
Intro
Unmanned Aerial Vehicles (UAVs), commonly known as drones, have become integral to modern military operations, particularly for intelligence, surveillance, and reconnaissance (ISR) missions. As their use has expanded, so has the focus on counter-UAV (C-UAV) technologies designed to detect and neutralize these aerial threats. Cybercriminal groups and foreign nation-state actors express a significant interest in these technologies.
The increase in malicious cyber activity targeting drones was especially notable during periods of local conflicts, including the escalation of the Russia-Ukraine war and the Israel-Hamas confrontation. The trend of malicious targeting in the drone manufacturing segment increased during Q3-Q4 2024 and continued into Q1 2025.
Multiple postings on the Dark Web by actors looking to acquire sensitive military and intellectual property (IP) documents related to drones. Such tactics enable foreign actors to optimize their efforts and blur attribution, operating under the guise of cybercriminals.
It is also well known that drug cartels use dark web actors for espionage against law enforcement and other government agencies, as well as their rival cartels, to protect their illicit operations.
There are indications that China is involved in hacking activities targeting UAV vendors, particularly in regions like Taiwan. Independent reports suggest that a Chinese-speaking hacking group has been conducting cyberespionage operations against drone manufacturers in Taiwan, which is home to several key players in the UAV industry. Similar efforts targeting enterprises in other regions, including North America, the Middle East, the United Kingdom, and the European Union (EU), have been detected.
Resecurity observed an increased interest in specialists involved in science and technology (S&T) and drone engineering by foreign actors, which enables them to pivot from cyber to traditional industrial espionage. In several incidents investigated by Resecurity, the actors were more interested in actual buyers of UAV and counter-UAV technologies rather than the specifics of the technology involved, which likely is the reconnaissance for future cyber threats against buyers of these technologies. Which could include Human Intelligence (HUMINT) efforts concentrated on specific areas of interest relevant to the defense industrial base (DIB) workflow.
Specific Threats Observed in UAV and Counter-UAV Technologies
The rise of UAVs has introduced several specific threats that are increasingly being observed, particularly in the context of military and security operations. Here are some of the key threats:
1. Surveillance and Intelligence Gathering: Adversaries can use UAVs to conduct surveillance and gather intelligence on military installations, troop movements, and critical infrastructure. Their ability to fly at predetermined coordinates and small size makes them difficult to detect, allowing for covert operations. This also includes countersurveillance and counterintelligence, enabling the threat actor to see what the UAV observes. This allows the adversary to monitor the UAV's observations on the battlefield and during its navigation behind its friendly lines.
2. Weaponization of Drones: There is a growing trend of UAVs being weaponized, which poses a direct threat to both military and civilian targets. Armed drones can be deployed for precision strikes, making them a potent tool for asymmetric warfare.
3. Cyber Vulnerabilities: UAVs are susceptible to cyberattacks that can compromise their control systems. Hackers can hijack drones, manipulate their flight paths, usurp their original mission, or disable them entirely, leading to significant operational risks.
4. Swarming Tactics: Coordinated swarming tactics involving multiple drones present a complex challenge for defense systems. This approach can overwhelm traditional countermeasures, making it difficult to neutralize threats effectively.
5. Counter-UAV Systems Targeting: As counter-UAV technologies evolve to detect and neutralize drones, these systems become targets for cyberespionage and attacks. Adversaries may seek to disable or deceive these systems to allow their UAVs to operate freely.
6. Supply Chain / Component Security: Drones often have numerous components sourced from various suppliers. If these suppliers are compromised, malicious hardware or software can be introduced into drone systems. This could allow unauthorized access or control over the drones, posing serious security risks.
