Smishing Triad Is Targeting India To Steal Personal and Payment Data at Scale
Fraud Intelligence

Intro
Internet users from India have reported a spike of fraudulent smishing activity impersonating India Post, an Indian government-operated postal system in India, and the trade name of the Department of Post under the Ministry of Communications.
In June, the Press Information Bureau (PIB), an official agency of the Government of India under the Ministry of Information and Broadcasting, has warned users about the increasing smishing activity and urged citizens to remain vigilant and cautious towards any suspicious messages claiming to be from postal services such as India Post, which could be impersonated by fraudsters.
India's massive population (over 1.417 billion) and economy make it a prime target for cybercriminals and fraudsters. The estimated 1 billion smartphone users in India by 2023 will make them a lucrative target for malicious parties. As a result, consumers can expect to be targeted more frequently by foreign cyber threat actors. To carry out large-scale malicious activity, threat actors will focus on smishing campaigns aimed at stealing digital identities.
Aggregating stolen data in large volumes can be an excellent catalyst for cyberespionage. Nation-state actors, in particular, would be highly interested in collecting such information, potentially masking their activities under the guise of traditional cybercrime. The situation with Smishing Triad is complex, as from one side the group uses smishing kits to steal credit card information while also distributing malicious code against the energy sector and impersonating major Fortune 100 brands, which have been used in targeted phishing attacks, based on recently uncovered network infrastructure. Moreover, smishing activity will be extremely valuable for both cybercriminals and nation-state actors in the long run, as both will seek to collect digital identity information on a massive scale.
Background
Resecurity has identified a new campaign by the Smishing Triad, which reportedly started amplifying around July 8, 2024, based on multiple victim reports and the detection of new infrastructure set up in the days preceding. This month, the group has vastly expanded its attack footprint in India, preparing for the campaign in advance. The actors registered domain names impersonating the India Post around June, but were not actively using them, likely preparing for a large-scale activity, which became visible by July. The goal of this campaign is to steal massive amounts of personal identifiable information (PII) and payment data.
Previous episodes of Smishing Triad activity have been described by Resecurity, earlier targeting other geographies, including the U.S., U.K., EU, UAE, KSA, and the most recently Pakistan:
- Smishing Triad Is Targeting Pakistan To Defraud Banking Customers At Scale
https://www.resecurity.com/blog/article/smishing-triad-is-targeting-pakistan-to-defraud-banking-cust...
- Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season
https://www.resecurity.com/blog/article/cybercriminals-impersonate-uae-federal-authority-for-identit...
- Smishing Triad Impersonates Emirates Post to Target UAE Citizens
https://www.resecurity.com/blog/article/Smishing-Triad-Impersonates-Emirates-Post-Target-UAE-Citizen...
- Smishing Triad Targeted USPS and US Citizens for Data Theft
https://www.resecurity.com/blog/article/smishing-triad-targeted-usps-and-us-citizens-for-data-theft
Timeline
Threat actors have registered multiple domains impersonating India Post. The actors use geographical filtering and check the User-Agent if the victim is accessing the smishing pages from a mobile device, under Apple iOS or Android.
July 8:
inddiapost[.]top (Cloudflare)
indiapostyt[.]vip (Tencent)
July 9:
indiapostos-in[.]com (Cloudflare)
huangcn[.]sbs (Alibaba)
The majority of fraudulent domain names have been identified in .top, .vip and .sbs domain zones. Interestingly, the .sbs zone is relatively exotic and particularly notable as it stands for 'side by side'. The actors likely exploited weaknesses in abuse management, enabling them to register domain names for fraudulent purposes.
Notably, the domains have been registered via NameSilo and Gname specifically, a known pattern used by the Smishing Triad in previous campaigns. One of the most notable domains - indiapostyt[.]vip resolves to IP 119.28.68.187 (AS 132203 / Tencent) having over 200 fraudulent domains mapped to it with registration date starting June 11, 2024:
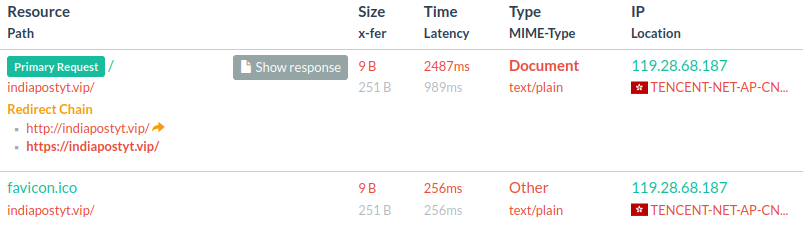
The majority of domains mapped to the identified Chinese IP address are impersonating India Post along with some other popular brands and online services including Airbnb (airpnl[.]com). The full list of Indicators of Compromise (IOCs) is provided at the end of this threat research in the appendix.
