

Resecurity® has identified a relatively new ransomware family called “Nevada Ransomware”. The actors behind this new project have an affiliate platform first introduced on the RAMP underground community, which is known for initial access brokers (IABs) and other cybercriminal actors and ransomware groups. On February 1st (2023), the operators behind the project updated and significantly improved the functionality of the locker for Windows and Linux/ESXi, and distributed new builds for their affiliates which have been analyzed by our malware intelligence team. Notably, identified were multiple updates of the locker in January - what may confirm how the project has good support and is actively developing.
Resecurity® HUNTER (the threat research & intelligence team) published exclusive screenshots and details acquired as a direct result of the Nevada Ransomware analysis. Part of this research is based on Human Intelligence (HUMINT), engagement with the actors responsible for inviting and vetting new affiliates. Notably, the operators behind the project combined ‘the best’ sides of known RaaS platforms as of today, and likely have an origin from one of the now closed projects, which is reborn under a new brand.
On December 10th, 2022 – the actor ‘nebel’ published a post describing the new project and then proceeded to invite new affiliates. The Nevada Ransomware offers very attractive and competitive conditions – 85% (to partner) with a further increase to 90% assuming further progress. Notably, the actors also acquired compromised access for further development besides being ransomware developers. Based on our current assessment, they have a team performing post exploitation to develop the initial point of compromise into full blown network intrusion to achieve maximum damage.
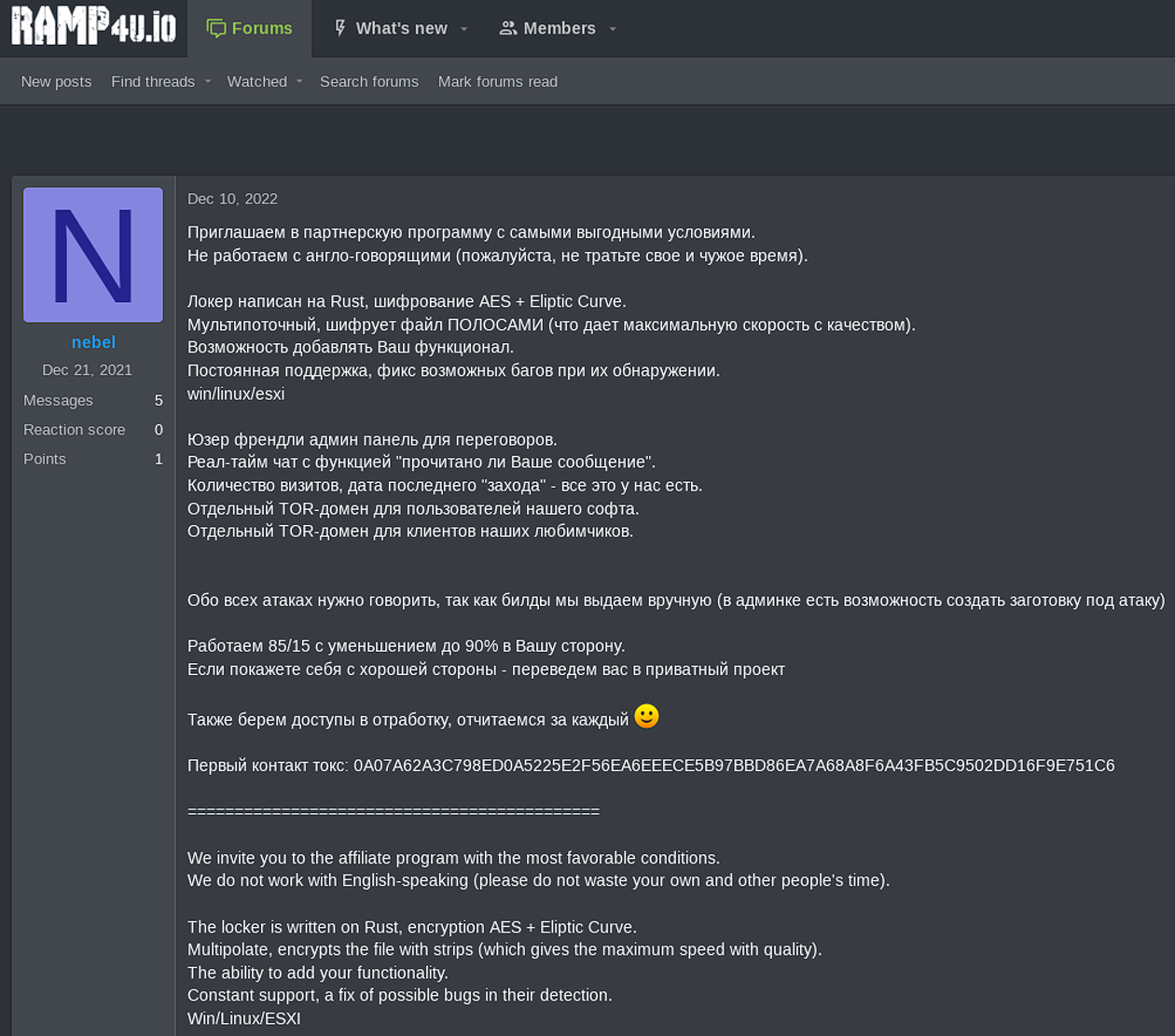
The post also contains a translation in English and Chinese – which may depict how the actors are interested in attracting a broader audience besides the Russian-speaking only audience. Interestingly, they contradicted themselves by stating how they don’t work with English-speaking affiliates. However, based on our assessment, the group is pretty open to doing business with vetted actors in the access brokerage niche – some of them have been identified with origins to ex-USSR, European Union, Islamic Republic of Iran and China, and previously they’ve been traced in hacked RDP and VPN suppliers for other ransomware networks.
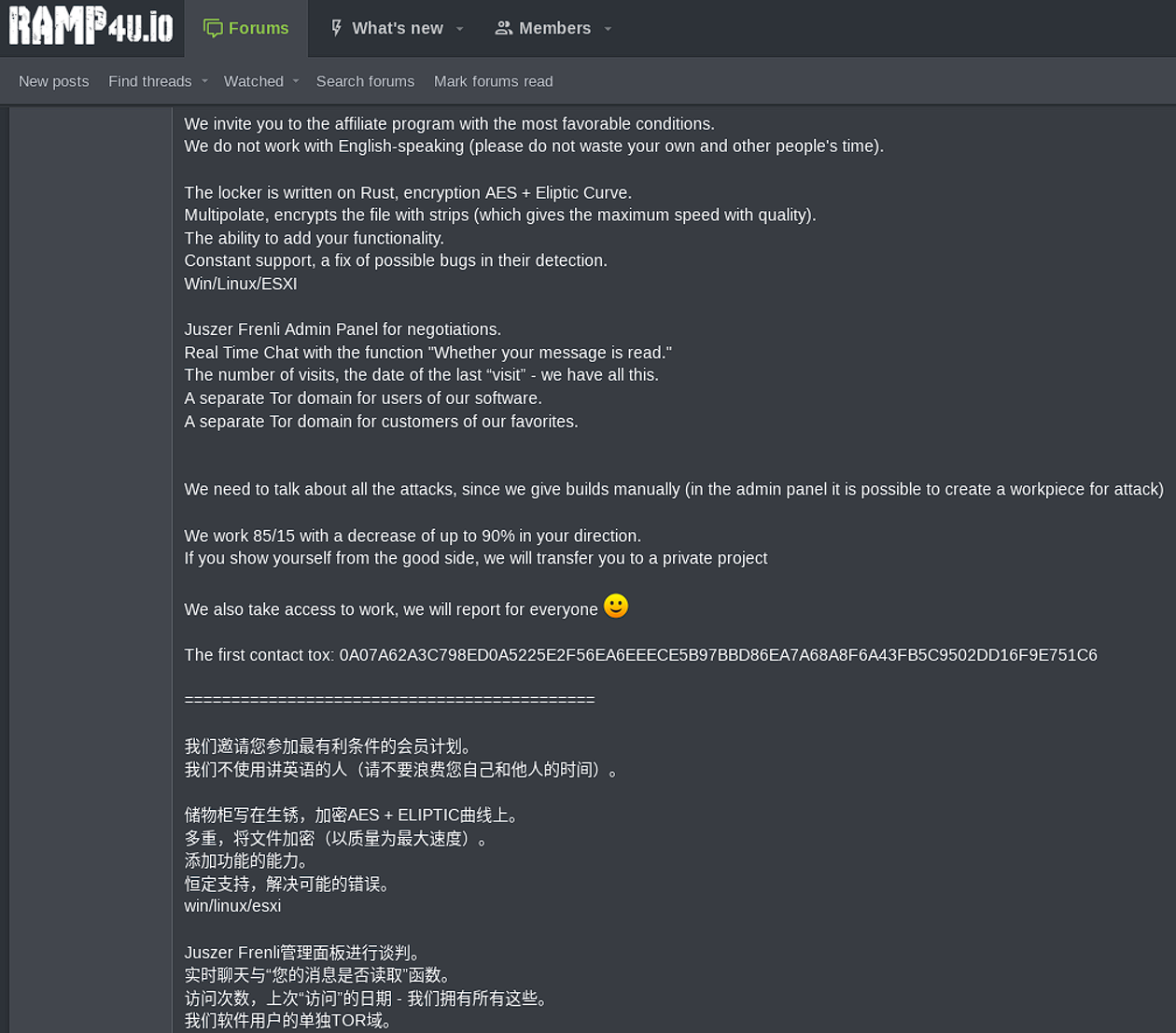
Some of the other actors present at RAMP ironically mentioned in a response to the Nevada Ransomware representative that the exclusion of English-speaking actors is bad for business. Many credible bad actors from the non-English-speaking countries communicate in English on criminal forums.
Resecurity was able to gain access to the affiliate panel hosted on the TOR network. The access is provided to affiliates after the initial vetting procedure. Such tactics are used for security purposes to ensure the affiliate is credible and won’t create risk for the project.