Notable Cybersecurity Incidents
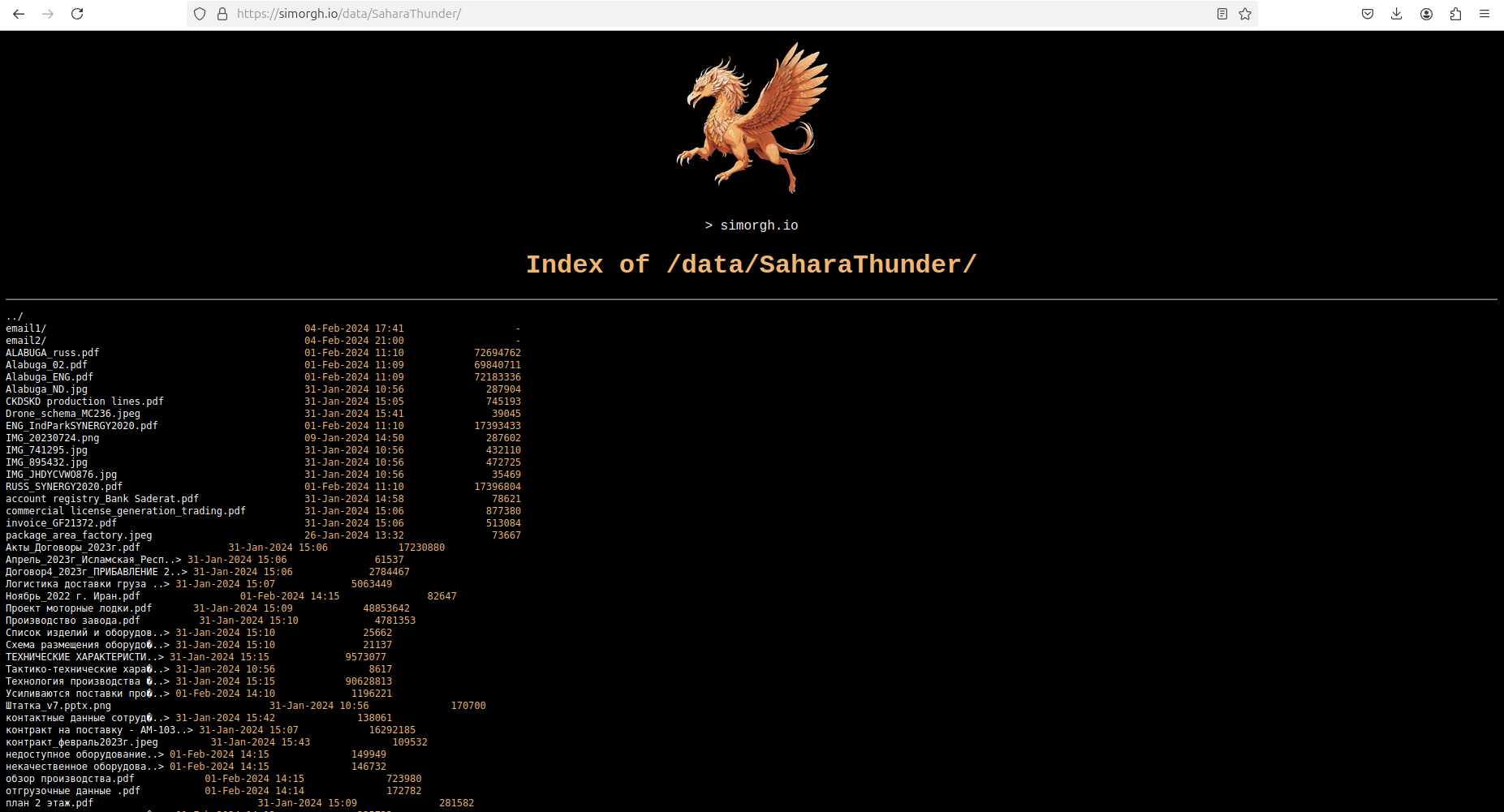
Last year, hackers from the Prana Network group compromised the mail servers of the Iranian company IRGC Sahara Thunder, which contained an array of data on the production of Shahed-136 attack drones in Alabuga’s special economic zone based in Tatarstan.
