Cyber Threat Intelligence
An intelligence platform for enterprises and governments to accelerate threat analysis.
Identifying the exposure of sensitive data & confidential documents.
Continuously updating repository of underground communities & marketplaces.
Lightning-fast search reaching the darkest corners of the Internet.
Delivering global visibility across all continents.
Cyber Threat Intelligence Platform
With the emergence of new threats and security challenges on a daily basis, it’s now more than ever important to use effective tools to achieve a timely in-depth analysis of any digital threat.
Contexttm is an intelligence platform to accelerate analysis, prevention, and investigation workflows. Lightning-fast search and data science serve analysts, investigators, SOC/DFIR teams, Risk management, and C-level security executives.
-
Take a holistic approach to piracy and counterfeit monitoring across various industry verticals. Prevent illicit distribution and use of your products using actionable intelligence.
-
Protect your brand from abuse, reputational risks, copyright infringement and intellectual property (IP) violation. Minimize loss of revenue, brand damage and loss of customer trust.
-
Identify the exposure of sensitive data, such as intellectual property, confidential documents, customer and employee data. Prevent the risk of data breaches in your infrastructure or clouds.
-
Catalogue your digital assets and control their risk across a variety of digital channels. Customize the settings of your digital footprint and get early warning notifications.
-
Leverage our lightning-fast search capabilities in the darkest corners of the internet by tapping into the biggest and constantly updated repository of underground communities and marketplaces (TOR, 12P, Freenet, IRCm IM-based).
-
Manage multiple internal and external threat intelligence feeds. Enrich circulating threat telemetry in your SOC/SIEM/TIP for strategic decision making and proactive incident response.
-
Use cloud-scale AI to detect and mitigate threats before they happen using our filtering scheme designed from the ground up to protect your enterprise.
-
Discover the latest tools, tactics and procedures (TTPs) of fraudsters and cybercriminals targeting your enterprise. Use our SDK and the REST API in your apps and services to strengthen anti-fraud.
-
Diligently setting up the network to accept new services for its users while simultaneously ensuring the network perimeter is safe from attacks.
-
Planning, Collection, Processing, Analyzing, Dissemination, and Evaluation. This is our Six-Step process used for Threat response and is used by high caliber governments and agencies.
Capabilities of cyber security intelligence platform
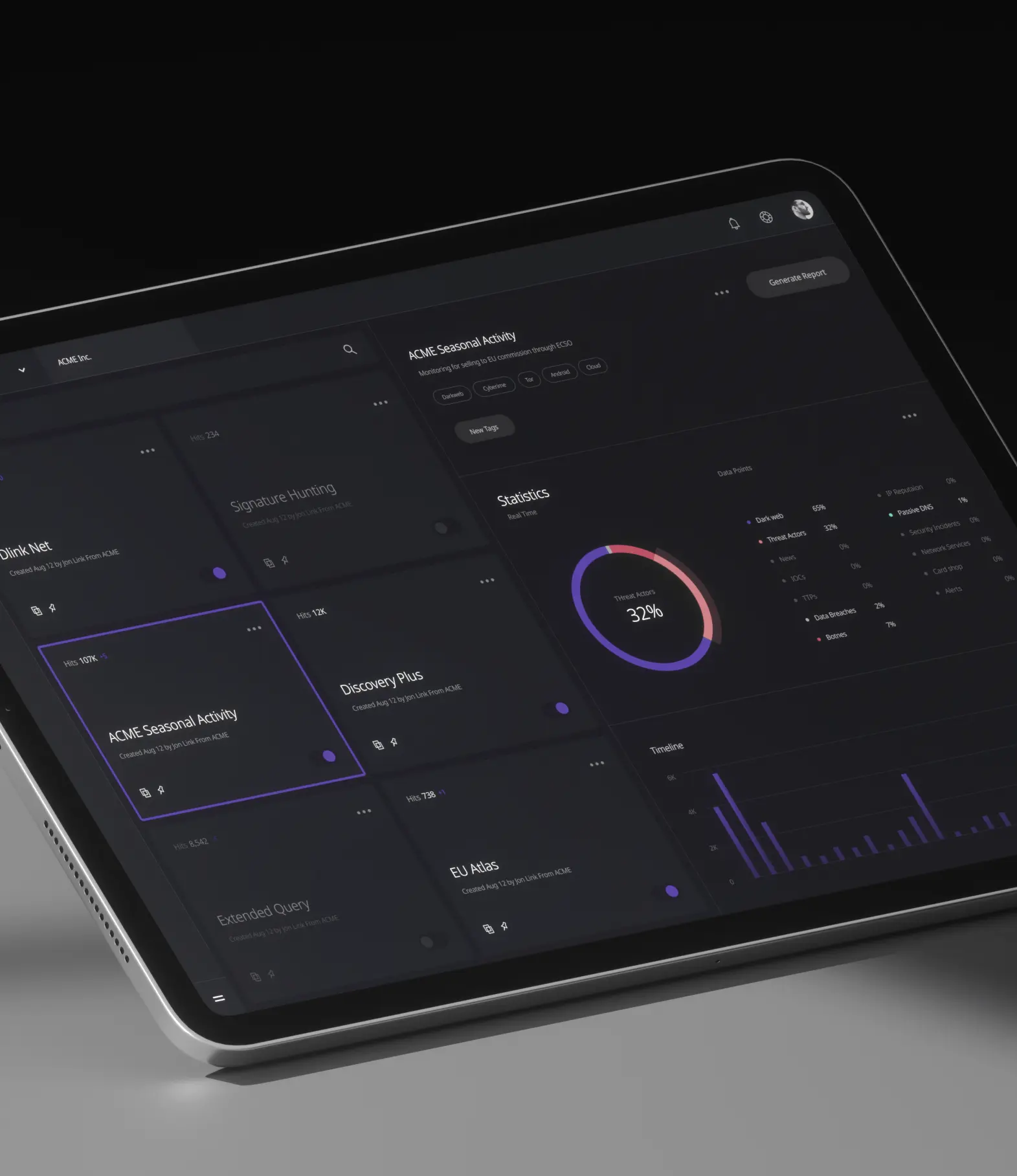
Feel the difference of Contexttm, the ability to draw from an unparalleled number of sources gives Contexttm the leading edge in Cyber Security.
- Botnet
- Darkweb
- Threat actors
- ISP Traffic
- Data breaches
