Phishing-Kit Campaigns Target The Financial Sector in the Kingdom of Saudi Arabia
Cybercrime Intelligence


Resecurity, Inc (USA), cybersecurity company providing managed threat detection and response, has been informed about the victim (-s) of financial fraud based in Saudi Arabia. Based on our assessment, the threat actors are using a WEB-site “maktabkhadimat.com” impersonating legitimate WEB-site of Saudi Manpower Solutions Company (SMASCO).
URL: https://maktabkhadimat.com/

Legitimate WEB-site: https://www.smasco.com/
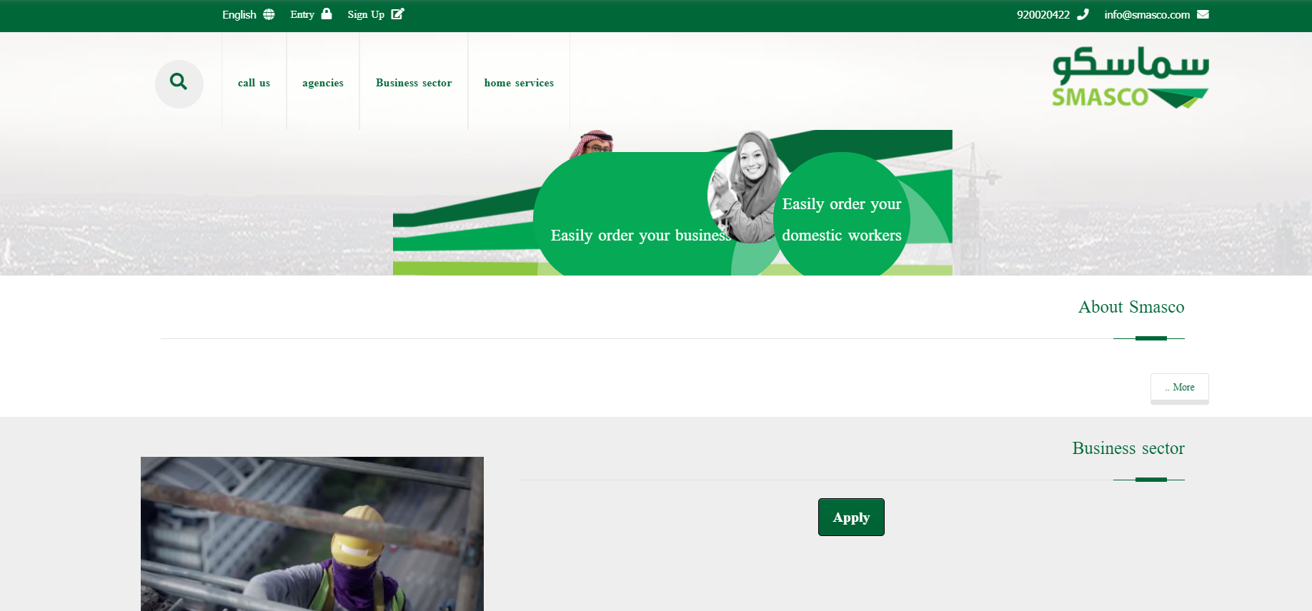
The phishing WEB-site has ‘cloned’ design of SMASCO, and copies of some of the key pages without any additional information.
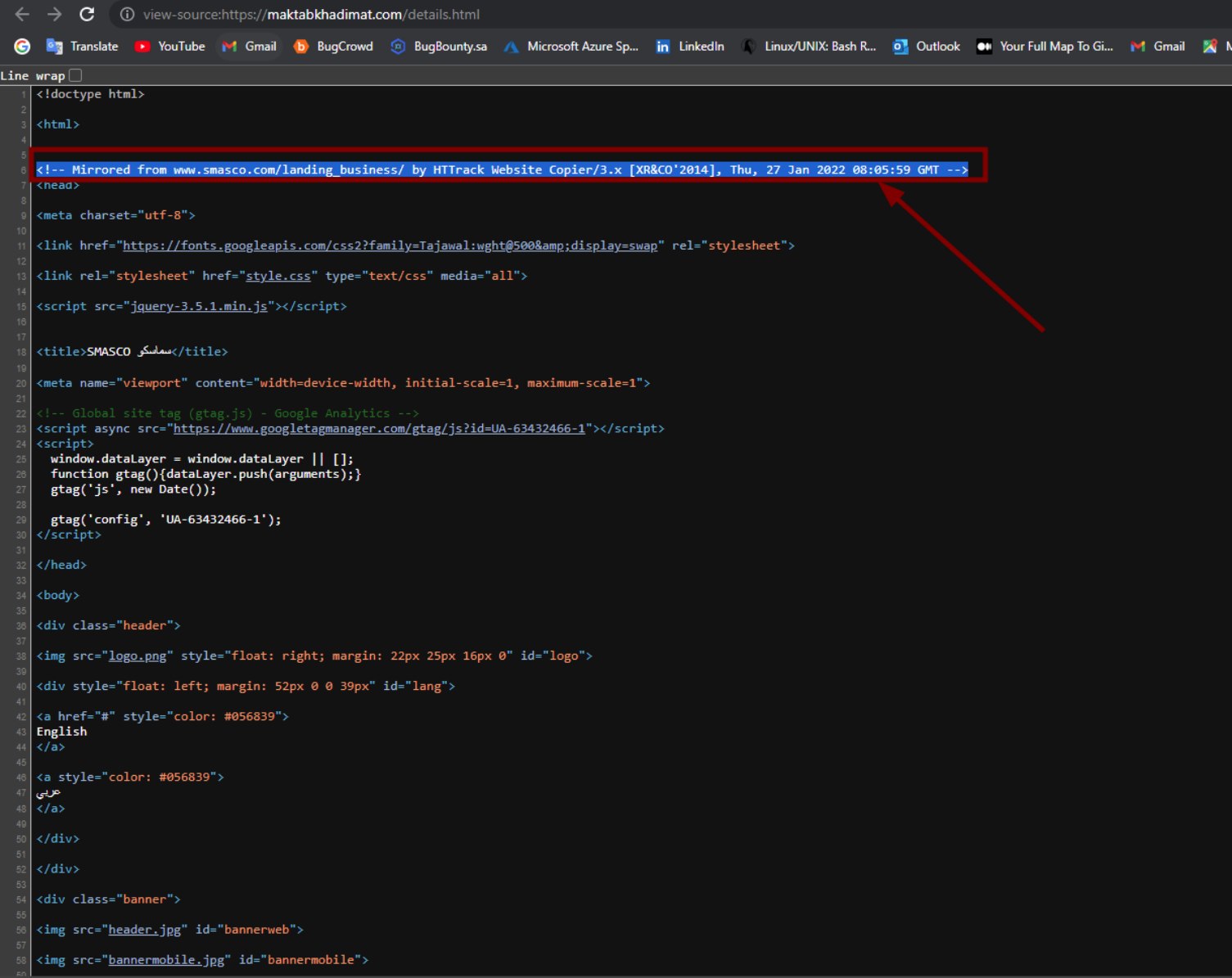
Based on the analysis of the HTML pages, the threat actor has downloaded legitimate WEBsite of SMASCO around January 27, 2022 08:05:59 GMT using Htrack Website Copier:
In the result of extensive digital forensics, there were identified multiple malicious phishing kits and other tools hosted at “maktabkhadimat.com” configured to intercept online banking credentials of various financial institutions in Saudi Arabia and credit card data.