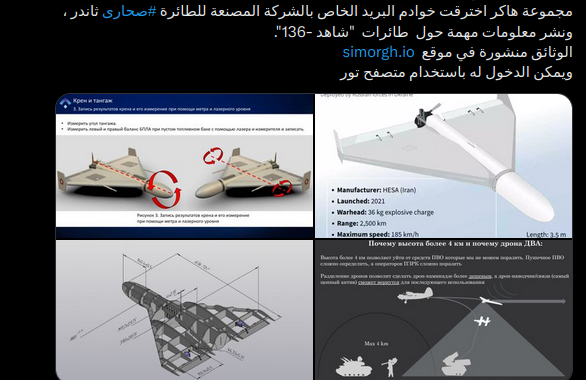
Prana Network has leaked the stolen data under a hacktivist group's guise; however, their tactics' pattern may indicate an advanced cyberespionage group or a nation-state actor. The actor focused on uncovering the supply chain and financial transactions facilitating drone manufacturing and logistics processes. These transactions included legal entities registered in the UAE and Hong Kong that were used as proxies to evade sanctions.
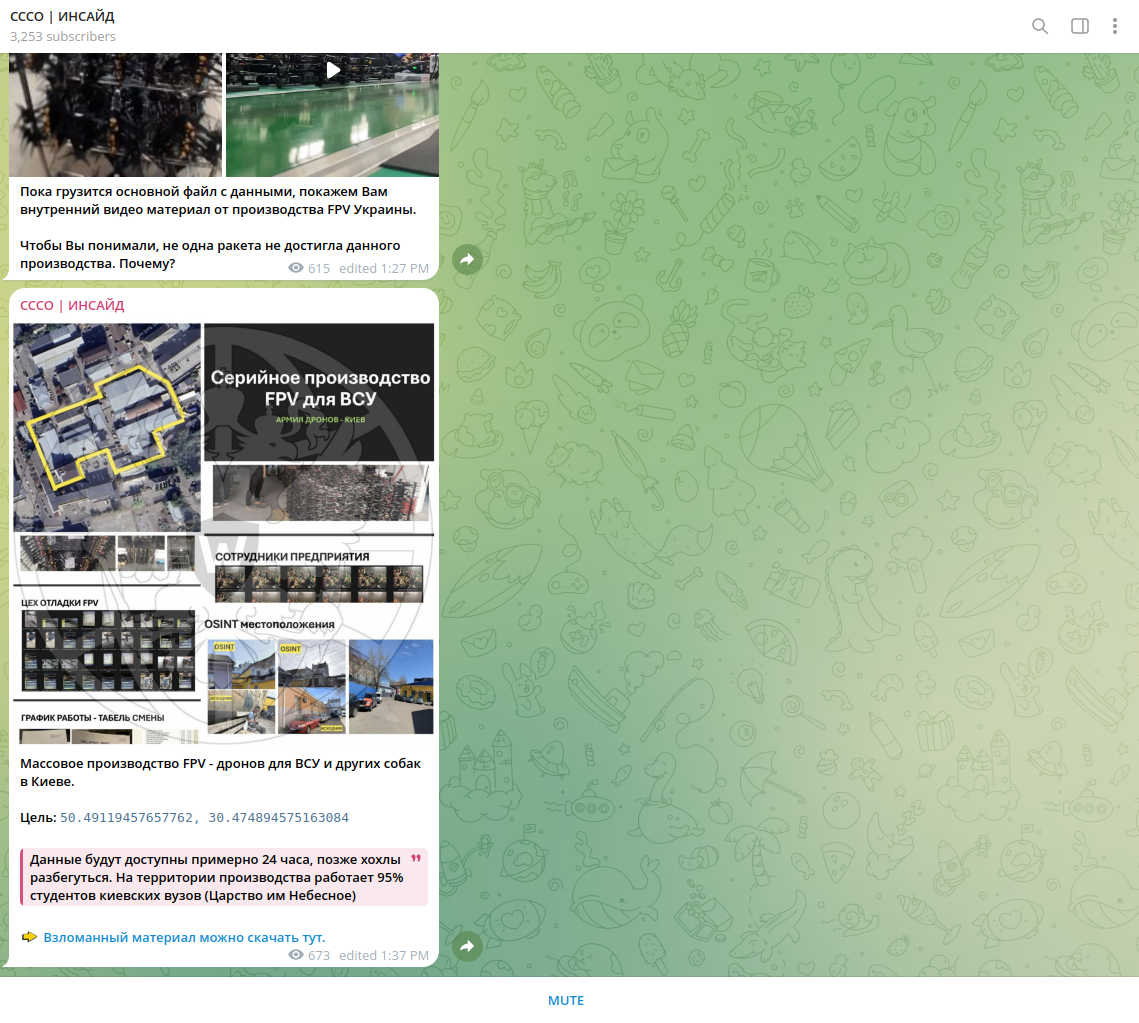