Example:
indiapostil[.]top
indiapostok[.]top
indiapostao[.]vip
indiapostyy[.]vip
indiapostzq[.]vip
indiapostit[.]vip
indiapostec[.]vip
indiapostsf[.]vip
indiapostzu[.]vip
indiapostkl[.]vip
indiapostpi[.]vip
indiapostqo[.]vip
indiapostyl[.]vip
indiapostto[.]vip
indiapostwf[.]vip
indiapostnc[.]vip
indiapostvm[.]vip
indiapostyz[.]vip
indiapostdk[.]vip
indiaposttb[.]vip
indiapostsp[.]vip
indiapostbj[.]vip
indiapostyt[.]vip
indiapostxn[.]vip
indiapostqi[.]vip
indiapostim[.]vip
indiapostpt[.]vip
indiapostvd[.]vip
Another notable domain name with fake landing page of India Post is huangcn[.]sbs resolving to 8.211.194.9 (Alibaba). This host has an extensive history of malicious activity, including spreading malware through oil & gas/energy-themed attachments. And reference to "singlipost[.]top" domain name, which was registered to impersonate Singpost, a major postal service provider in Singapore.
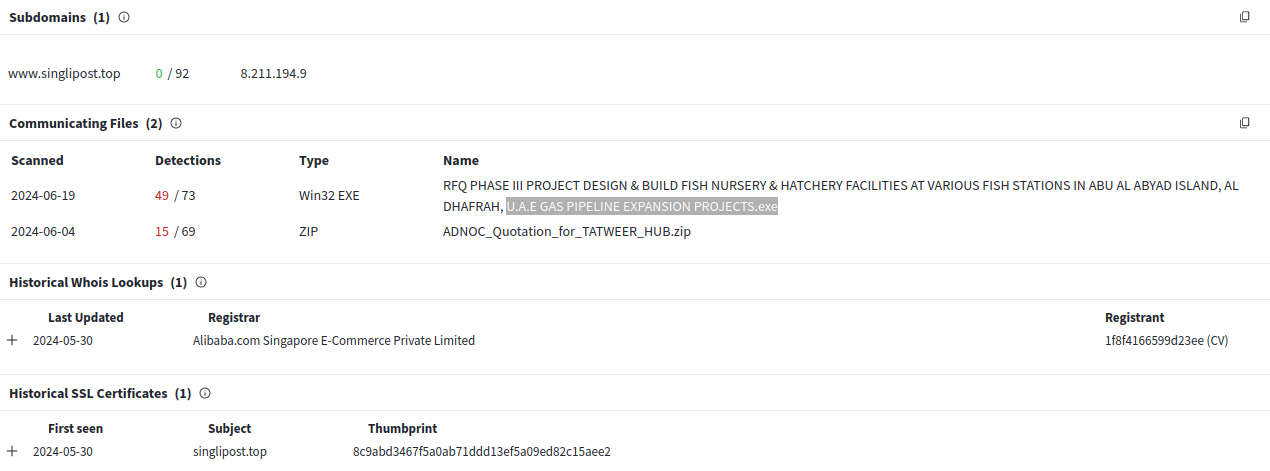
Domains related to attacks against Singapore postal provider were registered around May 30, 2024 amd mapped to the same IP prior to this campaign targeting India:
singillpost[.]top
singilipost[.]top
singililpost[.]top
sinlogilopost[.]top
sinlgilopost[.]top
singpilost[.]top
singiqlpostl[.]top
singpiost[.]top
singilpostl[.]top
singqlpostl[.]top
singilpost[.]top
singlilpost[.]top
singlipost[.]top
singliipost[.]top
Concurrently, the actors registered a group of domains impersonating La Poste, a major postal service provider in France:
lapiostie[.]top
laipostie[.]top