The identified phishing-kits have been deployed by the following URL: https://maktabkhadimat.com/bank/
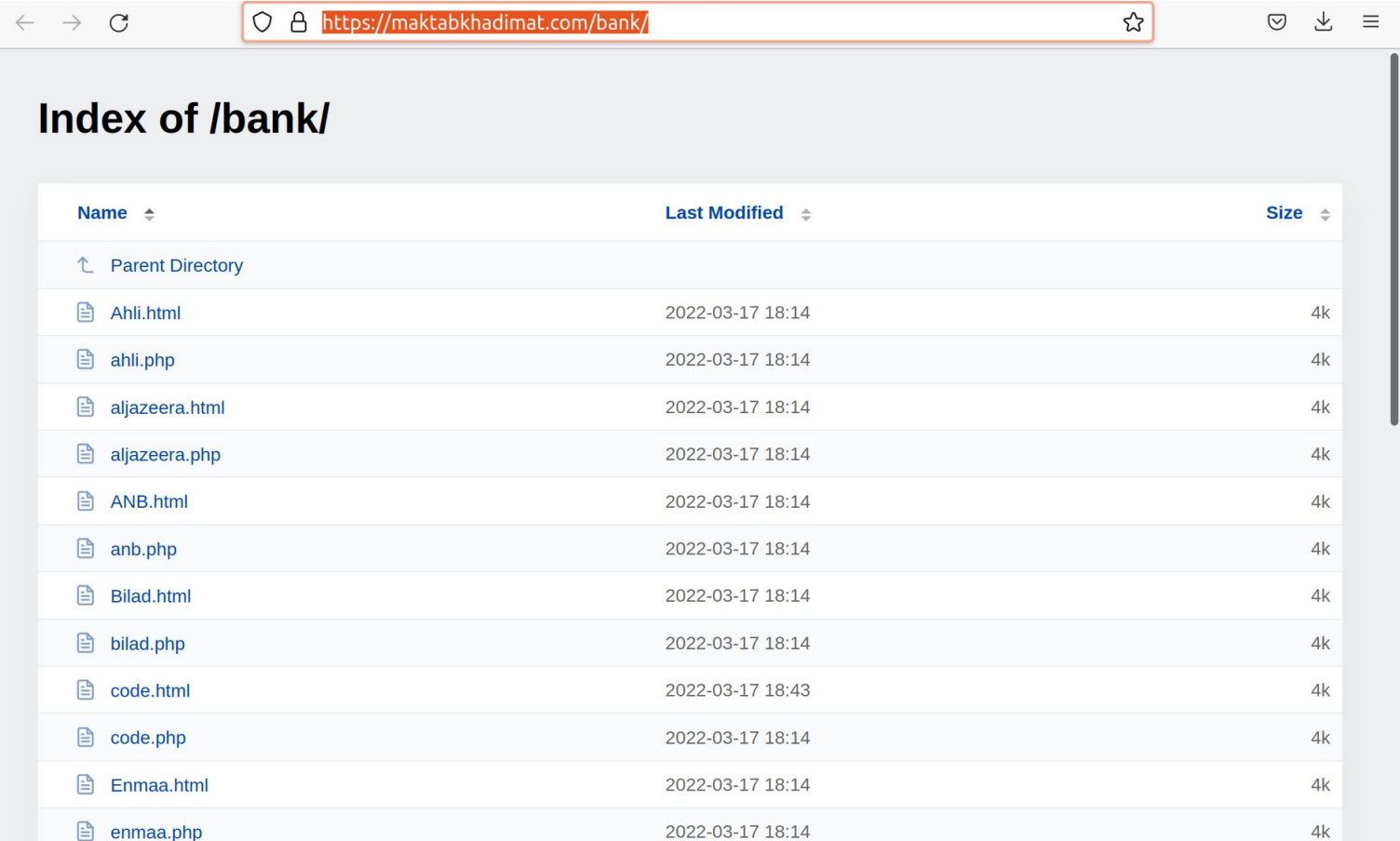
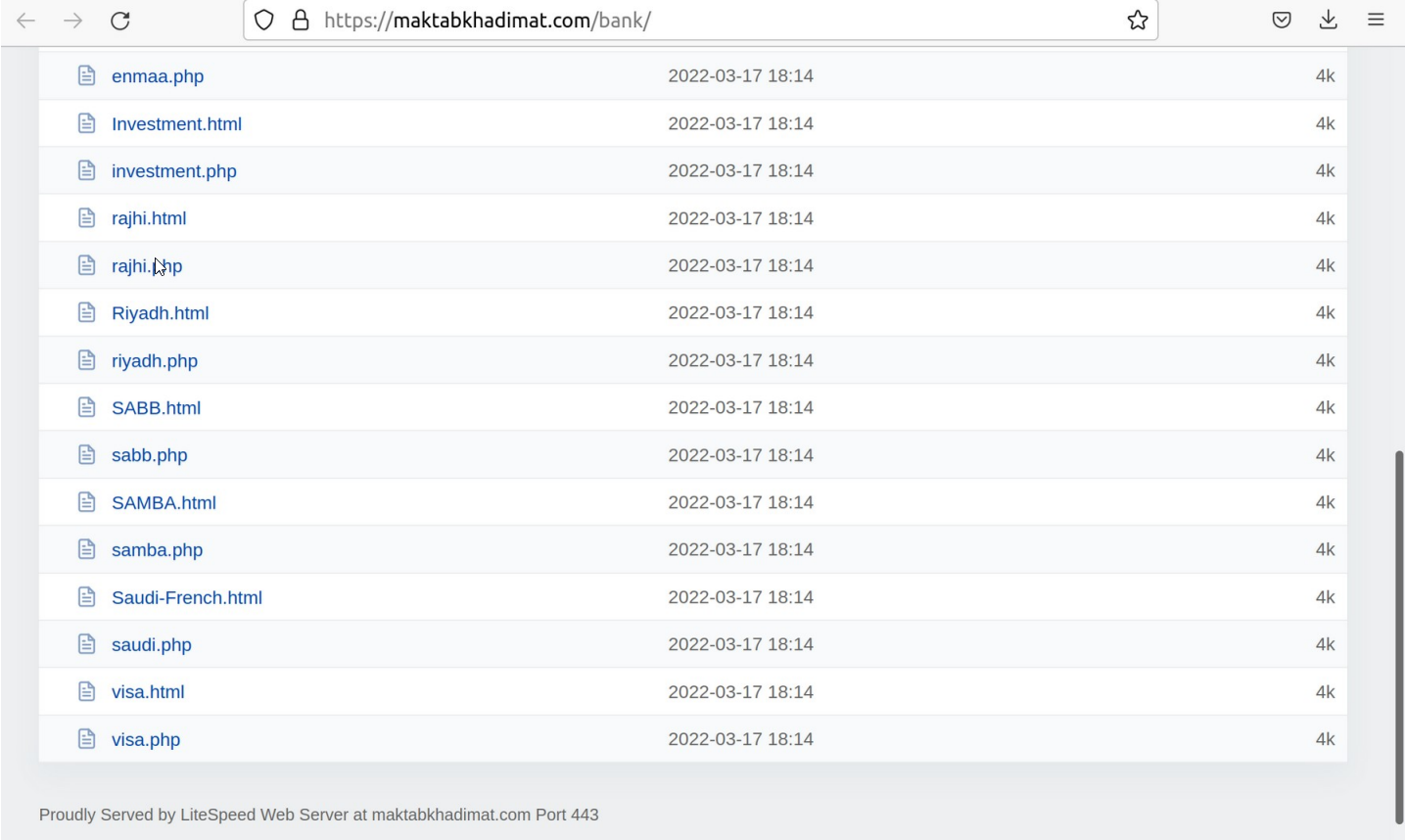
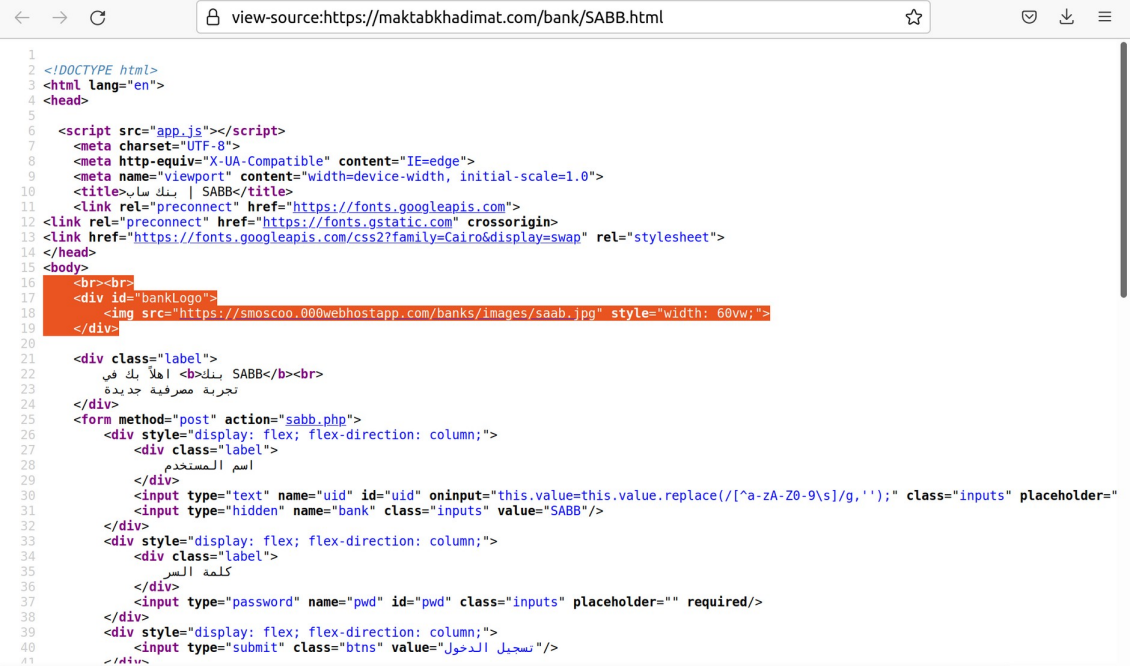
Each of the deployed scenarios (.php) and associated HTML content is related to a separate phishing-kit targeting particular financial institution in Saudi Arabia.
