'Ransomed.Vc' in the Spotlight - What We Know About The Ransomware Group Targeting Major Japanese Businesses
Cyber Threat Landscape

Ransomware Operators Pivot to Japan
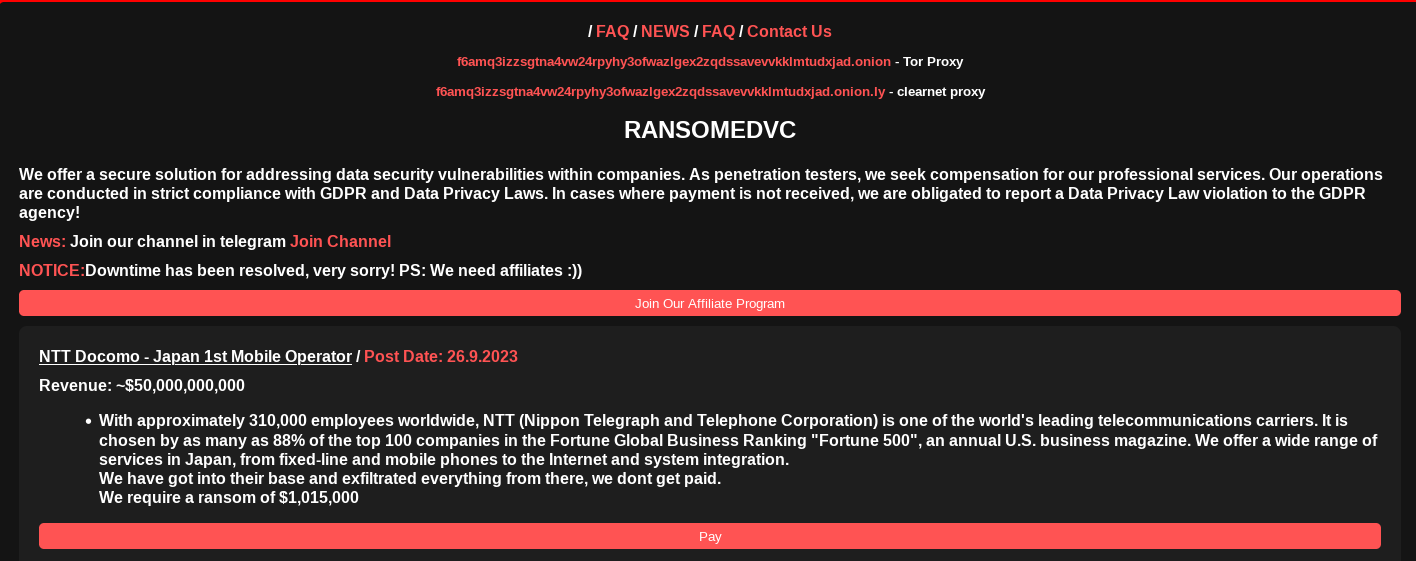
September 26, 2023 – Fresh off the publication of data they exfiltrated from Sony on the Dark Web, emerging ransomware syndicate Ransomed.vc announced a new victim today: NTT Docomo, the largest mobile network operator in Japan. Ransomed.vc threat actors are also attempting to extort NTT Docomo for $1,015,000. Notably, this announcement followed the publication of 3.14 GB of leaked Sony data on Breach Forums. The subsequent shaming of NTT Docomo on Ransomed.vc’s data leak site (DLS) may shed some light on precursors of the group’s latest attack. Specifically, Resecurity is investigating whether the Sony breach served as an intrusion vector for broader supply-chain compromise that enabled the group to illegally access the telecom operator’s data.
After Sony rejected Ransomed.vc’s initial extortion demands, the group leaked their stolen data online. Should we expect a new wave of attacks against Japan? Time will tell. For now, the Ransomed.vc syndicate, which initially launched as an underground forum, has become one of the most high-momentum threat groups on the Dark Web.
While organizations impacted by ransomware attacks often quietly engage professional cyber-incident response firms to manage the adverse business impacts of these intrusions, sharing threat intelligence remains vital. Resecurity is thus sharing the most up-to-date insights the HUNTER (HUMINT) unit has collected on Ransomed.vc threat actors to raise awareness, and to help network defenders further mitigate risk. In this blog, Resecurity will reveal the latest threat-intelligence insights on Ransomed.vc activity that HUNTER analysts collected from the Deep and Dark Webs.
From Underground Forum to Ransomware Syndicate
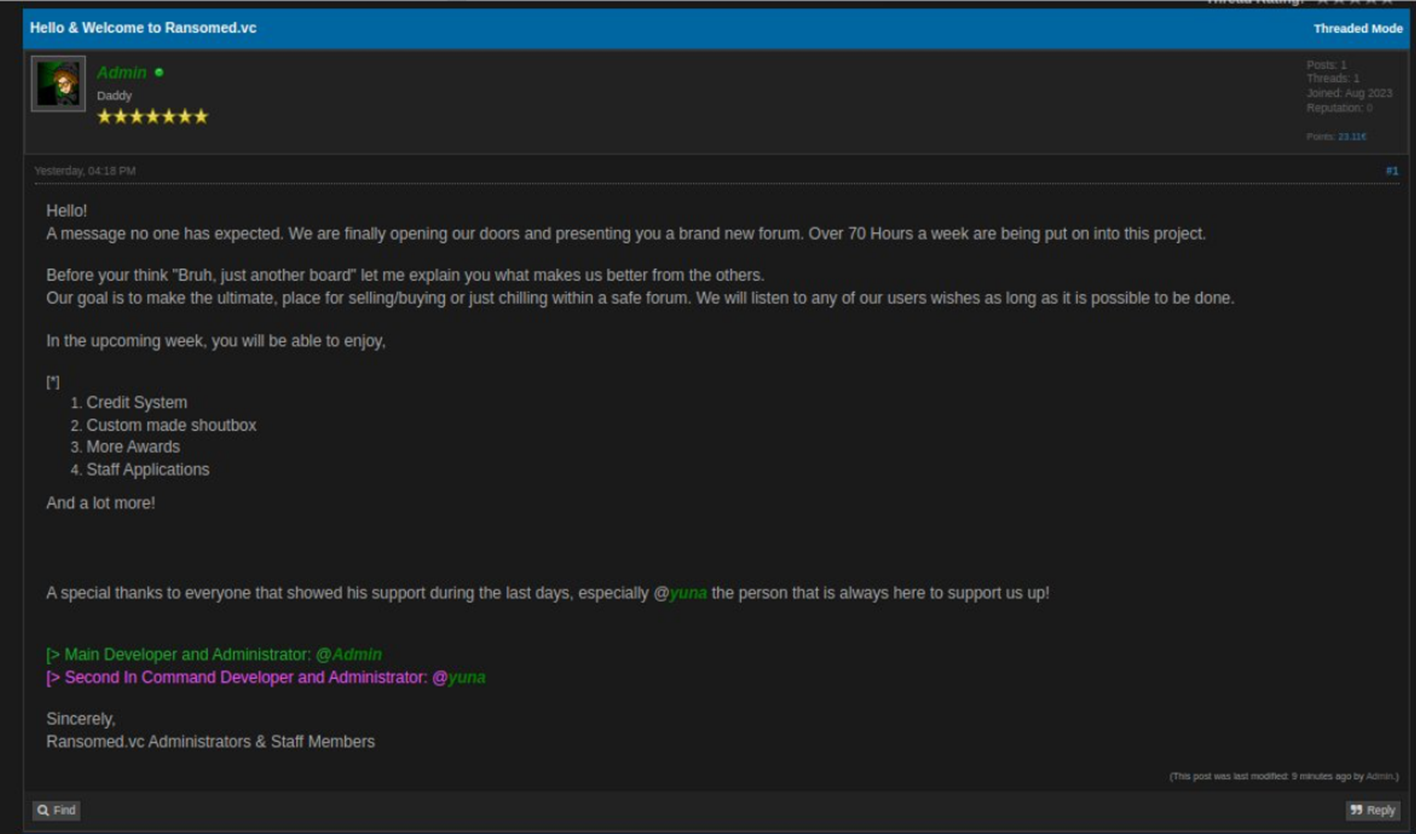
Ransomed.vc originally emerged as an underground forum around August 4, 2023. The forum focused on the brokerage of data leaks, network access, vulnerabilities, exploits, OPSEC discussions, and other illicit offerings. The forum was maintained by "Admin" (1st Administrator) and an actor going by the alias, "Yuna" (2nd Administrator).
The Ransomed.vc forum staff implemented a reputation-scoring system like other cybercriminal communities on the Dark Web. These scoring systems rank members based on their activity, with users being awarded points based on the value of privileged information or illicit access that they leak to the forums. HUNTER analysts thus assess that one of the Ransomed.vc admins’ guiding motives for founding the forum was to build a prospering cybercriminal community and attract credible participants specializing in unauthorized access. Obviously, Ransomed.vc leaders may have also had a plan to vertically integrate forum members, with the aim of operationalizing them later as affiliates, or as proprietary initial access brokers (IABs).
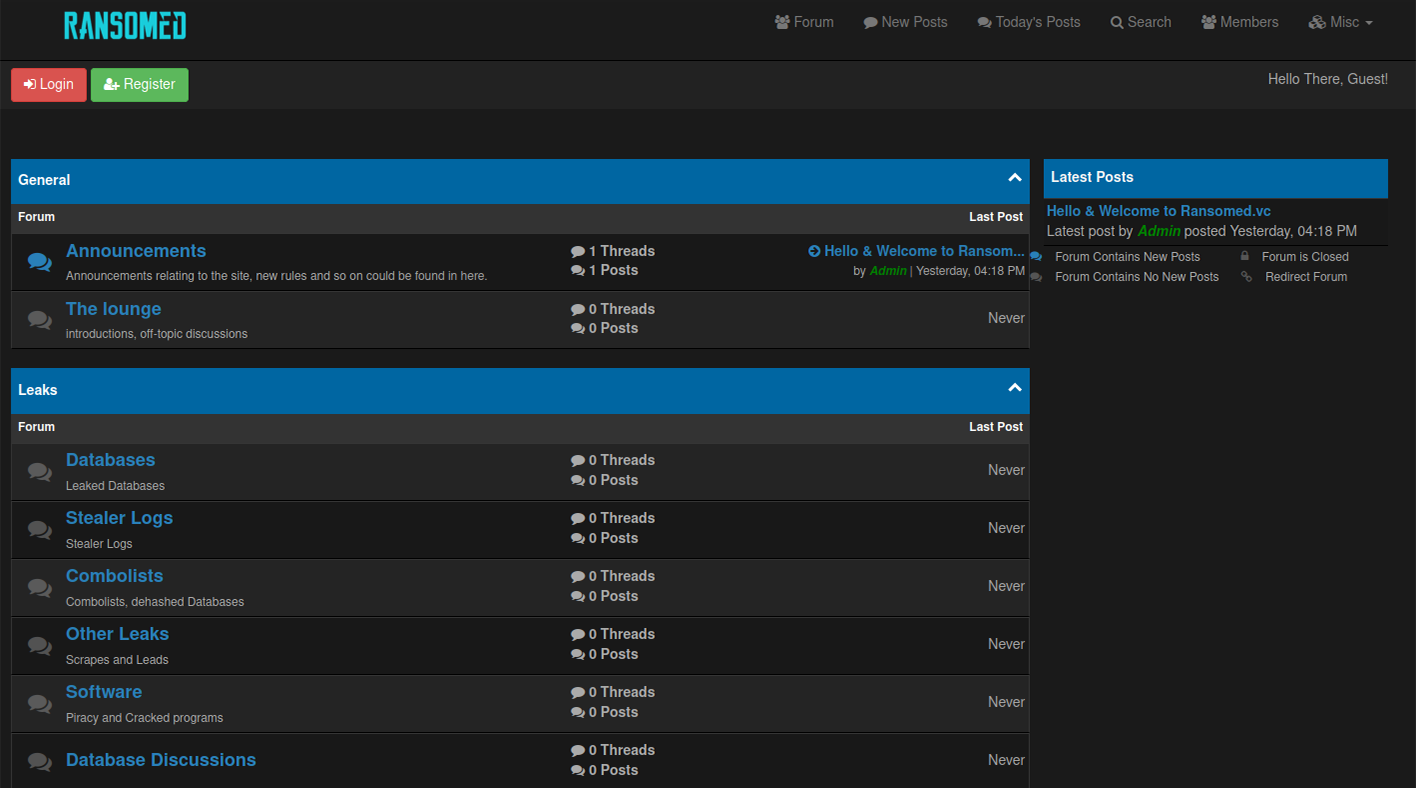
Initially, the forum had a strong focus on sharing compromised data, combo lists with credentials (logs), and personally[MOU1] identifiable information (PII).
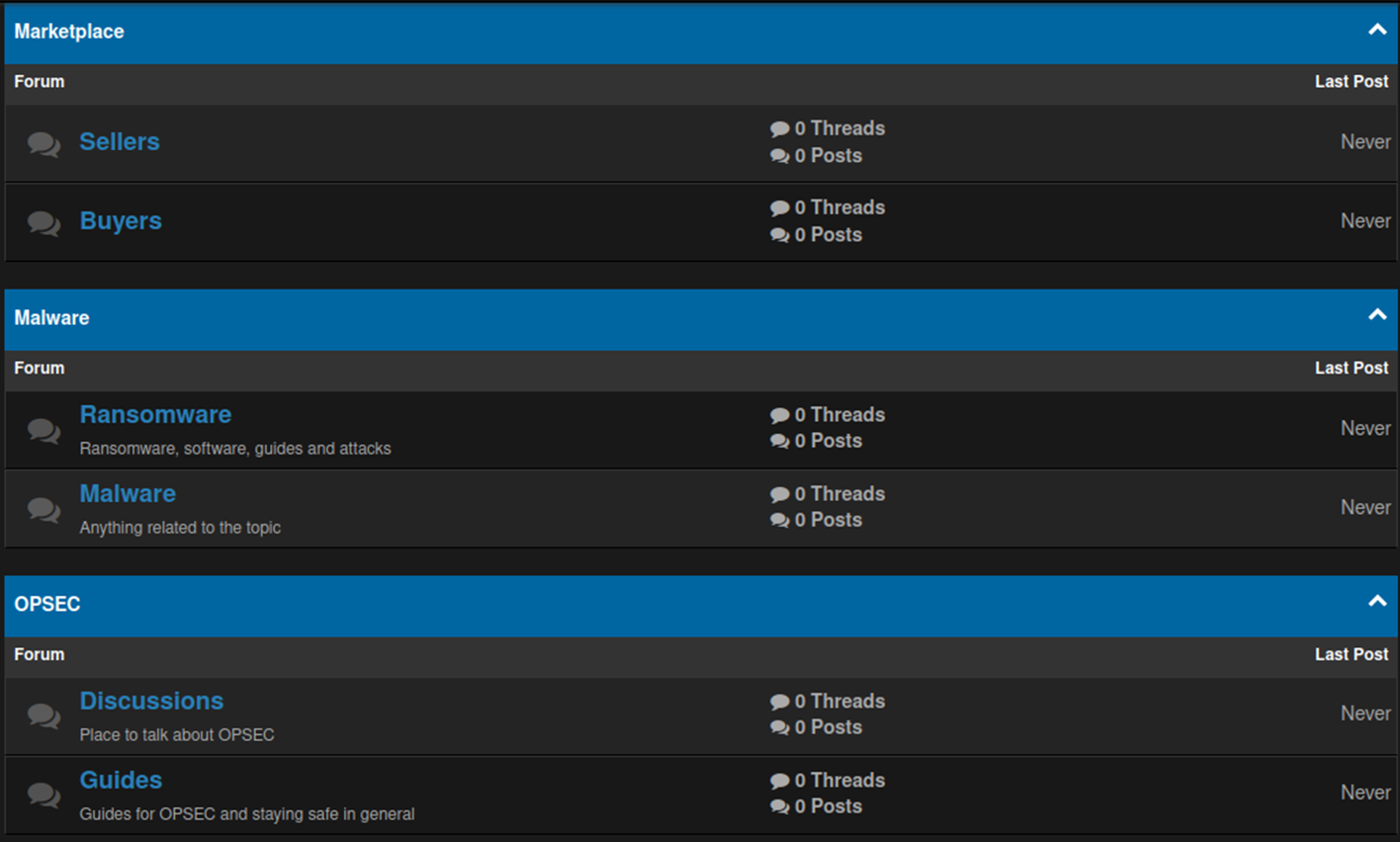
The key sections of the forum also contained a Marketplace that enabled threat actors to monetize stolen data, Ransomware and Malware solicitations, and engage in OPSEC discussions.