After a successful encryption procedure and/or data exfiltration, the operator may create a new victim via the panel:
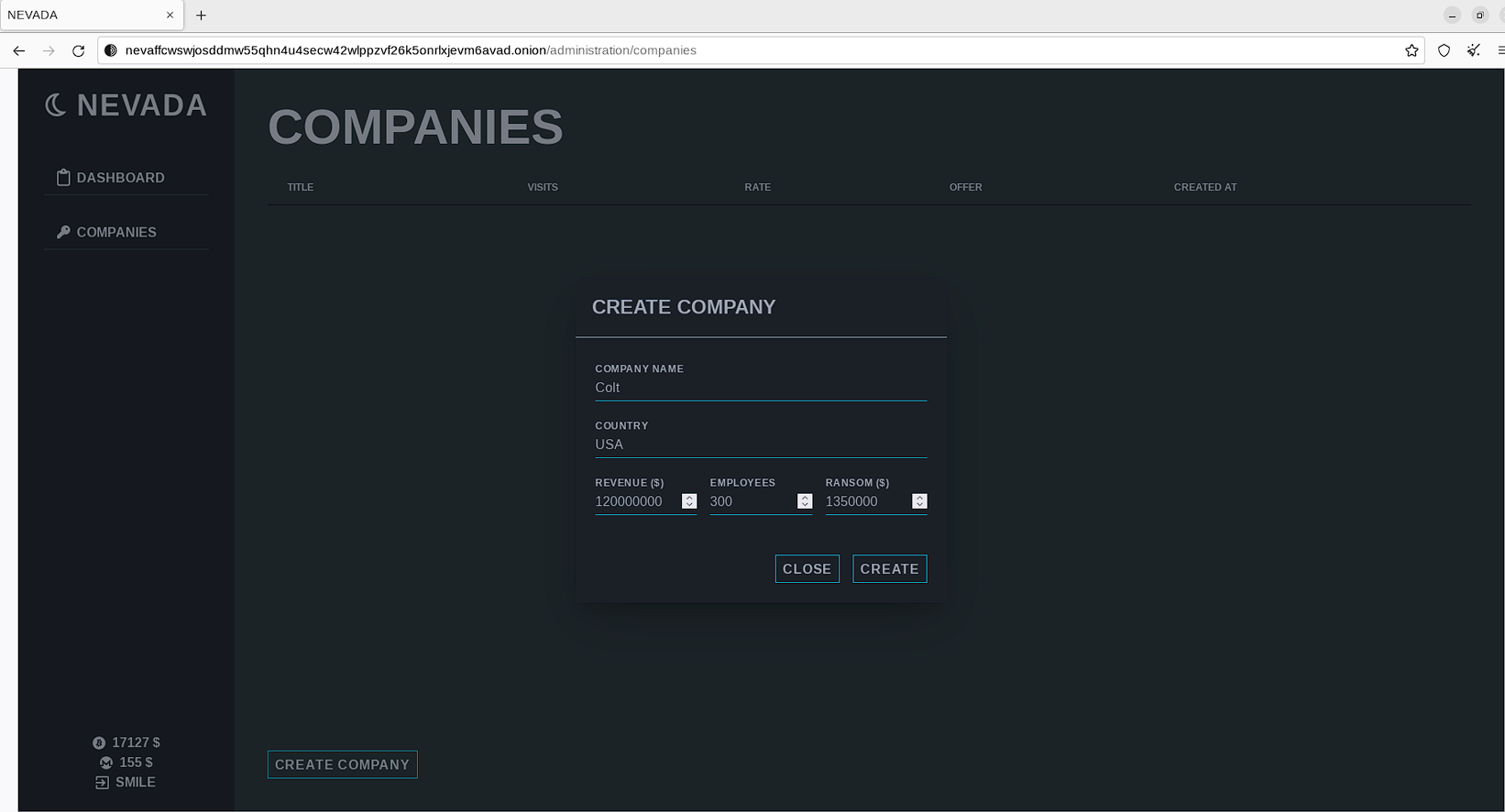
In the panel, the operator is required to define brief information about the victim (name, geography, revenue) along with a desirable ransom payment.
The victim will become visible in the list of companies for further tracking and communications via the available live chat. Similar chats were used by Blackhat, Lockbit, Hive and other notable ransomware projects to pressure victims into paying the ransom.
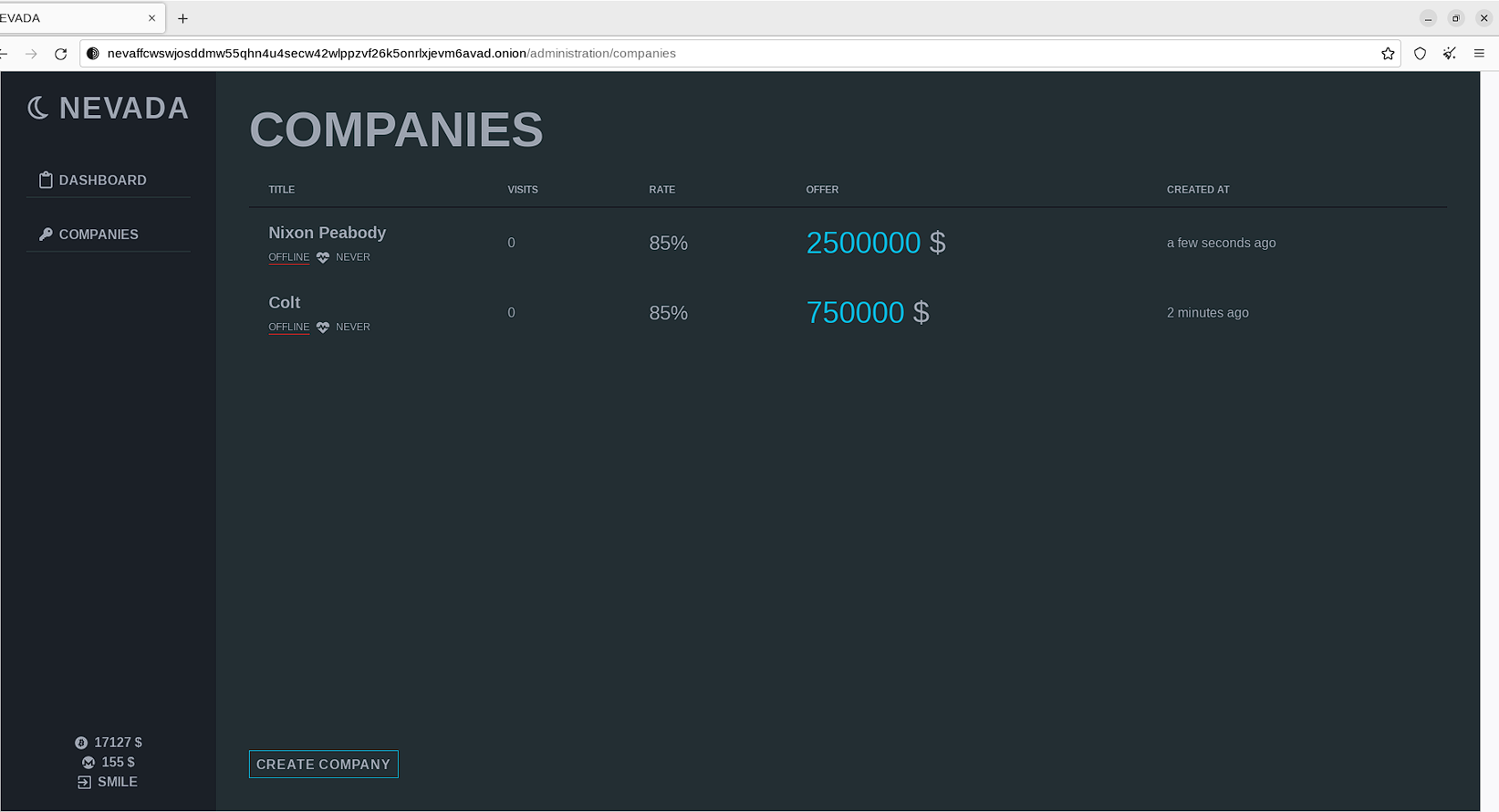
Each company which falls victim is added into the panel which then provides a dedicated work space to engage with victim.
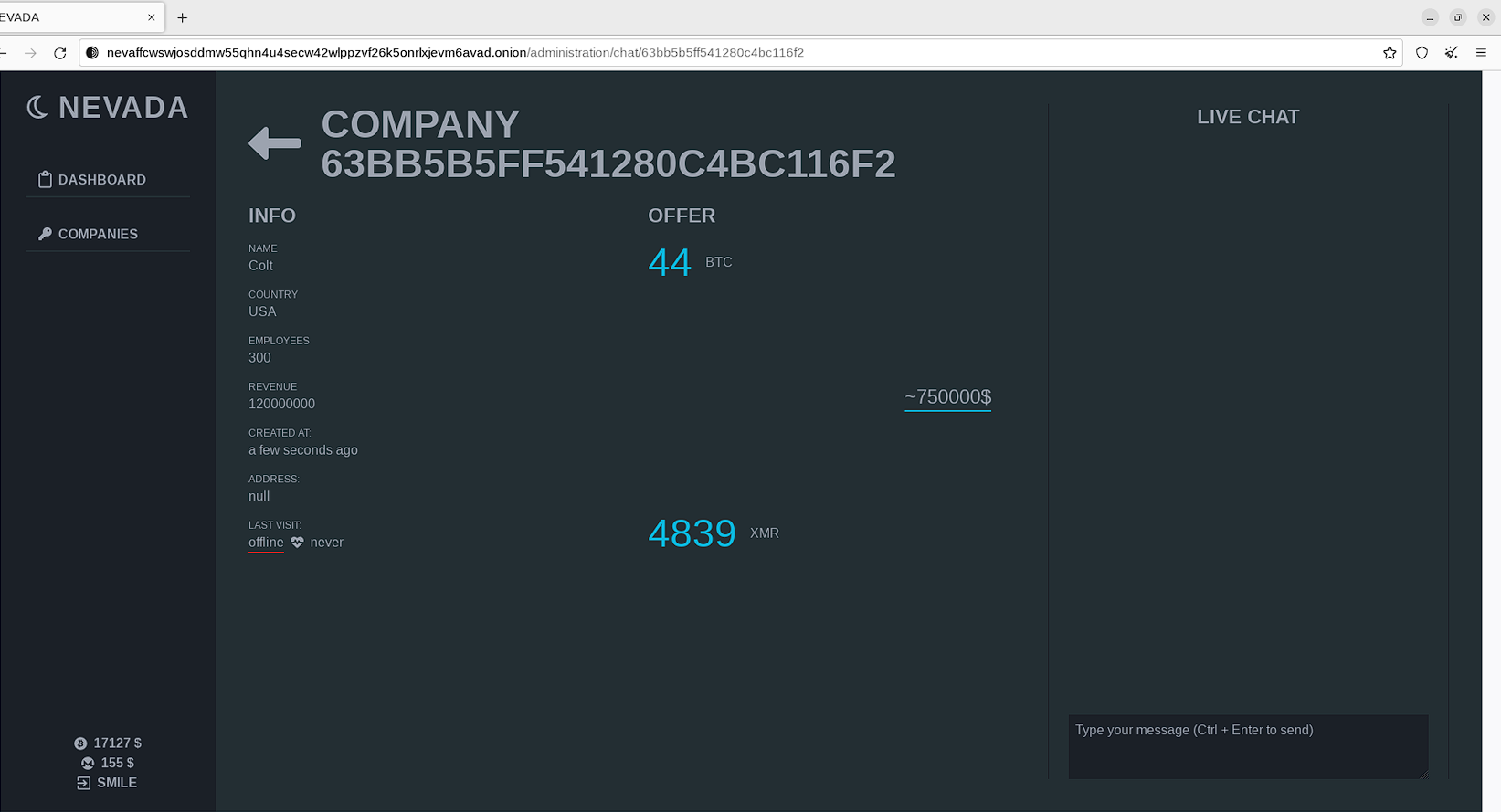
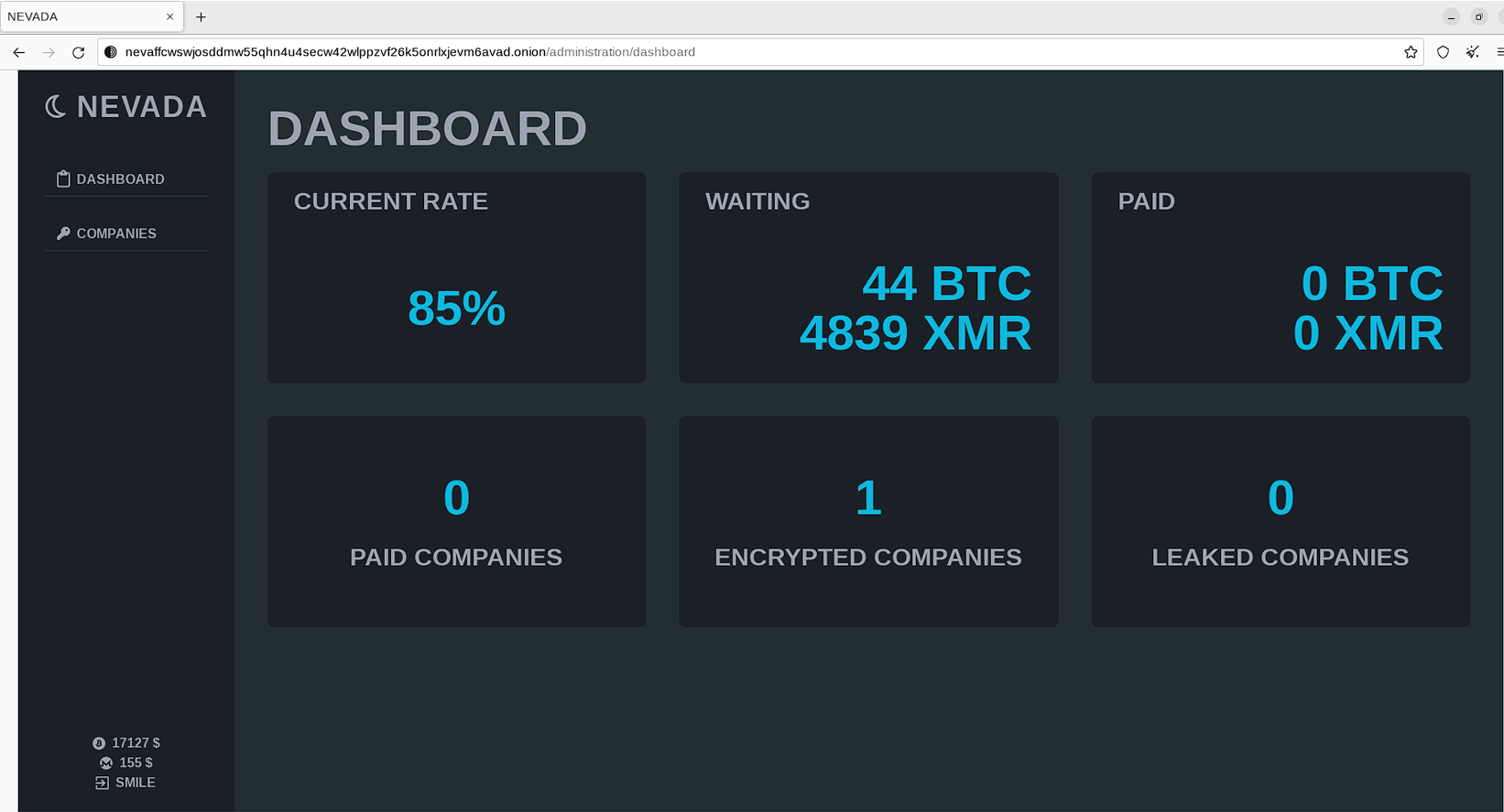
Later, the statistics with further details will be visible on the index page – with the status of the ransom payments.