NCB Bank
https://maktabkhadimat.com/bank/Ahli.html

Bank Aljazira
https://maktabkhadimat.com/bank/aljazeera.html

Bank ANB
https://maktabkhadimat.com/bank/ANB.html

Bank Albilad
https://maktabkhadimat.com/bank/Bilad.html
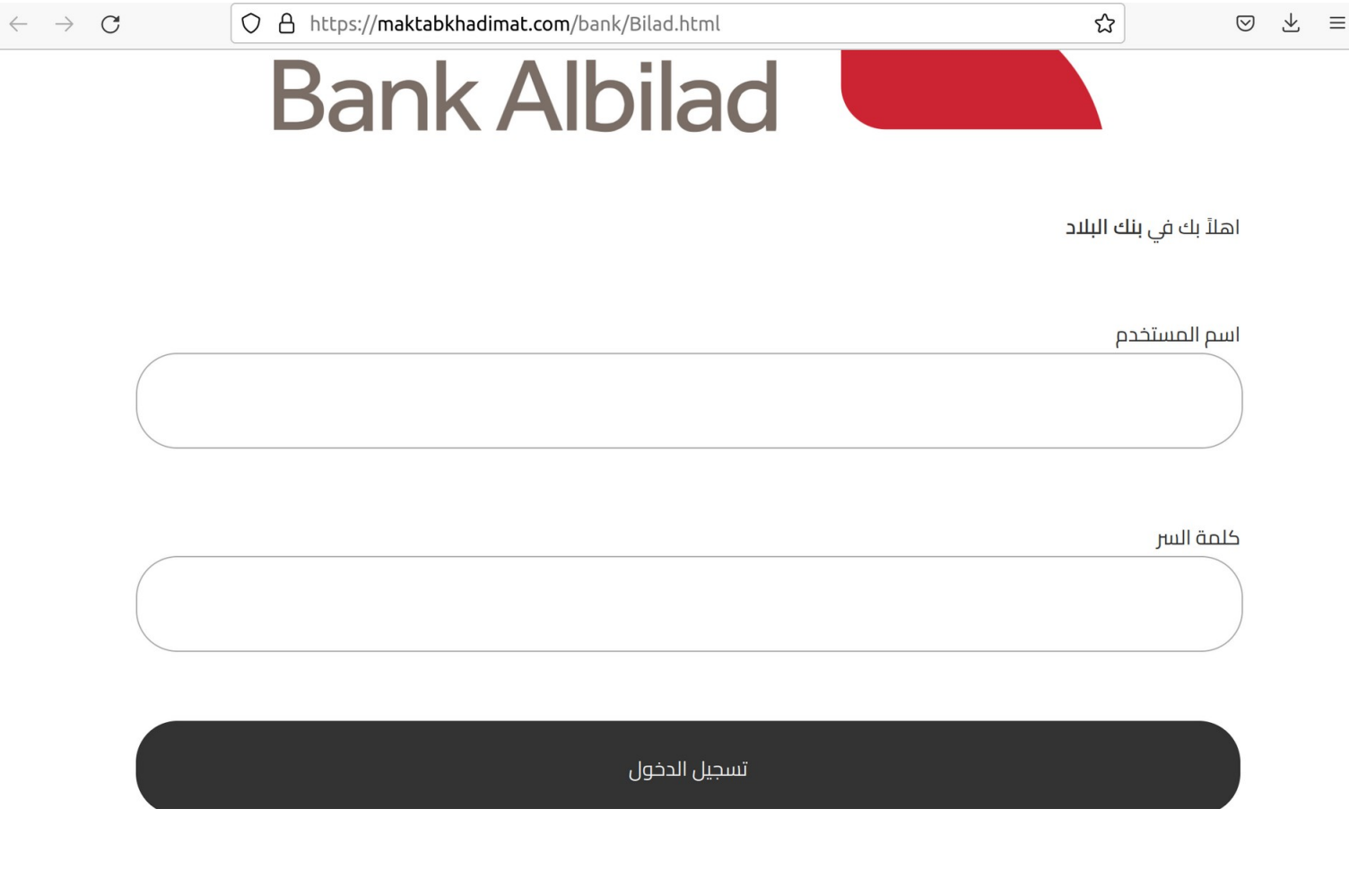
Alinma Bank
https://maktabkhadimat.com/bank/Enmaa.html

The Saudi Investment Bank
https://maktabkhadimat.com/bank/Investment.html

