Terrorist Activity is Accelerating in Cyberspace - Risk Precursor to Summer Olympics and Elections
Terrorism

Intro
Yesterday FBI Director Christopher Wray expressed growing concerns over the potential for a coordinated foreign terrorist attack in the United States. During his testimony to the House Oversight Committee, Mr. Wray cited the ISIS-K attack on Crocus City Hall in Moscow in March as an example of the type of threat the bureau is increasingly concerned about. He also mentioned the need for more help from international partners in addressing terrorism threats and highlighted the potential exploitation of the U.S. southern border by foreign terrorists. The FBI is currently investigating various terrorist groups, including ISIS, al Qaeda, al Shabbab, Hezbollah, and IRGC forces. “We are increasingly concerned not just about the possibility of a foreign terrorist-inspired attack, which is already a significant concern, but also about the potential for a coordinated foreign terrorist attack" - he said. He pointed out that prosecutors this year won a sentence against an Iraqi immigrant who had plotted to sneak in a terrorist hit squad to try to assassinate former President George W. Bush. Mr. Wray also mentioned the vulnerability of the U.S. southern border, suggesting that it could be exploited by foreign terrorists. He emphasized the need for more international cooperation to address these threats. These details are alarming to the security community and private sector,
and demand a proactive approach to combat this threat, including identifying precursors to it in the cyberspace.
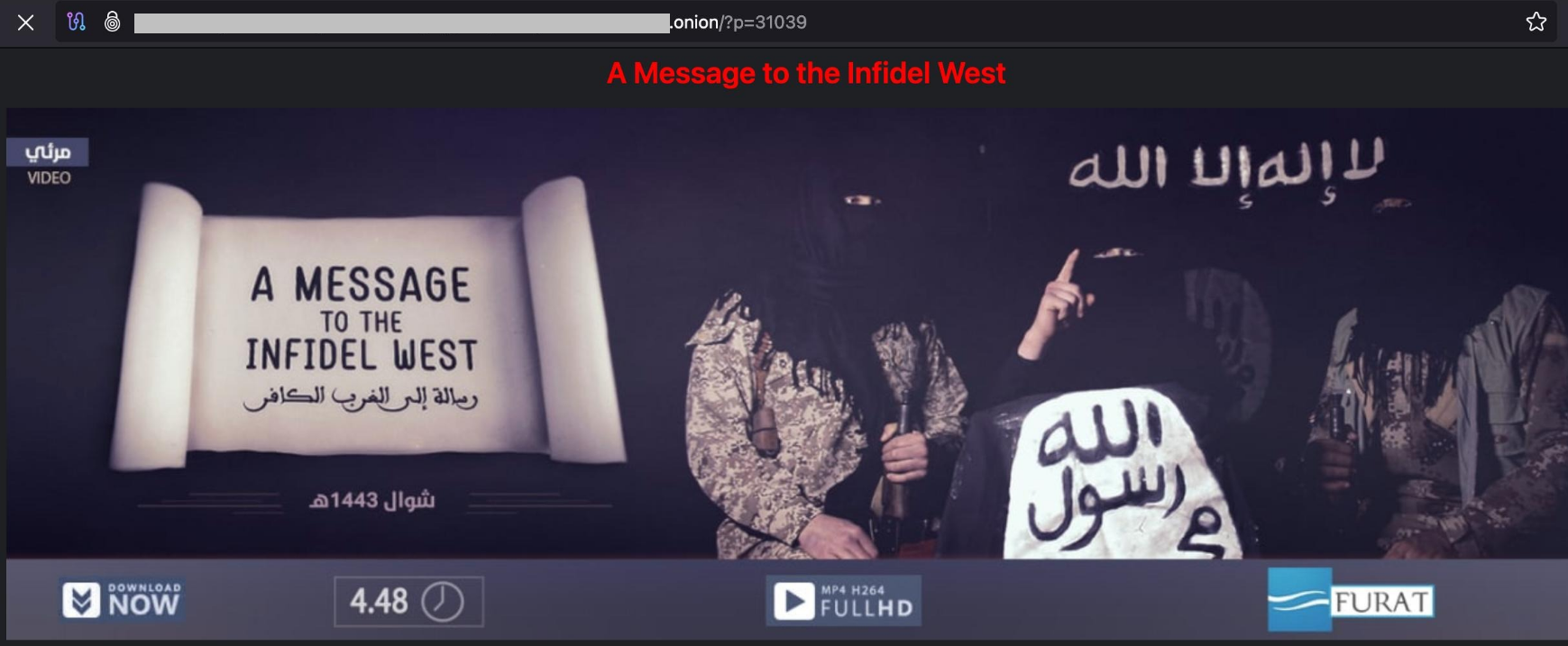
"A Message to the Infidel West"
According to assessment by Resecurity, terrorist groups are increasingly using cyberspace and digital communication channels to plan and execute attacks, as well as to conduct recruitment and establish anonymous communication channels. Multiple resources created by terrorists have been identified and deployed both in the surface web and the Tor network.