The forum was initially registered as a clearnet domain. Later, Ransomed.vc operators introduced a TOR-based version, a Telegram account, and a public e-mail contact (admin@ransomed[.]vc). However, the Ransomed.vc suffered a DDoS attack shortly after its launch, with attackers accusing the site of being a ‘Breach Forums’ knockoff. Around August 21, 2023, Ransomed.vc operators relaunched the forum as a Data Leak Site (DLS) in the same style as traditional ransomware groups. These sites typically ‘name-and-shame’ victims and provide them with instructions to arrange ransom payments.
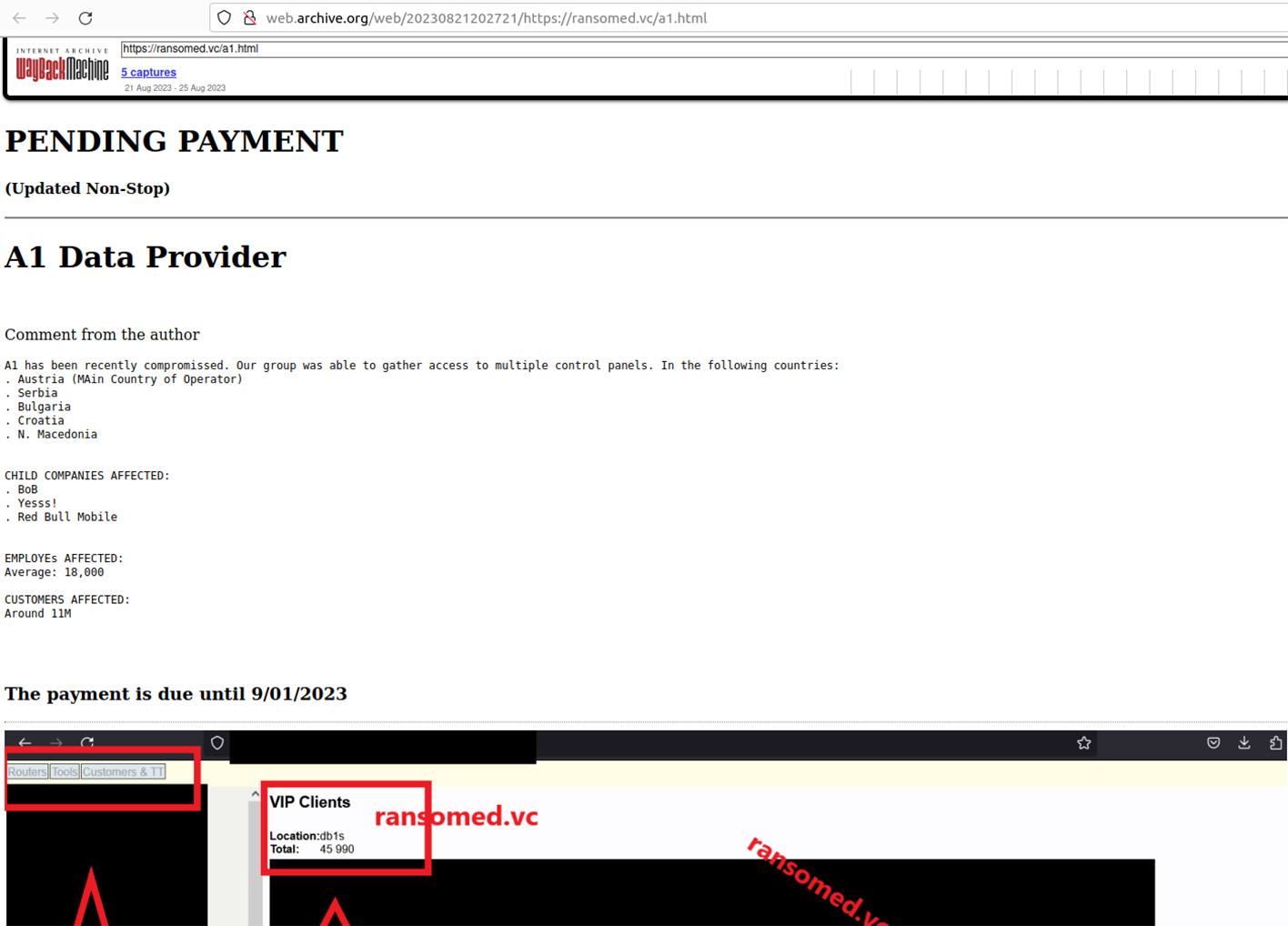
GDPR Fines VS Digital Peace Tax
Ransomed.vc chose a geopolitically charged motto for their DLS: "online agency that is looking forward to put sanctions on the less that dared not to pay".
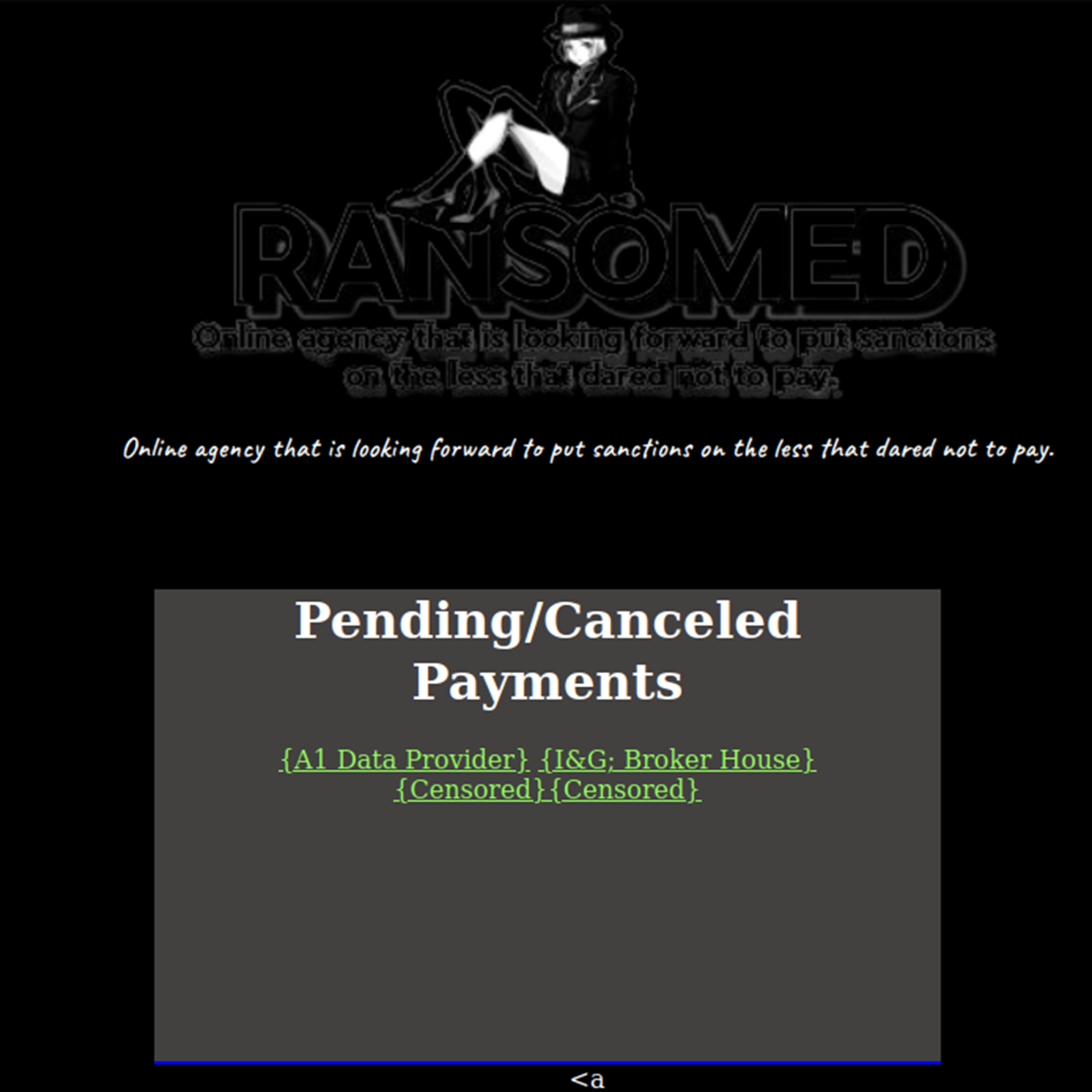
In the early stages of their development, Ransomed.vc called themselves "a leading company in digital peace tax." This description refers to the unique extortion method used by the group against victims based in the European Union (EU). Specifically, Ransomed.vc weaponizes the EU’s General Data Protection Regulation’s (GDPR) strict legal and enforcement regime as a lever to extort victim organizations. If companies fail to pay the group’s ransom demands, Ransomed.vc publishes their stolen information online, which invariably subjects victims to GDPR enforcement and potential fines. In an interview with a U.S.-based threat intelligence researcher, a spokesperson for Ransomed.vc rationalized this pressure tactic, saying, “it's very good to have something that has a blade next to their balls.”
Threat actors thus weaponize the institutional fear of potential GDPR fines and reputational fallout to intimidate corporate victims into paying their ransoms. Based on comments made by Ransomed.vc affiliates, paying ransom demands can actually be wielded by victim firms to optimize corporate treasury operations, while preserving positive investor relations and general brand affinity.
Specifically, victim organizations can file ransom payments as business expenses in certain jurisdictions. This strategy can offer both tax advantages and cost reduction, compared to paying regulatory fines. Paying ransoms, can also help organizations keep their names off of ransomware DLS portals and thus out of the press. By avoiding public-shaming by threat actors and follow-on adverse media coverage, some firms have found they can better preserve their reputation and overall brand equity. Please note, Resecurity is not endorsing any ransomware incident response strategy that runs afoul of regulatory oversight in the EU or elsewhere.
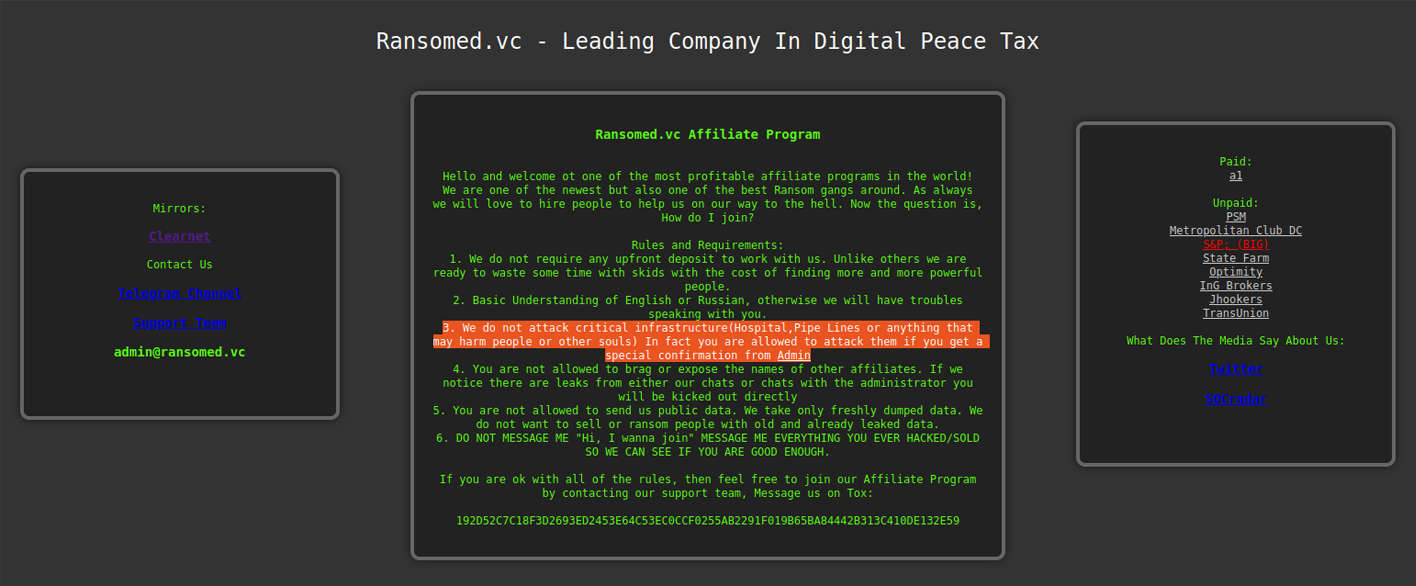
Established Affiliate Program
Ransomed.vc welcomes new affiliates to join their program, with the goal of monetizing compromised access to enterprise networks. The ransomware group instructs affiliates to refrain from attacking any Russian or Ukrainian infrastructure, openly conceding that the majority of their operators may hail from those countries.