- Credit Cards
- Malware
Context™ is based on a classic six-step process called the Intelligence Cycle. Used by government agencies and industry experts to support a balanced and comprehensive approach to intelligence gathering and analysis.

intelligence cycle
Contexttm process is a tried and trusted method used by high caliber Governments and institutions during their investigations.
planning
Contexttm receives subjects of interest from the user enabling a definition of criteria and direction for further intelligence collection. Based on specific factors, Contexttm prioritizes sources by leveraging AI & ML mechanisms to formulate the most adequate results.
collection
Contexttm harnesses a constantly expanding cloud of indexed threat artifacts and associated adversaries. The platform captures the results based on source criteria for further enrichment and tagging.
processing
This involves converting vast amounts of information collected to form usable data through decryption, language translation, and data reduction forming a suitable structure for intelligence production.
analysis & production
For organizations to make strategic and timely decisions, intelligence must be current and actionable with enough context to fully interpret. Effective intelligence production focuses on the consumer’s requirements.
dissemination
To convey the intelligence to the consumer in a usable form, intelligence can be provided to the consumer in a variety of formats. Contexttm is flexible, providing a workspace for collaboration between team members to store and distribute the final intelligence dossier.
evaluation
Providing feedback on whether your requirements are met is fundamental to creating a successful intelligence dossier. Adjustments or improvements to the intelligence can be made to suit your requirements. This information is used to score and train the ML engine.
Threat artifacts, including indicators of compromise (IOCs), indicators of attacks (IOAs), tools, tactics and procedures (TTPs) of adversaries with valuable meta-data stored in a historical form used to deep-dive investigations.
Profiles of threat actors collected from various underground communities and criminal marketplaces, intelligence reports and security expert communities with associated metadata.
Fully indexed and translated Dark Web data entries with extracted artifacts, graphical screenshots and link visualizations.
languages
A built-in offline translation solution and unique linguistic expertise provide details on threat actors’ digital chatter.
sources
A continuously updated repository of Dark Web sources, including Tor; I2P, Freenet, IRC, IM groups (Telegram) and more.
Our team is ready to act as and when your organization requires a specific skill set from any one of a vast array of cyber security vertices. Our team is trained in multiple specializations, we are here to help you and your organization so business remains unaffected.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps

