
Intro
Resecurity has identified a new activity of Smishing Triad, which has expanded its operations to Pakistan. The group's latest tactic involves sending malicious messages on behalf of Pakistan Post to customers of mobile carriers via iMessage and SMS. The goal is to steal their personal and financial information. The code and templates used by the attackers in this smishing kit are consistent with those observed in previous instances of Smishing Triad.
Previously, Resecurity described multiple episodes of Smishing Triad activity targeting online banking, e-commerce and payment systems customers in other geographies including USA, EU, UAE, KSA:
- Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season
https://www.resecurity.com/blog/article/cybercriminals-impersonate-uae-federal-authority-for-identit...
- Smishing Triad Impersonates Emirates Post to Target UAE Citizens
https://www.resecurity.com/blog/article/Smishing-Triad-Impersonates-Emirates-Post-Target-UAE-Citizen...
- Smishing Triad Targeted USPS and US Citizens for Data Theft
https://www.resecurity.com/blog/article/smishing-triad-targeted-usps-and-us-citizens-for-data-theft
Estimating the scale of threat actors' activities, our analysts believe they send between 50,000–100,000 messages daily. To achieve this, they leverage stolen databases acquired from the Dark Web, which contain sensitive personal data of citizens including phone numbers. Pakistan, with a population of over 235.8 million, has experienced multiple data breaches in the first half of 2024, compromising the personal identifiable information (PII) of citizens. These records are then processed at scale using automation tools for malicious purposes.
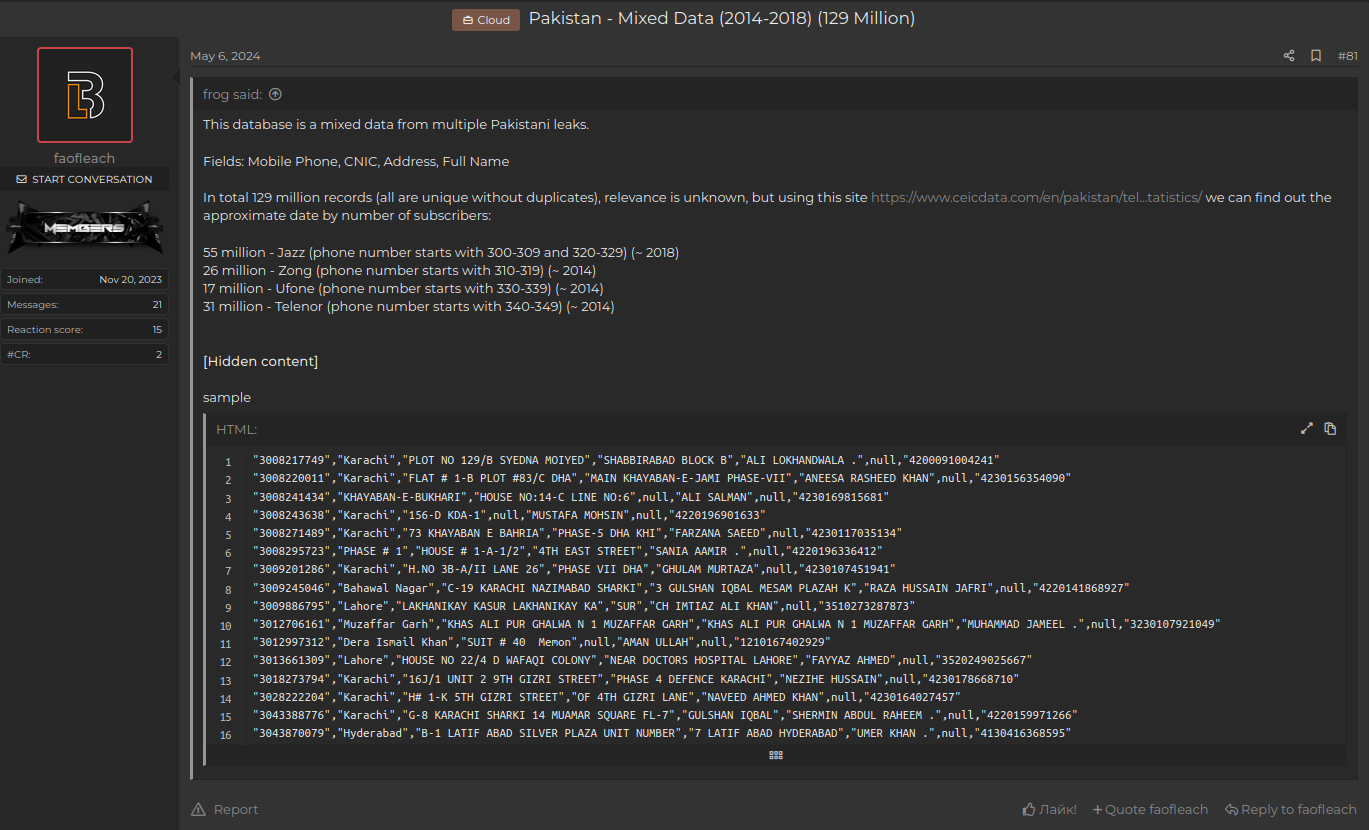
This warning sign serves as a reminder to telecom operators to enhance their fraud detection capabilities and proactively block such malicious activity to protect their customers. Resecurity has received multiple samples of smishing texts from a reported campaign, which was shared by customers of popular mobile carriers in Pakistan including Jazz/Warid, Zong, Telenor Pakistan, and Ufone.
Modus Operandi
The threat actors are using local phone numbers, making it appear to the end recipient as if they are receiving a text from a local postal office or a company attempting to reach out.
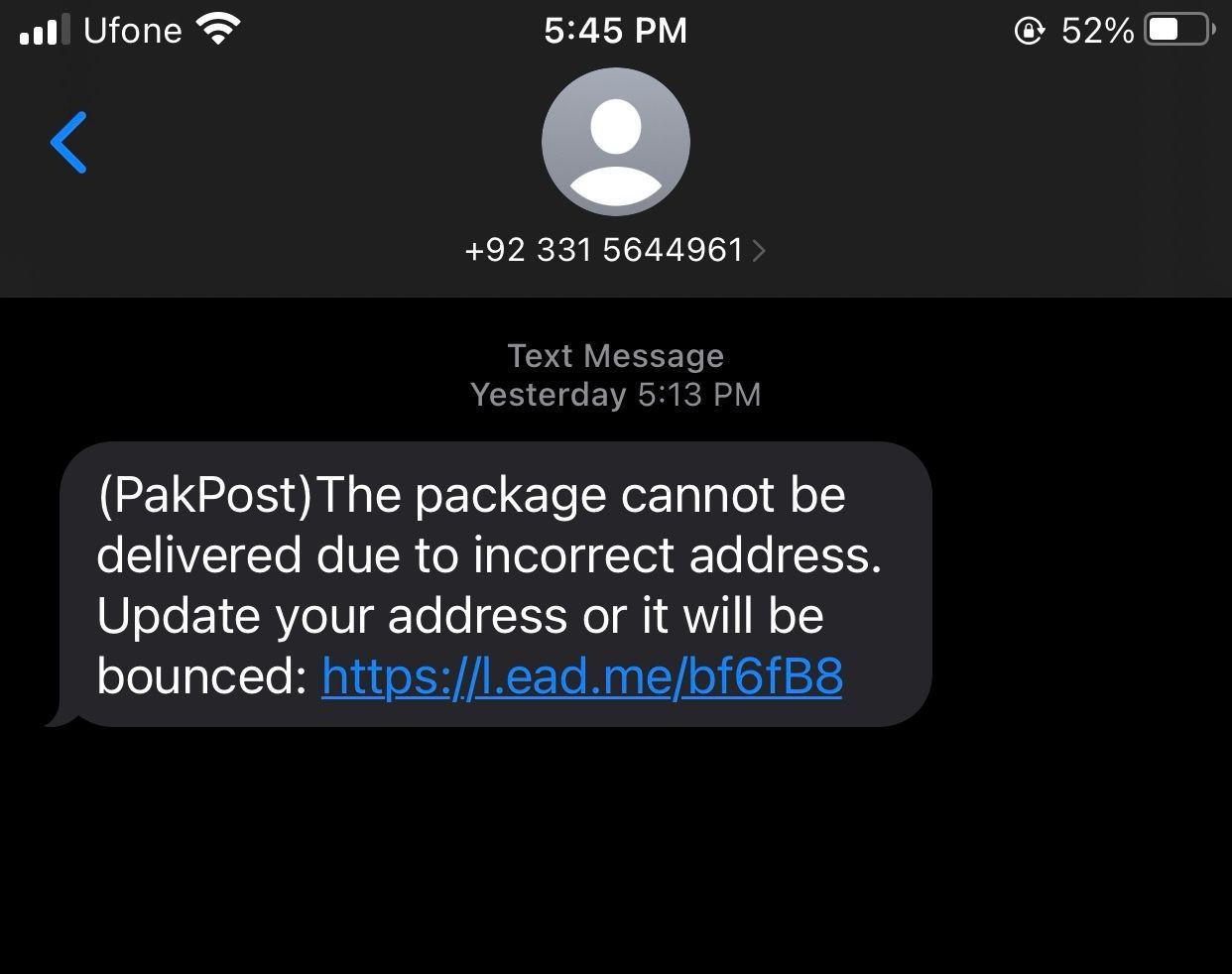