Resecurity acquired Linux-based and Windows versions of the Nevada Ransomware. During the research we became aware of 2 released updates – these were released around January 20th and February 2nd with improved functional and significant tweaks in the affiliate portal.
- Nevada Ransomware (Windows Version x64):
Nevada Ransomware is written in the Rust language. Similar to Hive Ransomware, the locker can be executed via a console with pre-defined flags. Resecurity was able to recover information about the functions of each flag:
| -file | encrypt selected file |
| -dir | encrypt selected directory |
| -sd | self delete after everything done |
| -sc | delete shadow copies |
| -lhd | load hidden drives |
| -nd | find and encrypt network shares |
| -sm | safe mode encryption |
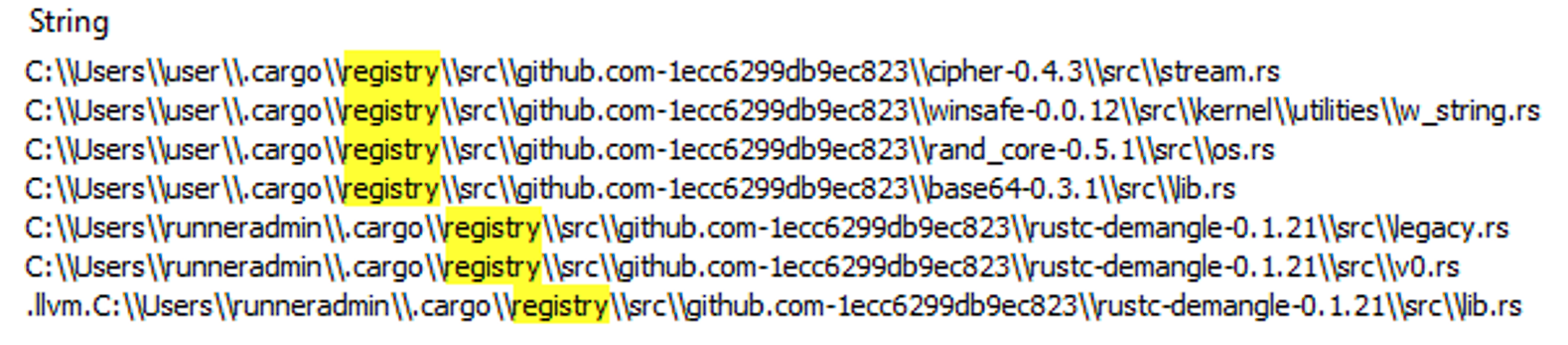
Nevada Ransomware is using the following Rust libraries (crates):
● https://github.com/RustCrypto/traits/cipher/
● https://github.com/marshallpierce/rust-base64/
● https://github.com/rust-random/rand/
● https://github.com/rodrigocfd/winsafe/ (old wrapper for WinApi functions)
● https://github.com/rust-lang/rustc-demangle/
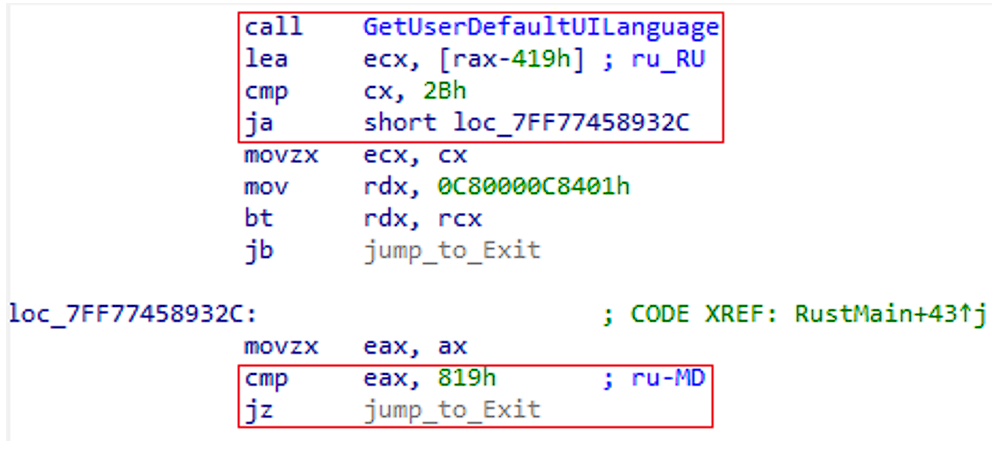
The encryptor is checking locales (see Figure 2), and doesn’t work with the following locales related to ex-USSR geographies, and what is more interesting - Albania, Hungary, Vietnam, Malaysia, Thailand, Turkey, Iran.
ru-RU |
0x0419 |
vi-VN |
0x042A |
se-NO |
0x043B |
hr-HR |
0x041A |
hy-AM |
0x042B |
yi-001 |
0x043D |
sk-SK |
0x041B |
az-Latn-AZ |
0x042C |
ms-MY |
0x043E |
sq-AL |
0x041C |
eu-ES |
0x042D |
kk-KZ |
0x043F |
sv-SE |
0x041D |
hsb-DE |
0x042E |
ky-KG |
0x0440 |
th-TH |
0x041E |
mk-MK |
0x042F |
sw-KE |
0x0441 |
tr-TR |
0x041F |
st-ZA |
0x0430 |
tk-TM |