Alrajhi Bank
https://maktabkhadimat.com/bank/rajhi.html

Riyadh Bank
https://maktabkhadimat.com/bank/Riyadh.html

SABB
https://maktabkhadimat.com/bank/SABB.html

SAMBA
https://maktabkhadimat.com/bank/SAMBA.html

Banque Saudi Fransi
https://maktabkhadimat.com/bank/Saudi-French.html

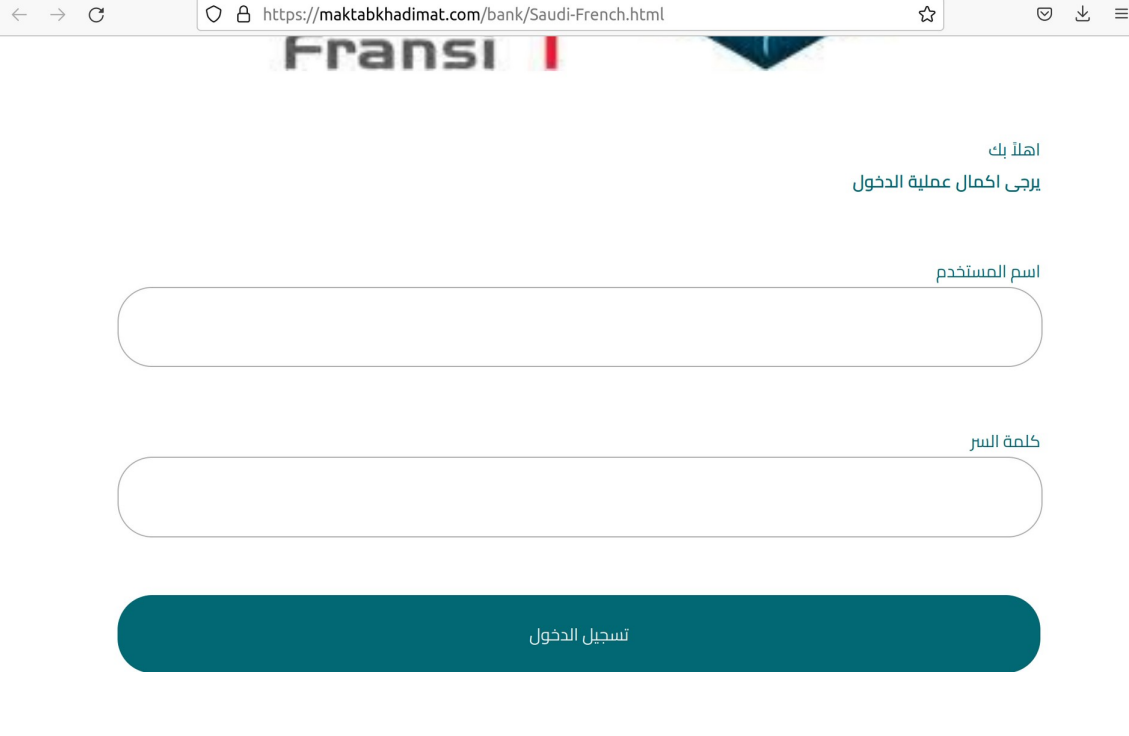
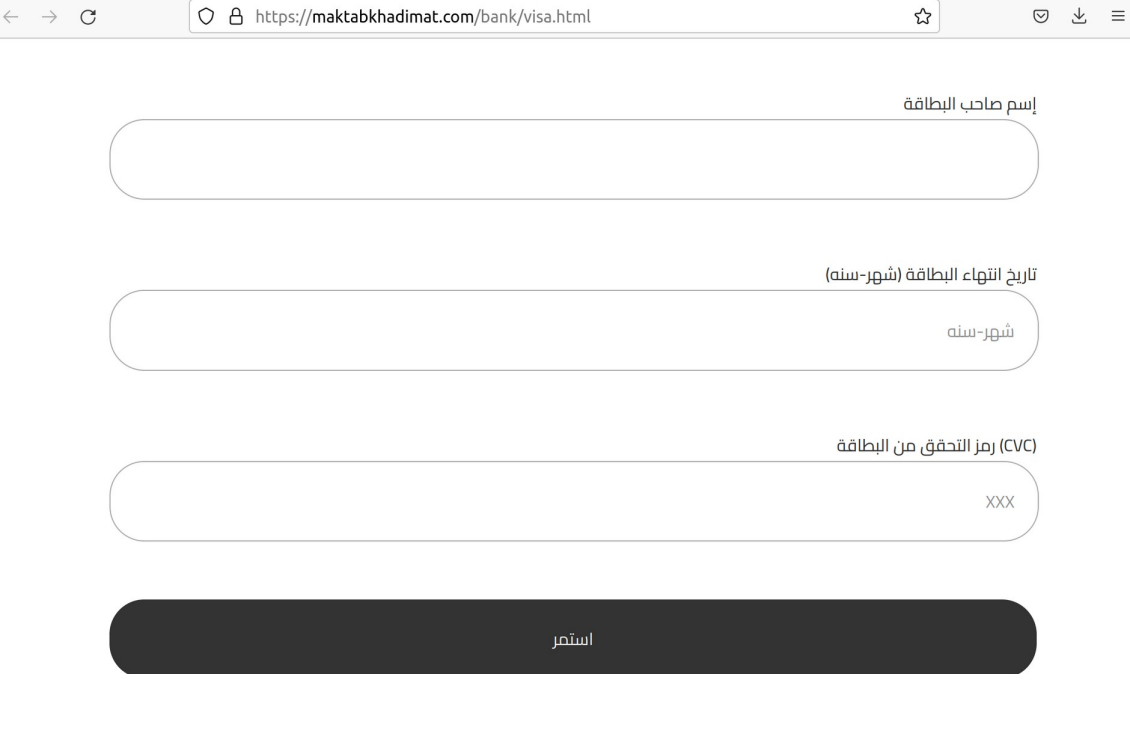
Visa, Inc.