This activity was especially notable in Q2 2024, with new resources appearing at the beginning of Q3 2024. The international security community is tracking such resources and aims to take them down from the surface web to prevent the distribution of illegal content, but exploiting anonymous peer-to-peer networks creates a challenge to censor it. Terrorists exploit this issue to spread propaganda, attract youth, and recruit new members.
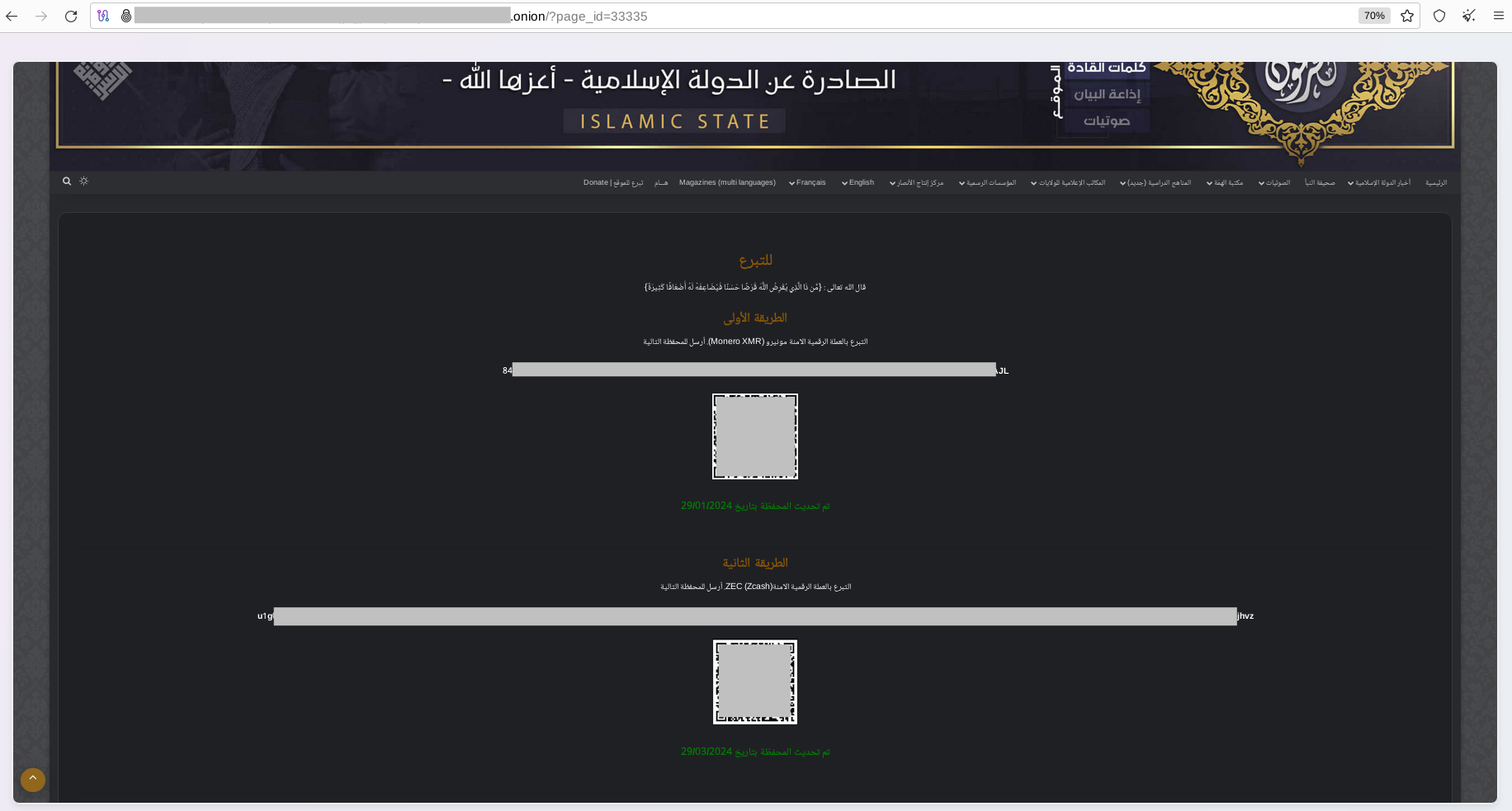
Furthermore, they create mechanisms to receive donations and other financial support using cryptocurrencies. As the most popular cryptocurrencies used by terrorists were identified Monero (XMR) and ZEC (Zcash). Threat actors update cryptocurrency wallets periodically to evade tracking and blur the distribution channels for financial transactions as a form of money laundering. Notably, one of the last updates to cryptocurrency wallets was detected on March 29, 2024.
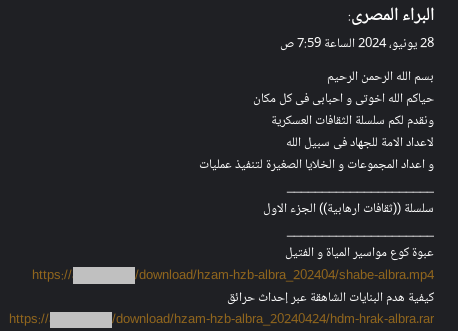
June 28, 2024 - the actors released multiple instructions and detailed tutorials on manufacturing explosive devices. One of the key goals of terrorists to spread malicious propaganda.
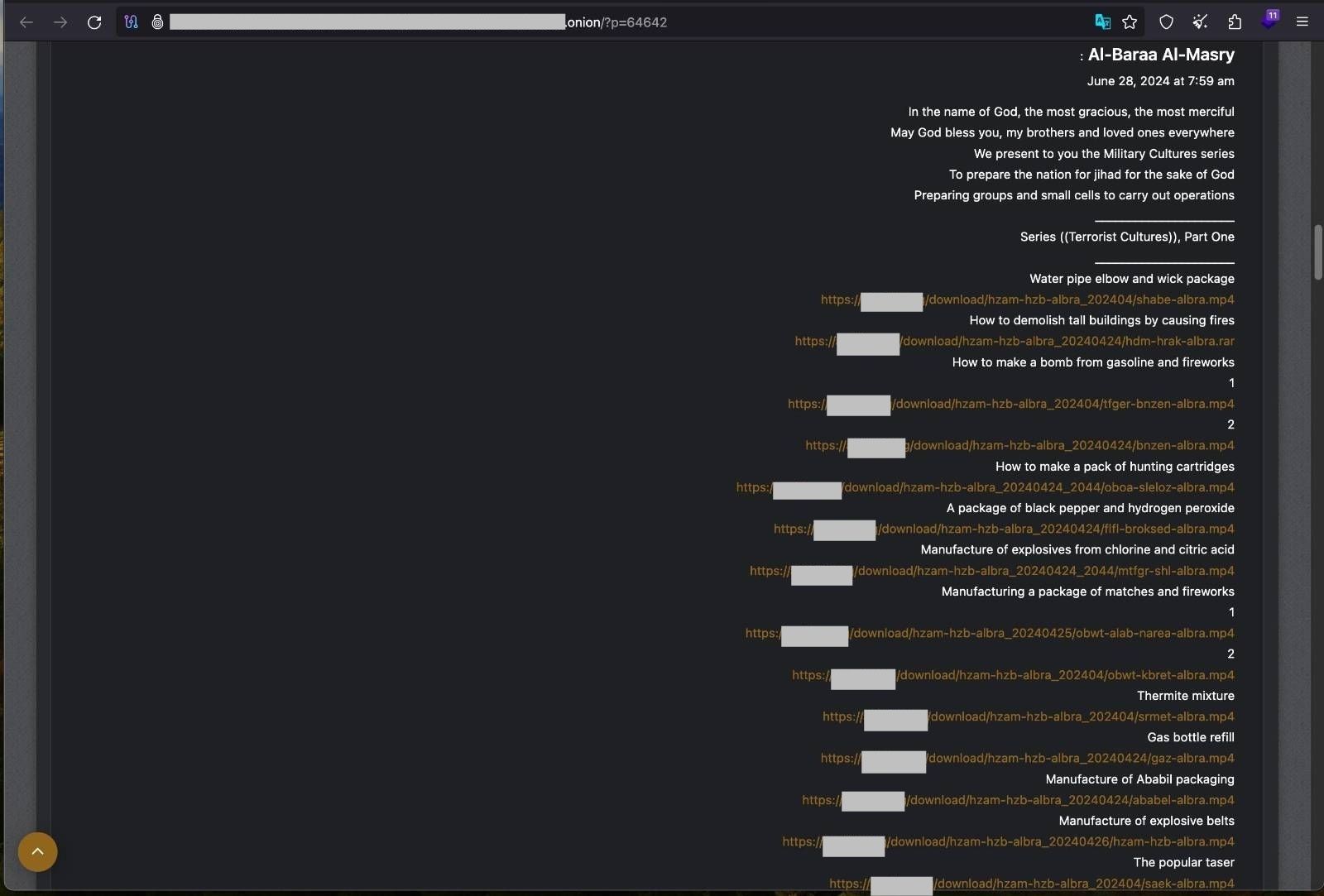