0x0442 |
ur-PK |
0x0420 |
ts-ZA |
0x0431 |
uz-Latn-UZ |
0x0443 |
id-ID |
0x0421 |
tn-ZA |
0x0432 |
tt-RU |
0x0444 |
uk-UA |
0x0422 |
ve-ZA |
0x0433 |
ru-MD |
0x819 |
be-BY |
0x0423 |
xh-ZA |
0x0434 |
|
|
sl-SI |
0x0424 |
zu-ZA |
0x0435 |
|
|
et-EE |
0x0425 |
af-ZA |
0x0436 |
|
|
lv-LV |
0x0426 |
ka-GE |
0x0437 |
|
|
lt-LT |
0x0427 |
fo-FO |
0x0438 |
|
|
tg-Cyrl-TJ |
0x0428 |
hi-IN |
0x0439 |
|
|
fa-IR |
0x0429 |
mt-MT |
0x043A |
|
|
Table 1 – Locales that the encryptor doesn’t work with
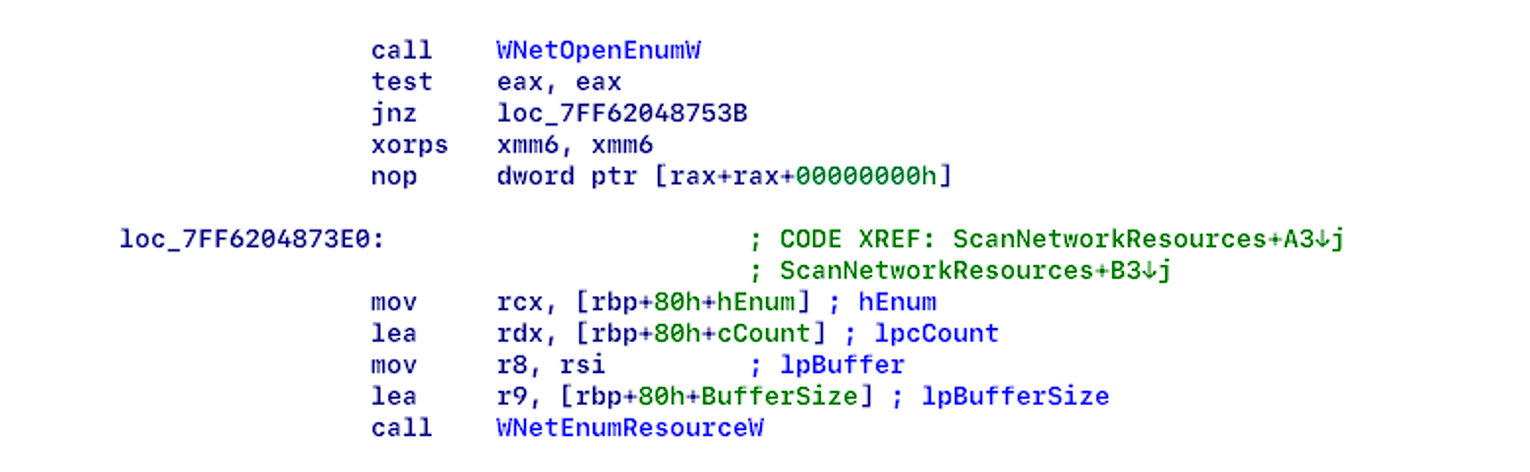
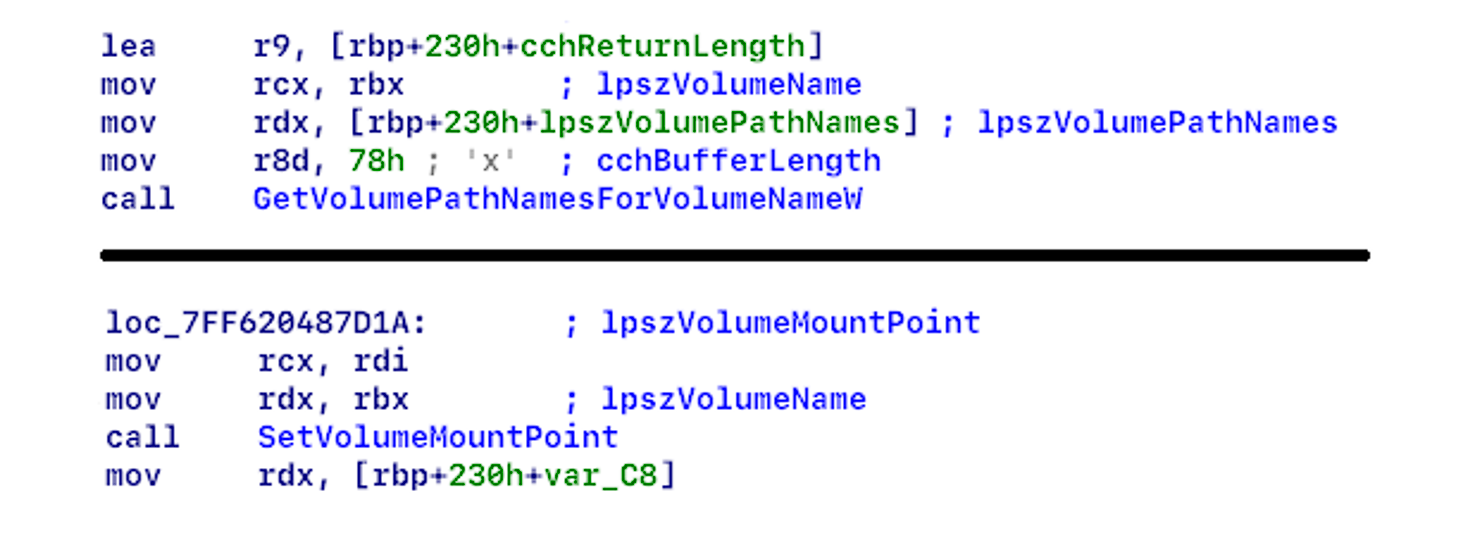
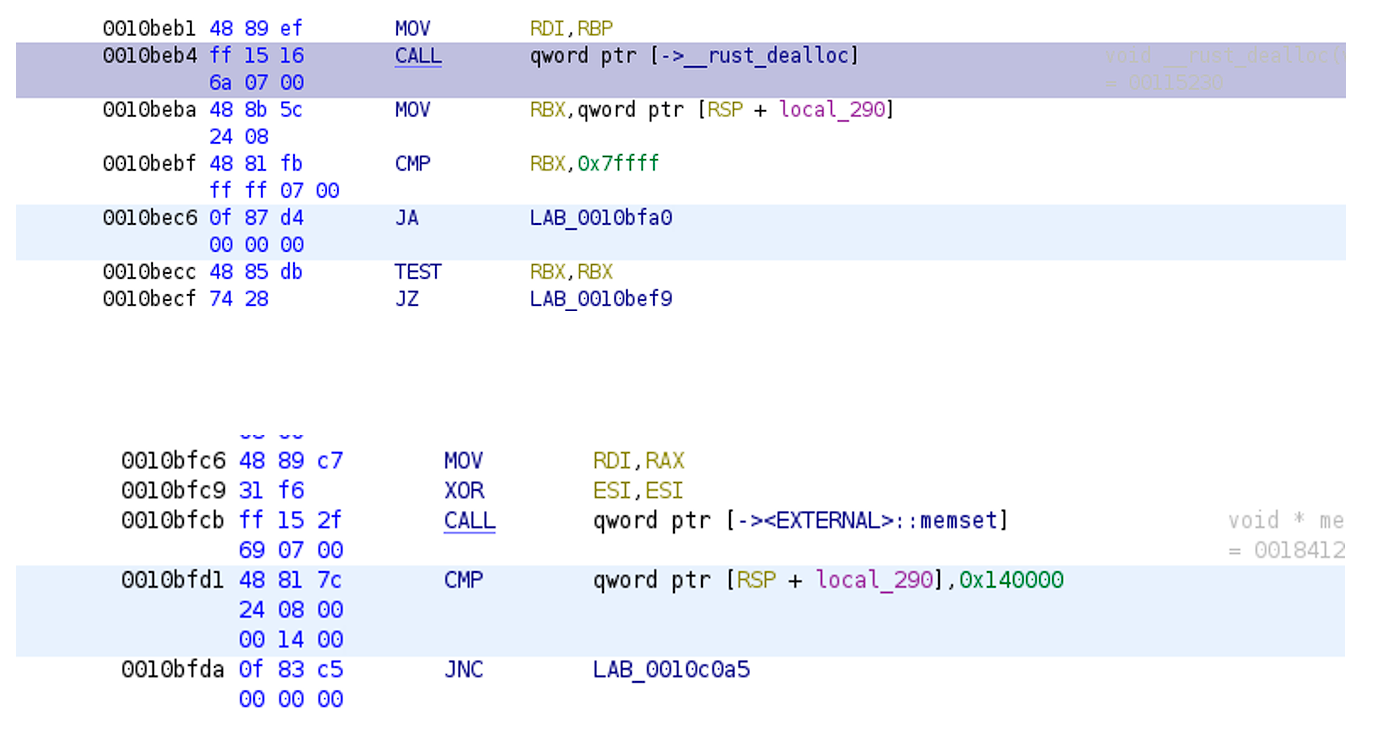
The encryptor doesn’t send requests to a server, because it doesn’t import winsock.dll or load dynamically (see Figure 3), but if it’s ran with the argument “-nd”, it collects information about network resources, because it’s using the MPR.dll (see Figure 4), which the malware often utilize for such actions. The recursive algorithm (see Figure 5) for collecting this information was implemented in the code. Then the information about shared directories will be saved in a queue for further encryption.
The encryptor is capable of showing all drives (including the hidden drives), if its run with tje argument “-lhd”. It takes the drives and assigns them a letter (see Figure 6). Then the information about the files on any hidden drive will be saved in a queue for further encryption. (See Figure 7)
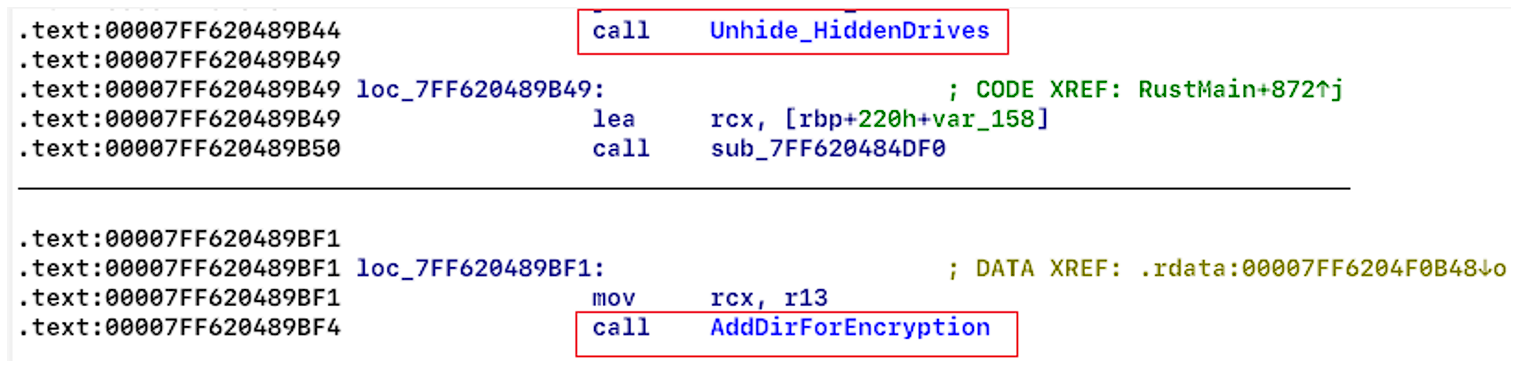
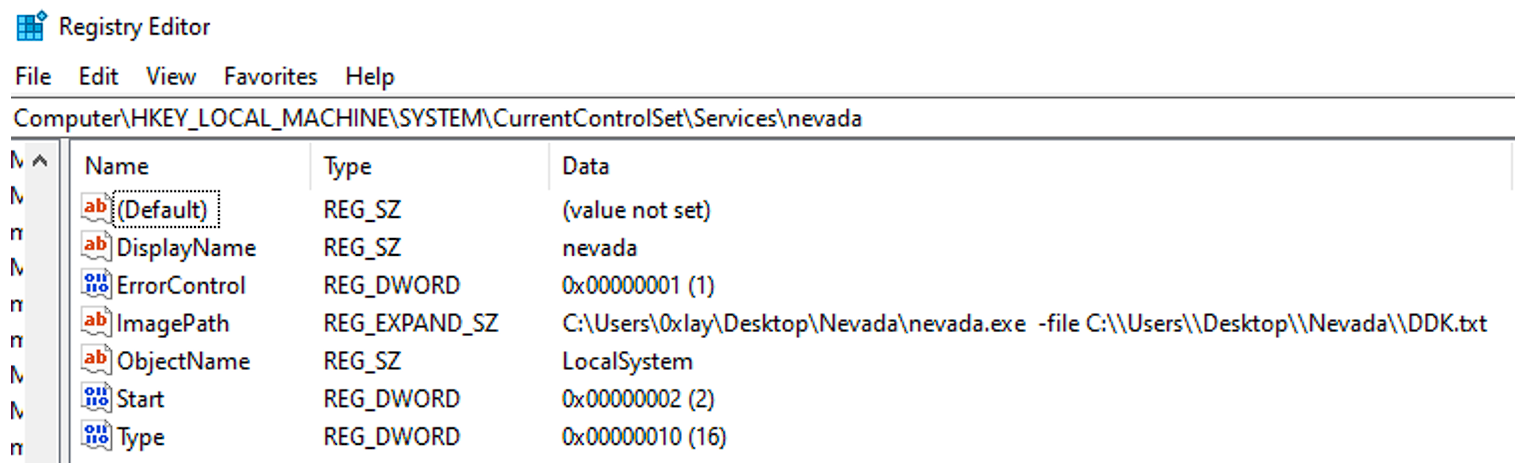
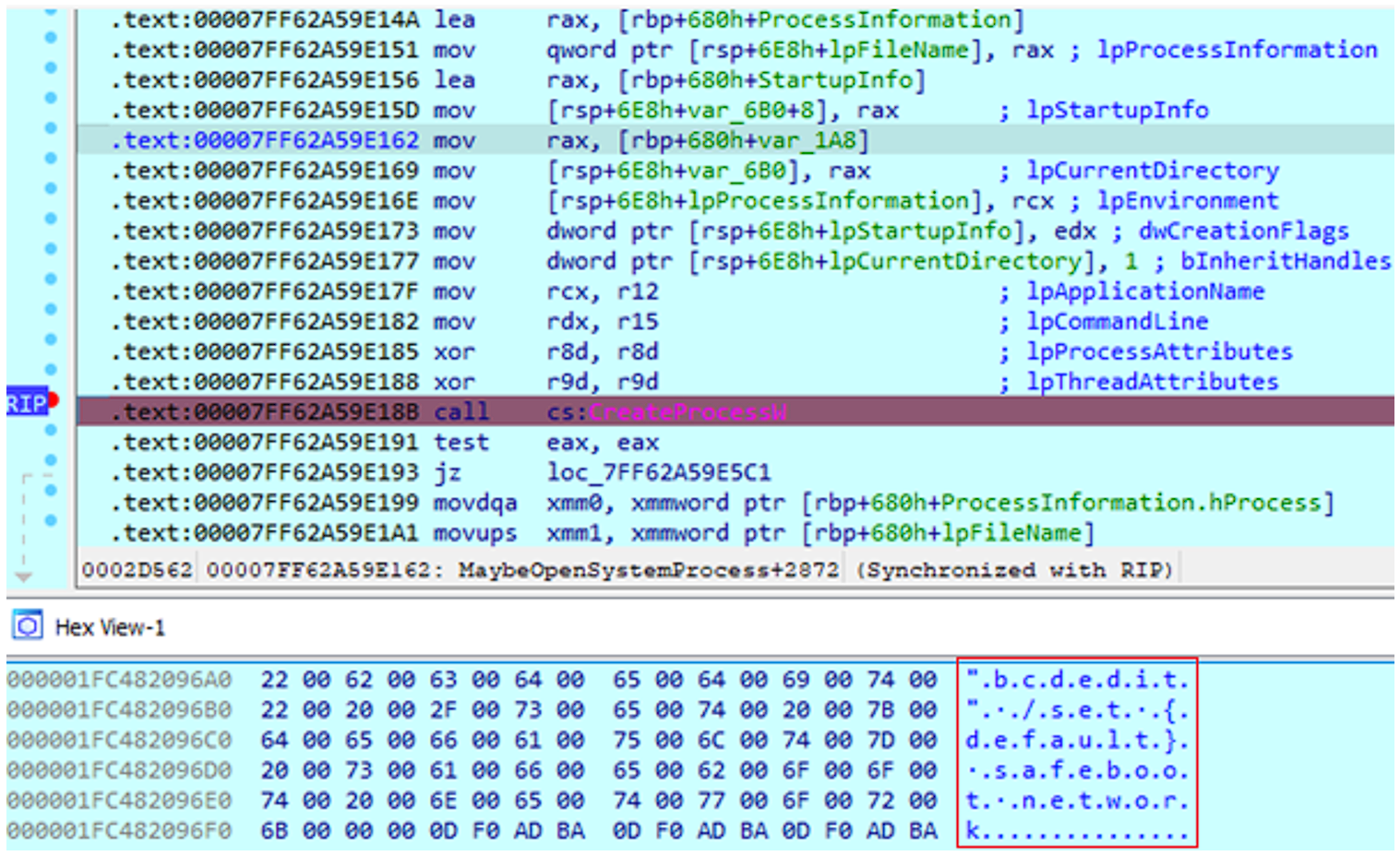
The encryptor can be installed as a service (see Figure 8) when run with the argument “-sm”. After that the computer will be rebooted, and then Windows will start in the safe mode with a network connection (see Figure 9).