lapposstie[.]top
liapiostie[.]top
lapposstiee[.]top
laaposstiee[.]top
lapiostiee[.]top
lapiosstiee[.]top
lapositie[.]top
laapostee[.]top
Besides this, domain names impersonating other major postal providers were found to have been registered earlier in April and May 2024:
- ParcelHub and Pos Malaysia
parcelhu[.]buzz
postmyy[.]lat
- J&T Express
jtexpiessgroup[.]top
- NZ Post
nzipost[.]sbs
- Czech Post
ceskkpoostaa[.]beauty
ceskkppostaa[.]xyz
ceskkpoostaa[.]monster
ceskkpoostaa[.]pics
ceskkppostaa[.]sbs
- Latvia Post
posts-lv[.]sbs
- DHL
dhhlllde[.]sbs
dhhlllde[.]cfd
Besides postal providers, several domains impersonating major Fortune 100 organizations were identified, including but not limited to:
- McKinsey & Company
mckinseya[.]sbs
mckinseya[.]xyz
- Visa
vlsia[.]xyz
vlsia[.]buzz
vlsia[.]icu
vlsia[.]top
vlsia[.]sbs
vlsia[.]icu
- Citi
citti[.]top
These details may confirm the global scale of Smishing Triad activity and the interconnection, by impersonated organizations, to previous episodes of their activity reported by Resecurity.
Modus Operandi
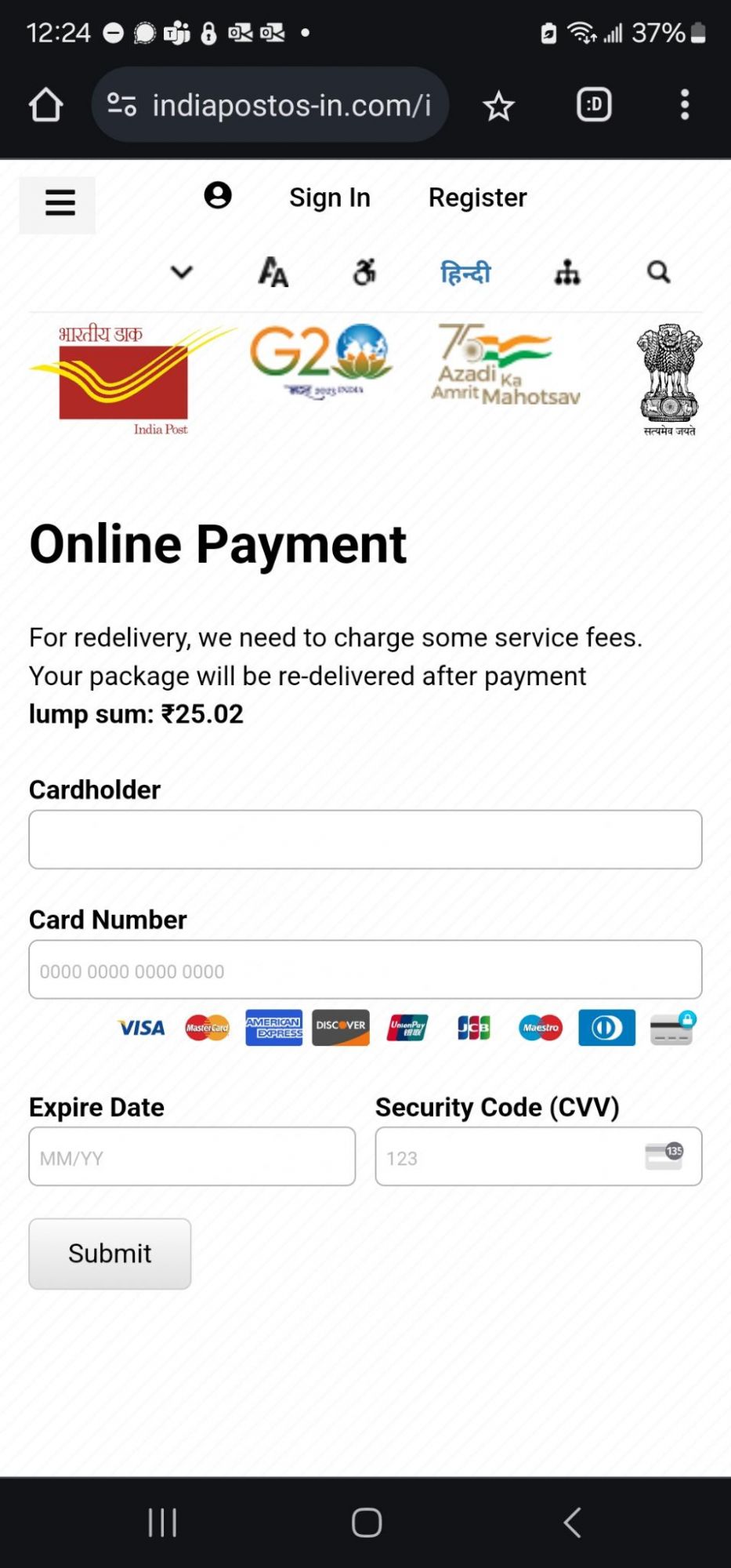
The misleading SMS falsely asserts that a package is awaiting delivery at a warehouse and alleges multiple failed delivery attempts due to incomplete address information. It directs recipients to click on a provided link to update their details, promising new delivery attempt within 24 hours upon completion. However, the link leads to a suspicious website that could potentially compromise personal information.