Some illegal materials were freely available for download via surface web resources, which terrorists misused and made such information easily accessible. The security community must accelerate efforts to combat the distribution of such information online.
This activity is coordinated and supported by several prohibited media organizations promoting illegal radical ideologies.
ISIS Makes Chilling Threat to Bomb Opening Ceremony of Paris Olympics
ISIS has published a menacing image online, suggesting the use of drones as potential bomb delivery systems for an attack on the Paris Olympics, accompanied by a caption declaring the start of the "Lone Wolves' Olympics".

Operatives for the terror group shared a picture of a faceless person operating a drone carrying a package marked ‘gift’ towards the Eiffel Tower. The image was shared with the caption: “Lone wolves’ Olympics have begun with the Will of Allah.” The picture was published on al-Ru’ud (al-Raud), a website linked to the Islamic State. The page was titled: “The Lone Wolves qualifiers have begun, God willing Al-Adiyat Media Foundation.”
Illegal Content Distribution and Propaganda
Beside 'lone wolf' attacks terrorists are spreading educational materials for other groups, providing them military trainings on advanced level.
The content is uploaded to file-exchangers hosted in TOR network and made available by leveraging customized plugins such as http://playerjs.com.
Hosting illegal video content on the Tor Network allows it to remain isolated from possible takedown efforts. This is because the Tor Network provides a high degree of anonymity, making it challenging for authorities to identify and block the content. According to research publication "Countering Violent Extremism Videopower and Cyberspace" by J.Rami Mroz, terrorists and extremist groups recognized the enormous emotional and psychological impact of video formats and have used them to inspire and captivate international audiences. Threat actors use video and cyberspace in order to:
- inject ideological or religious rhetoric into political debates
- mold existing imagery from mainstream media to suit their purposes
- generate emotive responses from their target audiences to develop and/or amplify a belief-driven sense of purpose
- protect and control channels of communication
- operate diffuse networks
- build an “army of believers”
- recruit operatives, especially young people, to commit violence
- provide operational intelligence and information
- intimidate their enemies
- raise funds.