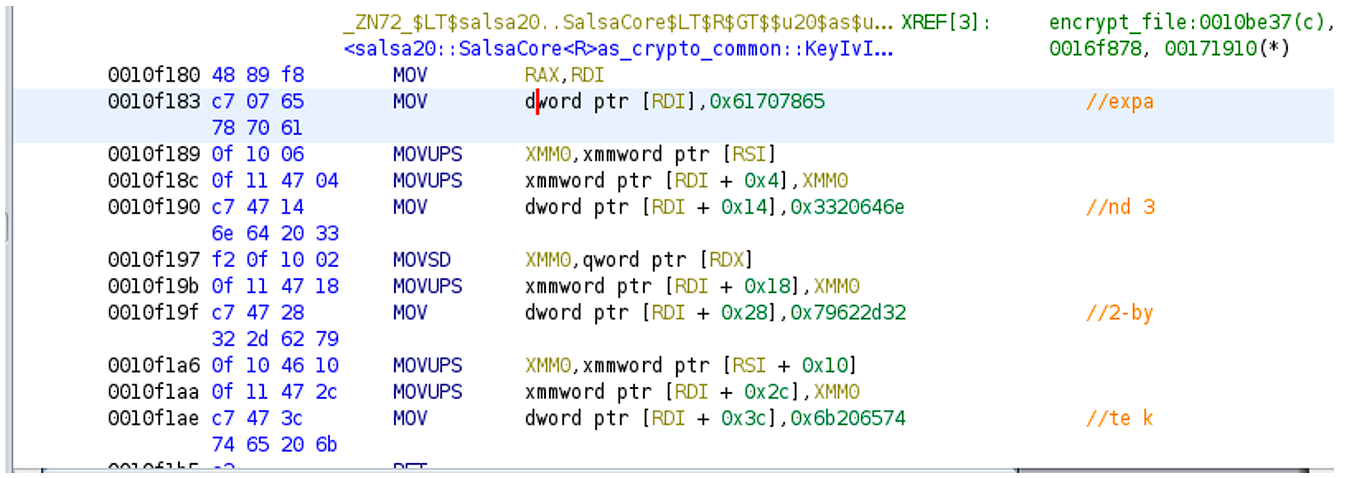
The encryptor is using Salsa20 encryption algorithm (see Figure 10, 11). Resecurity specialists have encrypted two identical files and noticed that the file was encrypted in parts (or “stripes” – as the actors call it at Nevada Ransomware (see Figure 12)). The original and encrypted file has the size of 56,983,552 bytes. The band size is 524,288 bytes, which is 512 KB. Files smaller than 512KB are fully encrypting.
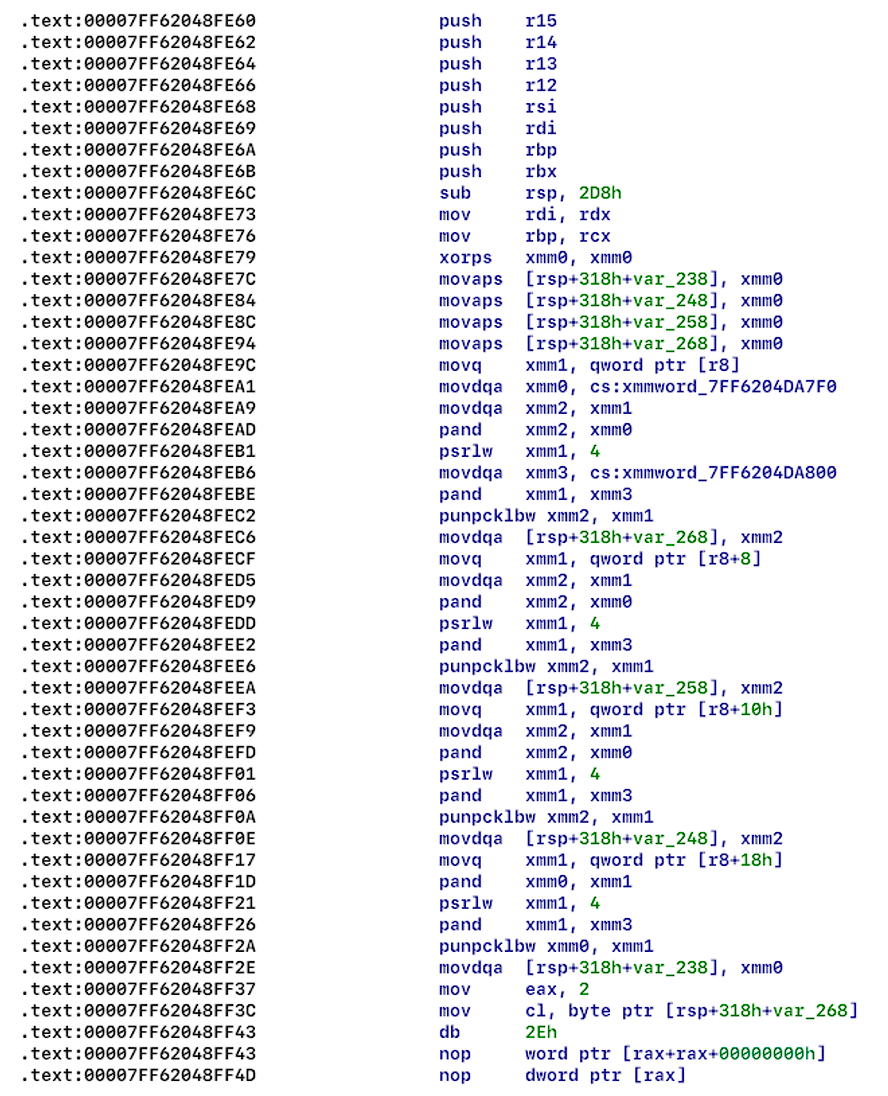
When the encryptor uses the ‘-dir’ argument, it encrypts directories (see Figure 13), but ignores system folders (see Figure 14), and some file extensions (see Figure 15.1 and 15.2).