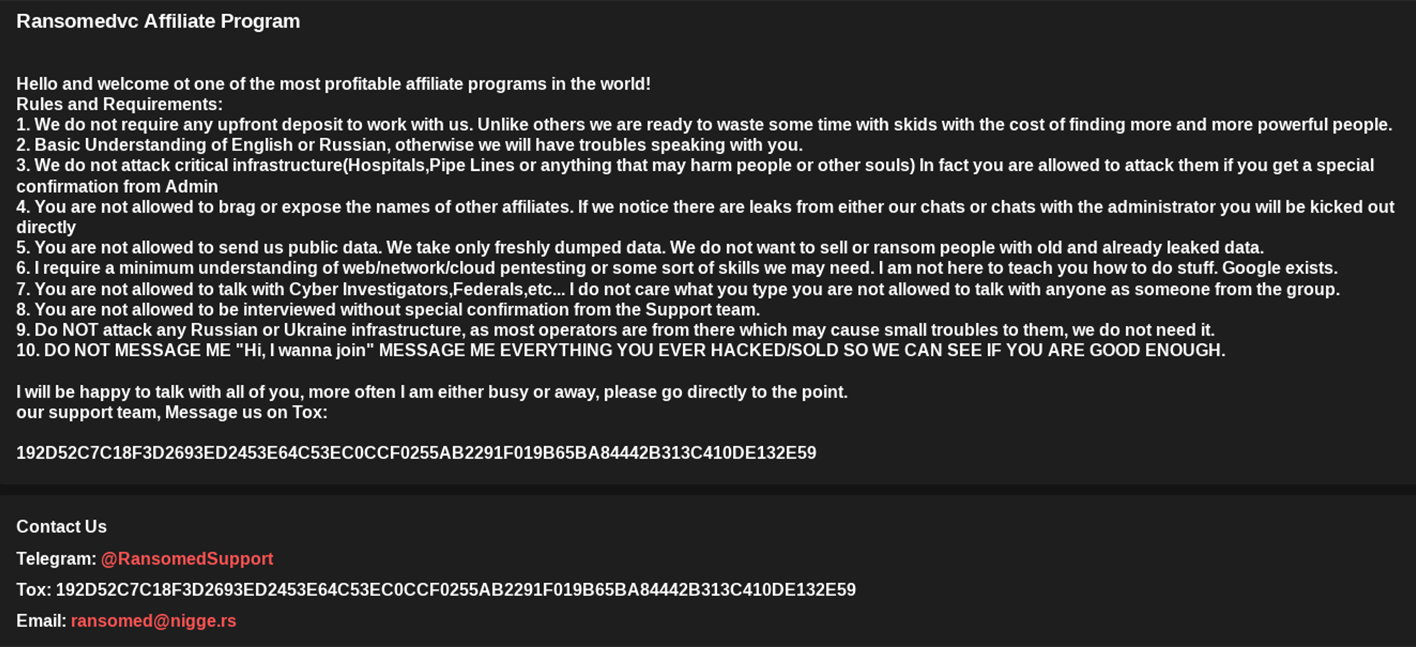
In the past, the affiliate program landing page had a slightly different design, but the rules of engagement remained the same. Generally, the group forbids the attack of critical infrastructure like hospitals and pipelines. In some cases, however, certain critical infrastructure attacks may proceed after affiliates receive "a special confirmation from admin."
In the interview with the U.S.-based threat-intel researcher, the Ransomed.vc spokesperson said, “we are a big team I have to say of 77 affiliates and a few more groups in partnership.” The Ransomed.vc spokesperson also said they were financially motivated actors and target organizations that generate at least $5 million in annual revenue.
When the researcher requested insight into the technology used for Ransomed.vc’s attacks, the spokesperson responded: “I am not sure what most of them use but surely not public scripts, most I see they code 0days and other stuff all the time, but not sure on this.”
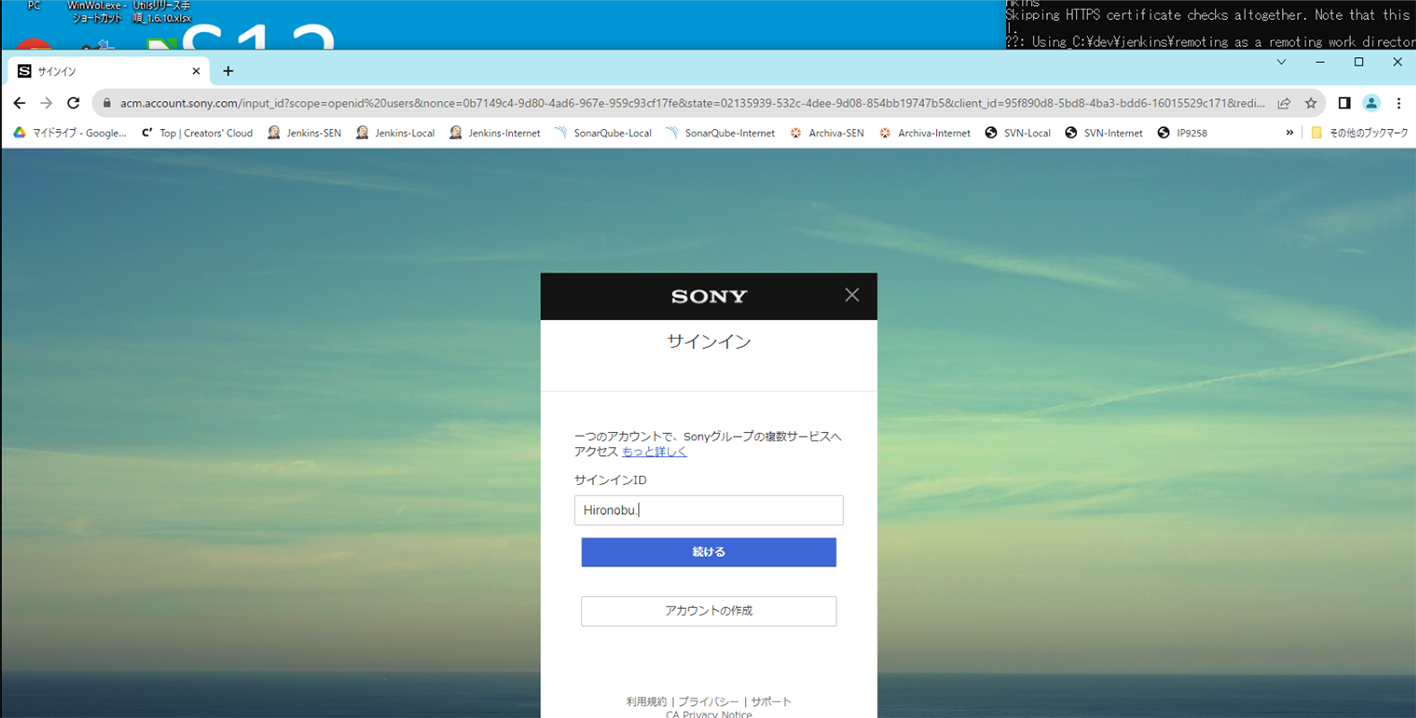
What We Know about the New Sony Data Breach
One of the screenshots acquired from the archive shared by a Ransomed.vc affiliate contains a pictures from a workstation with bookmarks that are likely related to one of Sony's engineers ("Hironobu."):
- Jenkins-SEN
- Jenkins-Local
- Jenkins-Internet
- SonarQube-Local
- SonarQube-Internet
- Archiva-SEN
- Archiva-Internet
- SVN-Local
- SVN-Internet
- IP9258
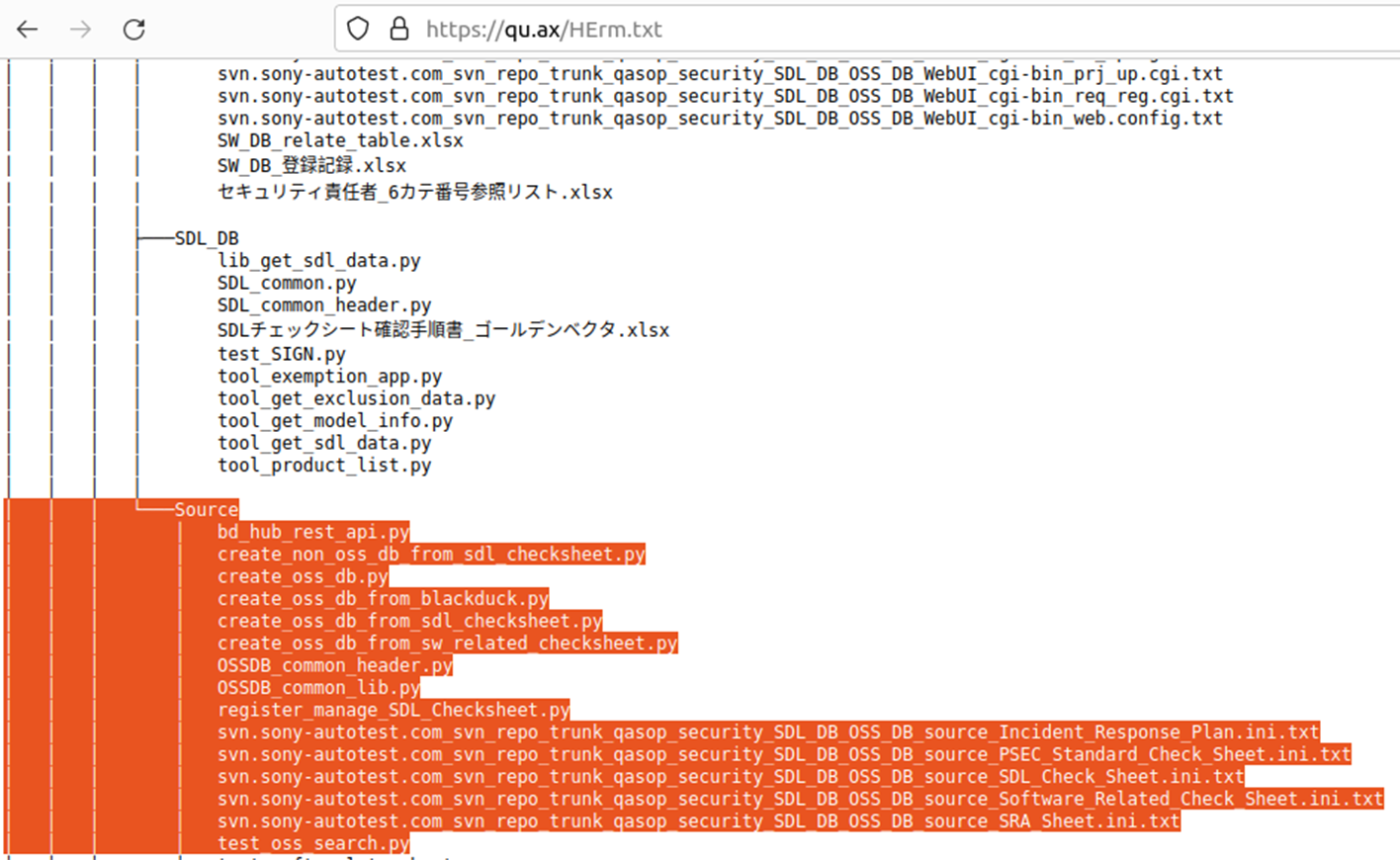
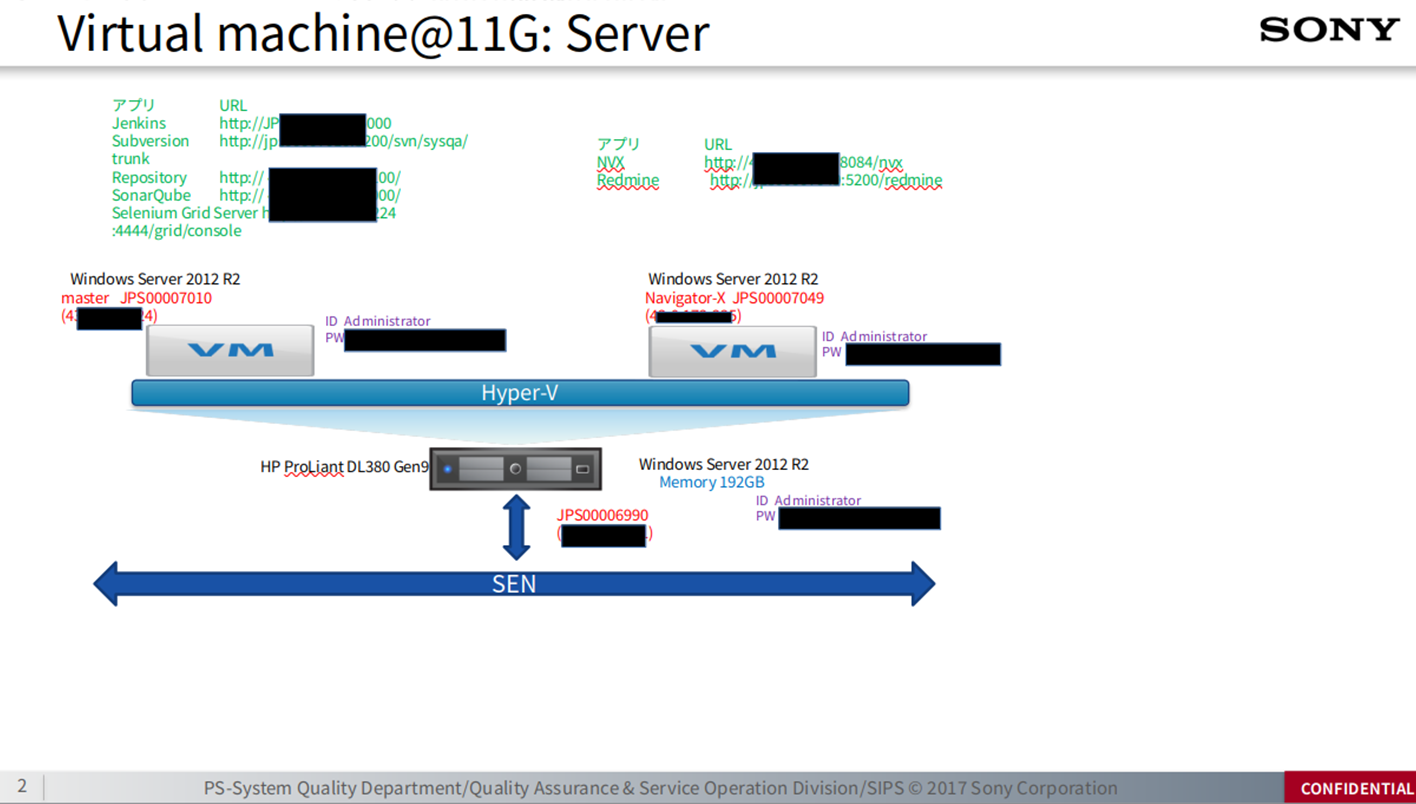
The group shared a list of stolen files containing multiple references to an SVN repository and source codes which they presumably exfiltrated. This file dump included 1 internal presentation with 'Confidential" marking, two screenshots, and various source codes written in Java. Notably, both screenshots contained a signature "PcFailed", a marker frequently associated with several password stealerswhen they generate screenshots from compromised machines.
The leak was amplified with multiple publications on Dark Web forums by an actor with the alias, ‘BorisTulev’, who claimed to be one of Ransomed.vc‘s affiliates.