Anonymous Communication Channels
One of the recently observed trends is the promotion by terrorists of secure messenger apps like Session. There were identified multiple tutorials provided for their followers and new recruits as one of the primary communication channels.
Observed tutorials provide detailed instructions on how to improve OPSEC, as well as configure mobile devices in case they may be seized by law enforcement.
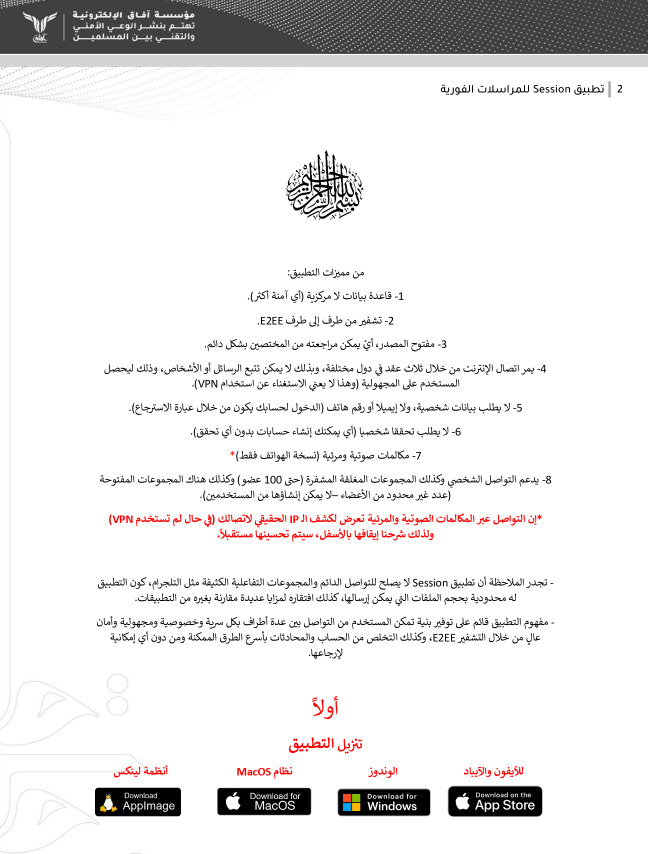
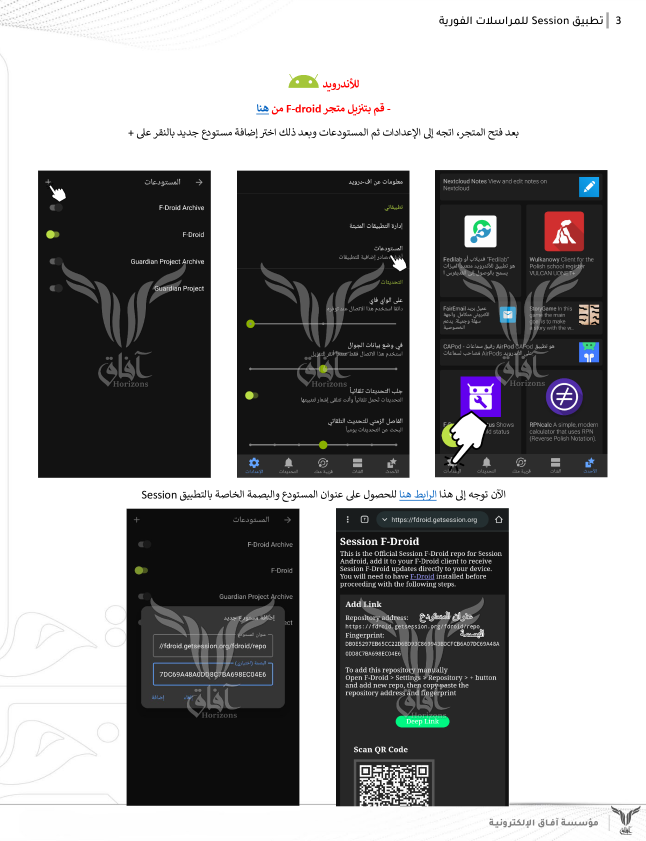
The content is primarily written in Arabic, but there were identified translations in other languages as well including French and Russian:

Emerging Technologies May Heighten Terrorist Threats
According to the published report by ODNI, in the coming years, the development of emerging and disruptive technologies may transform the capabilities of terrorists, complicating investigations and responses to attacks. Terrorists may use emerging technologies to: (1) further enable radicalization to violence and recruitment; (2) augment planning, training, and plotting; and (3) employ new, remote attack methods. First responders can prepare for these threats by building awareness of how technological advances can enable terrorist tactics, techniques, and procedures (TTPs) as well as by investing in and adopting countermeasures.