Identified actors collected OSINT and proprietary information about possible drone manufacturing facilities. Such information may be especially relevant during local conflicts, and details about them may be sensitive and damaging, making them targets of attack (cyber disruption, kinetic attack, or terror activity). One such actor, known as the "Special (Cyber) Operations Service," leaked information about one such facility, highlighting the involvement of students.
DDOS-focused groups such as NoName057 attacked several drone manufacturers in the U.K.
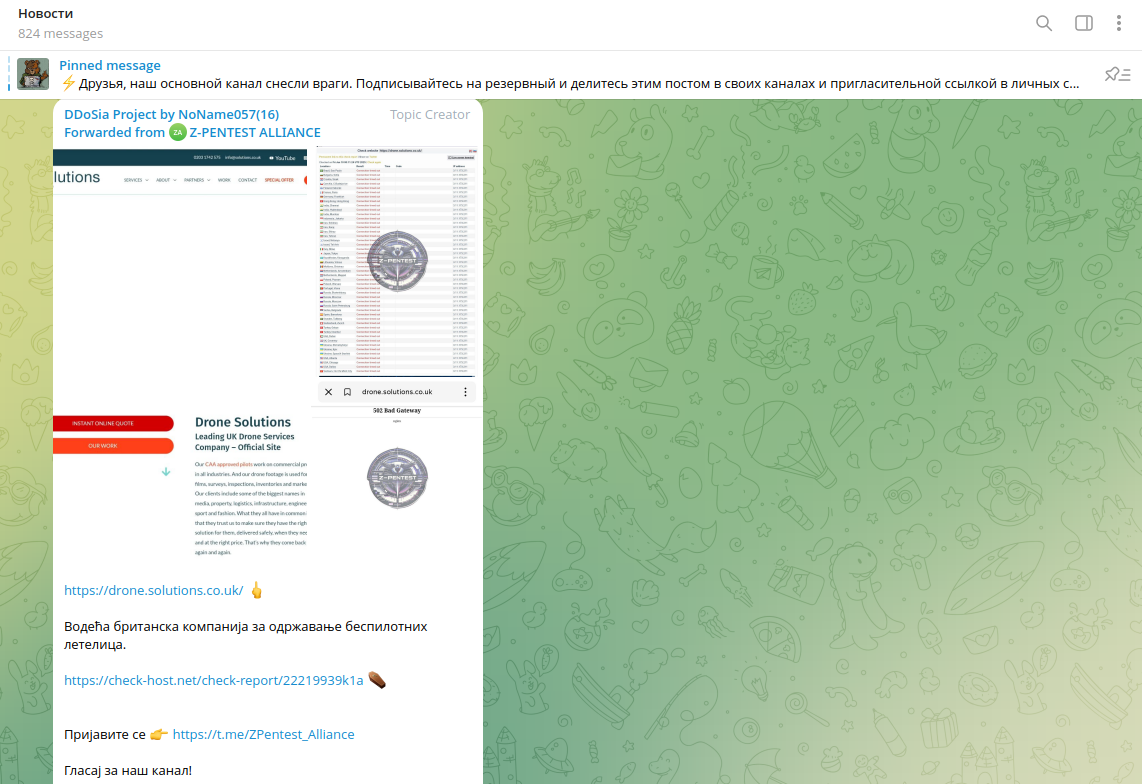
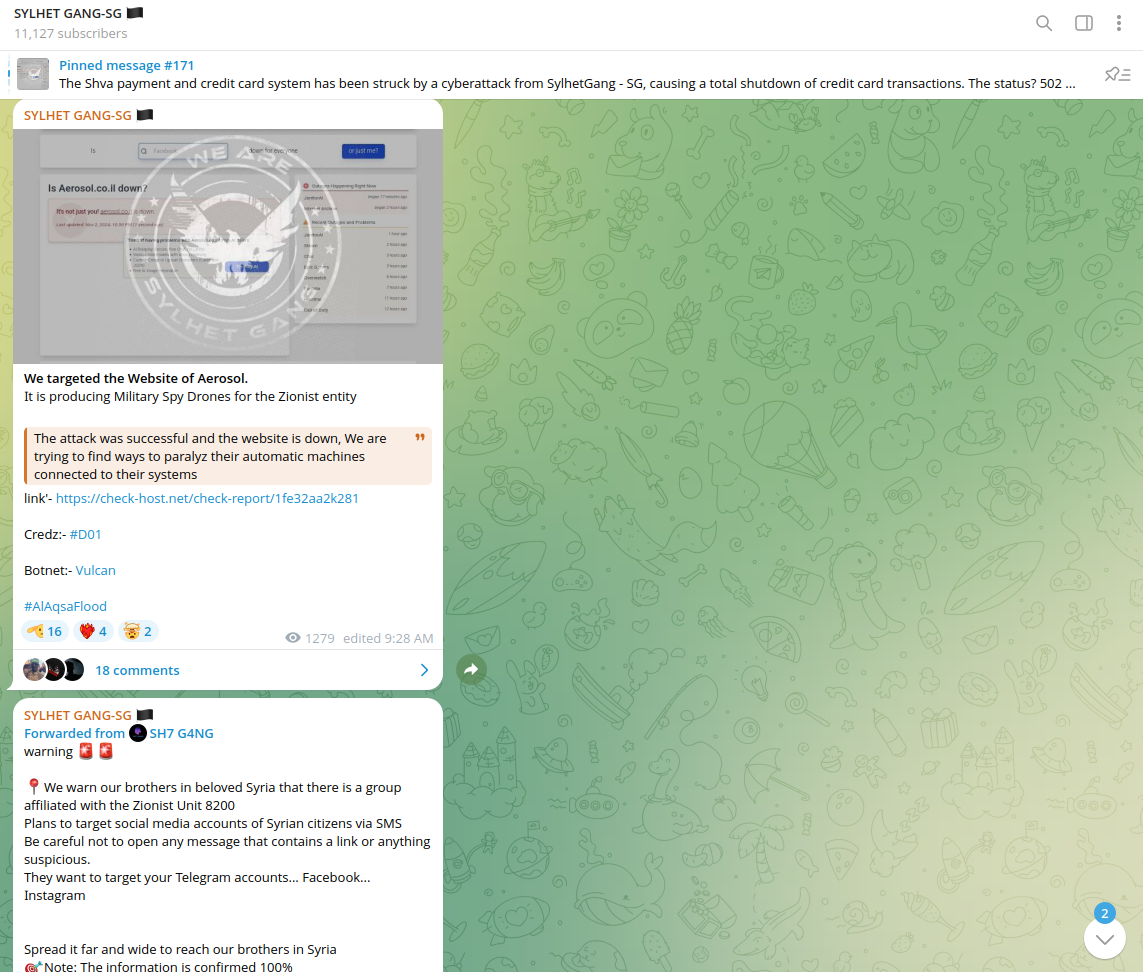
A similar activity took place against an Israel-based manufacturer targeted by Sylhet Gang-SG:
Unmanned drone systems maker Autonomous Flight Technologies (AFT) has allegedly fallen victim to a cyberattack orchestrated by the notorious BlackCat ransomware group investigated by Resecurity. The attackers claimed the Autonomous Flight Technologies data breach and purportedly sold exfiltrated data to an undisclosed foreign entity. AFT, recognized for its cutting-edge unmanned drone technology, boasts prominent partnerships with industry giants such as Airbus, NASA, NBC, and Northrop Grumman.
