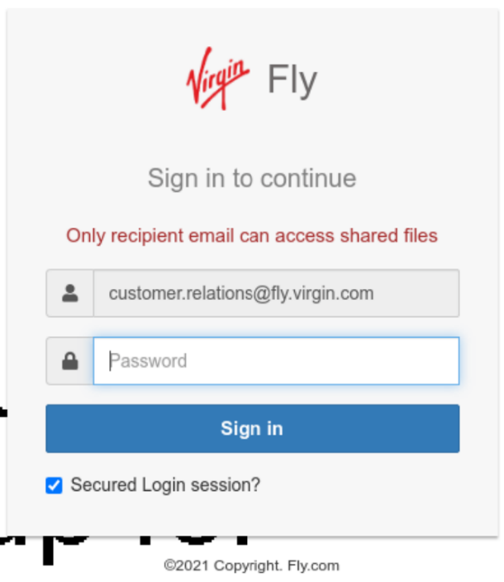
- Office 365
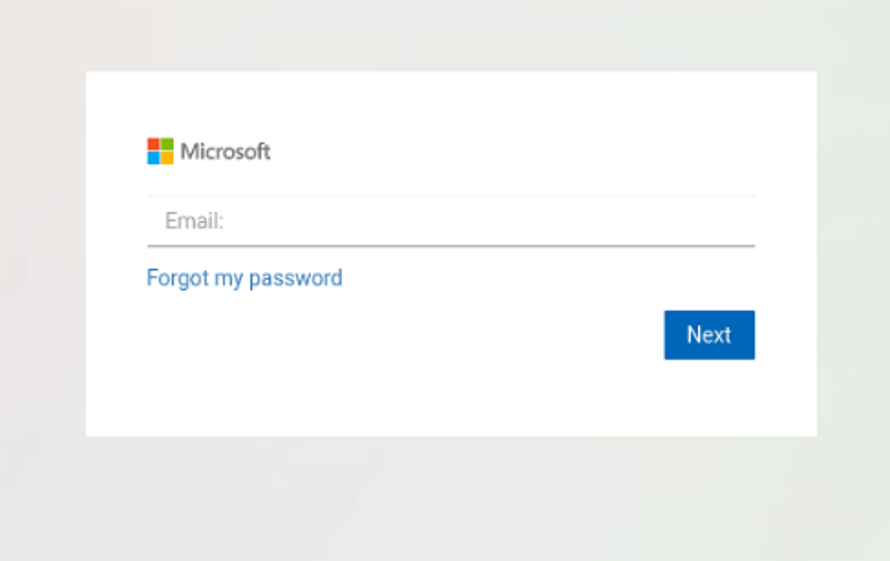
- GoDaddy
- Firebase
References:
https://urlscan.io/result/acee5510-cde3-4003-a2cc-940764f43bbb/
https://urlscan.io/result/3134f384-6bee-47cf-baa6-4786fed728d3/
https://www.zdnet.com/article/new-cybercrime-tool-can-build-phishing-pages-in-real-time/
https://community.riskiq.com/article/a068810a
IOCs:
fleek[.]co
storageapi.fleek[.]co/0ad91b1c-9994-4a1d-bf88-18cf07dbaf52-bucket/continue.html?#(emailaddress)
institutoaxioma.com.ar/ #(emailaddress) URL(http): /email25.godaddy.com-sign-realm.getforge.io/ #(emailaddress)
web[.]app, csb[.]app
us[.]archive[.]org
gl1hz[.]csb[.]app
ia801507[.]us[.]archive[.]org
cerstts[.]ga/100/wgbground