Some of these domain names still remain active and online delivering fraudulent content impersonating government branding:
https://indiapostos-in[.]com/in/
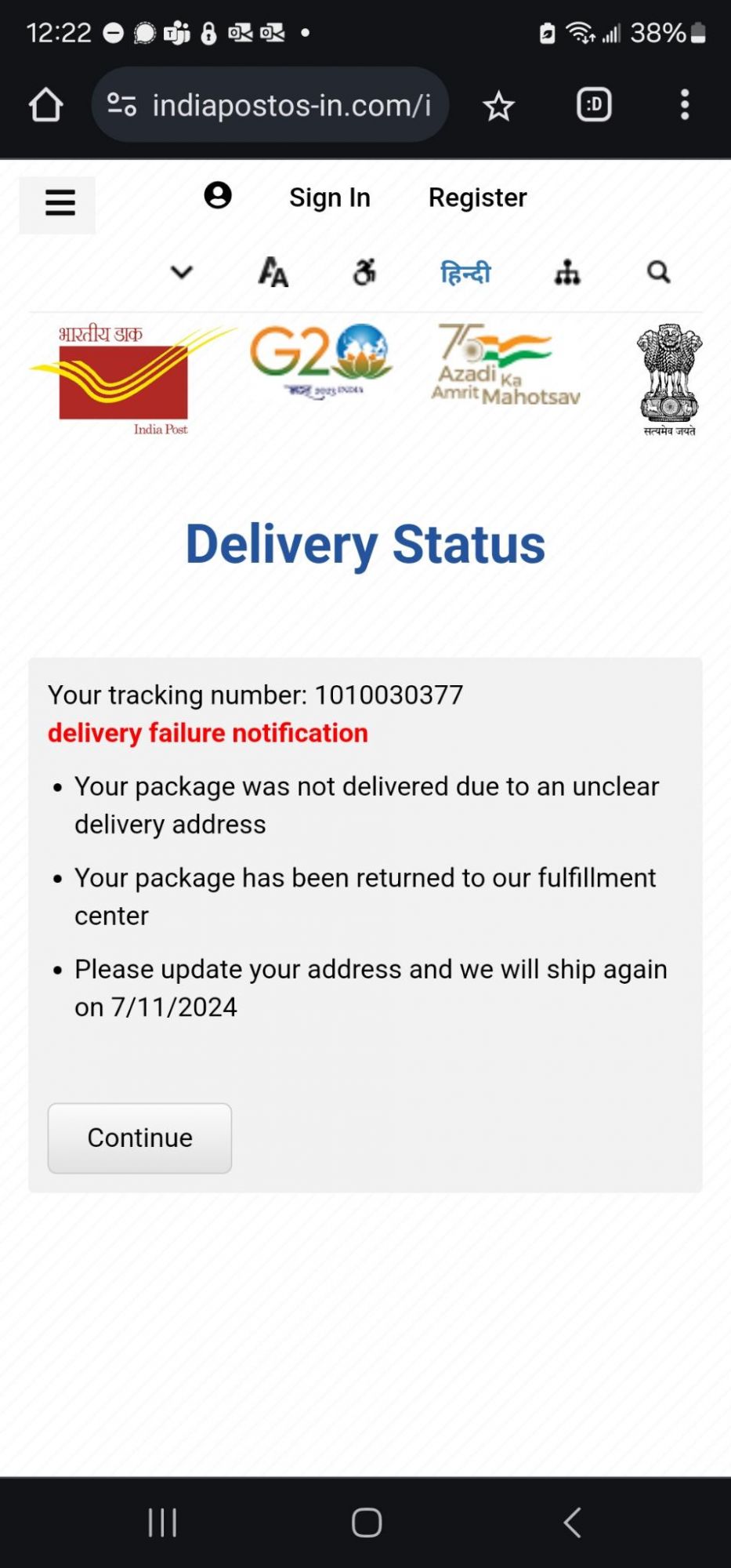
The victim will be asked to provide detailed information including personal details, which will later be used by fraudsters along with payment data.