| System folders: | Extensions: |
| Windows | exe |
| Program Files | ini |
| Program Files (x86) | dll |
| AppData | url |
| Programdata | lnk |
| System volume information | scr |
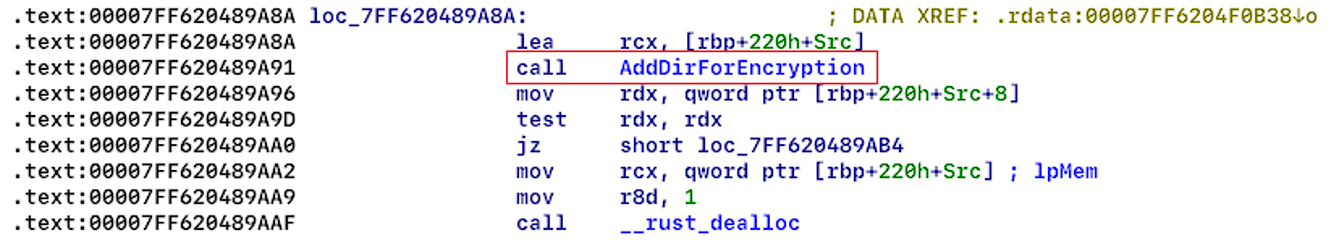
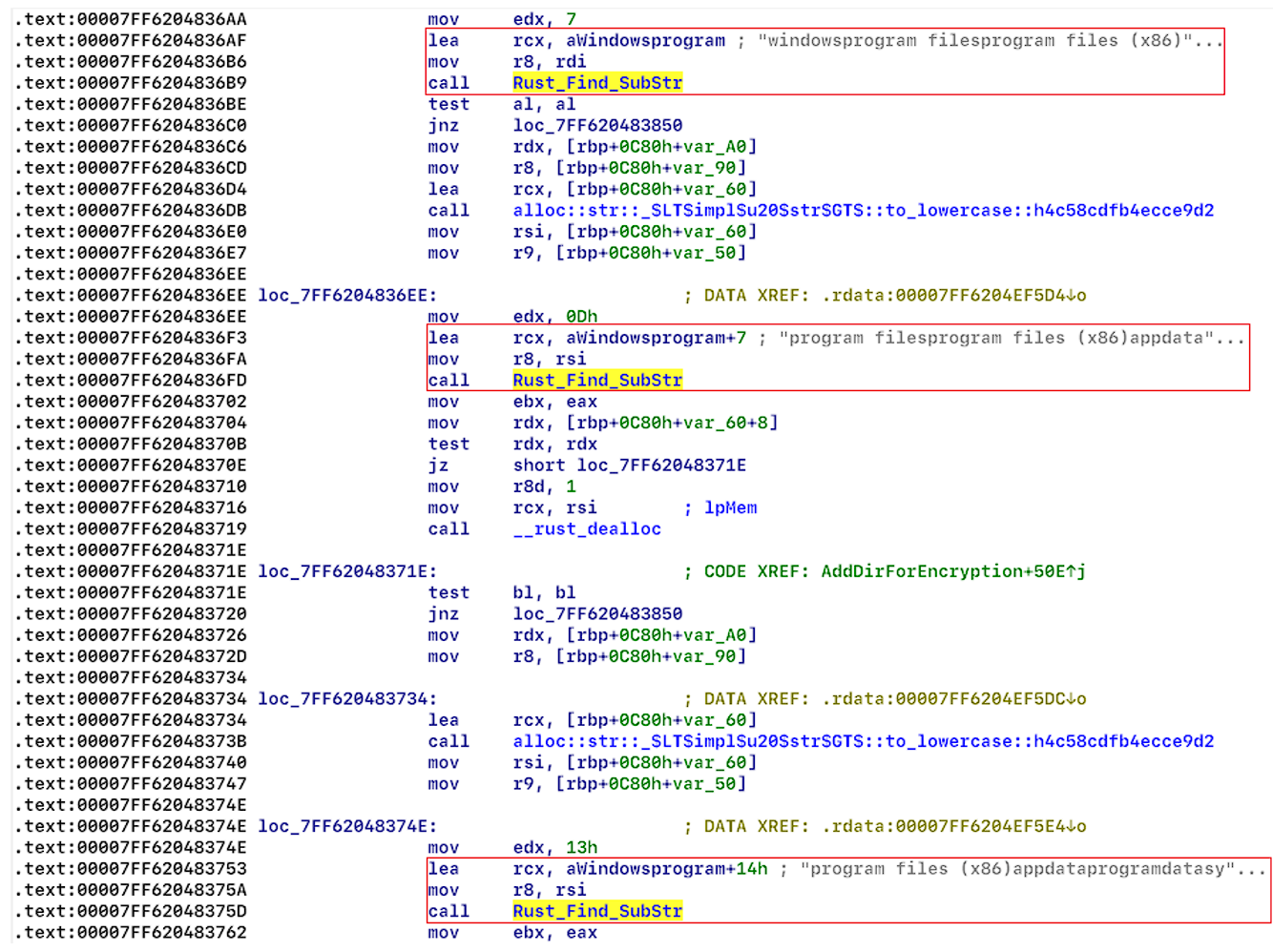
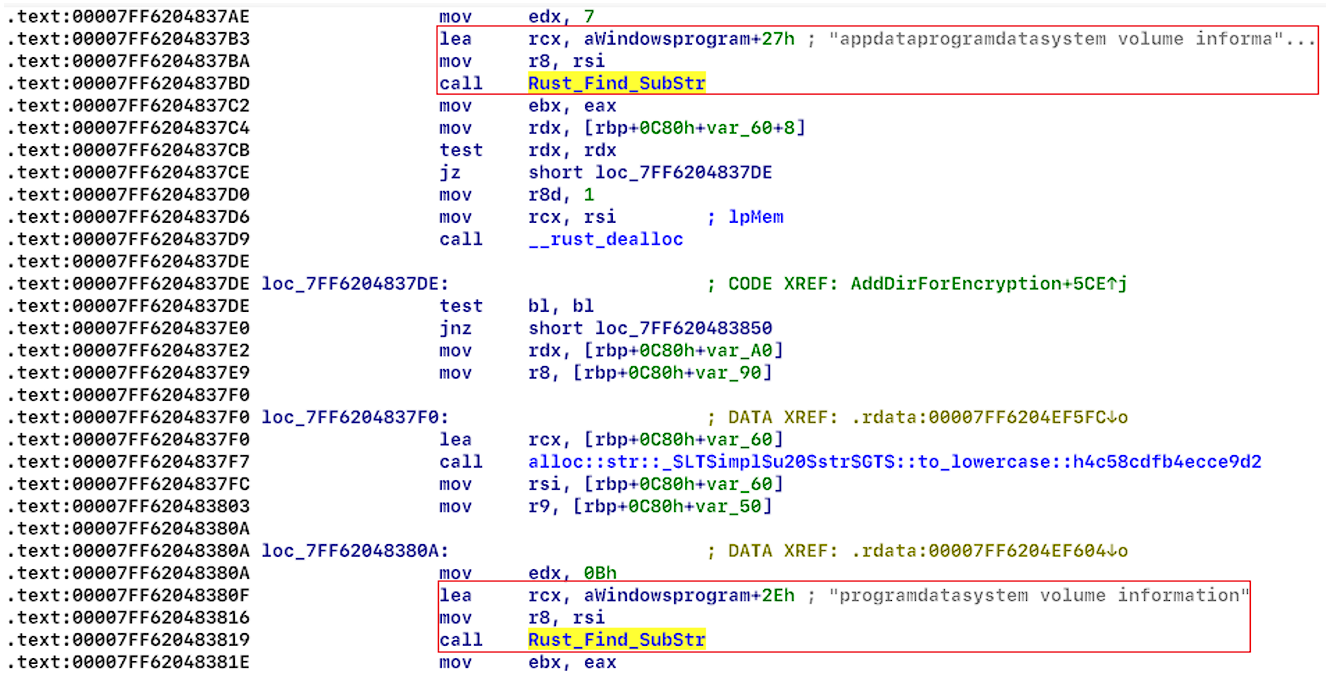
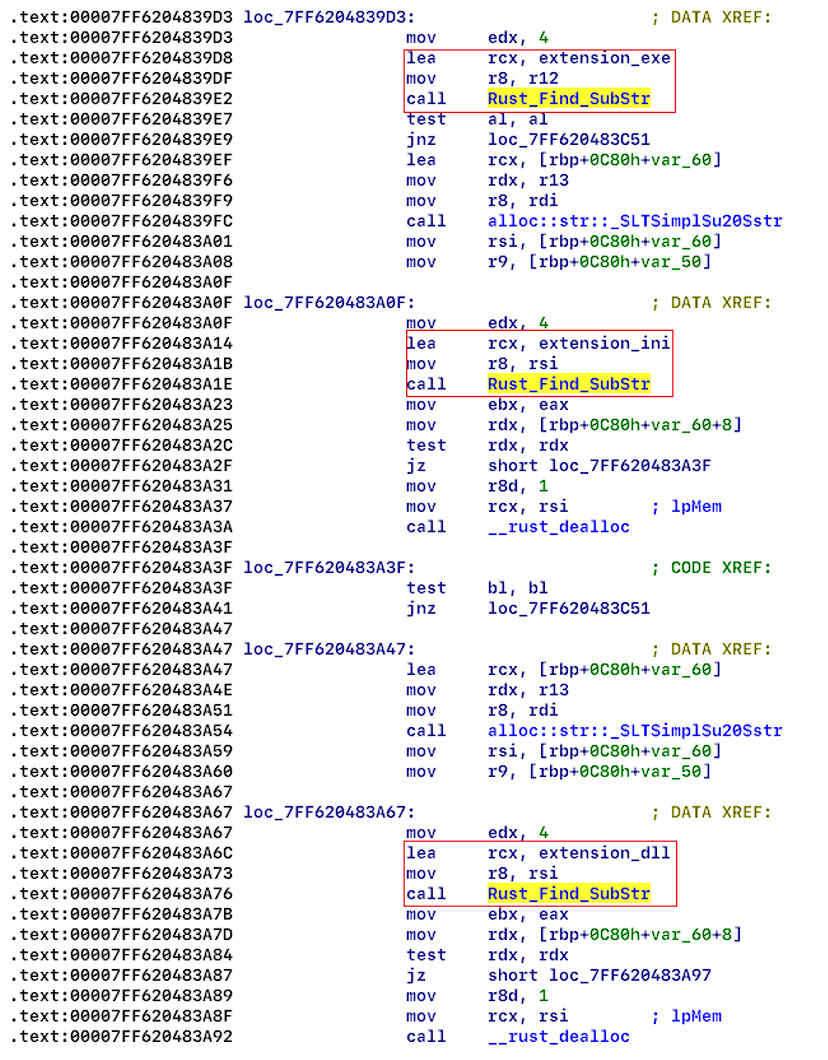
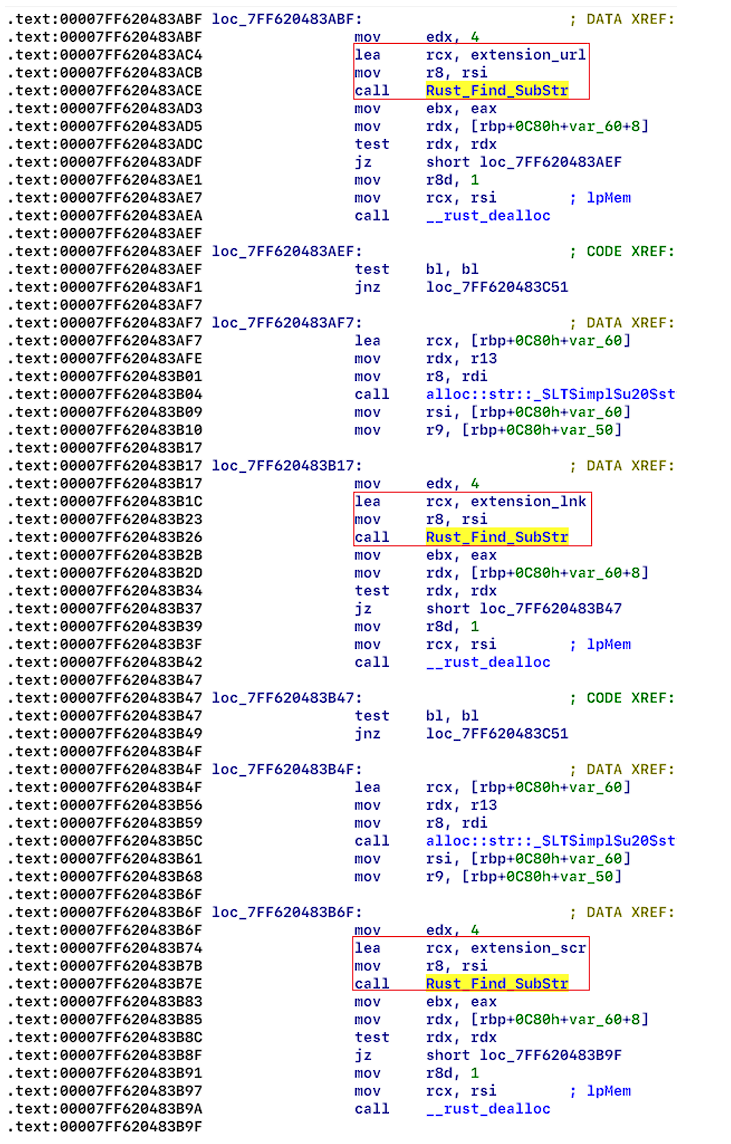
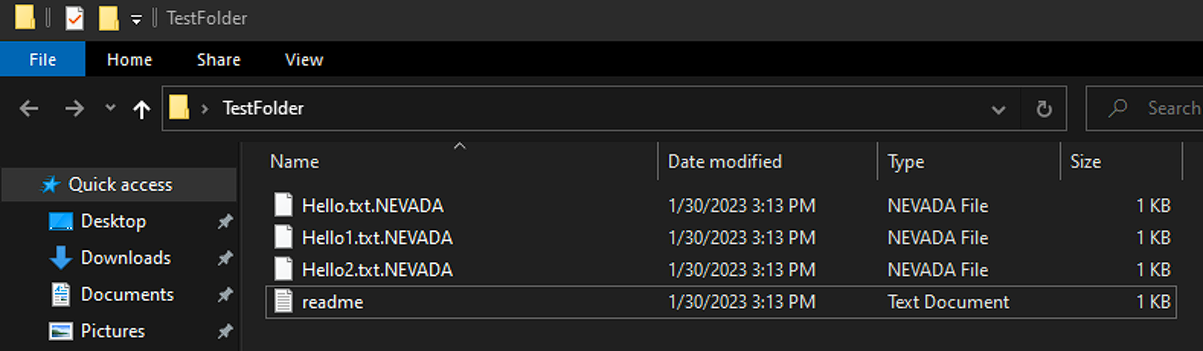
Each encrypted folder contains a new file named “readme” (see Figure 16), and the extension of the encrypted files have the extension “.NEVADA” (see figure 17).