Spring 2024, there was observed a spike of illegal content related to educational materials related to explosives spreaded on the Dark Web. At some point, such content is promoted as "anarchy" ideology encouraging youth to get involved in illegal activities. Making such information available using Dark Web means created a significant threat for our society. By July 2024, the number of such resources indexed by Resecurity is almost doubled compared to previous timeframes. This may highlight the growing effort to distribute such illegal content before important events. It is expected that such activity may amplify by the the elections in the United States, with the intention of sowing chaos and radical activity.
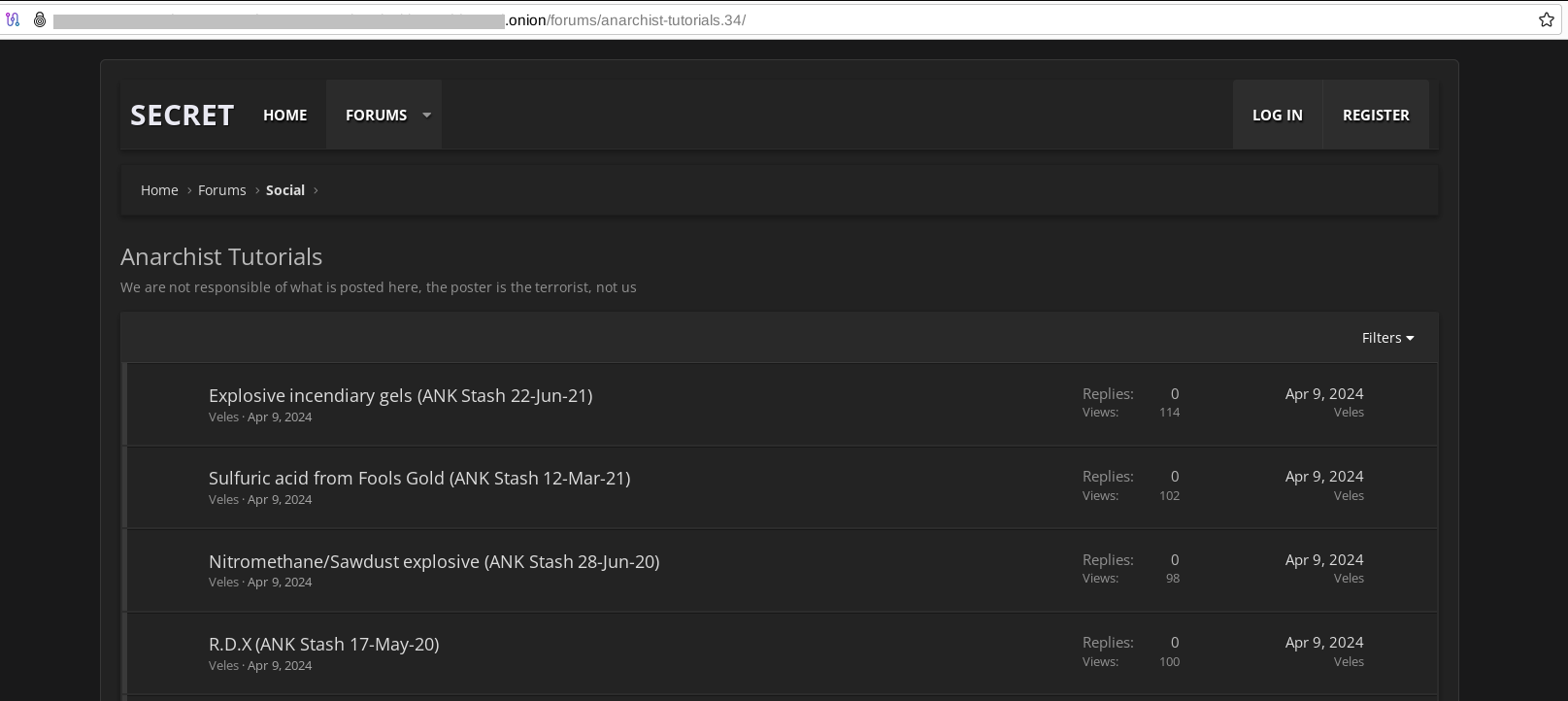
It is expected, Artificial Intelligence (AI) may be used to leverage such data in training models (by bad actors) outside of publicly available LLMs, in order to facilitate quick decision, translation and navigation across available TTPs for the new generation of terrorists. Security community is already envisioning this threat, that's why popular GPT engines try to incorporate concept of LLM firewalls restricting relevant keywords, but bad actors are constantly searching ways to bypass it ("jailbreak").
According to a special report by SITE (Extremist Movements are Thriving as AI Tech Proliferates) terrorists are already using AI to generate content. Salivating at the potential from these technologies, jihadi media groups are now investing more time into deploying them across their communities. On February 9, an al-Qaeda-aligned media group called The Islamic Media Cooperation Council (IMCC) announced an “artificial intelligence workshop.” “This workshop is concerned with developing skills in using artificial intelligence software in media work in particular, and other fields,” it stated.