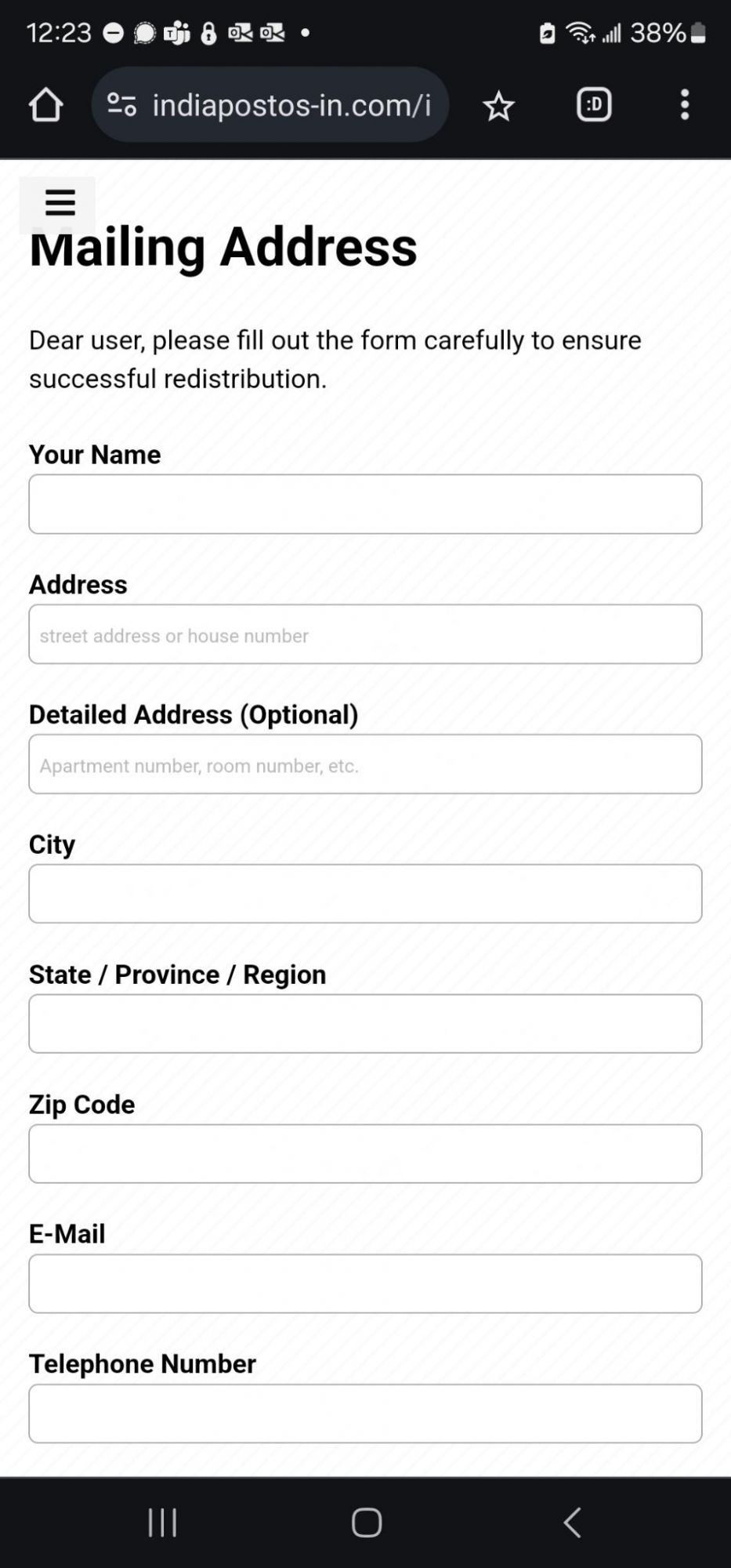
The fraudsters ask the victim to provide credit card information to arrange a small payment. In fact, this tactic is used to steal payment data:
The actors are using compromised and purposefully registered iCloud accounts to send fraudulent iMessages with smishing URLs. The number of such accounts used for smishing content delivery can range from hundreds to thousands. These accounts could be acquired on the Dark Web from underground brokers.