Once the victim reacts to the phishing link, the actors will display a payment form and notification impersonating Pakistan Post, demanding that the victim arrange payment and provide their credit card details to cover additional fees supposedly required to receive a package.
Early indicators of this activity emerged in the second half of May, with the peak of activity observed in early June. Some variations of smishing text require users to confirm receipt by responding to the message. This allows actors to validate whether a user is active on their mobile device, enabling them to adjust their tactics and target the user more effectively. Recently, multiple users from Pakistan reported suspicious activity on Reddit, receiving suspicious text messages, which prompted concerns about potential fraud or smishing attempts.
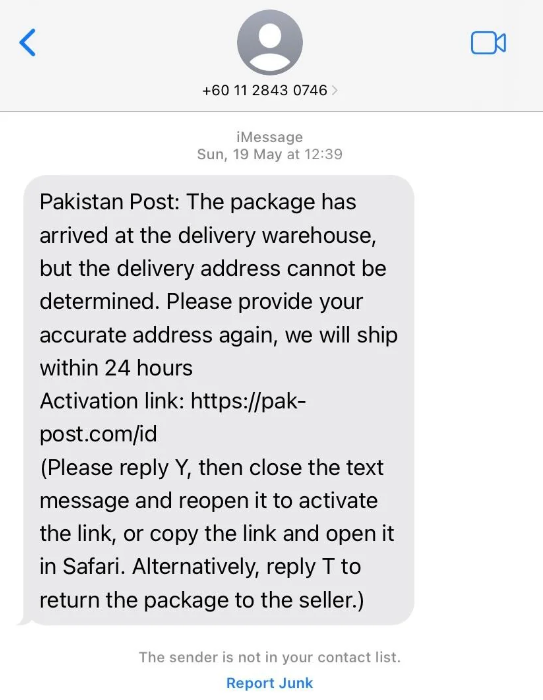
The most actively used smishing kits were discovered on hosts "pk-post-goi.xyz" and "ep-gov-ppk.cyou", which were set up by an actor impersonating the Express Mail Track & Trace System. The majority of domain names used for smishing have been registered through NameSilo, LLC using anonymous details and fake contact information. The identified domain names have been successfully taken down by Resecurity.