https://maktabkhadimat.com/bank/visa.html

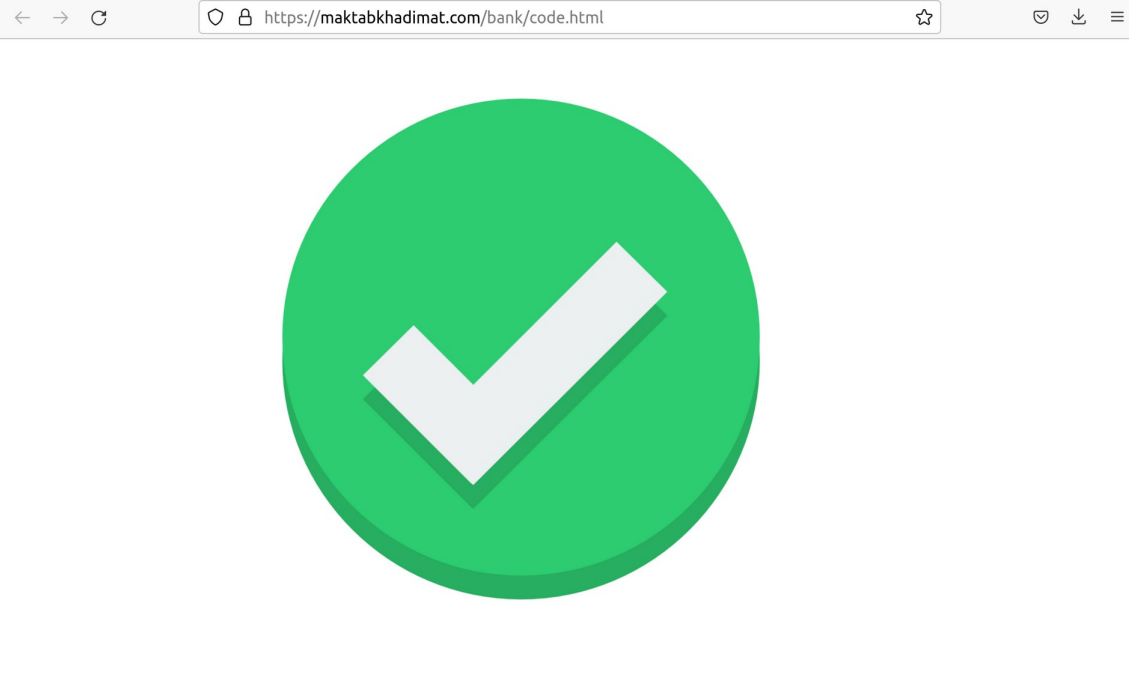
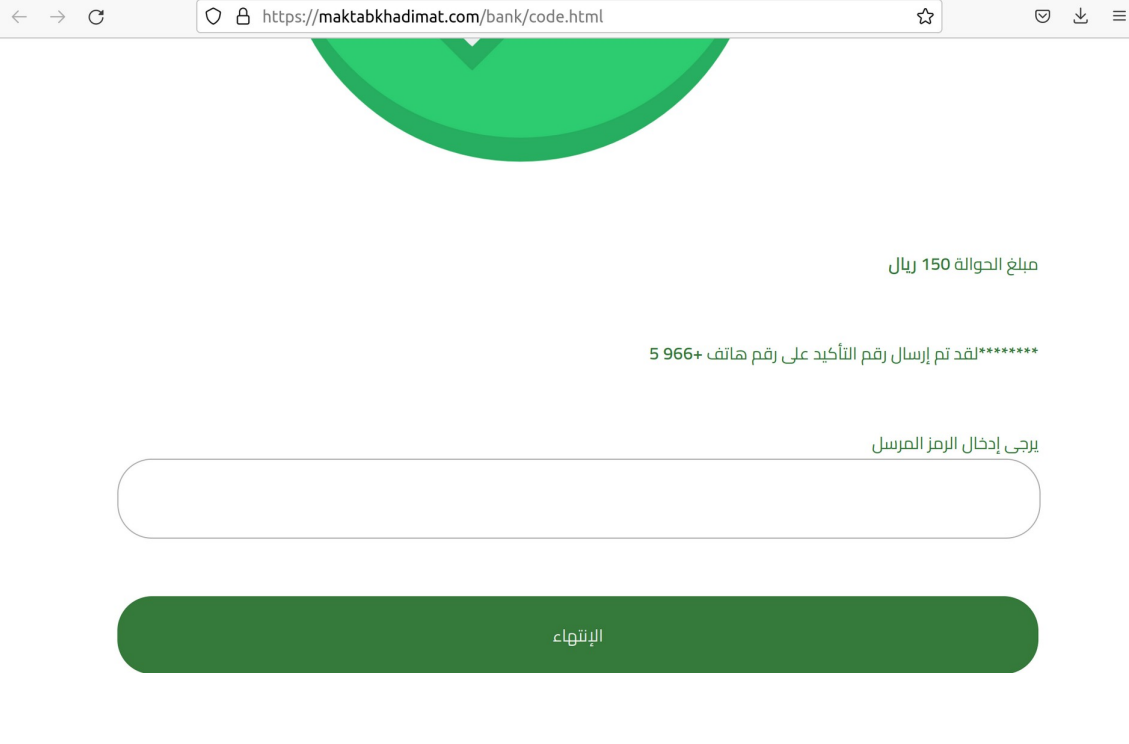
In addition to that, there were identified an interactive scenario demonstrating the user fake notification about successful authorization with further redirect.