List of senders:
- jdxfydd@gmail[.]com
- bzejamesking679@gmail[.]com
- kytidicoguh@gmail[.]com
- chermonahscales2980545@gmail[.]com
The full list of identified senders, along with additional information about this campaign, has been provided to law enforcement agencies.
Mitigation Measures
Press Information Bureau (PIB), an official agency of the Government of India under Ministry of Information and Broadcasting, has warned users to not click on such malicious links. Additionally, they also clarified that “India Post never sends such messages asking for updating addresses for delivering articles.”
To protect yourself from such scams, users need to verify the authenticity of the sender by checking the address of the email, phone number of the message or call or by any other means possible.
In case you are skeptical of any emails, messages and calls, report it to authorities like PIB Fact Check or cyber police (1930 or visit cybercrime.gov.in). Smartphone users also need to make sure that their devices are updated with the latest software.
Indicators of Compromise
Resecurity collected the most recent IOCs from the Smishing Triad campaign targeting India, with the goal of sharing them with the cybersecurity community for awareness and further risk mitigation.
inddiapost[.]top
indiapostyt[.]vip
indiapostos-in[.]com
indiapostil[.]top
indiapostok[.]top
indiapostao[.]vip
indiapostyy[.]vip
indiapostzq[.]vip
indiapostit[.]vip
indiapostec[.]vip
indiapostsf[.]vip
indiapostzu[.]vip
indiapostkl[.]vip
indiapostpi[.]vip
indiapostqo[.]vip
indiapostyl[.]vip
indiapostto[.]vip
indiapostwf[.]vip
indiapostnc[.]vip
indiapostvm[.]vip
indiapostyz[.]vip
indiapostdk[.]vip
indiaposttb[.]vip
indiapostsp[.]vip
indiapostbj[.]vip
indiapostyt[.]vip
indiapostxn[.]vip
indiapostqi[.]vip
indiapostim[.]vip
indiapostpt[.]vip
indiapostvd[.]vip
indiapostej[.]vip
indiapostgw[.]vip
indiapostpy[.]vip
indiapostzy[.]vip
indiapostag[.]vip
indiapostxw[.]vip
indiapostfy[.]vip
indiapostgf[.]vip
indiapostha[.]vip
indiaposton[.]vip
indiapostwk[.]vip
indiapostsl[.]vip
indiapostrf[.]vip
indiapostgm[.]vip
indiapostmh[.]vip
indiapostrc[.]top
indiapostjt[.]vip
indiapostks[.]vip
indiapostgx[.]vip
indiapostwv[.]vip
indiapostbx[.]vip
indiapostvt[.]vip
indiapostnh[.]vip
indiapostpd[.]vip
indiapostvu[.]vip
indiapostiu[.]vip
indiapostyx[.]vip
indiapostnw[.]vip
indiaposttj[.]vip
indiapostcb[.]vip
indiapostlk[.]vip
indiapostnm[.]vip
indiapostaw[.]vip
indiapostmf[.]vip
indiapostoj[.]vip
indiapostxc[.]vip
indiaposttn[.]vip
indiapostds[.]vip
indiapostty[.]vip
indiapostop[.]vip
indiaposter[.]vip
indiapostui[.]vip
indiapostjh[.]vip
indiapostew[.]vip
indiapostxp[.]vip
indiapostbe[.]vip
indiapostss[.]vip
indiapostaq[.]vip
indiapostqv[.]vip