- Nevada Ransomware (Linux Version)
The locker is written in Rust and can be executed with several flags described below. Resecurity has recovered the following details with exact functions of each flag:
| -help | help |
| -daemon | creation and launch of a service nevada |
| -file | encrypt particular file |
| -dir | encrypt particular folder |
| -esxi | disable all virtual machines |
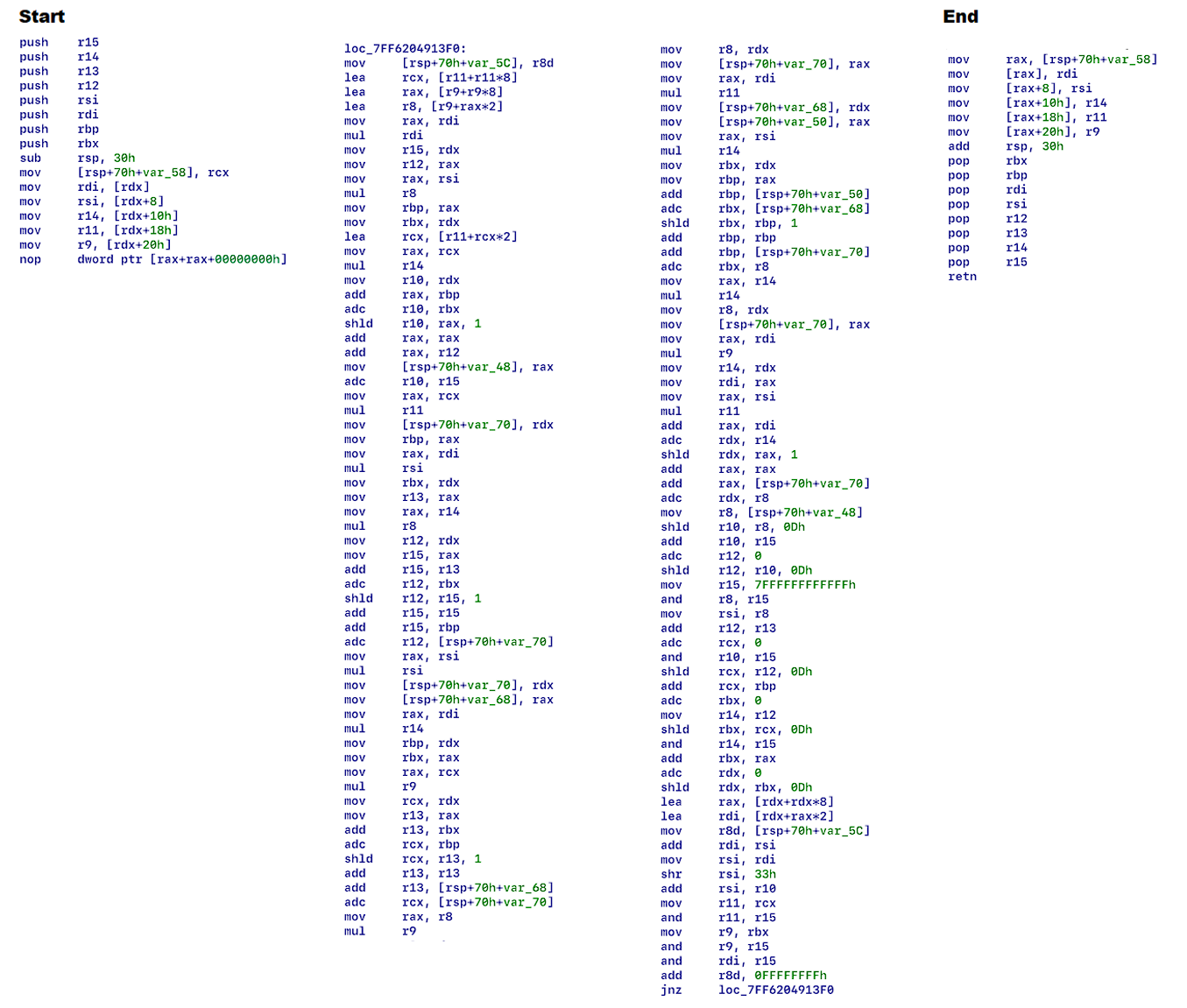
Similar to the Windows version, the Linux version is using Salsa20 with a constant variable “expand 32-byte k” – notably, the same approach was used in famous Petya Ransomware. Petya has been using the Salsa20 stream cipher to encrypt the Master File Table and make the compromised disk inaccessible.
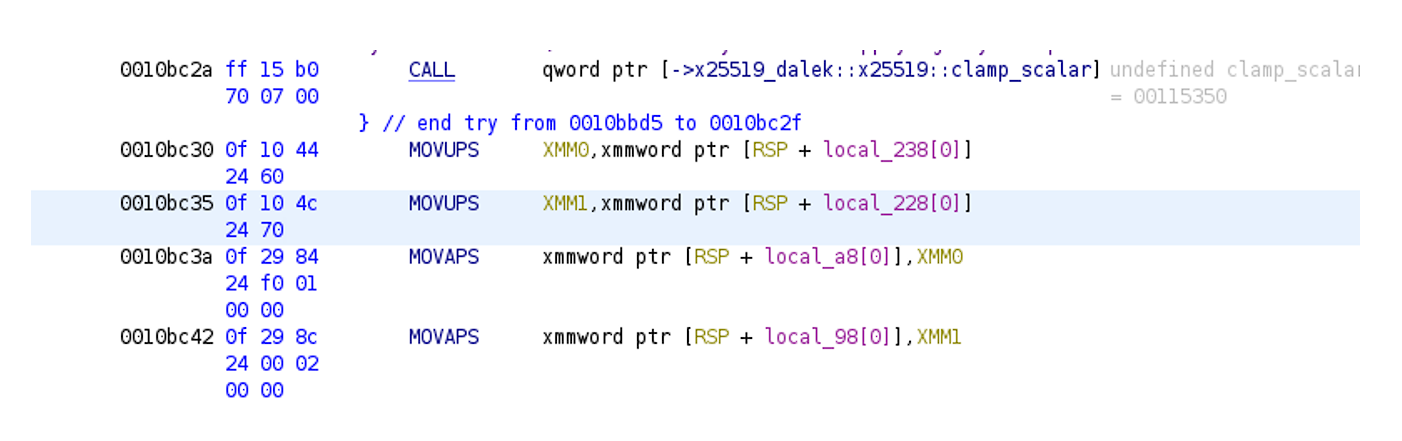
An encryption key exchange is based on x25519_dalek library - A pure-Rust implementation of x25519 elliptic curve Diffie-Hellman key exchange, with curve operations provided by curve25519-dalek (https://github.com/dalek-cryptography/x25519-dalek).
As observed in the Windows version, Nevada Ransomware is encrypting files ‘by stripes’ – which are positioned by operators behind the project as a significant advantage facilitating speed in combination with Sales20. That being said, for a successful decryption, it is required to know which area hasn’t been encrypted – which makes the process complicated. Files less than 524288 byte (512kb) – will be fully encrypted, which seems to be an exception.
Interestingly, for some reason, Nevada Ransomware (at least, for Linux) – wont encrypt files in the range of 524288 and 1310719 bytes. Those files will remain the same, but with only added extension (.NEVADA) and an additional 38 bytes on the end of the file. This small detail makes recovery process possible in practice with files having sizes between 524326 and 1310757 bytes. We also detected a locker with customized extensions provided to vetted
affiliates. These tactics are likely utilized to prevent attribution to Nevada Ransomware and thus allow affiliates to leverage it under their own brand.
If the file is less than 2048 Kbs – there will be only 1 block (stripe) encrypted. If more or equal – the blocks will be used one by one (512 Kbs after every 256 Kbs).
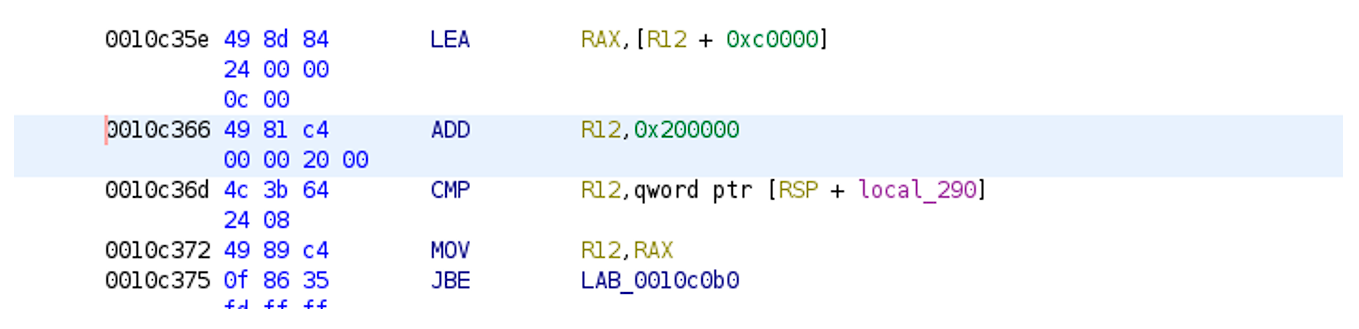
If after the last encrypted block there is less than 768 Kbs (512+256), it won’t be touched by the locker. In the end of the binary the key and signature “Nevada” will be added.