On the Radar of Terrorists and Drug Cartels
Terrorists and drug cartels have shown a growing interest in drones, recognizing their potential as tools for carrying out attacks, reconnaissance, and distribution of illicit material, and have been identified as significant threats by security experts and organizations, including the United Nations Security Council Counter-Terrorism Committee.
Resecurity identified several ISIS-linked communities where actors track the latest trends in drone engineering and discuss operational security (OPSEC) for operators. This includes exploiting vulnerabilities using the radio spectrum and sensitive information likely sourced from distributors and suppliers that is not available in the public domain.
Terrorists' interests are like those of foreign nation-state actors. They seek to increase the effectiveness of their attacks by learning about new technologies involved in counter-UAVs.
It is well documented that drug cartels are increasingly using drones for smuggling, surveillance, and evading law enforcement. By modifying commercial drones, they transport drugs across borders or into prisons in small quantities to avoid detection while maximizing profits. Drones also assist in mapping out routes, scouting security checkpoints, and monitoring rival gangs, providing real-time intelligence. Additionally, cartels have tested the mounting of weapons or explosives on drones for targeted strikes and intimidation. Thus, drones offer a strategic advantage, complicating the fight against the evolving tactics of drug cartels. They also employ counter-UAV technology to prevent drones from being used against them by law enforcement and rival cartels.
Cyber Espionage in War Between Drones
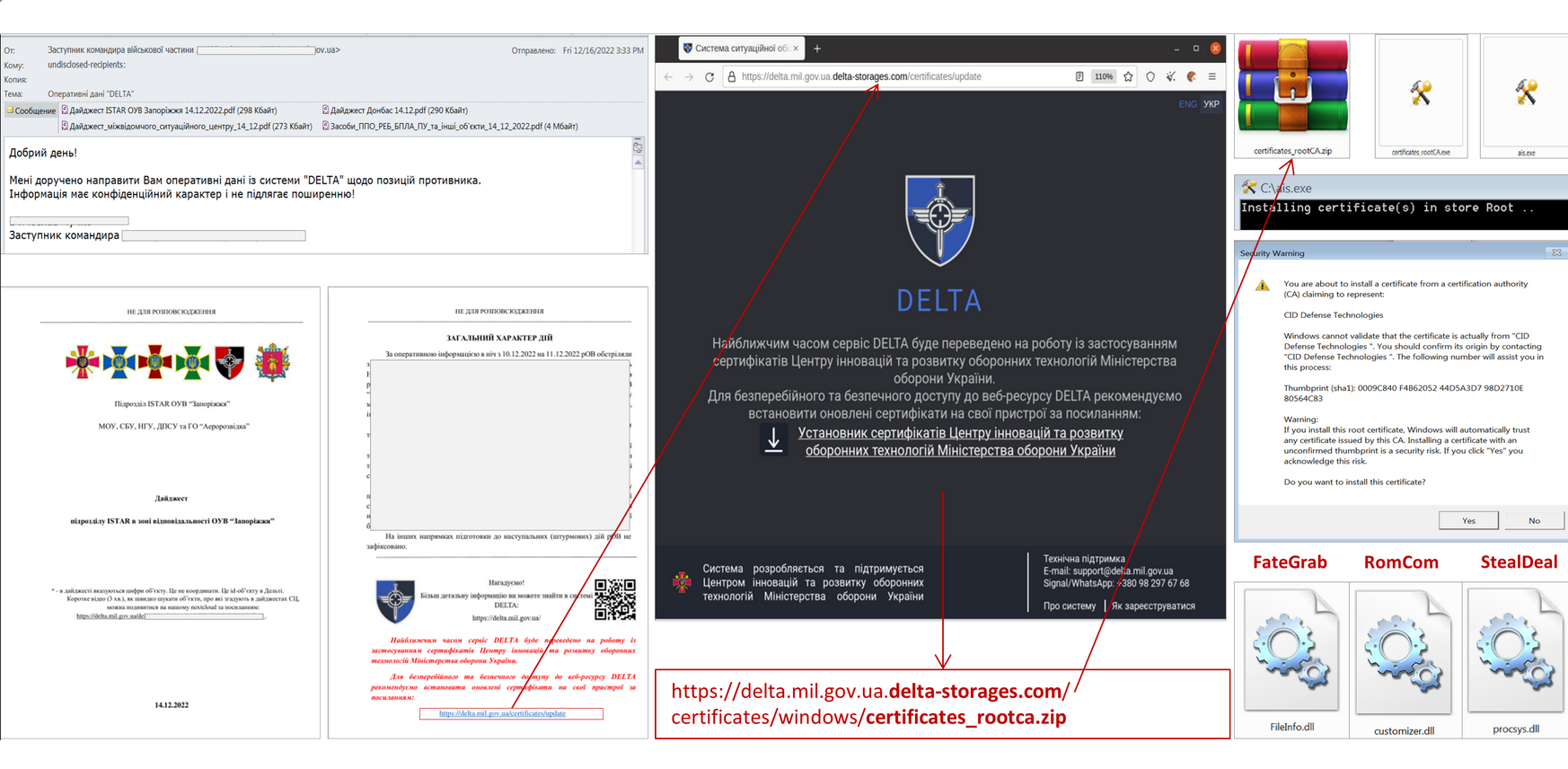