indiapostkz[.]vip
indiapostgy[.]vip
indiapostrl[.]vip
indiapostse[.]vip
indiapostsq[.]vip
indiapostvy[.]vip
indiapostbs[.]vip
indiapostgt[.]vip
indiapostyr[.]vip
indiapostut[.]vip
indiapostzp[.]top
indiapostjf[.]vip
indiapostcs[.]vip
indiapostkm[.]vip
bhehua[.]com
indiapostjd[.]vip
indiapostog[.]vip
indiapostpj[.]vip
indiapostwg[.]vip
indiapostqh[.]vip
indiapostfr[.]vip
indiapostdd[.]vip
indiapostqf[.]vip
indiapostdq[.]top
indiapostqs[.]vip
indiapostbm[.]vip
indiapostlt[.]vip
indiapostol[.]vip
indiapostwh[.]vip
indiapostmk[.]vip
indiapostlt[.]top
indiapostru[.]vip
indiapostiv[.]vip
indiapostur[.]vip
indiapostzd[.]vip
indiaposteg[.]vip
indiapostbv[.]vip
indiapostrq[.]top
indiapostlv[.]top
indiapostqr[.]top
indiapostwg[.]top
indiapostky[.]vip
indiapostmn[.]vip
indiapostjx[.]vip
indiapostdf[.]vip
indiapostvg[.]vip
indiapostzc[.]vip
indiapostqr[.]vip
indiapostlj[.]vip
indiapostap[.]vip
indiapostnr[.]vip
indiapostib[.]vip
indiapostgu[.]vip
indiapostpq[.]vip
indiaposteo[.]vip
indiapostxf[.]vip
indiapostwc[.]vip
indiapostht[.]vip
indiapostci[.]top
indiapostfw[.]top
indiaposttx[.]vip
indiapostek[.]vip
indiapostld[.]vip
indiapostzv[.]vip
indiapostjk[.]vip
indiapostjq[.]vip
indiapostph[.]vip
indiapostmz[.]vip
indiapostdv[.]vip
indiapostoi[.]vip
indiapostrc[.]vip
indiaposttg[.]vip
indiapostbz[.]vip
indiapostnt[.]vip
indiapostgi[.]vip
indiapostxz[.]vip
indiapostaz[.]vip
indiapostvx[.]vip
indiapostwq[.]vip
indiapostuf[.]vip
indiapostby[.]vip
indiapostoc[.]vip
indiaposthd[.]vip
indiapostxr[.]vip
indiapostqw[.]vip
indiapostmt[.]vip
indiapostvb[.]vip
indiapostjo[.]vip
indiapostkr[.]top
indiapostmk[.]top
indiapostyb[.]top
indiapostyw[.]top
indiapostne[.]vip
indiapostps[.]vip
indiapostjp[.]top
indiapostnx[.]top
indiapostos[.]top
indiapostzc[.]top
indiapostns[.]vip
indiapostmj[.]top
indiapostpy[.]top
indiapostub[.]top
indiaposthn[.]vip
indiapostwm[.]top
indiapostam[.]vip
indiapostlg[.]vip
indiapostes[.]vip
indiapostub[.]vip
indiapostfs[.]vip
indiapostir[.]vip
indiapostdo[.]vip
indiapostcp[.]vip
indiapostik[.]vip
indiapostqq[.]vip
indiapostax[.]vip
indiapostqb[.]vip
indiapostwe[.]vip
indiapostwp[.]vip
indiapostdt[.]vip
indiapostpm[.]vip
indiapostkx[.]vip
indiapostpo[.]vip
indiapostmr[.]vip
indiapostym[.]vip
indiapostmu[.]vip
indiapostiw[.]vip
indiapostxt[.]vip
indiapostbl[.]vip
indiapostjl[.]vip
indiapostei[.]vip
indiapostul[.]vip
indiapostny[.]vip
vkgwbr[.]com
indiapostfv[.]vip
indiapostnz[.]vip
indiapostfw[.]vip
indiapostfj[.]vip
indiapostux[.]vip
indiapostox[.]vip
indiapostdx[.]vip
indiapostbg[.]vip
indiapostrg[.]vip
indiapostfd[.]vip
indiaposthk[.]vip
indiapostah[.]top
indiapostwl[.]top
136476[.]com
khctv[.]com
airpnl[.]com
sapostml[.]top
sapostpf[.]top
sapostkn[.]top
sapostfw[.]top
sapostmn[.]top