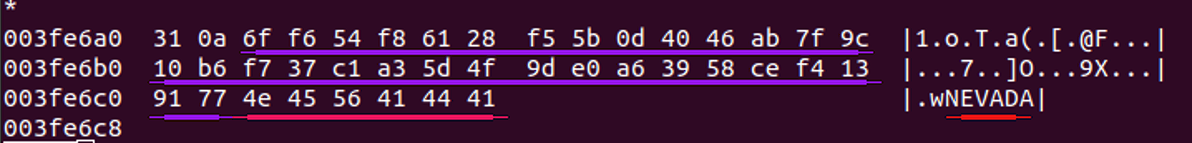
The Public Key is stored at the end of the file:
Possible Data Decryption
In order to recover the data encrypted by Nevada Ransomware, we need to know the private key “B” and public key “A”, which are added to the end of the file, nonce for Salsa20 and the size of the file and algorithm used for selecting ‘stripes’ to encrypt (which may potentially be measured or guessed). Below is a prototype of the decryption process in Rust with Salsa20 and x25519_dalek libraries. The example is purposely simplified for research purposes:
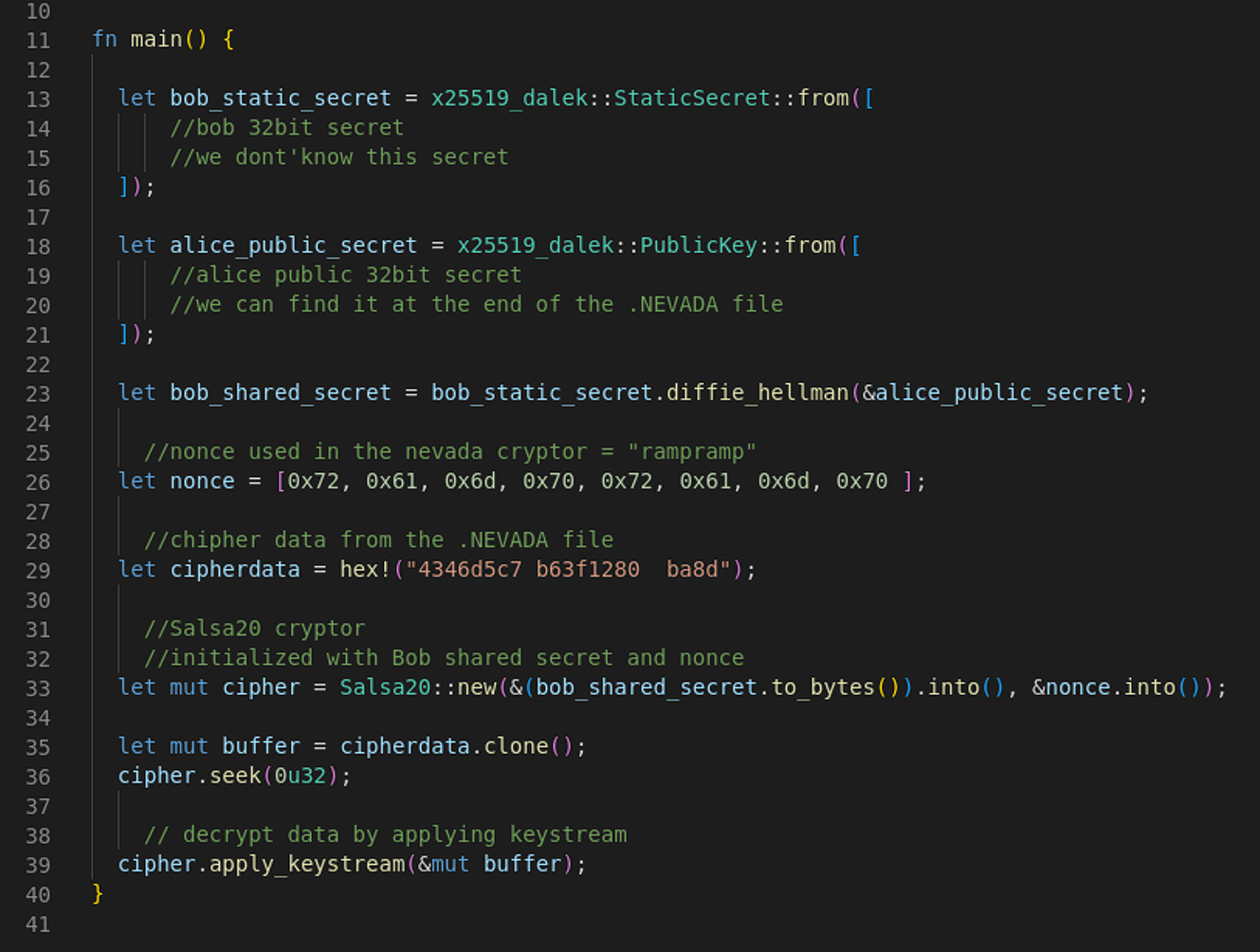
However, similar to Petya Ransomware it also contained a series of implementation bugs that rendered the encryption algorithm flawed, making it possible to recover data without paying the ransom.
Encryption Note
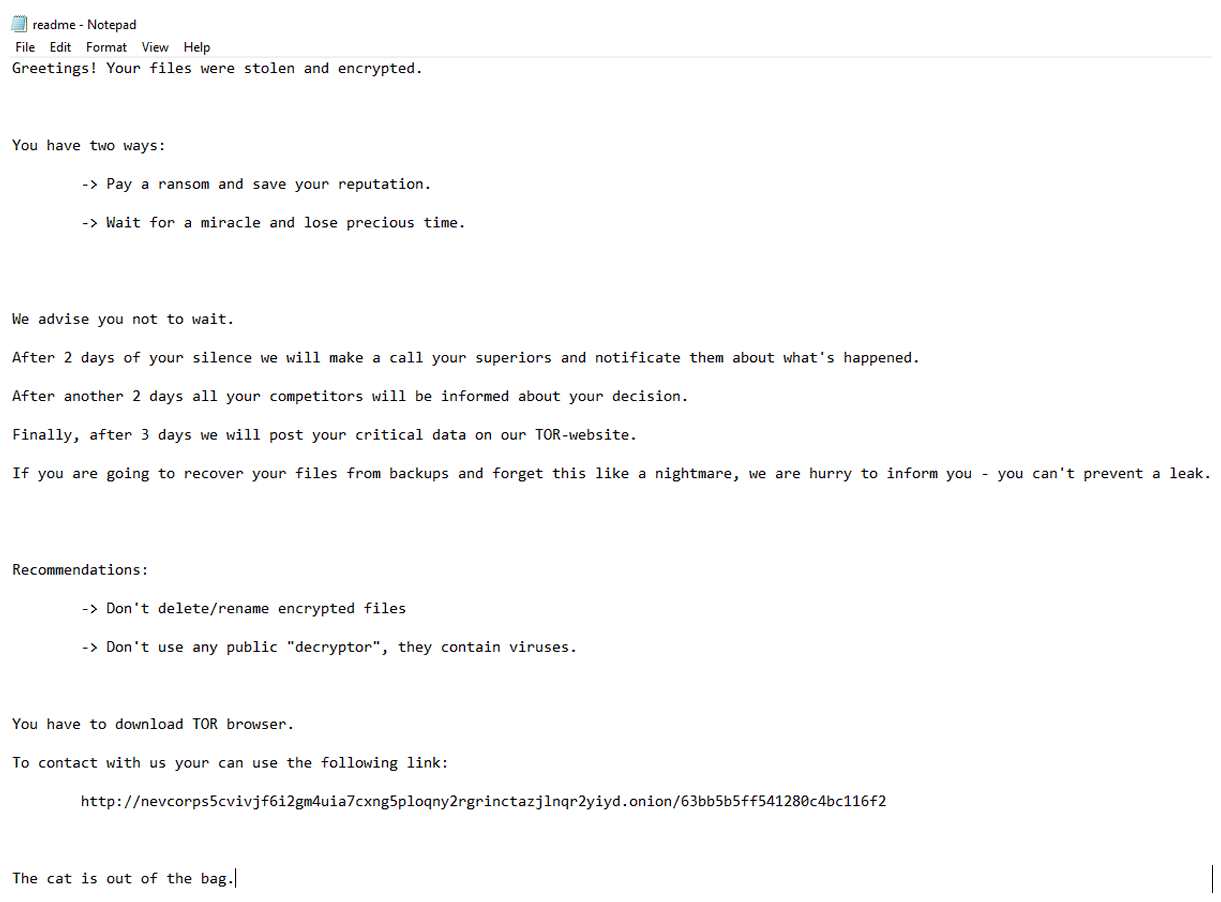
After successful encryption Nevada Ransomware will drop ‘readme.txt’ in each folder with files on the victim's machine:
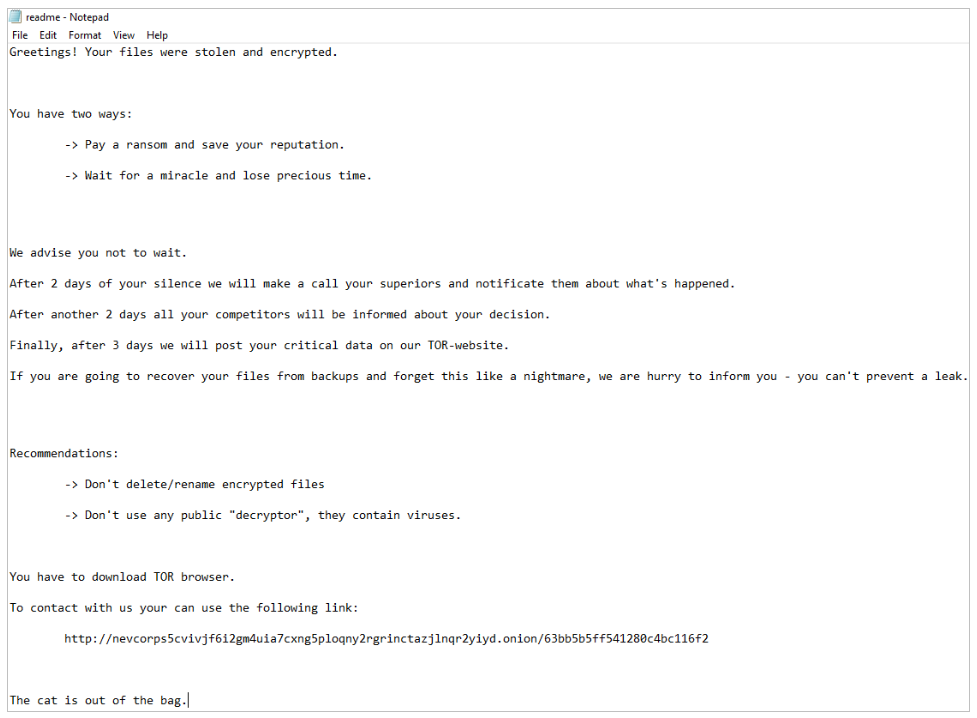
Interestingly, identified were several exceptions when analyzing the encryption process. The folders having at least 1 sub-folder named “nevada” won’t be encrypted:
- /some/dir/nevada/folder/file.dat – won’t be encrypted
- /some/dir/folder/subfolder/file.dat – will be encrypted
Files with possible extensions ".exe", ".ini", ".src", ".lnk" located in folders won’t be encrypted by default – to encrypt them the operator needs to specify a flag "-file" (when executing Nevada from a console).
Indicators of Compromise (IOCs)
URL (TOR):
nevcorps5cvivjf6i2gm4uia7cxng5ploqny2rgrinctazjlnqr2yiyd[.]onion/{victim ID}
MD5:
99549bcea63af5f81b01decf427519af (Windows)
MD5:
fb5dcf0b880b57b10a2093f164f2ed27 (Windows)
MD5:
709ba88e758454f097959c3e62997000 (Windows)
MD5:
f1f569c6e4f961007f7411fca131bbe0 (Linux)
MD5:
1396ab93e9104faaf138ac64211471ba (Linux)
Significance
Nevada Ransomware is a new and actively progressing Ransomware-as-a-Service (RaaS) with an established affiliate network. The actors are inviting both Russian- and English-speaking affiliates to collaborate with a big number of Initial Access Brokers (IABs) in Dark Web. Notably, the group behind the Nevada Ransomware is also buying compromised access by themselves, the group has a dedicated team for post-exploitation, and for conducting network intrusions into the targets of interest. Resecurity is expecting a spike in active growth from Nevada Ransomware in 2023 - both in number of victims and affiliates collaborating with the group, this is due to the attractive conditions (85/15, 90/10). The project is well presented on the RAMP underground forum and has already attracted interest from credible cybercriminals who may be joining them after the closure of other major ransomware networks.