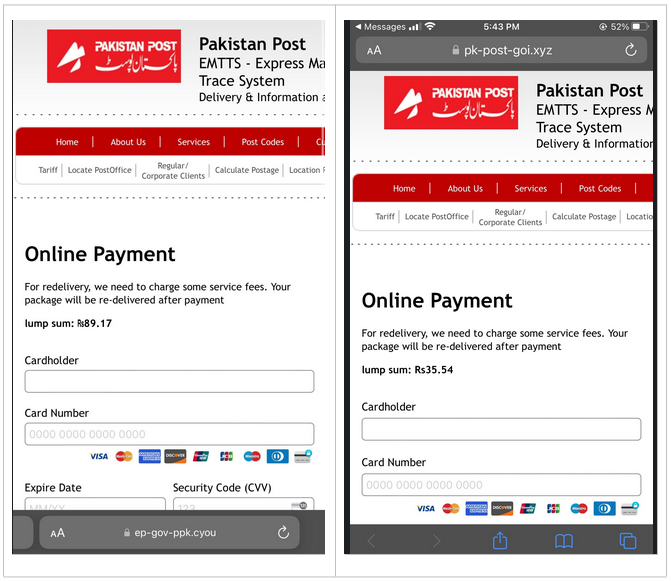
The actors employ techniques to evade detection, including the use of URL shortening services, such as those that provide QR code generation capabilities:
- https://support.qr-code-generator.com/hc/en-us
The National Cyber Emergency Response Team of Pakistan (PKCERT) issued a security advisory sharing patterns of observed smishing activity, urging citizens to take proactive measures to protect themselves. Besides Pakistan Post, the group was also involved in detecting multiple fake delivery package scams. These scams primarily targeted individuals who were expecting legitimate packages from reputable courier services such as TCS, Leopard, and FedEx.
Attribution
Resecurity observed multiple hosts used by attackers operating smishing kits targeting Pakistan's postal providers, including Correos, a state-owned postal provider in Spain, observed in previous episodes of Smishing Triad activity from last year. There were identified multiple domain names mapped to the same IP address 23[.]231[.]48[.]129:
ep-gov-pkw[.]cfd
ep-gov-ppk[.]cyou
ep-gov-ppk[.]icu
correosytelegrafos-civ[.]icu
correos-es[.]cn
This confirms the group's continued targeting of victims from the EU as well. Earlier, in July 2023, Smishing Triad was targeting Correos (Spain), previously reported in our research on the group's activities.
Mitigation Measures
Smishing (SMS phishing) attacks can be deceptive and aim to trick individuals into revealing personal information or clicking on malicious links through text messages. Here are some tips to defend against smishing:
1. Be Skeptical: Treat unsolicited text messages with caution, especially if they ask for personal information or contain suspicious links. Remember that legitimate organizations typically do not request sensitive information via text message.
2. Don't Respond: The simplest defense against smishing attacks is to ignore and not respond to suspicious text messages. By not engaging with the message, you minimize the risk of falling victim to the scam.
3. Verify the Source: If you receive a text message claiming to be from a trusted organization or individual, independently verify its authenticity. Contact the organization directly using their official contact information to confirm the legitimacy of the message.
4. Don't Click on Links: Avoid clicking on links in text messages, especially if they are unexpected or from unknown sources. These links may lead to malicious websites or initiate the download of malware onto your device.
5. Use Security Software: Install and regularly update security software on your mobile device. This can help detect and block known smishing attacks.
6. Report Suspicious Messages: If you receive a smishing message, report it to your mobile service provider. They may be able to take action to block future attempts from the same source.
7. Educate Yourself: Stay informed about the latest smishing techniques and scams. By being aware of common tactics used by smishers, you can better protect yourself and recognize potential threats.
Remember, vigilance and skepticism are key when it comes to defending against smishing attacks. By following these tips, you can reduce the risk of falling victim to smishing scams and protect your personal information.
Indicators of Compromise
Resecurity has obtained indicators of compromise (IOCs) from multiple sources. Our investigation is ongoing to determine the full scope of the infrastructure and activity involved. Notably, the attackers have shifted their focus towards Pakistan.
- Domain Names
ep-gov-ppk[.]cyou
pk-post-goi[.]xyz
pak-post[.]com/id
pakpotech[.]top/id
- URLs
l[.]ead[.]me/bf6fB8
is[.]gd/bpEPk3
l[.]ead[.]me/BjsT
is[.]gd/8vcwYW
2h[.]ae/nwxP
2h[.]ae/cNRd
ytfrt[.]top/id
linkr[.]it/4bStpB
qrco[.]de/bf56c0
- Phone Numbers
+923361021455
+923301956704
+923315640313
+601128430746
+923301956704
+923328862313
+923121461238