https://maktabkhadimat.com/bank/code.html
Notably, the observed phishing-kits have a reference to content hosted on another resource:
There was identified a folder “banks” - https://smoscoo.000webhostapp.com/banks/
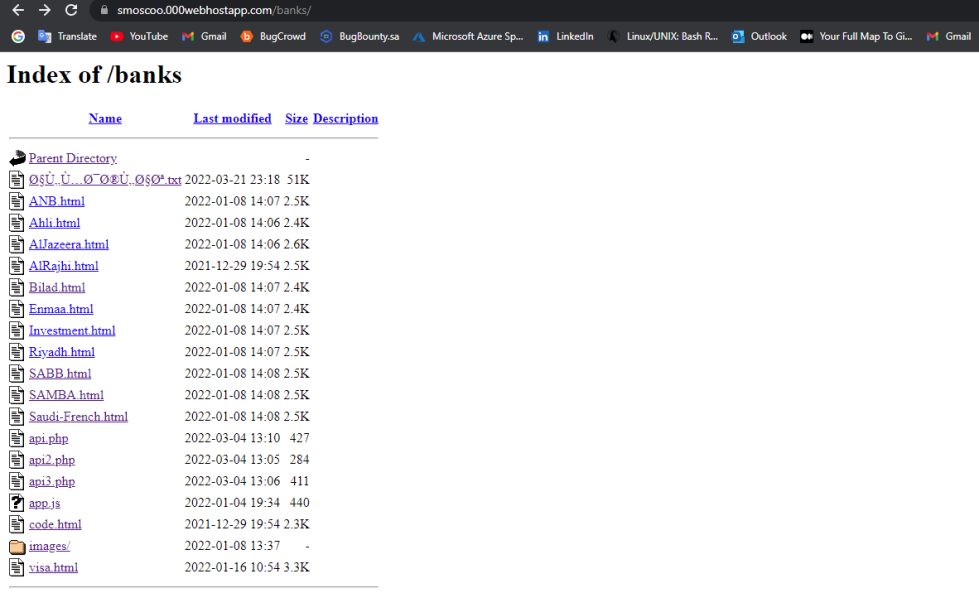
The folder contains phishing-kits along with HTML and graphical content related to major financial institutions in Saudi Arabia to impersonate online-banking authorization (form).
Based on further investigation there was identified a folder and a file containing intercepted online-banking customers credentials along with test data used to debug phishing-kit by the threat actor. The full log of the text file is attached in Appendix A to this intelligence report.
https://smoscoo.000webhostapp.com/banks/%D8%A7%D9%84%D9%85%D8%AF%D8%AE%D9%84%D8%A7%D8%AA.txt
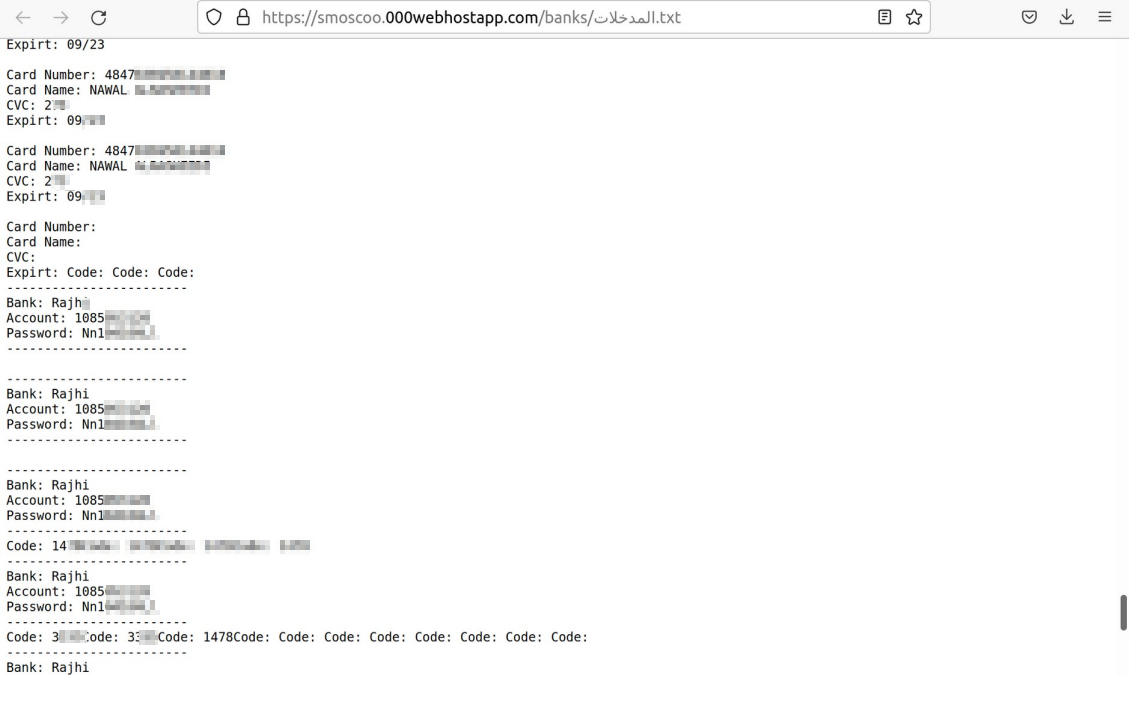
Once credentials have been successfully intercepted from the victim, the threat actor performs unauthorized WIRE transfer to one of the banking accounts opened on “money mule” (which they will use for further cash-out operations or further money laundering).