The Islamic State Khorasan (ISKP) group, an IS affiliate active in Afghanistan and Pakistan, produced in a video an AI-generated anchorman to appear reading news following an IS-claimed attack in Bamiyan province in Afghanistan on May 17 that killed four people, including three Spanish tourists. The digital image posing as an anchor spoke the Pashto language and had features resembling local residents in Bamiyan, according to The Khorasan Diary, a website dedicated to news and analysis on the region. Another AI-generated propaganda video by Islamic State appeared on Tuesday with a different digital male news anchor announcing IS’s responsibility for a car bombing in Kandahar, Afghanistan.
Growing Social Media Activity
The Asayish Internal Security Forces announced the successful arrest of 30 Islamic State (ISIS) suspects who were found to be spreading extremist ideas on social media platforms. The suspects had planned to join the ranks of ISIS and become fighters for the terrorist group. According to information received, two groups were spreading extremist ideas in the Pishdar and Bitwen regions.
ISIS seized control of significant territory in Iraq in 2014. Although declared territorially defeated in 2017, the group continues to carry out attacks across several provinces. By July 2024, the cyber landscape showed an emerging threat originating from Iraq and the Kurdistan Region. Resecurity identified multiple actors with profiles on popular social media platforms, including Facebook, with some repeatedly violating terms of service.
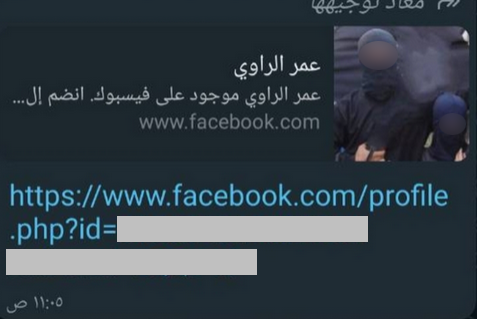
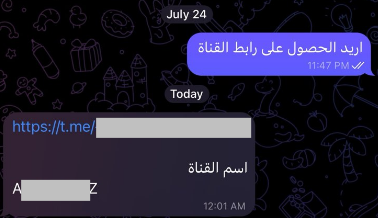
Telegram IM is also widely misused by terrorists and extremists. On July 13, 2024, multiple resources were detected spreading information about Telegram bots providing instructions and details on accessing illegal content related to explosive devices.