Resecurity has identified multiple actors presumably linked to a foreign state targeting Delta, a situational awareness and battlefield management system developed by the Ukrainian military for use in the Russo-Ukrainian War. This system utilizes UAVs to stream data for further sharing with warfighters. Threat actors intend to gain unauthorized access to such systems and compromise operators to obtain sensitive military intelligence. The following screenshots have been received from actors referred to as the 'Special (Cyber) Operations Service,' targeting the Ukrainian Military:
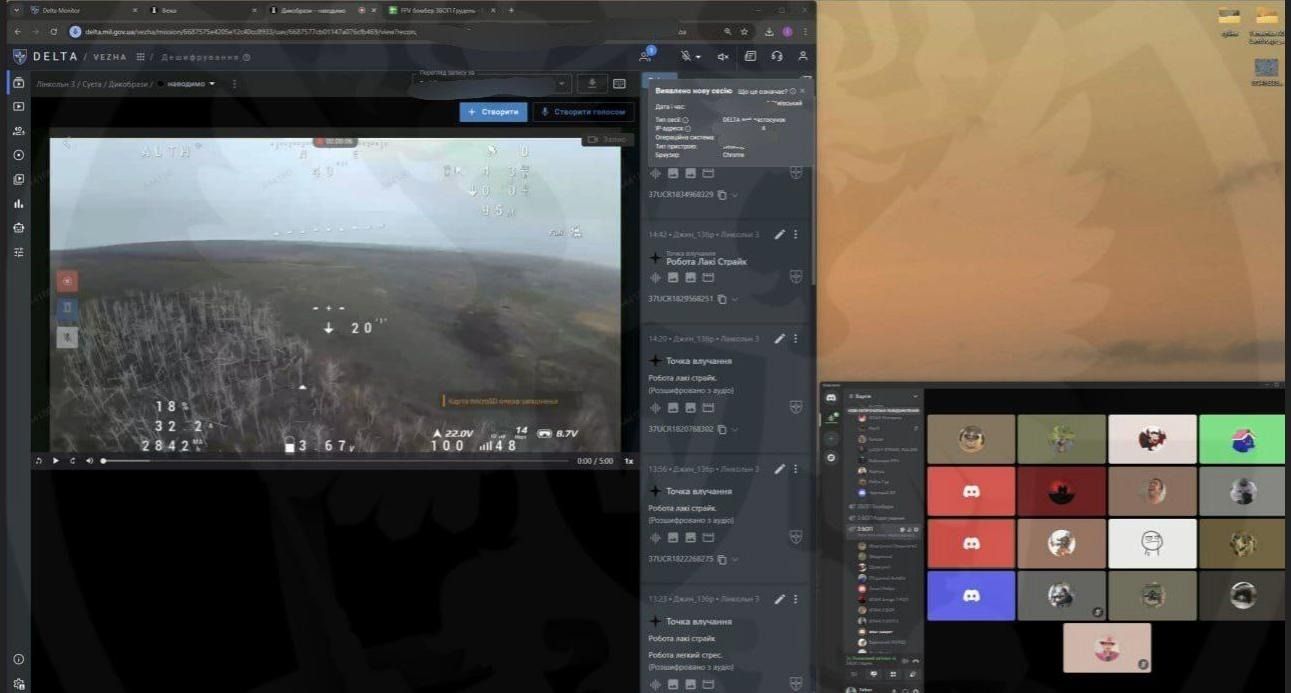
Previously, Ukraine's Computer Emergency Response Team (CERT-UA) shared a threat intelligence notification involving Delta and malicious code targeting the military.
The Measures UAV Vendors Can Take Against Cyber Threats
To protect against cyber threats, particularly from state-sponsored actors like China targeting UAV vendors, companies can implement several strategic measures:
1. Adopt Secure by Design Principles: Vendors should prioritize the development of UAVs with security integrated into the design process. This includes using secure coding practices and ensuring all components are built with cybersecurity. By adopting a "Secure by Design" approach, vulnerabilities can be minimized from the outset.
2. Implement Robust Cybersecurity Frameworks: Utilizing established cybersecurity frameworks, such as the STRIDE threat model, can help identify and mitigate potential risks. This model assists in analyzing threats across various dimensions, allowing vendors to develop comprehensive security strategies tailored to their systems.