Example:
One of such accounts has been identified in SABB:
- unauthorized transaction on 1,300.58 (SAR)
- unauthorized transaction on 20,000.58 (SAR)
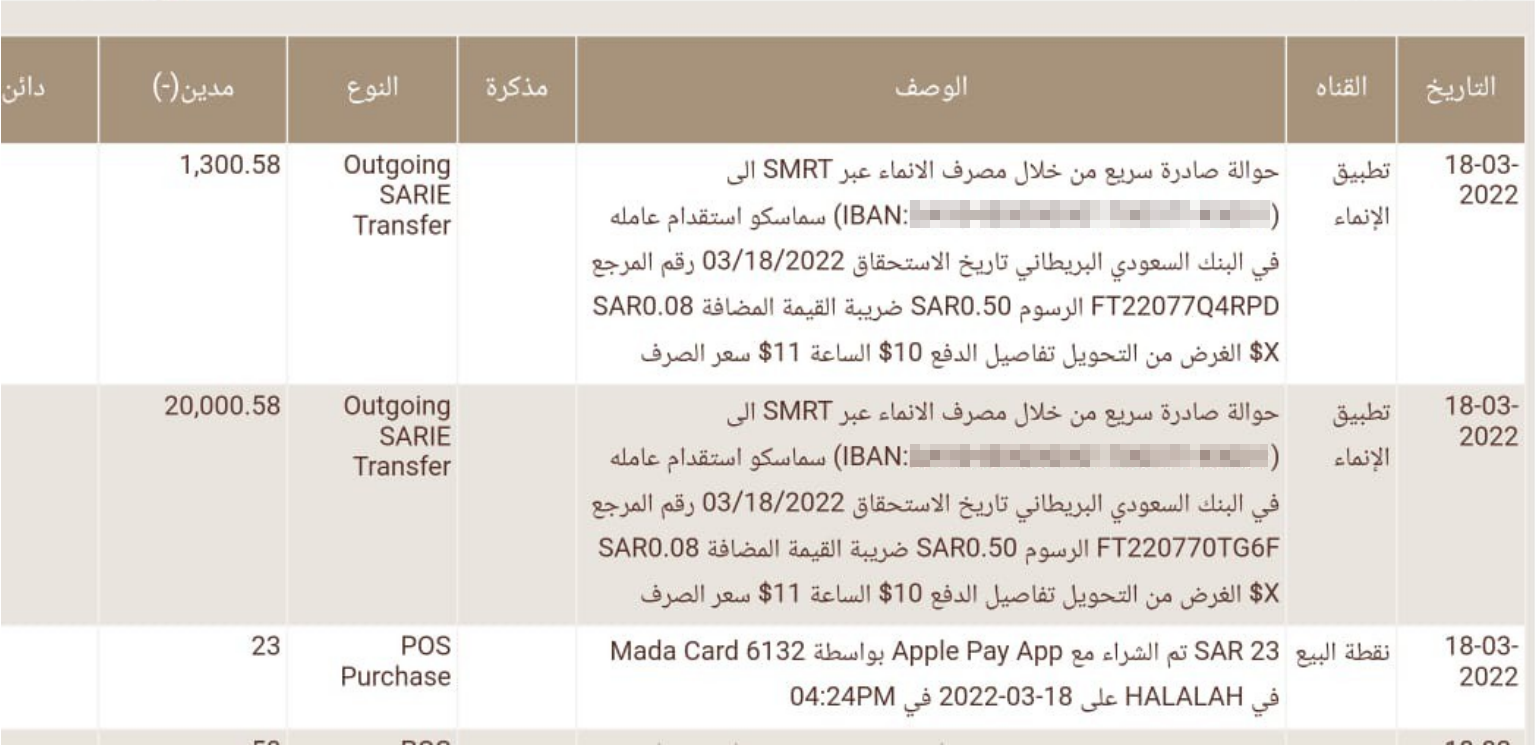
One of the accounts belonging to threat actor (or money mule): - IBAN: SA9345000000170057145001
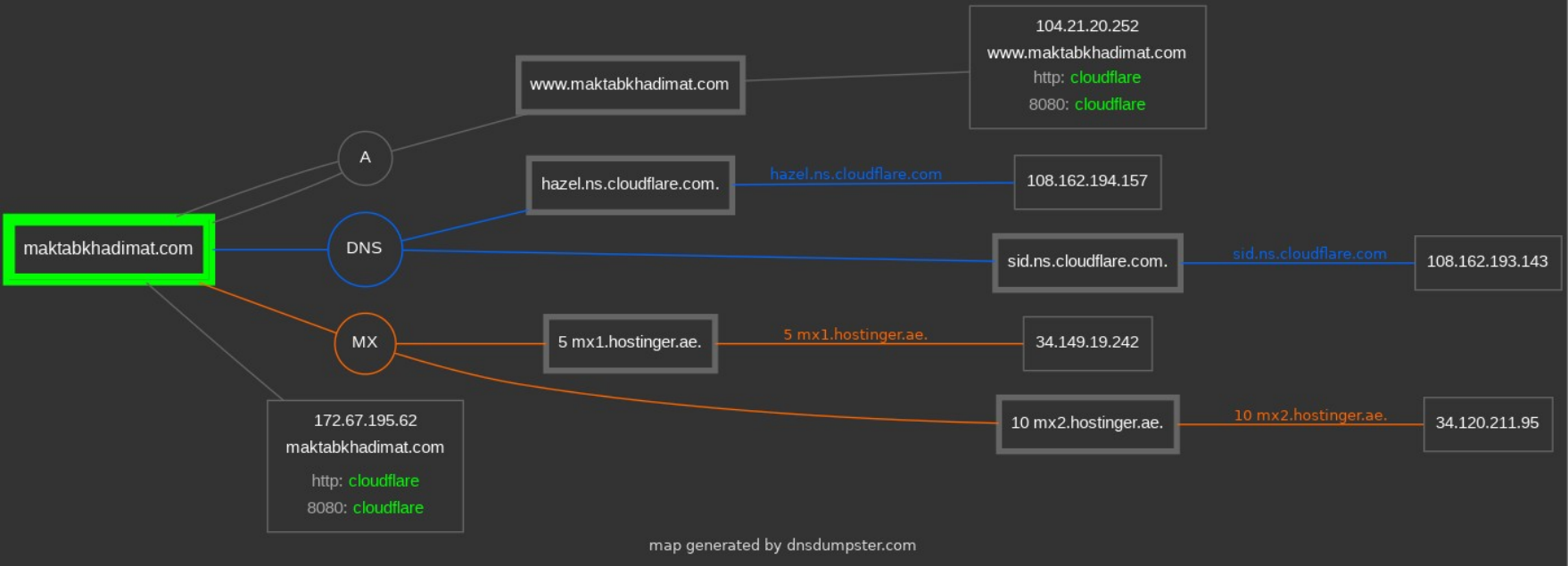
Visual Graph
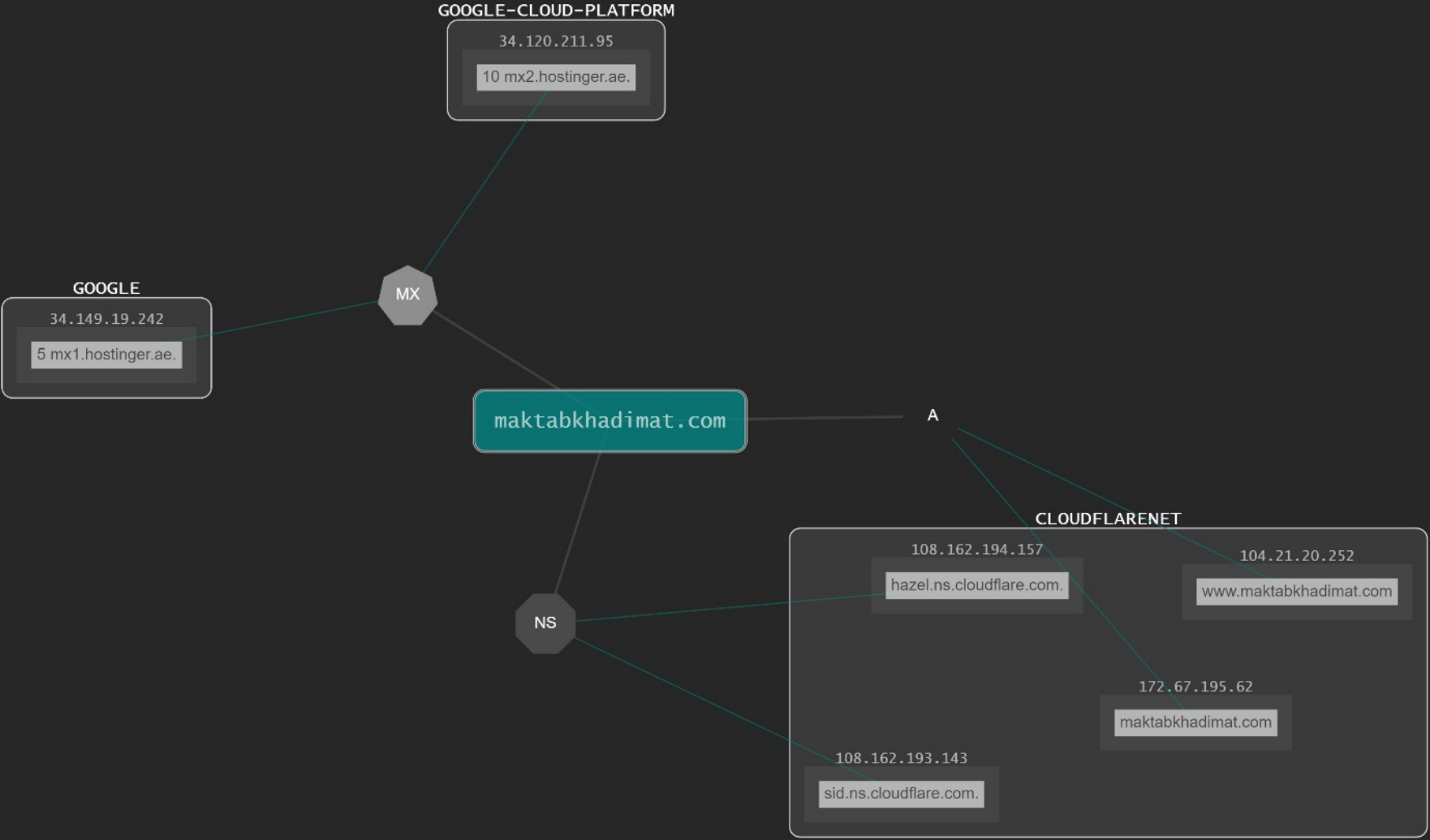
Indicators of Compromise (IOCs)
maktabkhadimat[.]com
smoscoo.000webhostapp[.]com
Last year, Ministers in Saudi Arabia approved a new law designed to enhance the Kingdom’s efforts to combat financial crime. According to the Saudi Arabian Central Bank (the Saudi Monetary Authority, or SAMA) a fraud is “any act involving deceit to obtain a direct or indirect financial benefit by the perpetrator or by others with his help, causing a loss to the deceived party.” This new law is an important step towards the “transparency and accountability,” “effective governance,” and “responsible enablement” anticipated by Vision 2030.
On April 30, 2021, Ministers in Saudi Arabia approved a new law, due to come into force in September of this year, which is designed to enhance the Kingdom’s efforts to combat financial crime.
Cabinet Decision and New Law
According to the Saudi Arabian Central Bank (the Saudi Monetary Authority, or SAMA) a fraud is “any act involving deceit to obtain a direct or indirect financial benefit by the perpetrator or by others with his help, causing a loss to the deceived party.”
The new law for Combating Financial Fraud and Deceit, approved by Cabinet Decision No. 534/1442, builds on that definition with the following significant provisions:
- Convicted fraudsters shall be subject to jail terms of up to seven years and fines of up to SAR 5 million (approximately USD 1.3 million). Article 1. Anyone convicted of inciting fraud shall be subject to the same maximum penalties, where the fraud occurs and loss is suffered, or up to half the same maximum penalties (e.g., imprisonment for up to 42 months and a fine of up to SAR 2.5 million (~USD 650,000)), where the fraud does not occur. Article 3.
- Anyone convicted of attempting to commit fraud shall be subject to up to half the maximum penalties (e.g., imprisonment for up to 42 months and a fine of up to SAR 2.5 million (~USD 650,000)). Article 4.