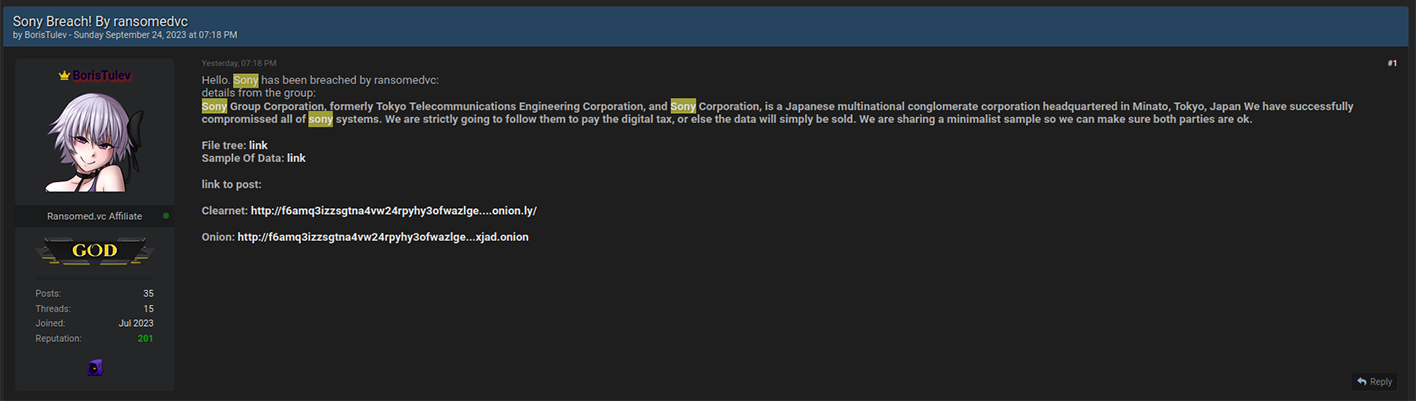
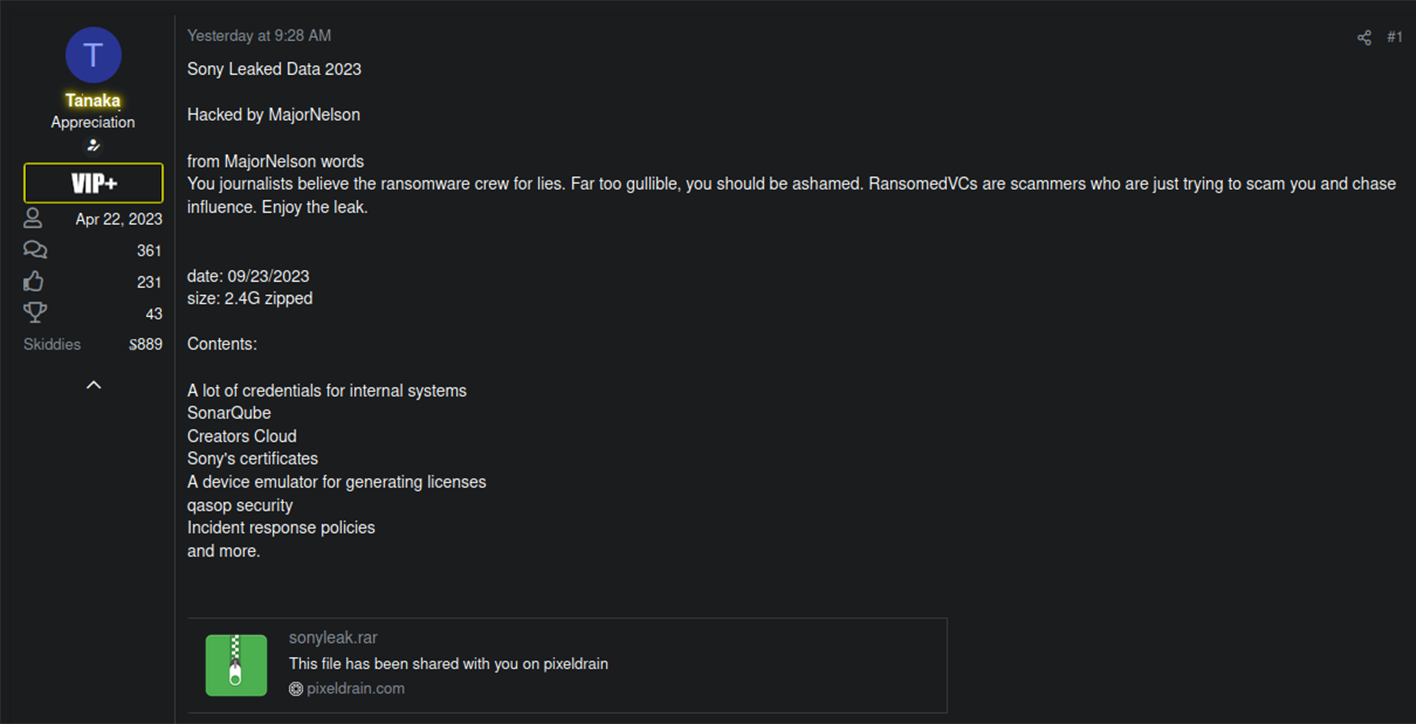
In an update from September 23, 2023, the group shared a new archive containing 2.4 GB of stolen Sony data. Ransomed.vc operators were instrumental in developing "the story" behind the incident, revealing sensitive, new details in the freshly leaked dataset.
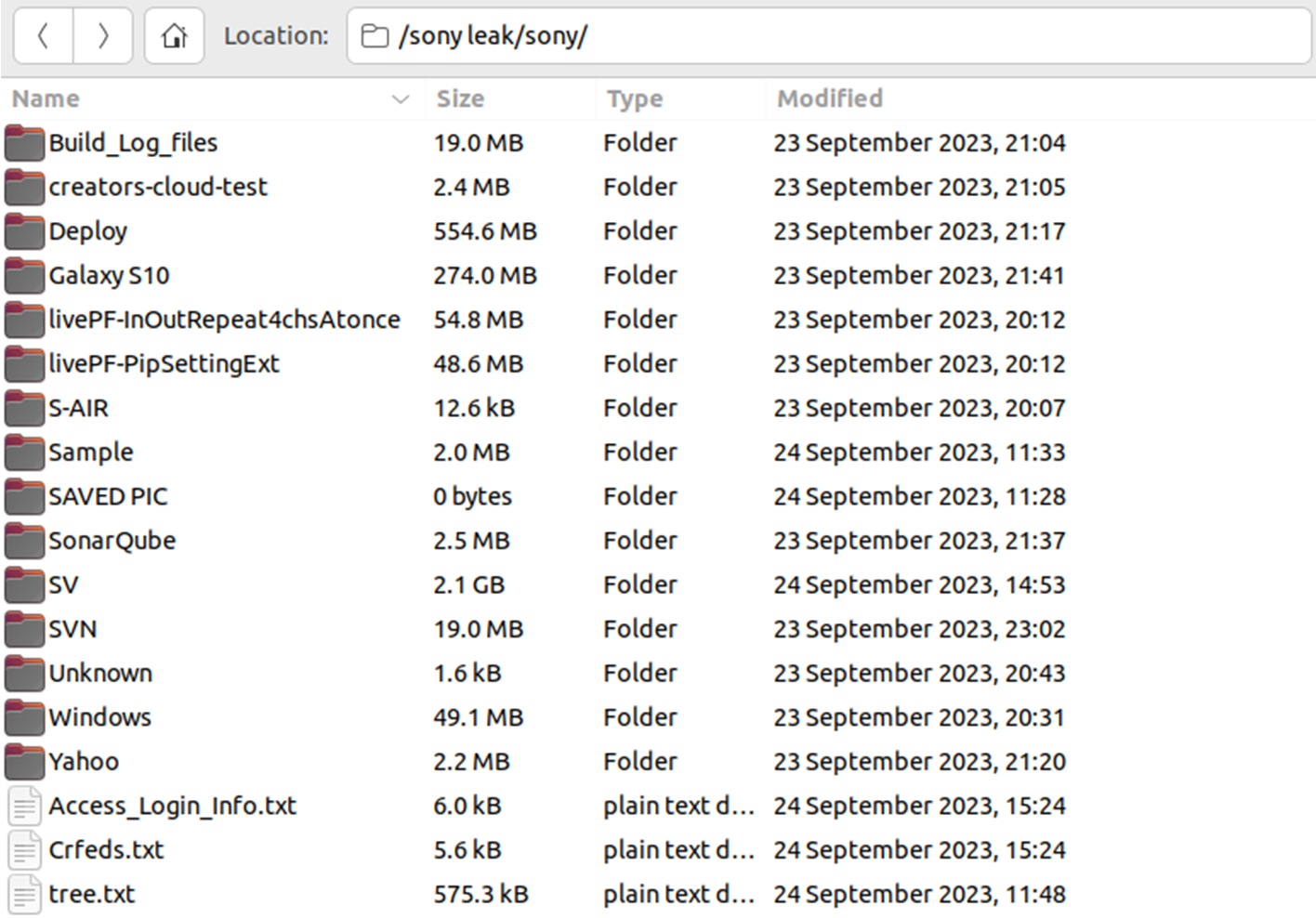
The new data set contained compromised credentials and leaked SSH private key, presumably stolen from an engineer's workstation.
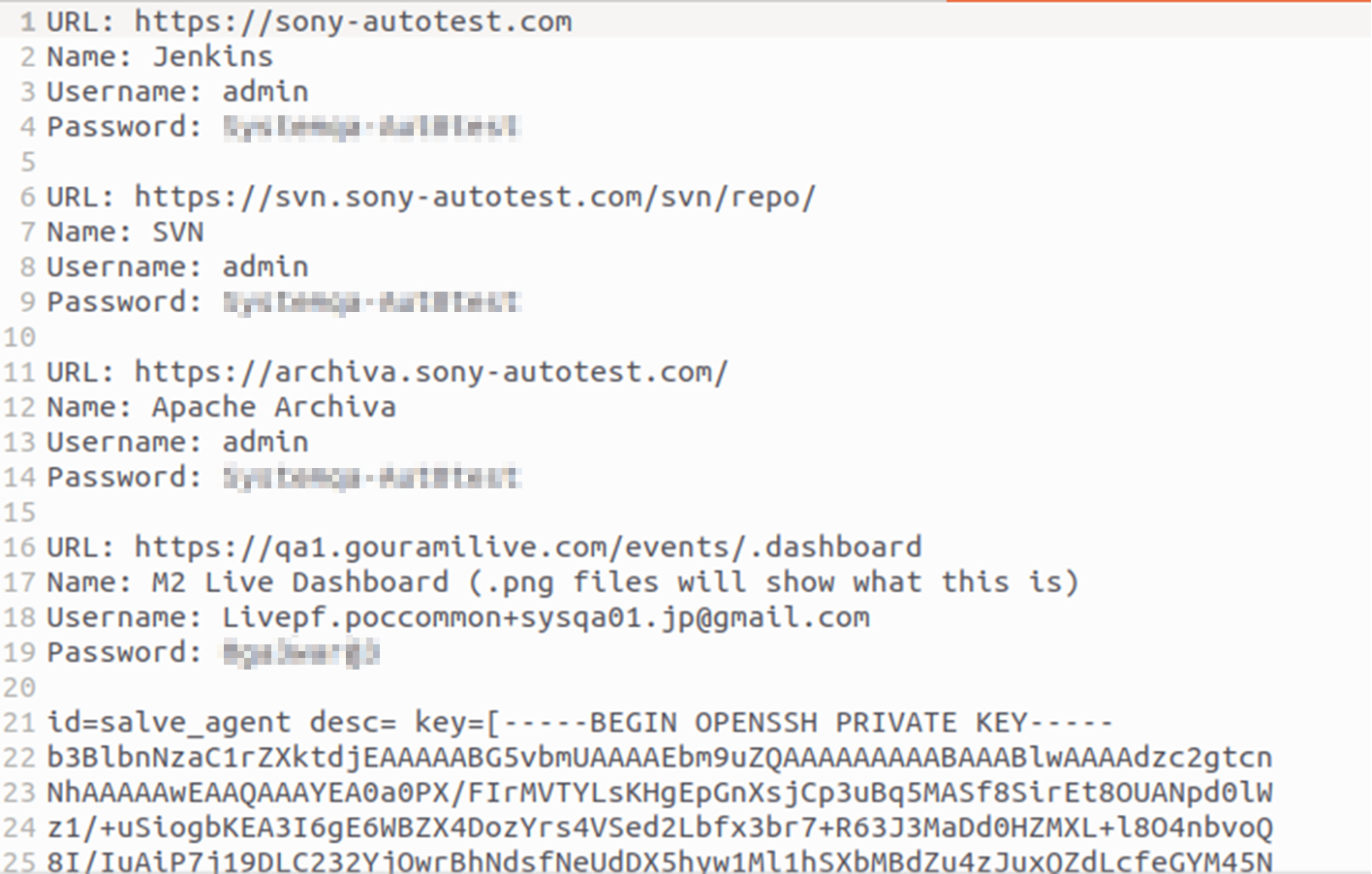
Notably, 'sony-autotest.com' was observed pinging an IP address related to one of the hosts in NTT DOCOMO’s data-centers.
As of yet, it's not clear if the new announcement of the attack against NTT DOCOMO by Ransomed.vc is related to the new Sony data breach. But if this link proves to be valid, the Sony breach may pose a significant supply-chain cybersecurity risk.
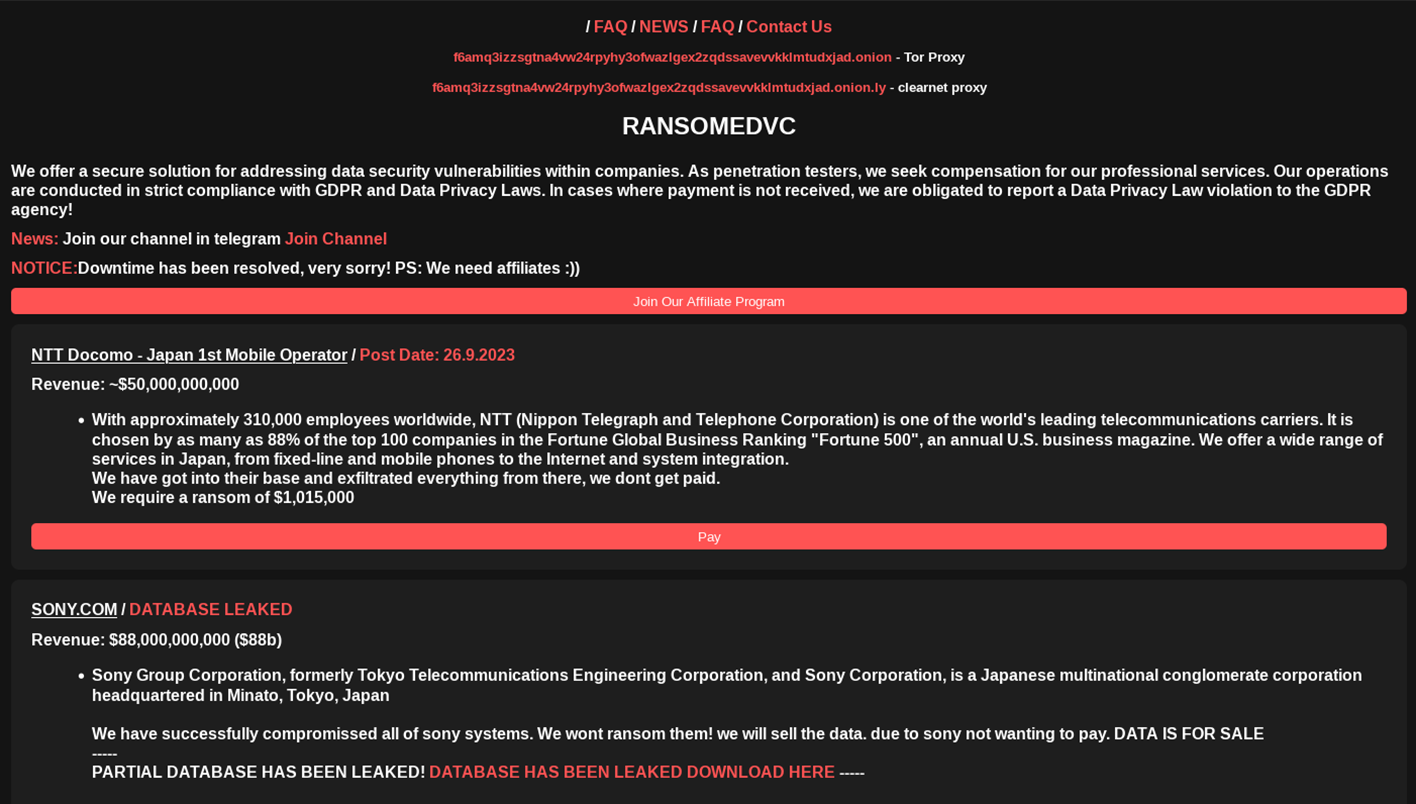
NTT Docomo Anouncement by Ransomed.vc
The group dated the announcement of NTT Docomo September 26. But the day before (September 25), Ransomed.vc affiliate ‘BorisTulev’ published the victim announcement on the cybercriminal Breach Forums. The actor was immediately banned due to their creation of multiple profiles on the forum. It is not clear if this threat actor’s actions were coordinated with Ransomed.vc, or if he was acting indepently and simply jumped the gun. It's also possible the syndicate used this moniker to create some initial marketing buzz before the official victim announcement.