3. Enhance Communication Security: Given the vulnerabilities in communications between UAVs, ground control stations, and pilot devices, vendors should implement strong encryption protocols and secure communication channels. This will help protect data integrity and prevent unauthorized access. It is also essential to recognize that the stolen intelligence can help adversaries detect and counter the drones.
4. Conduct Regular Security Audits and Penetration Testing: Regularly assessing the security posture of UAV systems through audits and penetration testing can help identify weaknesses before attackers can exploit them. This proactive approach allows for the timely remediation of vulnerabilities.
5. Invest in Drone Forensics: Establishing capabilities for drone forensics can help investigate security incidents. This involves analyzing breaches to understand how they occurred and improve future defenses.
6. Supply Chain Risk Management: Vendors should be aware of their suppliers' security standards and the jurisdictions in which they operate. Understanding the supply chain can help assess risks and ensure all components meet stringent security requirements.
7. Employee Training and Awareness: Ensuring all employees are trained in cybersecurity best practices is crucial. Regular training sessions can help staff recognize potential threats and respond appropriately, reducing the risk of human error leading to security breaches.
By implementing these measures, UAV vendors can significantly enhance their cybersecurity posture, protect sensitive data, and mitigate the risks posed by cyber threats, particularly from state-sponsored actors.
Conclusion
In summary, the threats posed by UAVs and the corresponding counter-UAV technologies are multifaceted. They involve surveillance capabilities, weaponization, cyber vulnerabilities, and advanced tactics like swarming. As these technologies continue to develop, robust defenses and cybersecurity measures become increasingly critical to mitigate these risks.