- Importantly, repeat offenders and groups of organized financial criminals shall be subject to up to double the maximum penalties, meaning jail terms of up to 14 years and fines of up to SAR 10 million (~USD 2.6 million). Article 5.
- Courts may at their discretion grant exemptions to these penalties, but only where individuals come forward and report the crime before there is any loss, or where individuals report the crime afterwards but where the reporting leads to the arrest of all the other parties involved. Article 8.
Legal Aspects
This new law is an important step towards the “transparency and accountability,” “effective governance,” and “responsible enablement” anticipated by Vision 2030. It should help to deliver the strategic objectives of His Majesty King Salman bin Abdulaziz and Crown Prince Mohammed bin Salman Al Saud of a “thriving economy” and a “vibrant society” by “creating an attractive environment for local and foreign investment.”
The incident has been addressed to the appropriate law enforcement agency and proper assistance has been provided to the victims of this campaign. Resecurity was able to block the financial transactions subject to stolen funds with the assistance from the banks used by the 'money mules', and assisted in the recovery of the stolen funds, including the compensation provided to the victims.
If you or your counterparts have faced online-banking fraud and your funds have been stolen, please, don't hesitate to contact us for further consultation via contact@resecurity.com. We are happy to assist you and do our best to clarify the root-cause of the incident, and to facilitate recovery of possible stolen funds. Please note, it is critical to use 2FA on your banking account including your e-mail account attached to it, following network hygiene principles will help prevent compromises.
Refrain from installing unknown mobile applications on your mobile devices, as they may potentially contain malicious code, and never execute attachments from suspicious e-mails - one of the key delivery channels of online-banking malware. Contact your financial institution immediately in case you may have identified a suspicious transaction on your account and file a police report to document the incident. The timing is critical in further incident response, and proper coordinated actions may result in successful bad actor identification and funds recovery.