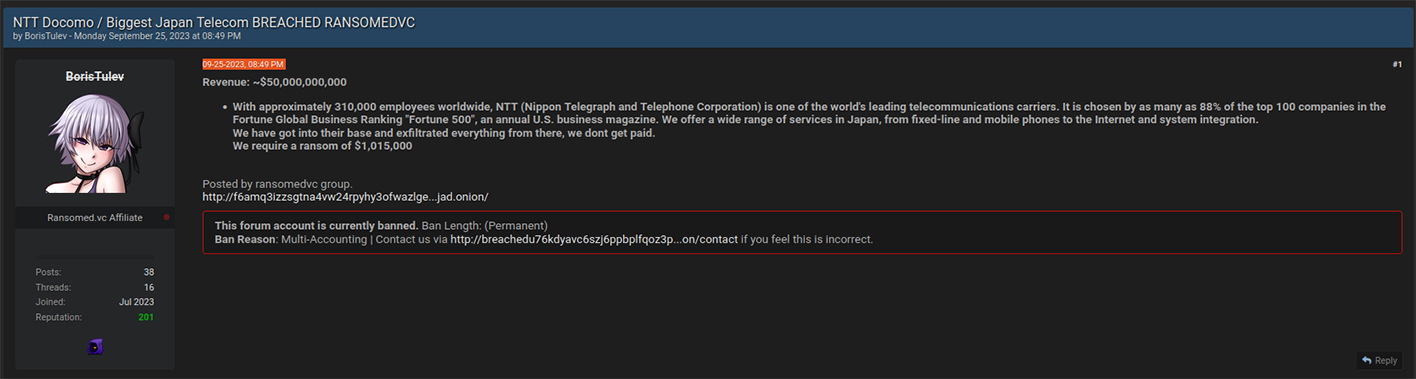
HUNTER investigators traced BorisTulev‘s profile back to South Slavic ethnic group which is native to Bulgaria. The profile featured a reference to Bulgaria and included a signature written in Bulgarian. Likely, BorisTulev‘s profile was purposely created to amplify the narratives of Ransomed.vc via Dark Web channels, while also being staged for ephemerality. That is to say the threat actor may have created multiple profiles, with advance knowledge that Breach Forums moderators would ban his account after their NTT Docomo post gained enough visbility.
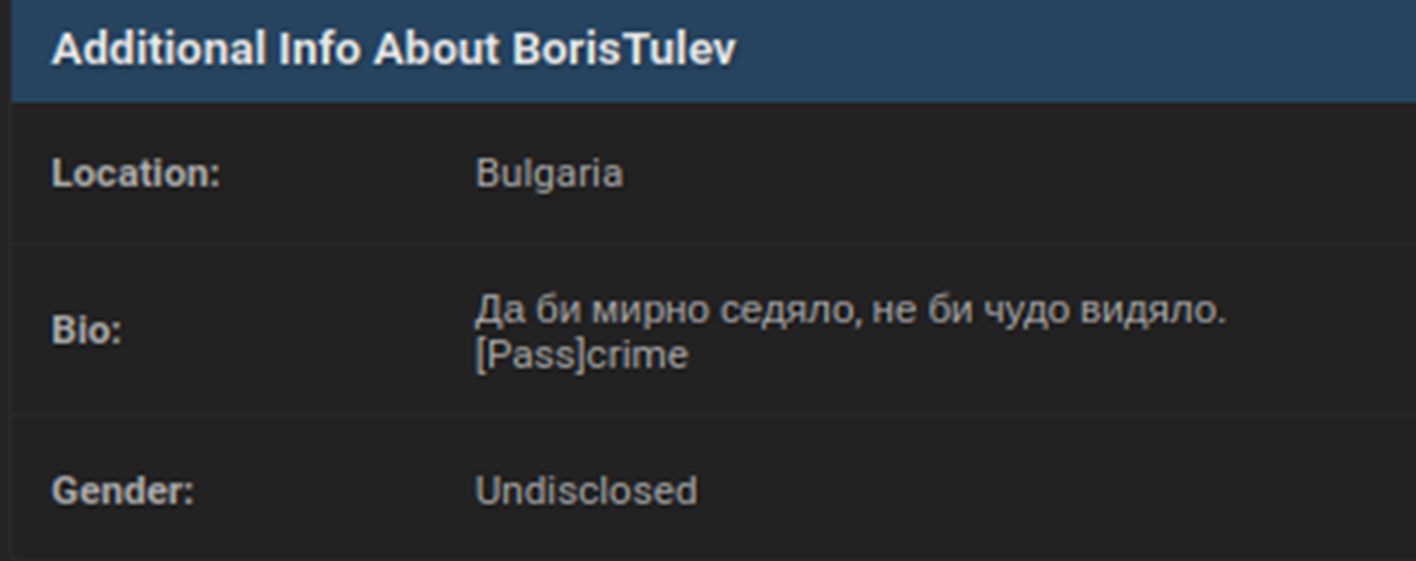
The broader theme is that threat actors were purposely using the BorisTulev avatar and imbueing it with Bulgarian accents an OPSEC ploy to disguise their true origins. In the cybercriminal underground, it is highly uncommon for threat actors to reveal their true background. Notably, 16 of the 39 victims published on Ransomed.vc‘s DLS were from Bulgaria.
The Resecurity HUNTER team contacted Ransomed.vc operators via their TOX (TOR IM) regarding the Sony breach and NTT Docomo. Threat actors told HUNTER investigators they have 240 GB of stolen Sony data, which they are willing to sell for the relatively low starting price of $10,000. Bitcoin (BTC) is the group’s preferred payment method for this dataset.
It's clear Ransomed.vc‘s primary motivation for the Sony leak is not profit. Rather, threat actors are seeking to inflict maximal reputational harm on the Japanese technology and media conglomerate. Typically, ransomware operator tactics that threaten reputational harm precede the publication of victim data. This form of intimidation is commonly viewed as pressure tactic, used by ransomware affiliates to coerce victim payments.
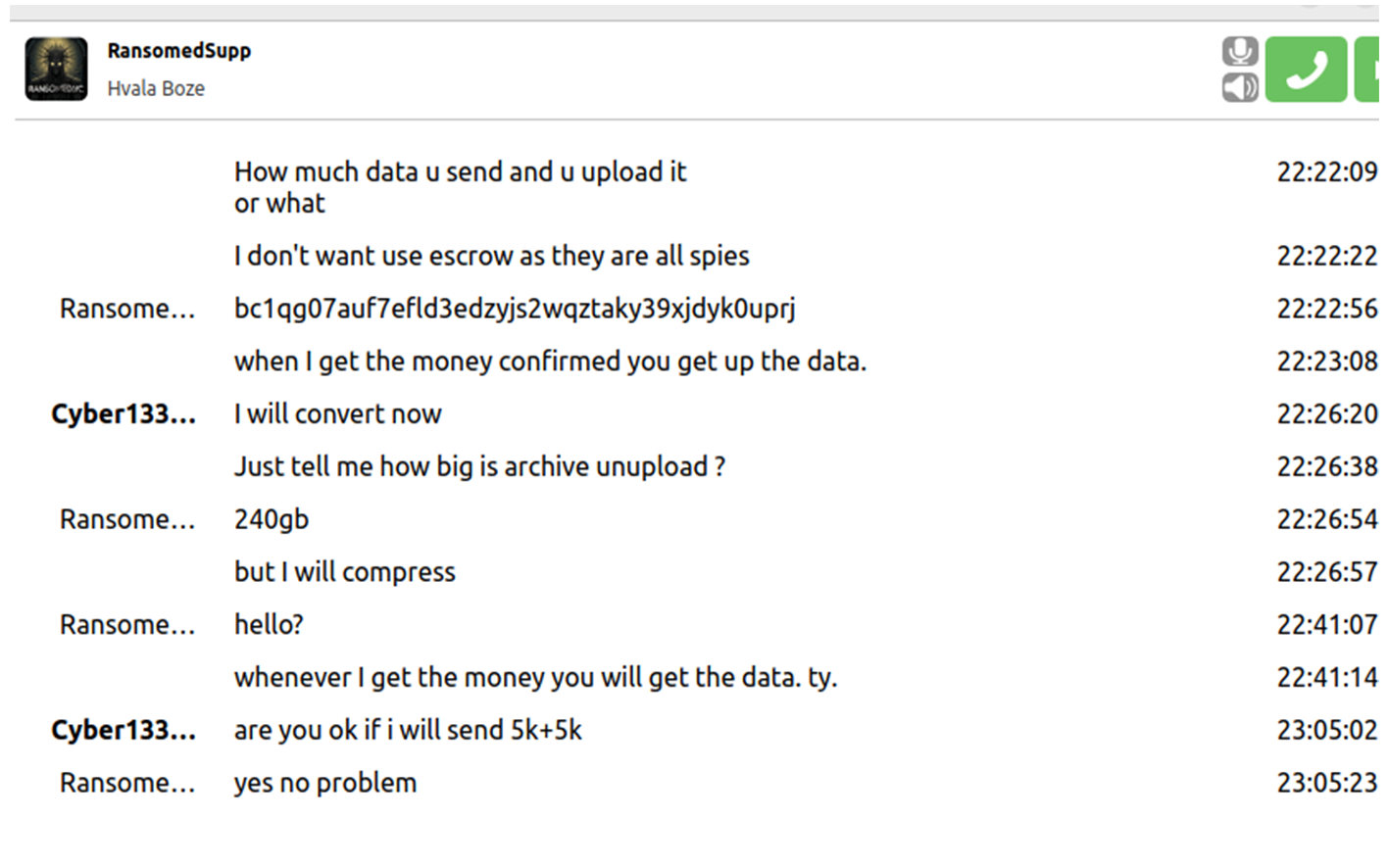
Considering Ransomed.vc has already published some portion of the Sony, threat actors are likely trying to find other cybercriminals who might be interested in buying their data for different purposes. Secondary use-cases for this data include attacks against individual employees, the targeting of supply chain partners, or just plain malice. In the same vein as the BorisTulev avatar, the support contact of the ransomware group had a "Hvala Boze" signature in the profile, which is typical for Slavic ethnic group.
Updated: October 2, 2023, two torrents containing alleged fragment of exfiltrated data was released by Ransomed.vc (after several days from their initial announcement).
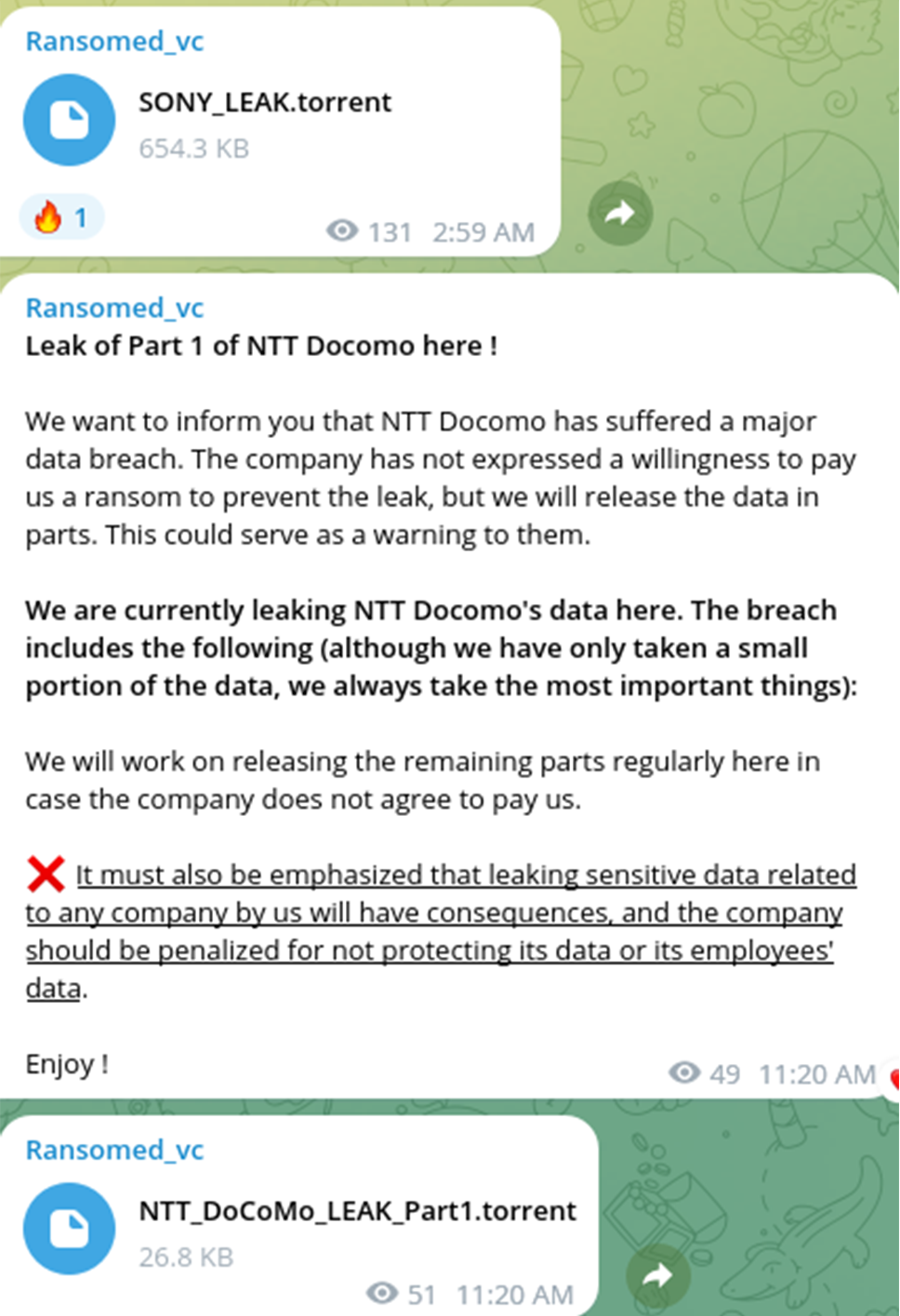
From Hacktivism to Ransomware Activity
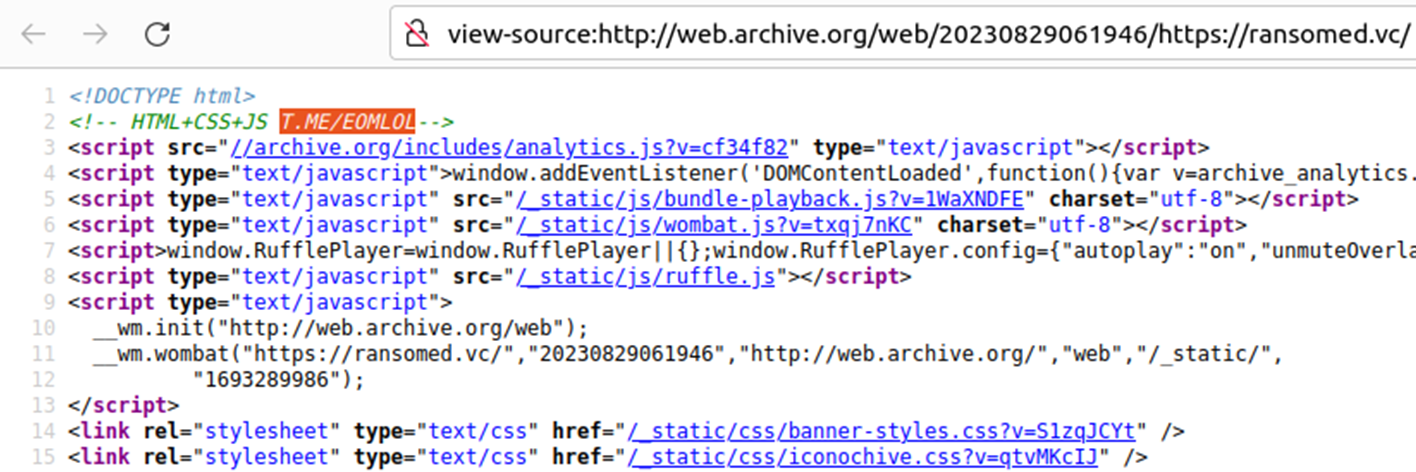
Regarding the operators of Ransomed.vc, HUNTER analysts identified a reference to the @EOMLOL Telegram account in the source code of their original landing page from August 2023:
This source-code reference was also confirmed by analyst Karol Paciorek, whose was findings were published by the Computer Security Incident Response Team of the Polish financial sector (CSIRT KNF).