Such bots generate one-time links to evade detection by external censorship and social media monitoring solutions.
Unfortunately, the abuse management and trust & safety teams of popular online platforms are not always able to react quickly enough or proactively identify such profiles at an early stage due to a lack of visibility and limited resources, which is exploited by threat actors.
Global Challenge for the Private Sector: AML and Trust & Safety
Besides efforts by law enforcement and public sector agencies to combat terrorism, there are many challenges on the shoulders of the private sector in managing online platforms, marketplaces, social media, and other resources. One of the key issues is tracking high-risk individuals who may misuse financial services, such as banks, e-commerce platforms, and payment networks, to engage in illegal activities, including money laundering and terrorism financing.
Resecurity has identified a strong interest in relatively new fintech services abroad, which provide actors with a quick way to obtain financial tools for transactions without undergoing deep KYC or other checks beyond public sanctions and PEP lists. Identifying such actors at an early stage requires businesses to be prepared with proper intelligence and solutions enabling them to scan their customer base. Threat actors involved in terrorism are well aware of the criteria that modern financial institutions use to identify customers, and aim to bypass these criteria by masquerading as regular customers. Typically, such actors avoid raising anomalies and strive to operate in a way that is indistinguishable from any other customer, without being flagged.
Financial institutions (FIs), virtual asset service providers (VASPs), and online marketplaces must modernize their defenses to combat next-generation threats. Resecurity is protecting major Fortune 100 organizations and government agencies by sharing actionable risk intelligence to facilitate the identification of high-risk individuals and accelerate anti-money laundering controls for compliance purposes.
To address this issue, Resecurity has built an extensive and constantly updating repository of high-risk individuals and businesses outside of public data feeds enabling businesses to enhance the detection. The access to it is provided for relevant law enforcement agencies, regulators and industry partners in scope of our risk intelligence portfolio. For any additional information, please, don't hesitate to reach out via contact@resecurity.com.
References
- The Emergence of Lone Wolf Terrorism: Patterns of Behavior and Implications for Intervention
https://www.start.umd.edu/publication/emergence-lone-wolf-terrorism-patterns-behavior-and-implicatio...
- Radicalization through the Internet: How ISIS became So Successful and Why the United States Needs to Catch up
https://research.library.fordham.edu/cgi/viewcontent.cgi?article=1020&context=international_senior
- Lone Wolf Terrorism in America: Using Knowledge of Radicalization Pathways to Forge Prevention Strategies
https://www.ojp.gov/pdffiles1/nij/grants/248691.pdf
- Terrorism in Cyberspace: The Next Generation
https://www.wilsoncenter.org/book/terrorism-cyberspace-the-next-generation
- Counter-terrorism in Cyberspace
https://www.un.org/securitycouncil/ctc/sites/www.un.org.securitycouncil.ctc/files/ctc_cted_factsheet...
- Cyber-radicalization: Combating terrorism in the digital era
https://www.efsas.org/publications/study-papers/cyber-radicalization-combating-terrorism-in-the-digi...
- Countering Online Radicalization in America
https://bipartisanpolicy.org/download/?file=/wp-content/uploads/2019/03/BPC-_Online-Radicalization-R...
- The Third Generation of Online Radicalization
https://extremism.gwu.edu/third-generation-online-radicalization
Disclaimer
The following information includes citations related to terrorist/extremist groups for the purpose of providing factual information and raising security awareness. The inclusion of these citations does not endorse or support any extremist ideologies or actions associated with ISIS. It is important to approach this topic with sensitivity and critical analysis.