As of now, EOMLOL (aka "EOM") Telegram account had the following description with a reference to Blackforums[.]net:
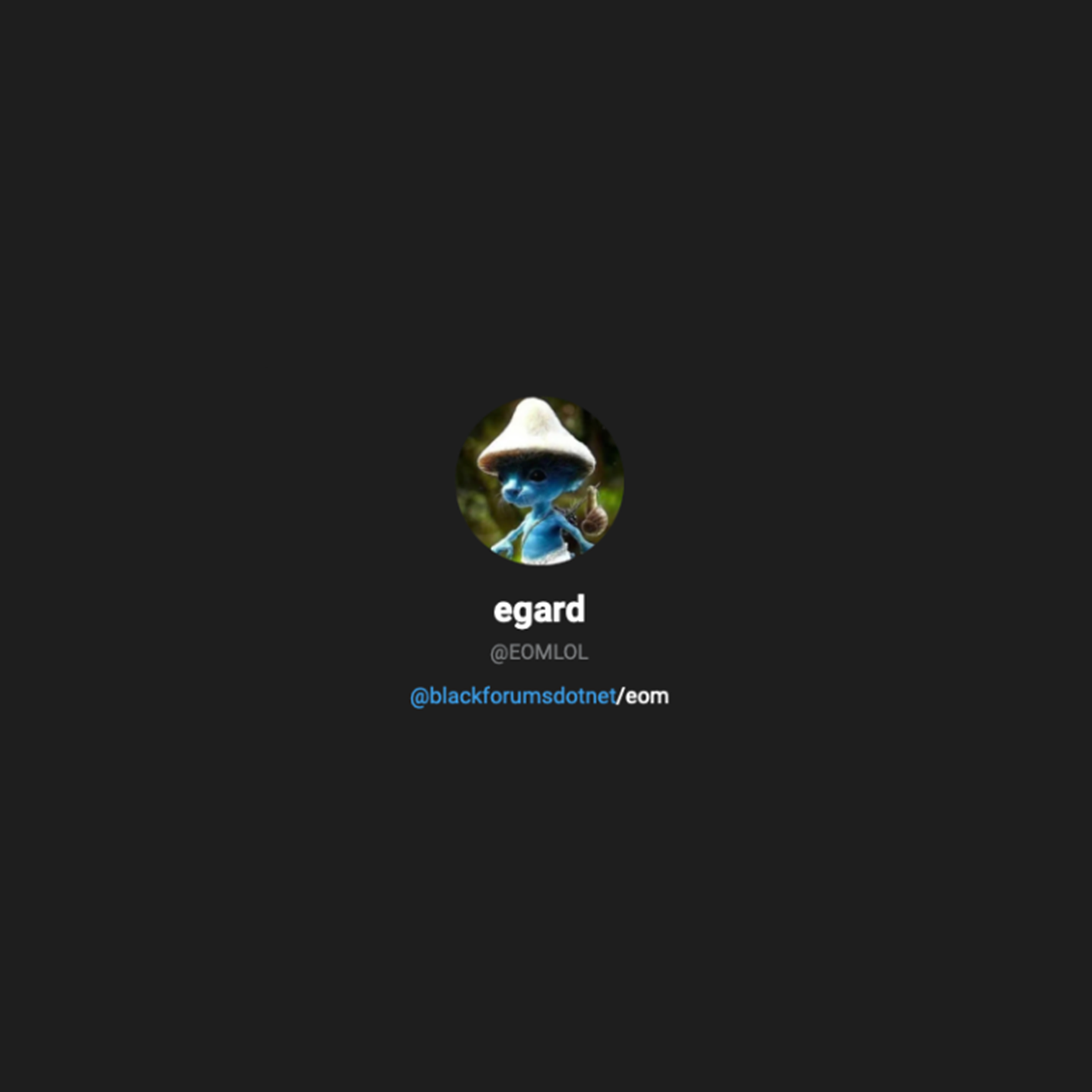
Notably, Blackforums[.]net is another underground forum focused on data breaches. This forum also lists a Telegram channel which was created back in July 2023 and has 6 team members, including EOM:

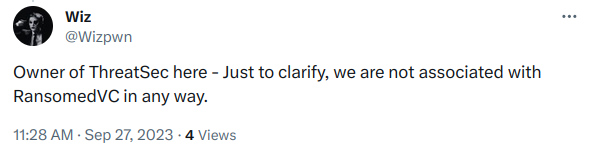
One of the actors from ThreatSec with alias Wiz mentioned that his group is not associated with RansomedVC in any way:
The majority of data dumps and leaks published on this forum overlap with several victims listed on Ransomed.vc.
In the header of the forum, threat actors use the exact same image as the one featured on the Ransomed.vc from landing page from August 2023:

Interestingly, the threat actor using the alias, ‘Tanaka’ on Blackforums[.]net accused Ransom.vc of unethical activity. It is possible the new incident with Sony may also involve several conflicting hacktivist groups, which have splintered off to form competing ransomware groups that target large organizations.
Currently, Tanaka‘s profile includes the following information with a reference to the ‘threatsec’ Jabber (OTR encrypted IM) handle. A threat actor with the same alias can also be found on Blackforums[].net.
The link in the bio field of threatsec‘s profile leads to a channel containing postings from Ransomed.vc Support:
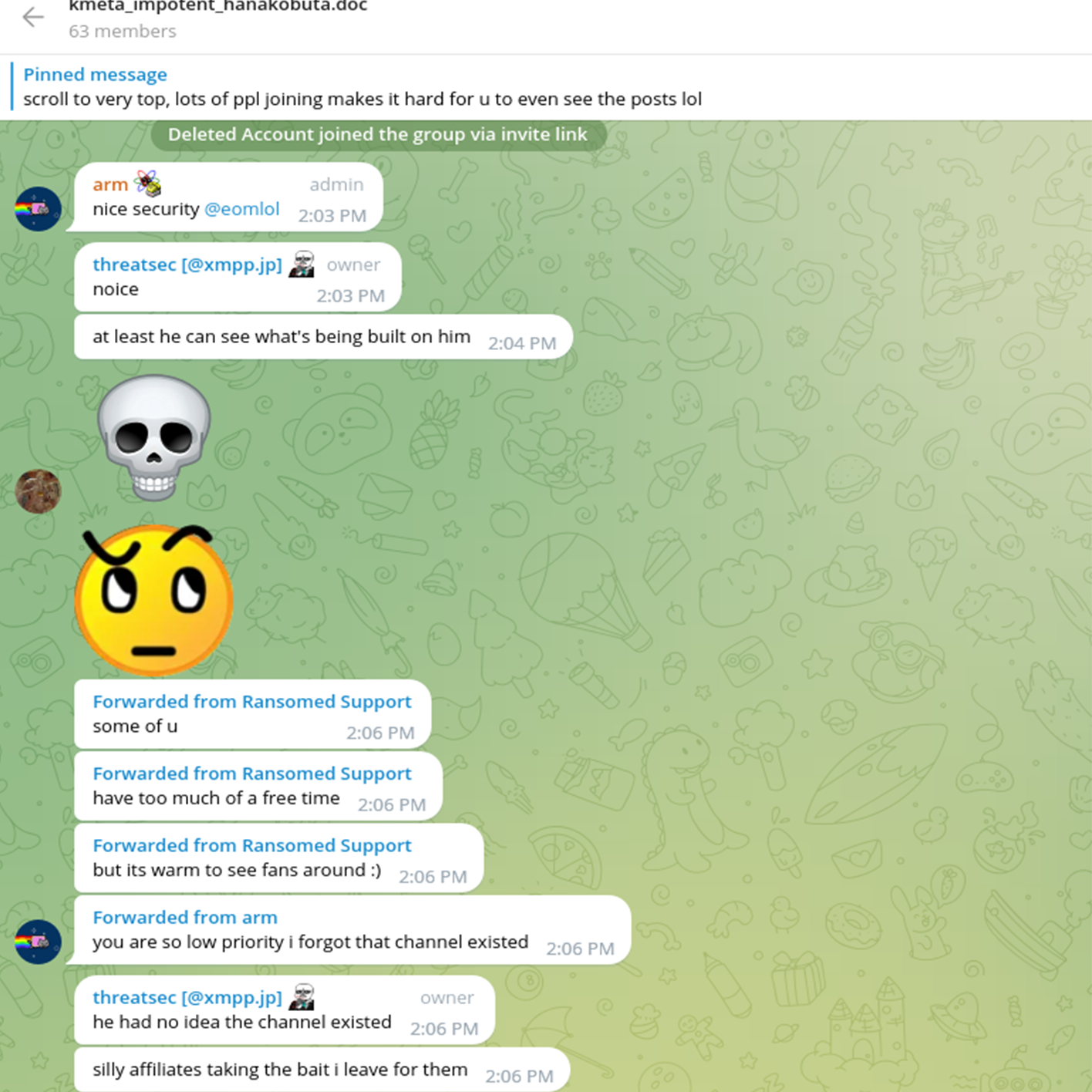
Notably, the actor threatsec is known to operate a Telegram channel that publishes leaked data. Promoting himself as a hacktivist, this threat actor published multiple data breaches from Brazil, Ethiopia, India, Malaysia, Russia, and other countries.
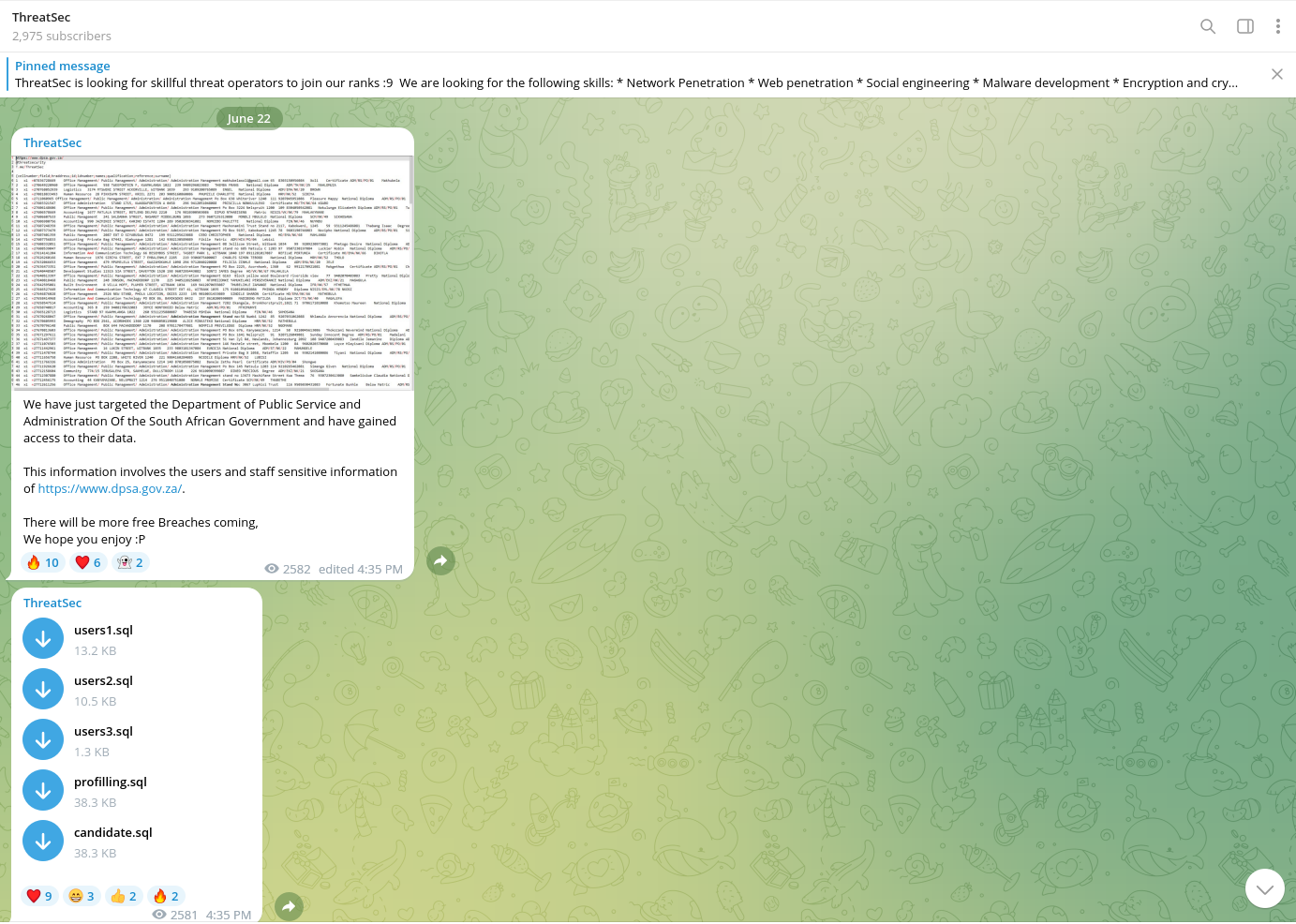
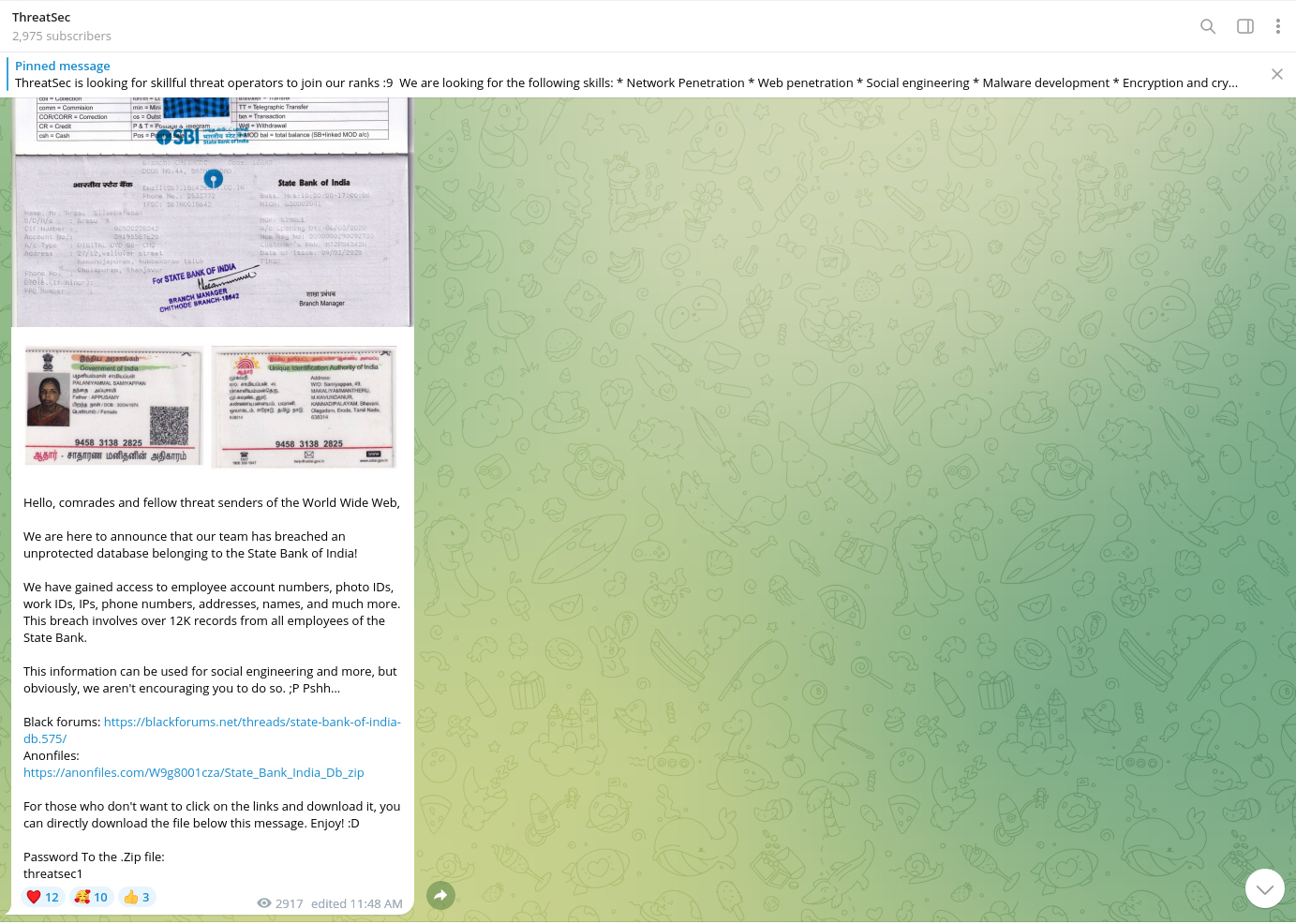
This threat actor is also involved in DDOS activity and collaborates with other actors such as HydraC2, a high-reputation underground DDOS vendor.
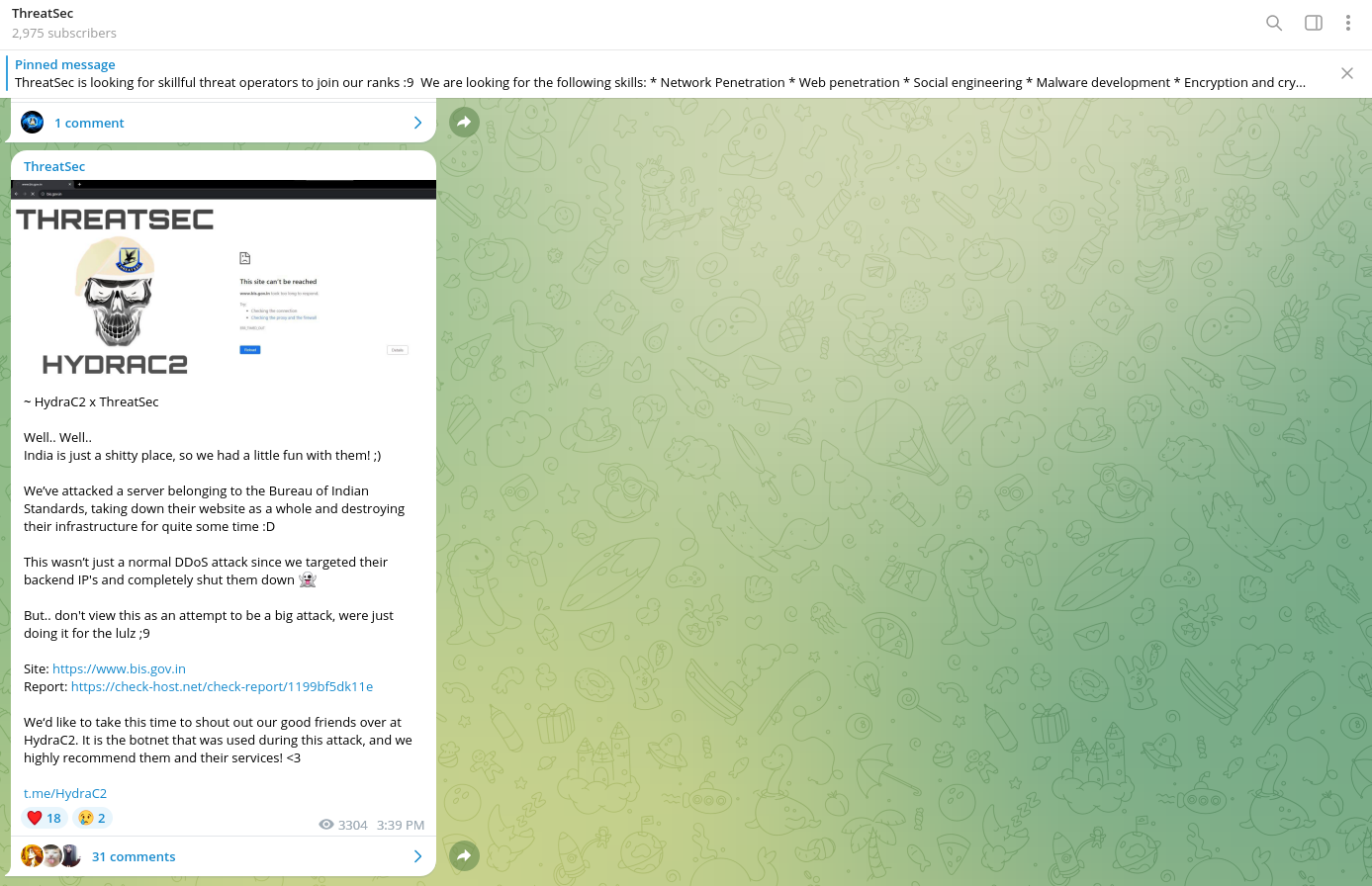
Interestingly, HydraC2 has multiple postings in English and Chinese that offer a description of their DDOS services.
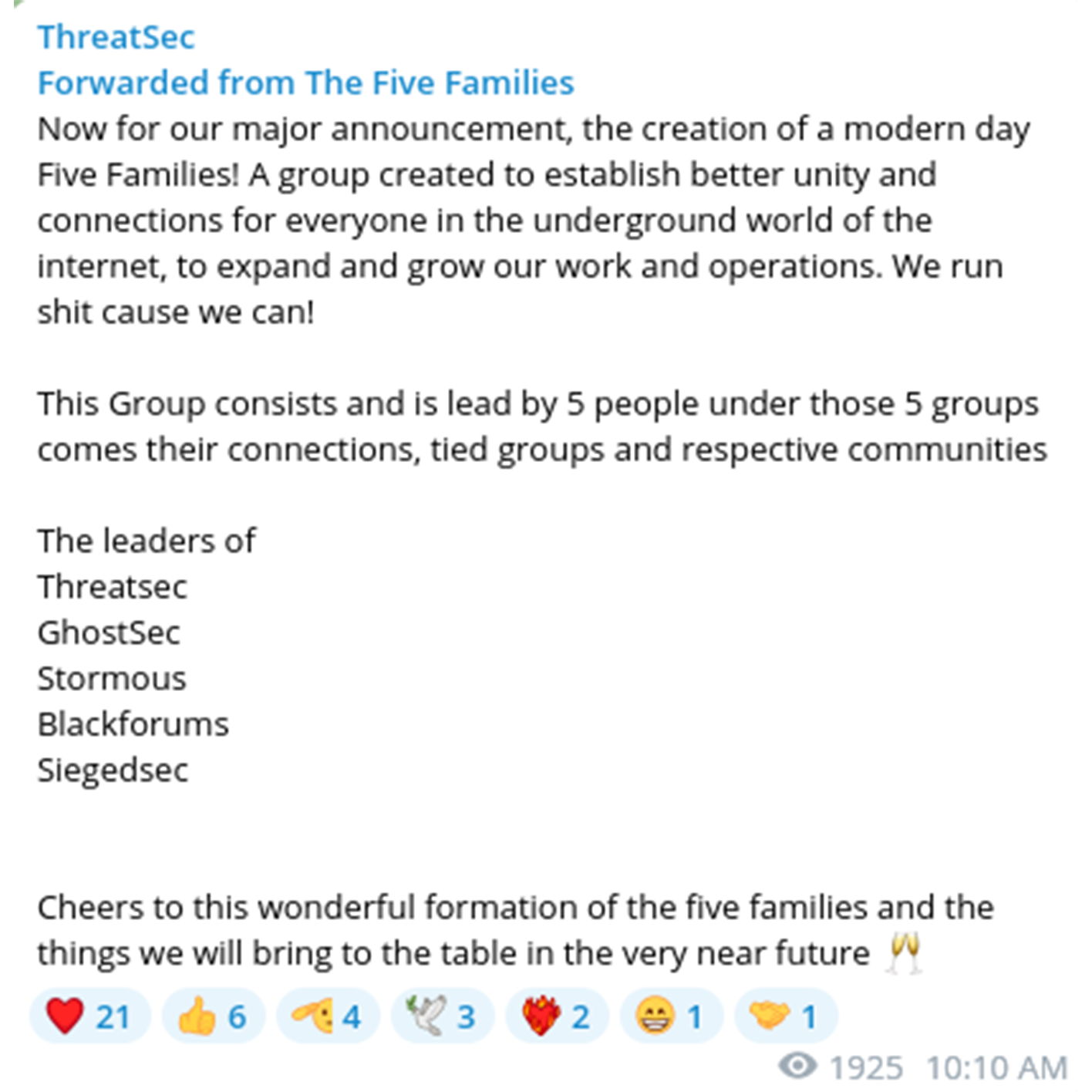
August 28, 2023 - HydraC2 announced the creation of a so called "Five Families" alliance, a coalition of several groups that have been attributed to various large-scale cyberattacks and data leaks. Collectively, their activities range from attacks on various governments to the publication of sensitive data from enterprises. For example, ‘family member’ SiegedSec previously publsihed data stolen from NATO’s Communities of Interest (COI) portal.
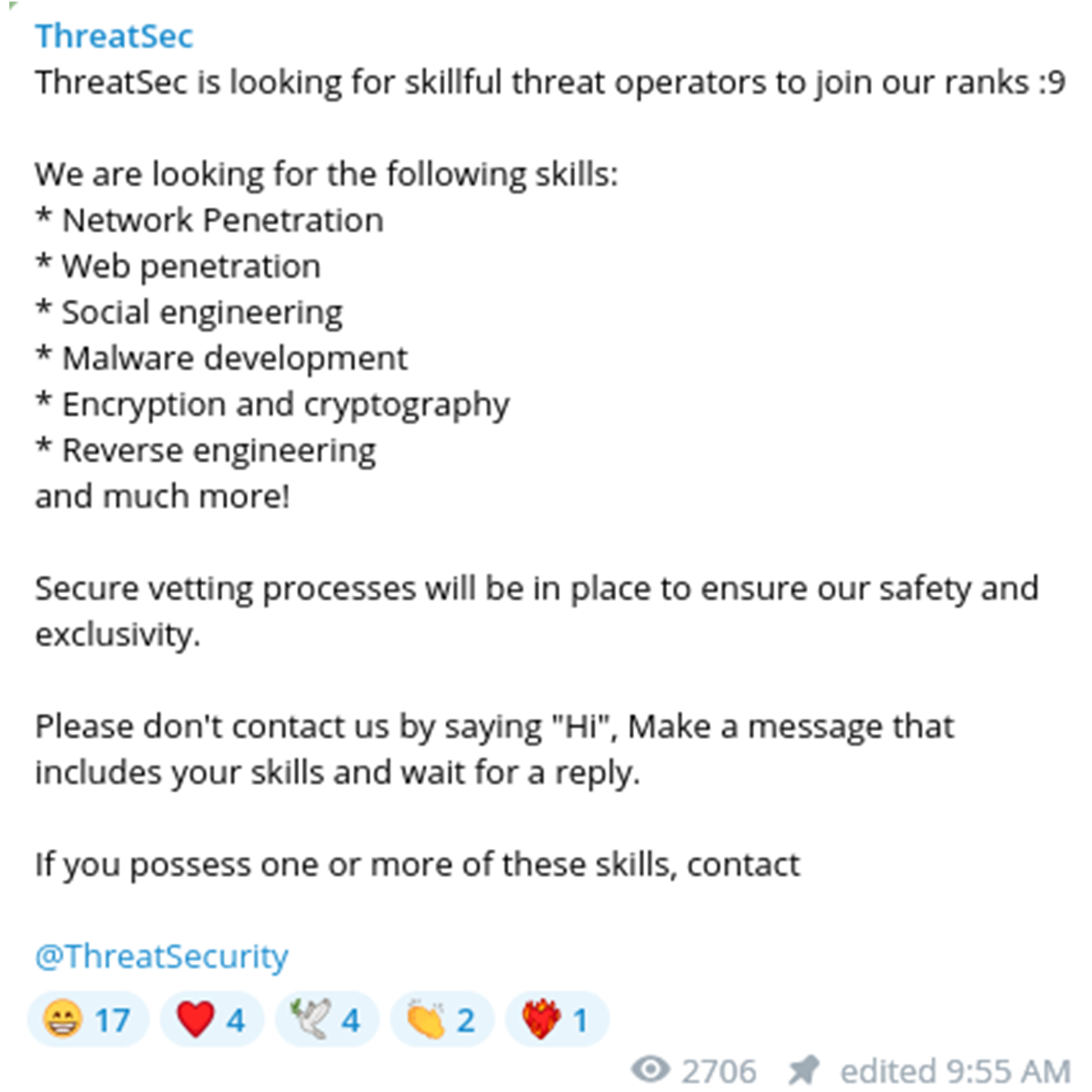
Similar to ransomware groups looking for affiliates, the actor is looking for "skillful operators" to join their team. It is possible this type of recruitment can lead to the involvement of further ransomware activity by acquiring access from independent access brokers and hacktivists.
Youth Movement
The rise of Ransomed.vc also illustrates a rapidly evolving demographic trend that is reshaping the cybercriminal landscape: the emergence of Generation Z. Colloquially referred to as zoomers, Gen Z is the generation born between 1996 and 2010, according to consultants McKinsey & Company.
This generation are true digital natives having grown up in an era when the Internet had already been widely adopted by society. However, the more deviant-minded technophiles of this generational spectrum are increasingly carving out their niche in the world of cybercrime. These anti-social, yet tech-savvy teens and early-20-somethings are staging increasingly brazen ransomware attacks, swatting campaigns, crowd-sourced violence, cryptocurrency theft, sim-swapping account takeovers, carding frauds, and DDoS disruptions.
Most recently, this emerging cybercriminal demographic made headlines with the devastating hacks of MGM Resorts and Caesars Entertainment, two of the largest gambling conglomerates in the world. While Caesars reportedly paid a ransom in the range of $15 million-to-$30 million to avoid business disruption, MGM elected to play hardball.
The net result is that MGM has experienced operational chaos, with guest check-ins delayed for hours if not days, while the company was losing $8.4 million a day at one point. All told, MGM has lost at least $80 million in revenue at this time of this writing. More astounding, the primary intrusion vector for the MGM attack was a social engineering ruse that tricked a helpdesk employee into giving threat actors an admin’s login credentials. Granted, it is likely the admin was sim-swapped prior to the social engineering attack on the helpdesk employee.
In the press, the MGM and Caesars attacks were attributed to an ALPHV ransomware affiliate that has been dubbed "Scattered Spider" by various threat researchers. Scattered Spider is believed to be a gang of 17-22 year-olds that reside primarily in Western countries. However, other researchers have said that the Scattered Spider group designation is inaccurate, "as it lumps the activities of multiple disparate and sometimes rival groups” from within a unique cybercriminal ecosystem into one entity.
This specific Gen Z cybercrime ecosystem has been called “the Comm” by the Federal Bureau of Investigation, according to an FBI affidavit filed in May. A Vice story on the Comm affidavit published last May said the group “uses Discord and Telegram to engage in a wide spread of criminal acts, according to the complaint. These include SIM swapping, stealing cryptocurrency, swatting, and “corporate intrusions.”
More recent reporting in Cyberscoop noted that young people within one of the Comm’s “subgroups, known as “Star Fraud,” were likely involved in the recent high-profile Caesars Entertainment and MGM Resorts extortion attacks.” A key vanguard of this cybercriminal youth movement, and one with several members who emerged from the Comm ecosystem, per Cyberscoop, is Lapsus$.
Lapsus$ is widely regarded as a pioneer of this youth movement, emerging sometime in in late 2021, according to the Cybersecurity & Infrastructure Security Agency’s (CISA) Cyber Safety Review Board. Lapsus$ initially made waves as a “loosely organized” and globally active, extortion-focused cyber threat actor group” that “attacked dozens of well-known companies and government agencies around the world,” according to the CSRB.
The group’s first headline-grabbing campaign was the ransomware attack against the Brazilian Ministry of Health in December 2021. The CSRB said that this threat actor gained further infamy as it “penetrated corporate networks, stole source code, demanded payments while rarely following up, lodged political messages in shadowy online forums, and swiftly moved on to its next targets.”
Lapsus$ has also demonstrated a “special talent for social engineering, luring a target’s employees to essentially open the gates to the corporate network,” according to the CSRB. The Board also noted Lapsus$’ use of “its public Telegram channel to discuss its operations, targets, and successes, and even to communicate with and extort its targets.”
Some of this group’s more notable cyberattacks include Nvidia, Samsung, Microsoft, Vodafone, Rockstar Games, Uber, and Okta. Initially, most Lapsus$ members were "based mainly in the United Kingdom (U.K.) and Brazil,” with eight to 10 known members as of April 2022, said the CSRB. In March 2022, the London Police arrested seven alleged Lapsus$ members, all of whom were teenagers.
On August 24, 2023, a jury in London found autistic, 18-year-old Lapsus$ member Arion Kurtaj guilty of leaking clips “of the unreleased Grand Theft Auto 6 game while on bail in a Travelodge hotel,” according to the BBC. The BBC also reported that another "17-year-old who is also autistic was convicted for his involvement in the activities of the Lapsus$ gang but cannot be named because of his age.“
According to the CSRB, the “FBI reported that it last observed Lapsus$ activity in September 2022 and assessed that the decrease in activity was likely due to the arrests of Lapsus$ members.” Nevertheless, the key threat presented by the rise of the young, globally dispersed network of anti-social technophiles that comprise the Comm ecosystem is that they are increasingly working with professional ransomware syndicates like ALPHV.
Cyberscoop notes that the role of the Comm in “inducting these young hackers into a life of crime is akin to the well-documented issue of how toxic online communities can radicalize children.” In this backdrop, the CSRB “recommends the advancement of “whole-of-society” programs and mechanisms to prevent juvenile cybercrime.”
To this end, certain proposals floated by the CSRB include increased congressional funding for juvenile cybercrime prevention, “fostering interruption and redirection programs,” and encouraging state and federal law enforcement to devise new ways to reduce “criminal incentives.”
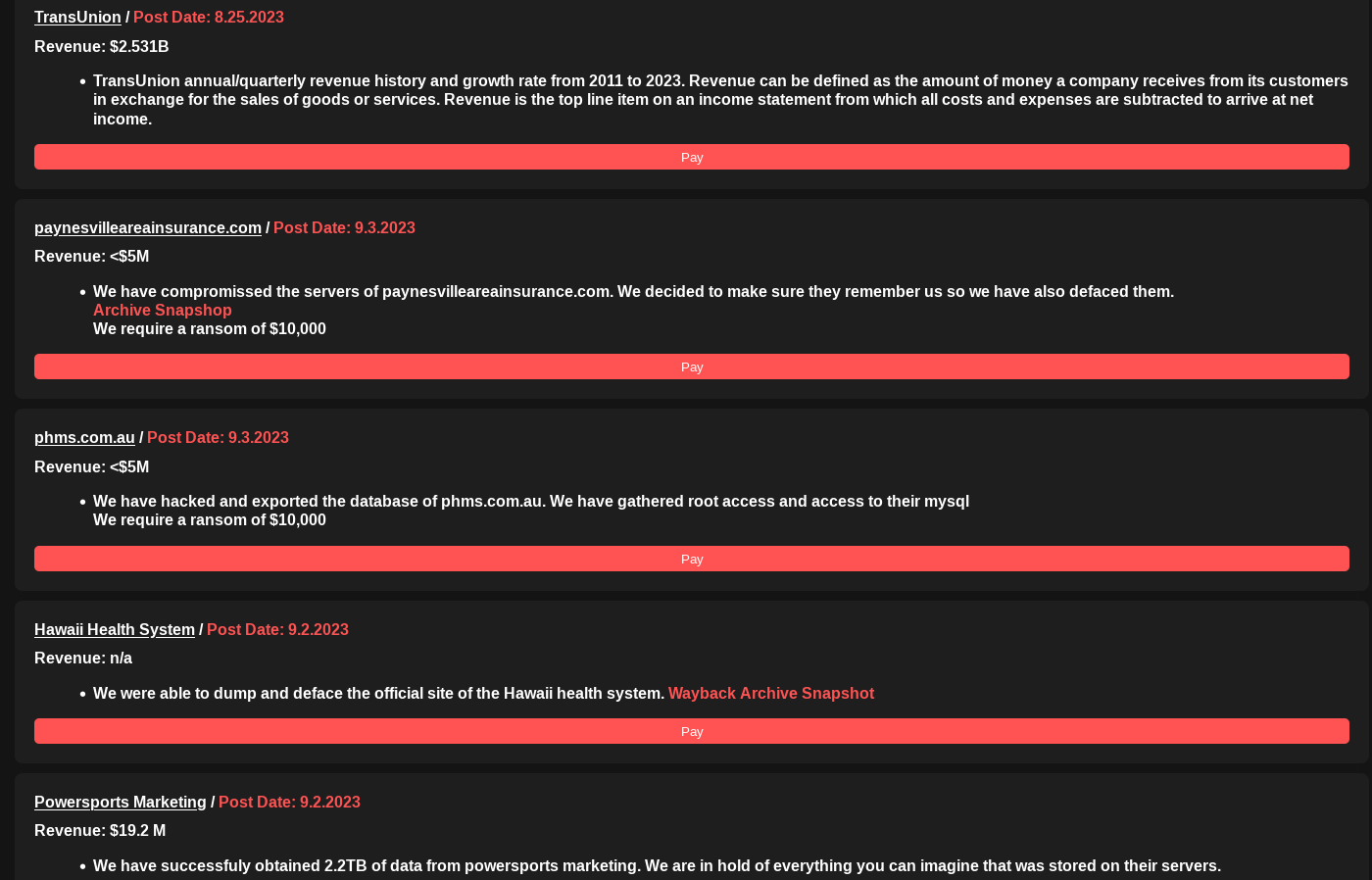
Significant Datasets up Their Sleeve
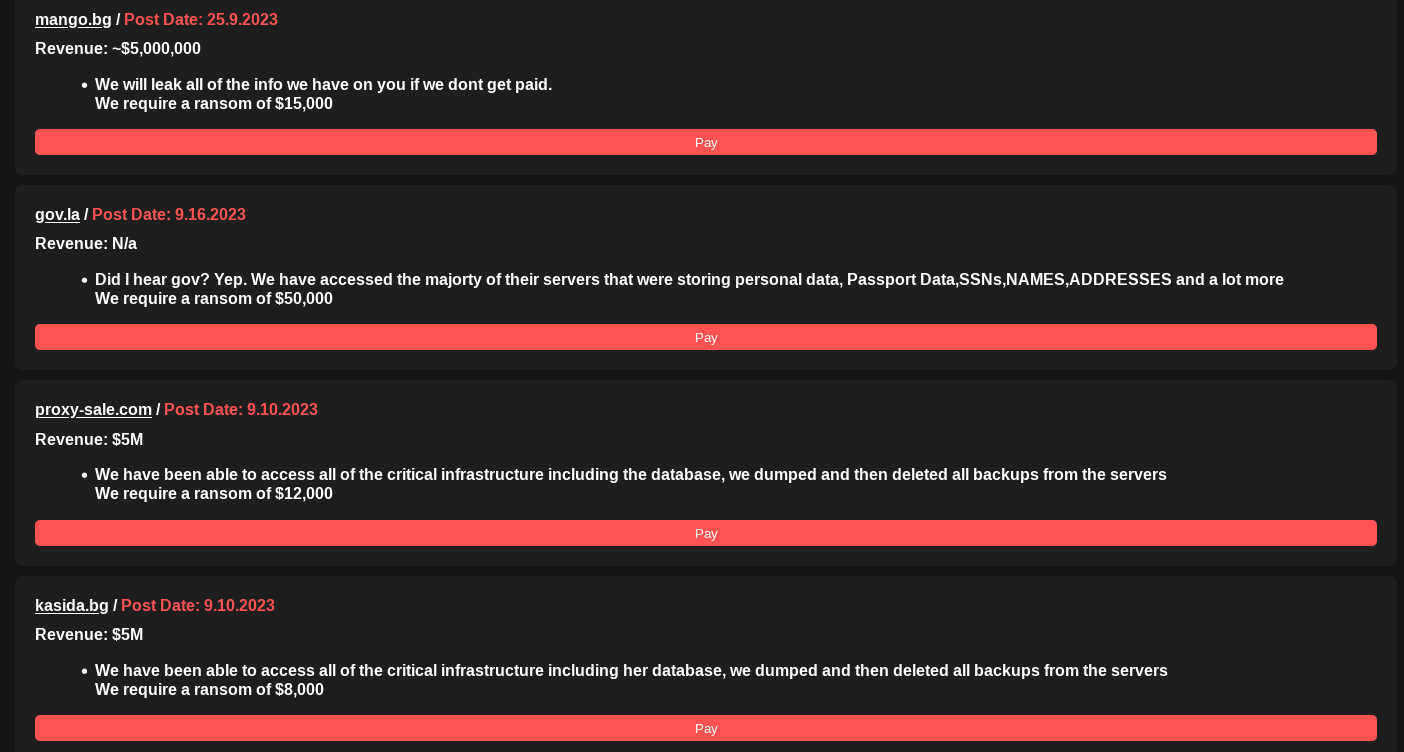
While the cybersecurity community tracks the latest updates from Ransomed.vc‘s malicious Japan campaign, defenders should be aware that the group also claims to have possession of meaningful datasets that they have yet to publish. The list of announced victims includes several U.S.-based corporations and government resources, and organizations based in the UK and European Union (EU).
The Return of "Big Game Hunting"
Beyond the $5-million annual revenue threshold required by Ransomed.vc to make their attacks worthwhile, ‘big game hunting’ is coming back into fashion for the broader ransomware community. According to the new Department of Homeland Security 2024 Homeland Threat Assessment, the number of known ransomware attacks in the U.S. increased by 47% between January 2020 and December 2022. Ransomware attackers extorted at least $449.1 million globally during the first half of 2023 and are projected to record their second-most profitable year ever.
This outlook is due to the reemergent popularity of ‘big game hunting,’ or the targeting of large organizations, in the cybercriminal underground. However, cybercriminal campaigns against smaller organizations also persist. Overall,
ransomware actors continue to attack a wide spectrum of victims, while hyper-targeting entities that they assess, through victim reconnaissance and research, as the most likely to pay a ransom.
In addition to disrupting the business operations of targeted victims, financially motivated cybercriminal actors will continue to impose significant financial costs on the global economy this year.
Resecurity continues to track the activity of Ransomed.vc through proactive surveillance of the Dark Web and the continuous collection of actionable threat intelligence from a variety of sources.
Conclusion
- Resecurity expects that threat actors will target enterprises from different market verticals (fintech, telecommunications, oil & gas, media) using stolen data with the goal of extortion, while leveraging similar tactics as Ransomed.vc.
- Hacktivists will increasingly reinvent themselves as ransomware groups to monetize their cyber offensive skillset and leverage stolen data for profit. Emerging hacktivist alliances like the “Five Families” consortium being pursued by the union of Stormous, GhostSec, SeigedSec, ThreatSec, and Blackforums may inflict increased damage via the force-multiplying effect of their collaboration;
- Similar to Ransomed.vc, the above groups may be looking to recruit new members to scale their operations and for later operationalization as affiliates for future ransomware projects;
- Ransomed.vc uses traditional and legally-conscious pressure tactics to motivate victim organizations to pay ransom demands. To coerce victim payments, these threat actor weaponize creative narratives, citing GDPR regulations and possible fines that can exceed ransom payout costs in certain cases.
References
Clearnet:
ransomed[.]vc
TOR Network:
f6amq3izzsgtna4vw24rpyhy3ofwazlgex2zqdssavevvkklmtudxjad[.]onion
Telegram IM:
https://t.me/RansomedSupport
TOX IM:
192D52C7C18F3D2693ED2453E64C53EC0CCF0255AB2291F019B65BA84442B313C410DE132E59
Known BTC wallets:
bc1qg07auf7efld3edzyjs2wqztaky39xjdyk0uprj
bc1qqc7nla44te4wxyvf9j7zxtc5q296sxn94k6v00
bc1qwv6hg860mf9g0at8fe64nsswa2pa73vgd9tvj5
bc1qqc7nla44te4wxyvf9j7zxtc5q296sxn94k6v00

